Asset dependence relation-based information security risk evaluation method and system
A dependency and information system technology, applied in transmission systems, electrical components, etc., can solve problems such as inaccurate risk assessment results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0086] The present invention will be further described below in conjunction with examples.
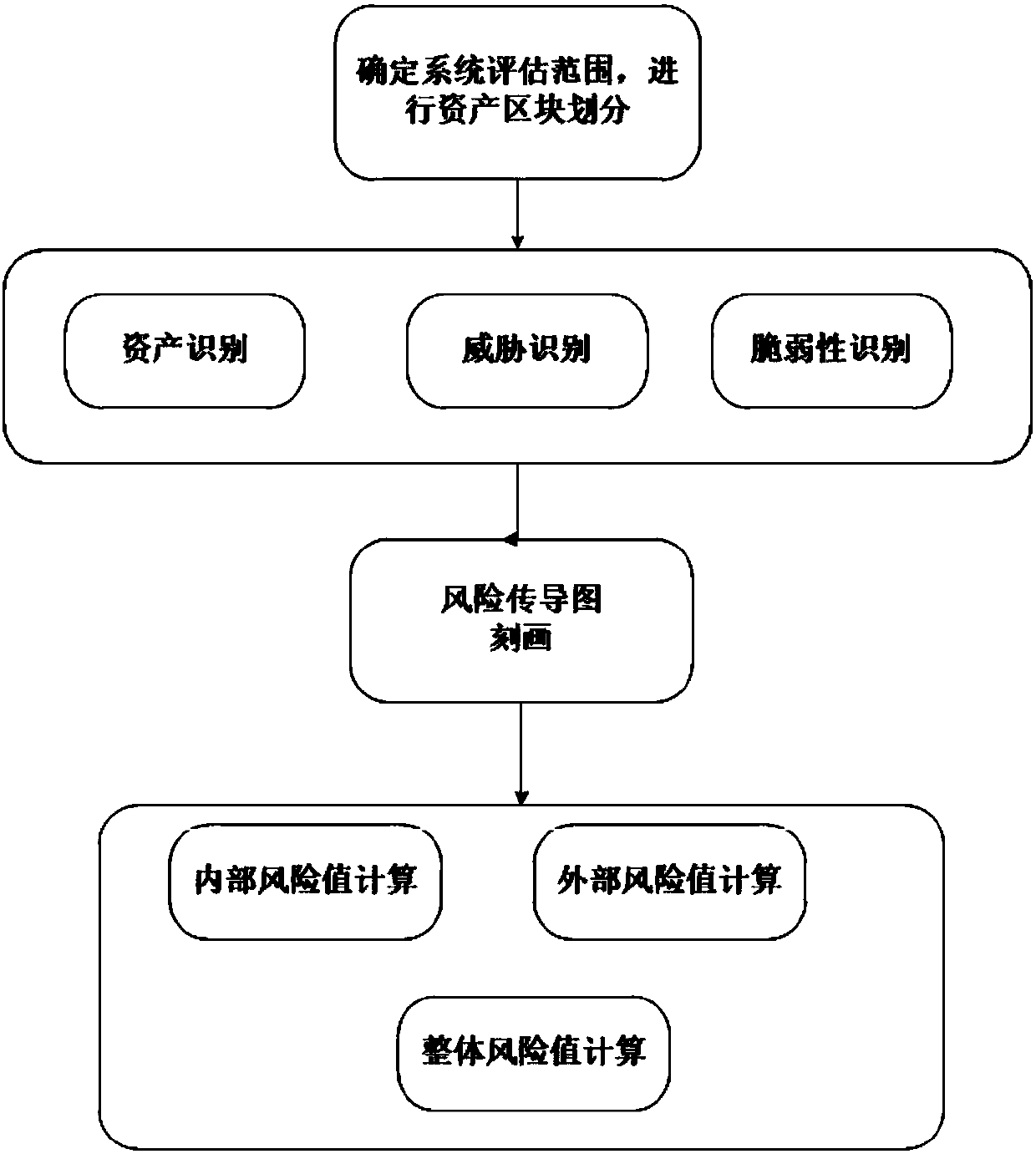
[0087] Such as figure 1 As shown, the embodiment of the present invention provides an information security risk assessment method based on asset dependencies, including the following steps:
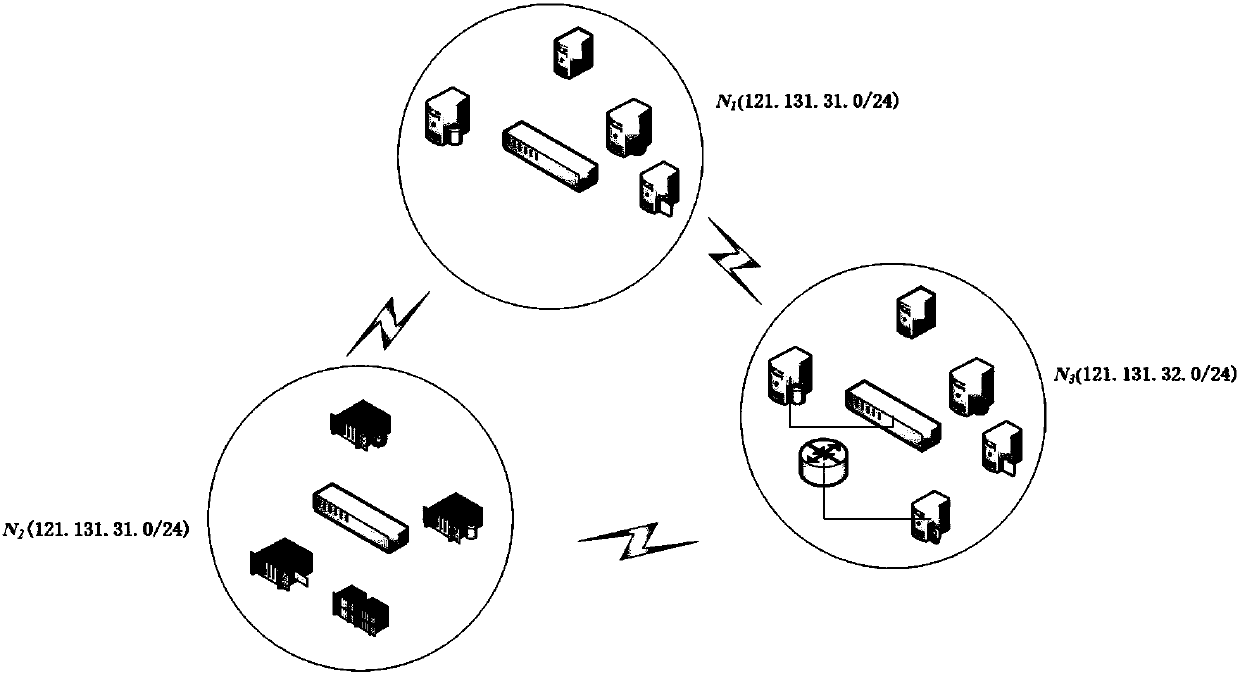
