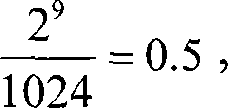An information system risk evaluation method and system
An information system and risk assessment technology, applied in transmission systems, digital transmission systems, security communication devices, etc., can solve the problem of high security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
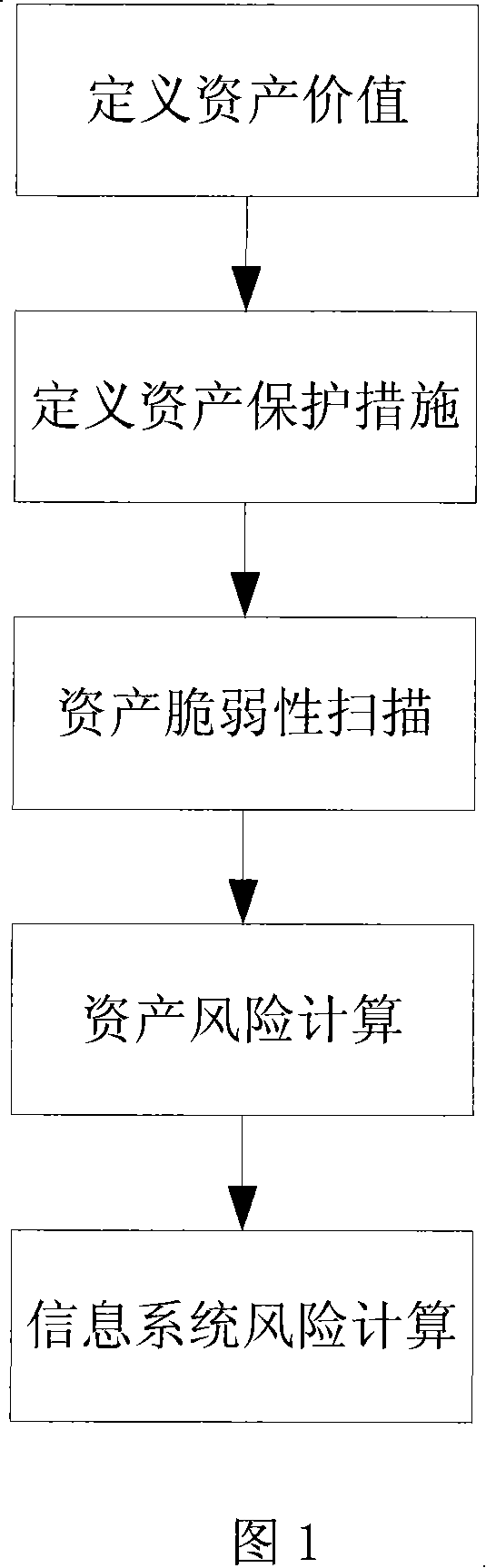
[0045] This embodiment is a specific implementation of the information system risk assessment method, and the main operation process is shown in FIG. 1 . The specific process of this embodiment includes the following steps:
[0046] 1. Define asset value
[0047] The asset value A of the host can be divided into five levels by the administrator according to the importance and value of the host. The higher the level, the higher the asset value, and the value range of asset value A is 0-1. The division method adopted in the present invention is:
[0048] Asset value is small: A=0.2;
[0049] The asset value is small: A=0.4;
[0050] Medium asset value: A=0.6;
[0051] Larger asset value: A=0.8;
[0052] The asset value is extremely large: A=1.
[0053] 2. Define Asset Protection Measures
[0054]Asset protection measures refer to the existing security devices and measures in the system, which can make assets prevent attacks against certain services. Asset protection mea...
