Patents
Literature
30 results about "Information security audit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An information security audit is an audit on the level of information security in an organization. Within the broad scope of auditing information security there are multiple types of audits, multiple objectives for different audits, etc. Most commonly the controls being audited can be categorized to technical, physical and administrative. Auditing information security covers topics from auditing the physical security of data centers to auditing the logical security of databases and highlights key components to look for and different methods for auditing these areas.
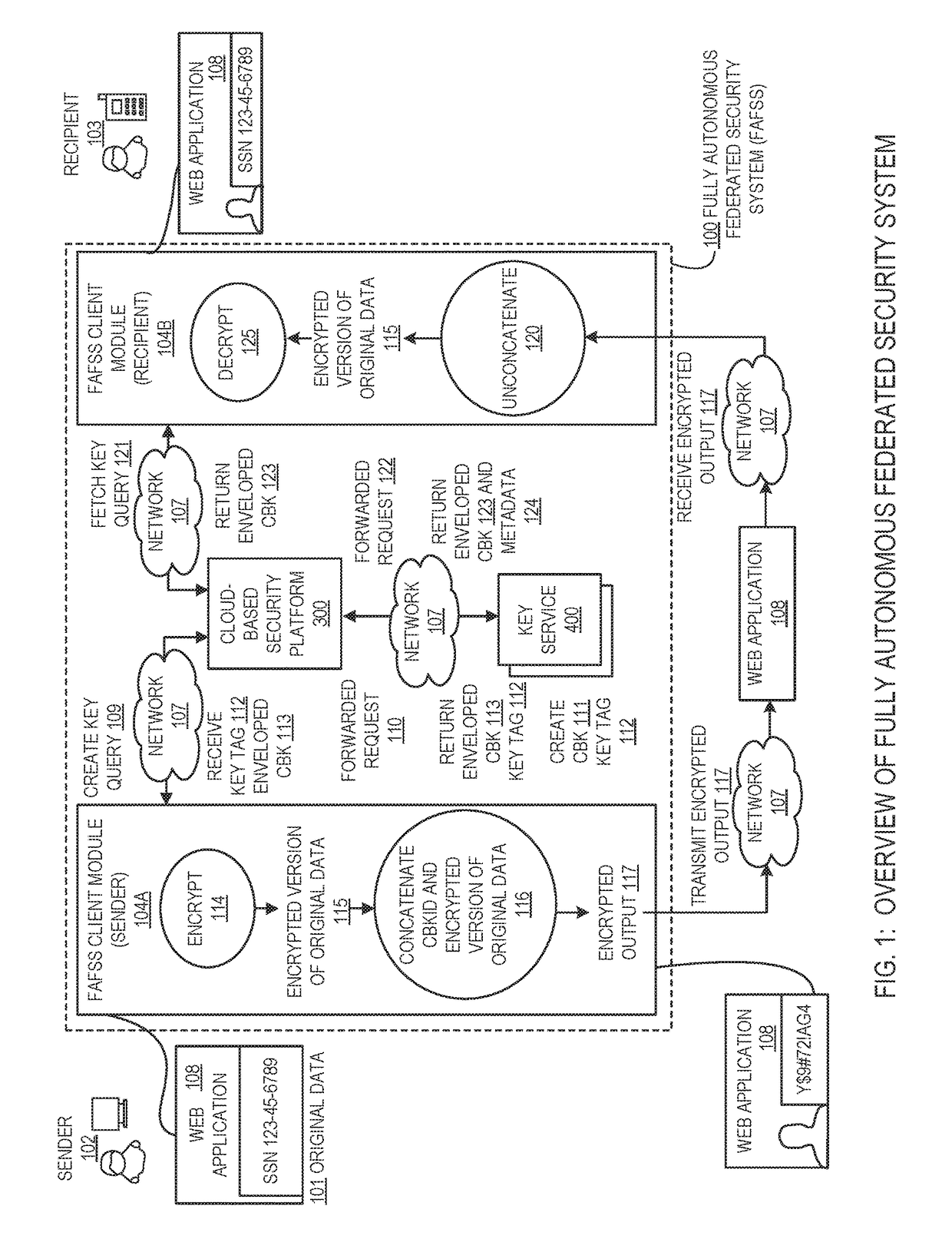
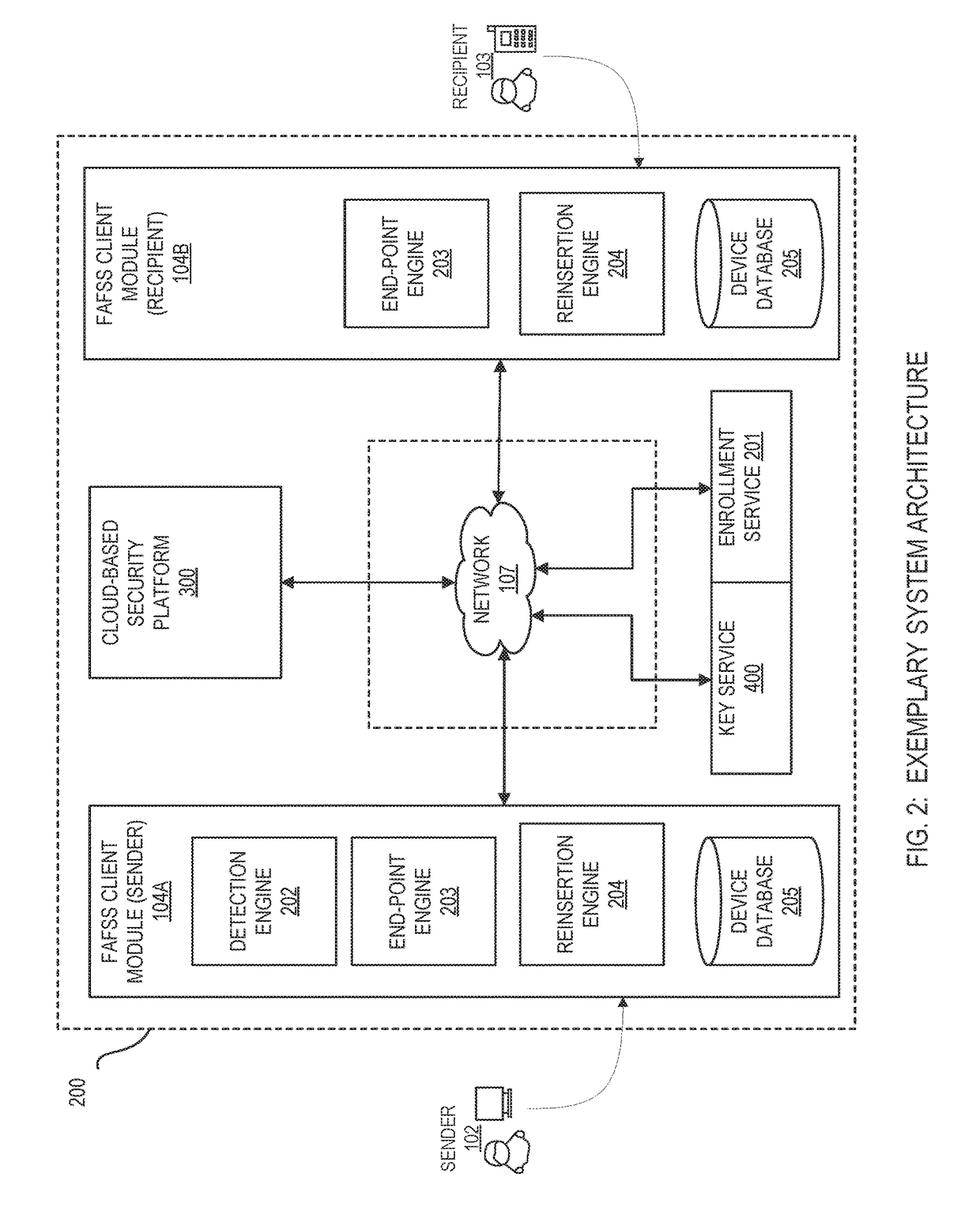
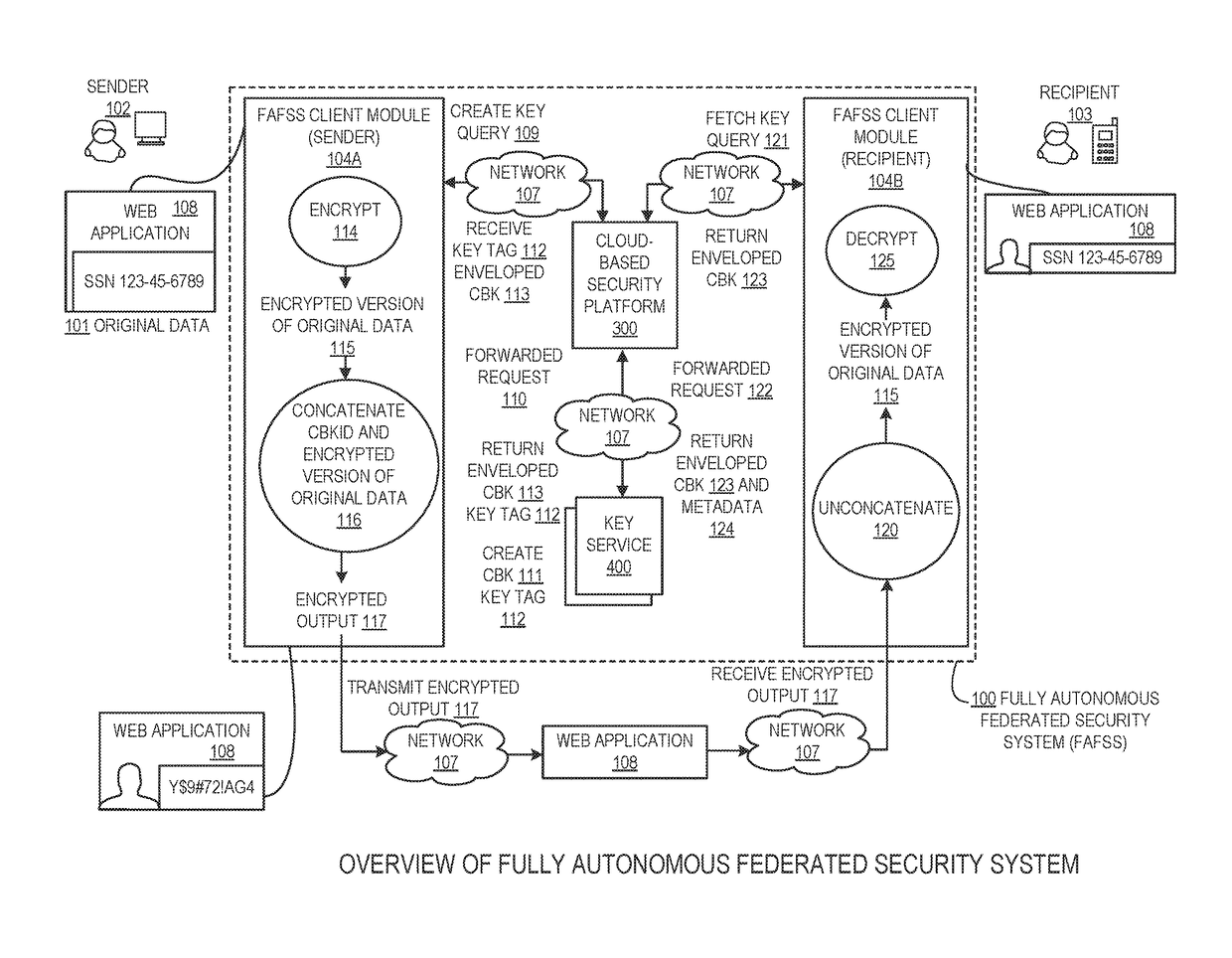
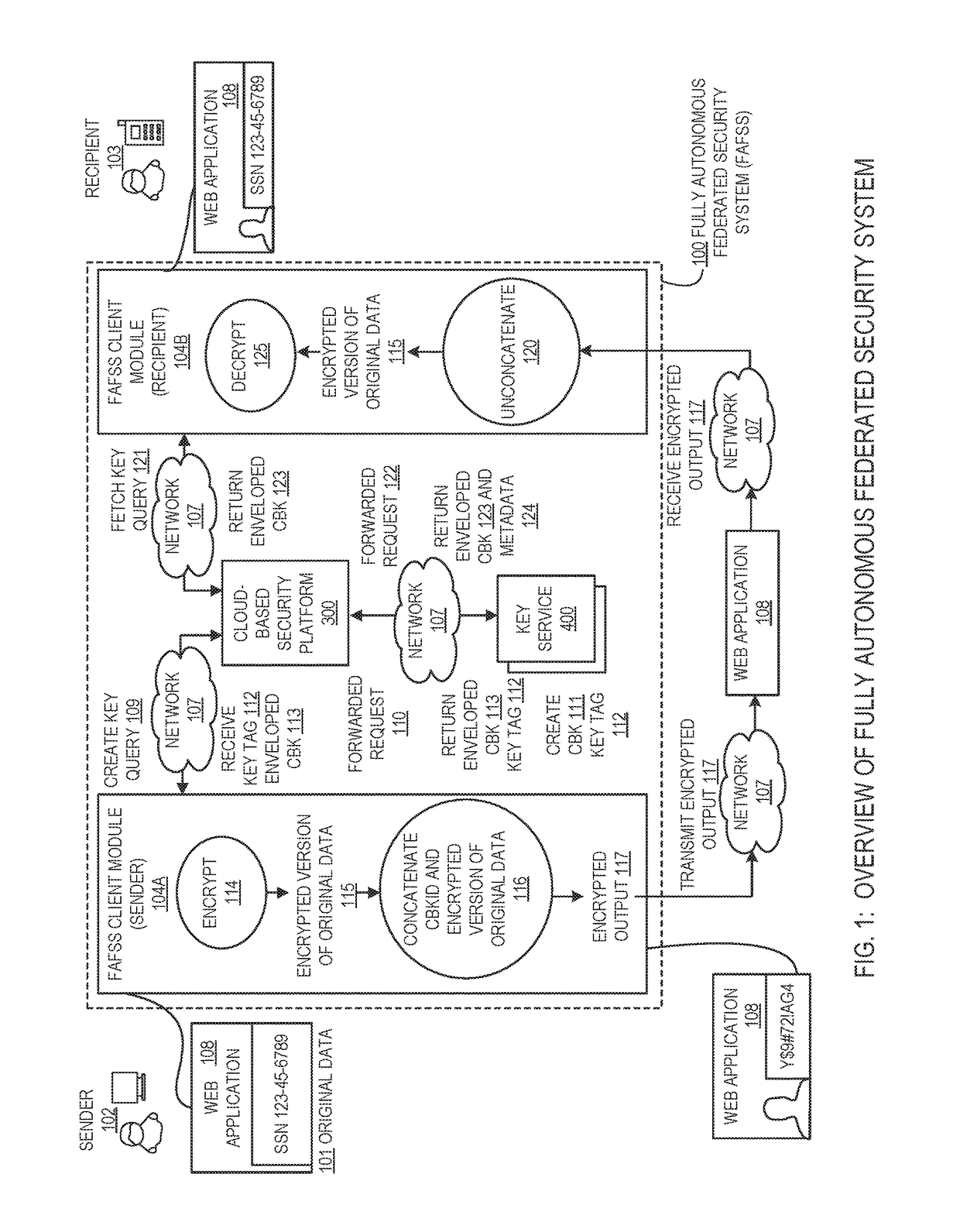
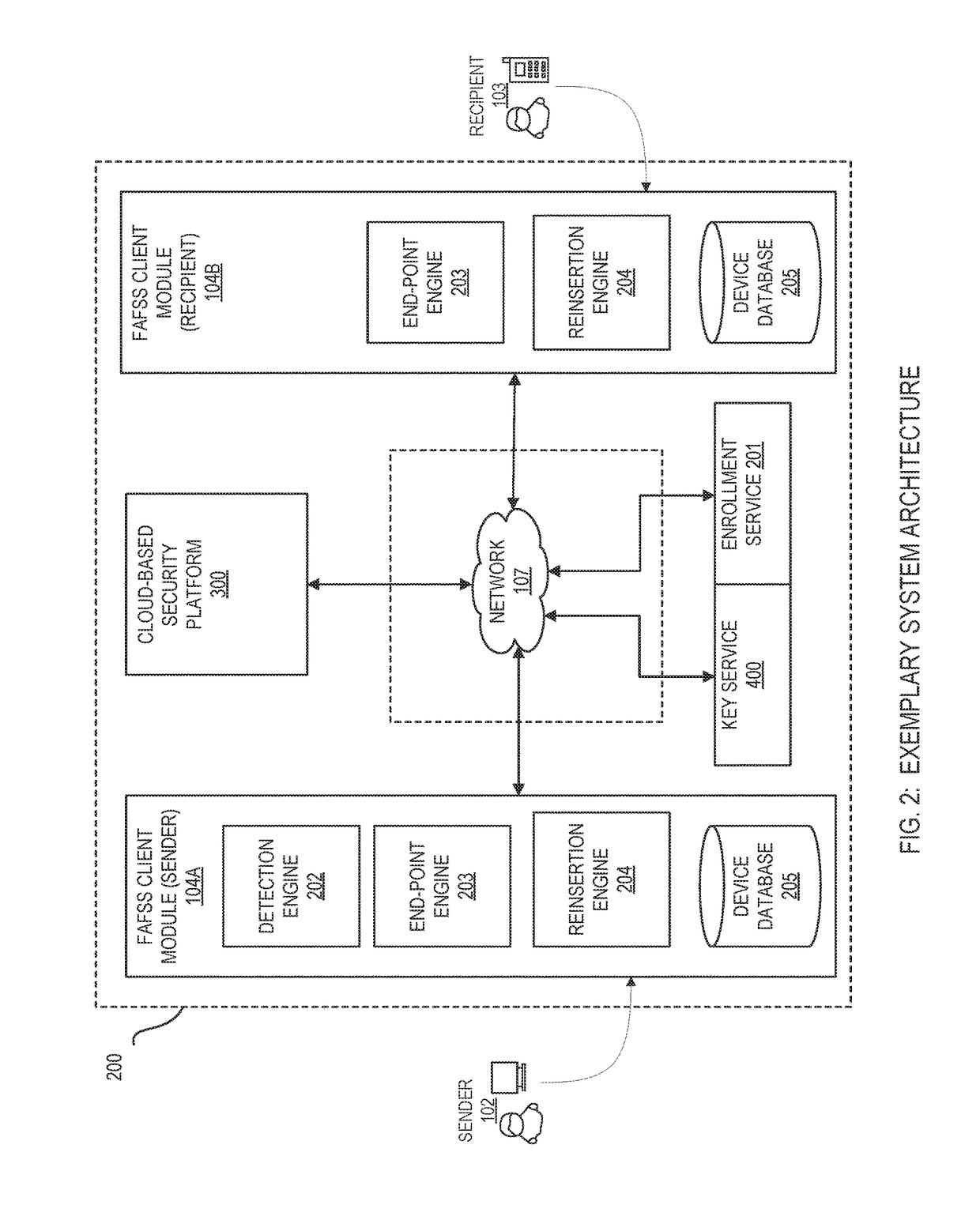
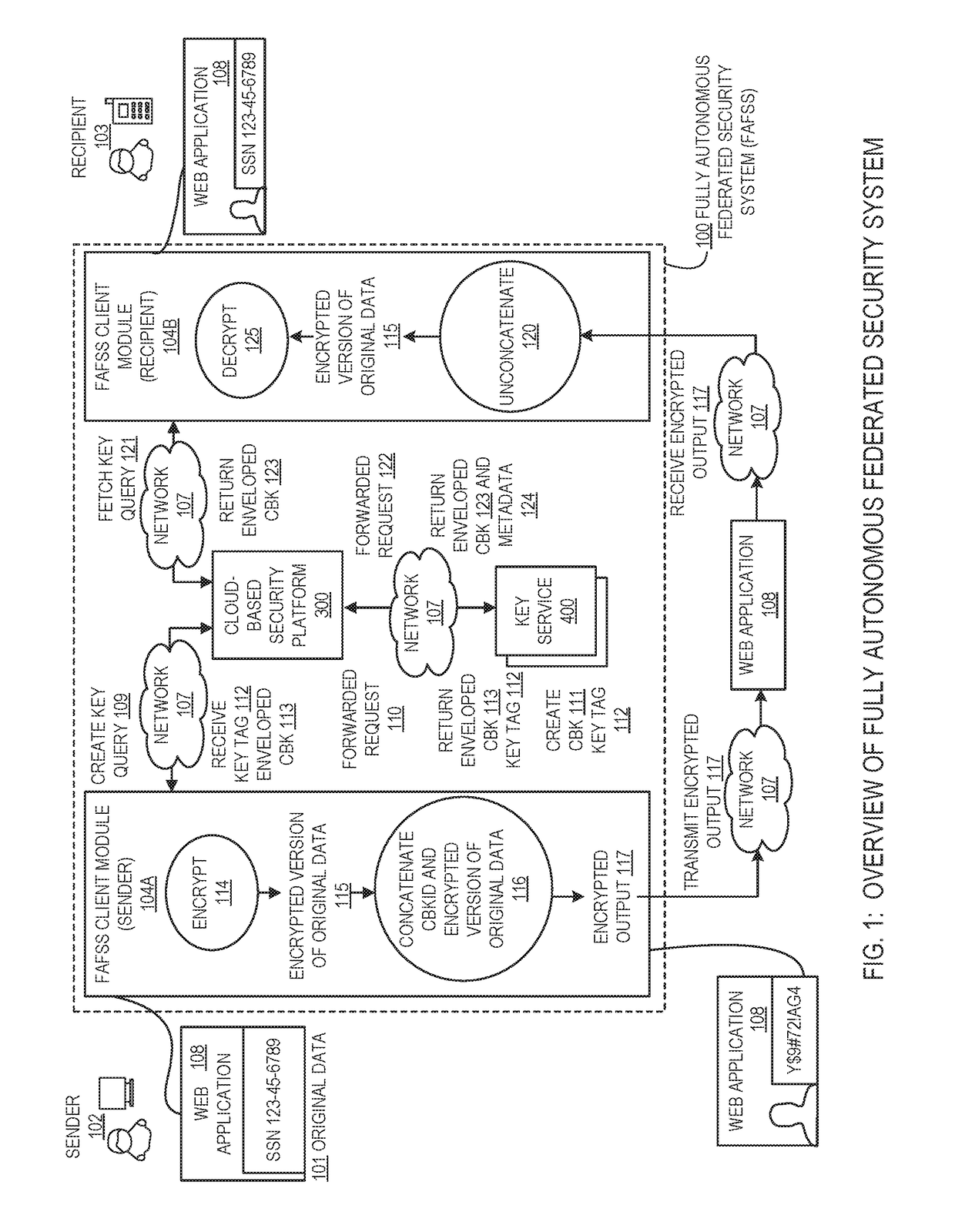
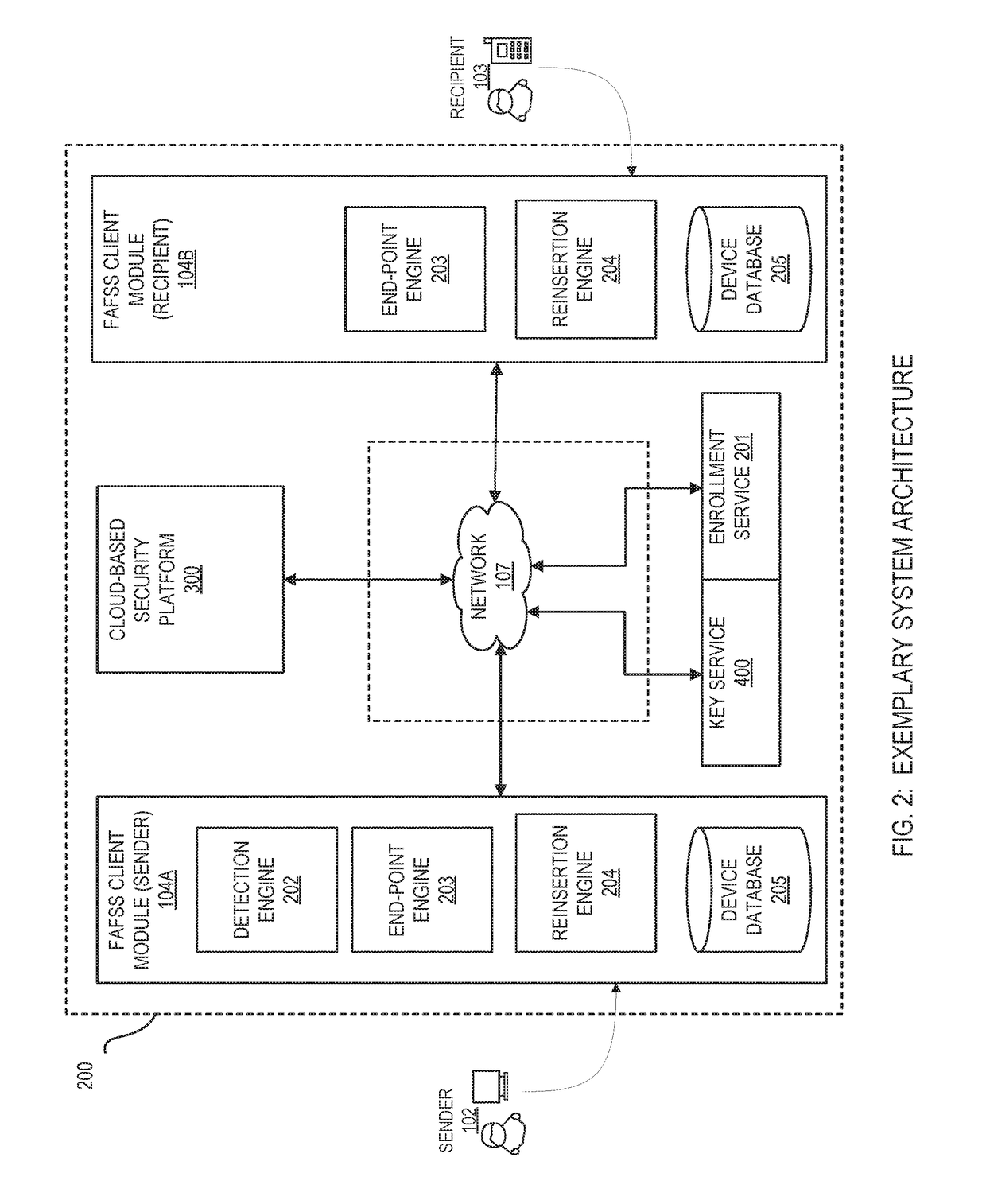
Systems and methods for encryption and provision of information security using platform services
ActiveUS9608809B1Enhanced interactionOptimizationKey distribution for secure communicationDigital data protectionCiphertextOriginal data
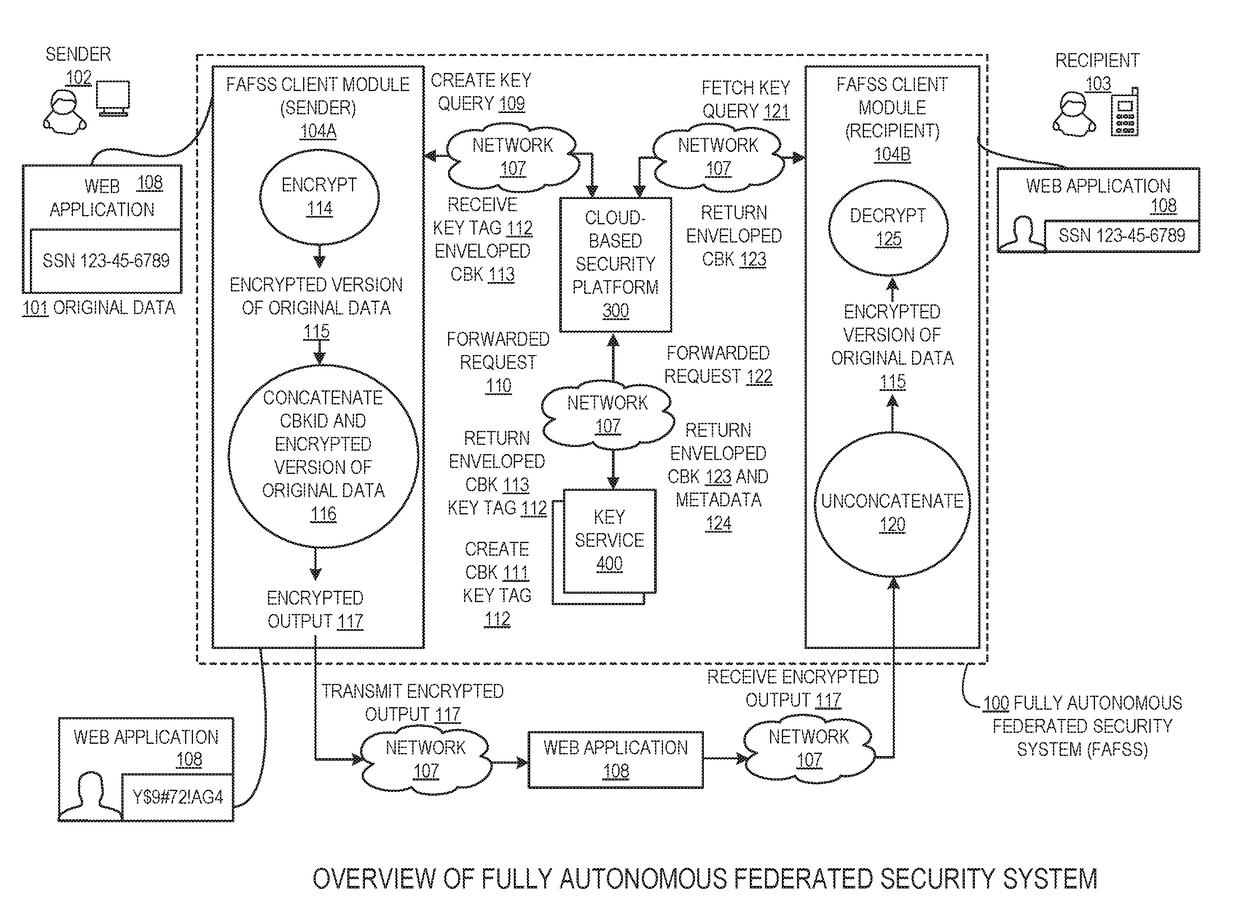
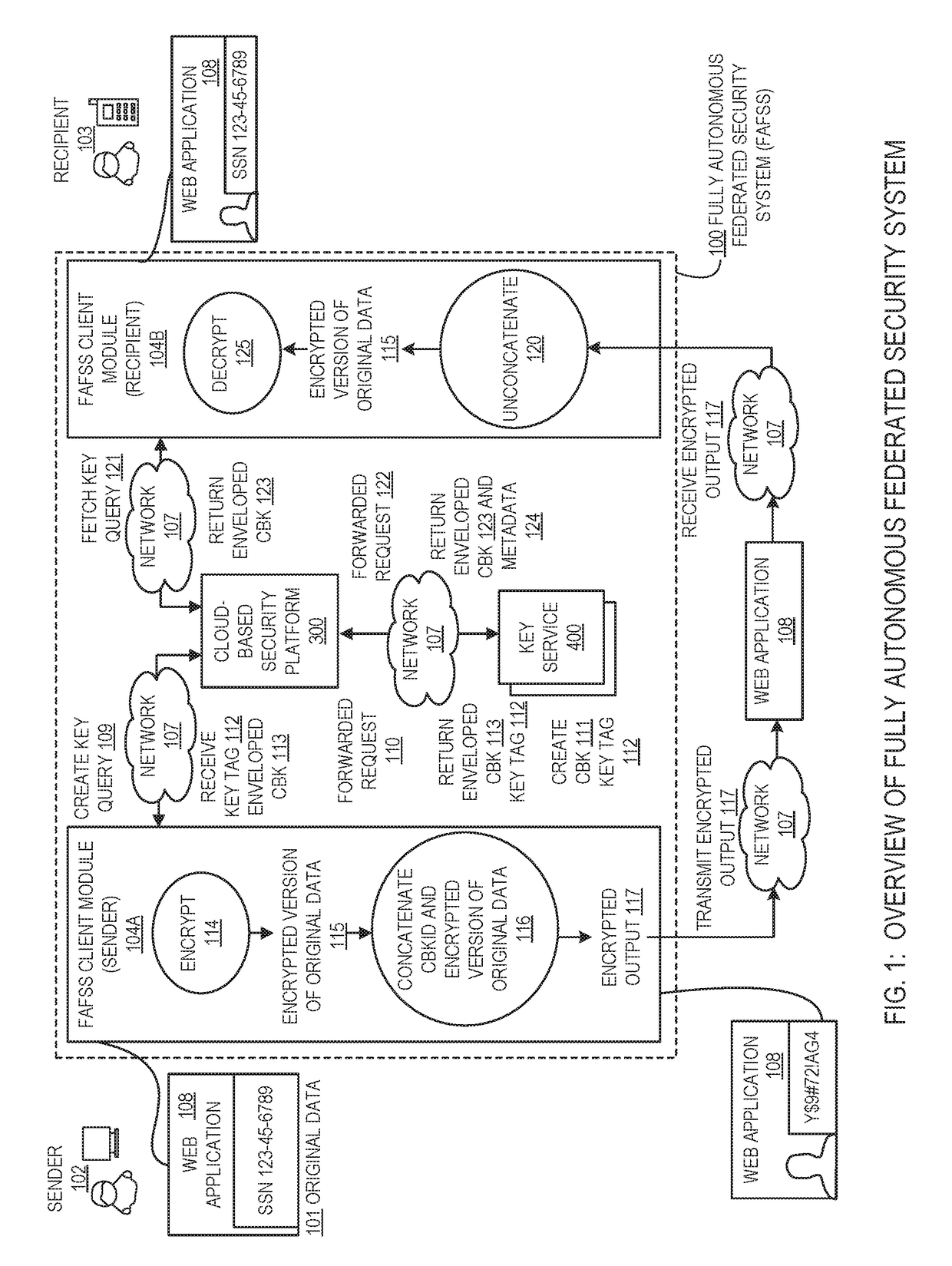
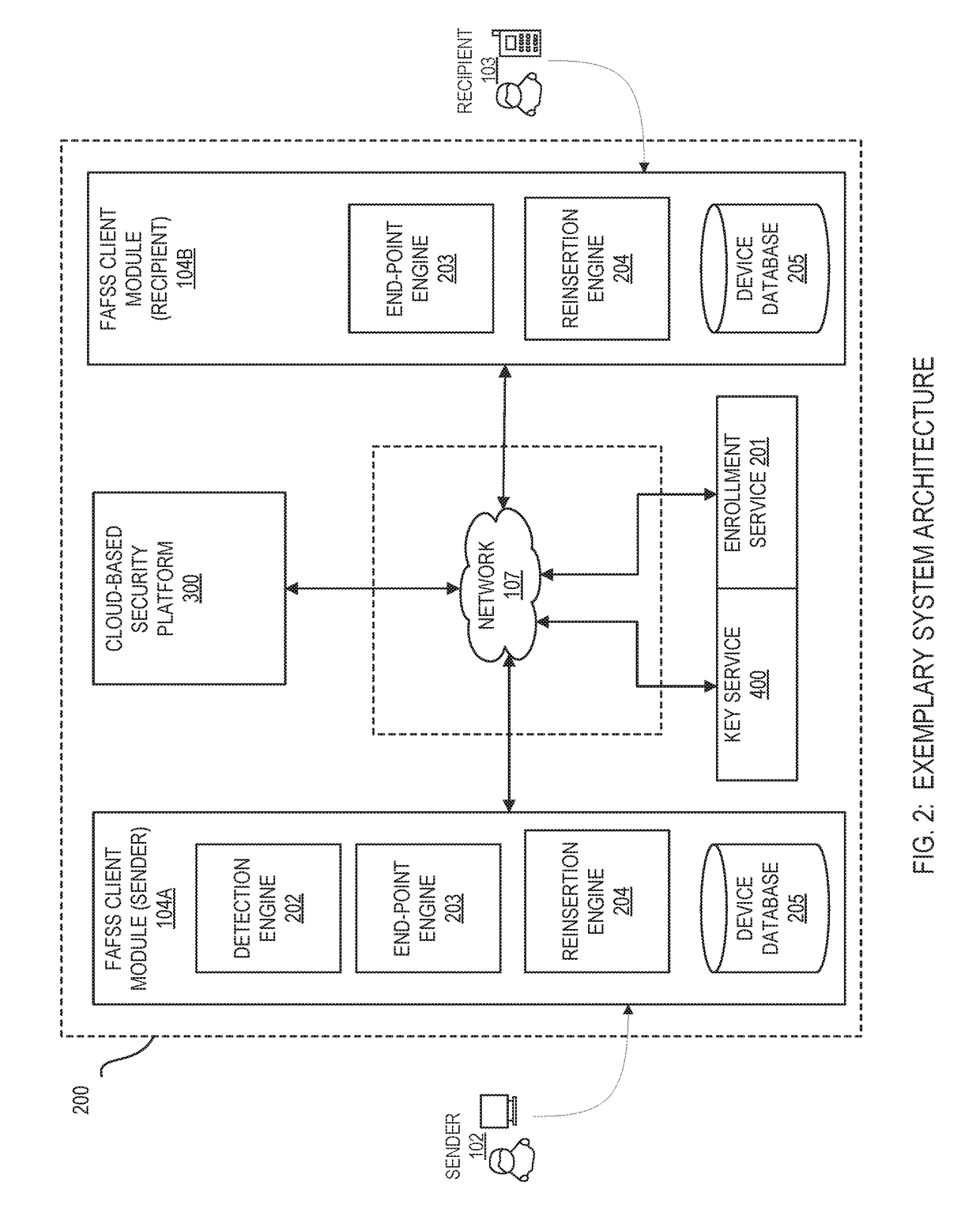
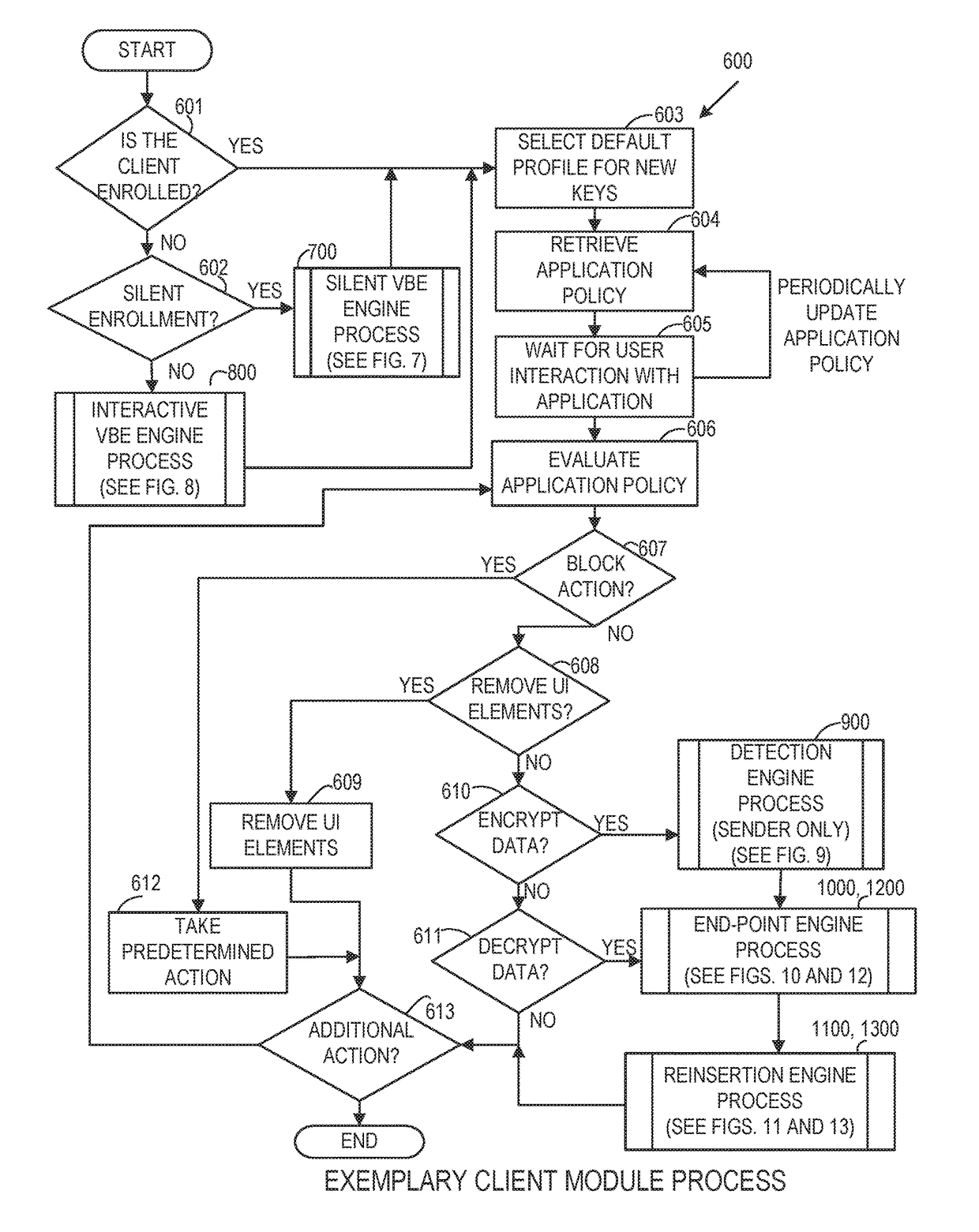
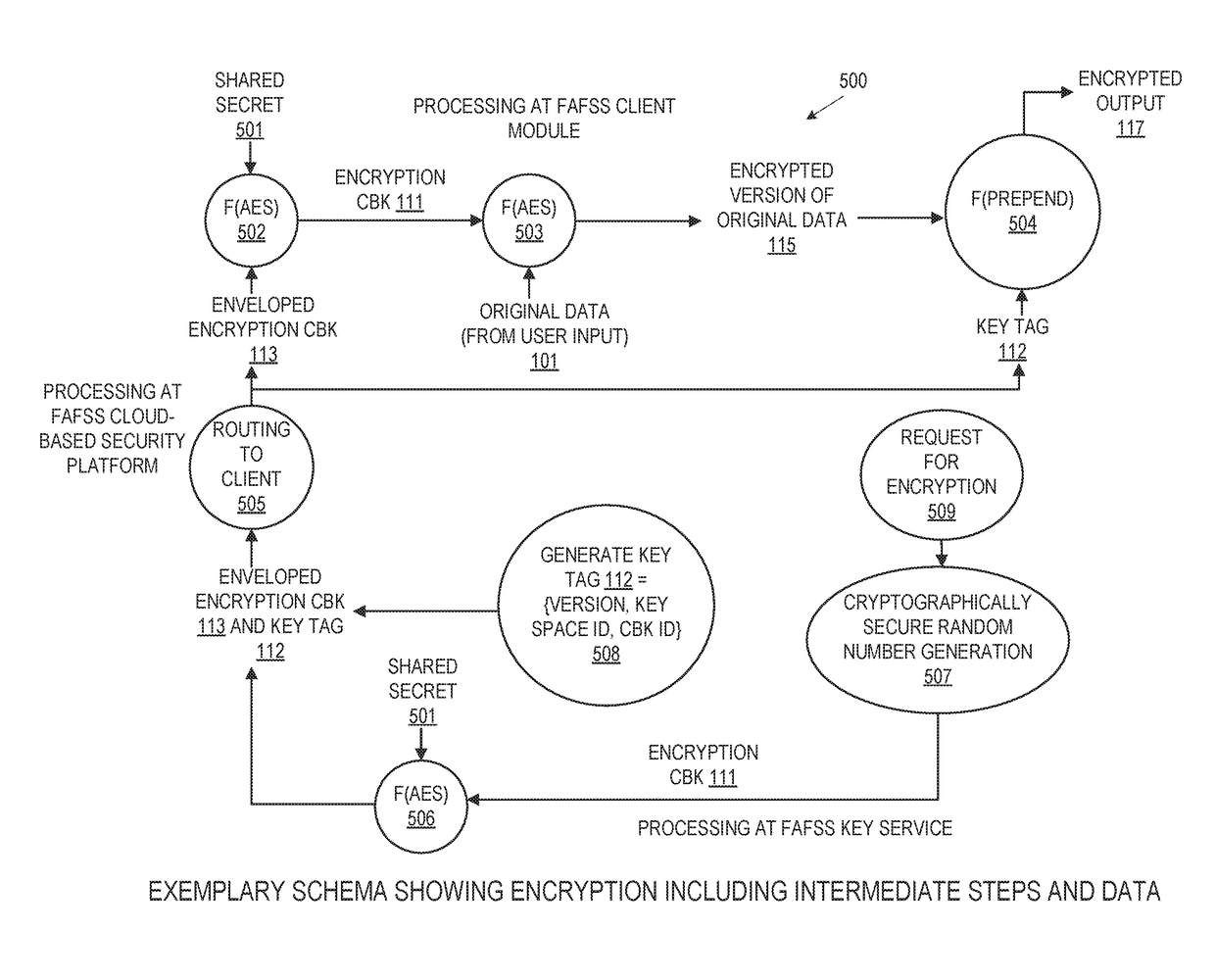
Systems and methods for securing or encrypting data or other information arising from a user's interaction with software and / or hardware, resulting in transformation of original data into ciphertext. Generally, the ciphertext is generated using context-based keys that depend on the environment in which the original data originated and / or was accessed. The ciphertext can be stored in a user's storage device or in an enterprise database (e.g., at-rest encryption) or shared with other users (e.g., cryptographic communication). The system generally allows for secure federation across organizations, including mechanisms to ensure that the system itself and any other actor with pervasive access to the network cannot compromise the confidentially of the protected data.
Owner:IONIC SECURITY
