Patents
Literature
392 results about "Federal state" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
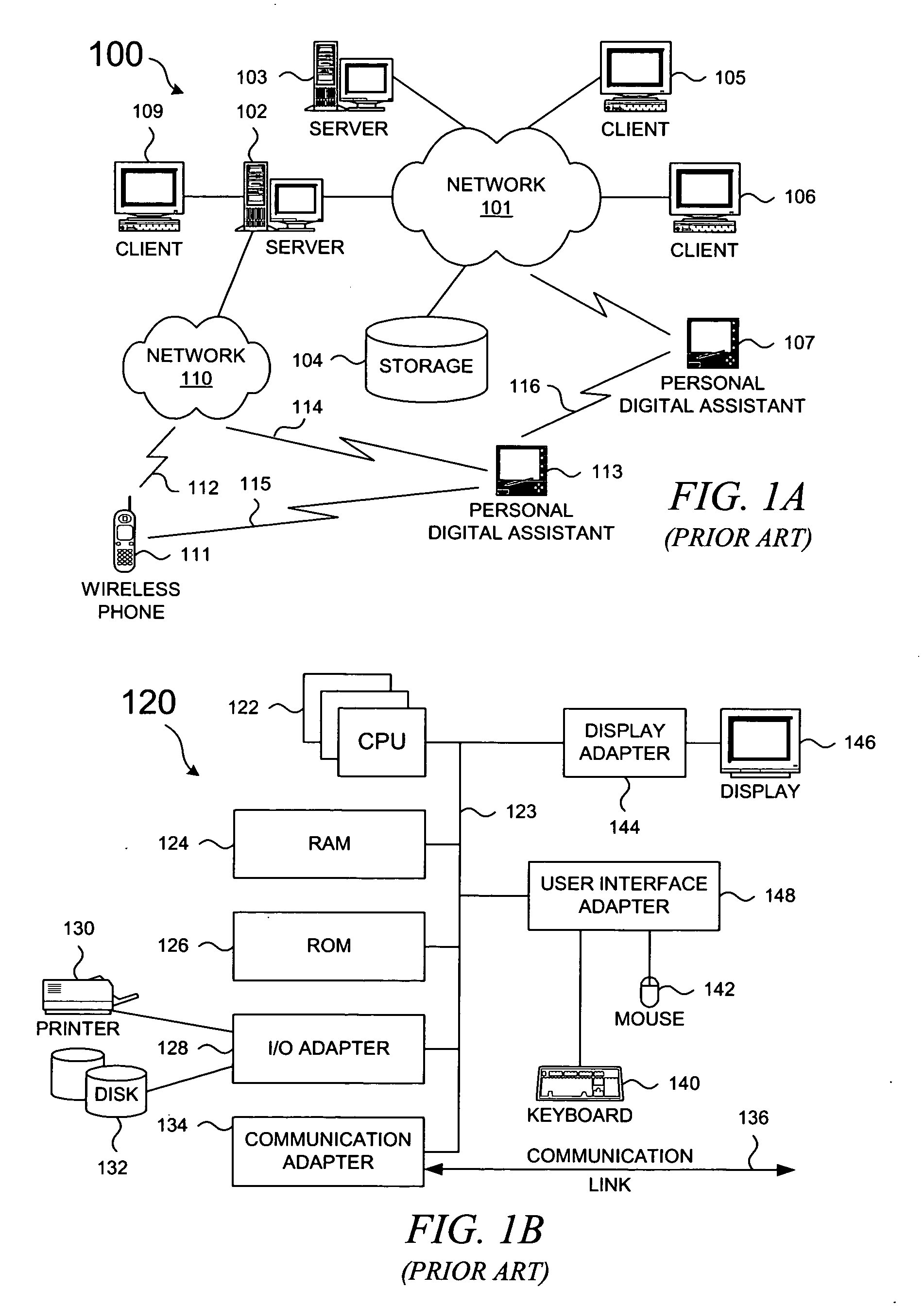
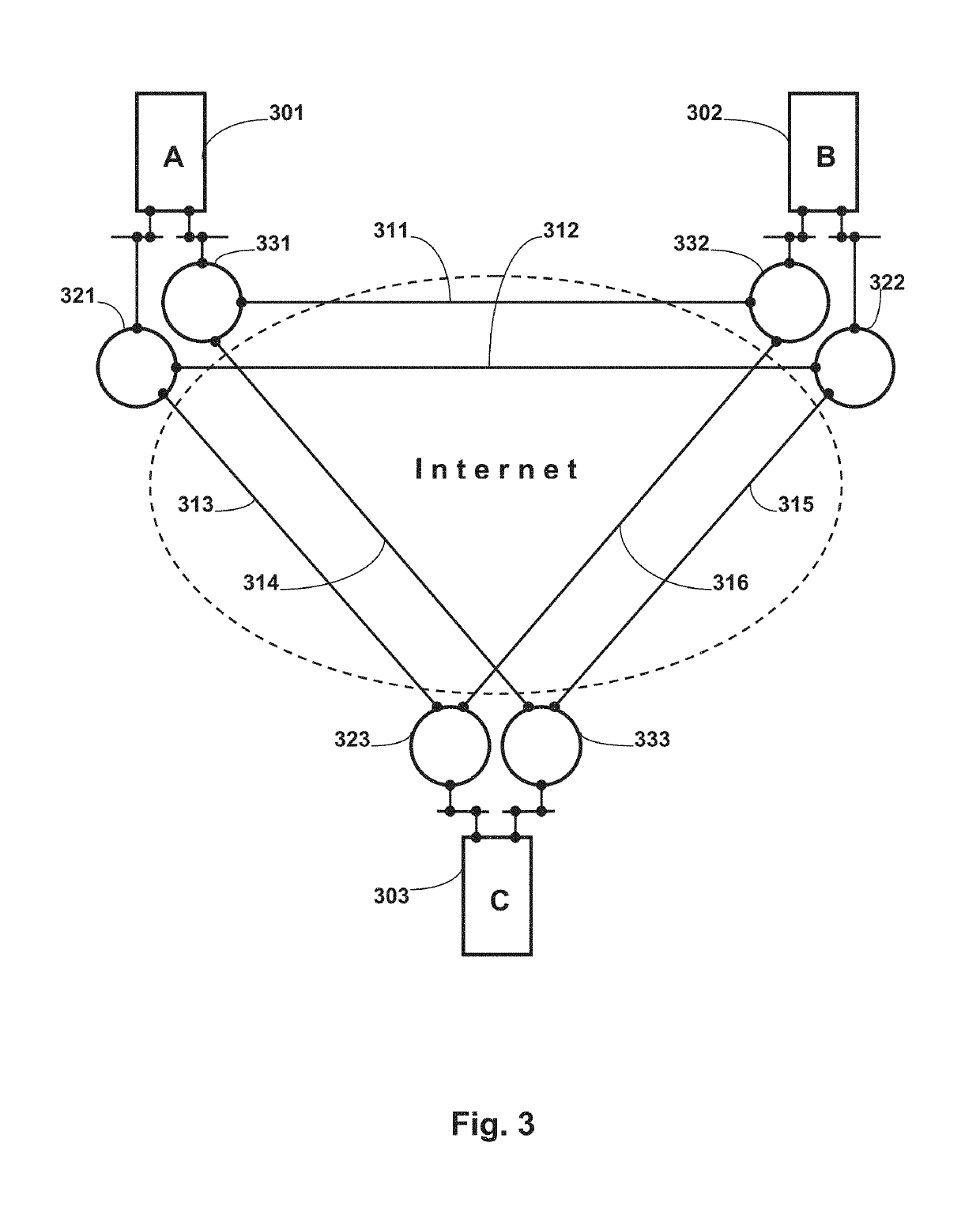
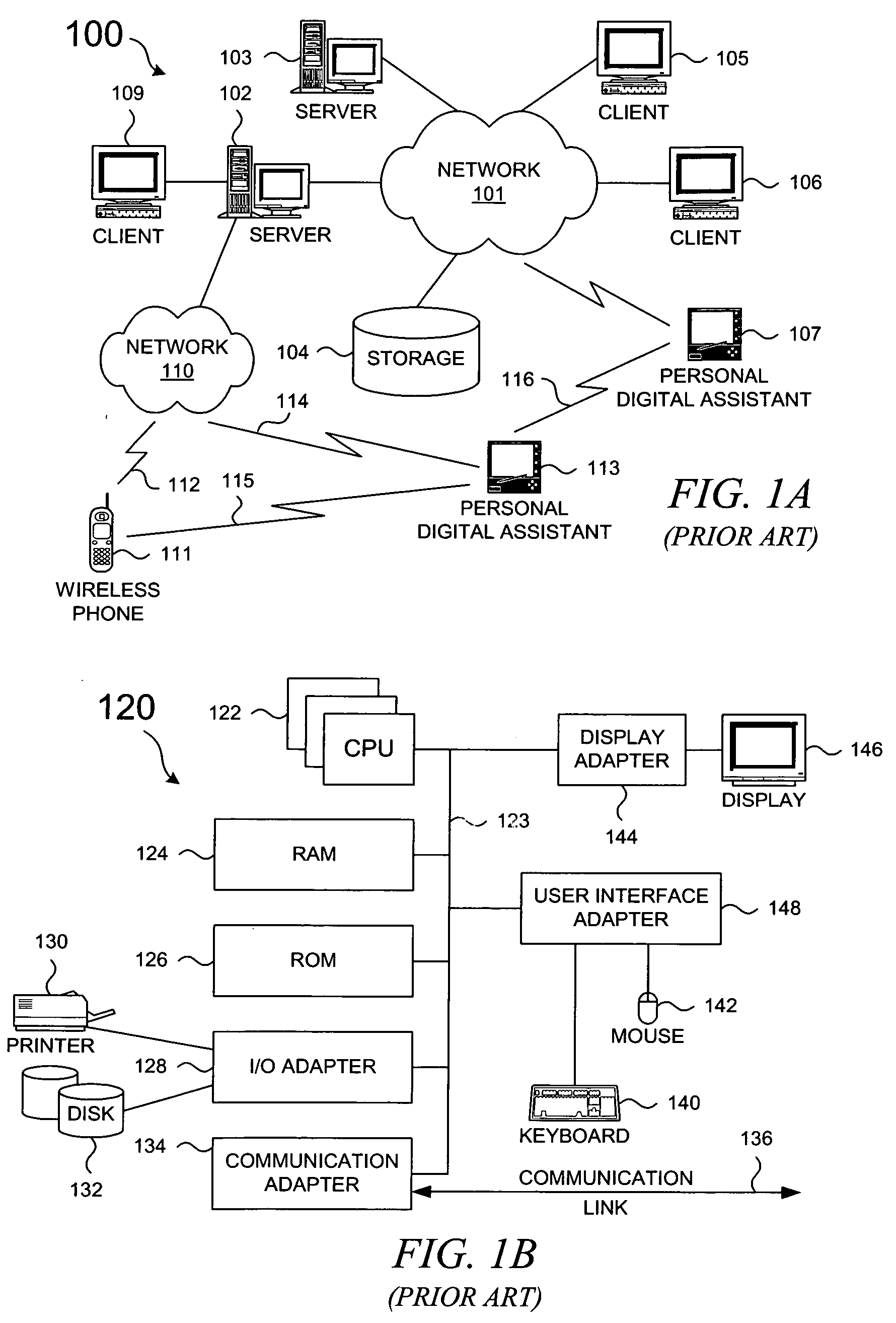
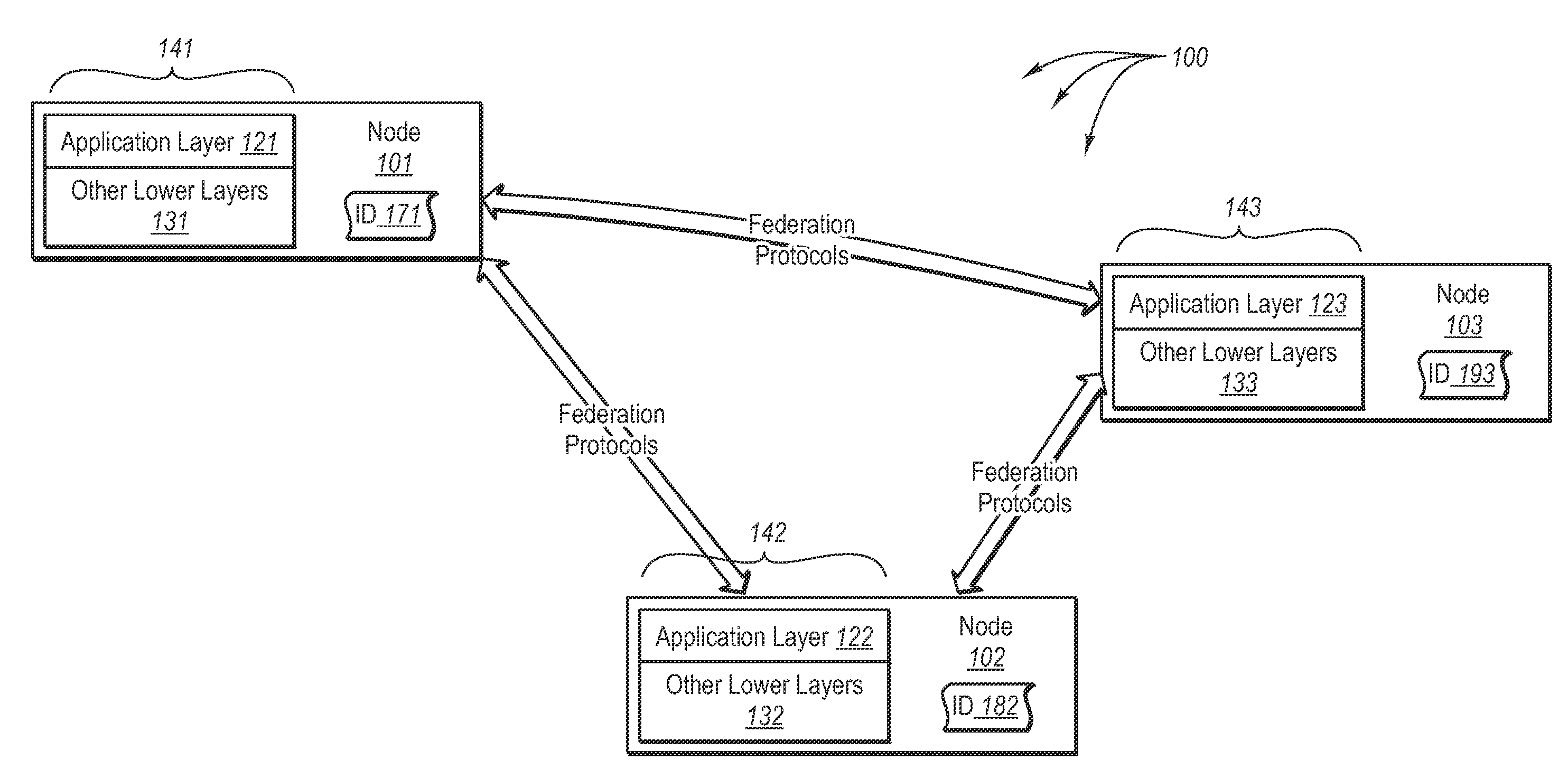
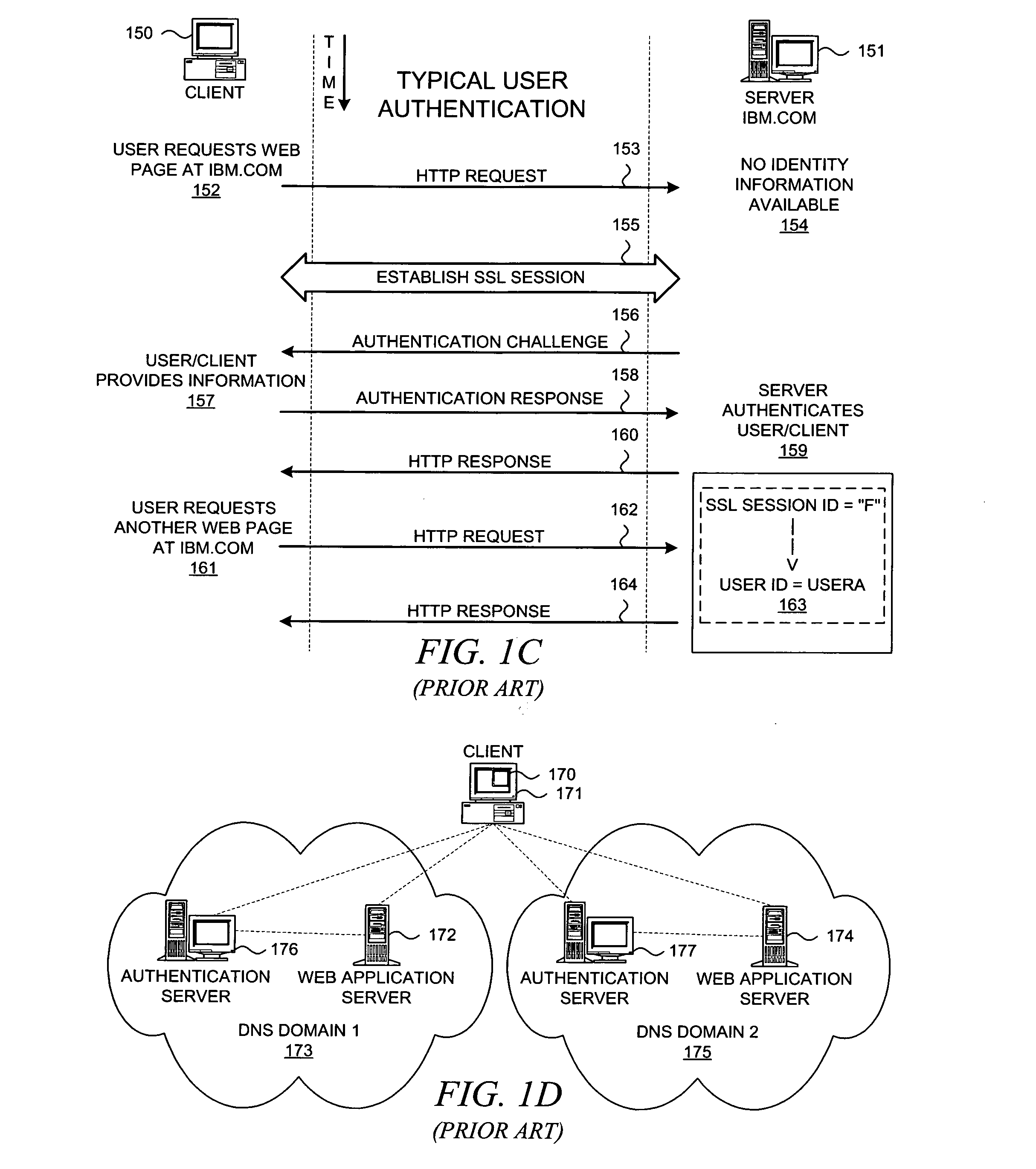
A federation (also known as a federal state) is a political entity characterized by a union of partially self-governing provinces, states, or other regions under a central federal government (federalism). In a federation, the self-governing status of the component states, as well as the division of power between them and the central government, is typically constitutionally entrenched and may not be altered by a unilateral decision of either party, the states or the federal political body. Alternatively, a federation is a form of government in which sovereign power is formally divided between a central authority and a number of constituent regions so that each region retains some degree of control over its internal affairs.
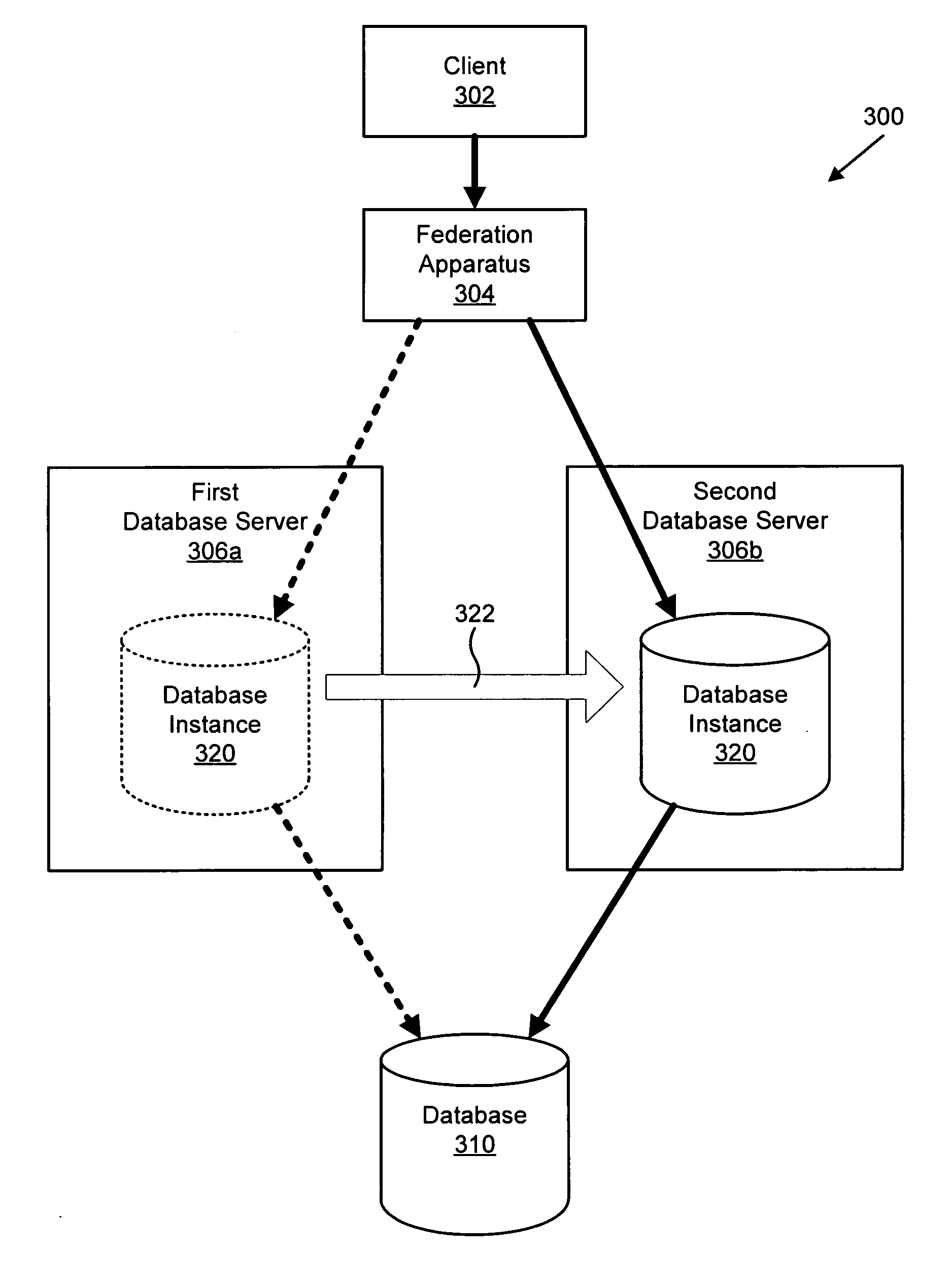
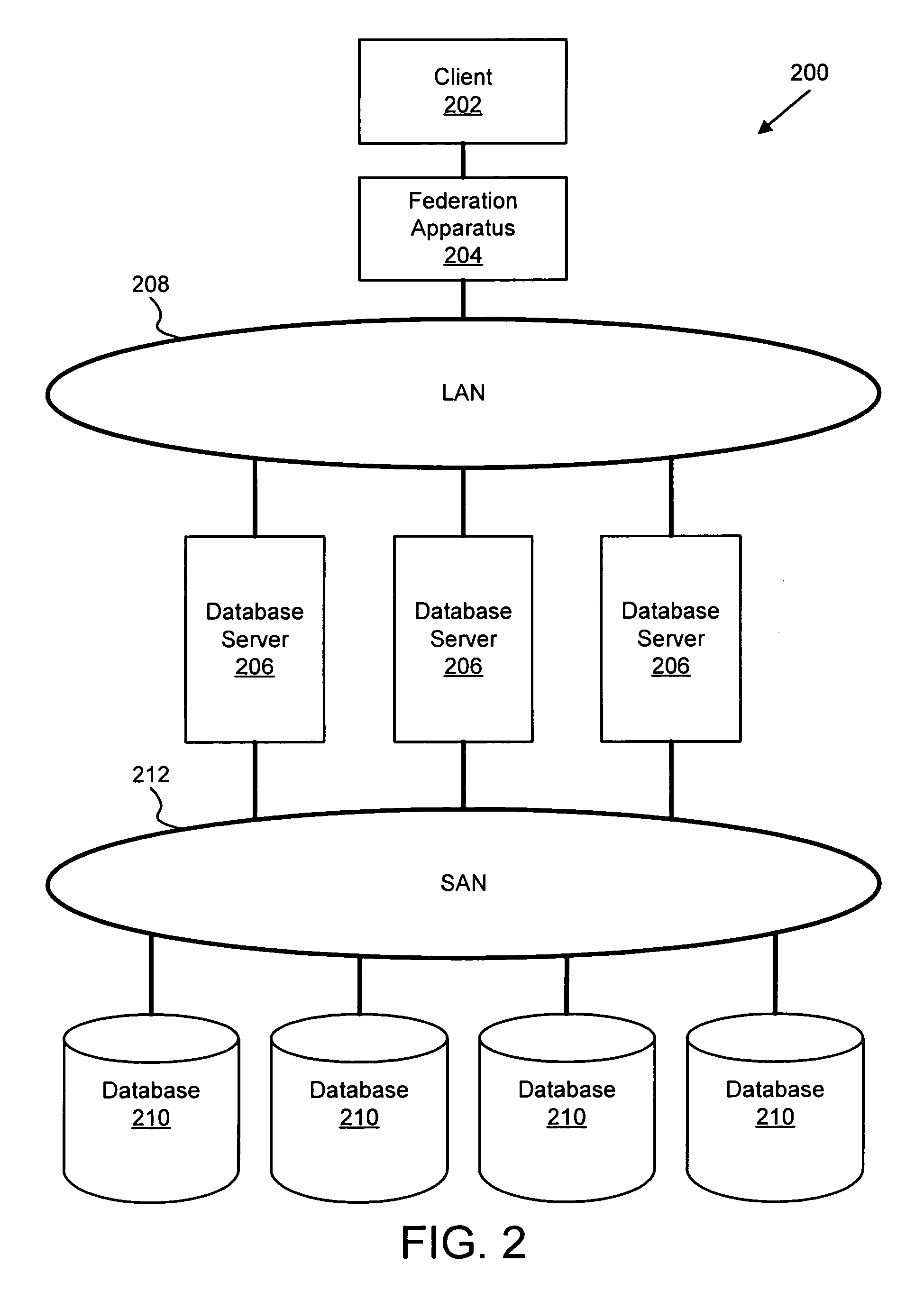
Apparatus, system, and method for database provisioning
ActiveUS20060136448A1Overcomes shortcomingDigital data information retrievalData processing applicationsApplication softwareClient-side
An apparatus, system, and method are disclosed for provisioning database resource within a grid database system. The federation apparatus includes an analysis module and a provision module. The analysis module analyzes a data query stream from an application to a database instance and determines if the data query stream exhibits a predetermined performance attribute. The provision module provisions a database resource in response to a determination that the data query stream exhibits the predetermined performance attribute. The provisioned database resource may be a database instance or a cache. The provisioning of the new database resource advantageously is substantially transparent to a client on the database system.