Embodiment 2
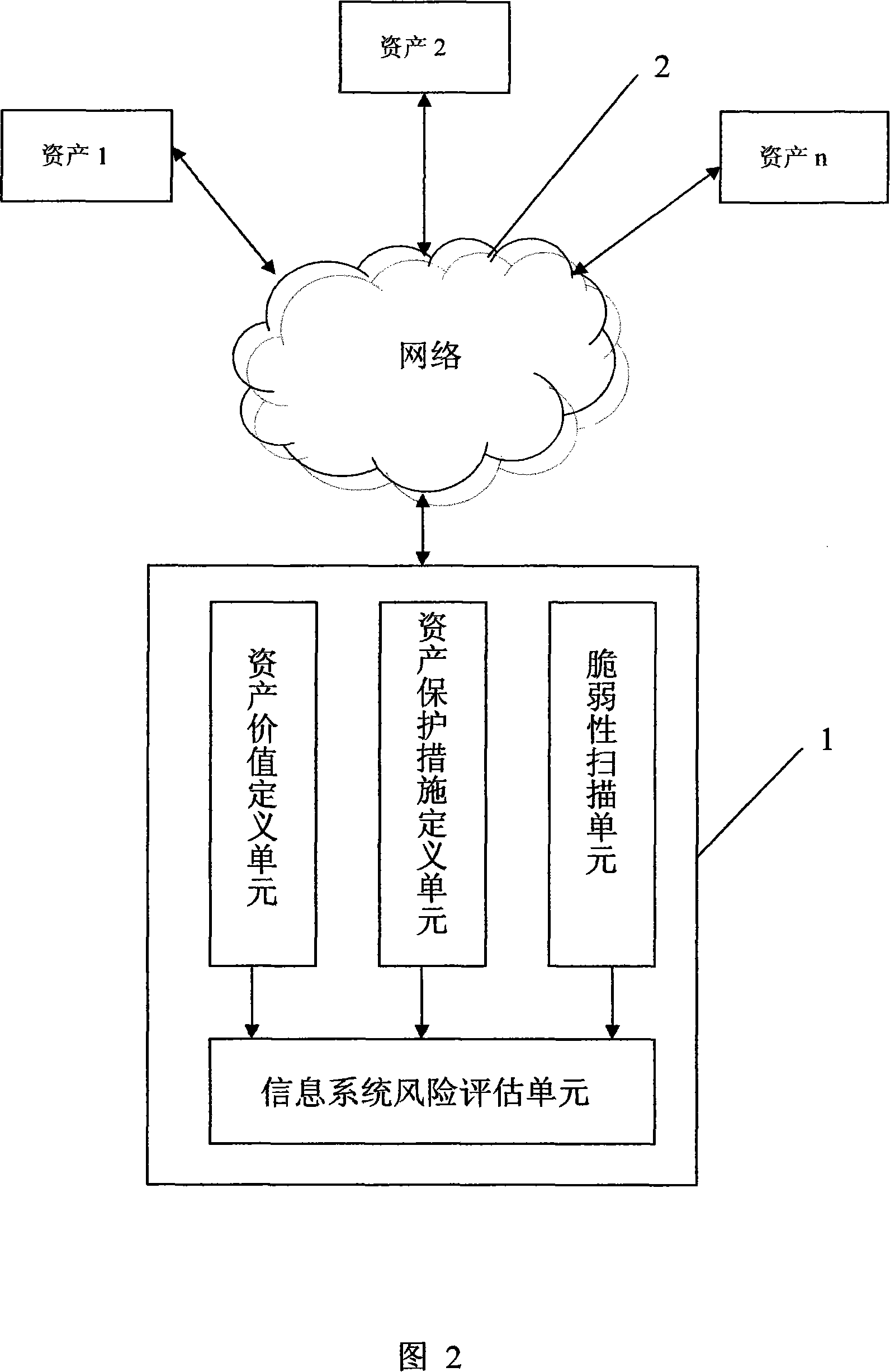
[0101] This embodiment is an example of an asset risk assessment process, and the main operation process is shown in FIG. 2 . The risk assessment system 1 scans the vulnerability of each asset in the system through the network 2, and then completes the calculation of the risk value of each asset and the entire information system based on the asset value, the protection measures taken by the asset, and the vulnerability scanning results, combined with the vulnerability information database. . Assuming that asset 1 is a computer, the vulnerabilities existing on the computer, the CVSS score of the vulnerability, and the services corresponding to each vulnerability are shown in Table 1 below: Table 1
[0102] Vulnerability name
CVSS score
Corresponding service
6.4
service 1
3.3
service 2
Vulnerability 3
8.0
service 2
Vulnerability 4
10.0
service 3
[0103] Assum...
Embodiment 3
[0118] This embodiment is an example of an information system risk assessment process. Suppose there are two information systems, System 1 and System 2. Information system 1 contains 100 computers, one of which is extremely risky, with a risk value of 0.95; the remaining 99 computers do not contain any vulnerabilities, with a risk value of 0. Information system 2 contains 10 computers, one of which is extremely risky, with a risk value of 0.95; the remaining 9 computers do not contain any vulnerabilities, with a risk value of 0. According to formula (5), the risk value of information system 1 is:
[0119] N 1 = [ 1 - ( 1 - 0.95 ) · 1 99 ] · ( 0.9 + 0.95 100 ) ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com