Systems and methods for encryption and provision of information security using platform services
ActiveUS9608810B1Enhanced interactionOptimizationKey distribution for secure communicationDigital data protectionCiphertextOriginal data
Systems and methods for securing or encrypting data or other information arising from a user's interaction with software and / or hardware, resulting in transformation of original data into ciphertext. Generally, the ciphertext is generated using context-based keys that depend on the environment in which the original data originated and / or was accessed. The ciphertext can be stored in a user's storage device or in an enterprise database (e.g., at-rest encryption) or shared with other users (e.g., cryptographic communication). The system generally allows for secure federation across organizations, including mechanisms to ensure that the system itself and any other actor with pervasive access to the network cannot compromise the confidentially of the protected data.
Owner:IONIC SECURITY
Systems and methods for encryption and provision of information security using platform services
ActiveUS9614670B1Enhanced interactionOptimizationKey distribution for secure communicationUser identity/authority verificationCiphertextOriginal data
Owner:IONIC SECURITY
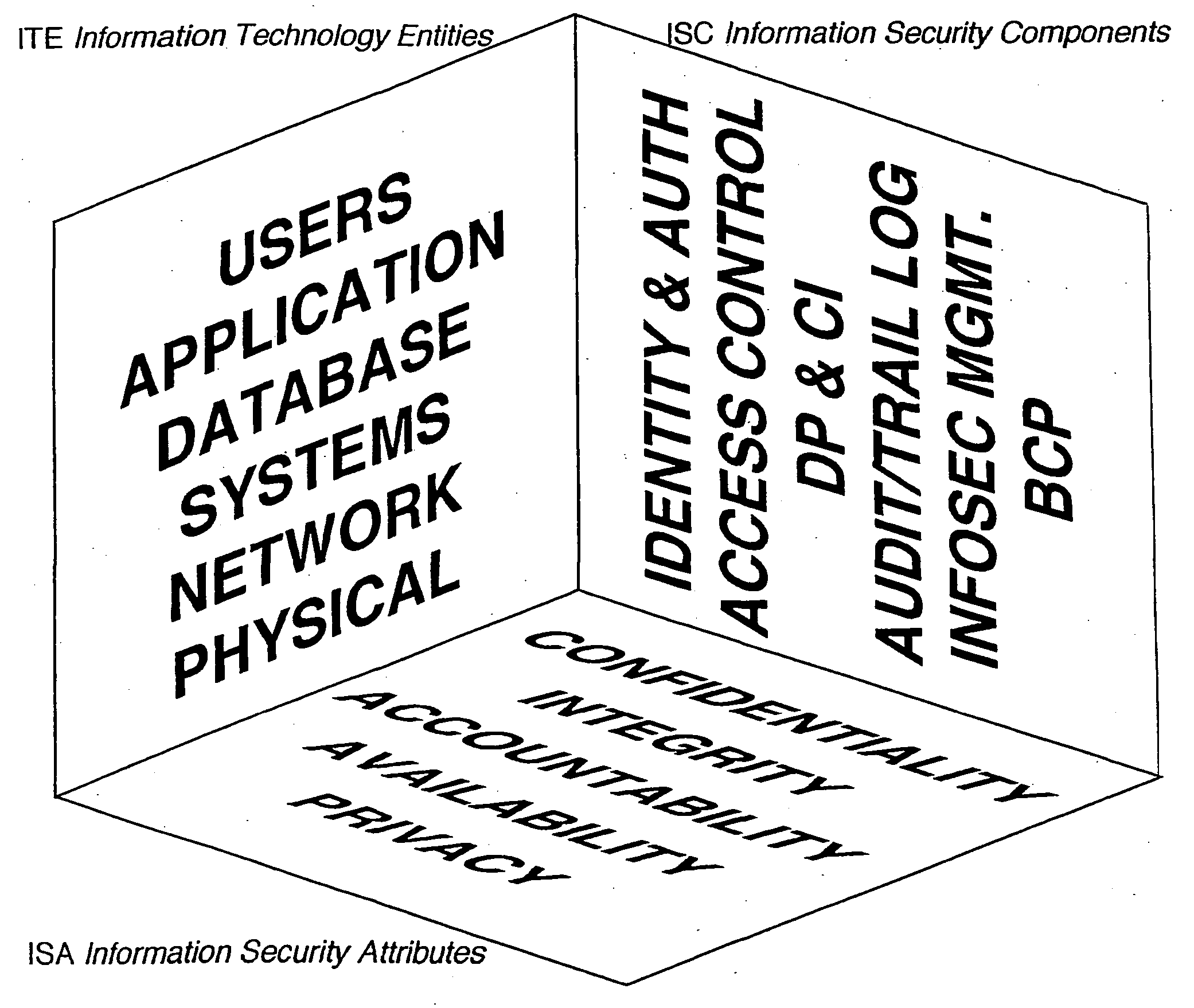
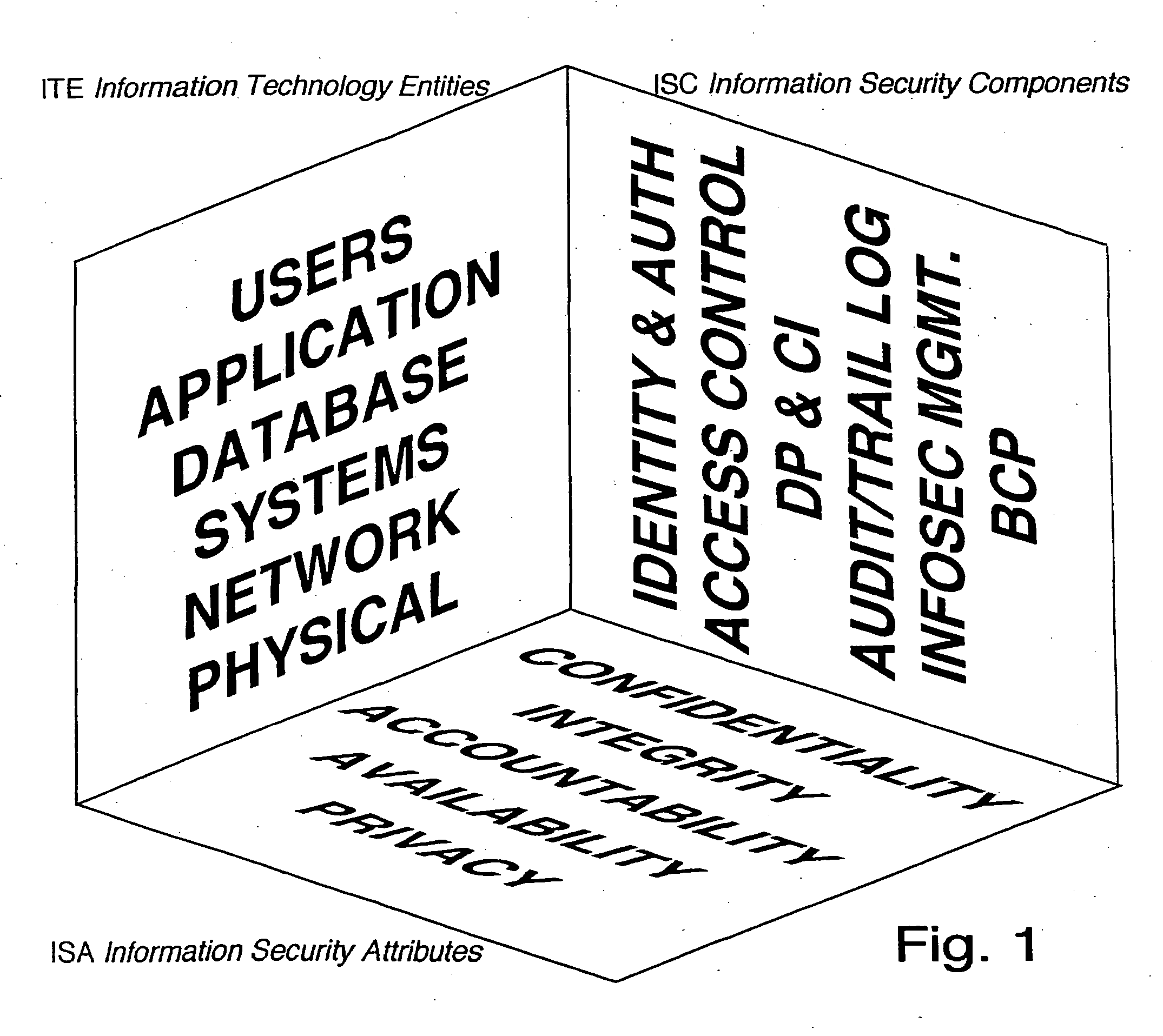
Information security model
InactiveUS20050038993A1Improve securityComputer security arrangementsOffice automationSecurity frameworkInformation security audit
An information security model provides a set of schemas that ensure coverage of all securing components. All points are addressed and evaluated in a net of three-dimensional coorindate knots The model defines the relation between components in the information risk and security space, and provides an information risk and security framework that ensures that all information security components are addressed; enables standardized information security audit; provides information risk compliance numbers; and defines strategic business direction to address information security implementation. The information security model of the present invention standardizes the approach and creates a matrix through which risk compliance factors can be calculated.