Owner:TWITTER INC
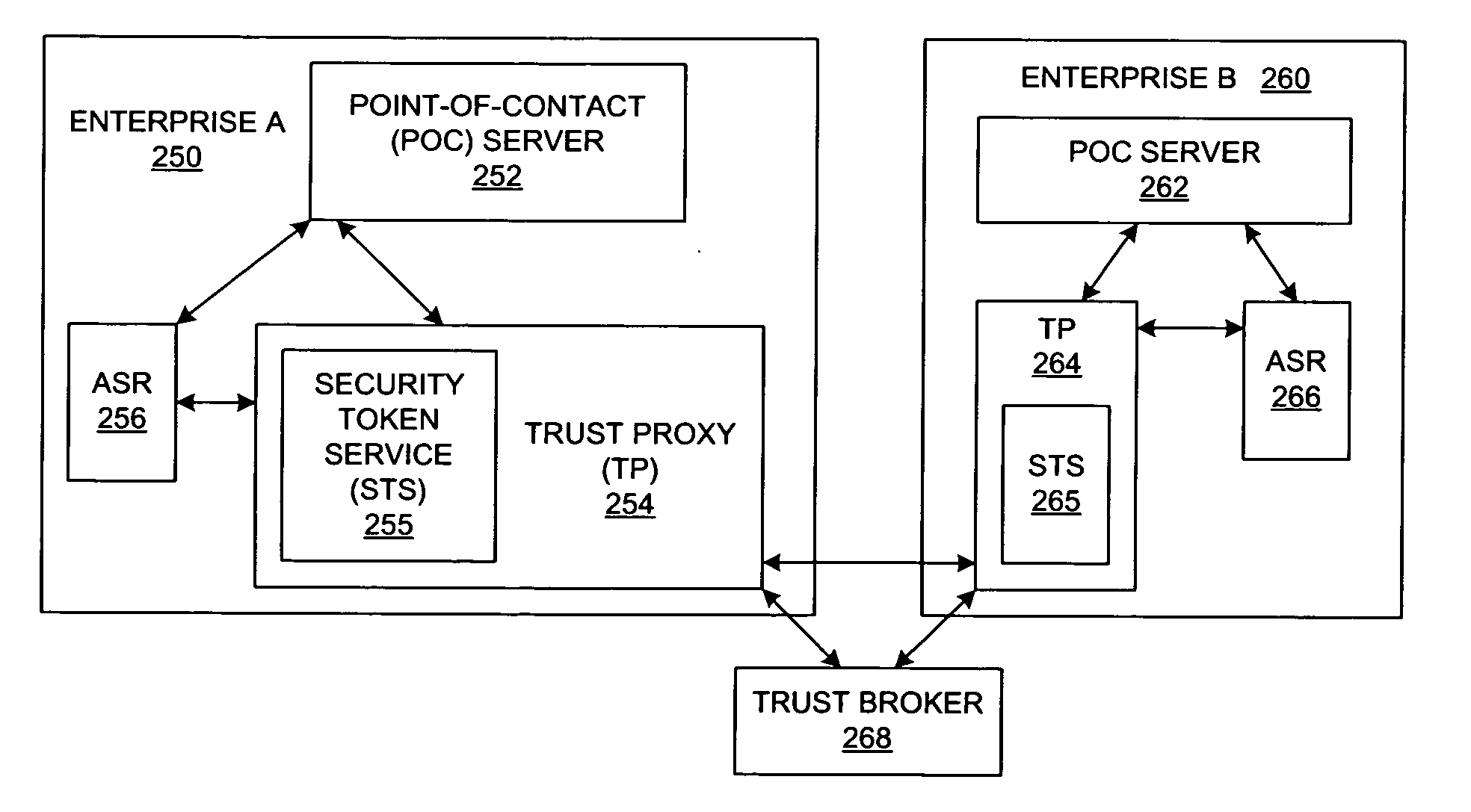
Method and system for federated provisioning
ActiveUS20060021019A1Digital data processing detailsUser identity/authority verificationInternet privacyTrust relationship
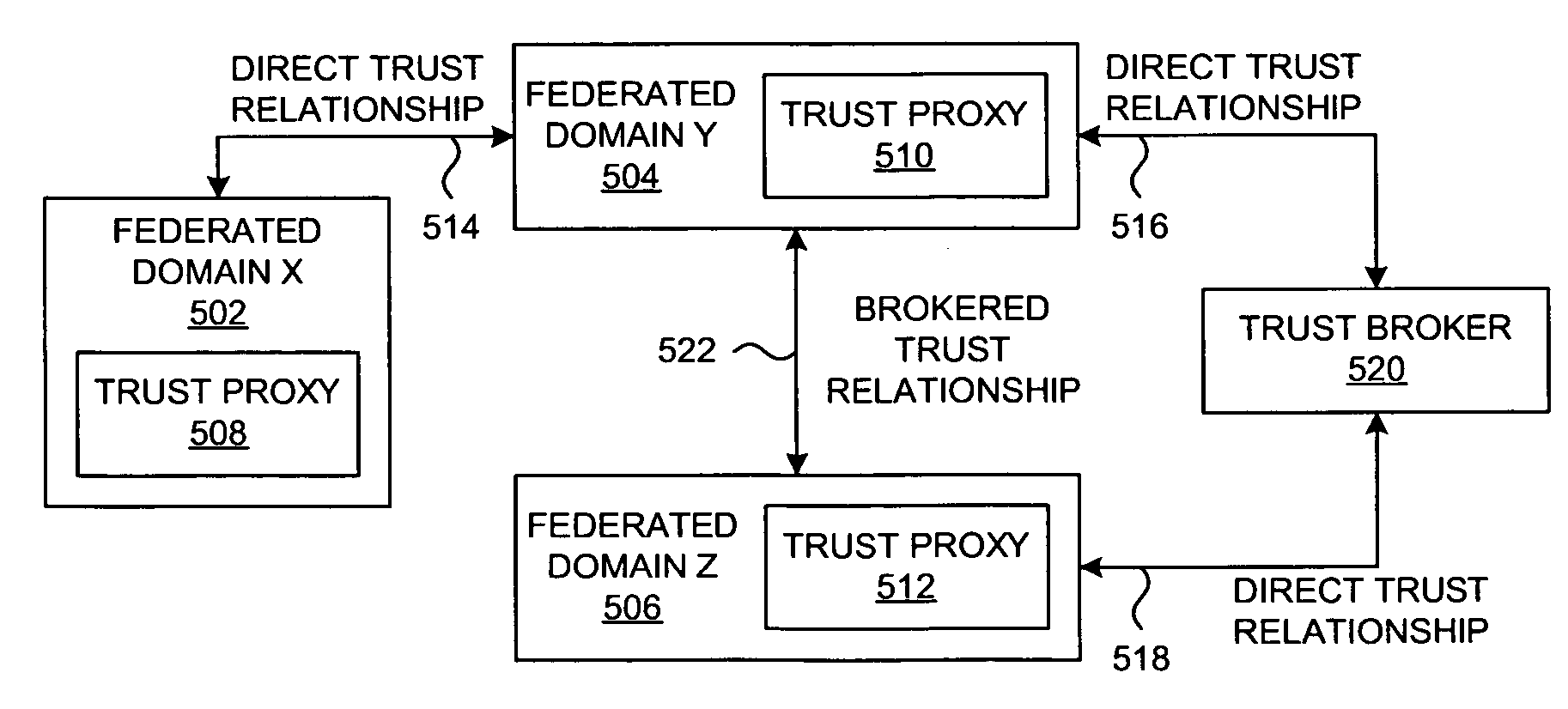
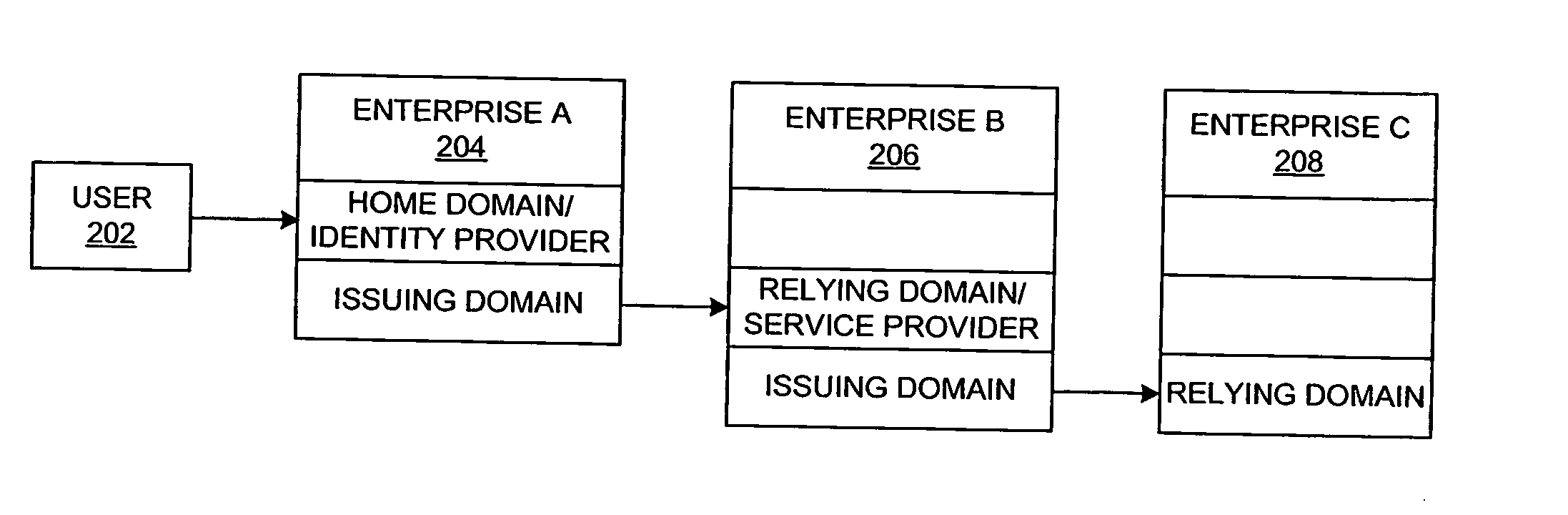
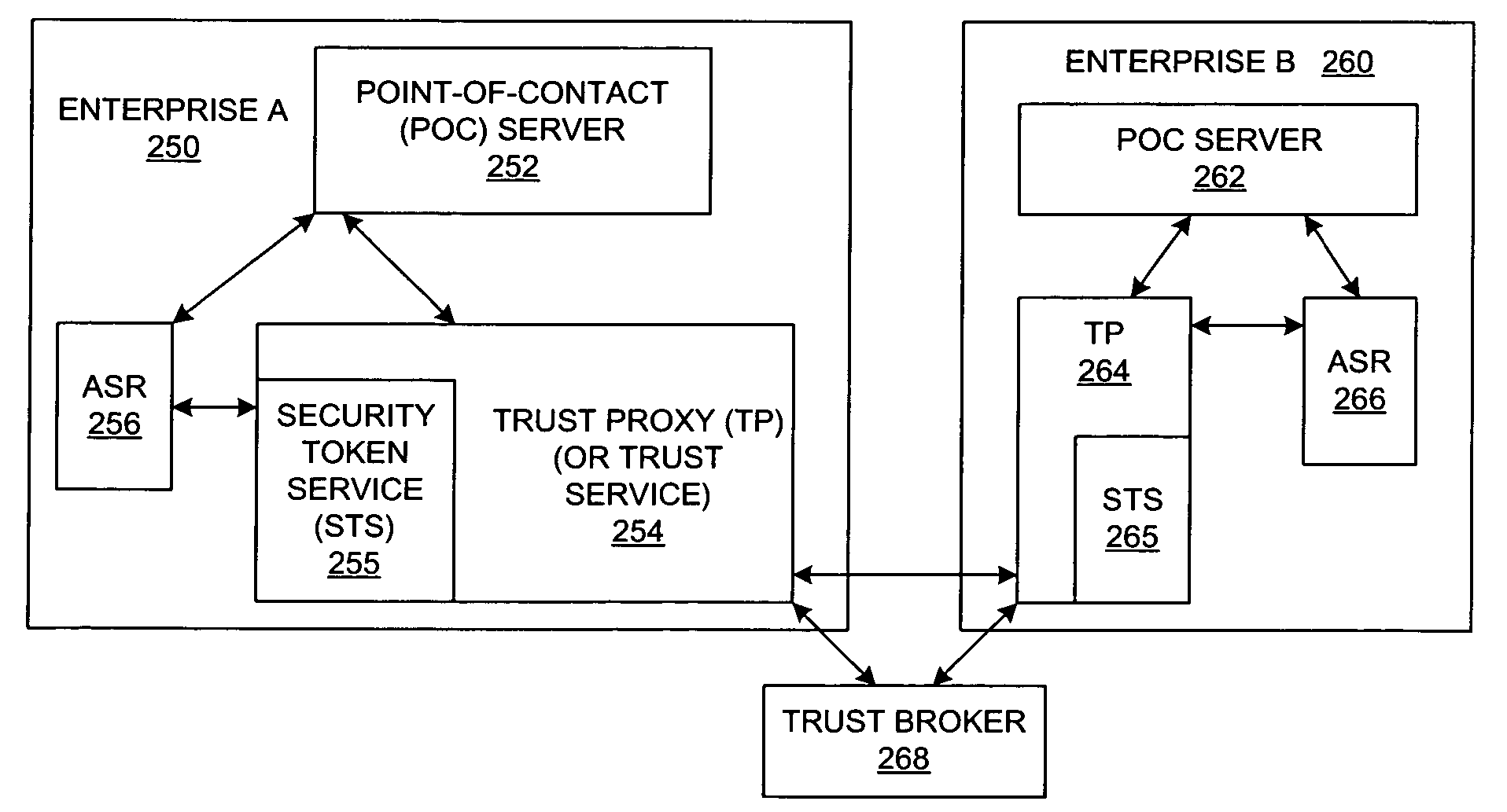
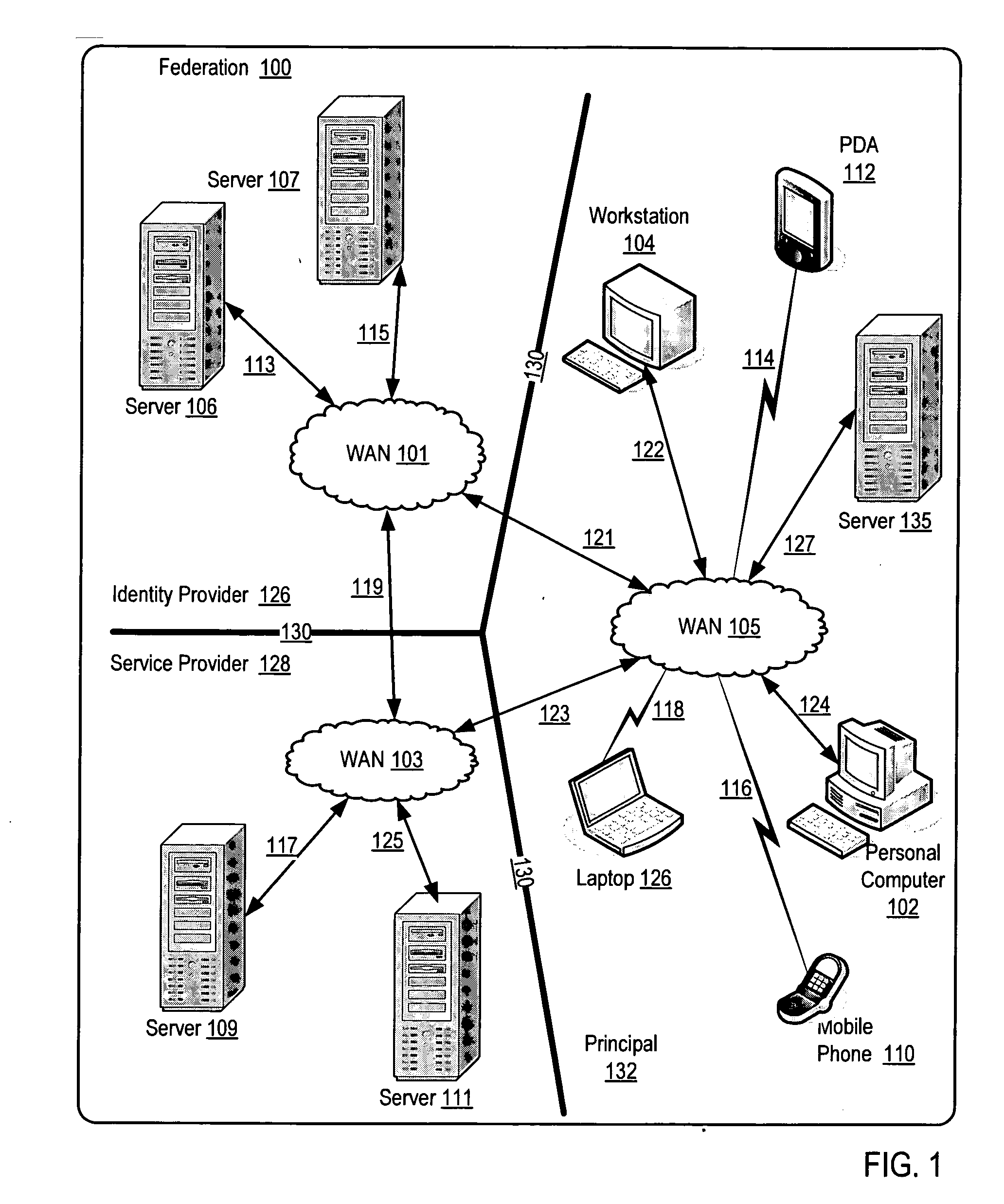
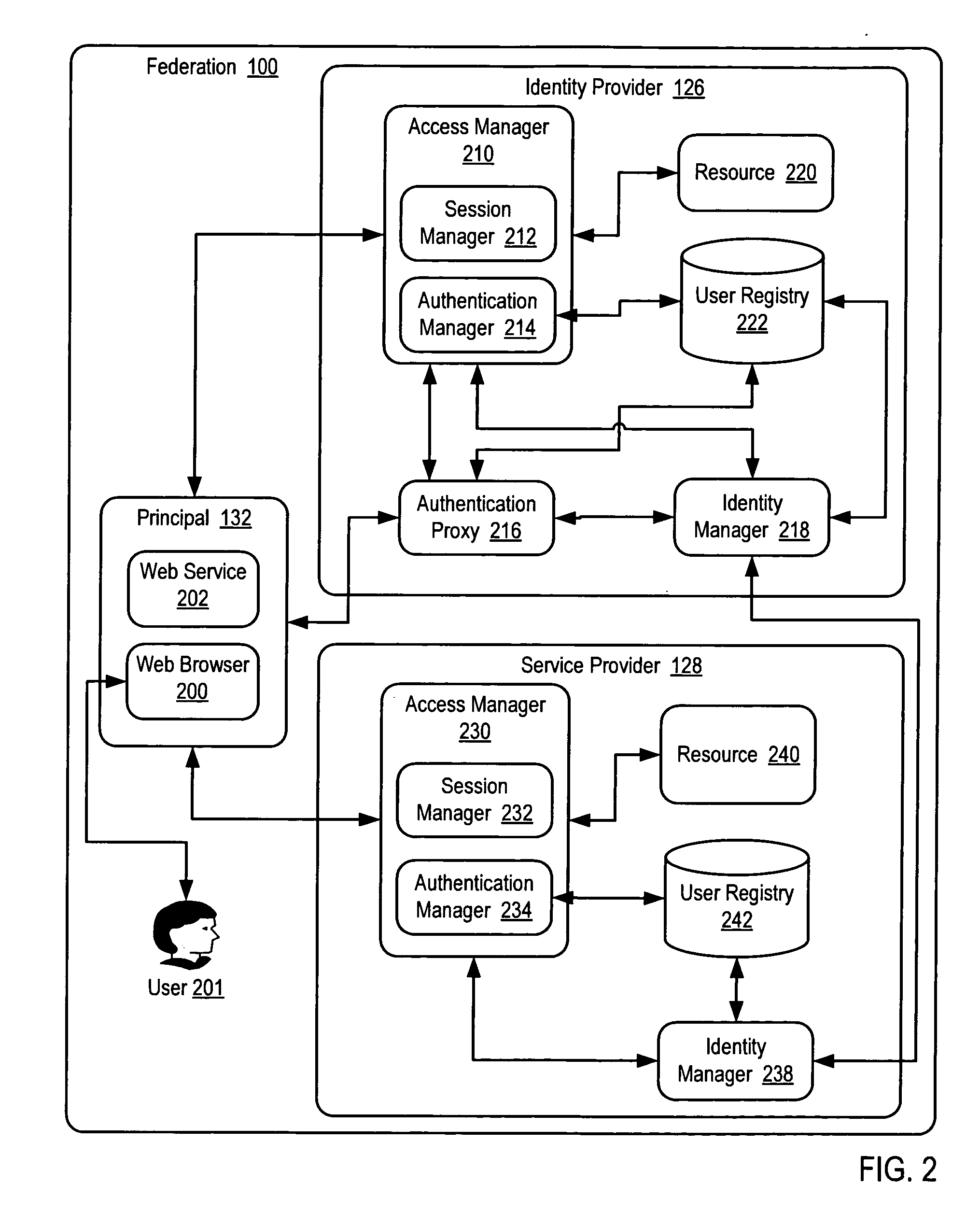
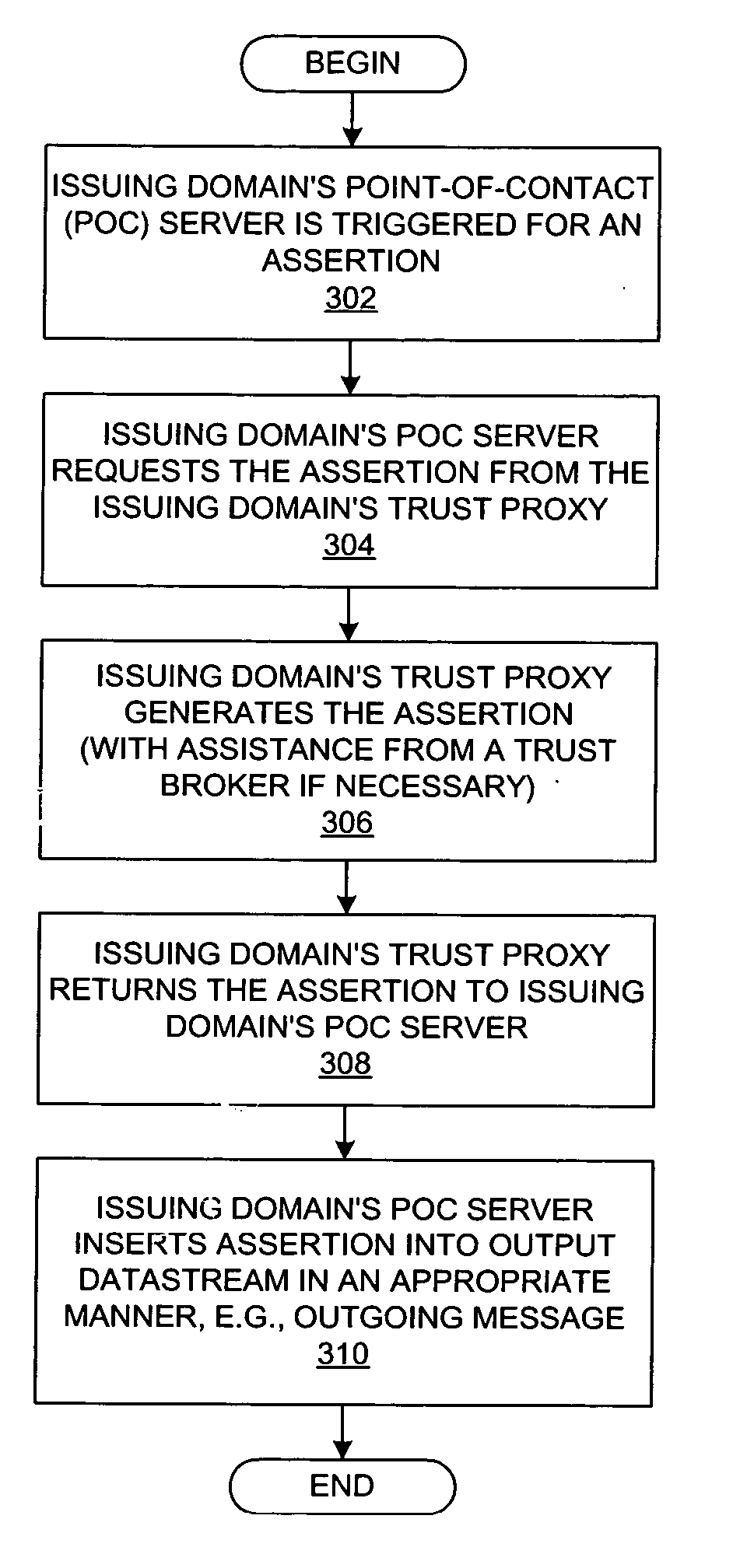
A method and a system are presented in which federated domains interact within a federated environment. Domains within a federation can initiate federated single-sign-on operations for a user at other federated domains. A point-of-contact server within a domain relies upon a trust proxy within the domain to manage trust relationships between the domain and the federation. Trust proxies interpret assertions from other federated domains as necessary. Trust proxies may have a trust relationship with one or more trust brokers, and a trust proxy may rely upon a trust broker for assistance in interpreting assertions. When a user is provisioned at a particular federated domain, the federated domain can provision the user to other federated domains within the federated environment. A provision operation may include creating or deleting an account for a user, pushing updated user account information including attributes, and requesting updates on account information including attributes.
Owner:SERVICENOW INC
Systems and methods for enabling trust in a federated collaboration
ActiveUS20060129817A1Ensure complianceDigital data processing detailsUser identity/authority verificationThird partySuccessful completion
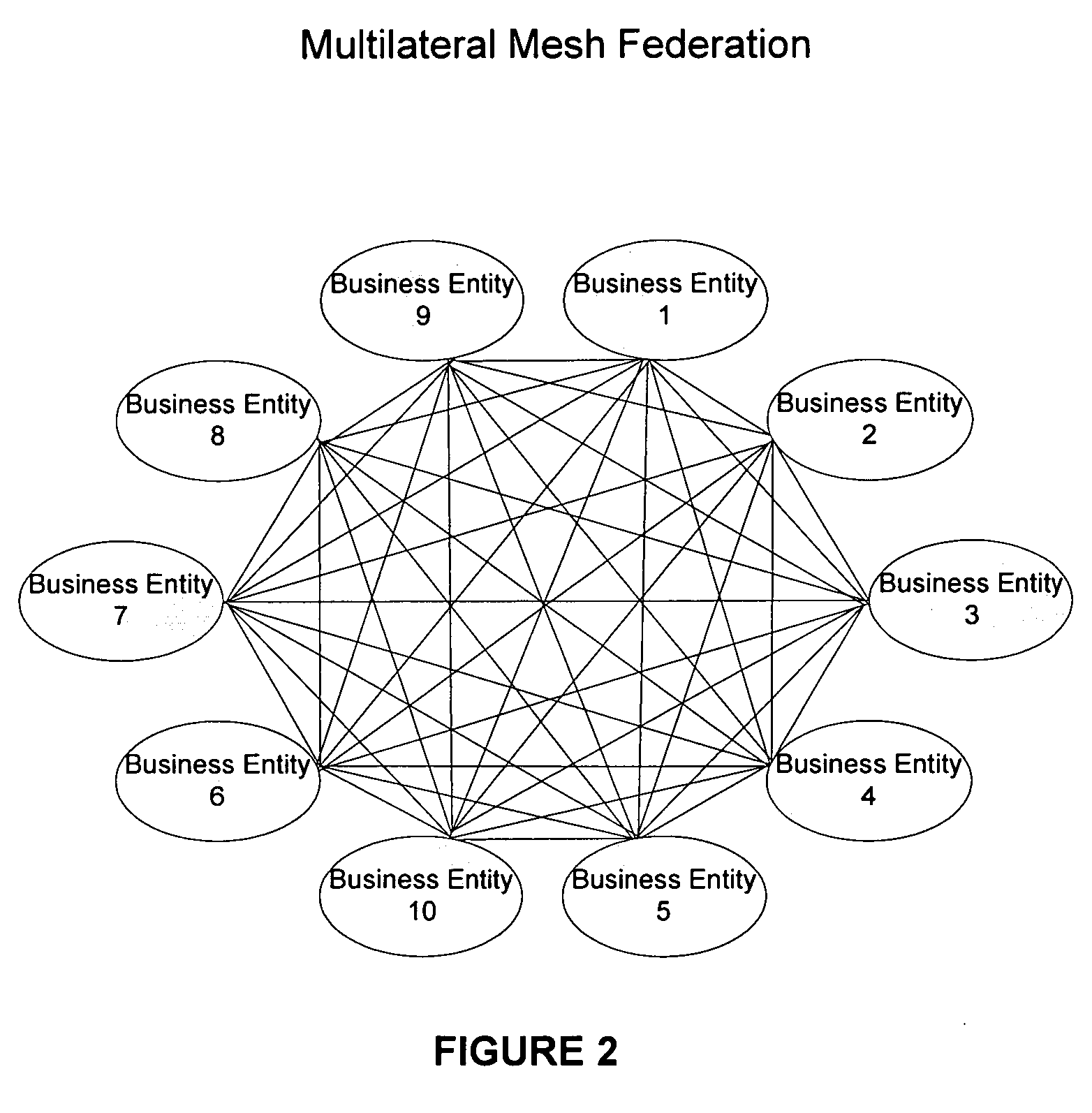
Systems and methods consistent with the present invention enable explicit and multilateral trust across a community of federated servers via a network. A trusted third party establishes a framework of policies and procedures governing a federation. Organizations joining the federation submit to an audit process of internal policies and procedures to ensure compliance with the policies and procedures of the federation. Upon successful completion of an audit, an organization may receive a digital certificate containing the digital public key of the organization and indicating approval of the trusted third party. The organization may then use the associated digital private key for signing security assertions associated with a request for resources from another federation service provider. The service provider may trust the assertion from the organization based on trust placed in trusted third party by the service provider and the trust placed in the organization by the trusted third party.
