Security policy flow down system
a security policy and flow down system technology, applied in the field of systems and methods for implementing an automated security policy, can solve the problems of affecting the implementation of information security in an organization, affecting the effectiveness of the security policy implementation process, and unable to provide a comprehensive framework for capturing, so as to facilitate further analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
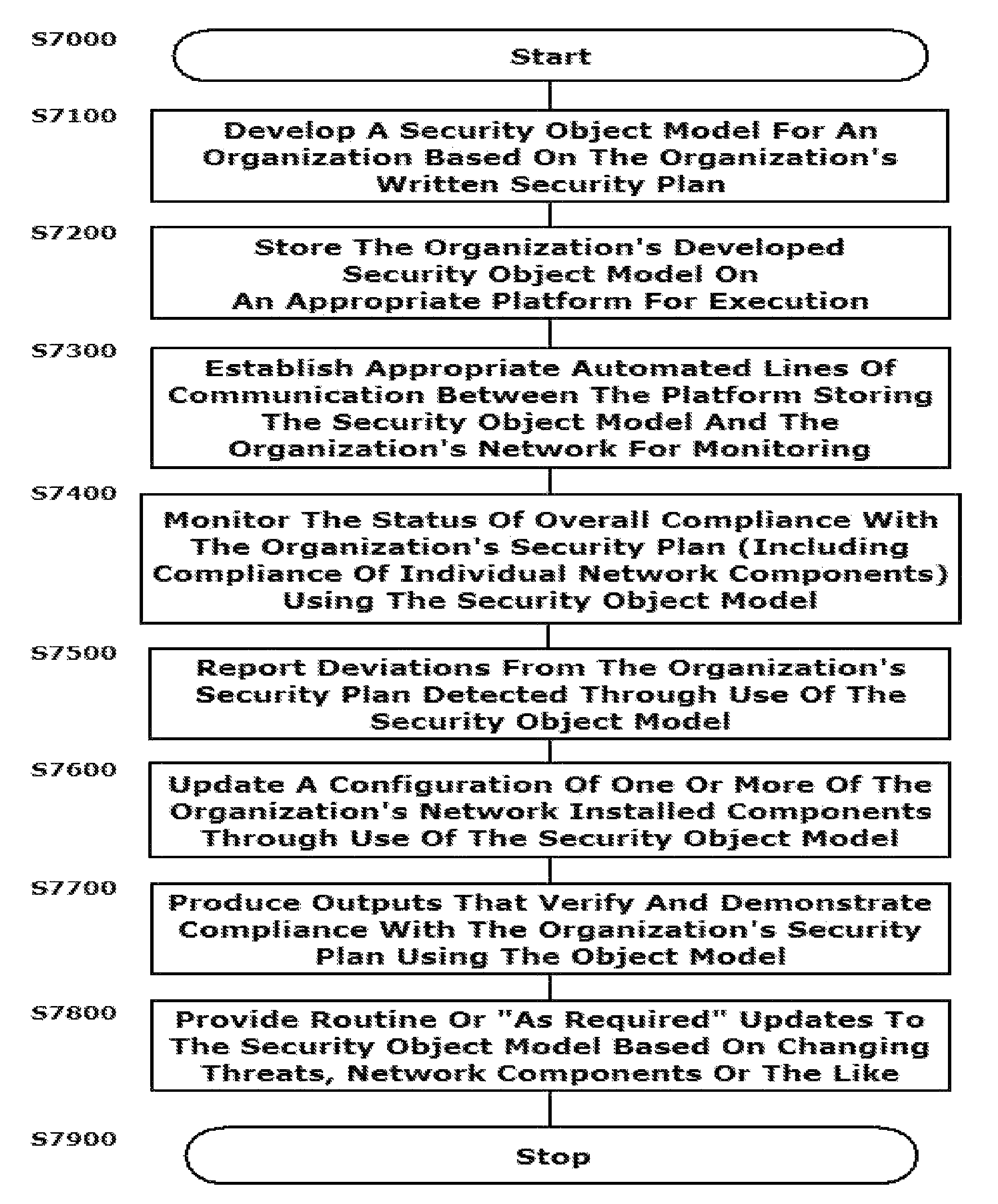
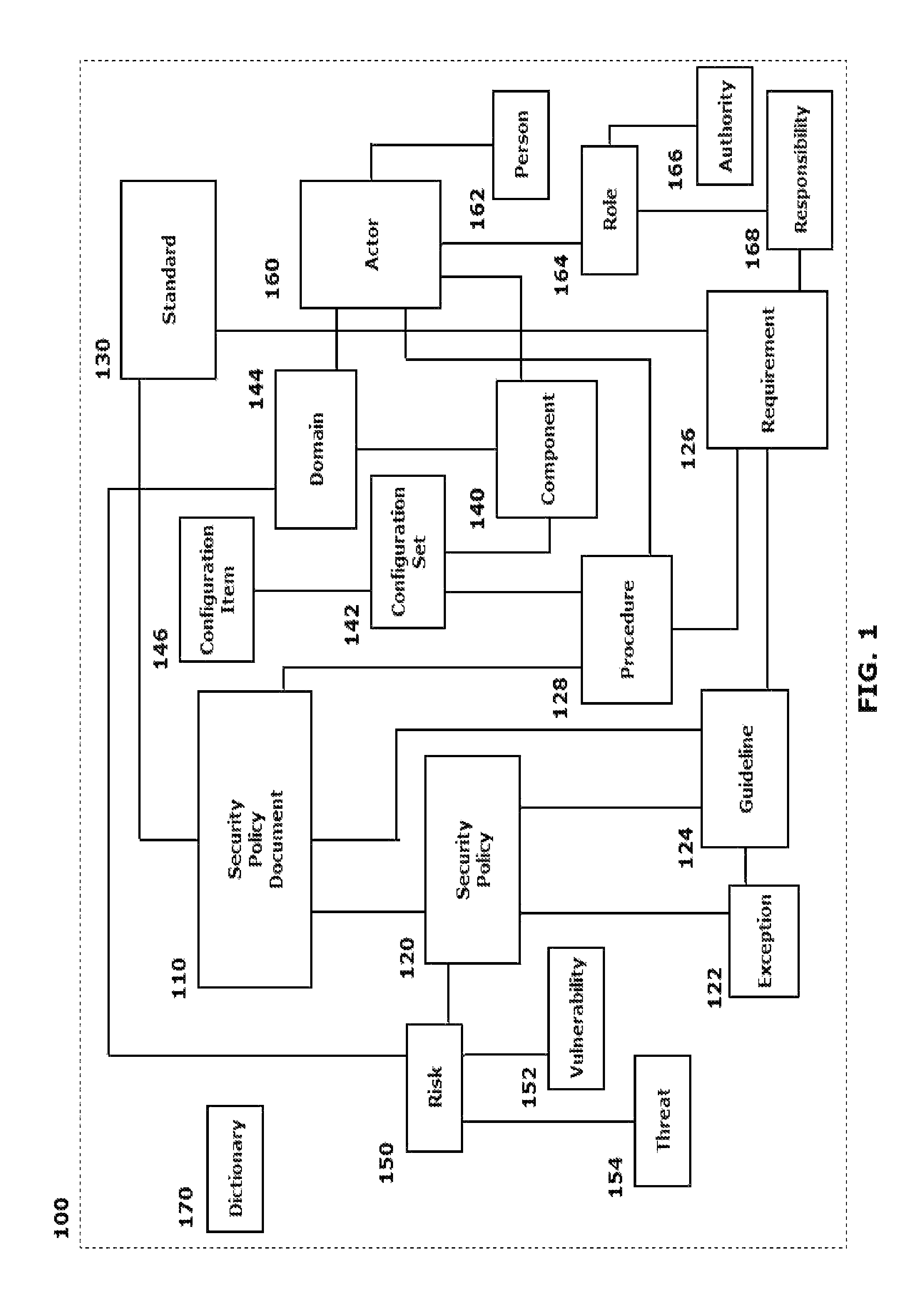