Owner:SCIENTON TECH
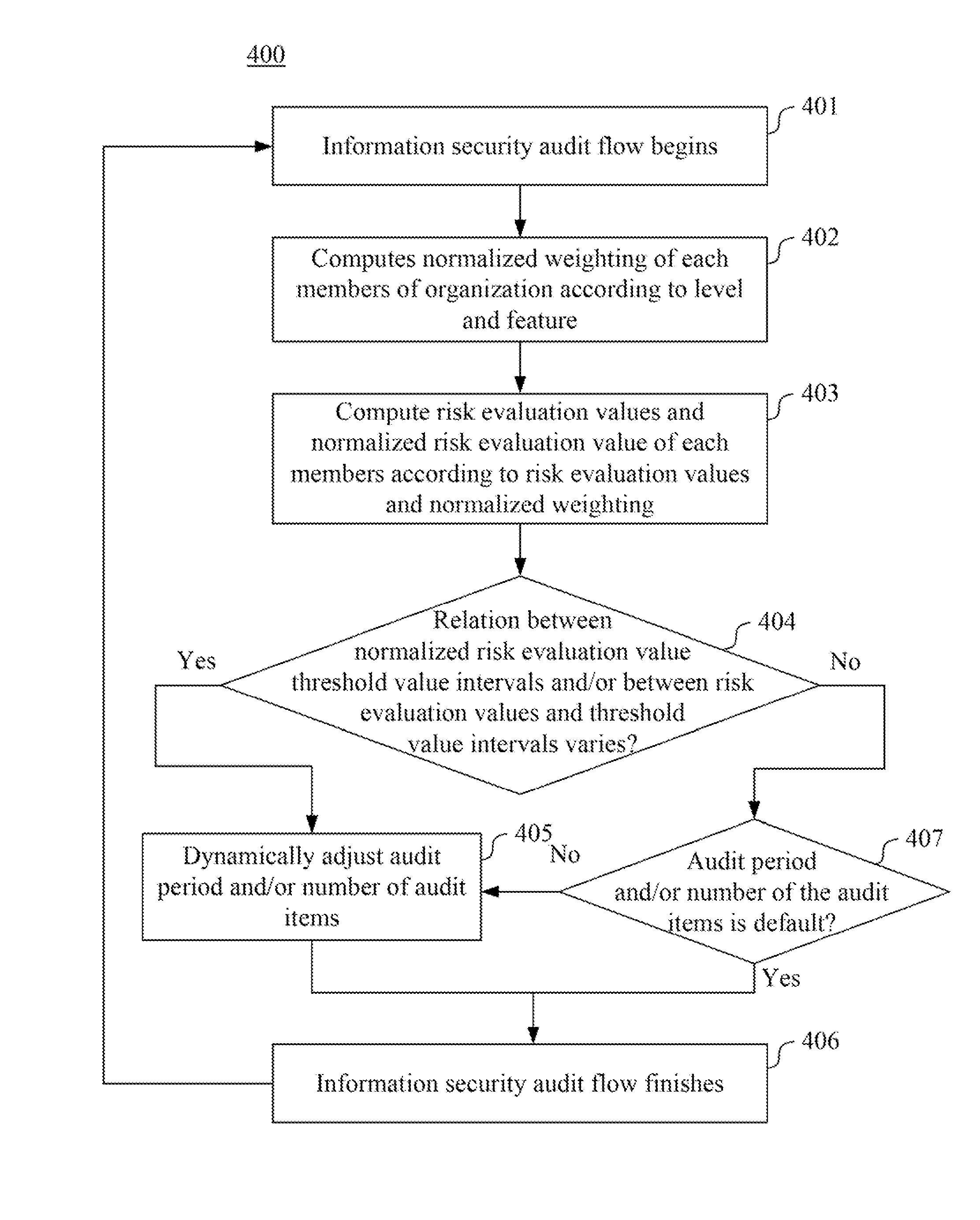
Information security audit method, system and computer readable storage medium for storing thereof
InactiveUS20140130170A1Memory loss protectionError detection/correctionInformation security auditInformation security
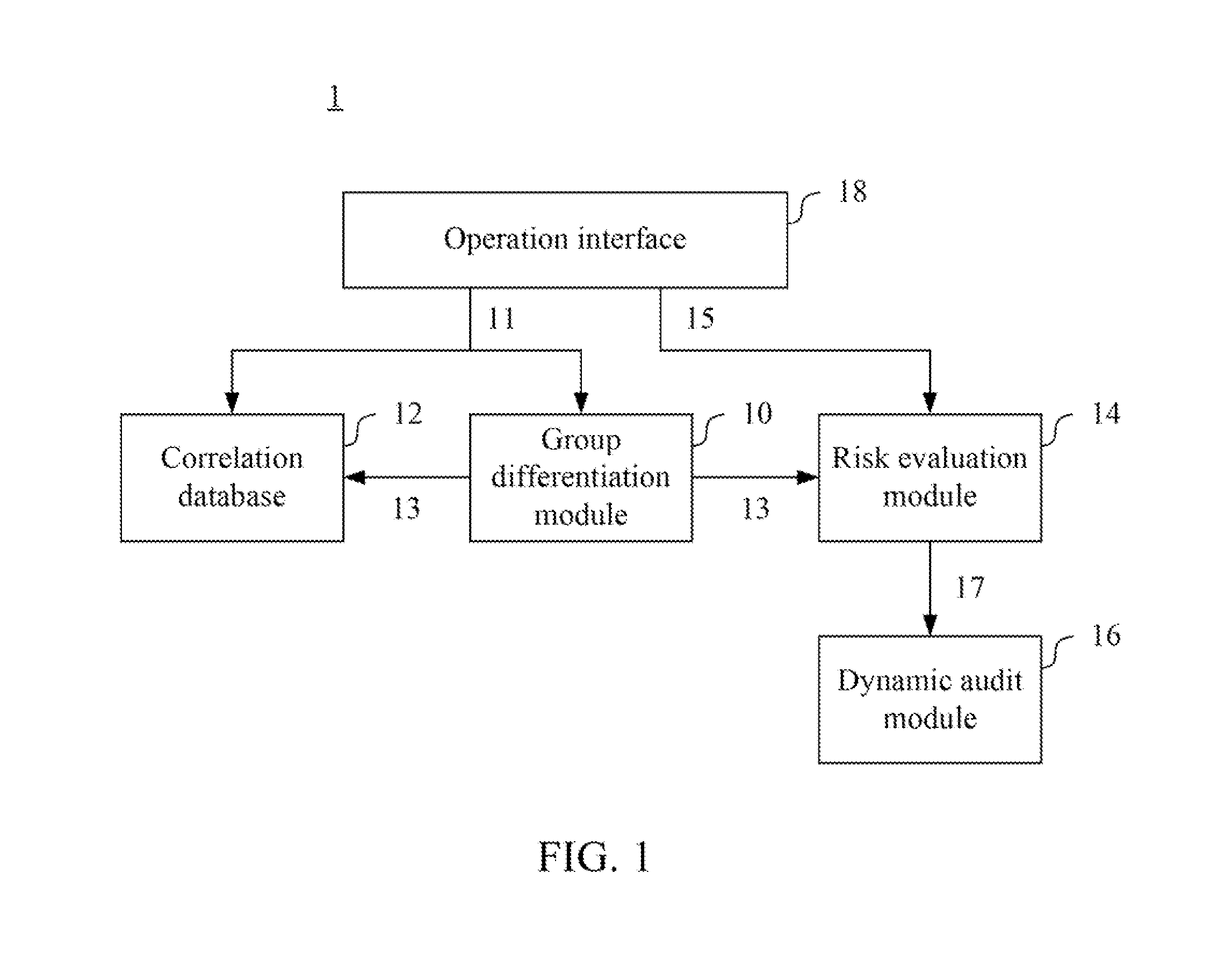
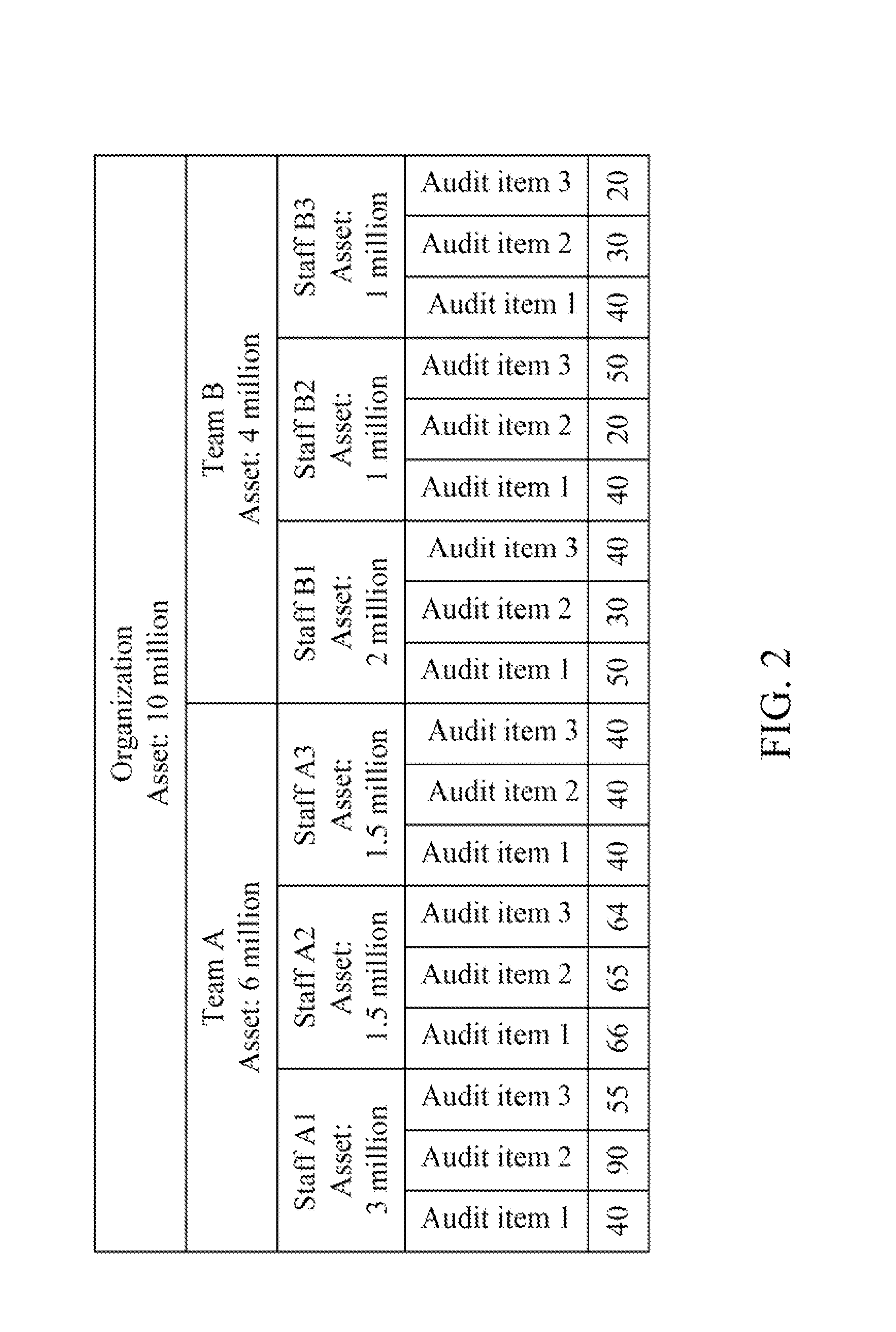
An information security audit method used in an information security audit system is provided. The information security audit method comprises the steps outlined below. A normalized weighting of each of a plurality of members of an organization is computed according to a level and at least one feature of each of the members. A plurality of risk evaluation values corresponding to a plurality of audit items are computed and a normalized risk evaluation value of each of the members is further computed according to the risk evaluation values and the normalized weighting. A relation of the normalized risk evaluation value and a plurality of threshold value intervals are determined to dynamically adjust an audit period and / or a number of the audit items according to the relation.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
Walk-through test technique based information security audit implementation method and system
InactiveCN104462988ADigital data protectionPlatform integrity maintainanceInternet privacyInformation security audit
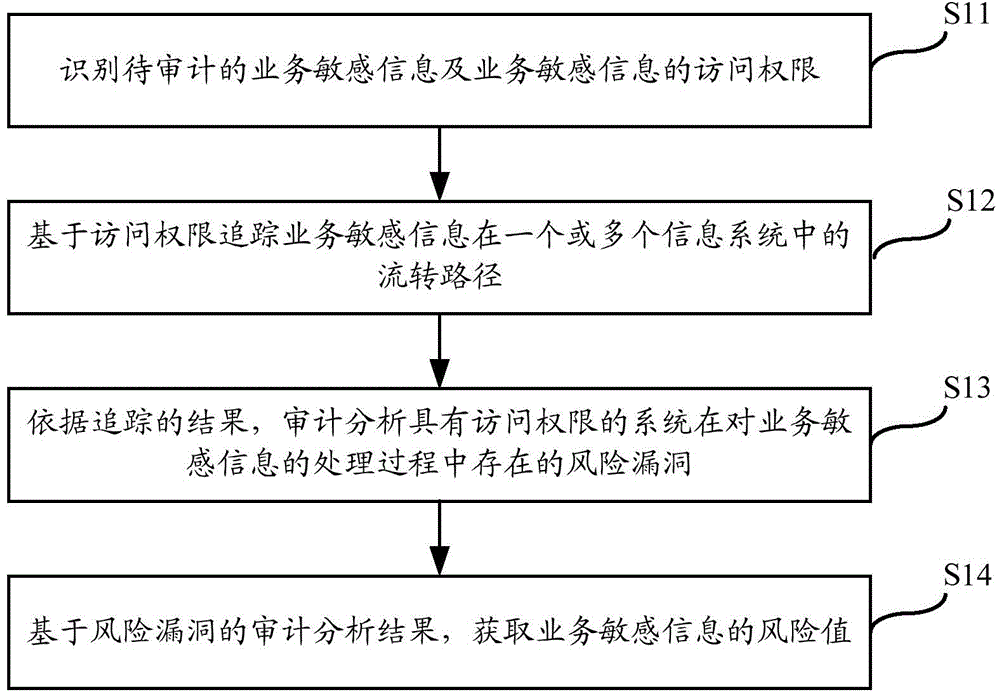
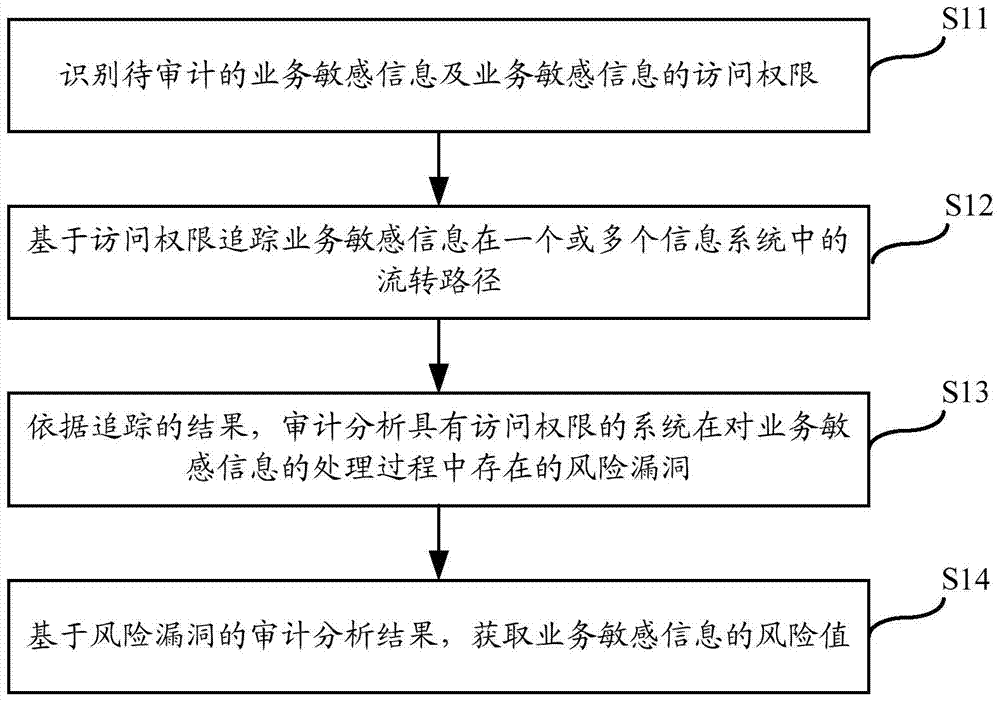
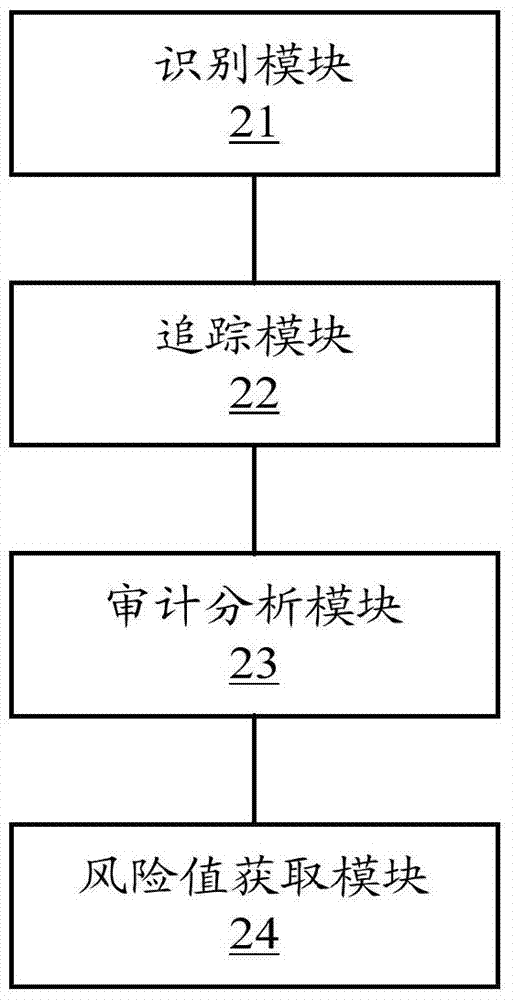
The invention relates to the technical field of information monitoring, in particular to a walk-through test technique based information security audit implementation method and system. The method includes: recognizing business sensitive information waiting for audit and access right of the business sensitive information; tracking flow paths of the business sensitive information in one or more information systems based on the access right; performing audit analysis on risk vulnerabilities existing in the process that the systems with access right process the business sensitive information according to tracking results; based on audit analysis results of the risk vulnerabilities, acquiring a risk value of the business sensitive information. By the method and system, risks existing in the process that the sensitive information flows in full life circles of the multiple information systems can be monitored.