[0088] Step 1: Obtain the scope of information assets in the information system to be evaluated, and divide the assets into blocks according to the logical network location and / or asset function of the assets;
[0089] Step 2: Identify the threat, vulnerability, and asset importance of the information system to be assessed, and obtain the asset importance value, threat threat value, and vulnerability vulnerability value;
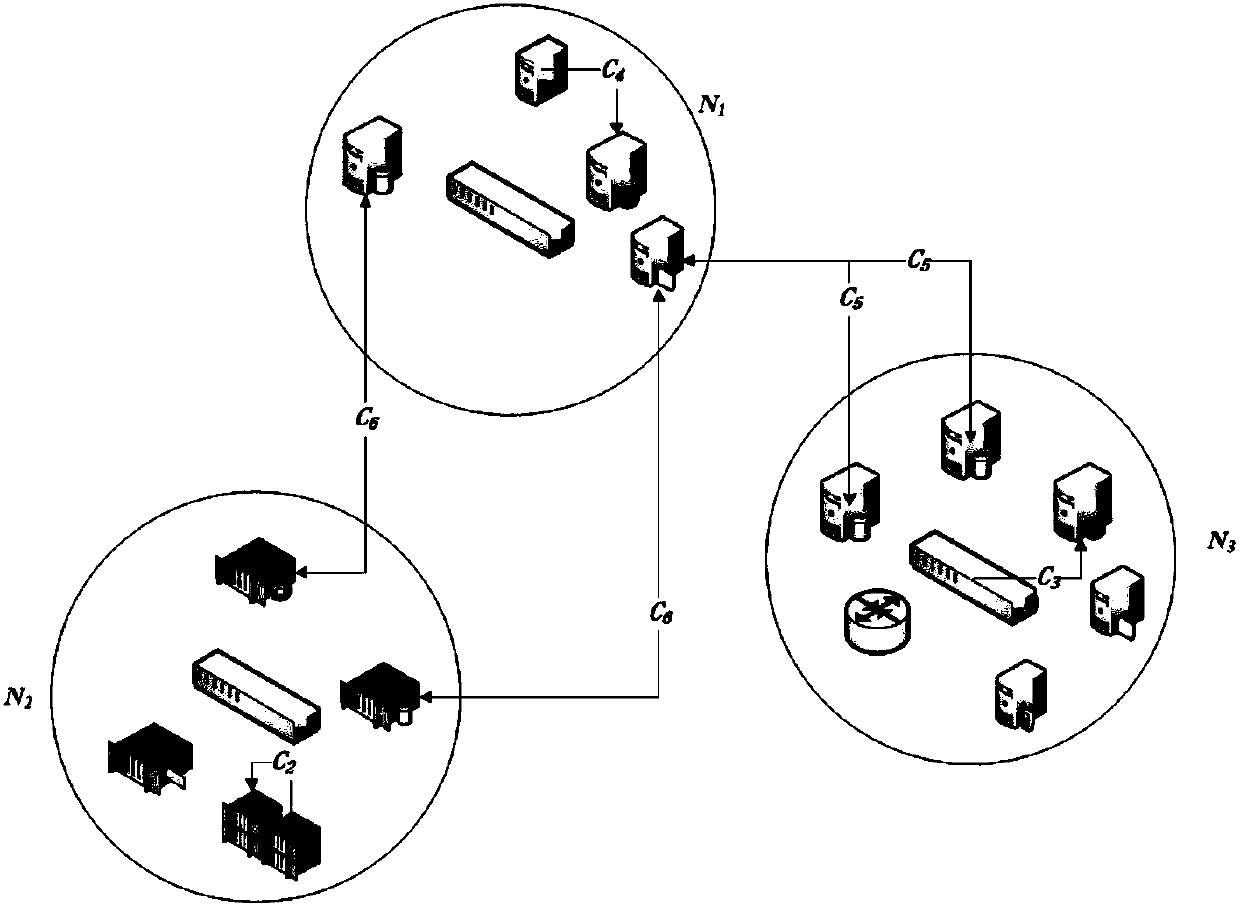
[0090] Step 3: Use the dependency structure matrix to calculate and construct the security dependency matrix between assets, and use the Delphi method to determine the risk transmission coefficient between assets and construct the risk transmission relationship based on the sec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com