Owner:EXOSTAR CORP
Secure network commercial transactions
InactiveUS20060235795A1Reduce the burden onSimpler and more secure online commercial transactions frameworkFinanceBuying/selling/leasing transactionsPaymentSecure communication
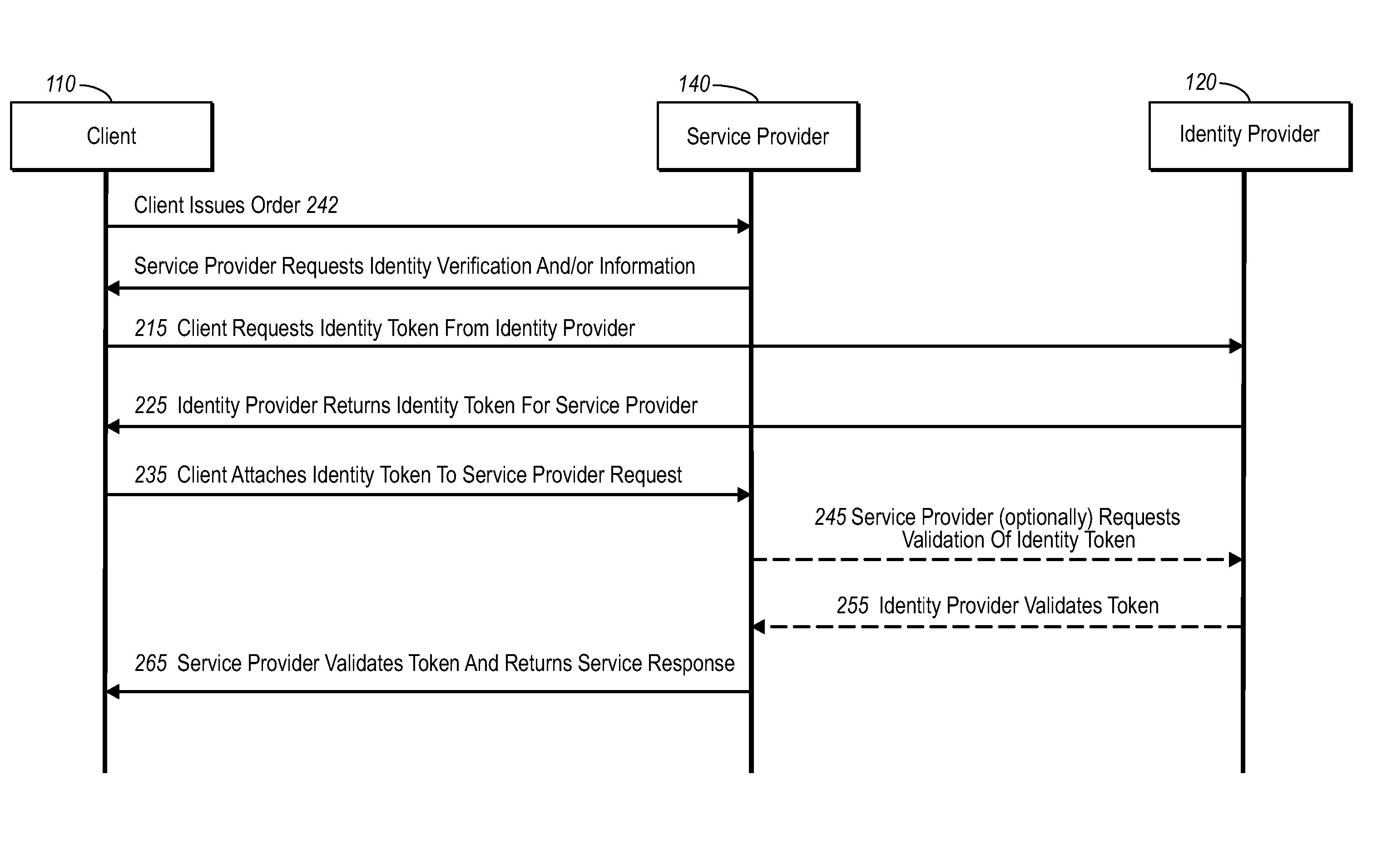
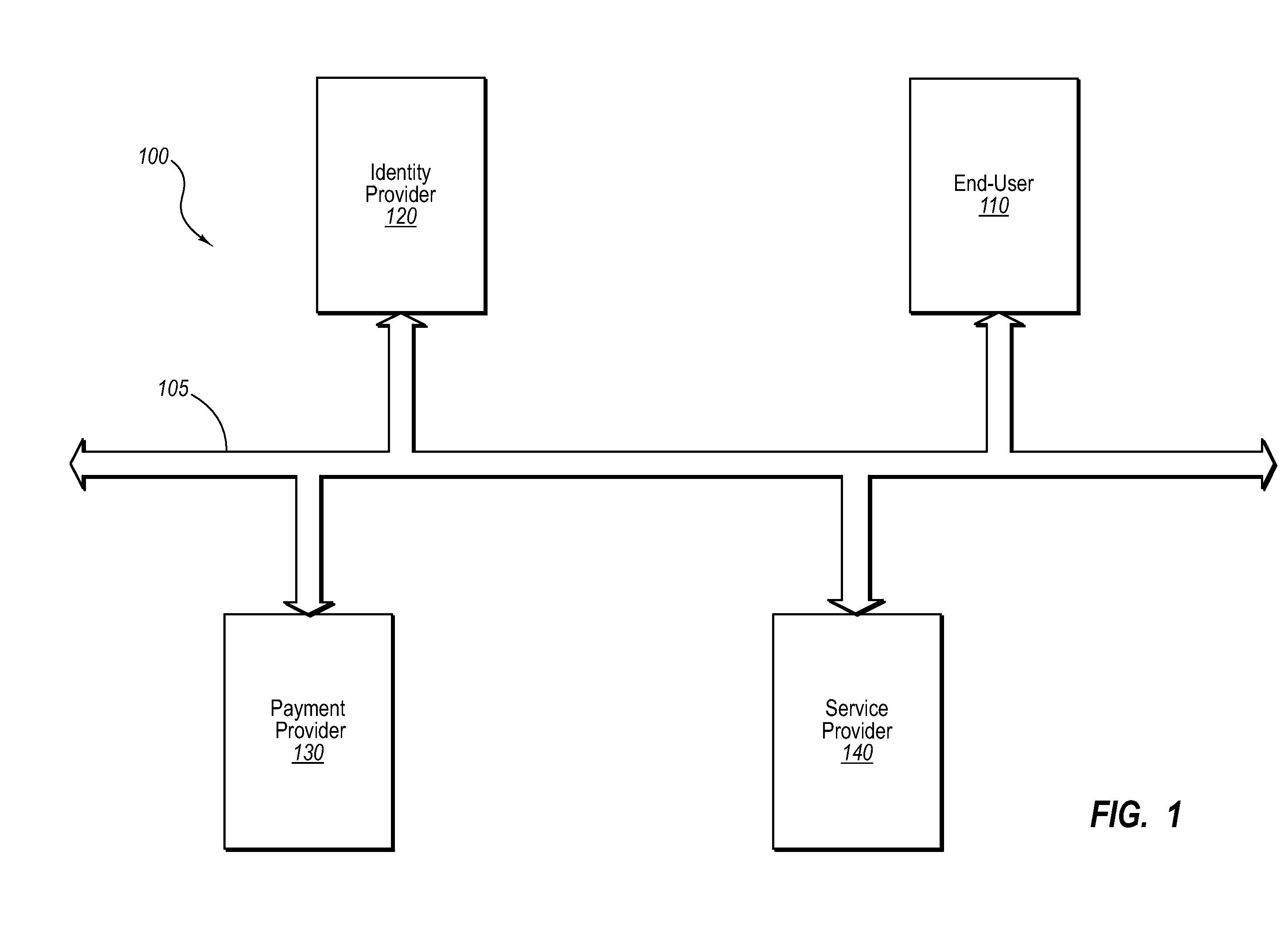
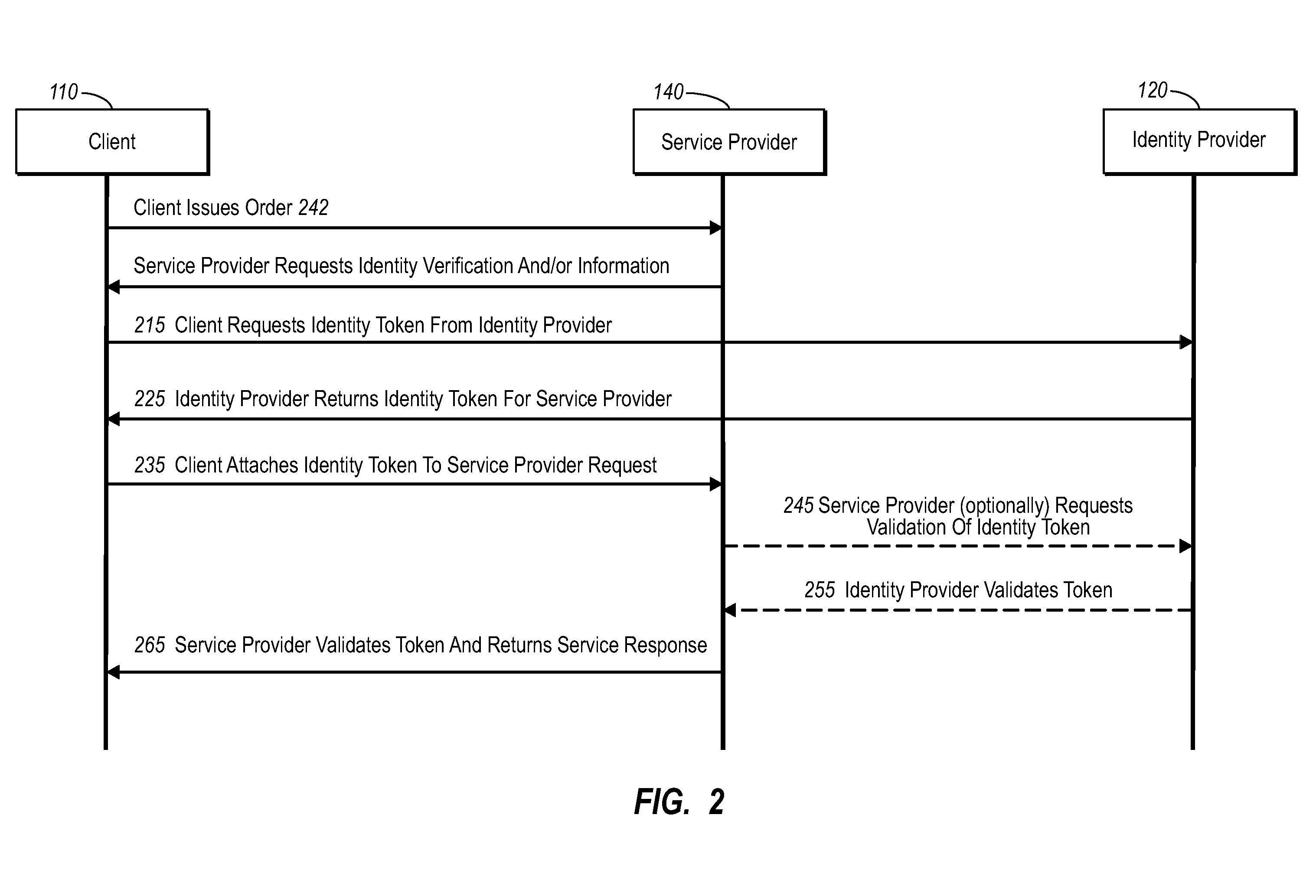
Current embodiments provide for authorization and payment of an online commercial transaction between a purchaser and a merchant including verification of an identity of the purchaser and verification of an ability of the purchaser to pay for the transaction, where the identity provider and the payment provider are often different network entities. Other embodiments also provide for protocols, computing systems, and other mechanisms that allow for identity and payment authentication using a mobile module, which establishes single or multilevel security over an untrusted network (e.g., the Internet). Still other embodiments also provide for a three-way secure communication between a merchant, consumer, and payment provider such that sensitive account information is opaque to the merchant, yet the merchant is sufficiently confident of the consumer's ability to pay for requested purchases. In yet another embodiment, electronic billing information is used for authorization, auditing, payment federation, and other purposes.
Owner:MICROSOFT TECH LICENSING LLC
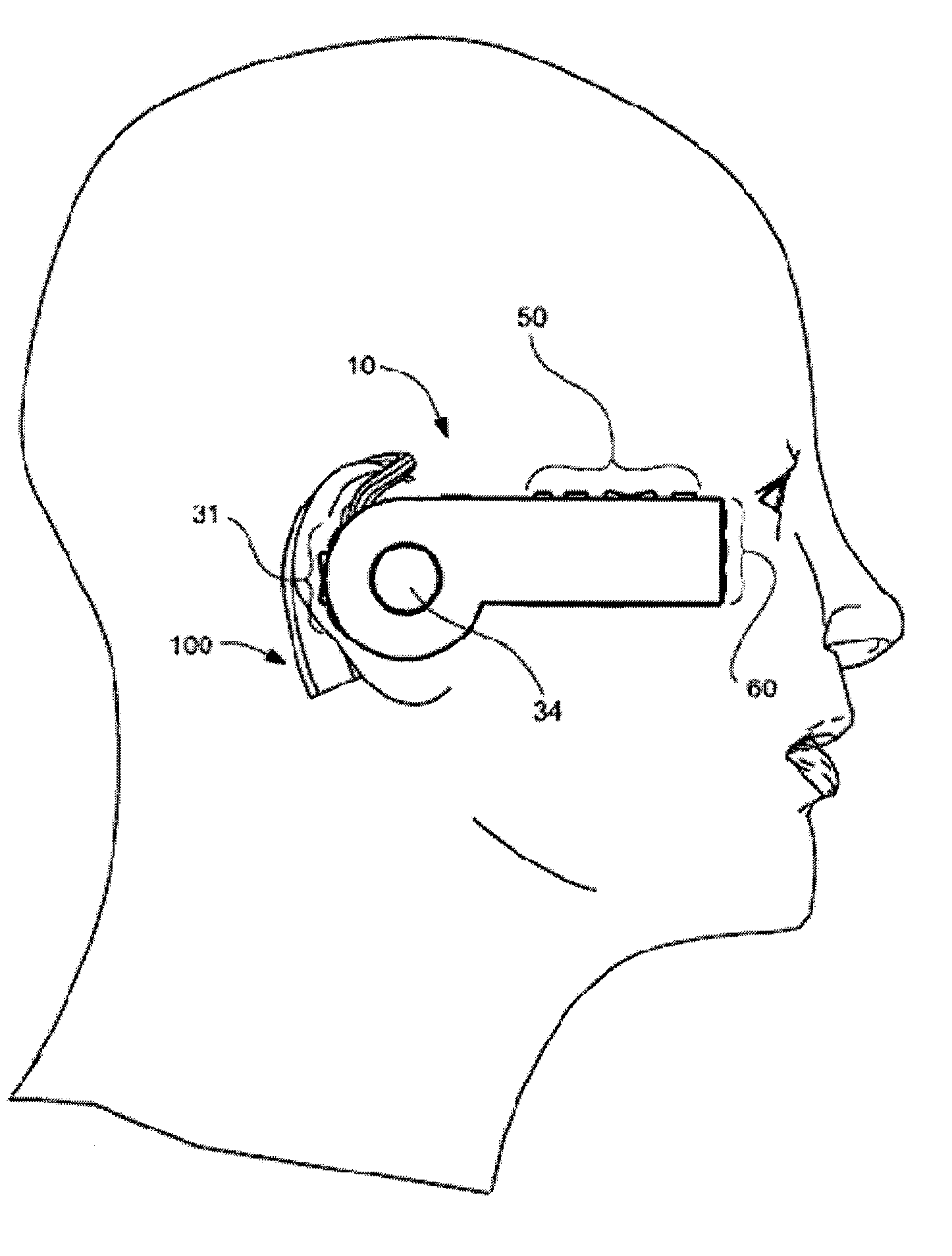
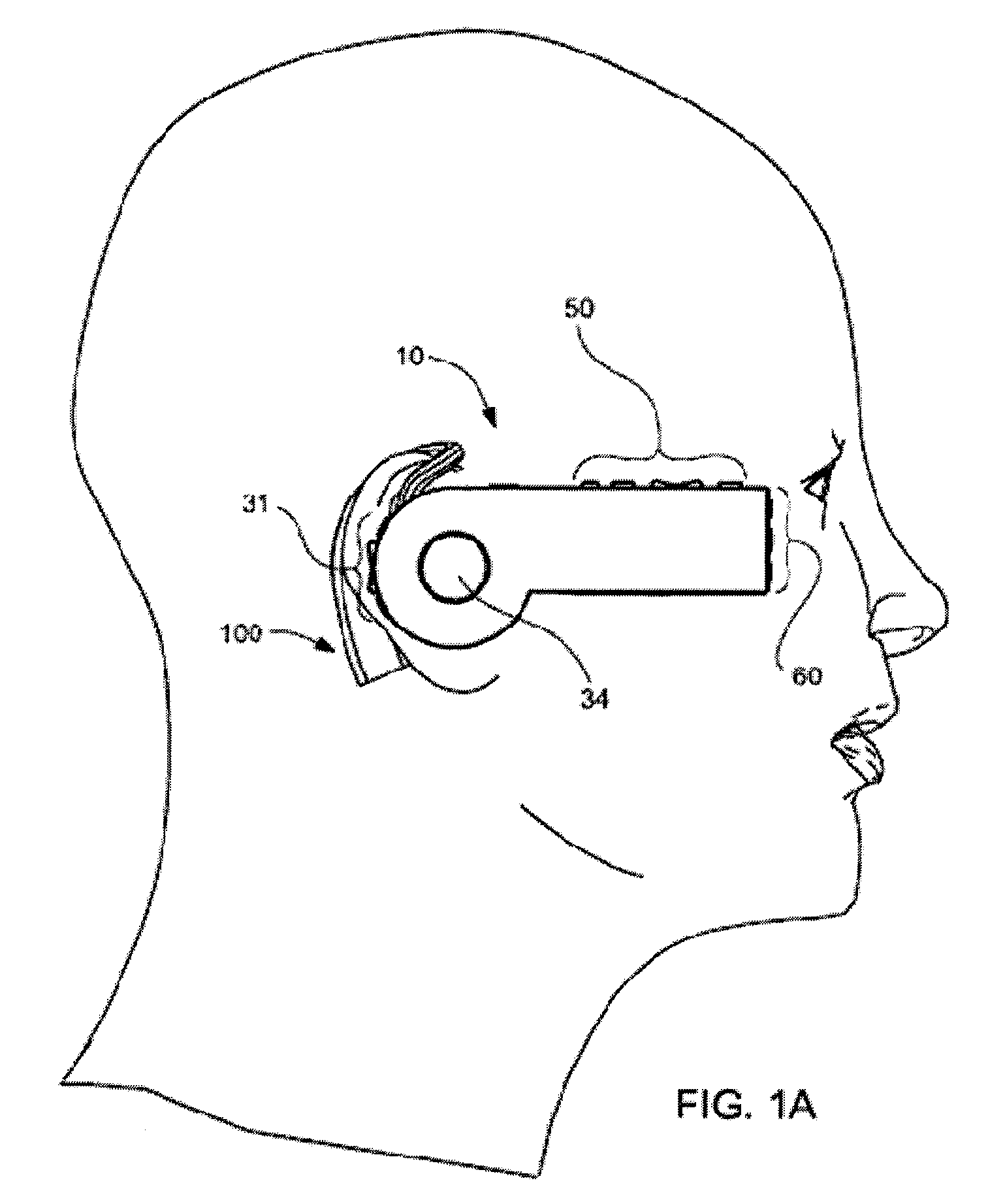
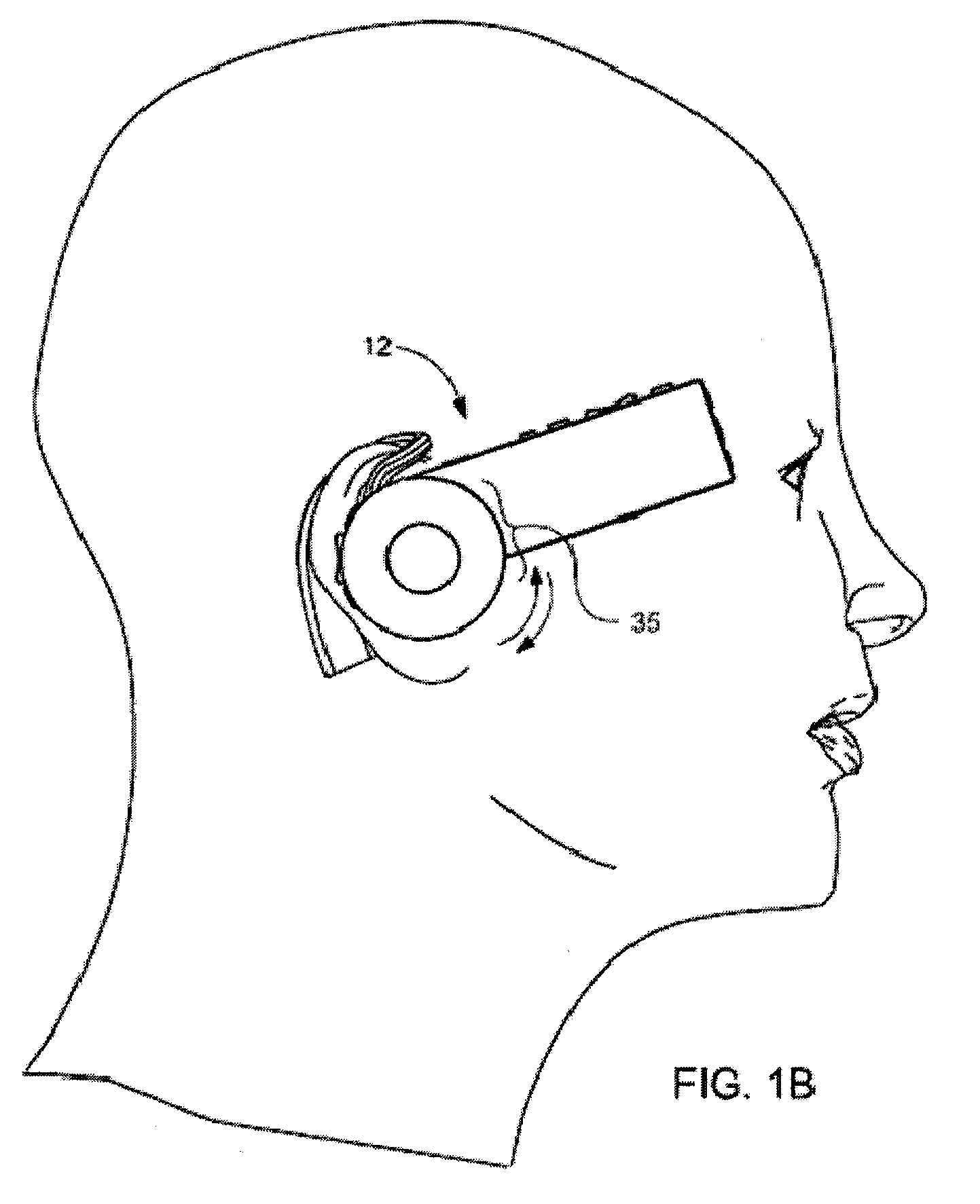
Headset-Based Telecommunications Platform
ActiveUS20100245585A1Extend battery lifeTelevision system detailsOptical rangefindersData streamPeer-to-peer
A hands-free wireless wearable GPS enabled video camera and audio-video communications headset, mobile phone and personal media player, capable of real-time two-way and multi-feed wireless voice, data and audio-video streaming, telecommunications, and teleconferencing, coordinated applications, and shared functionality between one or more wirelessly networked headsets or other paired or networked wired or wireless devices and optimized device and data management over multiple wired and wireless network connections. The headset can operate in concert with one or more wired or wireless devices as a paired accessory, as an autonomous hands-free wide area, metro or local area and personal area wireless audio-video communications and multimedia device and / or as a wearable docking station, hot spot and wireless router supporting direct connect multi-device ad-hoc virtual private networking (VPN). The headset has built-in intelligence to choose amongst available network protocols while supporting a variety of onboard, and remote operational controls including a retractable monocular viewfinder display for real time hands-free viewing of captured or received video feed and a duplex data-streaming platform supporting multi-channel communications and optimized data management within the device, within a managed or autonomous federation of devices or other peer-to-peer network configuration.
Owner:EYECAM INC
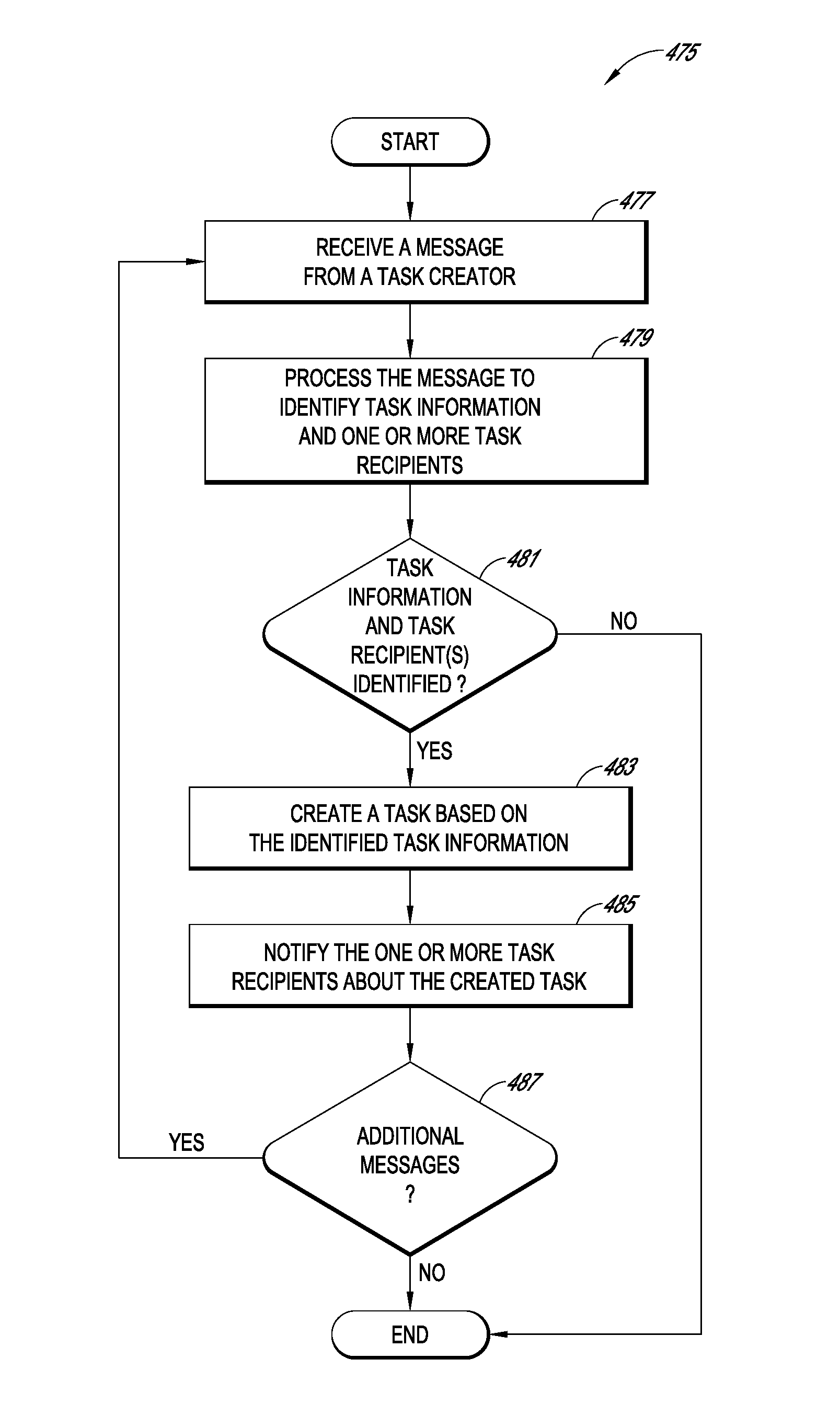
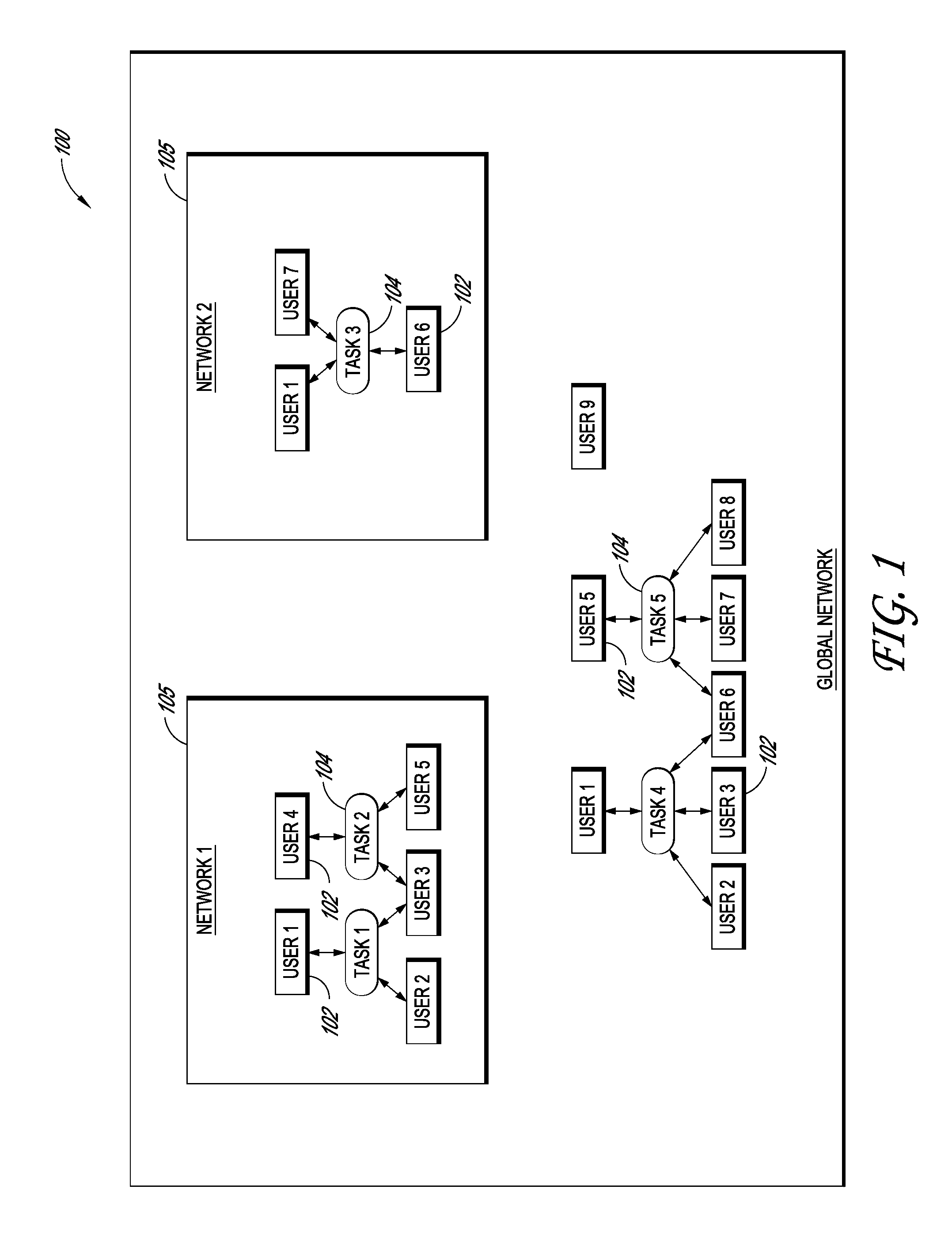
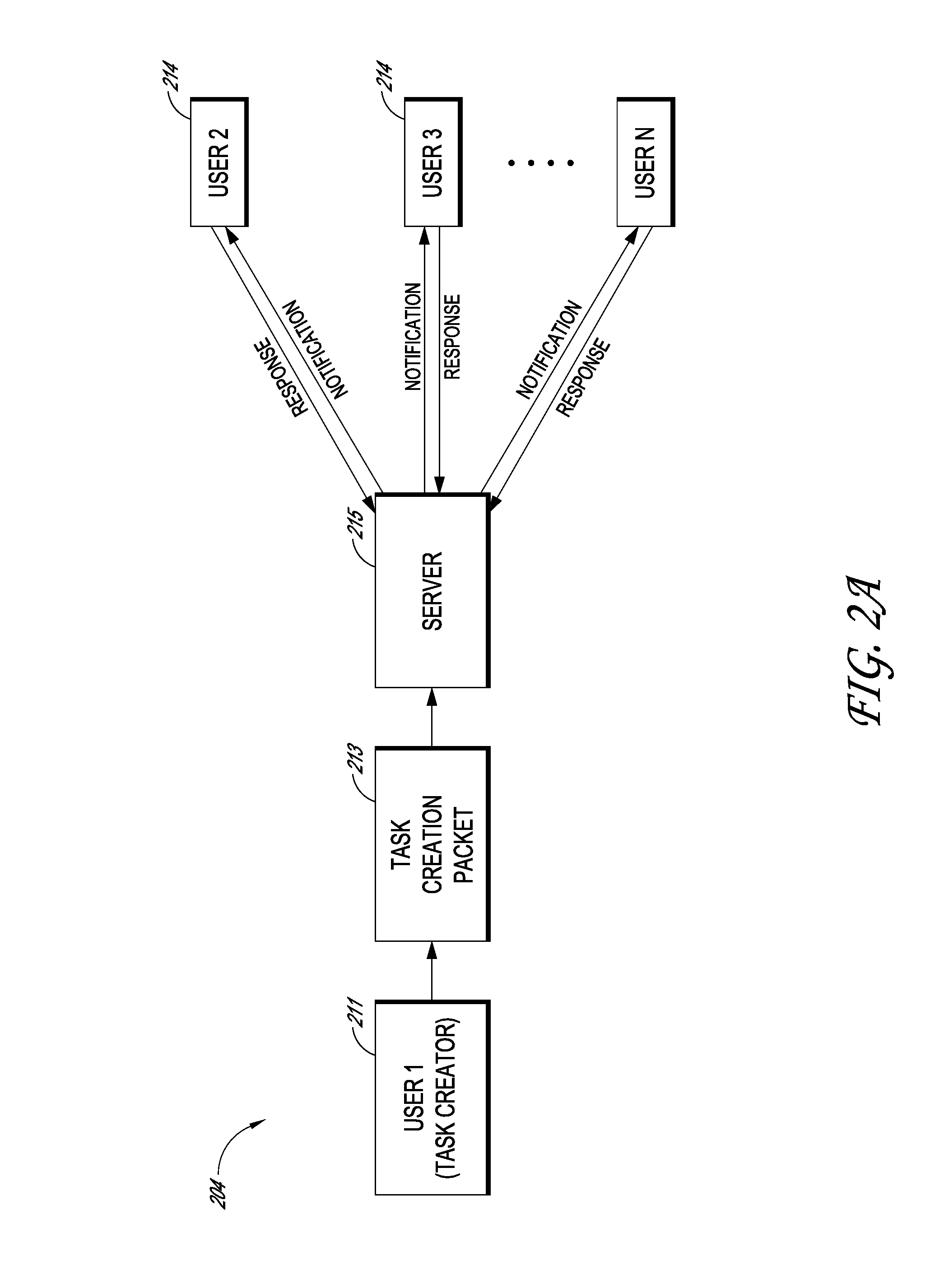
Systems and methods for creating and sharing tasks
Systems and methods for creating and sharing tasks over one or more networks are disclosed. In one embodiment, a system comprises a message retrieval module configured to retrieve electronic messages and parse them into a plurality of tasks. The system can also include a task creation module configured to process the message to identify task information and one or more task recipients. The task creation module can also be configured to create a task based on the identified task information. A task notification module can be configured to notify the one or more task recipients about the created task. The system may also include a multi-layer network management module configured to organize the tasks and task participants into multiple networks and clouds and into a federation of clouds. The system can also include a task analytics module programmed to analyze the tasks performed by users of the system.
