Threat detection and alert method and system based on big data analysis
A technology of threat detection and big data, which is applied in the field of information security technology and big data, can solve the problems of inversion, low efficiency, misreporting or omission of correlation analysis engine, etc., and achieve the effect of reducing the impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] Below is further detailed description of the present invention according to accompanying drawing and example:
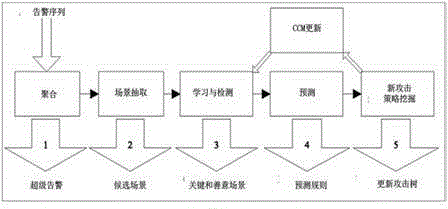
[0038] Many methods exist for alarm correlation analysis, however, each of them has many drawbacks. The method provided by this patent provides a real-time algorithm very suitable for EWS alarm correlation analysis.
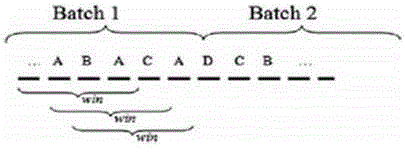
[0039] The alarm correlation analysis framework provided by this patent collects log information of various security devices such as IDS and IPS. Since they are log information generated by different devices, it is necessary to normalize them and sort alarms in chronological order. Then, the main attack scenario detection algorithm plays its part. Information security equipment generates most of the alarms. For the convenience of analysis, the alarm sequence is first divided into batches and then the batches are divided into smaller parts, namely: episode windows. figure 1 A schematic diagram of scene extraction using scene window is giv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com