Owner:STATE GRID CORP OF CHINA +2
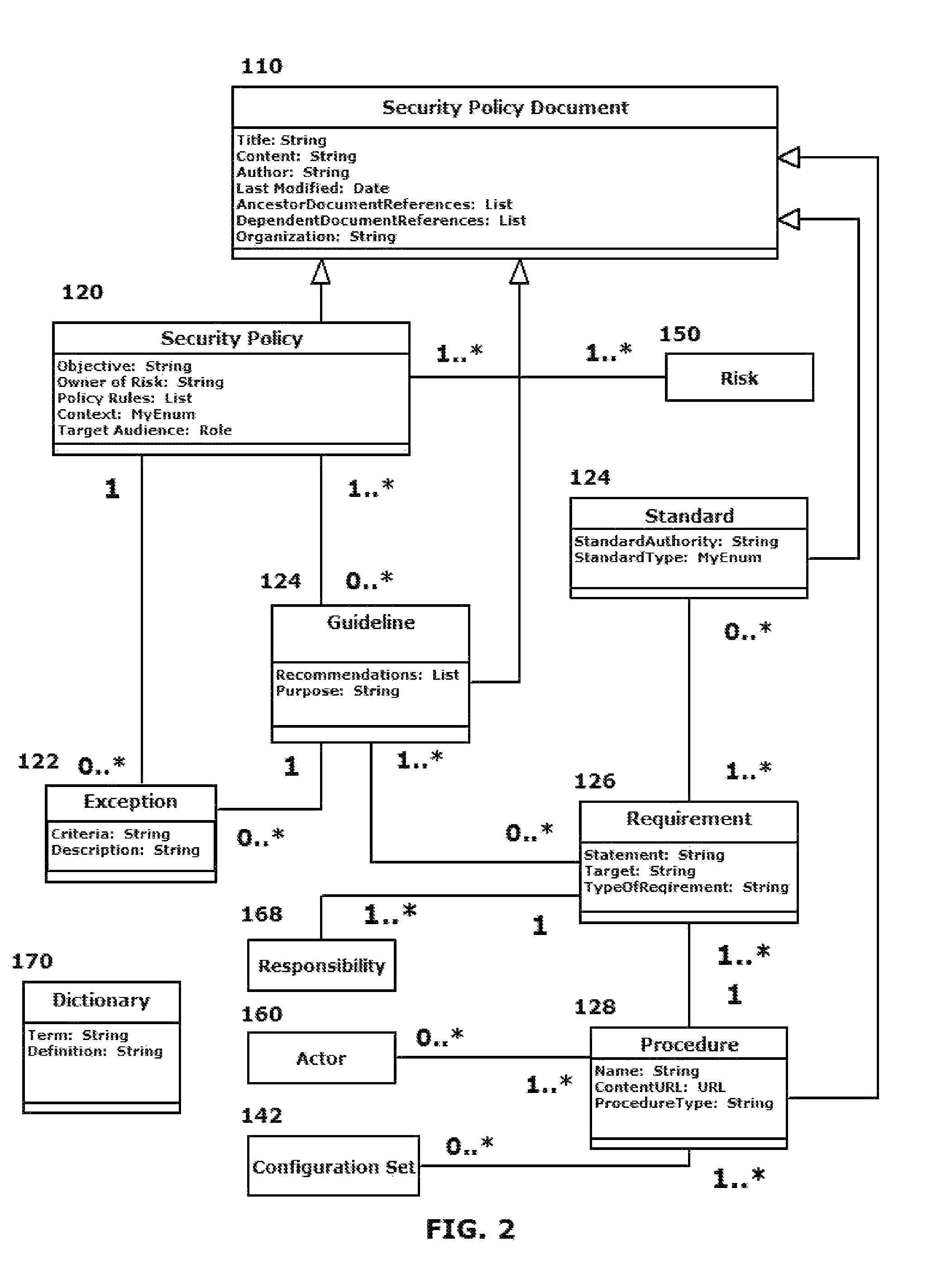
Security policy flow down system
ActiveUS20130167191A1Easy to analyzeMemory loss protectionError detection/correctionProgram planningSecurity compliance
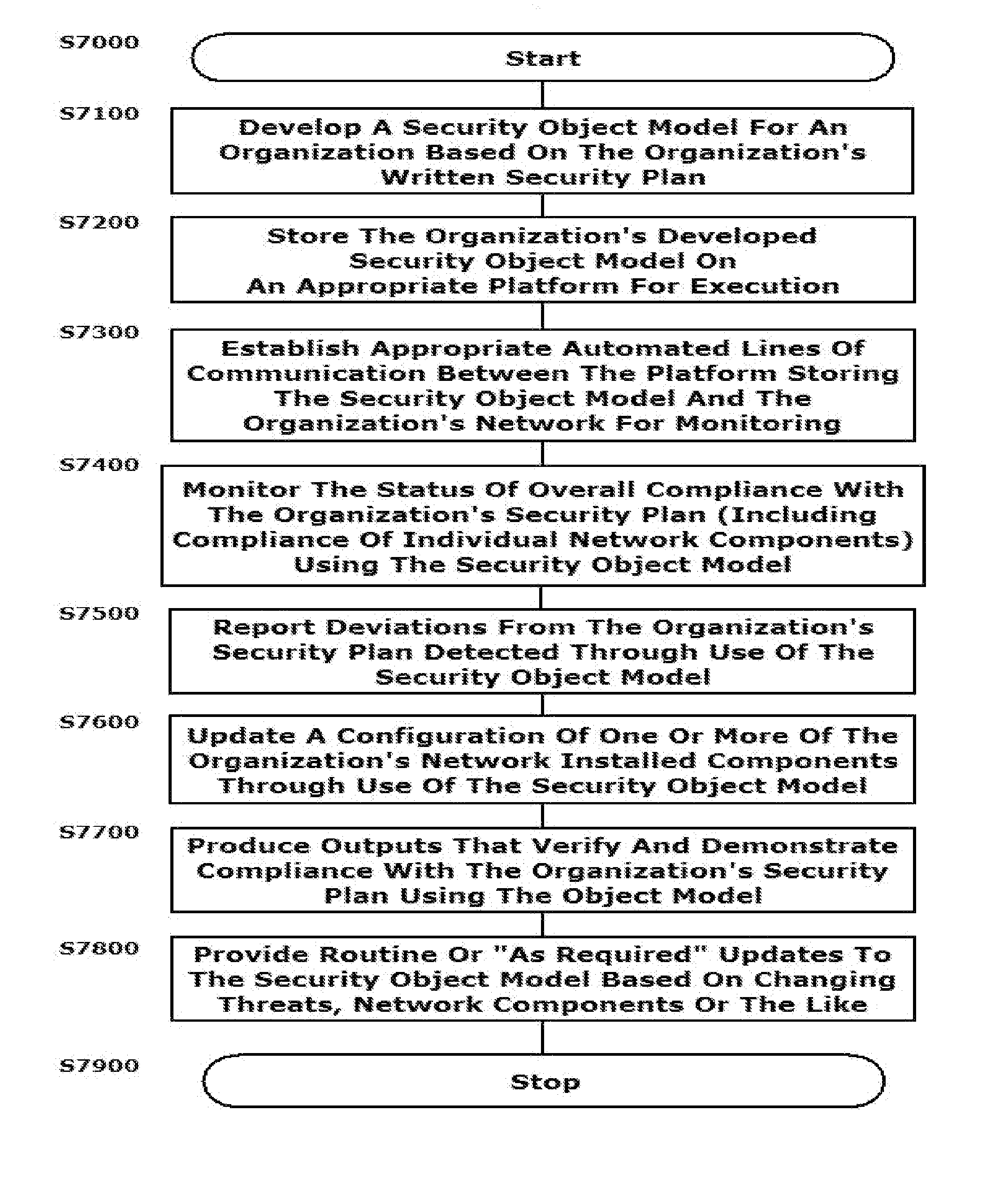
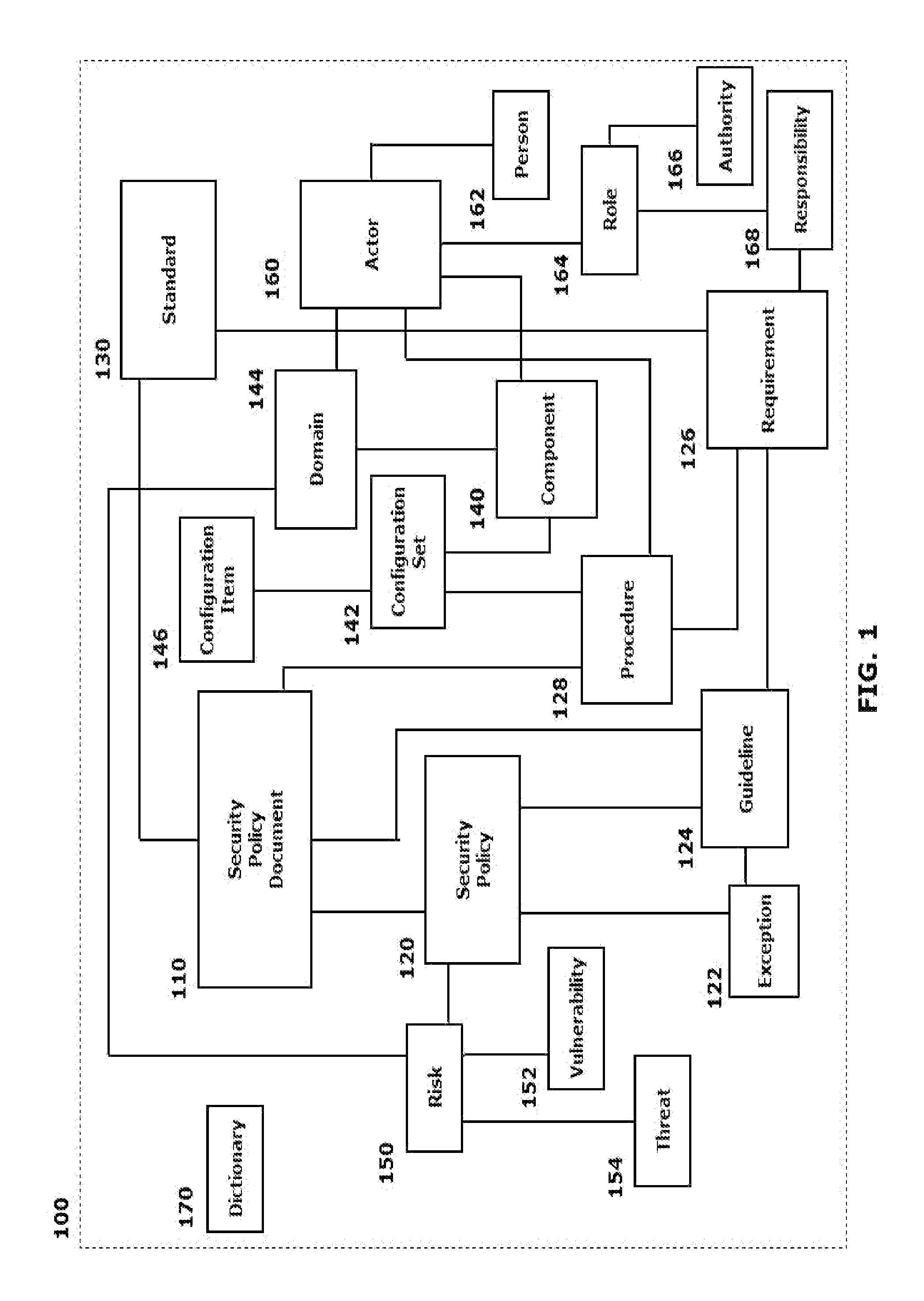
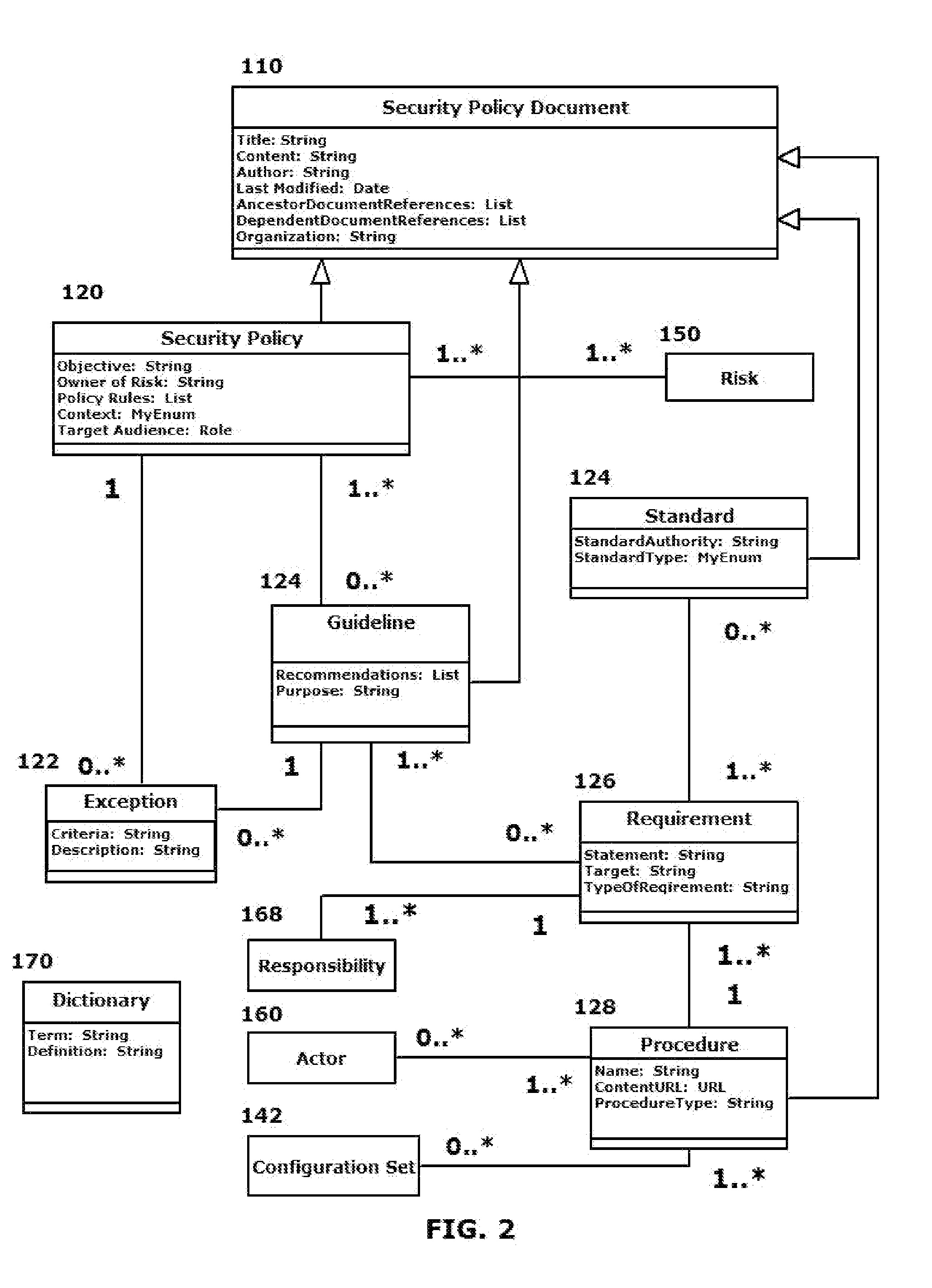
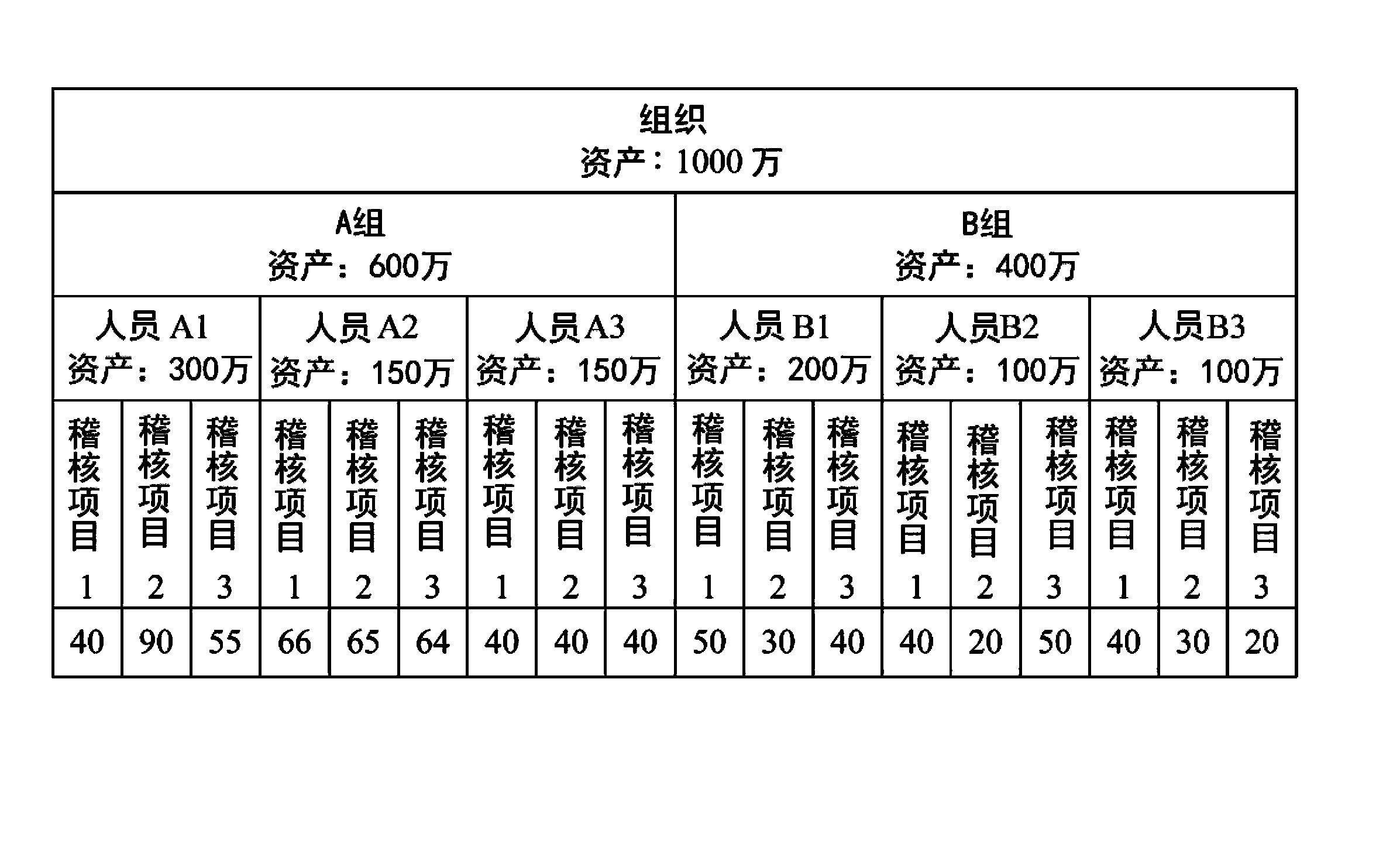
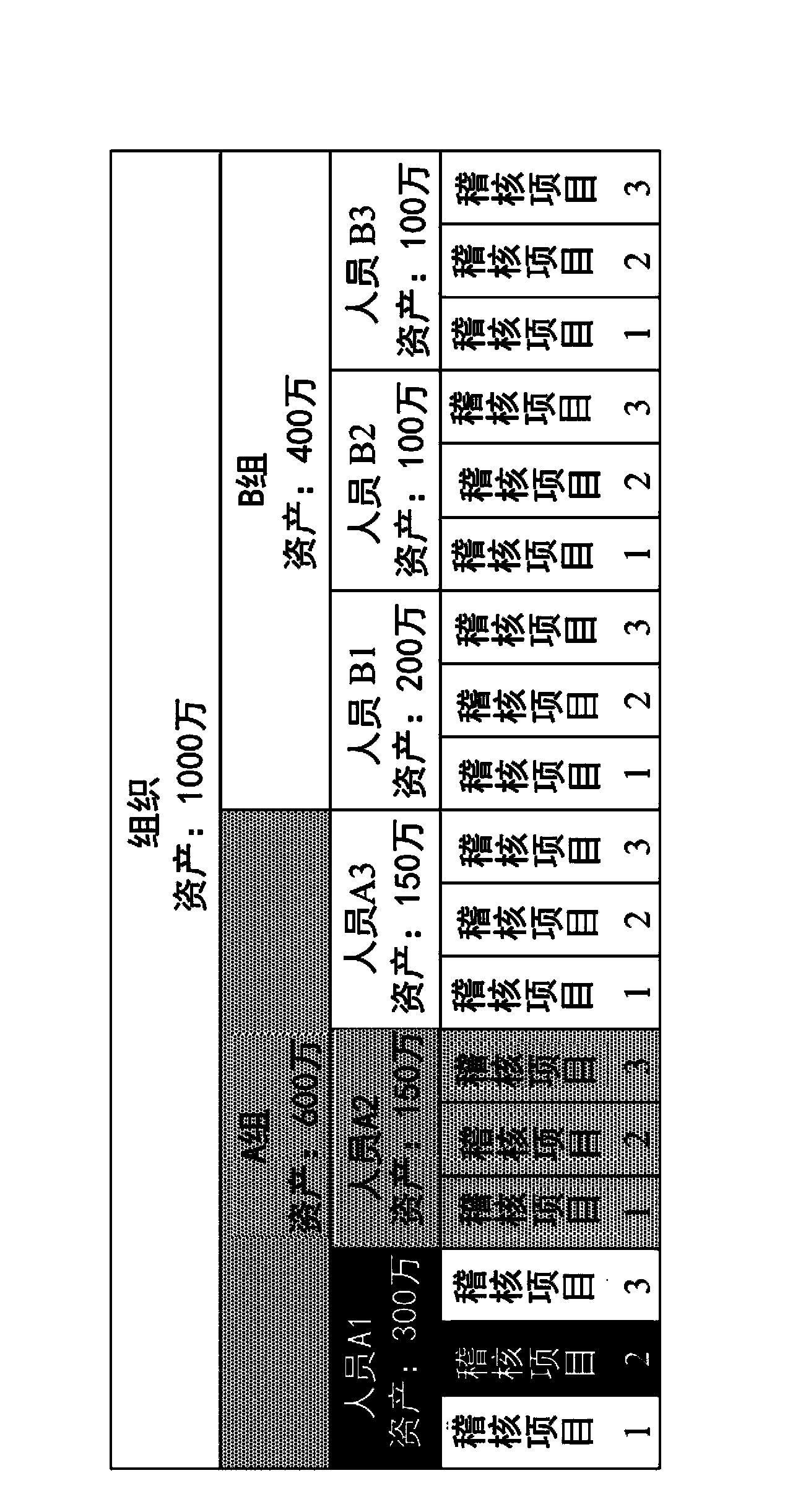
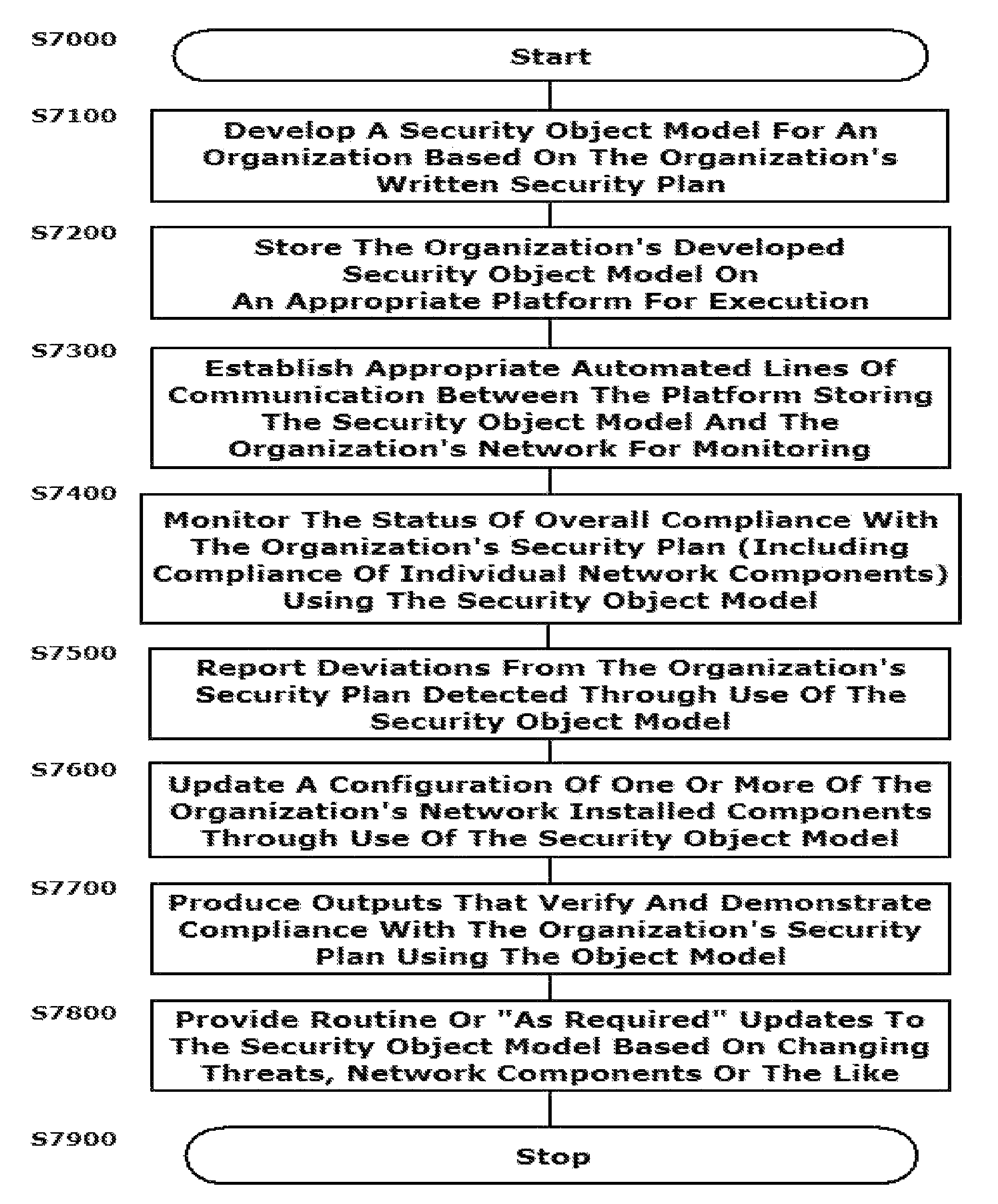
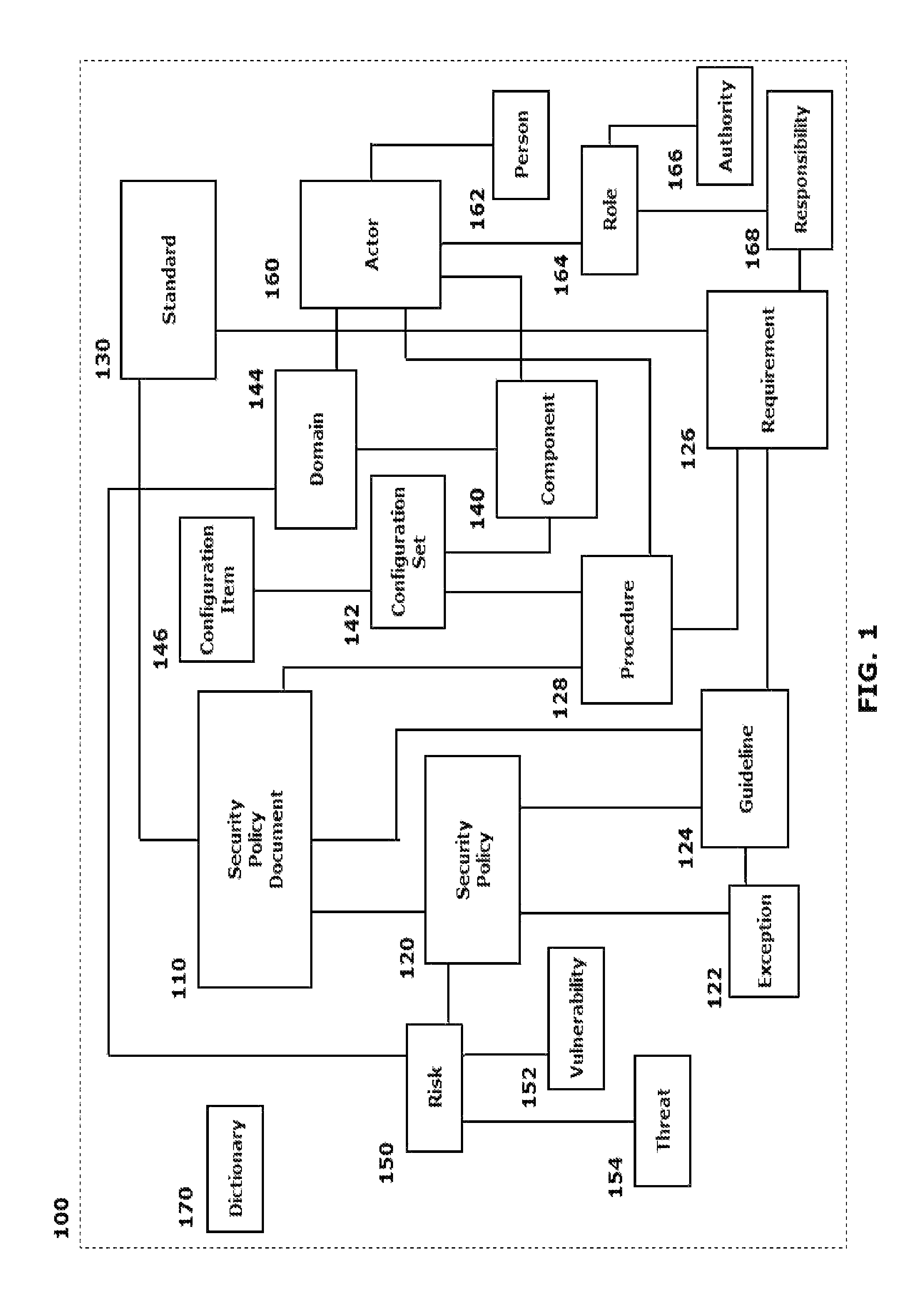
A system and method are provided that distill an organization's information security plan into a detailed and unambiguous security object model. The developed security object model provides a visualization of complex relationships between individual elements and levels that is usable to carry into effect the organization's information security plan. Configuration control and a verifiable level of security compliance are provided through implementation of the organization's information security plan by the developed security object model. The developed security object model is hosted on a computing platform in communication with at least the organization's network to provide information security plan compliance, configuration control and gap analysis in a usable form to the organization.