Owner:VMOSO INC
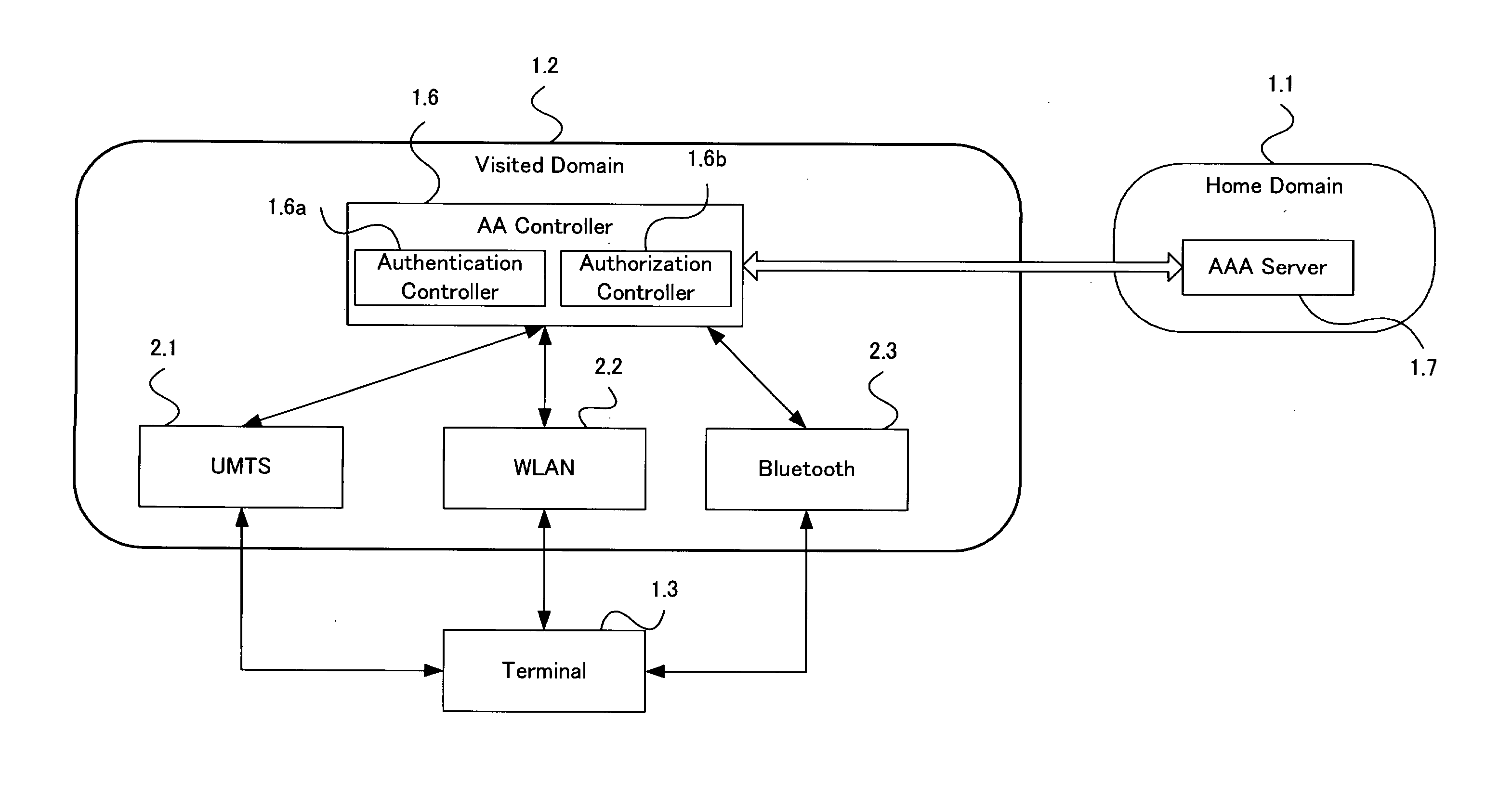
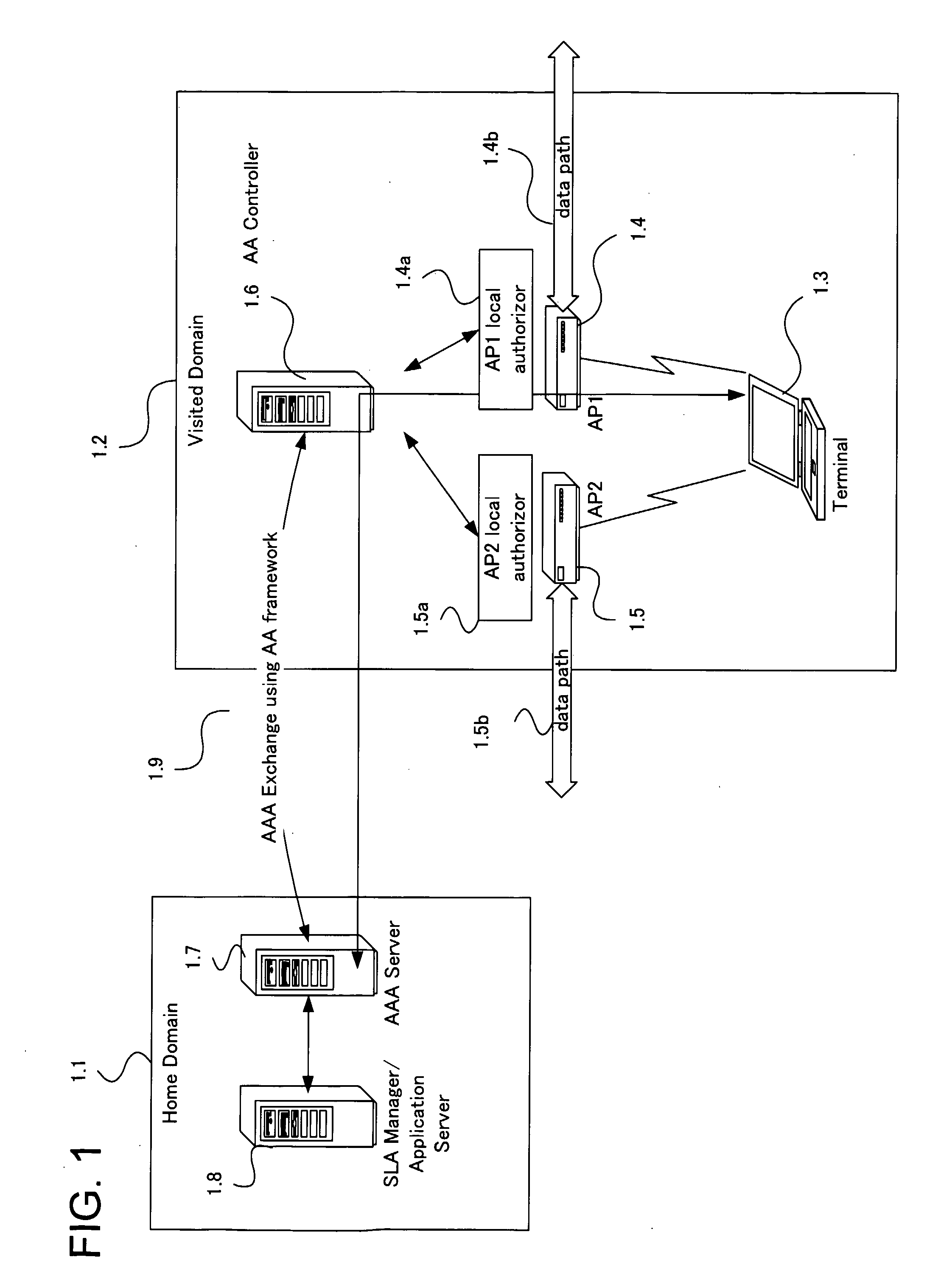
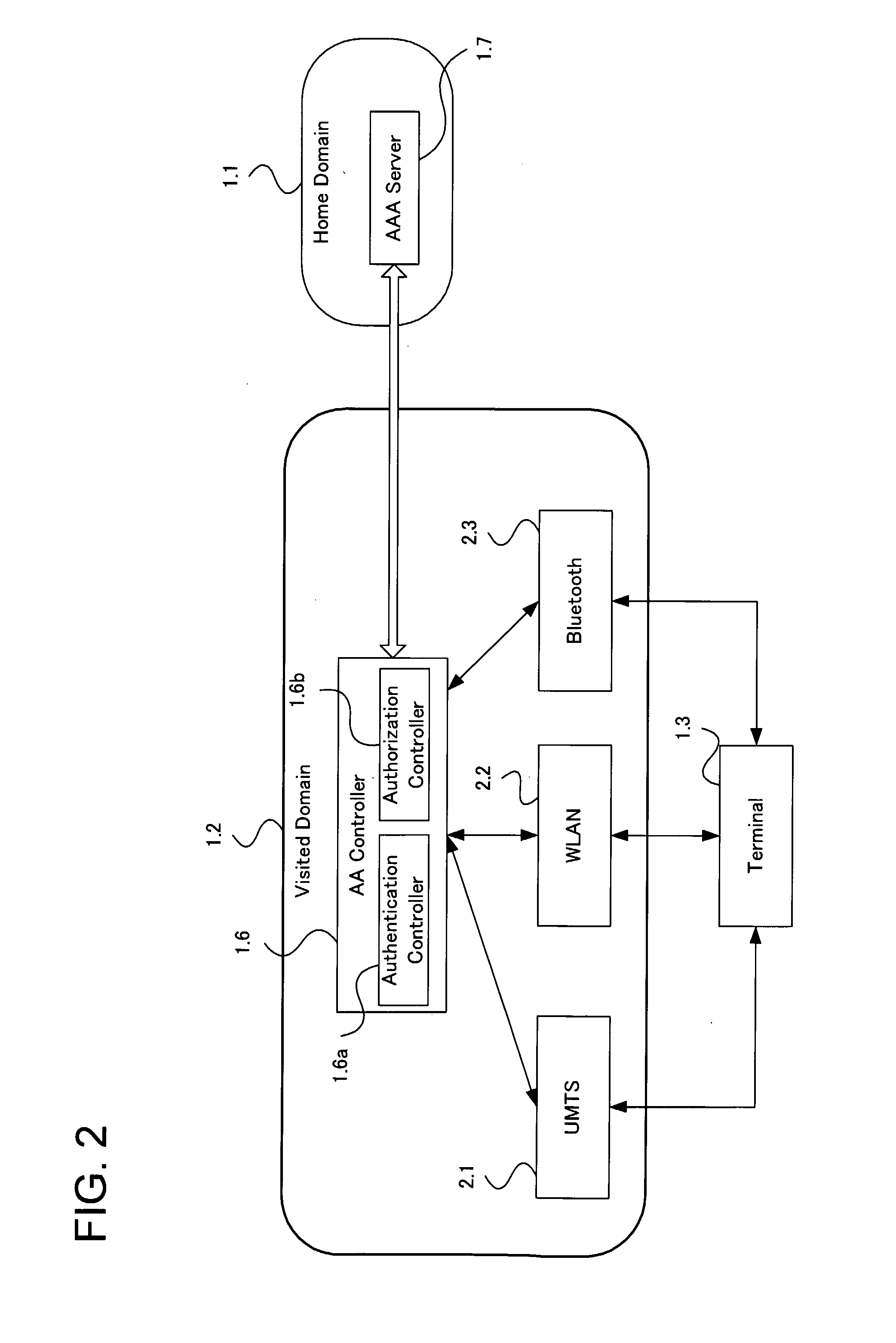
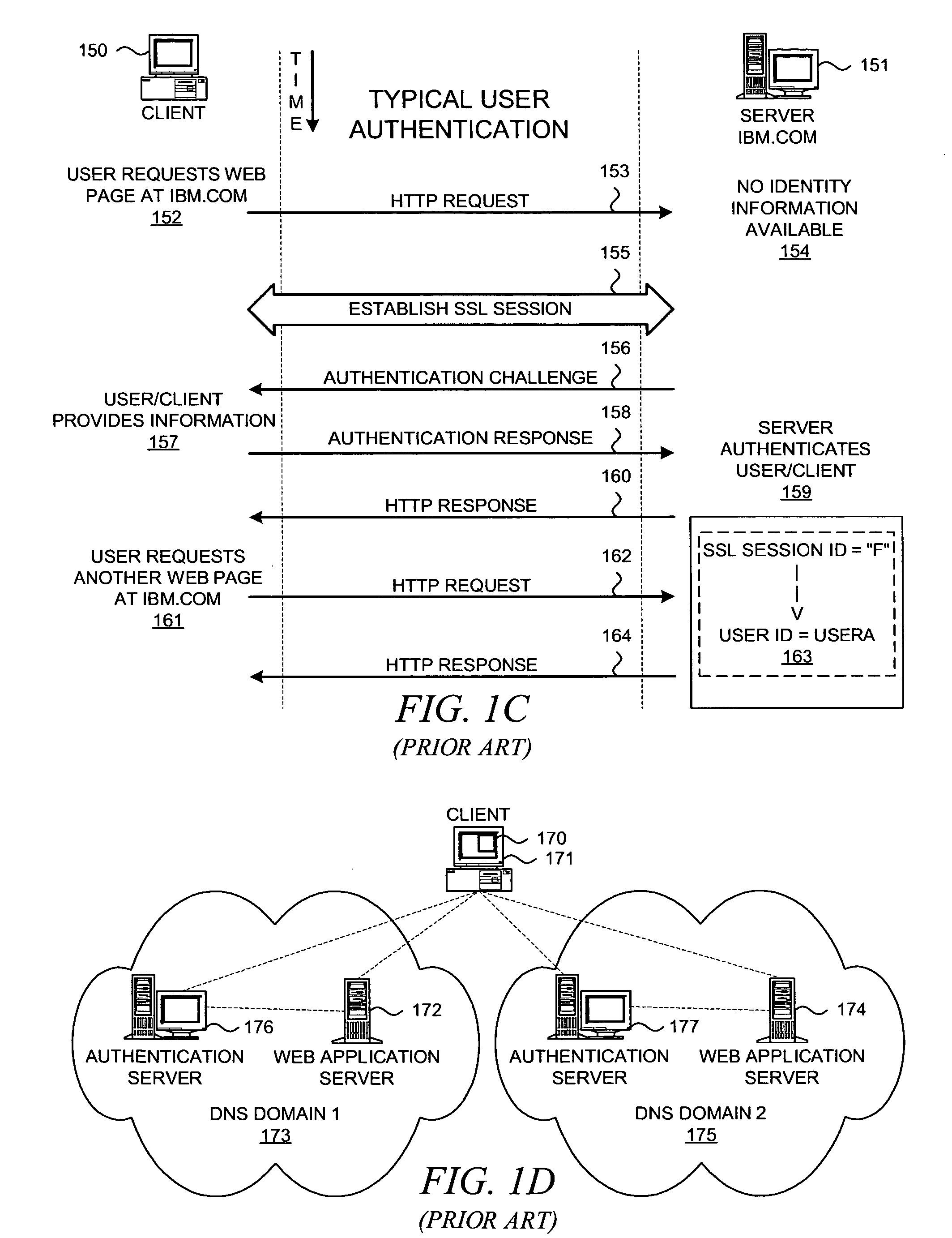
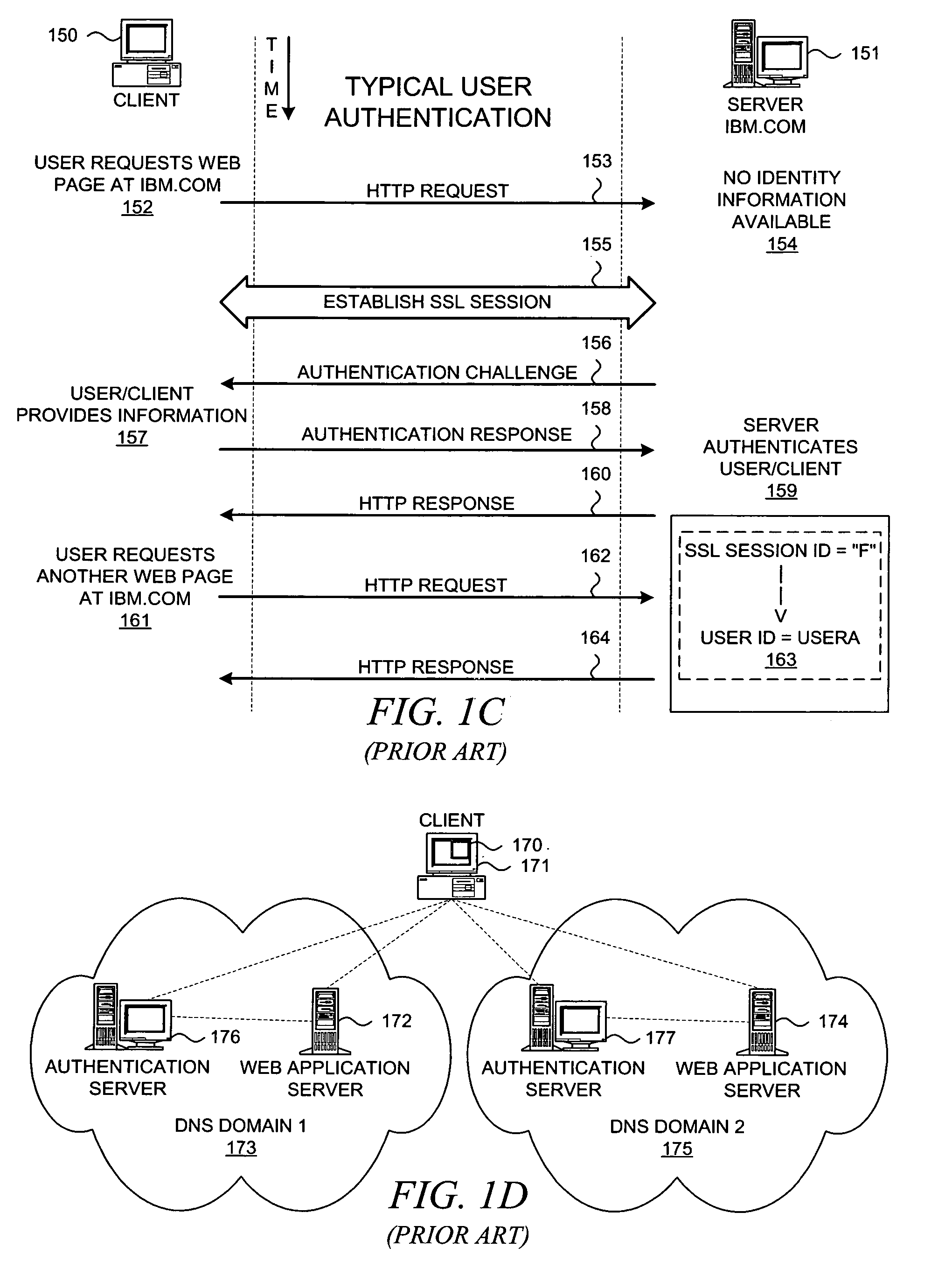
System And Method For Managing User Authentication And Service Authorization To Achieve Single-Sign-On To Access Multiple Network Interfaces
InactiveUS20080072301A1Timely controlShorten the timeDigital data processing detailsUser identity/authority verificationUser authenticationNetwork management
A single-sign-on to access multiple networks residing at multiple domains is disclosed. In particular the single-sign-on features refers to the authentication and the authorization process carried out among the different network administration domains so that the terminal using the end service need not explicitly initiate the authentication process each time it accesses a new service. This invention's single-sign-on feature can be extended for usage in a federated domain environment and non-federated domain environment. The non-federated domains are able to form an indirect federation chain through other domains in order to utilize this invention. Therefore discovery of intermediate domains to form a federation chain is also covered. The management of user credentials to allow a Visited Domain to perform authentication is also covered in this invention.
