Network security risk assessment method
A risk assessment and network security technology, applied in the field of network security, can solve the problems of inability to effectively restore attack scenarios, predict attack behavior, and have not yet found a solution, and achieve the effect of improving accuracy and real-time performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
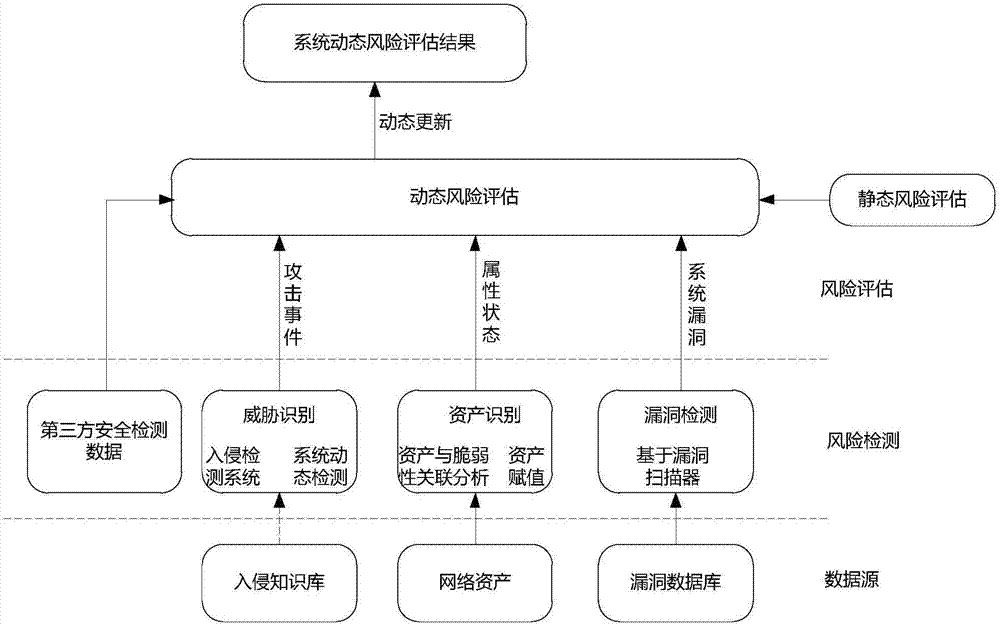
[0024] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. The method of the invention dynamically evaluates the security of the target network by combining the intrusion detection system, the loophole detection and the real-time attack events acquired by the third party on the basis of the static risk assessment. Assets, Threats and Vulnerabilities are the 3 basic elements of risk assessment.
[0025] In risk assessment, asset value is usually defined by experts or managers during static assessment, and there will be no major changes over a period of time. The threat and vulnerability information acquisition can be carried out with the help of corresponding tools. After the static risk assessment, the system risk is reduced to an acceptable range. Over time, under the influence of internal and external factors, and threats and vulnerabilities change, system risk will increase beyond the acce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com