Owner:LOCKHEED MARTIN CORP
Systems and methods for encryption and provision of information security using platform services
ActiveUS10020936B1Enhanced interactionOptimizationKey distribution for secure communicationUser identity/authority verificationCiphertextOriginal data
Systems and methods for securing or encrypting data or other information arising from a user's interaction with software and / or hardware, resulting in transformation of original data into ciphertext. Generally, the ciphertext is generated using context-based keys that depend on the environment in which the original data originated and / or was accessed. The ciphertext can be stored in a user's storage device or in an enterprise database (e.g., at-rest encryption) or shared with other users (e.g., cryptographic communication). The system generally allows for secure federation across organizations, including mechanisms to ensure that the system itself and any other actor with pervasive access to the network cannot compromise the confidentially of the protected data.
Owner:IONIC SECURITY
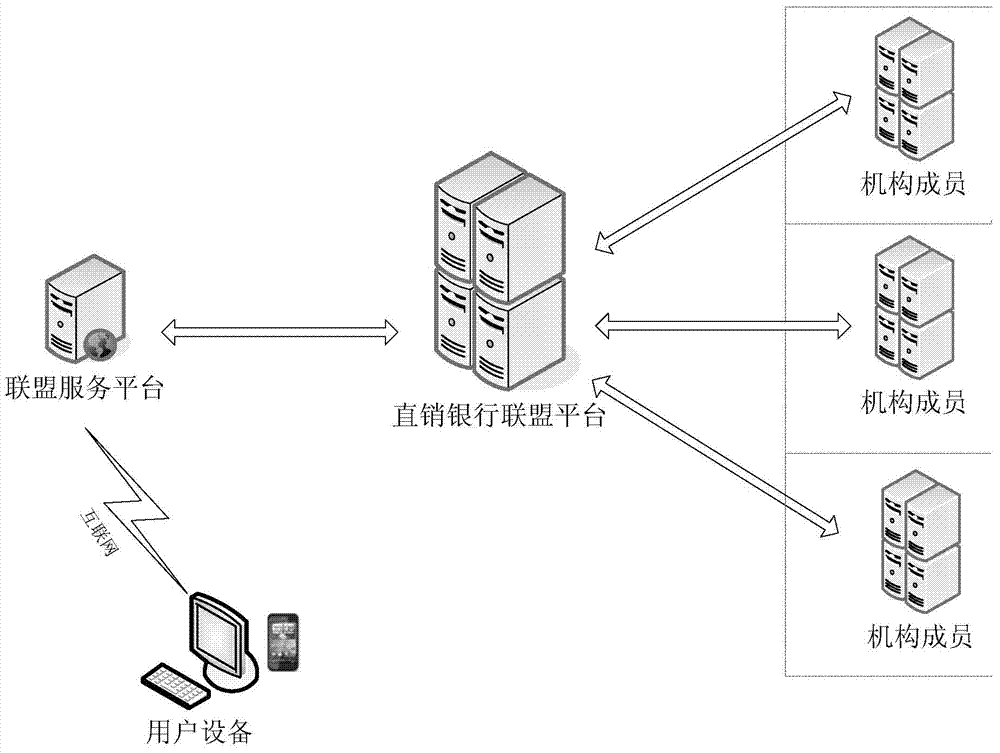
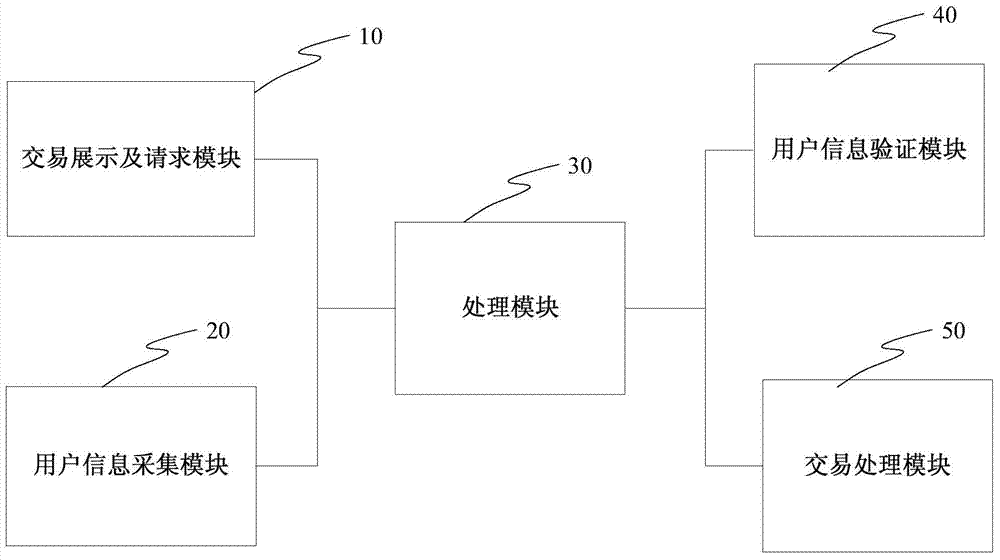
Security certification type trans-regional direct-selling bank alliance transaction method and system
ActiveCN104751364AImprove service typesRich choiceFinanceUser identity/authority verificationEnd to end securityInternet privacy
The invention provides a security certification type trans-regional direct-selling bank alliance transaction method and system. The system comprises an user information acquiring module, a transaction request module, a handling module positioned on a direct-selling bank alliance platform, an user information verification module for organization members, and a transaction handling module, wherein the user information acquiring module and the transaction request module are arranged on an alliance service platform. According to the system, the members of a financial service organization provide service, so that the services are diversified; the members of each financial product service organization are provided point-to-point security communication protection, and thus the funds security and information security of a user and the end-to-end security can be ensured; each organization provides the security real-name authentication information of the user, so as to ensure the validity of the user information; the direct-selling bank alliance platform serving the regional financial product service organization is built; the security real-name authentication information of the user in each financial product service mechanism is utilized on the premise that the security is ensured to provide the user the wide and secure financial service.
Owner:上海方付通科技服务股份有限公司
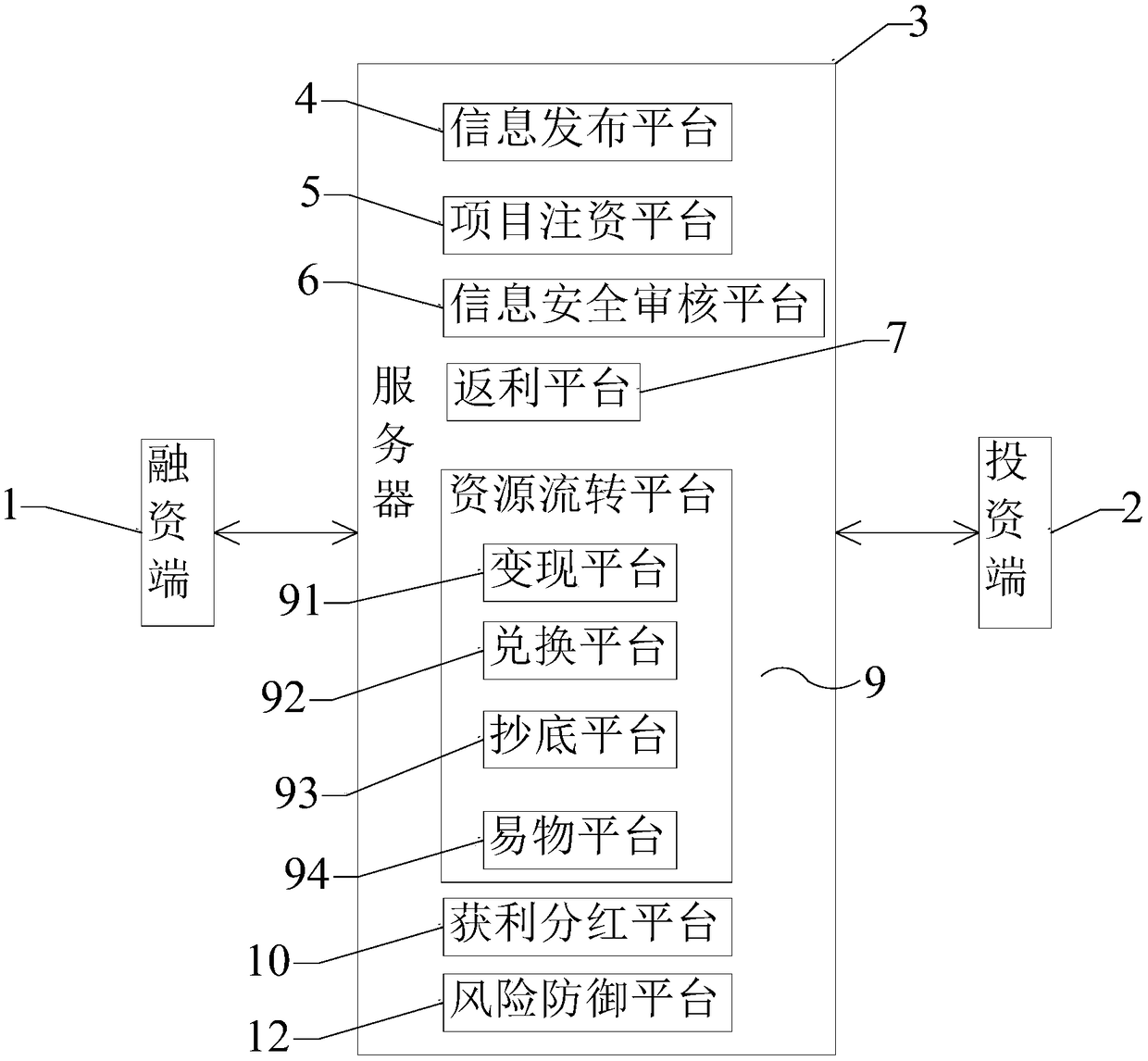
Financing integrated service platform and method
The invention belongs to the technical field of internet finance, and provides a financing integrated service platform. The platform comprises a server connected with both a financing side and an investing side, an information release platform, a project capital injection platform, an information safety auditing platform, a rebate platform and a profit participation platform; the information release platform is used for enabling a financing party to release financing project data; the project capital injection platform is used for enabling an investor to select a financing project and inject capital; the information safety auditing platform is used for enabling a service platform administrator for auditing identity and data authenticity of the investor and the financing party; the rebate platform is used for enabling the financing party to feed back a feedback object of a certain proportion according to the capital injection amount of the investor after financing project financing is successful; the profit participation platform is used for enabling the financing party to perform profit participation on the investor. The invention further provides a financing comprehensive servicemethod. The platform is exquisite in concept, and the technical problem that due to the fact that in the prior art, the market lacks a platform for performing comprehensive service on financing projects, a large number of resources are wasted is solved.
Owner:周斌
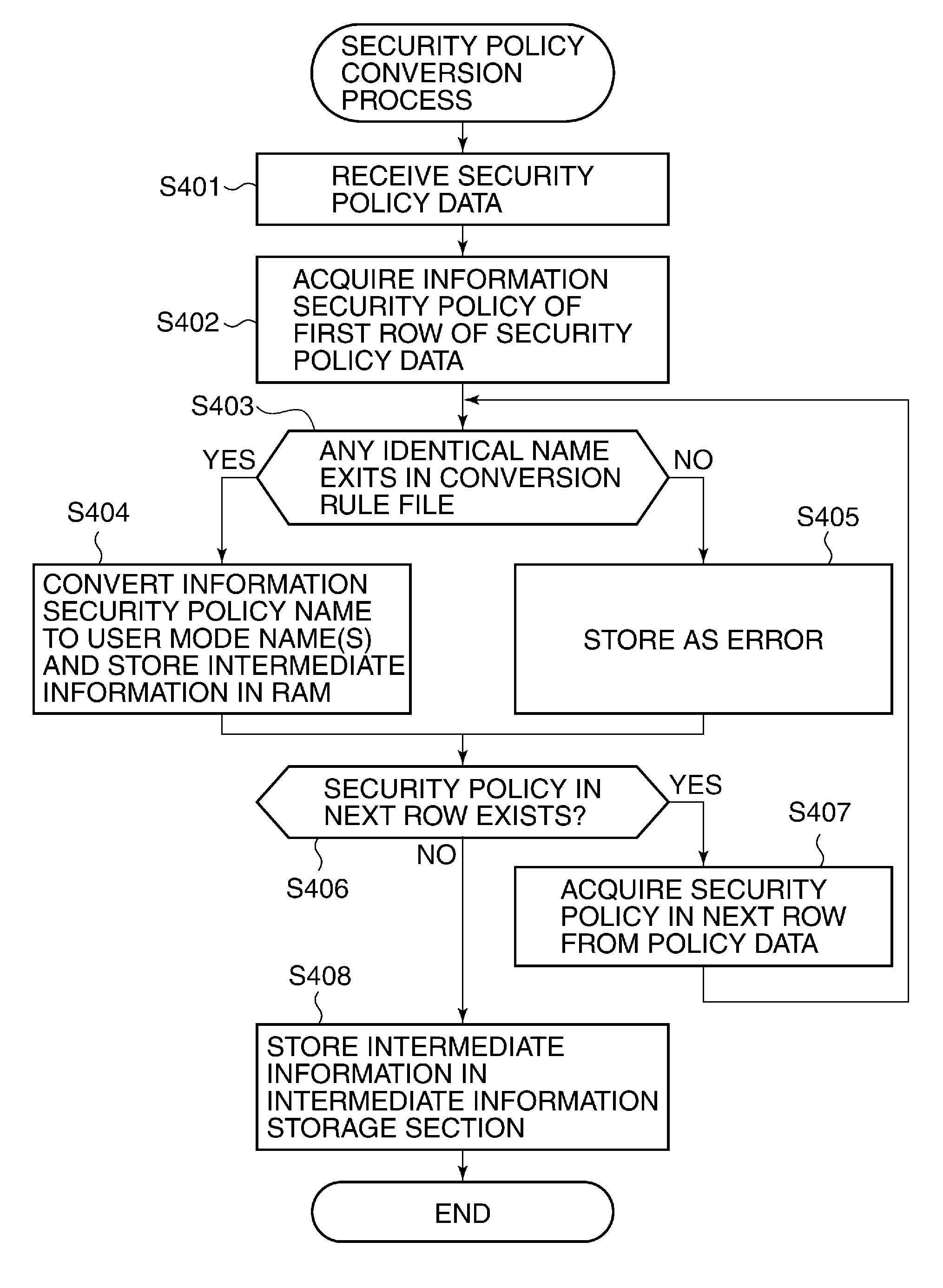
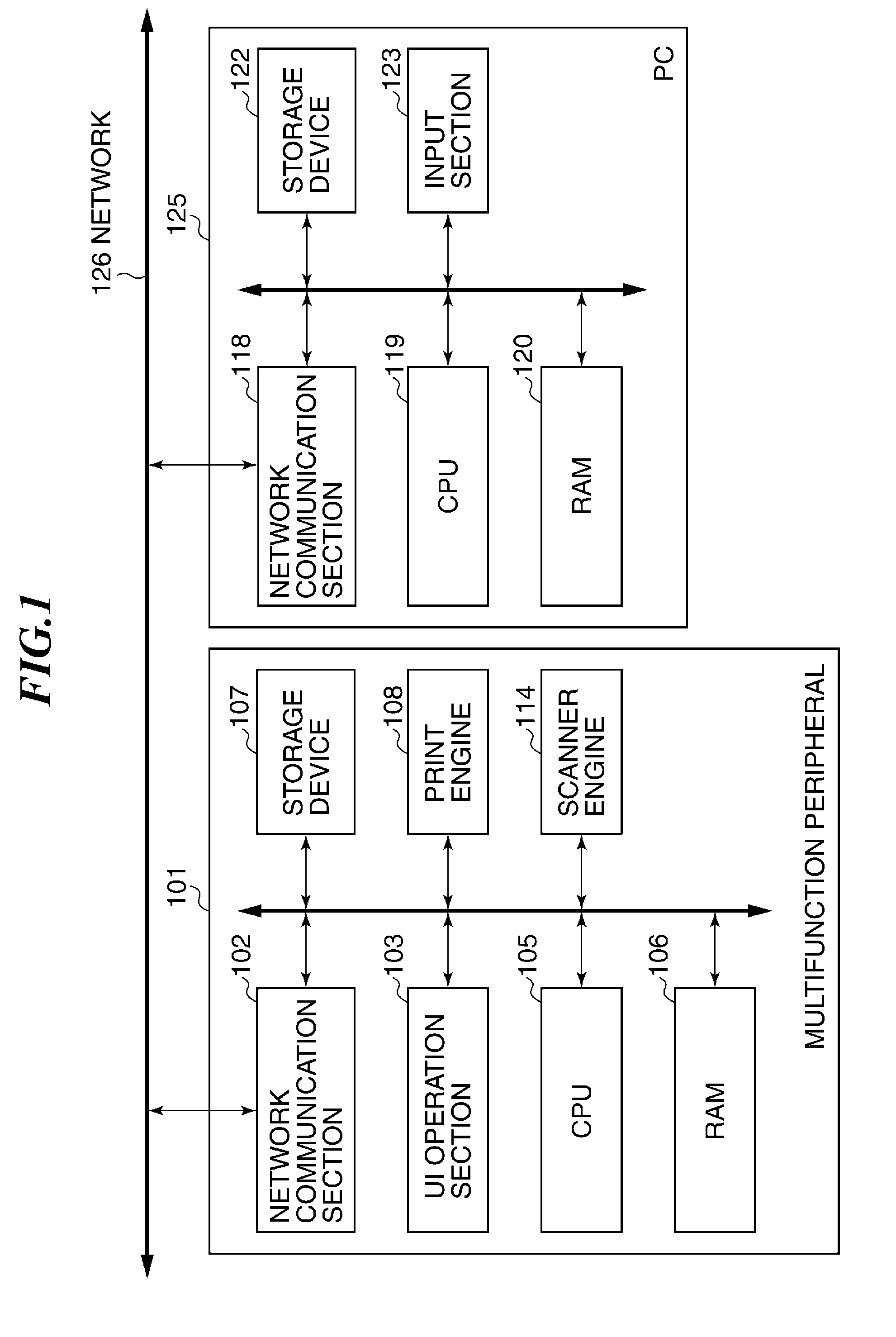
Image processing apparatus that configures settings of information security policy, method of controlling the same, program, and storage medium
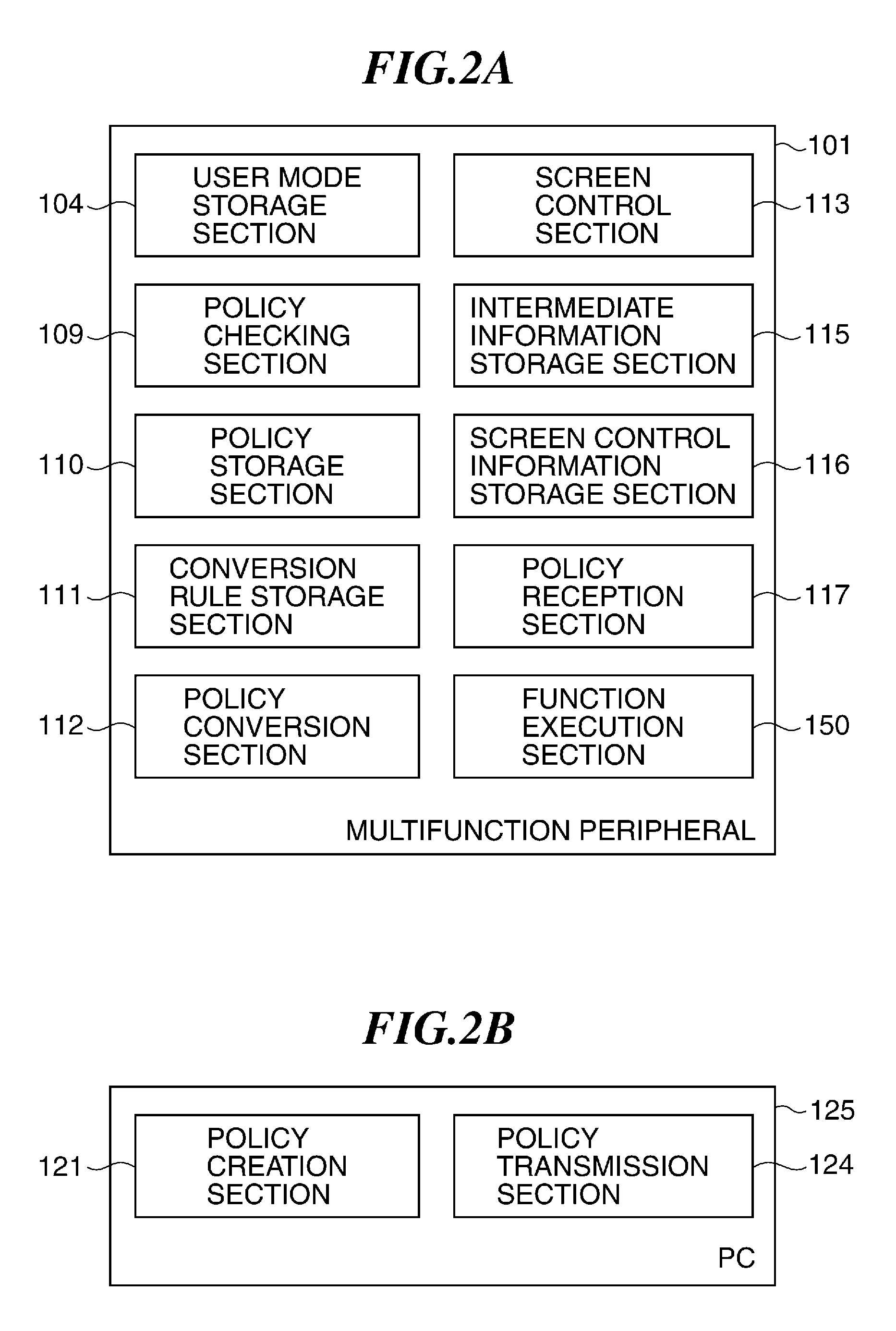
An image processing apparatus which enables a user to change the user mode while maintaining the state compliant with the information security policy. A network communication section receives security policy data in which information security policy is described from an external apparatus. A CPU identifies an operation mode of the image processing apparatus based on the received security policy. The CPU configures the identified operation mode such that the information security policy is satisfied.