Owner:PANASONIC CORP
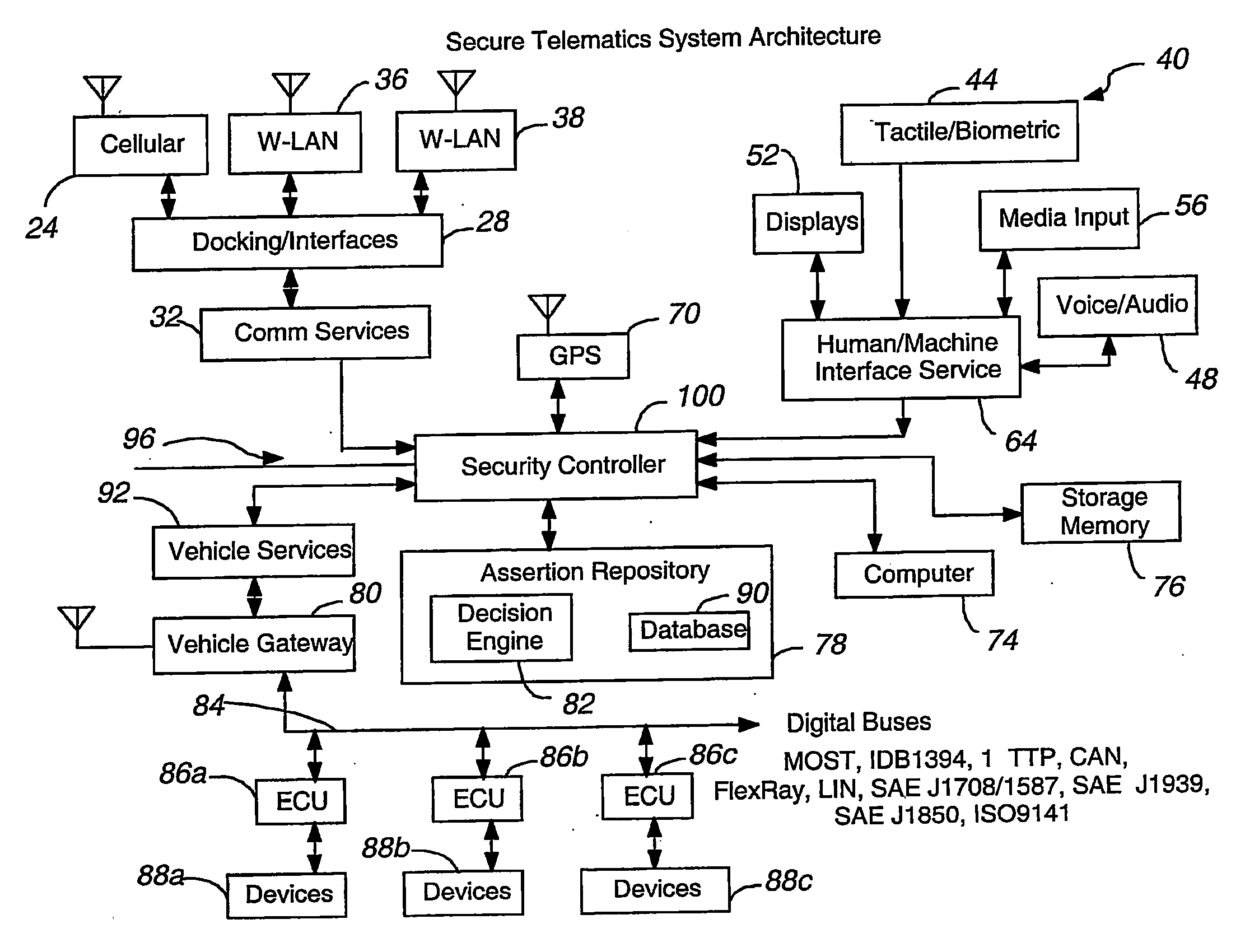
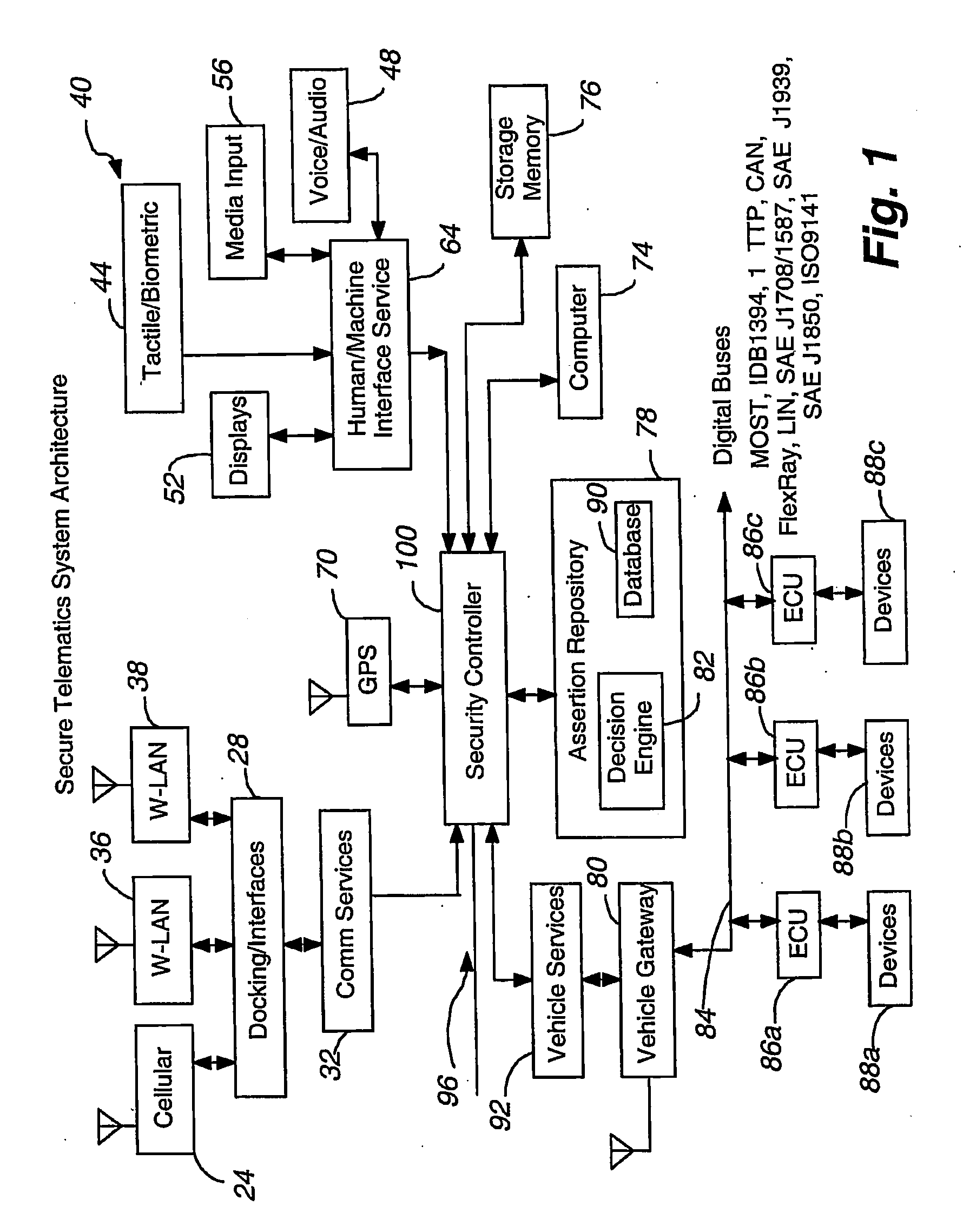
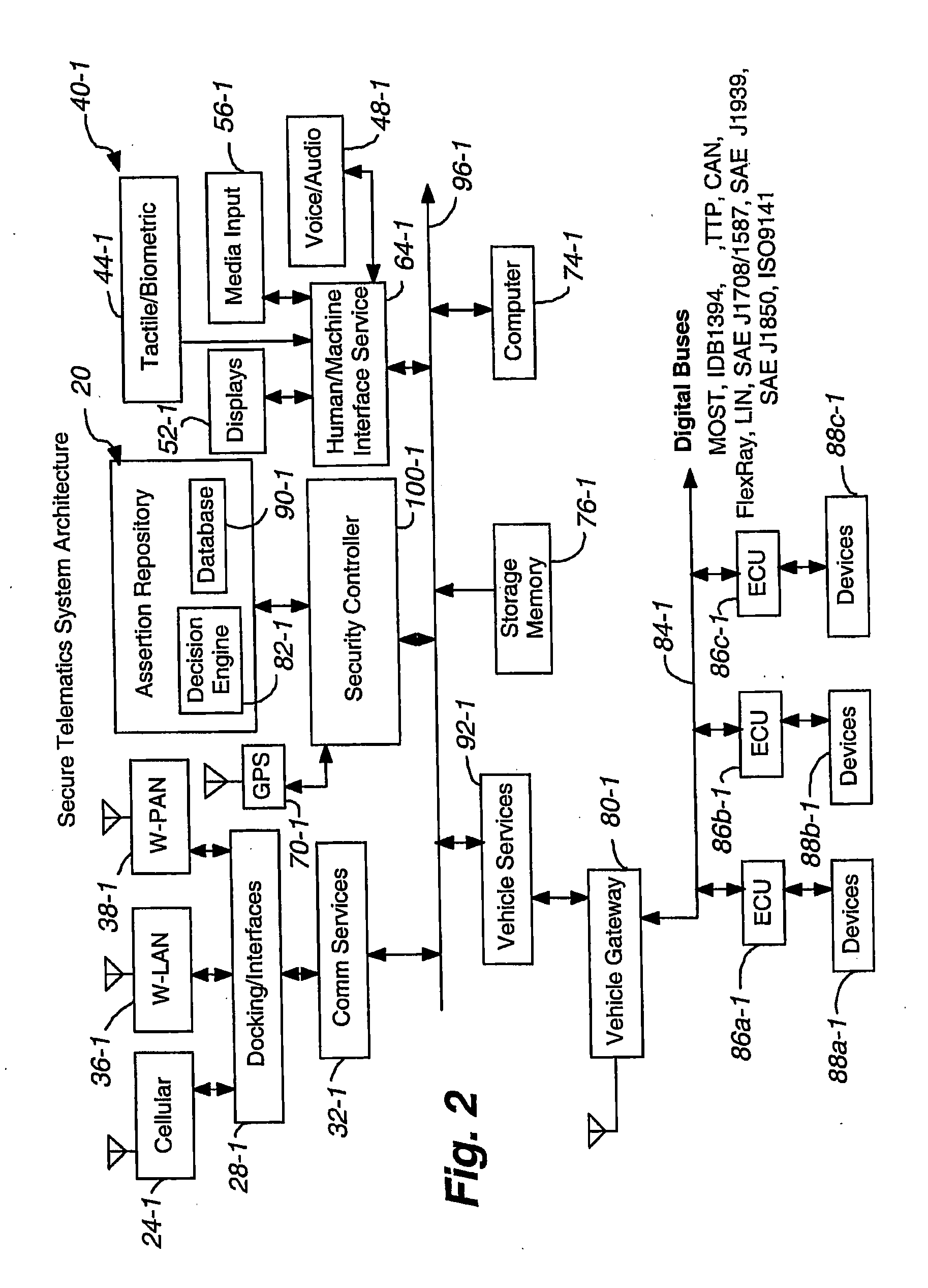
Secure telematics
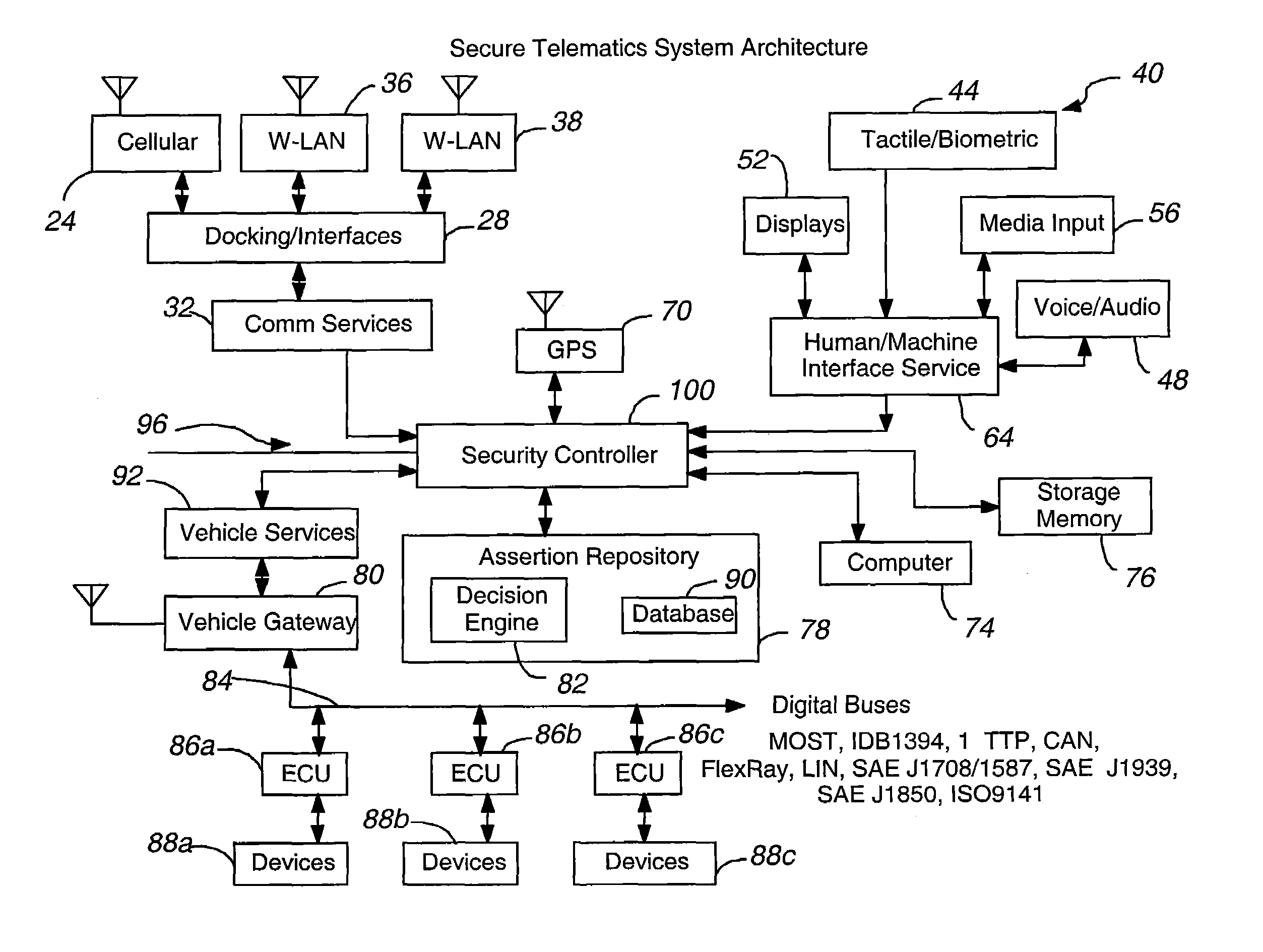
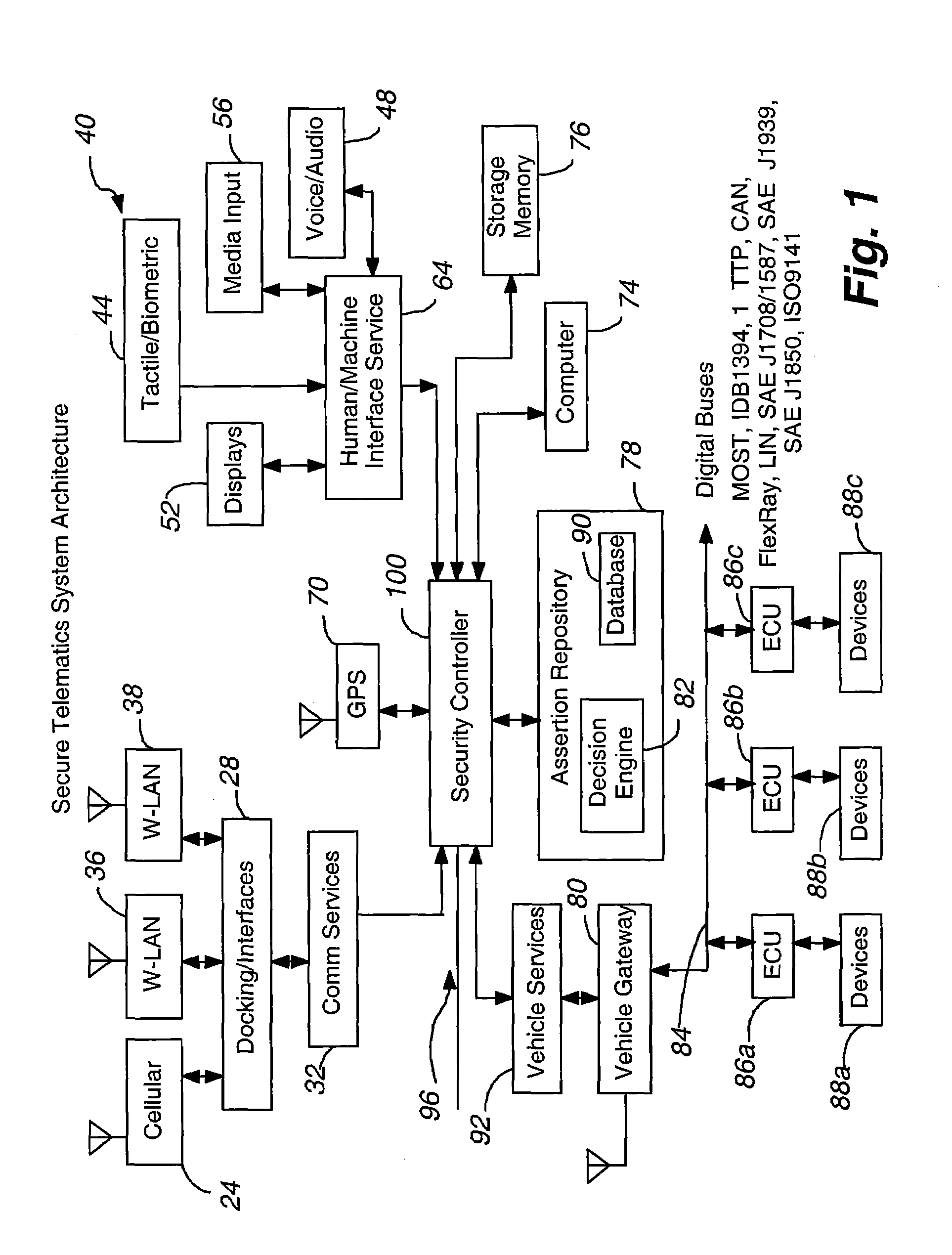
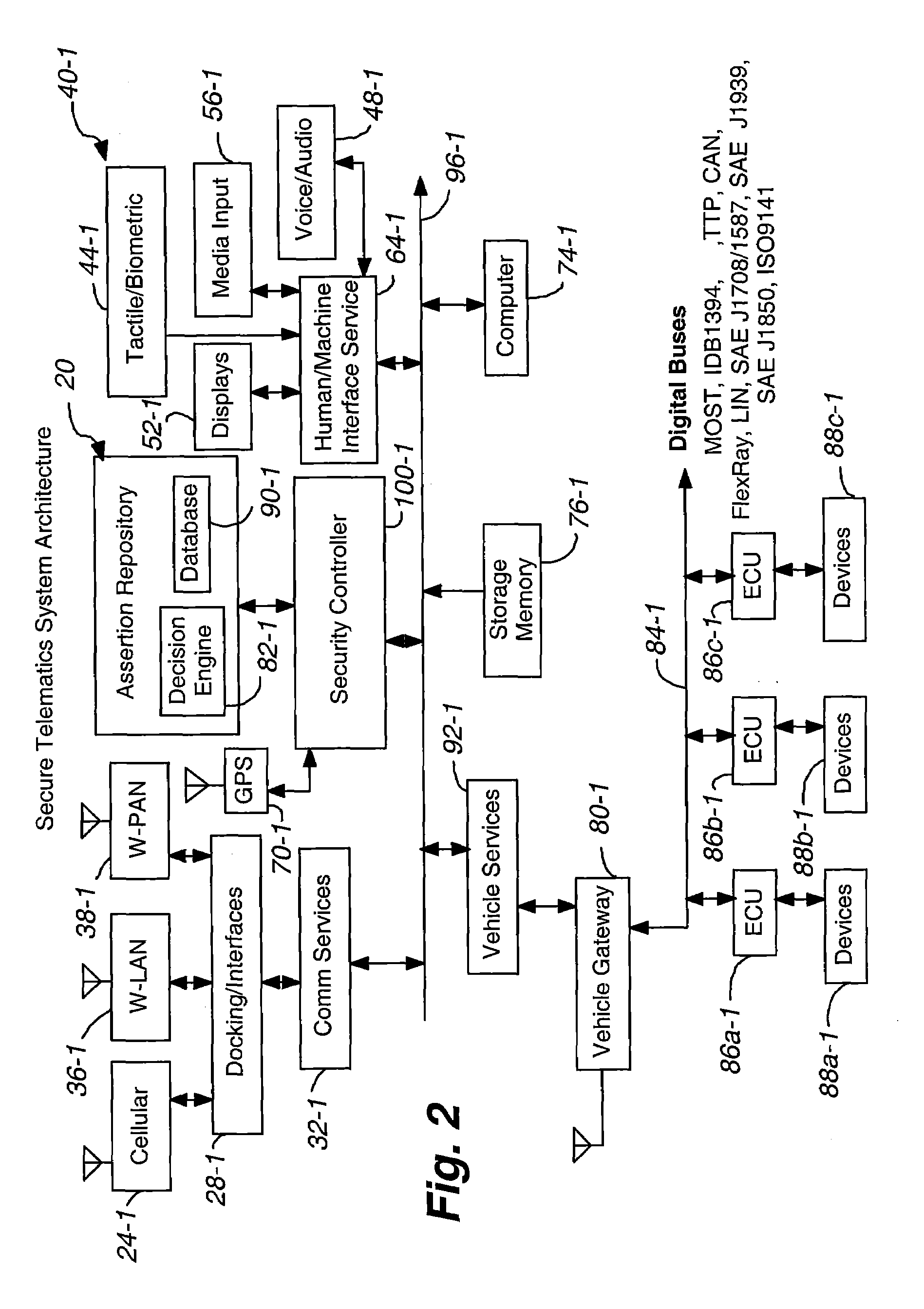
InactiveUS20080148374A1Expands telematics usageImprove integrityVehicle testingRegistering/indicating working of vehiclesComputer networkService provision
A telematics system that includes a security controller is provided. The security controller is responsible for ensuring secure access to and controlled use of resources in the vehicle. The security measures relied on by the security controller can be based on digital certificates that grant rights to certificate holders, e.g., application developers. In the case in which applications are to be used with vehicle resources, procedures are implemented to make sure that certified applications do not jeopardize vehicle resources' security and vehicle users' safety. Relationships among interested entities are established to promote and support secure vehicle resource access and usage. The entities can include vehicle makers, communication service providers, communication apparatus vendors, vehicle subsystem suppliers, application developers, as well as vehicle owners / users. At least some of the entities can be members of a federation established to enhance and facilitate secure access and usage of vehicle resources.
Owner:CYBERCAR INC
Secure telematics
ActiveUS7366892B2Expands telematics usageLow costUnauthorised/fraudulent call preventionRegistering/indicating working of vehiclesService provisionSecurity Measure
A telematics system that includes a security controller is provided. The security controller is responsible for ensuring secure access to and controlled use of resources in the vehicle. The security measures relied on by the security controller can be based on digital certificates that grant rights to certificate holders, e.g., application developers. In the case in which applications are to be used with vehicle resources, procedures are implemented to make sure that certified applications do not jeopardize vehicle resource'0 security and vehicle users' safety. Relationships among interested entities are established to promote and support secure vehicle resource access and usage. The entities can include vehicle makers, communication service providers, communication apparatus vendors, vehicle subsystem suppliers, application developers, as well as vehicle owners / users. At least some of the entities can be members of a federation established to enhance and facilitate secure access and usage of vehicle resources.
Owner:CYBERCAR INC
Method and system for a runtime user account creation operation within a single-sign-on process in a federated computing environment
ActiveUS20060236382A1Key distribution for secure communicationDigital data processing detailsComputer networkService provision
A method, system, apparatus, and computer program product are presented to support computing systems of different enterprises that interact within a federated computing environment. Federated single-sign-on operations can be initiated at the computing systems of federation partners on behalf of a user even though the user has not established a user account at a federation partner prior to the initiation of the single-sign-on operation. For example, an identity provider can initiate a single-sign-on operation at a service provider while attempting to obtain access to a controlled resource on behalf of a user. When the service provider recognizes that it does not have a linked user account for the user that allows for a single-sign-on operation with the identity provider, the service provider creates a local user account. The service provider can also pull user attributes from the identity provider as necessary to perform the user account creation operation.
Owner:IBM CORP
Method and system for policy-based initiation of federation management
ActiveUS20080010665A1Data processing applicationsDigital data processing detailsData processing systemJoint management
A method, a system, an apparatus, and a computer program product is presented for performing federation protocol operations within a data processing system. A message is received. In response to a determination that subsequent processing of the message requires execution of a first federation protocol operation, the message is filtered against a set of policies to determine a subset of one or more applicable policies. An applicable policy is enforced by performing a second federation protocol operation as indicated by the applicable policy prior to performing the first federation protocol operation. In response to concluding enforcement of the applicable policy, the first federation protocol operation is initiated.
Owner:IBM CORP
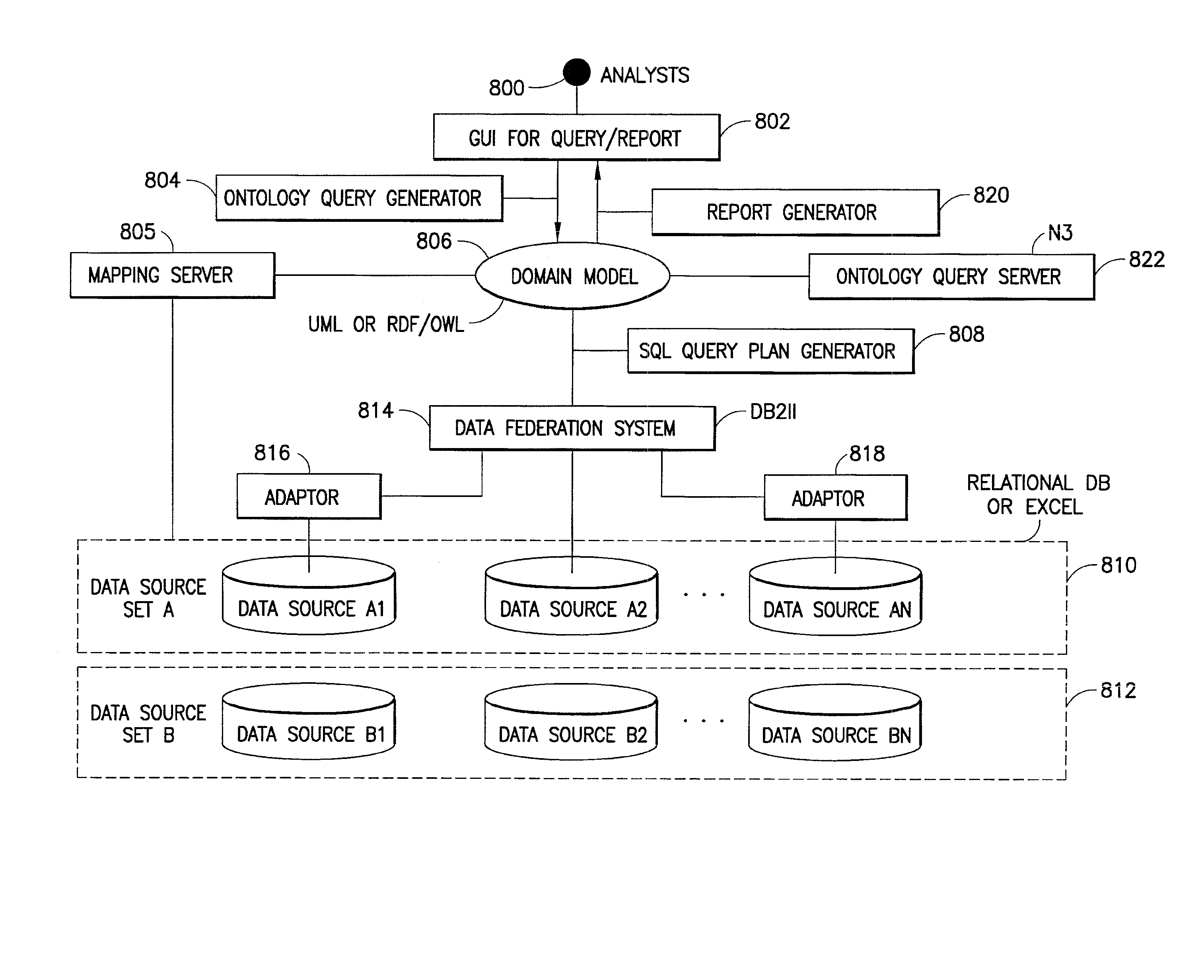
System and Method for Planning and Generating Queries for Multi-Dimensional Analysis using Domain Models and Data Federation
InactiveUS20080046422A1Data processing applicationsDigital data information retrievalDomain modelData warehouse
Data integration and data analysis using computing equipment, software as well as hardware, includes a system and method for integrating data from various data sources, structured and unstructured, without physically creating a data warehouse and automatically generating queries for analysis of the integrated data from a multitude of different views.
