System and method for evaluating security risk based on asset weak point analysis
A technology for assessing system and security risks, applied in transmission systems, computer security devices, instruments, etc., can solve problems such as the inability to accurately calculate the degree of system threat, and achieve the effect of beneficial risk assessment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
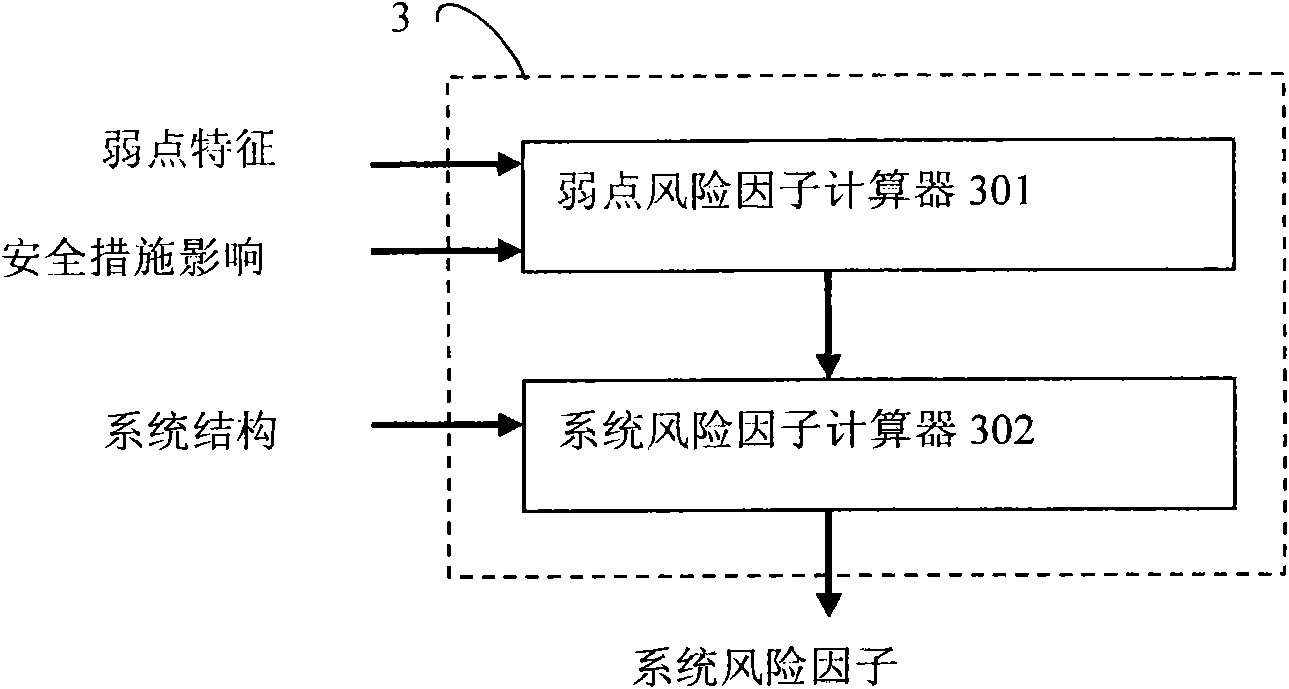
[0031] Example 1. image 3 is a system composition block diagram according to aspects of the present invention, which includes two cascaded risk factor calculators:
[0032] Weakness risk factor calculator 301, used to read the characteristics of the discovered weakness and the impact of corresponding security measures, and calculate the risk factor of the weakness;
[0033] The system risk factor calculator 302 is used to read the risk factor of the vulnerability and the structural composition information of the system, and calculate the total risk factor of the entire evaluated system.
Embodiment 2
[0034] Example 2. Figure 4 It is a structural block diagram of the vulnerability risk factor calculator 301 of a security risk assessment system based on asset vulnerability analysis according to Embodiment 1, which includes:
[0035] 1) The vulnerability feature reading device 401 is used to obtain a security feature of a vulnerability and send it to the vulnerability risk factor calculation output device 403;
[0036] 2) The vulnerability security measure reading device 402 is used to obtain the impact value of the system's security measures for the vulnerability on the security of the vulnerability, and send it to the vulnerability risk factor calculation output device 403;
[0037] 3) Weakness risk factor calculation output means 403, used to calculate and output the risk factor of a weakness.
Embodiment 3
[0038] Example 3. Figure 5 It is a structural composition block diagram of a system risk factor calculator 302 of a security risk assessment system based on asset weakness analysis according to Embodiment 1, which includes:
[0039]1) The system structure reading device 501 is used to obtain the structure information of the evaluated system and send it to the system risk factor calculation output device 503;
[0040] 2) Weakness risk factor reading device 502, used to acquire the risk factors of each weakness output by the system's vulnerability risk factor calculator and send them to the system risk factor calculation output device 503;
[0041] 3) System risk factor calculation and output means 503, used to calculate and output the total risk factor of the evaluated system.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com