Owner:CANON KK
Comprehensive information-security audit method
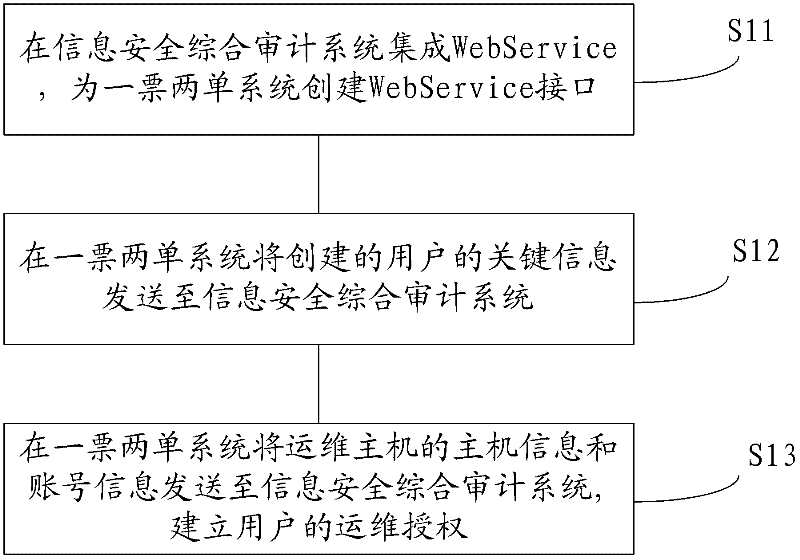
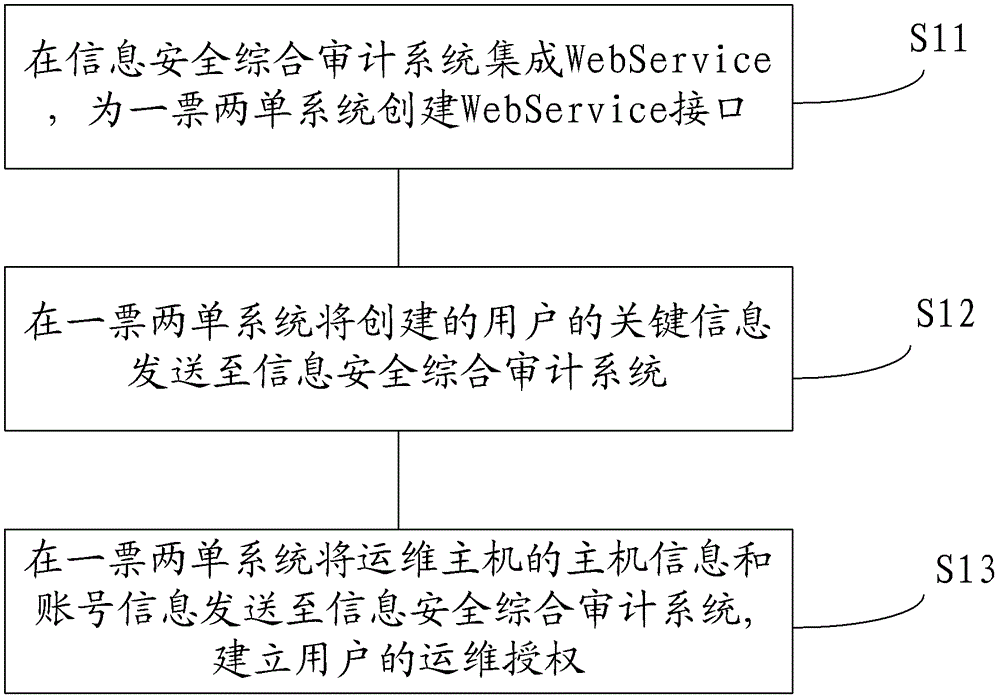
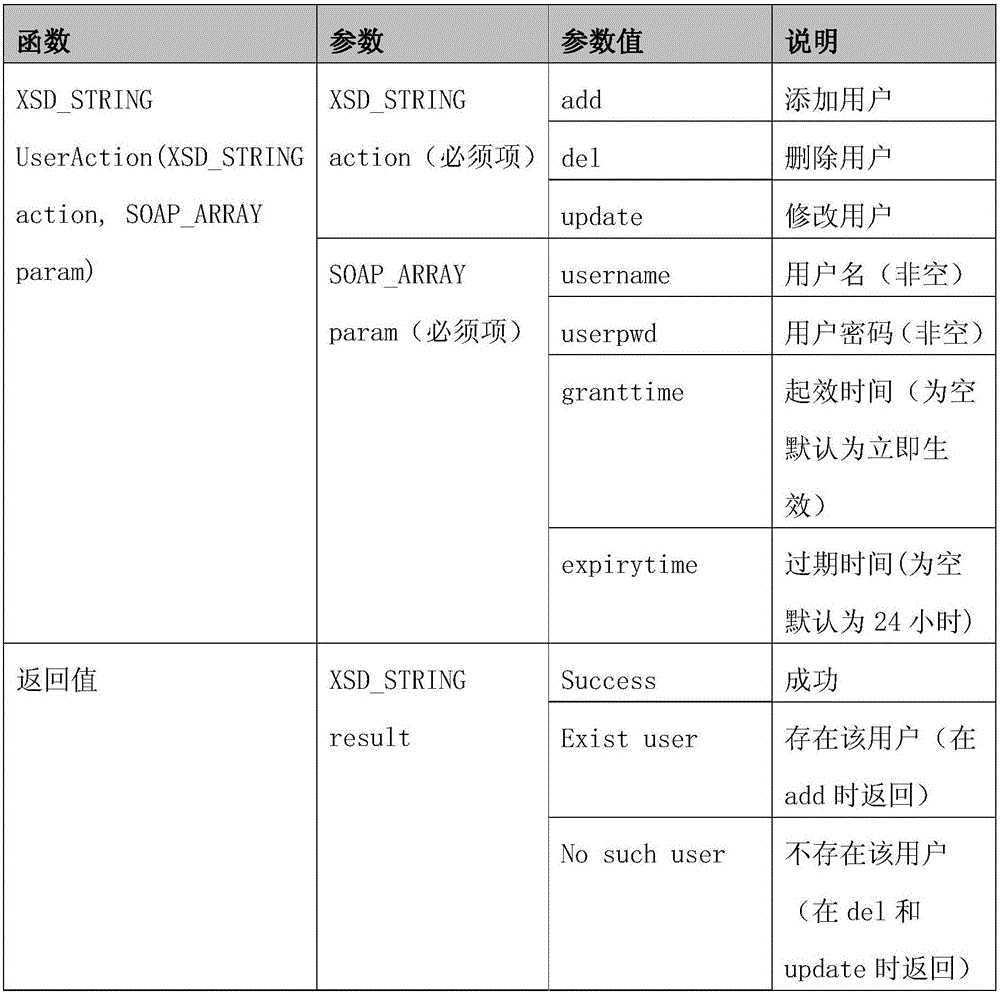
ActiveCN102567849ARealize unified managementSimple working processResourcesTransmissionWeb serviceInformation security audit
The invention discloses a comprehensive information-security audit method which comprises the following steps: integrating a Web Service on a comprehensive information-security audit system in advance, and creating a Web Service interface for a single-note two-list system; sending the created key information of a user to the comprehensive information-security audit system by the Web Service interface in the single-note two-list system, wherein the key information of the user includes the identifier of the user; storing the key information of the user by the comprehensive information-security audit system; sending the information and the account information of an operation and maintenance host to the comprehensive information-security audit system by the Web Service interface in the single-note two-list system when the operation and maintenance authorization needs to be applied for the user; and creating the operation and maintenance authorization of the user by the comprehensive information-security audit system. Due to the adoption of the comprehensive information-security audit method, the comprehensive information-security audit accuracy is improved, and in addition, the work load of a comprehensive information-security audit system manager is effectively reduced and the work efficiency is improved.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +1
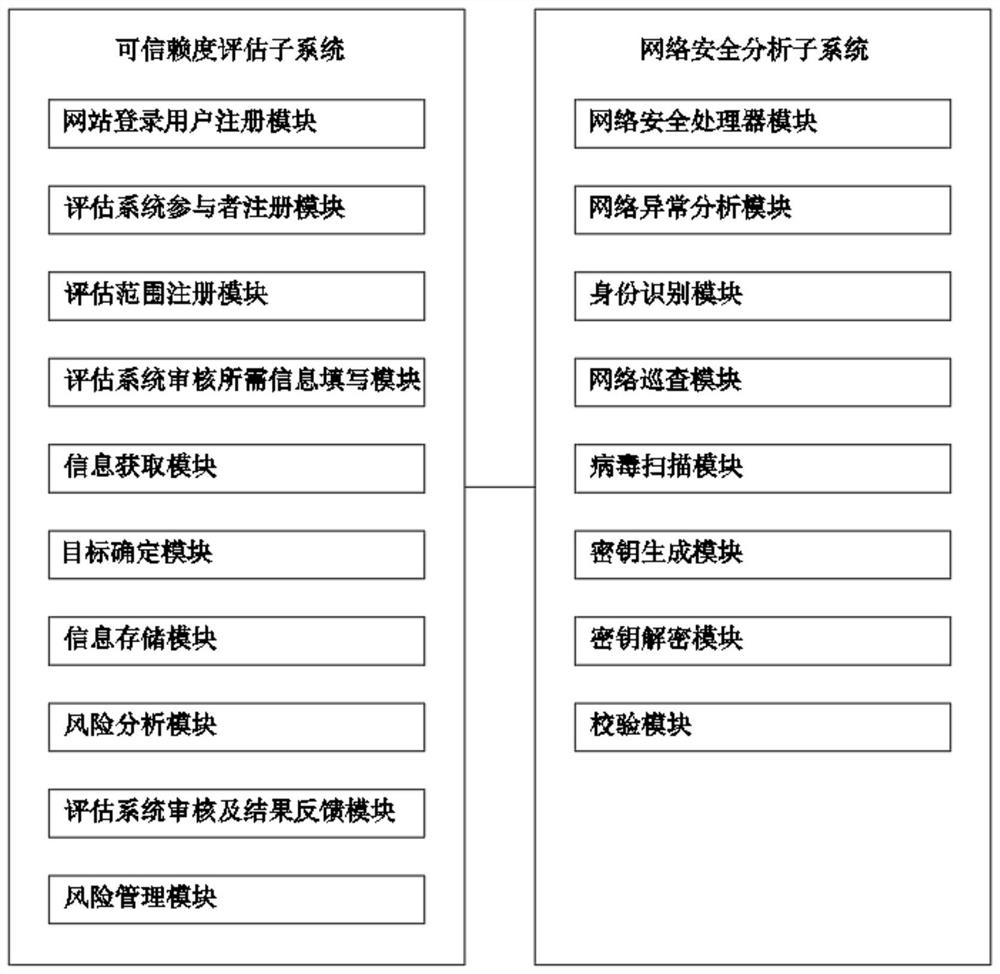
Automobile industry information safety system trustworthiness evaluation method and evaluation system
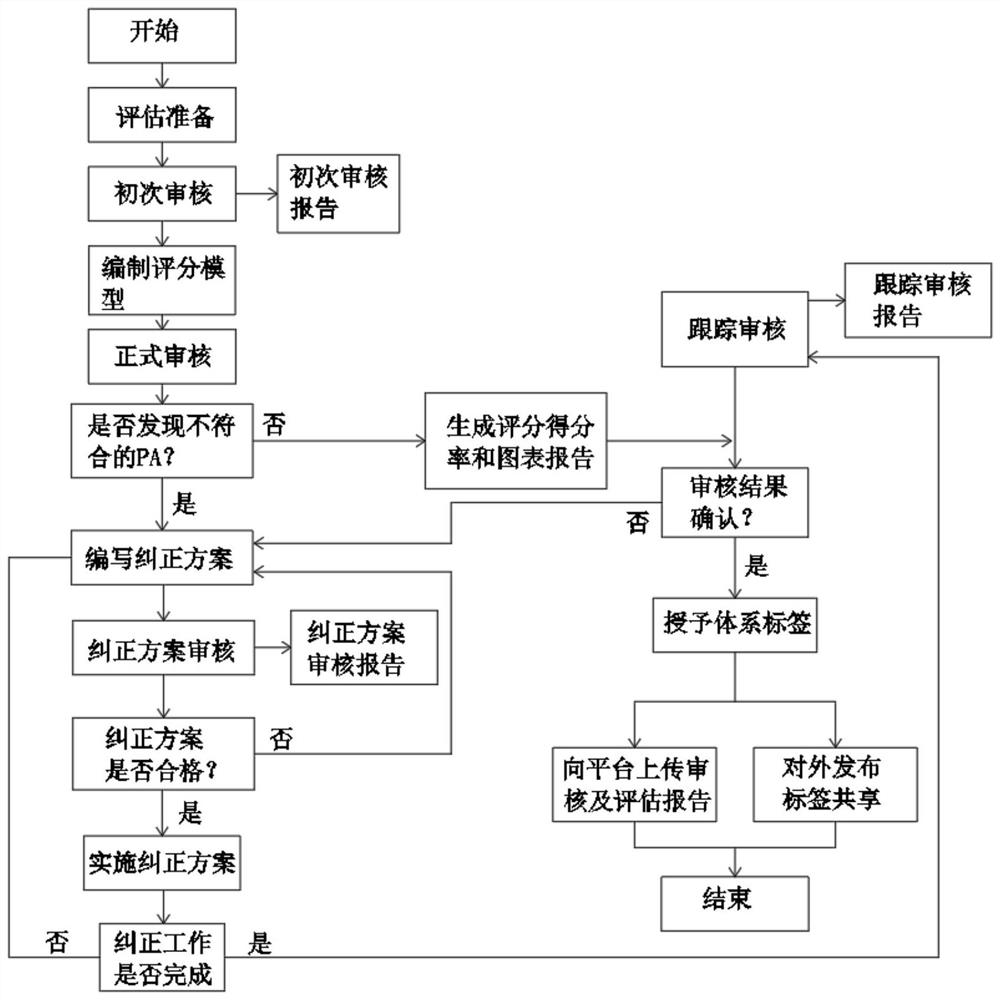
PendingCN114757556AApproval of audit resultsQuick searchResourcesInformation security auditInformation security
The invention discloses an automobile industry information safety system trustworthiness assessment method, which comprises the following steps: step 1, assessment preparation: completing a series of preparation work before assessment, and obtaining information required for auditing of an assessment system; step 2, primary auditing: performing primary auditing on the evaluation preparation work in the step 1 and the acquired information required by the auditing of the evaluation system; 3, a scoring model is compiled, and the scoring model is compiled according to the evaluation module and the safety process domain thereof; 4, performing formal auditing, auditing whether the security process domain of the evaluation module is in accordance, and determining the security process domain of the score rate of the evaluation module; the invention further discloses an automobile industry information safety system trustworthiness evaluation system. The independence and authority of the auditing result are high, the auditing result can be accepted by all parties, and it can be guaranteed that all demand parties can quickly, accurately and comprehensively inquire the information security auditing result from the evaluation system.
Owner:中汽研华诚认证(天津)有限公司
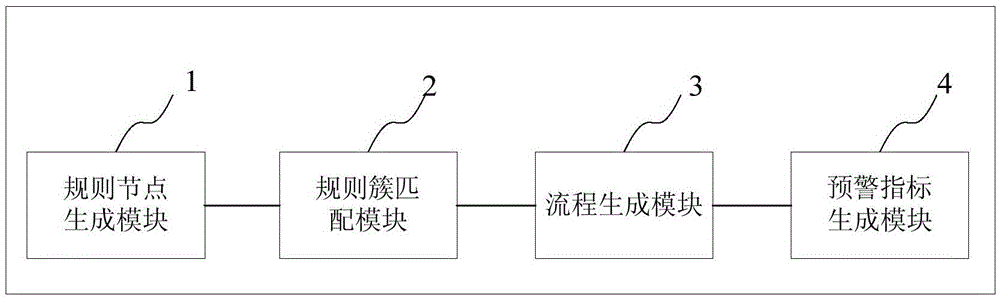
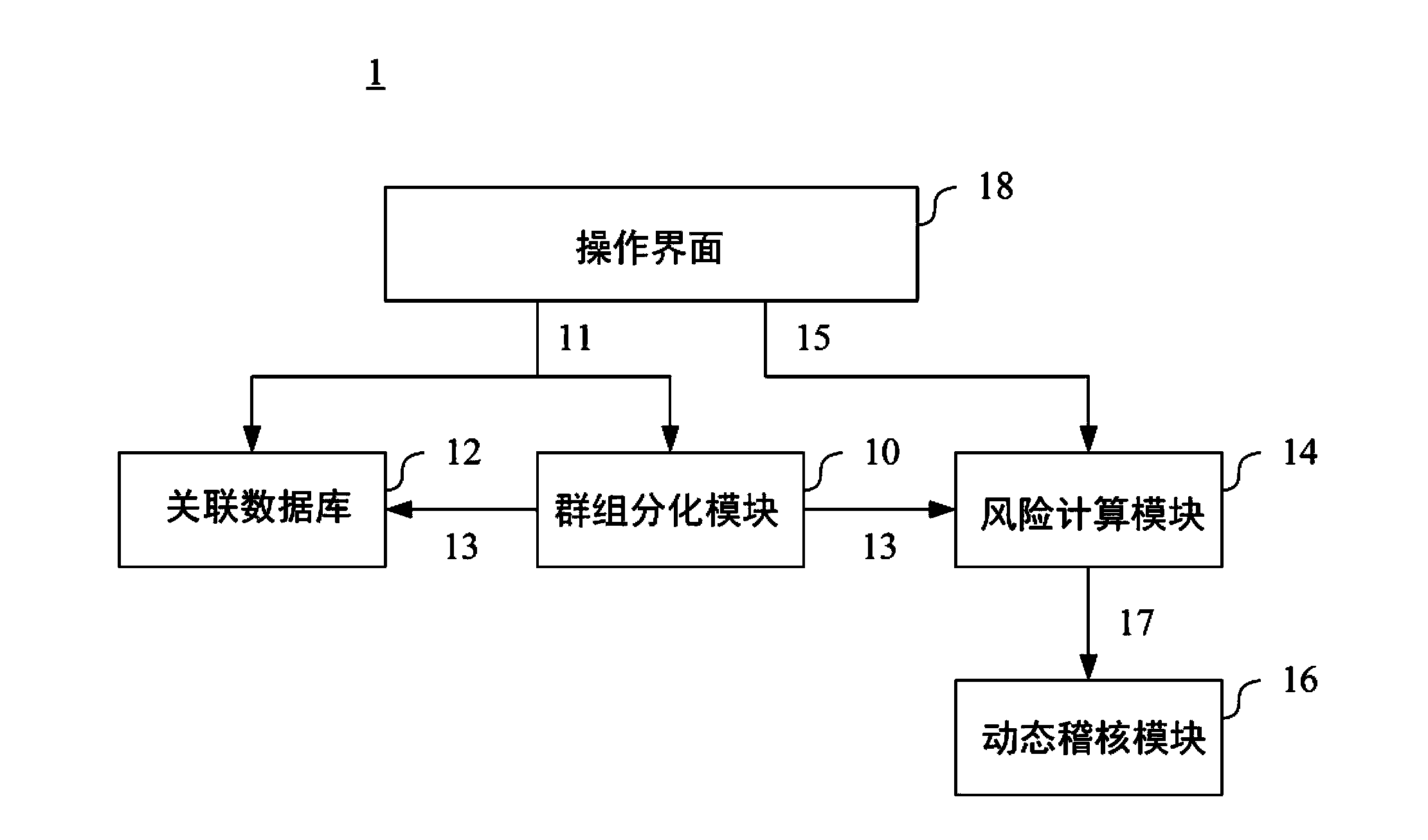
Service-based indexed information security audit early warning system and method
The invention provides a service-based indexed information security audit early warning system and method. The system comprises a regular node generating module, a regular cluster matching module, a flow generating module and an early warning index generating module; the regular node generating module is used for generating a regular node for each operation data of a service operation; the regular cluster matching module is used for screening the regular nodes with the same feature as a regular cluster from all the regular nodes of the service operation of a user; the flow generating module is used for generating a service flow for a series of single service operations of the user through regular cluster matching; and the early warning index generating module is used for generating an index for judging whether early warning is performed or not according to comprehensive judgment of a plurality of service flows. According to the service-based indexed information security audit early warning system and method, service requirements correspond to indexes, so that the indexed early warning technology is realized and the user experience is improved.
Owner:上海熙菱信息技术有限公司
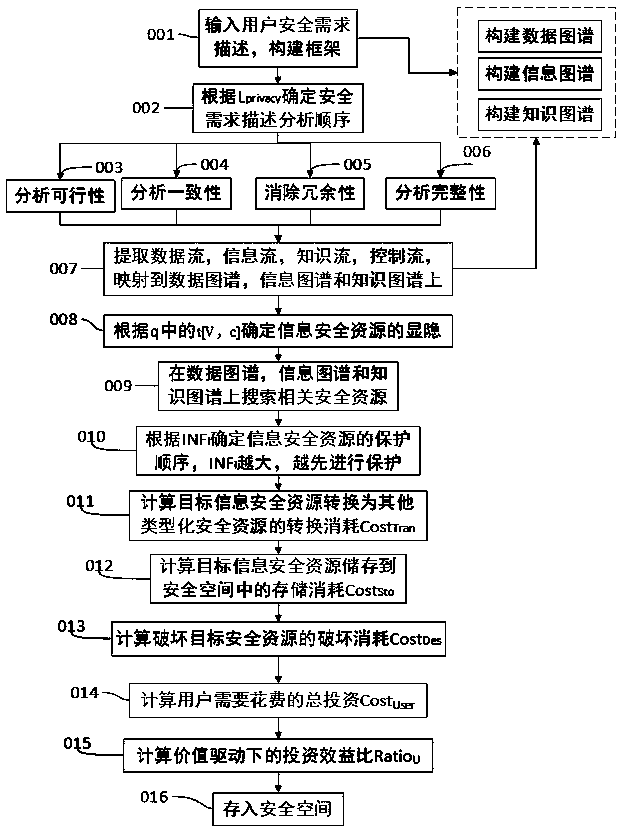
Information security protection method based on data graph, information graph and knowledge graph
InactiveCN108846299AClear classificationSpecific and efficient security protectionDigital data protectionSpecial data processing applicationsControl flowData graph
The invention relates to an information security protection method based on a data graph, an information graph and a knowledge graph, and belongs to the crossing field of distributed computing and software engineering. According to the method, security resources are classified into data security, information security and knowledge security. The feasibility, consistency, redundancy and integrity ofuser security requirements are analyzed based on the data graph, the information graph and the knowledge graph; user security requirement descriptions are optimized; and corresponding data flow, information flow, knowledge flow and control flow are mapped to the knowledge graph. Then, in a three-layer framework composed of the data graph, the information graph and the knowledge graph, the information security resources are converted into other types of security resources in sequence and then are stored in a security space for protecting the explicit and implicit information security resources.
Owner:HAINAN UNIVERSITY
Information security audit system and method thereof
InactiveCN103810558AComputer security arrangementsResourcesInformation security auditInformation security
The invention discloses an information security audit system and a method thereof. The information security audit method is applied to the information security audit system. The information security audit method comprises the steps outlined below. A normalized weighting of each of a plurality of members of an organization is computed according to a level and at least one feature of each of the members. A plurality of risk evaluation values corresponding to a plurality of audit items are computed and a normalized risk evaluation value of each of the members is further computed according to the risk evaluation values and the normalized weighting. A relation of the normalized risk evaluation value and a plurality of threshold value intervals are determined to dynamically adjust an audit period and / or a number of the audit items according to the relation.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
Security policy flow down system
ActiveUS8572678B2Easy to analyzeMemory loss protectionError detection/correctionProgram planningSecurity compliance
A system and method are provided that distill an organization's information security plan into a detailed and unambiguous security object model. The developed security object model provides a visualization of complex relationships between individual elements and levels that is usable to carry into effect the organization's information security plan. Configuration control and a verifiable level of security compliance are provided through implementation of the organization's information security plan by the developed security object model. The developed security object model is hosted on a computing platform in communication with at least the organization's network to provide information security plan compliance, configuration control and gap analysis in a usable form to the organization.