Owner:SERVICENOW INC
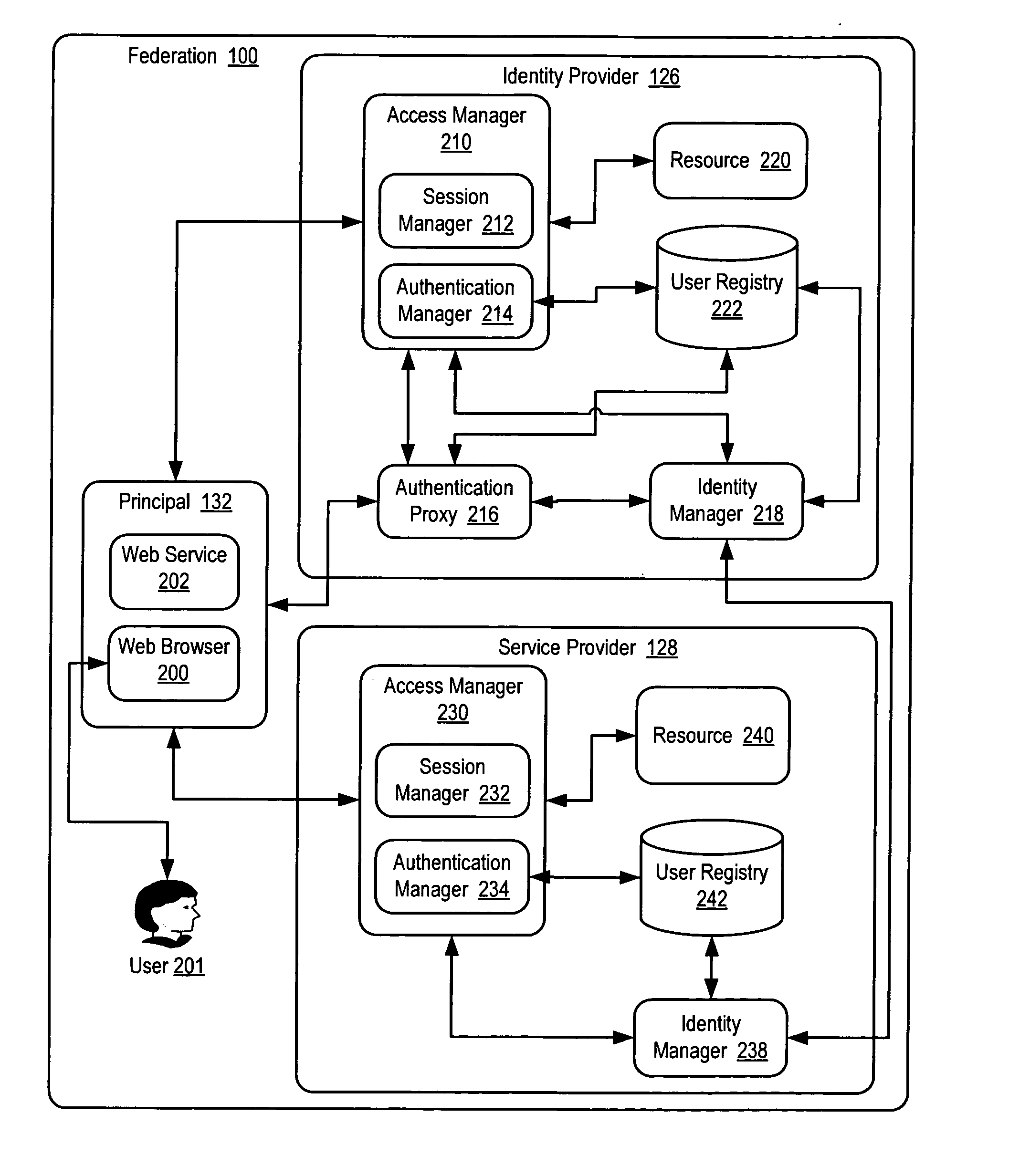
Specializing support for a federation relationship
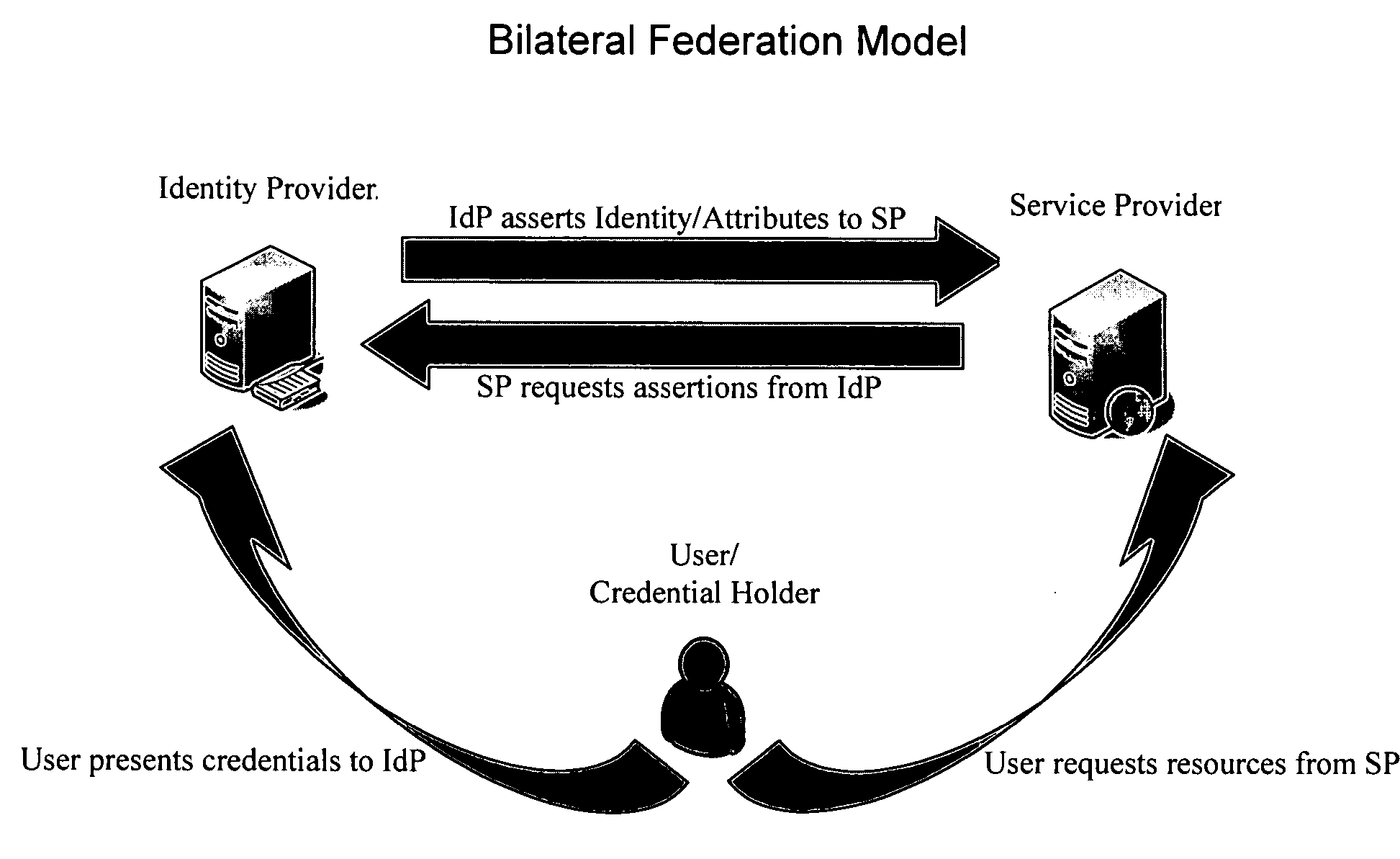
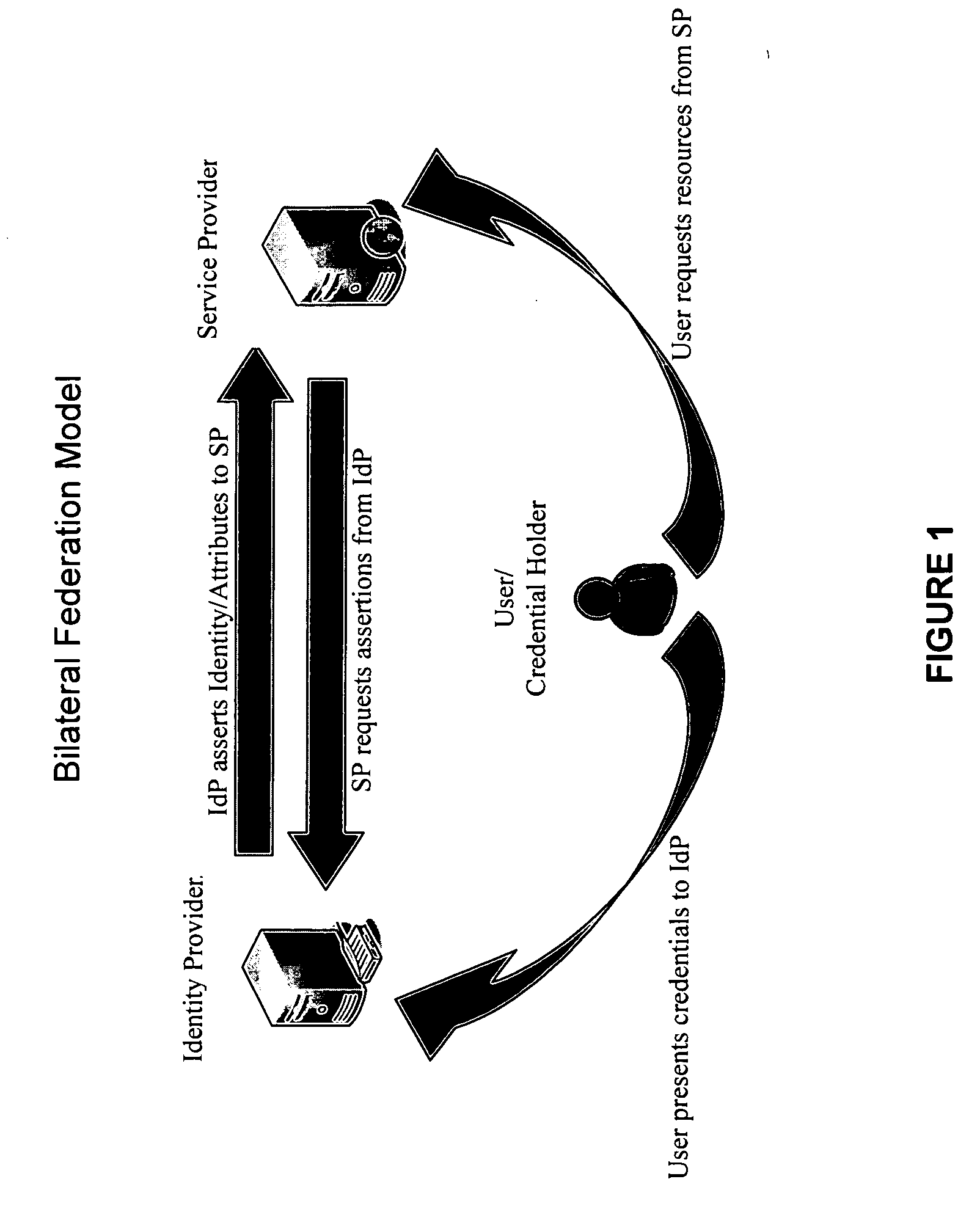
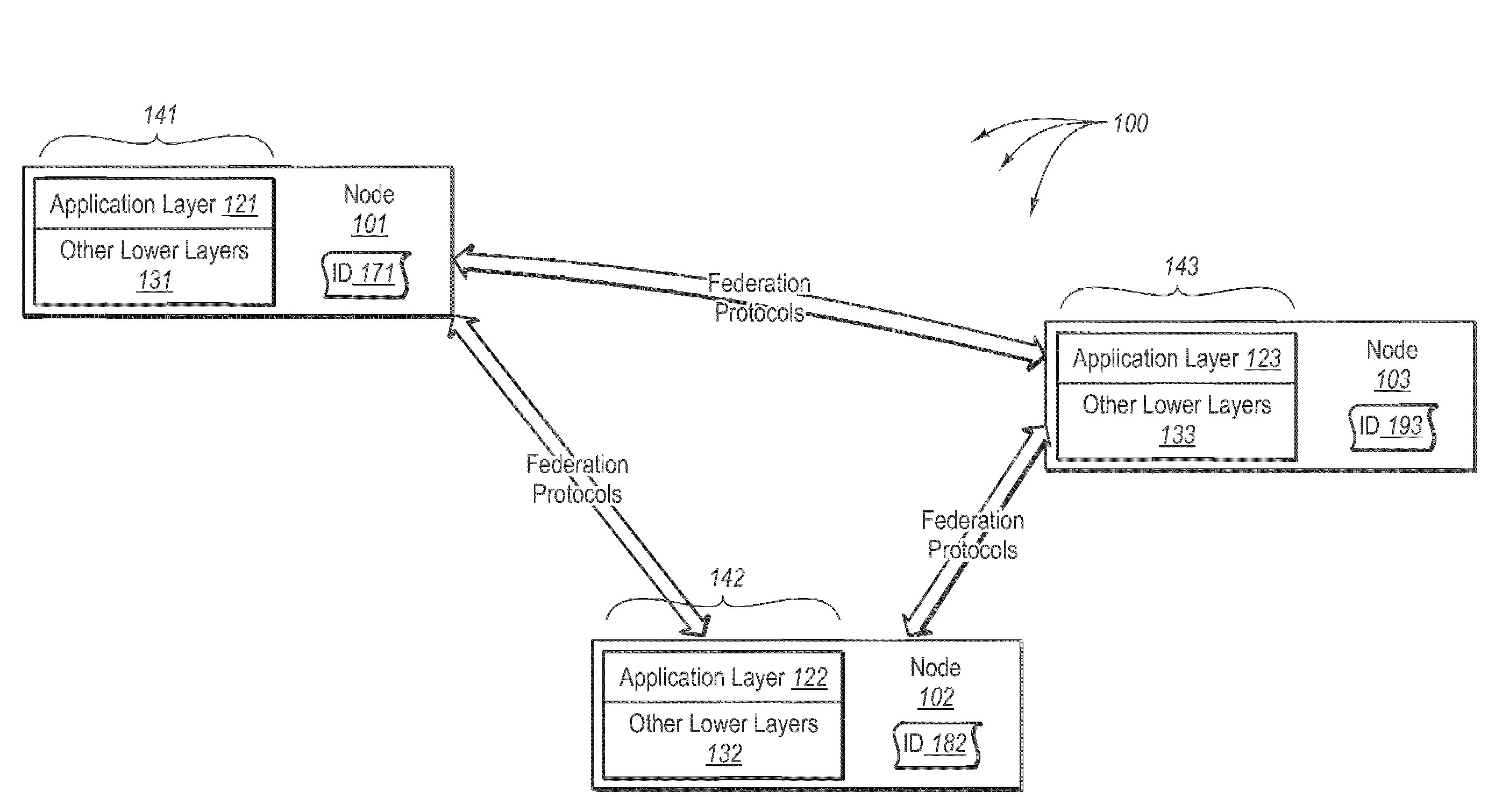
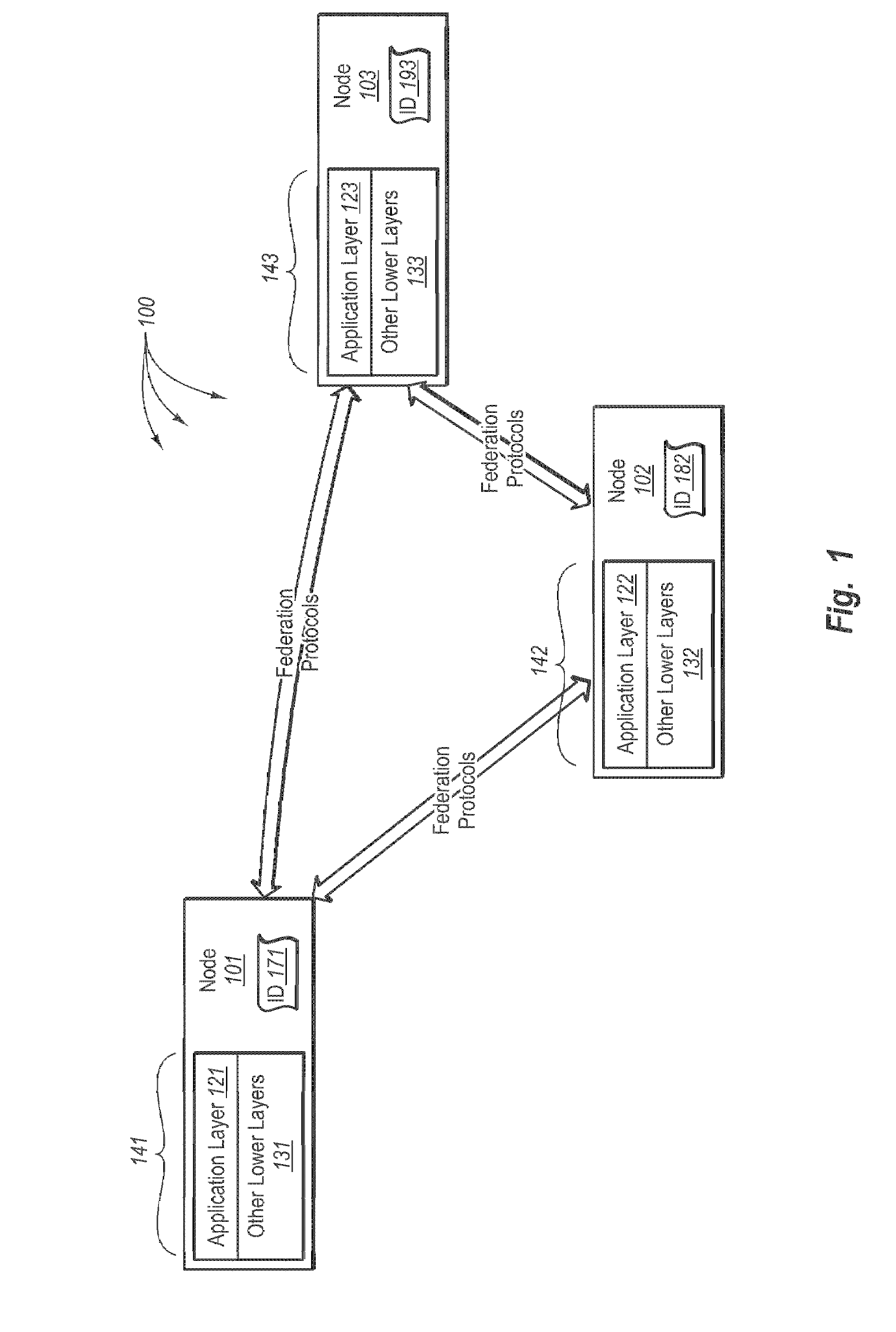
ActiveUS7562382B2Change is minimalDigital data processing detailsUser identity/authority verificationData processing systemIdentity provider
The invention provides federated functionality within a data processing system by means of a set of specialized runtimes. Each of the plurality of specialized runtimes provides requested federation services for selected ones of the requestors according to configuration data of respective federation relationships of the requestors with the identity provider. The configuration data is dynamically retrieved during initialization of the runtimes which allows the respective runtime to be specialized for a given federation relationship. Requests are routed to the appropriate specialized runtime using the first requestor identity and the given federation relationship. The data which describes each federation relationship between the identity provider and each of the plurality of requesters is configured prior to initialization of the runtimes. Configuration data is structured into global specified data, federation relationship data and requestor specific data to minimize data change, making the addition or deletion of requestors very scalable.
Owner:IBM CORP
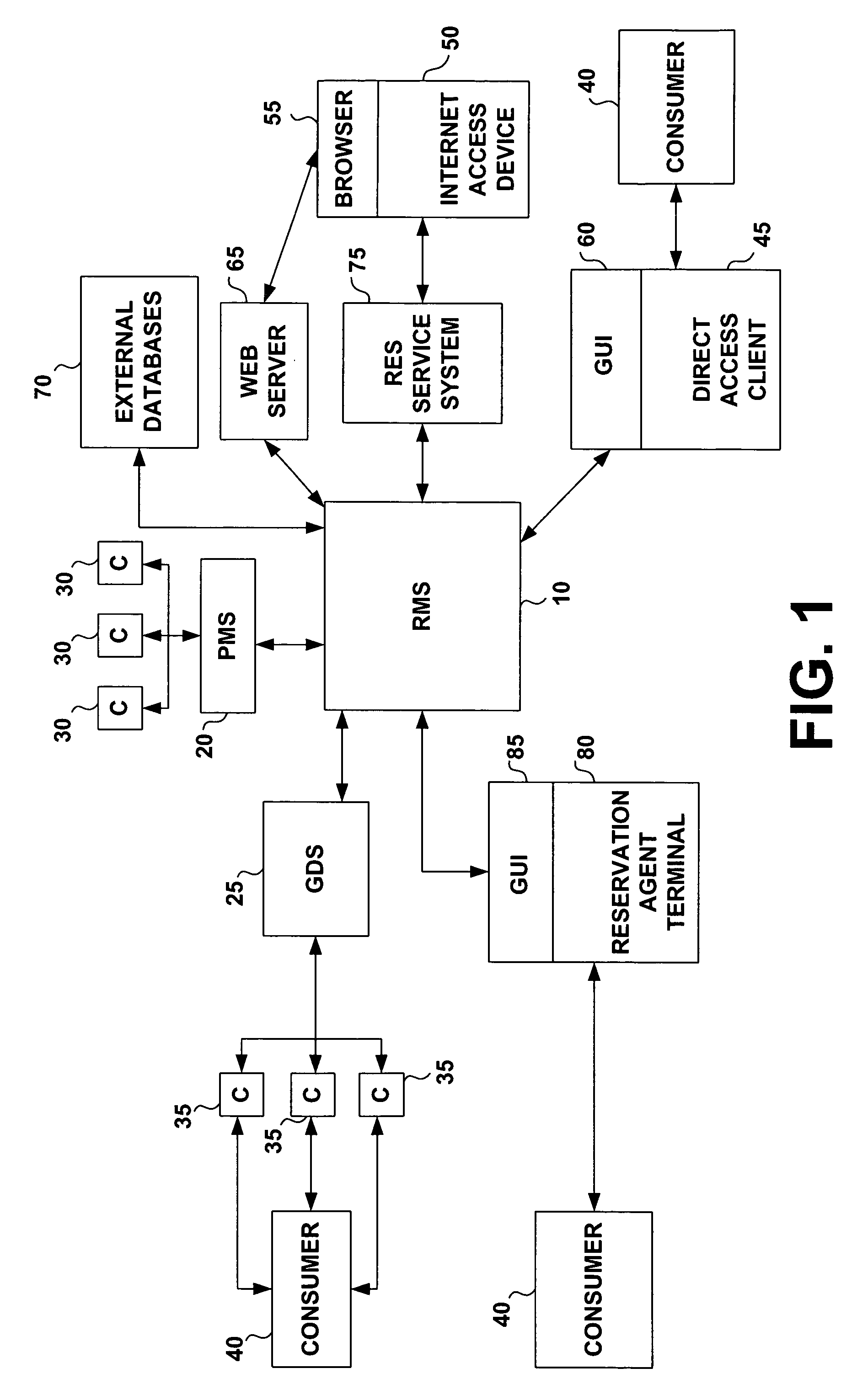
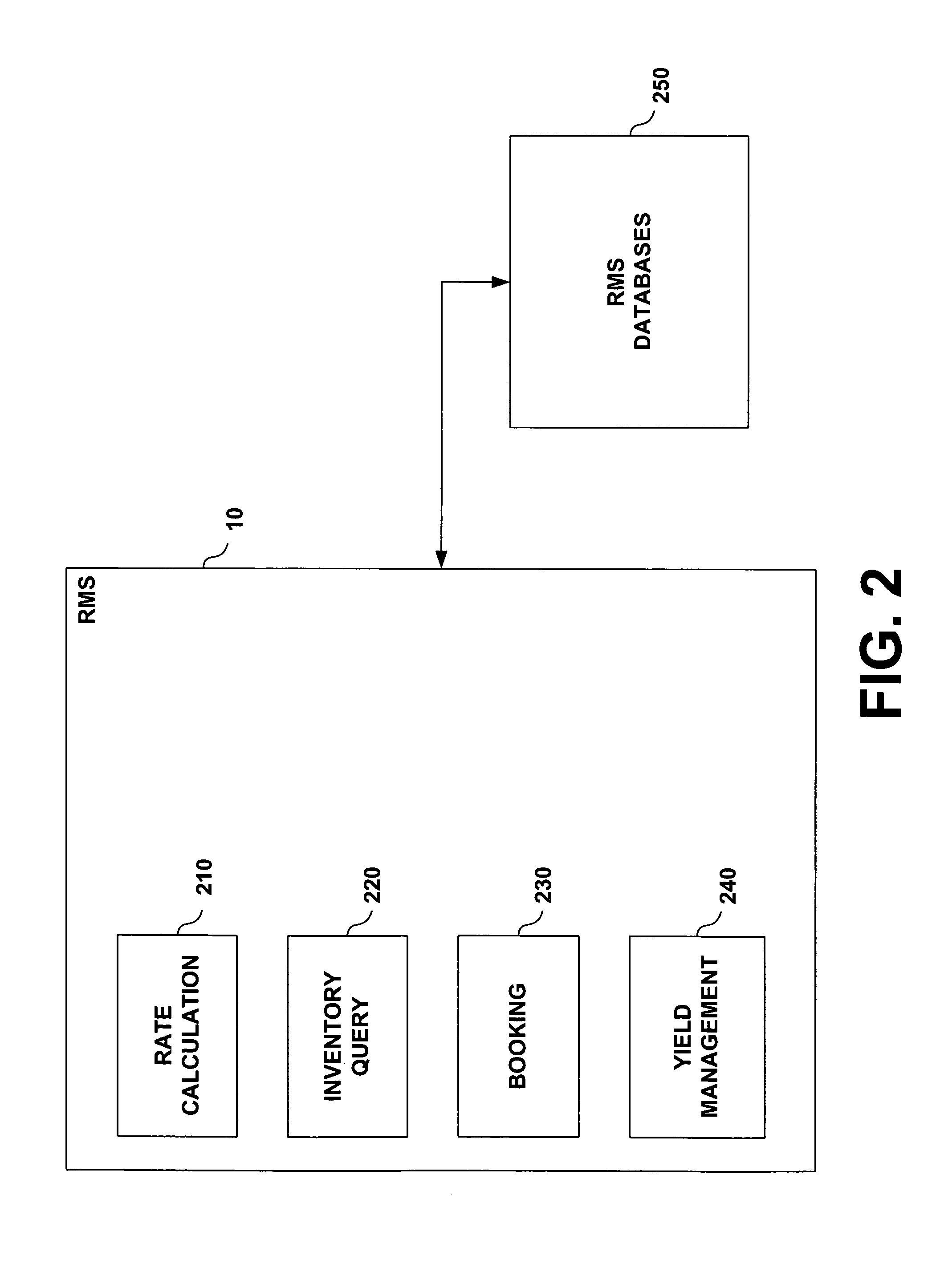
Global reservations transaction management system and method
InactiveUS7328166B1Increase incomeReal-time accessDigital data processing detailsReservationsThe InternetCentral database
A reservation system and methodology ensures that all changes to a database in a federation are reliably and immediately communicated to all of the other databases in the federation. The system communicates information concerning hotel reservation transactions. The system comprises multiple applications each associated with one or more databases including hotel reservation data. The databases in the federation reflect transactions that are communicated to other databases and they also employ information received from other databases in determining the transactions that their associated local applications permit and the way in which they are processed. In one embodiment of the invention, communication among databases occurs through the Internet and data storage devices via secure packetized messages addressed to objects that represent the relevant databases. The system of the present invention also preferably includes a central database that functions as the primary source for verifying reservations and hotel data. Additionally, the system of the present invention also includes a yield subsystem that allows hotels to increase revenues. The yield subsystem calculates rates and availability based upon forecasted changes in supply and customer segment demand.
Owner:SYNXIX
Transactions Across Blockchain Networks
In asynchronous public network, synchronous leaderless Byzantine consensus protocol operating with guaranteed safety and time-bound termination of individual protocol rounds is enabled with nodes having clustered architecture and highly available data transactions, and implemented with algorithm that defuses the effect of stop-faulty processes and bypasses the partitioned network links. Utilizing the time-bound consensus, a protocol and architecture for cross-chain transactions accomplish safe interoperability across blockchain networks. Multiple cross-chain transacting networks interconnected in a federation overcome the limitations of blockchain networks with monolithic ledgers in regard to transaction latency, scalability of throughput, volume of managed data, and openness for further interoperability.
Owner:KLIANEV IVAN
Data consistency within a federation infrastructure
InactiveUS20080288646A1Well formedDigital data information retrievalInput/output to record carriersClient dataClient-side
In some embodiments, it is determined that a primary node has been elected from among a plurality of nodes in a replica set of nodes. The primary node accepts and processes client data access requests. The replica set includes the primary node and other secondary nodes. The primary node receives client data access requests. The primary node assigns a data sequence number to each client data access request that mutates state in the order the client data access requests are received. The data sequence numbers include a linearized processing order that is to be followed by each of the nodes in the replica set. The primary node sends the mutating client data access requests including any corresponding data sequence numbers to the secondary nodes. The primary node receives, from a threshold number of secondary nodes, an acknowledgement indicating reception of the client data access request. The primary node commits the data mutating access request.
Owner:MICROSOFT TECH LICENSING LLC
Specializing support for a federation relationship
ActiveUS20060136990A1Change is minimalDigital data processing detailsUser identity/authority verificationData processing systemIdentity provider
The invention provides federated functionality within a data processing system by means of a set of specialized runtimes. Each of the plurality of specialized runtimes provides requested federation services for selected ones of the requestors according to configuration data of respective federation relationships of the requestors with the identity provider. The configuration data is dynamically retrieved during initialization of the runtimes which allows the respective runtime to be specialized for a given federation relationship. Requests are routed to the appropriate specialized runtime using the first requestor identity and the given federation relationship. The data which describes each federation relationship between the identity provider and each of the plurality of requesters is configured prior to initialization of the runtimes. Configuration data is structured into global specified data, federation relationship data and requestor specific data to minimize data change, making the addition or deletion of requesters very scalable.
Owner:IBM CORP
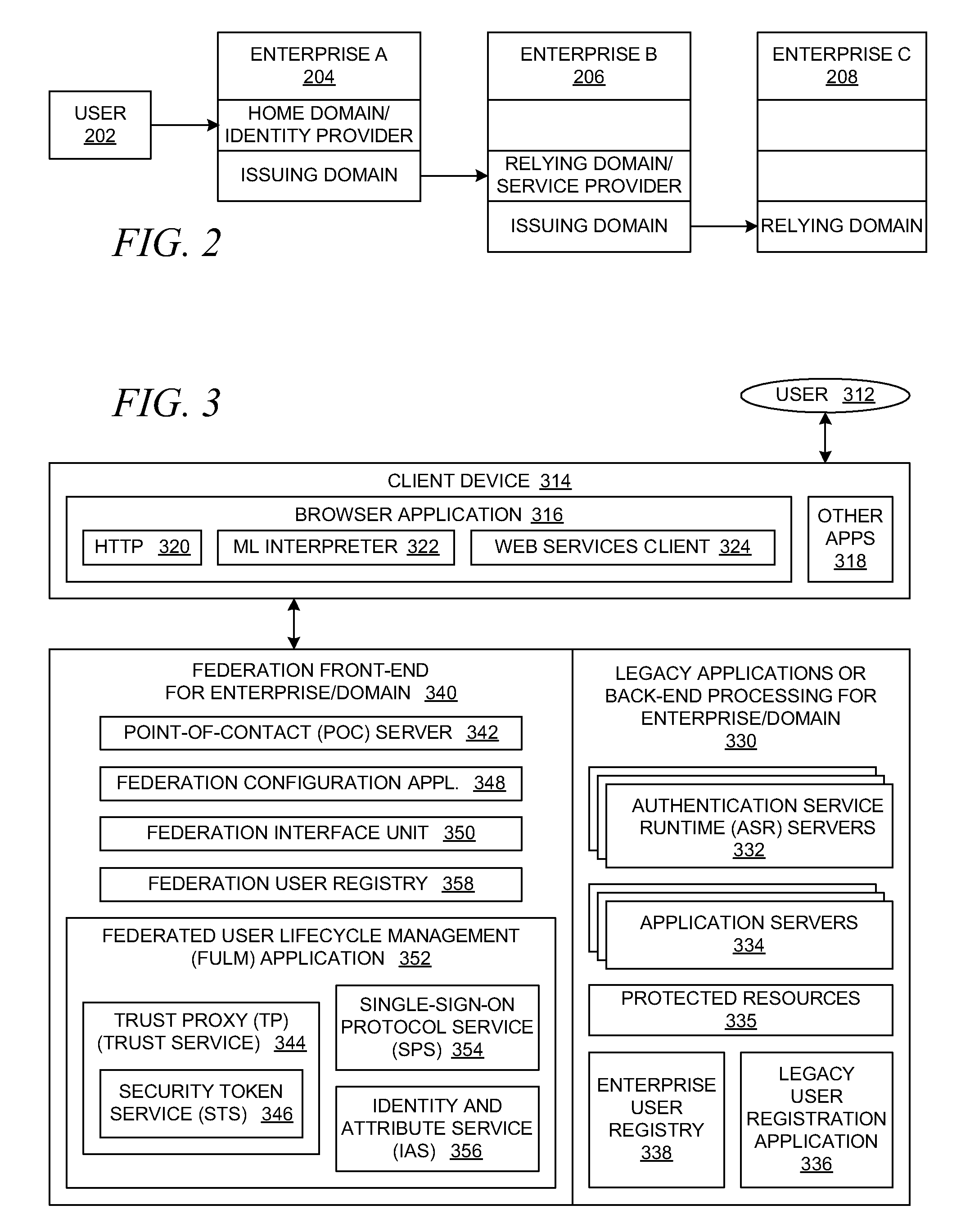
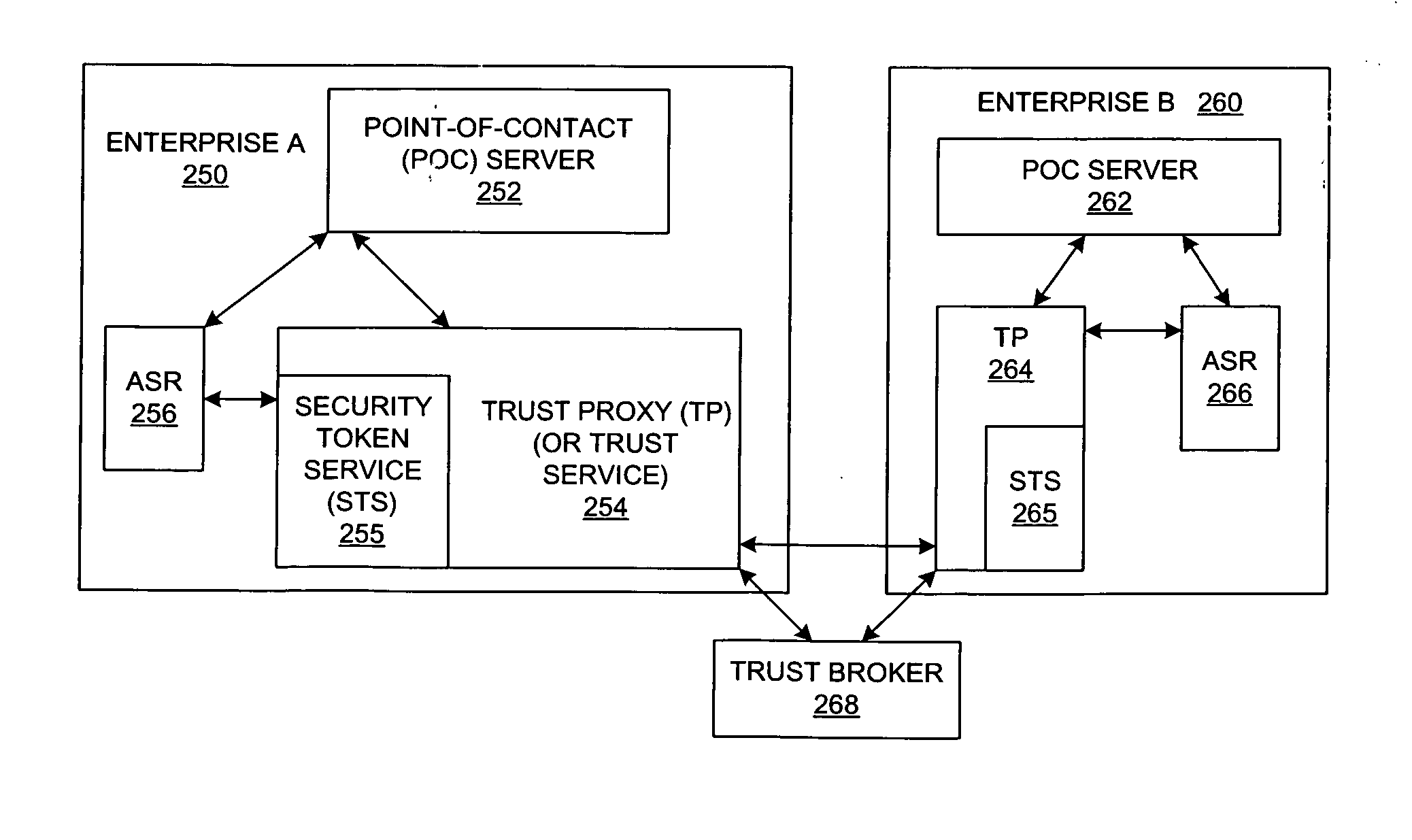
Method and system for enabling trust infrastructure support for federated user lifecycle management
InactiveUS20060021018A1Digital data processing detailsUser identity/authority verificationTrust relationshipKey management
A method and a system are presented in which computing environments of different enterprises interact within a federated computing environment. Federated operations can be initiated at the computing environments of federation partners on behalf of a user at a different federated computing environment. A point-of-contact service relies upon a trust service to manage trust relationships between a computing environment and computing environments of federation partners. The trust service employs a key management service, an identity / attribute service, and a security token service. A federated user lifecycle management service implements federated user lifecycle functions and interacts with the point-of-contact service and the trust service.