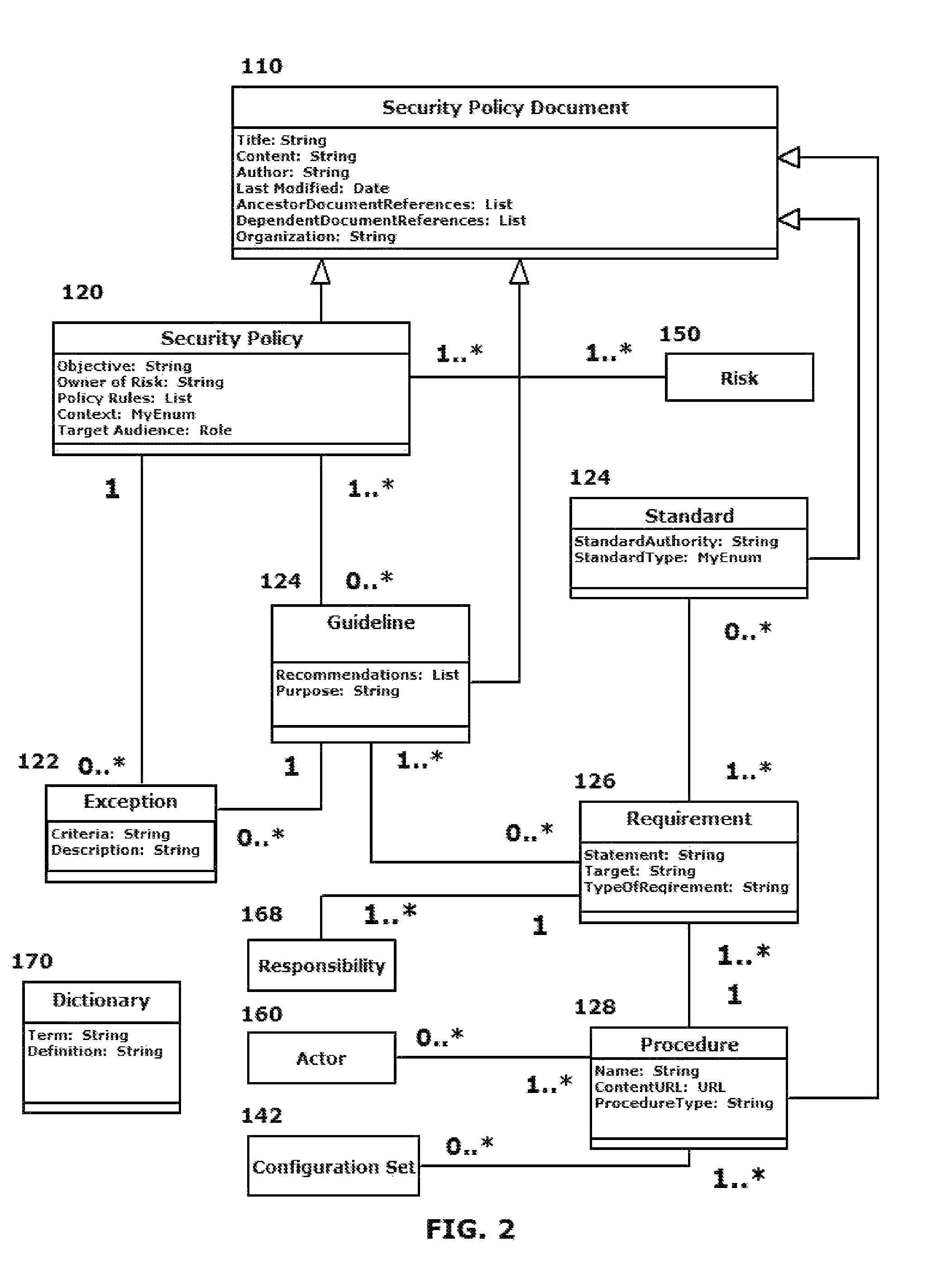
[0002]This disclosure relates to systems and methods for implementing an automated security policy for an organization, particularly through implementing a semantic model in a formal modeling language such as Unified Modeling Language Model (UML), Web Ontology Language (OWL), Semantic Application Design Language (SADL), a controlled-English language that maps directly into OWL, or any other semantic language capable of capturing the instances, classes, and relationships of the security domain in such a way as to render the model computable.
[0003]2. Related Art
[0004]The information security of an organization is generally governed at the highest levels by the existence of policies, guidelines and standards. These policies, guidelines and standards are generally provided in written form. One or more individuals in the organization are then tasked with developing information security procedures, requirements and, in many cases, specific configurations for information security policy im...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com