Owner:LOCKHEED MARTIN CORP
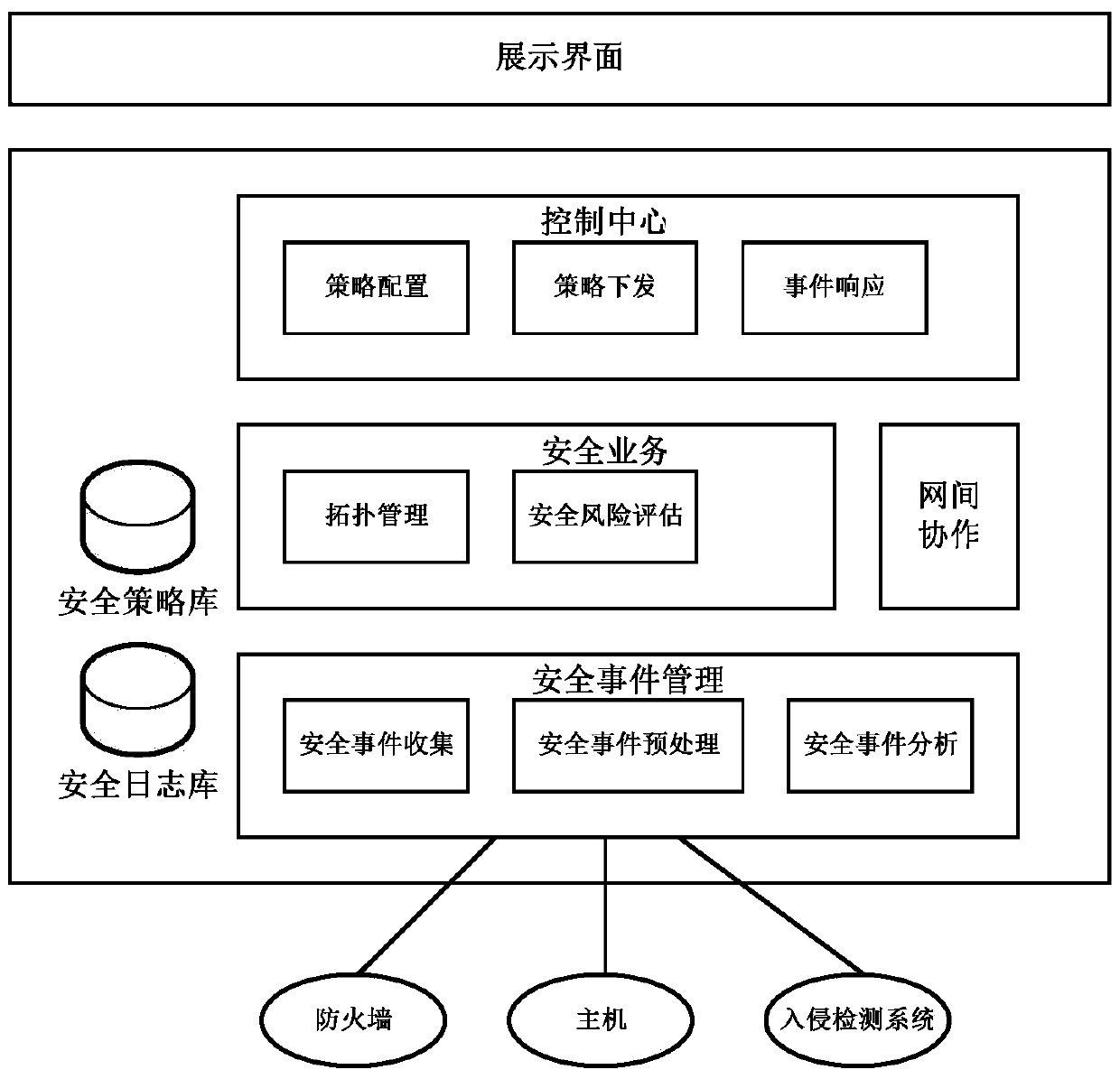
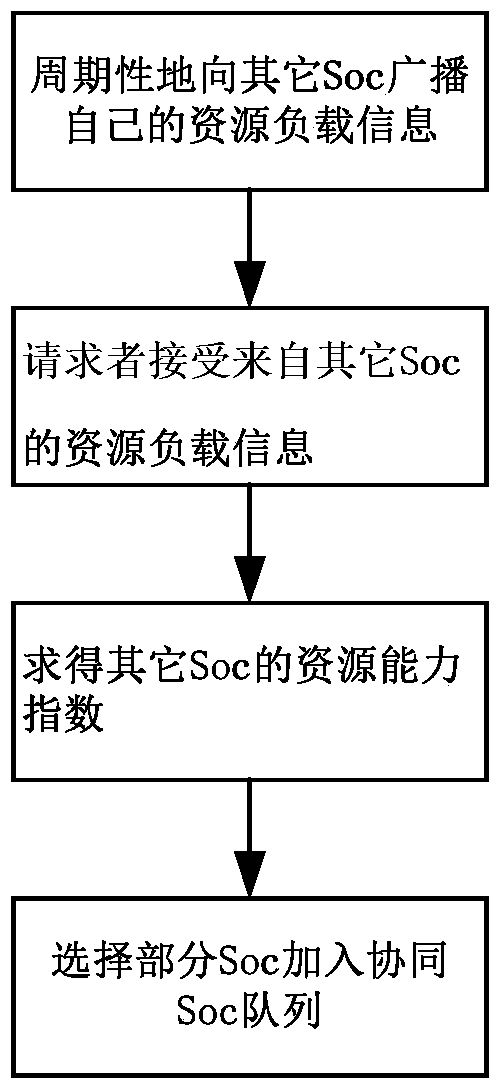
A Collaborative Analysis Method for Information Security Management Center
ActiveCN104378364BComprehensive judgmentImprove accuracyTransmissionInformation security risk managementSecurity operations center
The invention relates to the technical field of information safety, in particular to a collaborative analysis method of information security operation centers. An internetwork collaborative module of one of the security operation centers sends suspected threat information, then a safety event management module analyzes the suspected threat information, and it is determined that a threat is found if the threat meets the standard of a certain attack event; a receiver finding the threat informs a sender of the suspected threat and other security operation centers of confirmation information through the internetwork collaborative module; a requester takes corresponding measures through a safety strategy library; if the sender does not find the threat by himself, correlation analysis of the second stage is carried out by communication between the sender and other receivers; all the security operation centers take corresponding measures for response after receiving the information. The collaborative analysis method of the information security operation centers achieves the collaborative analysis of the information security operation centers and can be used for the security operation centers for information security operation.
Owner:GUANGDONG ELECTRONICS IND INST
Personal information security auditing and evaluating system
PendingCN113139186ADigital data protectionPlatform integrity maintainanceEngineeringInformation security audit
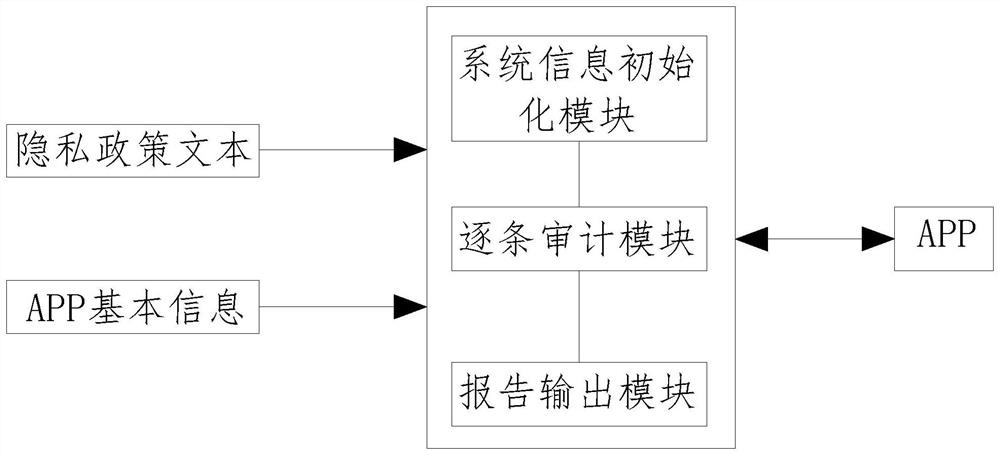
A personal information security audit evaluation system inputs a privacy policy text and basic information of a to-be-detected APP in advance and fills the to-be-detected APP, and comprises: a system information initialization module used for objectifying the input information and mounting detection items so that to-be-detected personnel perform detection one by one; an item-by-item auditing module which is in communication connection with the system information initialization module so that a detector can open the detection items item by item and detect the detection items; and an report output module which is in communication connection with the item-by-item auditing module, and is used for exporting the detection result according to a specified report format for a user to use after the auditing of all the detection items is completed. According to the system, a keyword hit and keyword association surrounding algorithm is adopted, the content indicated by the specified item is quickly found, detection personnel can conveniently and more accurately judge whether personal information violation exists or not, and finally the detection report is formed through arrangement and is provided for an owner unit to perform rectify and reform.
Owner:开元华创科技(集团)有限公司
An audit method and system for information security
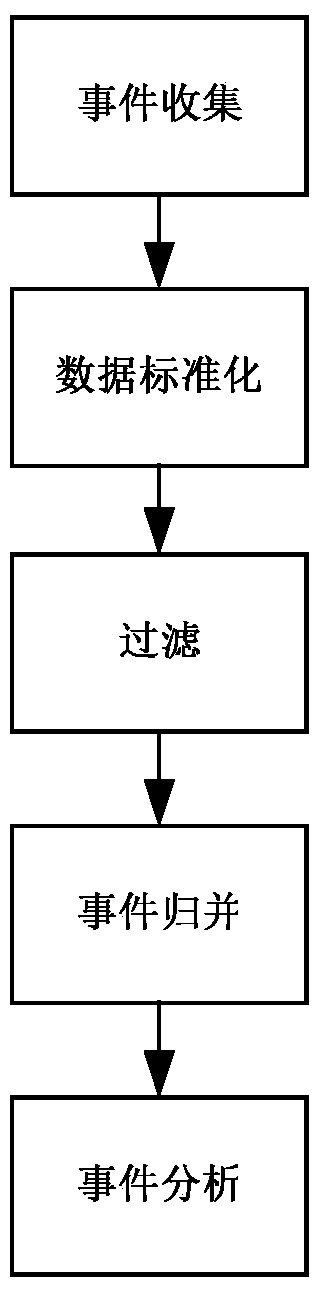
ActiveCN103577905BImprove work efficiencyImprove audit qualityResourcesInformation security managementInformation security audit
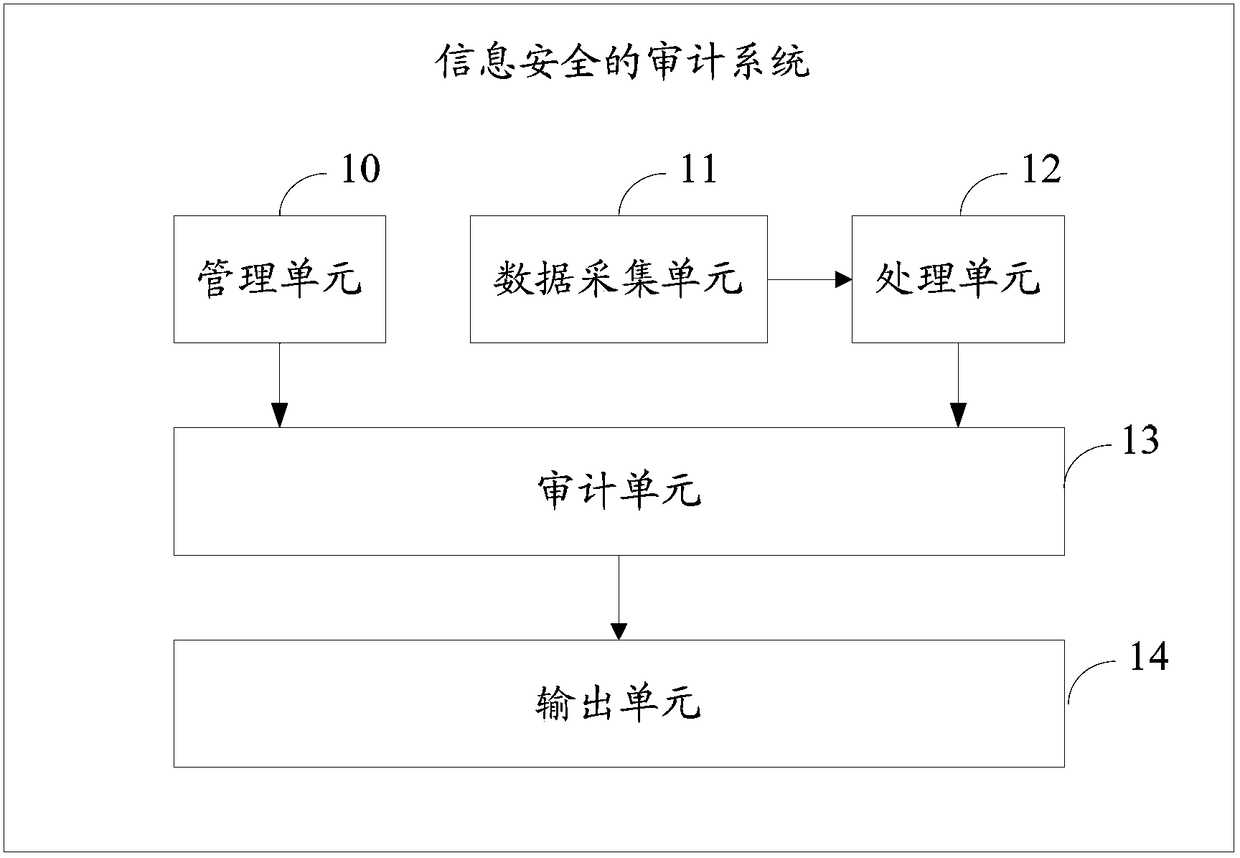
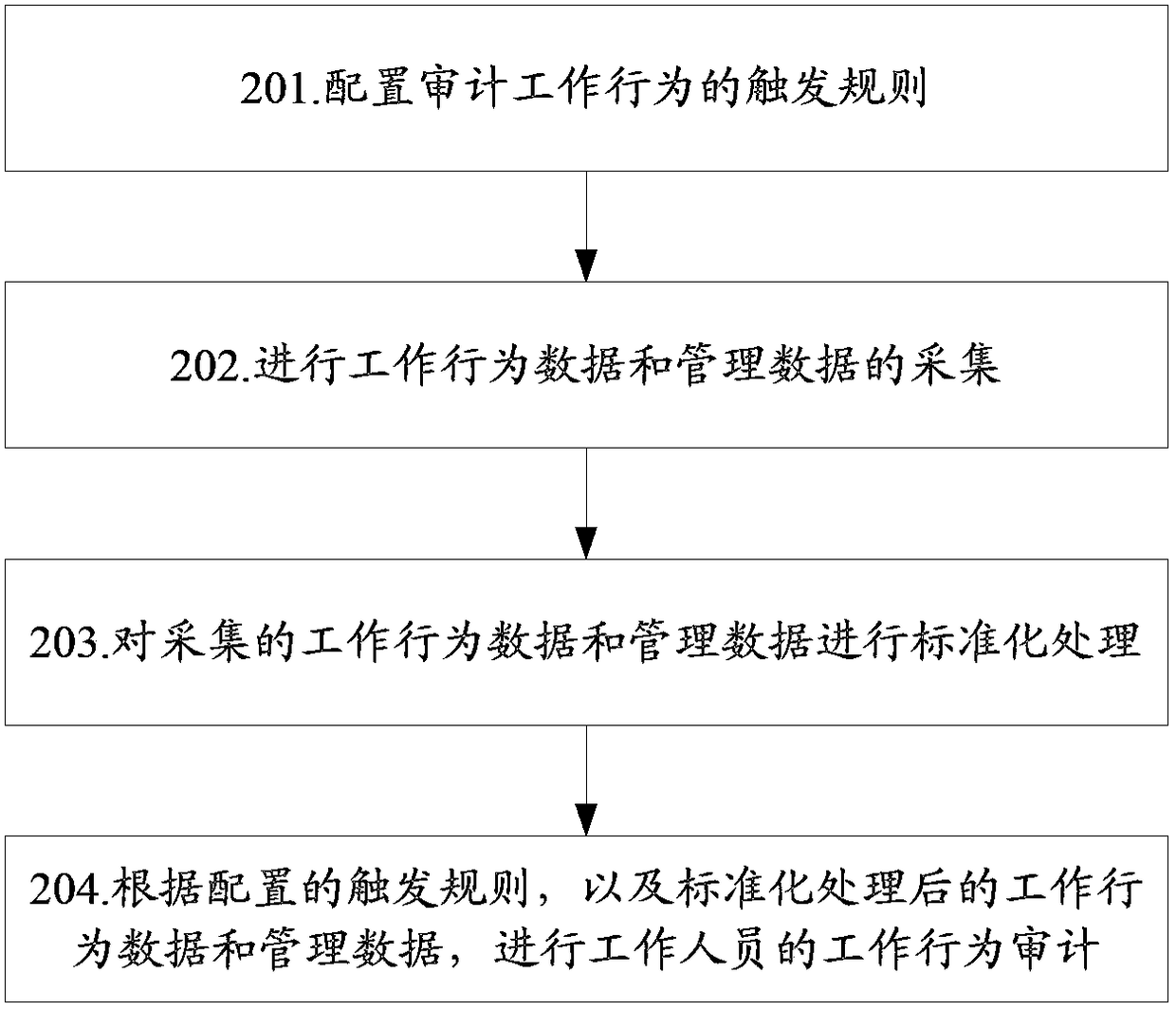
The invention discloses an information security audit method, which includes: configuring trigger rules for auditing work behavior; collecting work behavior data and management data; standardizing the collected work behavior data and management data; according to the configured trigger rules, And standardize the work behavior data and management data to audit the work behavior of the staff; the invention also provides an information security audit system. According to the technical solution of the present invention, the work efficiency of auditors or safety management personnel in auditing work behaviors can be improved, and wrong audits and missed audits in the auditing process can be reduced.
Owner:ZICT TECH CO LTD
Multiple real-time data encryption method for information security assurance in smart community and system
InactiveCN109286486AEnsure safetyGuaranteed reliabilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesReal-time dataConfidentiality
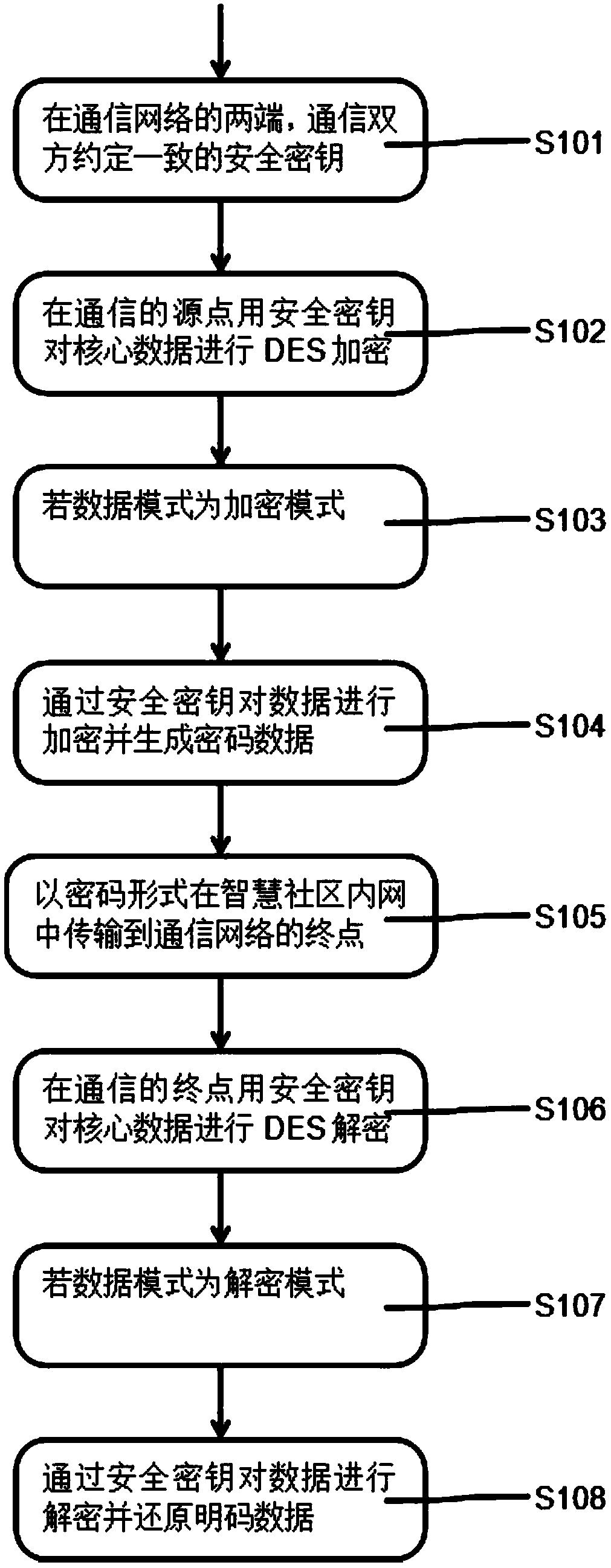
The invention belongs to the technical field of information security, in particular to a multiple real-time data encryption method for information security assurance in a smart community. The invention also provides a multiple real-time data encryption information security system for information security assurance in a smart community. A security key is used for carrying out DES encryption on coredata at a communication source point; if a data mode is an encryption mode, the data are encrypted by the security key and password data are generated. The problems that the security and the reliability of transmission of the core data in a smart community Intranet can not be assured when data in the smart community Intranet generally do not perform password transmission in the prior art can be solved, and the method and the system have the beneficial technical effects of high security, high reliability, high confidentiality and security password.
Owner:CHANGSHU INSTITUTE OF TECHNOLOGY +1
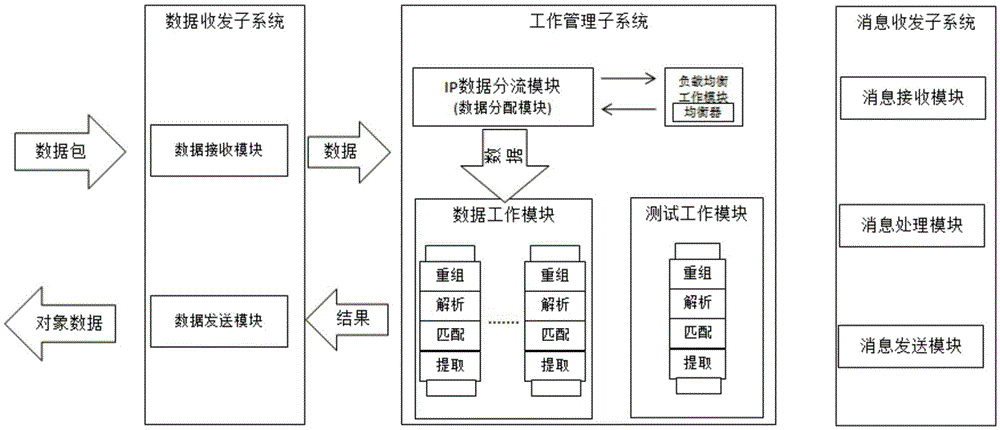
Method and system for analyzing and restoring network application behavior
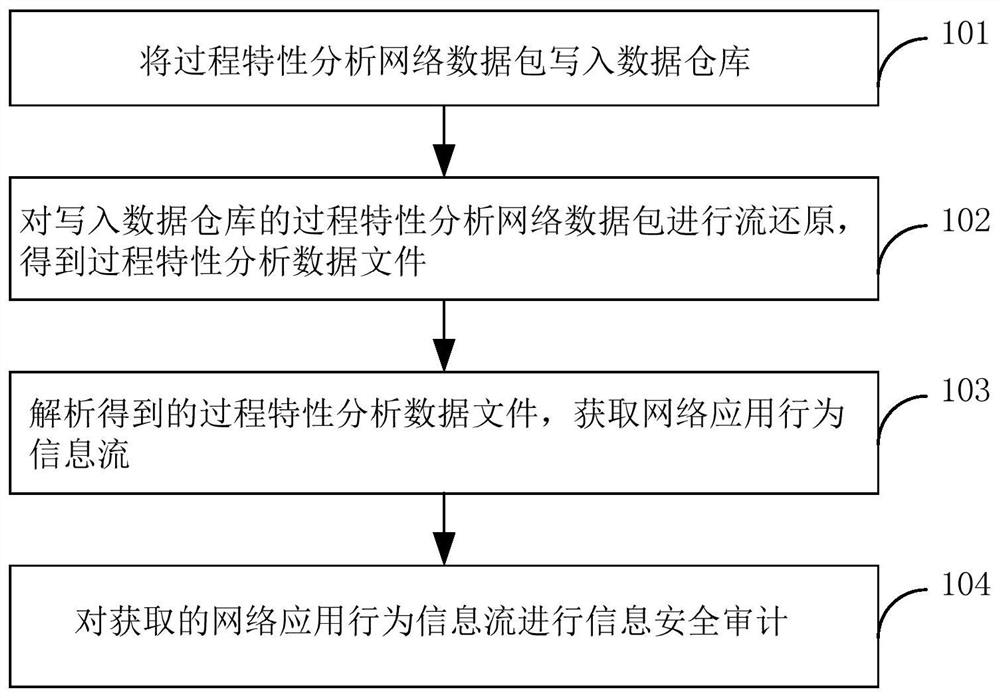
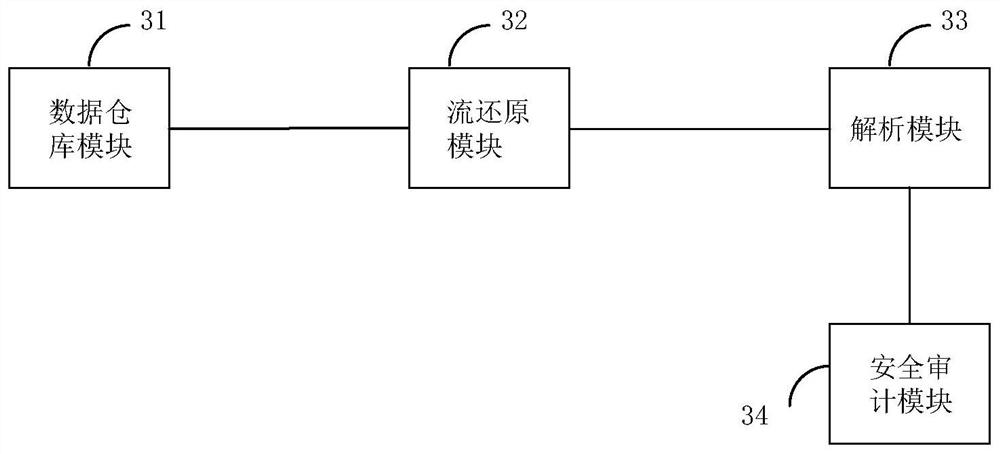
ActiveCN108650229BImprove safety precisionAdd dimensionPlatform integrity maintainanceTransmissionData packNetwork packet
The present application provides a method and system for analyzing and restoring network application behavior, which can improve the security accuracy of information security auditing. The network application behavior analysis and restoration method includes: writing process characteristic analysis network data packets into the data warehouse; performing flow restoration on the process characteristic analysis network data packets written into the data warehouse to obtain process characteristic analysis data files; analyzing the obtained process characteristic analysis data file to obtain network application behavior information flow; conduct information security audit on the acquired network application behavior information flow.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
Method and system for implementing information security audit based on walk-through test technology
InactiveCN104462988BDigital data protectionPlatform integrity maintainanceGlobal information systemInternet privacy
The invention relates to the technical field of information monitoring, in particular to a walk-through test technique based information security audit implementation method and system. The method includes: recognizing business sensitive information waiting for audit and access right of the business sensitive information; tracking flow paths of the business sensitive information in one or more information systems based on the access right; performing audit analysis on risk vulnerabilities existing in the process that the systems with access right process the business sensitive information according to tracking results; based on audit analysis results of the risk vulnerabilities, acquiring a risk value of the business sensitive information. By the method and system, risks existing in the process that the sensitive information flows in full life circles of the multiple information systems can be monitored.