Owner:IBM CORP
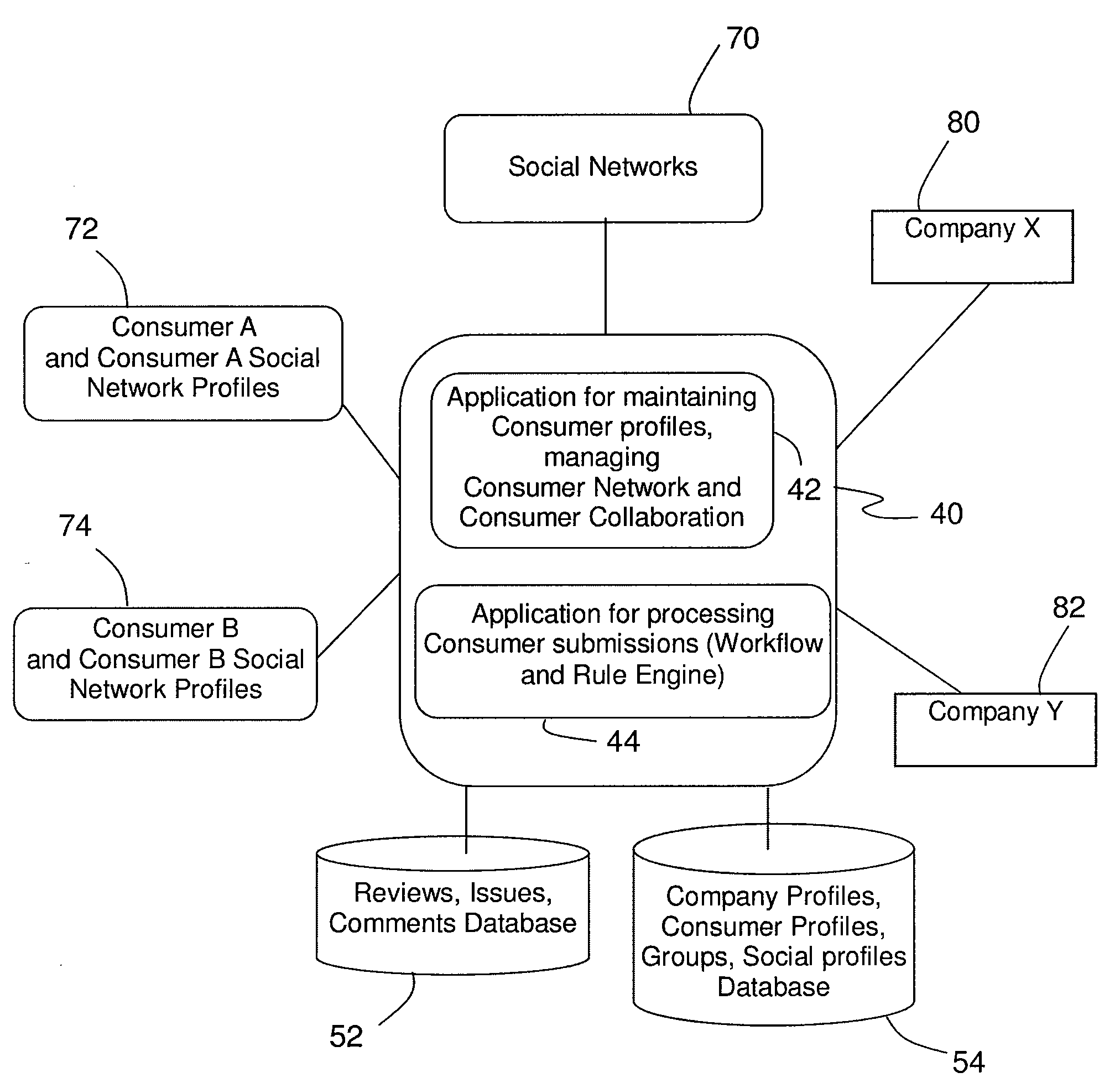
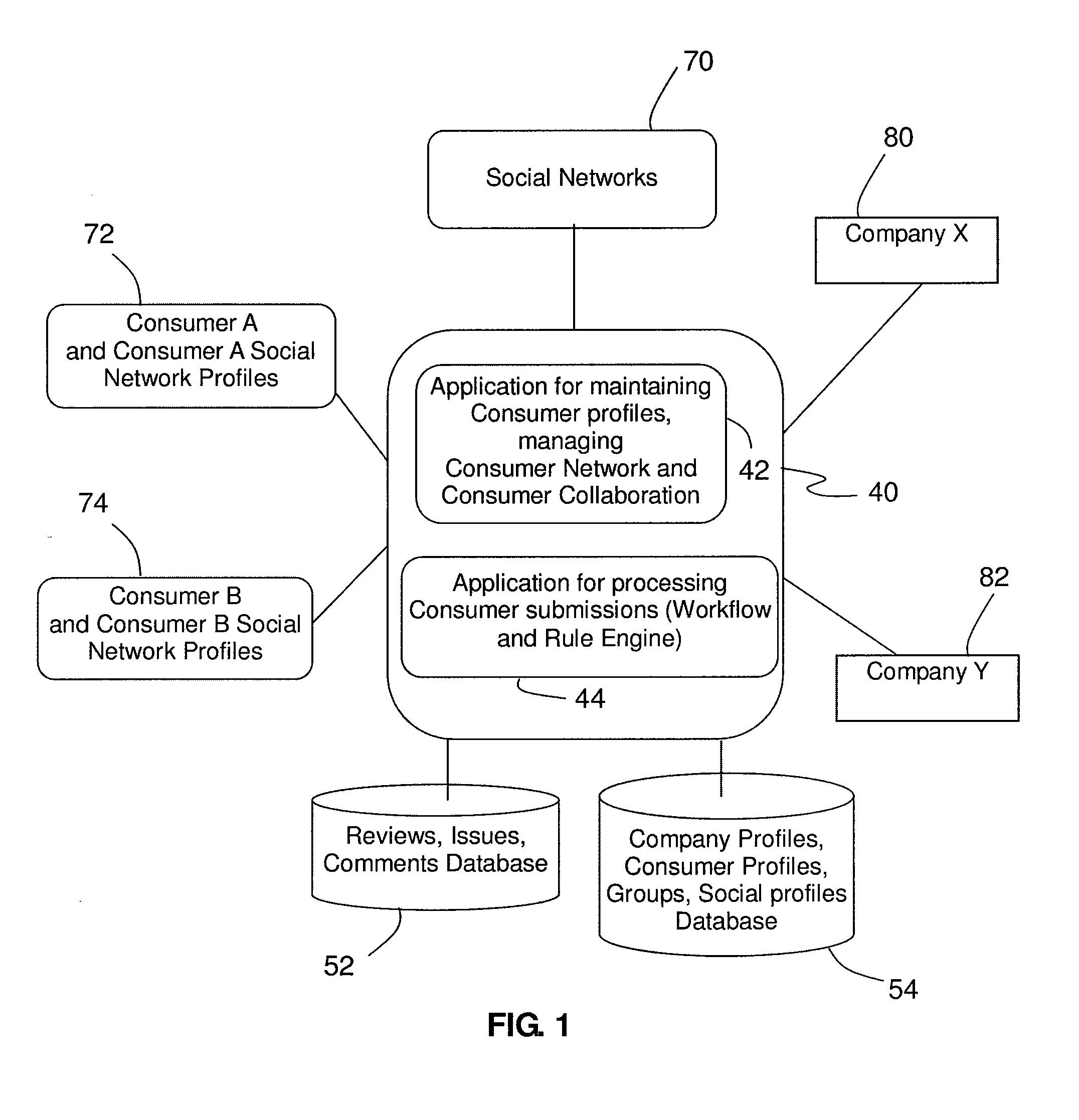
Customer-oriented customer relationship management process and system
InactiveUS20110071950A1Easy accessOffice automationCommerceCustomer relationship managementPersonal details
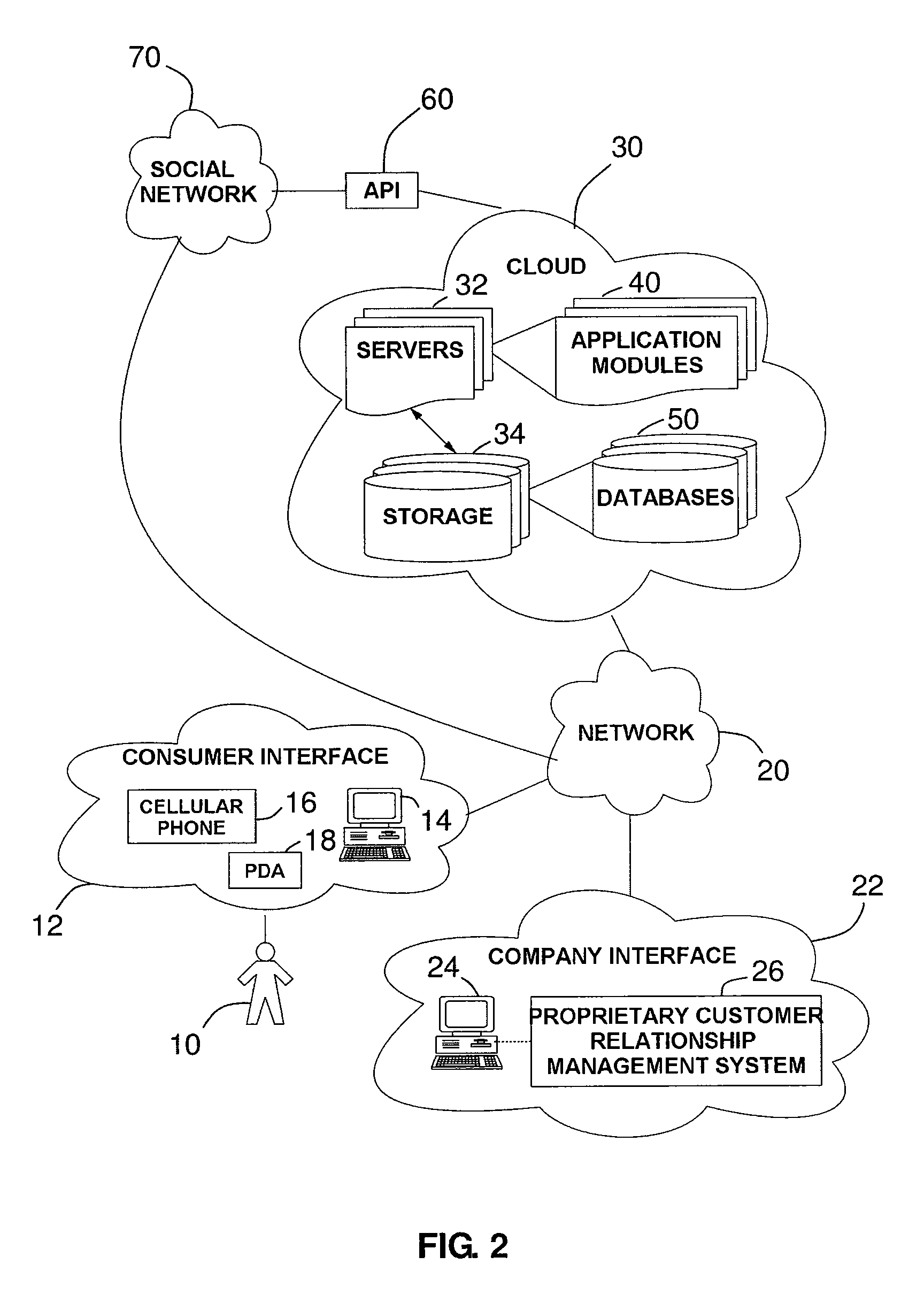
A method and system for customer service and support integrated with social networks includes an Internet available server application where consumers and providers can create their profiles, integrate their profiles with existing social network profiles, and collaborate with each other on resolving consumer issues using a workflow engine supported with a rule engine. Consumers may be organized into consumer groups and into federations of consumer groups. Consumer issues may be voted on thereby raising the significance of an issue and / or building a provider's reputation based in part on resolved issues, issue votes, and by reviews and comments. Consumers manage their profiles. Provider profiles are predominately affected by resolved / unresolved issues or positive / negative reviews. Notifications are handled automatically based on configured workflow and rule engine and utilize internal messaging system, emails, SMS and other available social network services (e.g. Facebook, Twitter, etc.).
Owner:CALLIDUS SOFTWARE
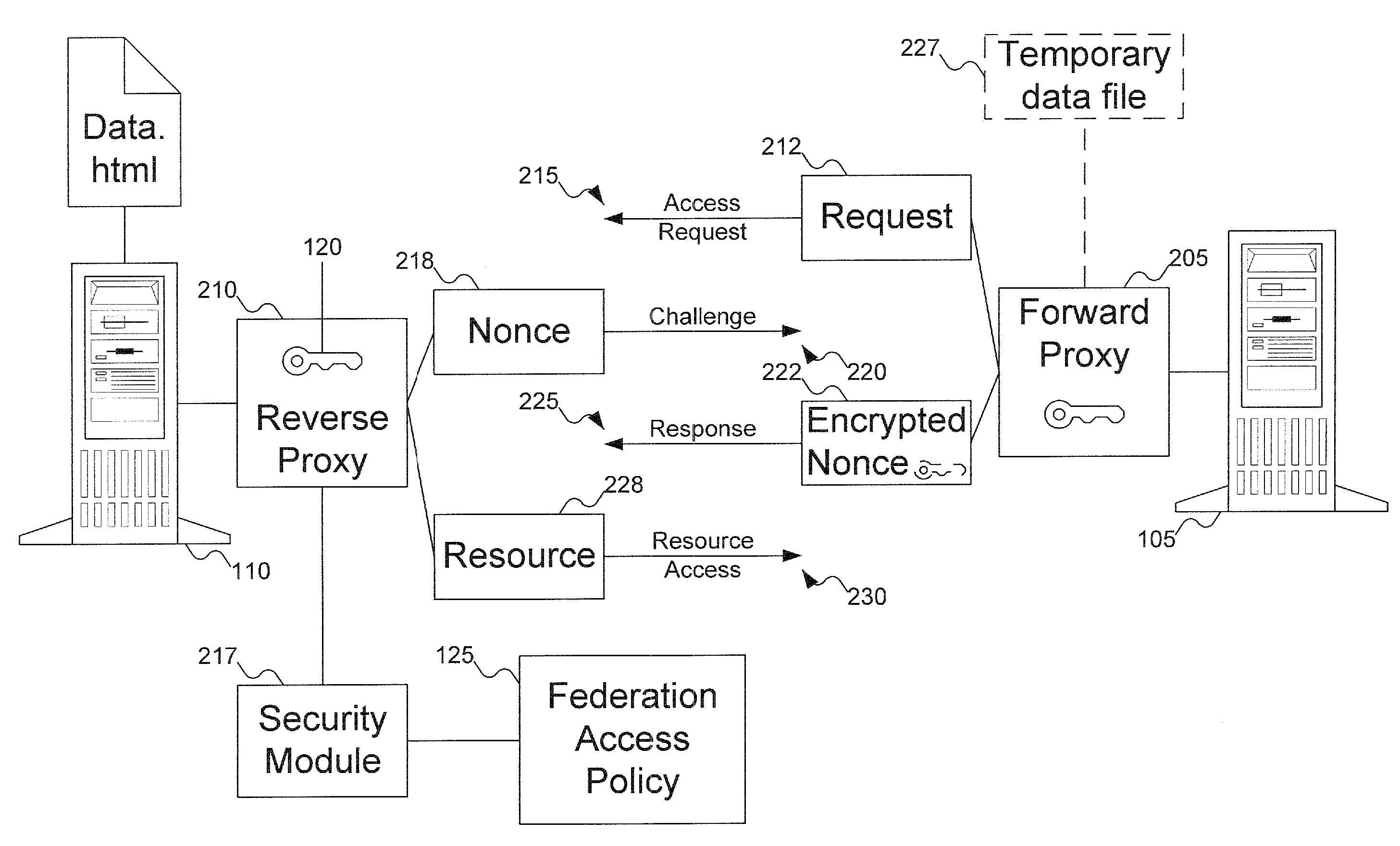
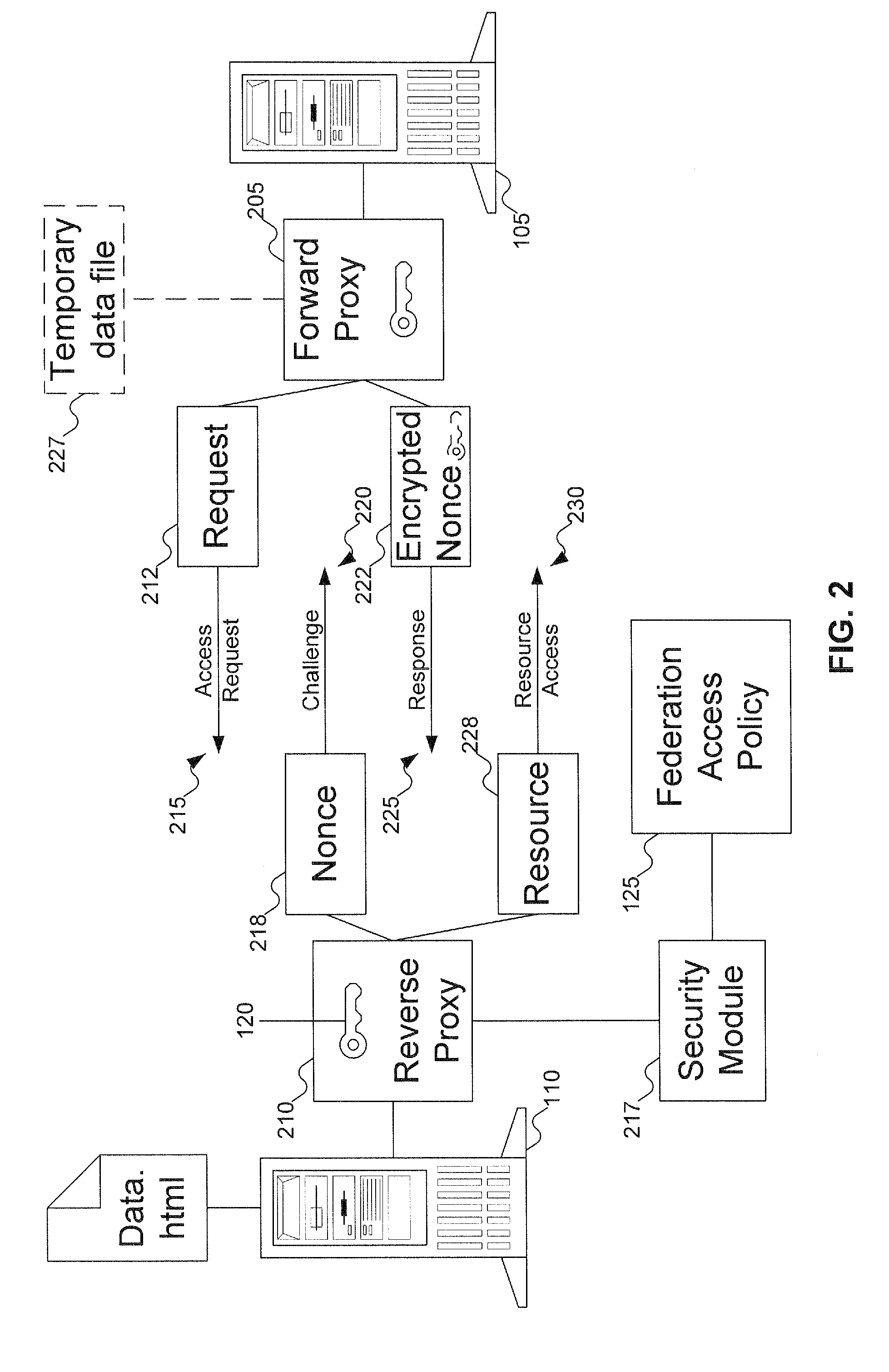
Cross domain authentication and security services using proxies for HTTP access
InactiveUS20070289006A1Digital data processing detailsUser identity/authority verificationAuthenticationAccess control
Two identity spaces form a federation by agreeing to use a secret key to facilitate secure access of resources between them. When one identity space receives a request for a resource from a user in the other identity space, the first identity space checks to see if the resource is protected. If the resource is protected, the first identity space requests that a mediator in the second identity space authenticate the external user. The mediator verifies the external user's authenticity. Once the external user is authenticated, the mediator securely informs the first identity space, using the secret key, that the external user is authenticated to access the resource. The identity space then grants the user access to the resource if the user is allowed access as per the access control policy of the identity space.
Owner:EMC IP HLDG CO LLC
Method and system for providing single sign-on service
InactiveUS20090119763A1Possible to useDigital data processing detailsUser identity/authority verificationWeb serviceInternet privacy
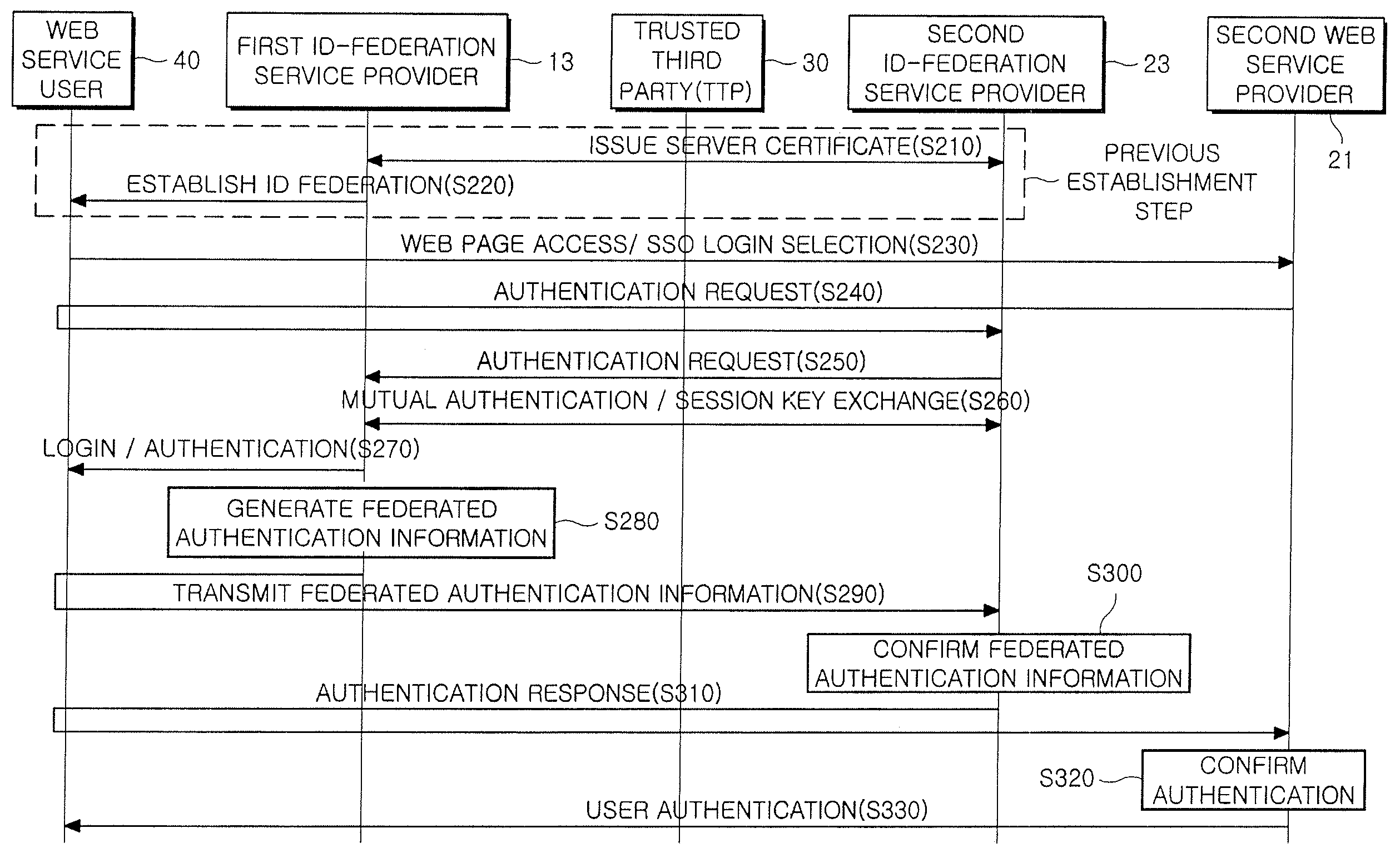
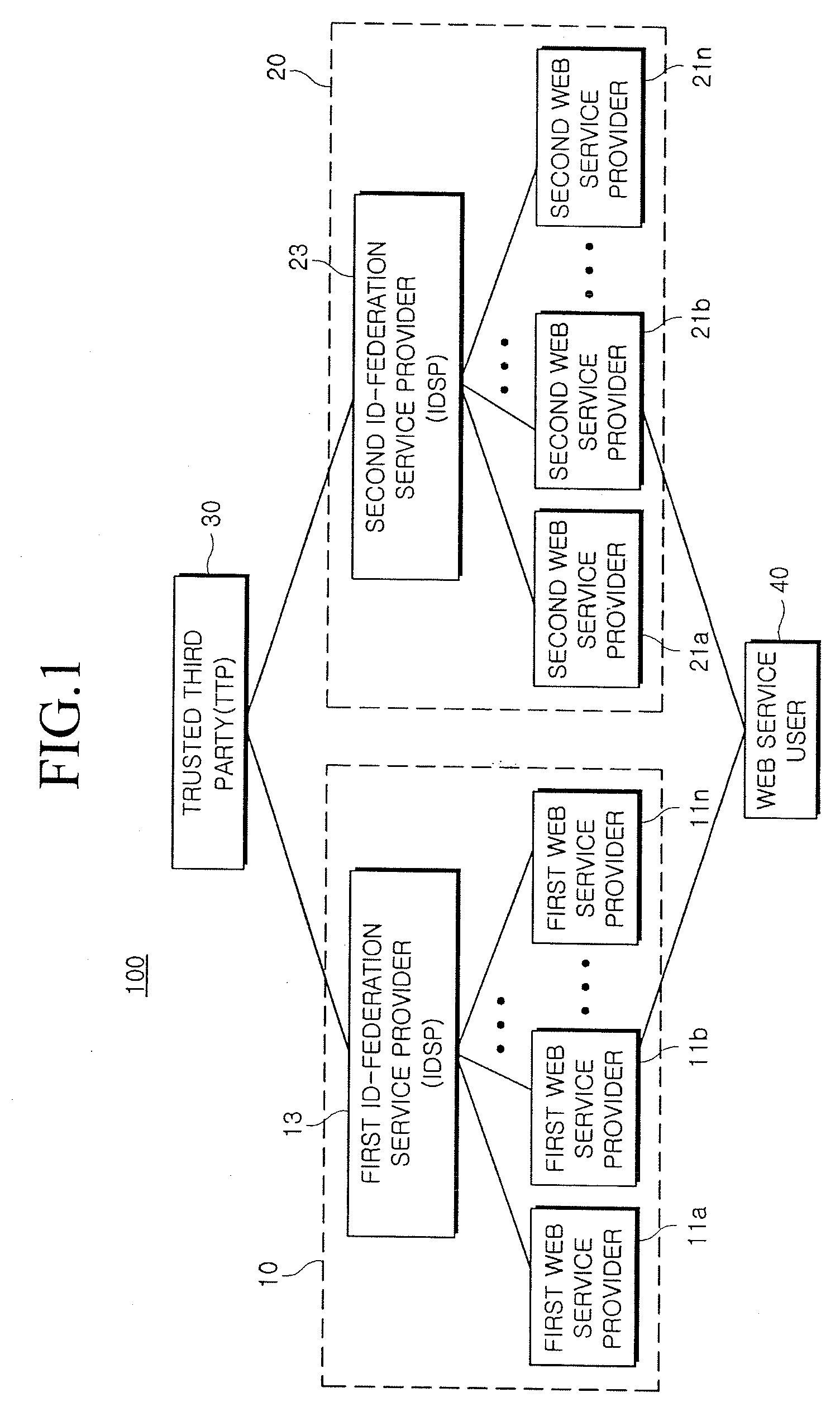
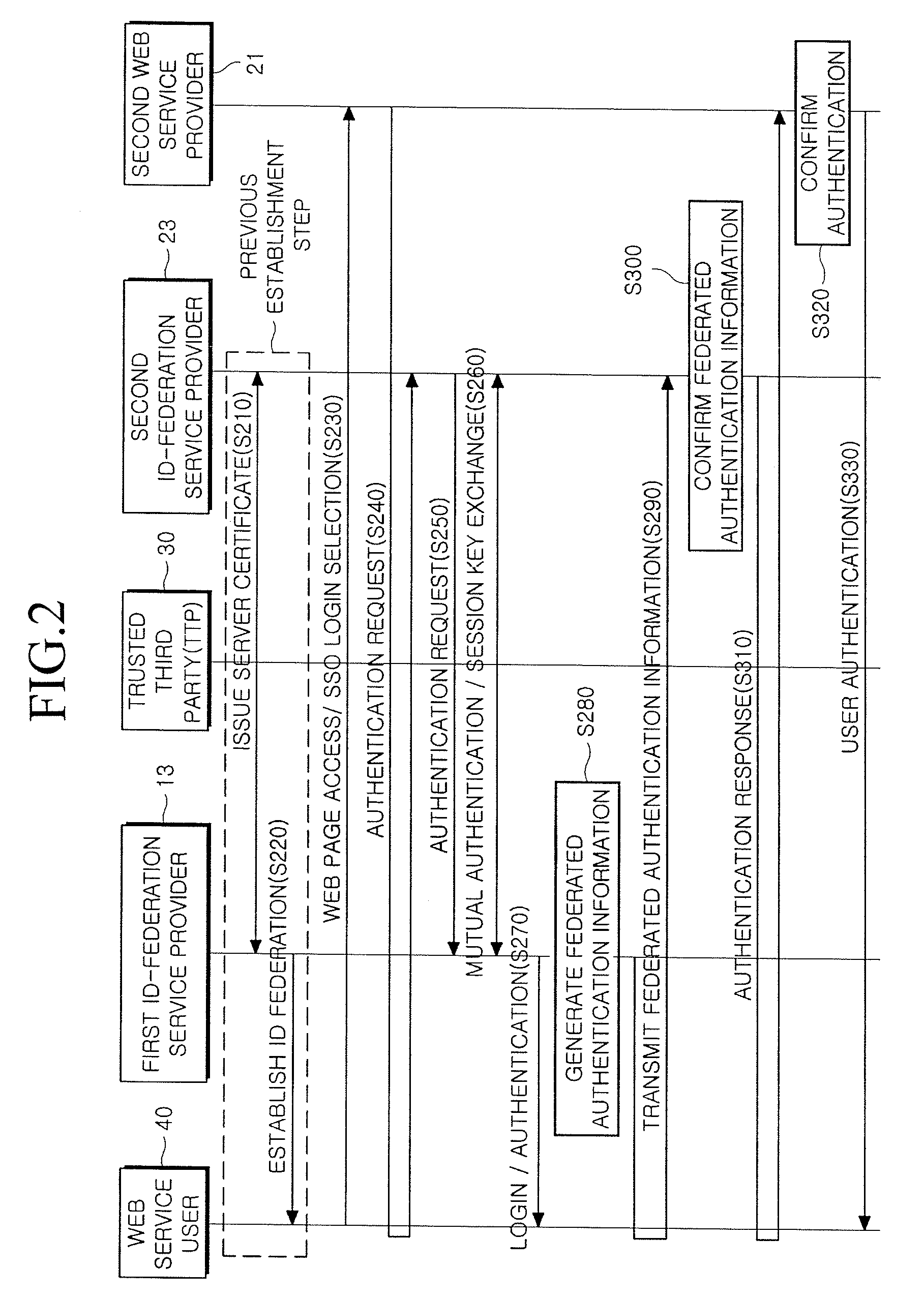
Provided is a method and system for providing an SSO service enabling the use of Web services in different trusted domains through a one-time authentication process. In the method, mutual authentication information is issued from a trusted third party to each of ID-federation service providers managing each of trusted domains, and an ID federation established between the ID-federation service provider and a user in the trusted domain of the ID-federation service provider. The first ID-federation service provider managing the first trusted domain, to which the user belongs to, is confirmed when a Web service provider in the second trusted domain receives a login request from the user in the first trusted domain. User authentication and mutual authentication arc performed between the first ID-federation service provider and a second ID-federation service provider managing the second trusted domain. The Web service provider authenticates the user in the first trusted domain and provides a corresponding Web service.