Owner:STATE GRID CORP OF CHINA +2
An adaptive cloud computing environment virtual security domain access control method and system
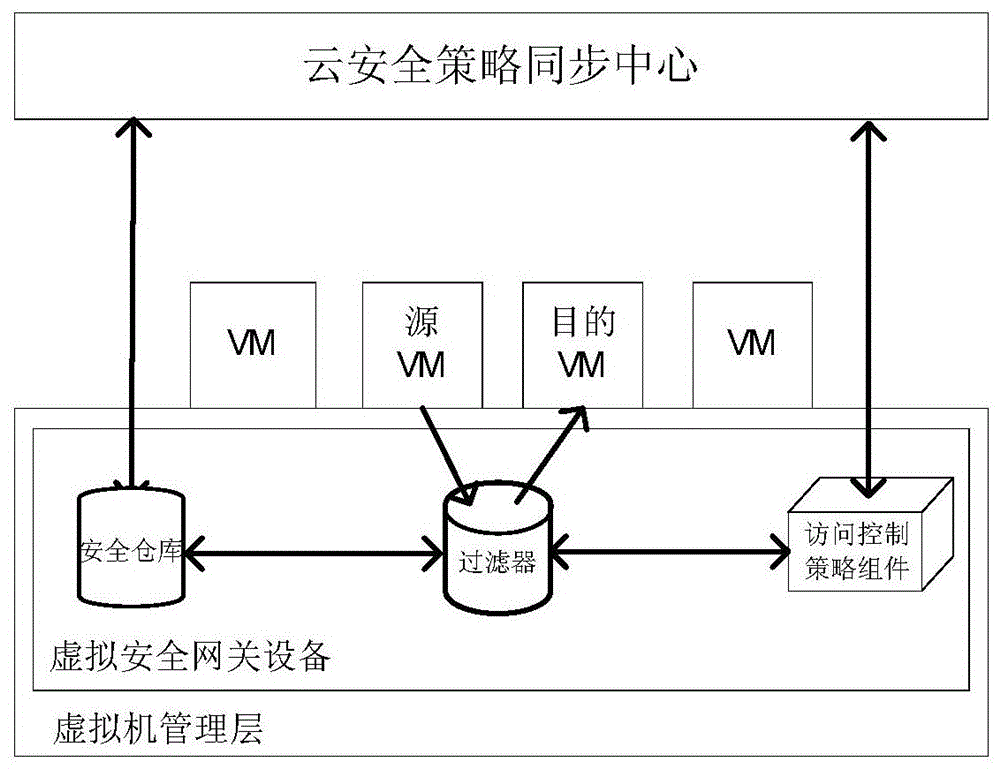
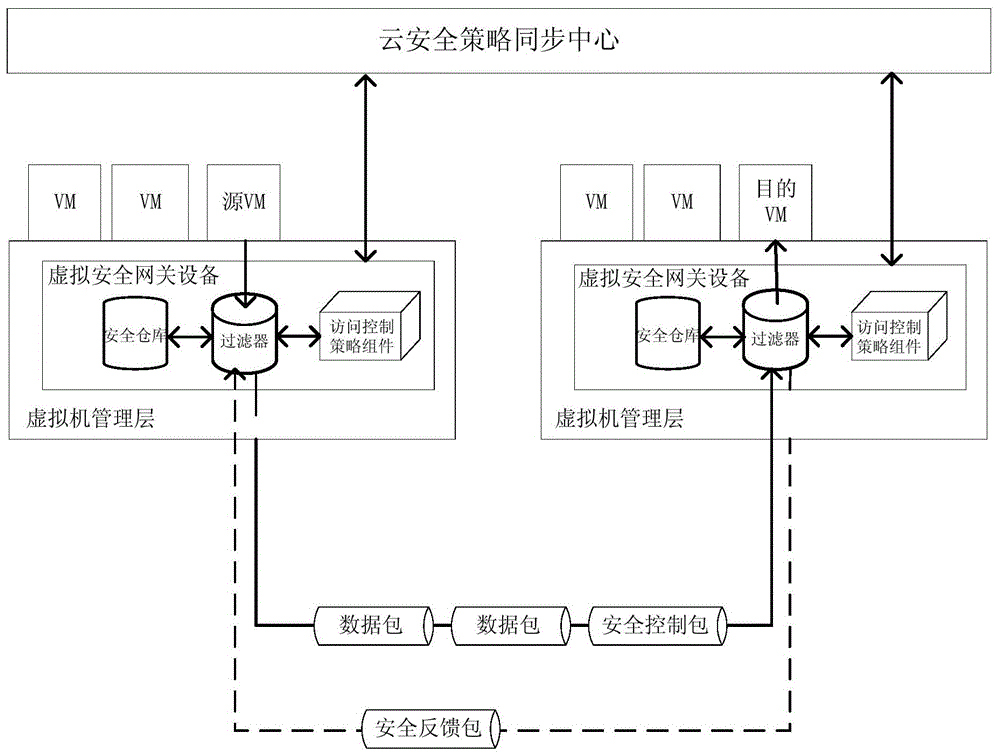
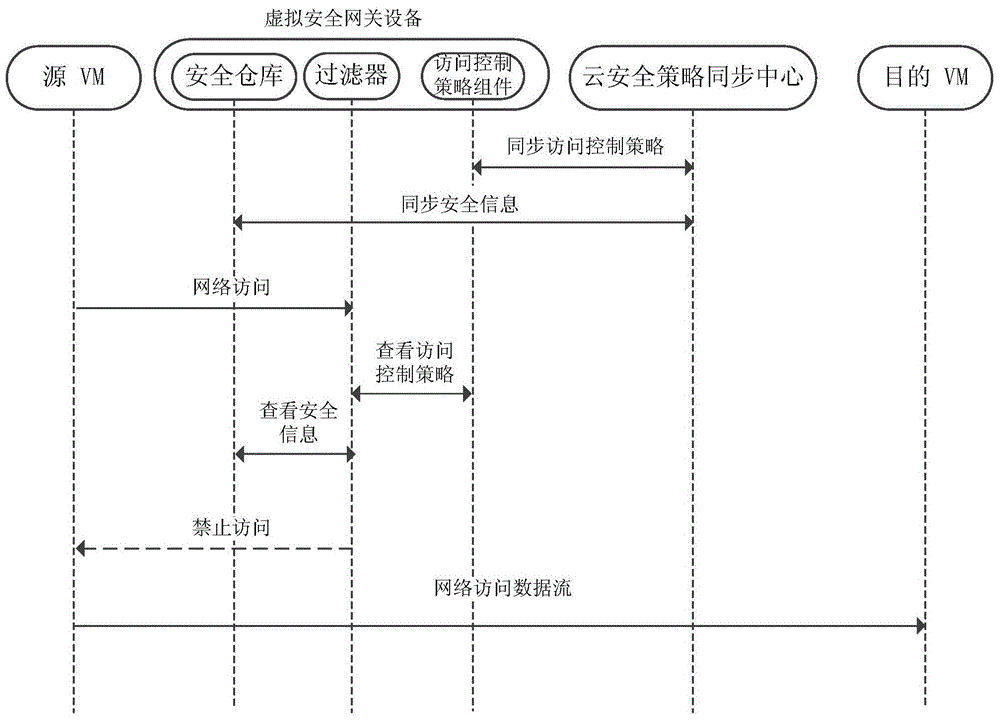
ActiveCN103458003BImplement access controlImplement cross-domain access controlTransmissionSecurity domainNetwork communication
The present invention relates to a method and system for controlling access to a virtual security domain in an adaptive cloud computing environment. The method deploys a virtual security gateway device on a virtual machine management layer, and implements the virtual security gateway device with a cloud security policy synchronization center in the cloud computing environment. Interact to obtain security policy information, and monitor the network communication behavior of the virtual machine on the virtual machine management layer according to the security policy, and directly perform access control on the network communication data packets inside the same physical machine; for network communication across physical machines The security control package is added to the data package, and the cross-physical machine adaptive access control is performed through the security control package and the security feedback package containing the dynamic adjustment access control policy information. The method and system can realize the fine-grained access control function for communication between different virtual machines on the same physical machine or different physical machines, and can dynamically adjust access control policies to realize adaptive cloud computing environment virtual security domain access control .
Owner:CEC CYBERSPACE GREAT WALL
A comprehensive audit method for information security
ActiveCN102567849BRealize unified managementSimple working processResourcesTransmissionSystem integrationWeb service
The invention discloses an information security comprehensive audit method, comprising: pre-integrating Web Service in the information security comprehensive audit system, and creating a Web Service interface for the one-ticket-two-bill system; The key information of the user is sent to the information security comprehensive audit system; the information security comprehensive audit system stores the key information; the key information includes the user ID; when it is necessary to apply for operation and maintenance authorization for the user, through the Web Service interface, the system will The host information and account information of the operation and maintenance host are sent to the information security comprehensive audit system; the information security comprehensive audit system establishes the user's operation and maintenance authorization. The invention improves the accuracy rate of the audit in the information security comprehensive audit work, effectively reduces the workload of the administrator of the information security comprehensive audit system, and improves the work efficiency.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +1
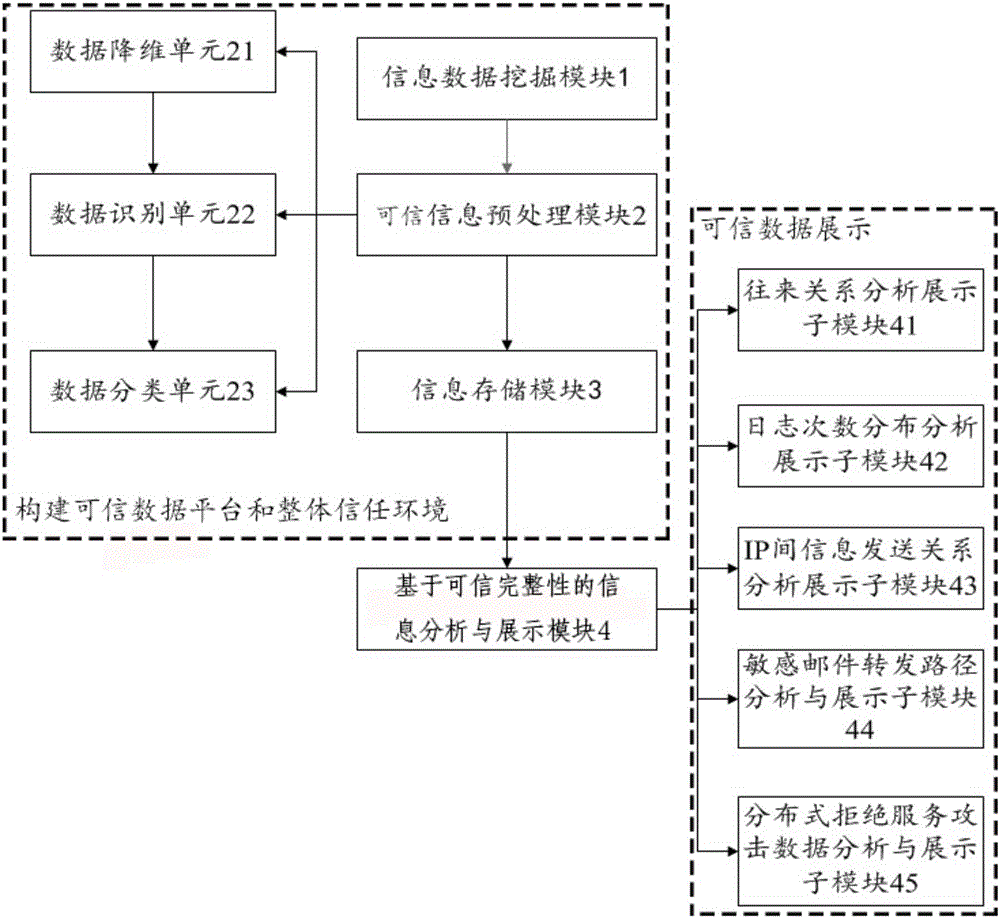
Cloud Computing Information Security Visualization System Based on Trusted Computing
The invention provides a cloud computing information safe visualization system based on trusted computing. According to the visualization system, an integrated trust environment is established on the basis of function modules such as data mining, data identification and data dimension reduction, so that the information safe visualization system from data mining to data processing and storage, and to trusted data display is established. Starting from data mining and preprocessing modules, the data of a trusted data information analysis and display module is trusted. According to the system, through adoption of a brand new module combination and an innovative algorithm, the trust and safety of the network information are ensured; trusted quantification and visualization evaluation of the information safety are realized; and the convenience is provided for a manager in an aspect of network safety management.
Owner:GUANGXI POWER GRID CORP
Preposed audit method
InactiveCN108337322ALow hardware requirementsReduce complexityTransmissionNetwork packetInformation security audit
The invention discloses a preposed audit method in the field of network information security audit. An audit analysis behavior is finished through an audit system, specifically, network data packets are intercepted through a netfilter, related policy matching is carried out on the intercepted data packets, through modification of the final data packet in a data packet stream, corresponding js is inserted before the final data packet, the js obtains necessary information from a client browser, and an audit process is realized. According to the method, the audit efficiency is improved, an auditmode is changed, and through utilization of the system, a user can obtain the necessary information relatively comprehensively and rapidly, and the existing behavior audit mode is expanded.
Owner:SHENZHEN SEENTECH INFORMATION TECH DEV
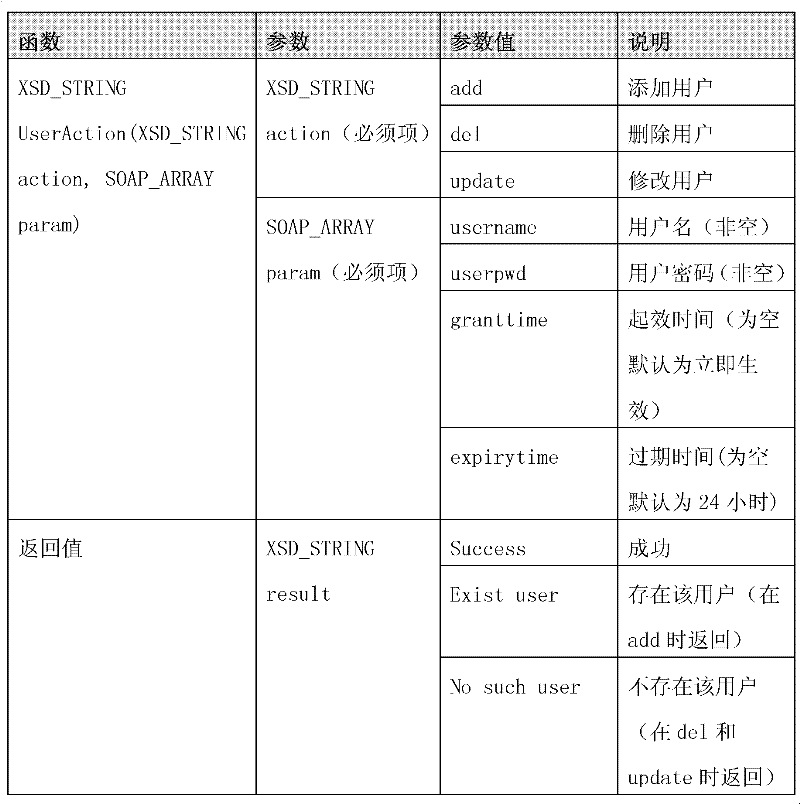
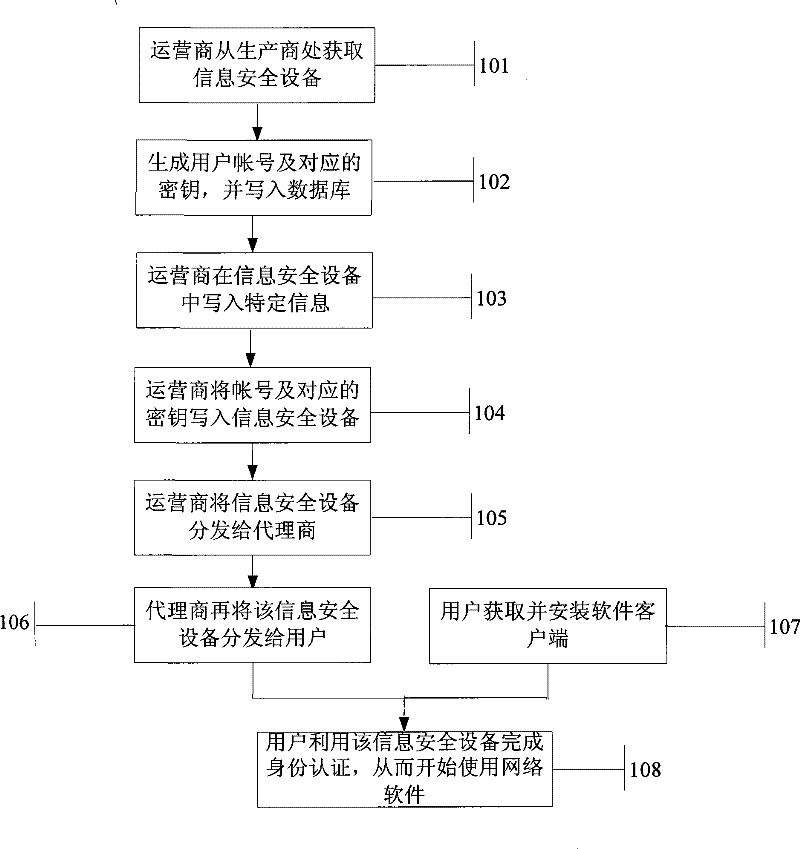
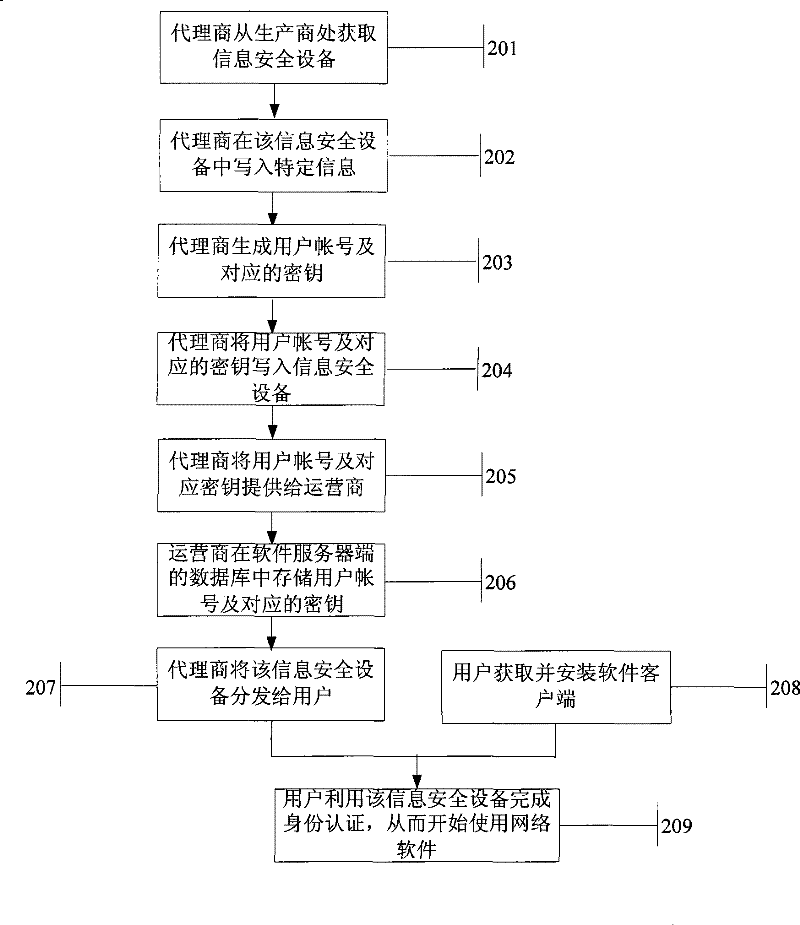
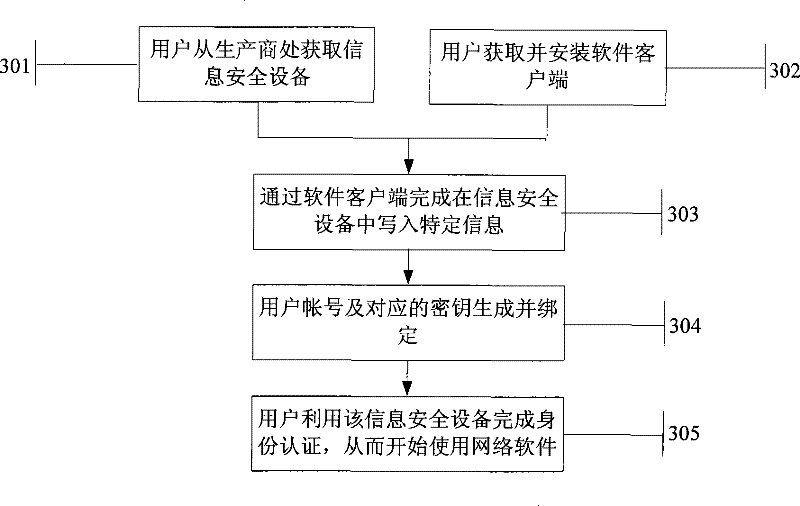
Method for information security device for binding network software
ActiveCN101588351BEfficient managementPrevent theftUser identity/authority verificationInformation security auditInformation security
The invention relates to the field of information technology safety, and in particular provides a method for an information security device for binding network software. The method comprises the following steps that: a service end generates corresponding accounts and keys according to a hardware identification number of the information security device, writes the hardware identification number, the corresponding accounts and keys into a network software database, and writes the accounts and keys into the information security device; specific information is written into the information securitydevice, and the specific information is network software characteristic information and / or service end characteristic information; and a user acquires the information security device with the accounts, the keys and the specific information, installs the software, uses the software by using the specific information in the information security device, and uses the accounts and the keys in the information security device to carry out authentication. The binding method greatly improves the safety of the information security device.
Owner:FEITIAN TECHNOLOGIES
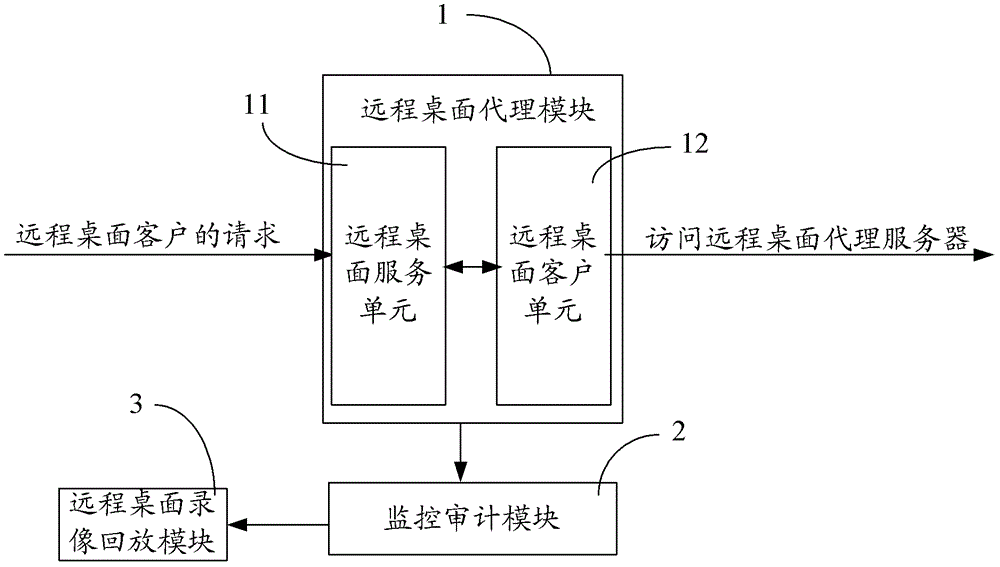
An information security comprehensive audit system and method
The invention discloses an information security comprehensive audit system and method. The system comprises a remote desktop proxy module, a monitoring and auditing module and a remote desktop video playback module, wherein the remote desktop proxy module is used for receiving a request from a remote desktop proxy client, authenticating identity of a remote desktop proxy request, realizing data exchange between the remote desktop proxy client and the remote desktop proxy server and recording session content; the monitoring and auditing module is used for providing an interface for querying historical records and performing data statistics and recording graphic operation of a server in a video mode; and the remote desktop video playback module is used for playing back the graphic operation at the server recorded by the monitoring and auditing module. Since the information security comprehensive audit system in the embodiment is allocated in a computer in a network without installing a specific audit engine at the server, the allocation task is simplified. In addition, occupancy of system resource at the server is avoided.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +1
Information security management system
The invention relates to an information security management system which comprises an information security server and a control table, wherein the information security server is provided with information security management software, the control table is coupled with the information security server through the Internet and is coupled with a plurality of computers through local area networks, and the computers are all provided with the agent program of the information security management software. After being linked to the information security server, the control table can set information security policies of the computers on the information security management software to generate set results, and the agent program in the computers can control and manage the information security of the computers according the set results. Compared with the traditional information security management system, the cost of the information security management system of the invention is lower, and can be afforded by ordinary middle-size and small-size enterprises, and the information security management system is very suitable for practical use.
Owner:FINEART TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com