Owner:ELECTRONICS & TELECOMM RES INST
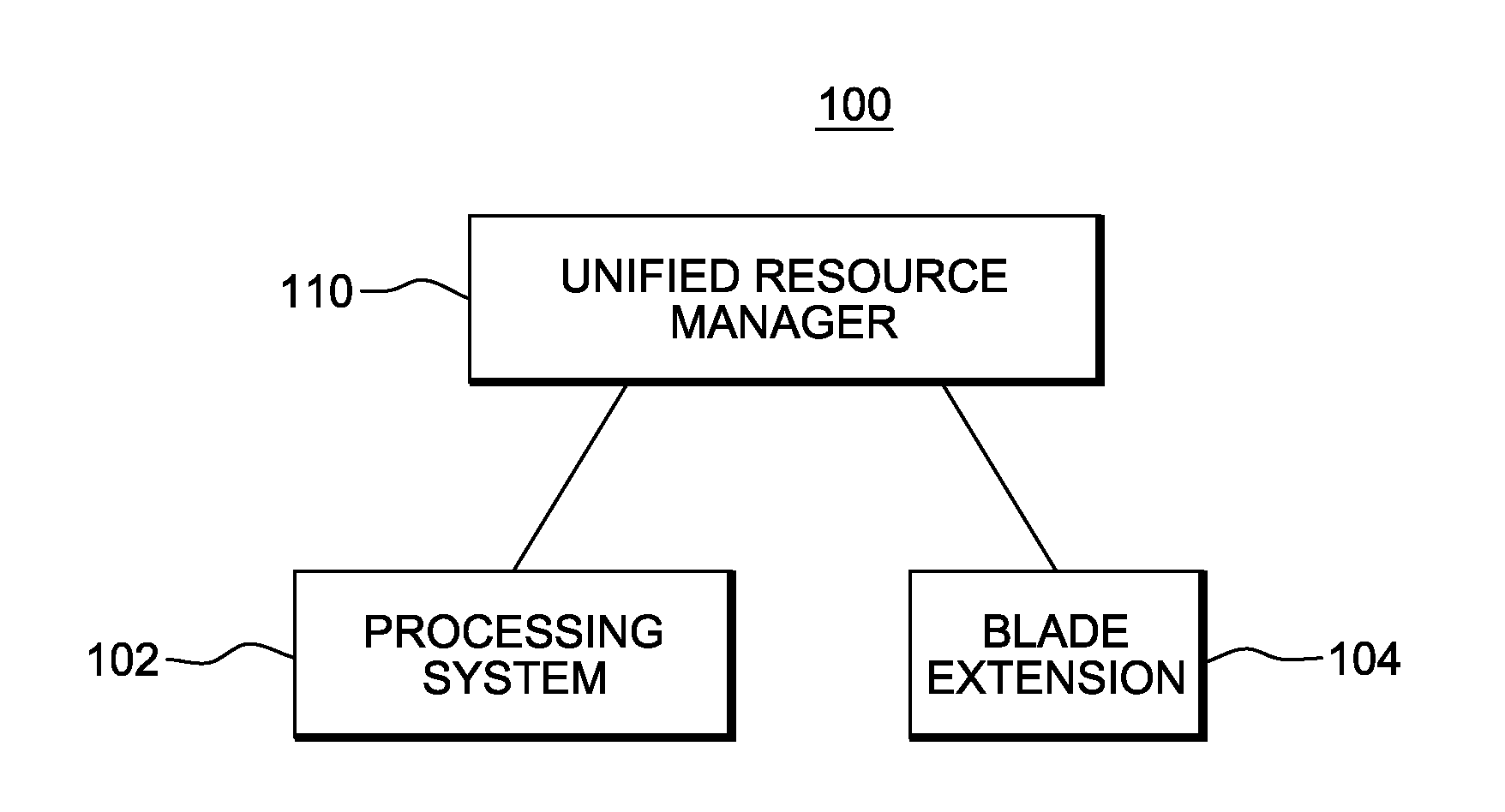
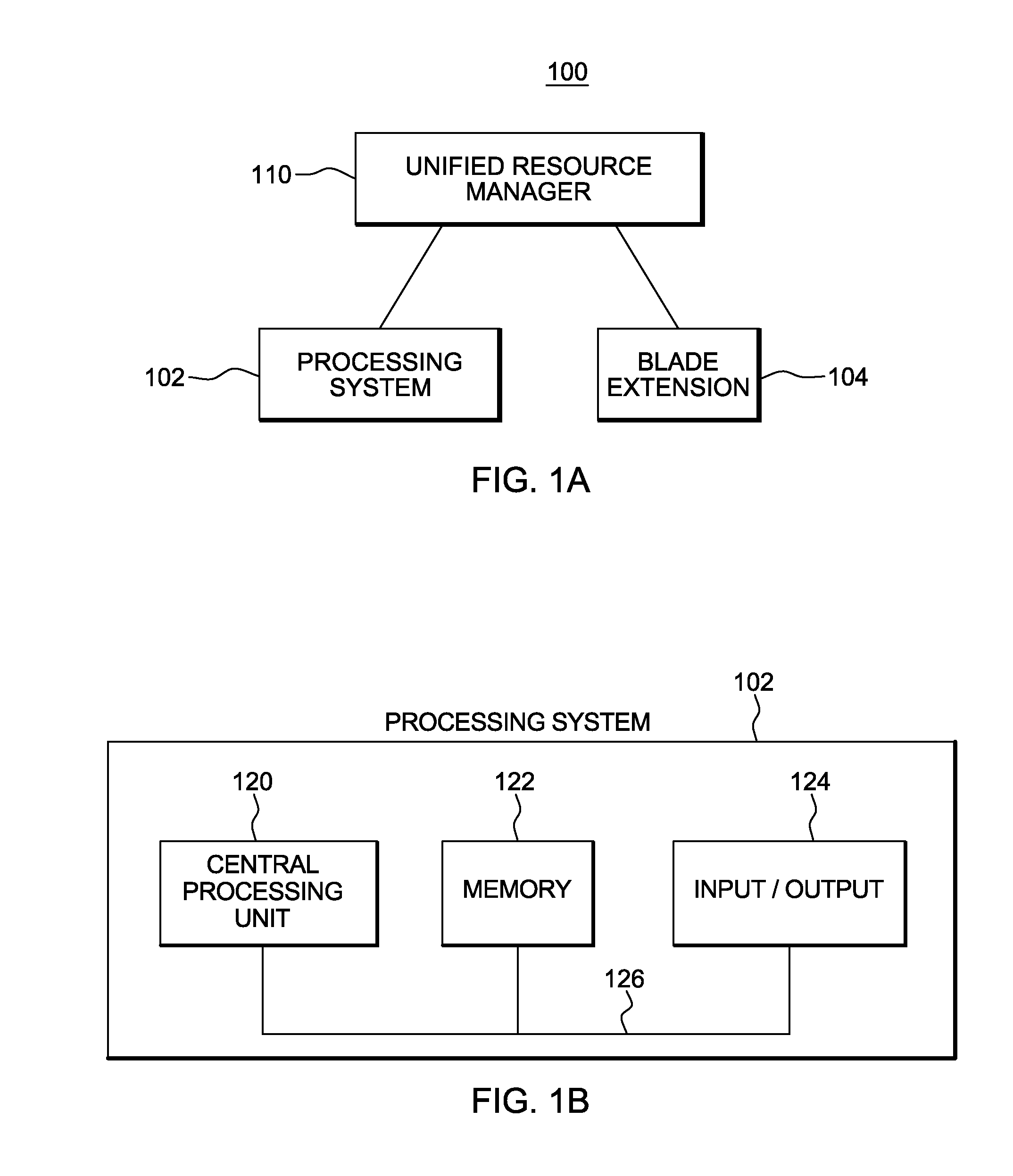
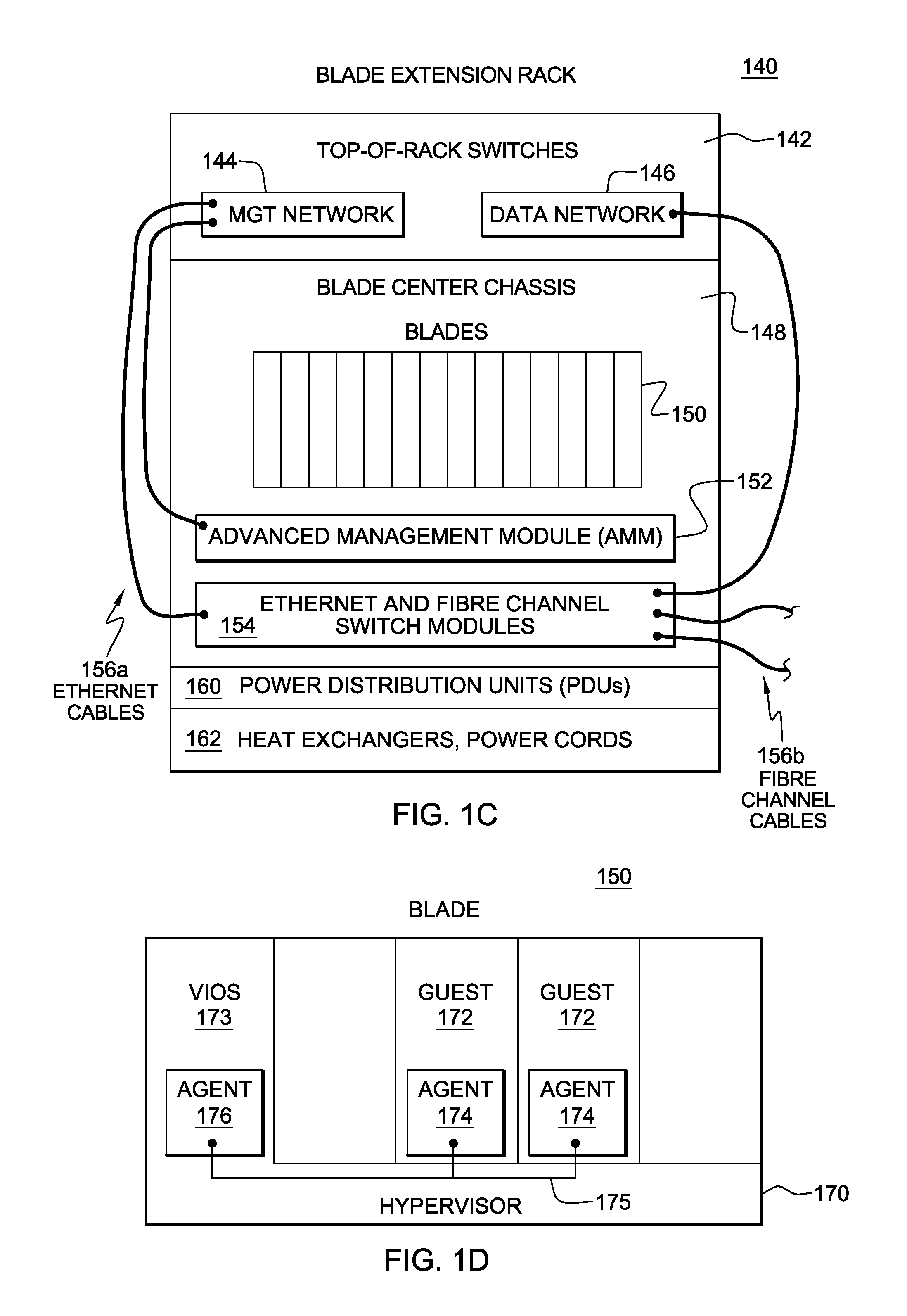
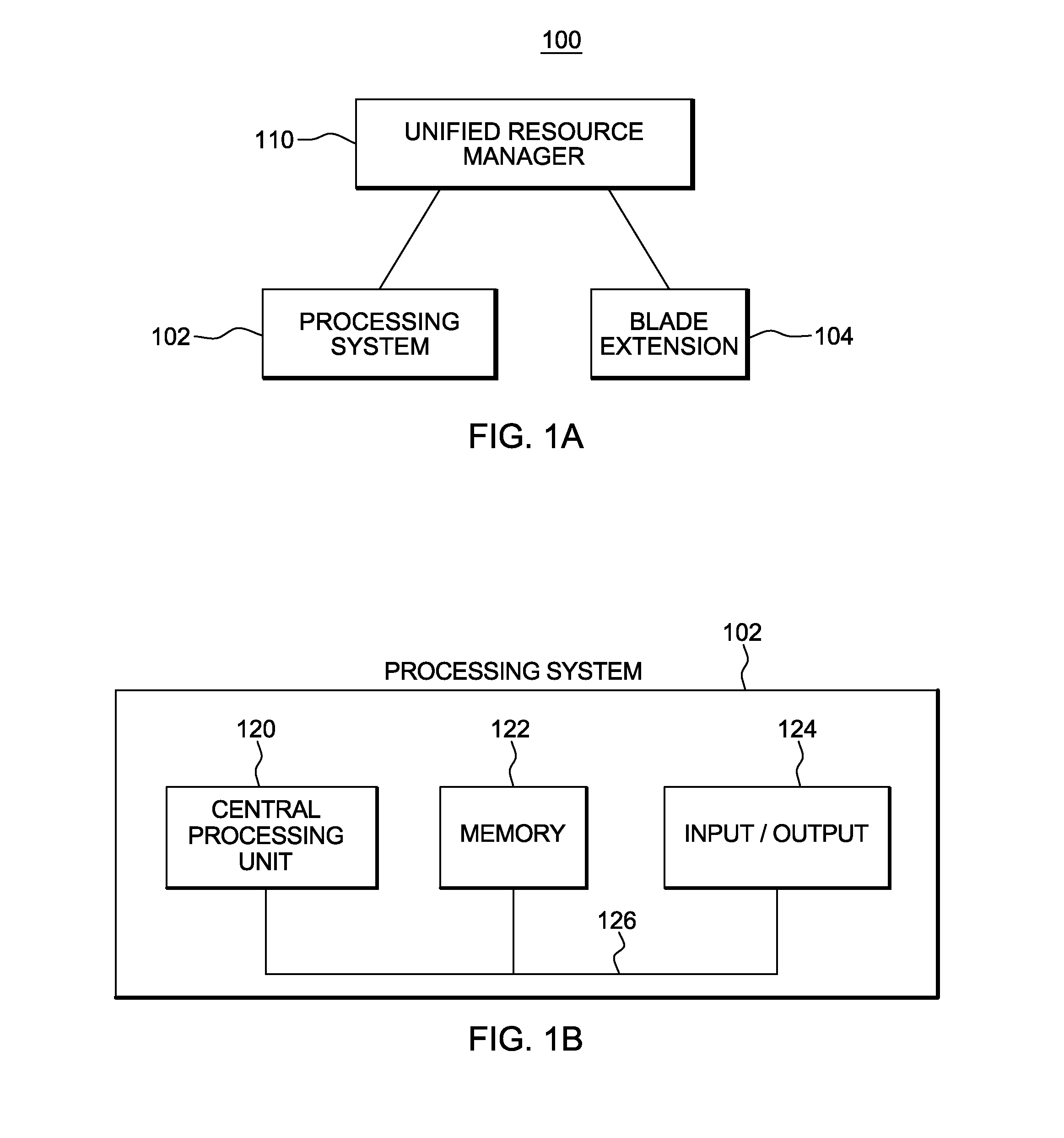
Unified resource manager providing a single point of control
ActiveUS20120110588A1Easy to operateOvercomes shortcomingEnergy efficient ICTResource allocationHybrid systemDistributed computing
An integrated hybrid system is provided. The hybrid system includes compute components of different types and architectures that are integrated and managed by a single point of control to provide federation and the presentation of the compute components as a single logical computing platform.
Owner:IBM CORP
Management of a data network of a computing environment
InactiveUS20120110155A1Overcomes shortcomingDigital computer detailsProgram controlHybrid systemDistributed computing
An integrated hybrid system is provided. The hybrid system includes compute components of different types and architectures that are integrated and managed by a single point of control to provide federation and the presentation of the compute components as a single logical computing platform.
Owner:IBM CORP
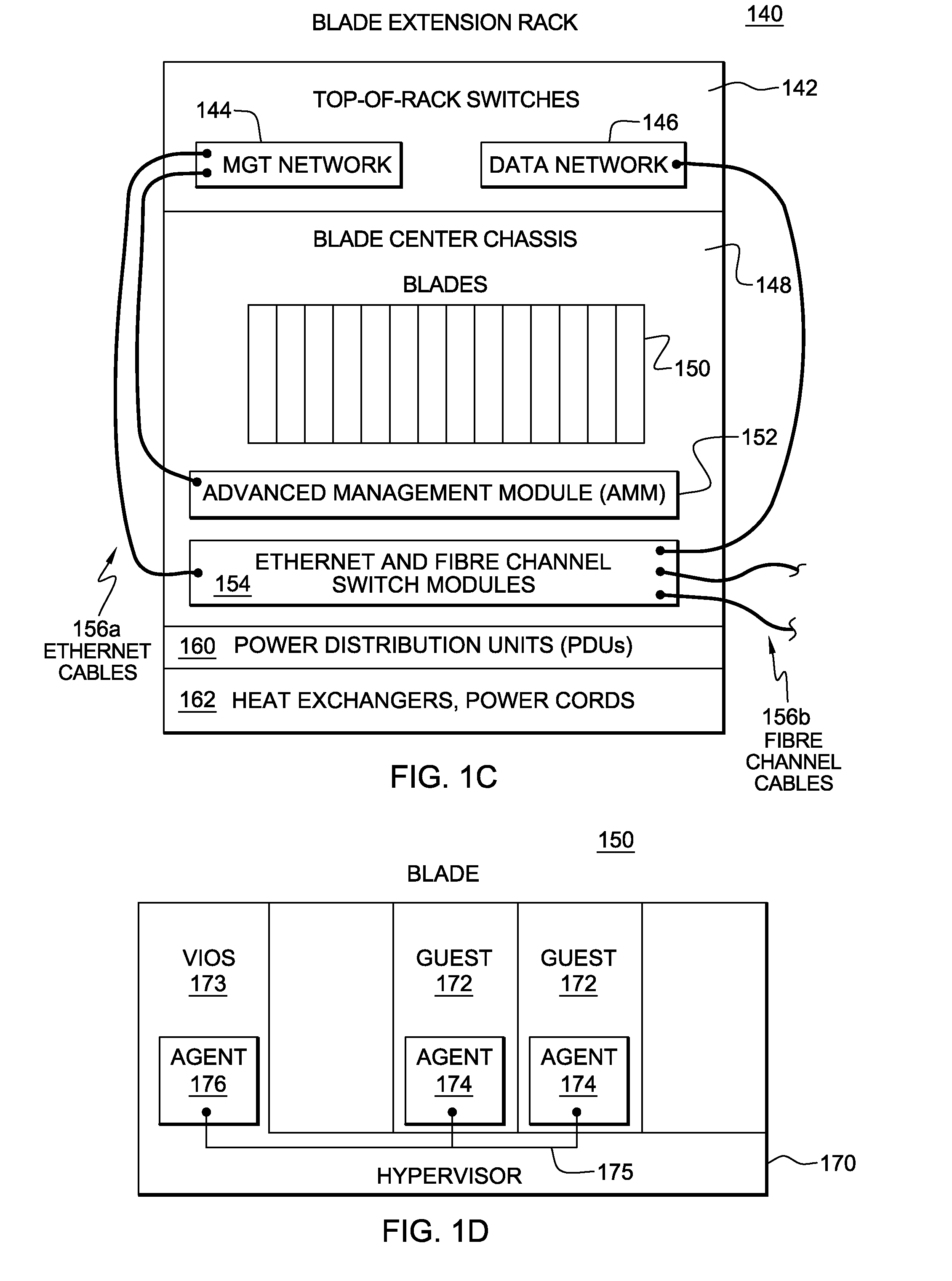
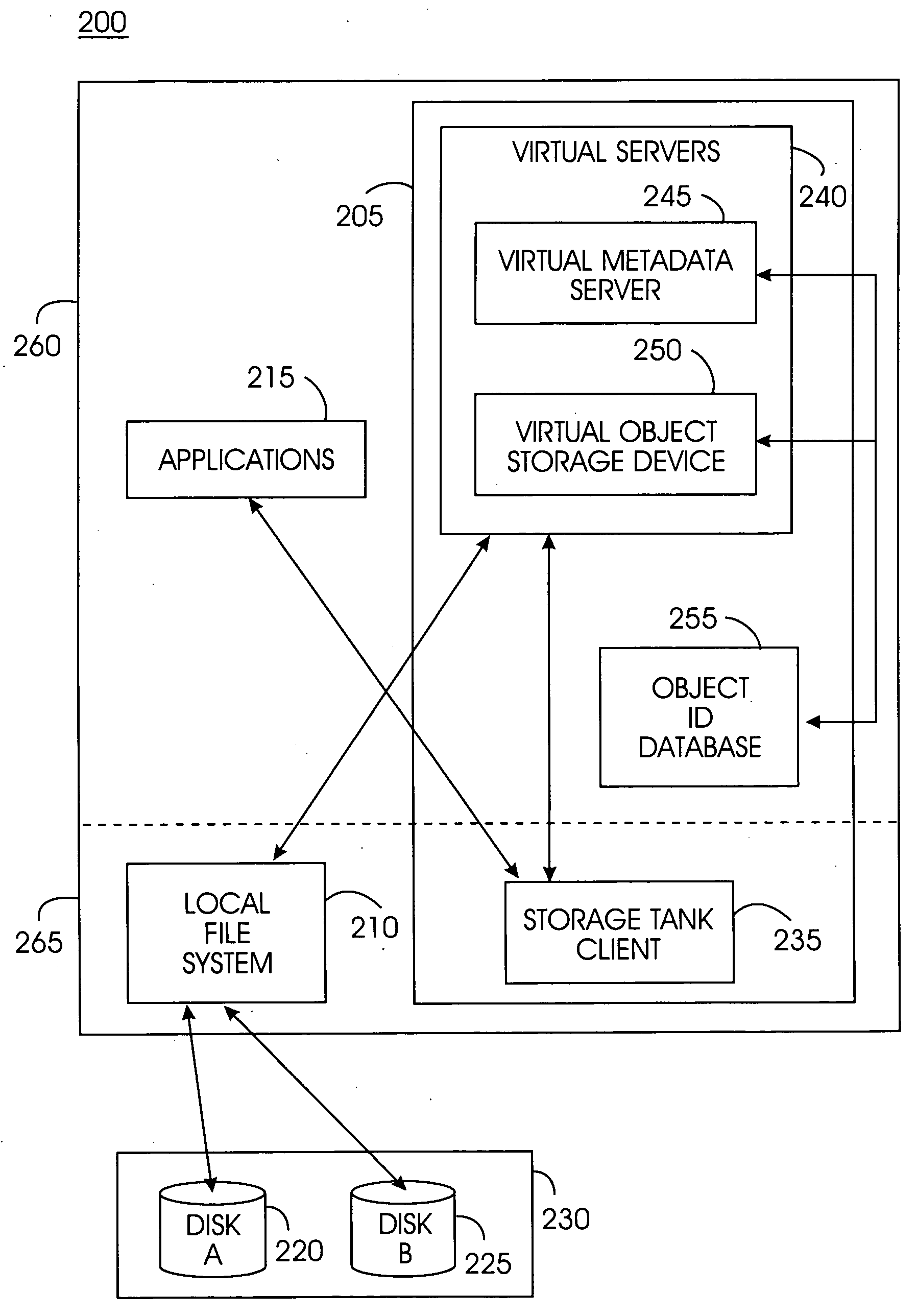
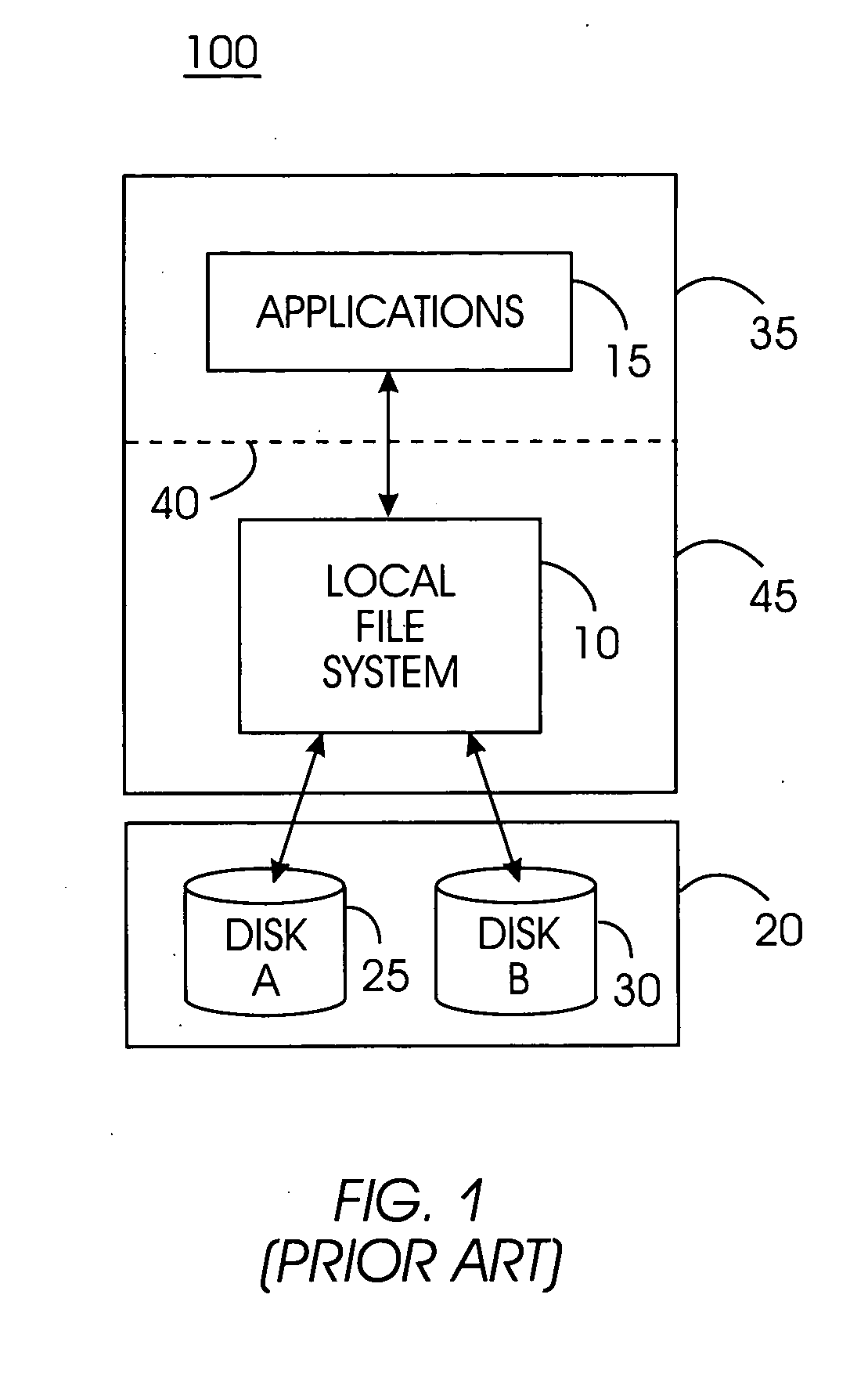
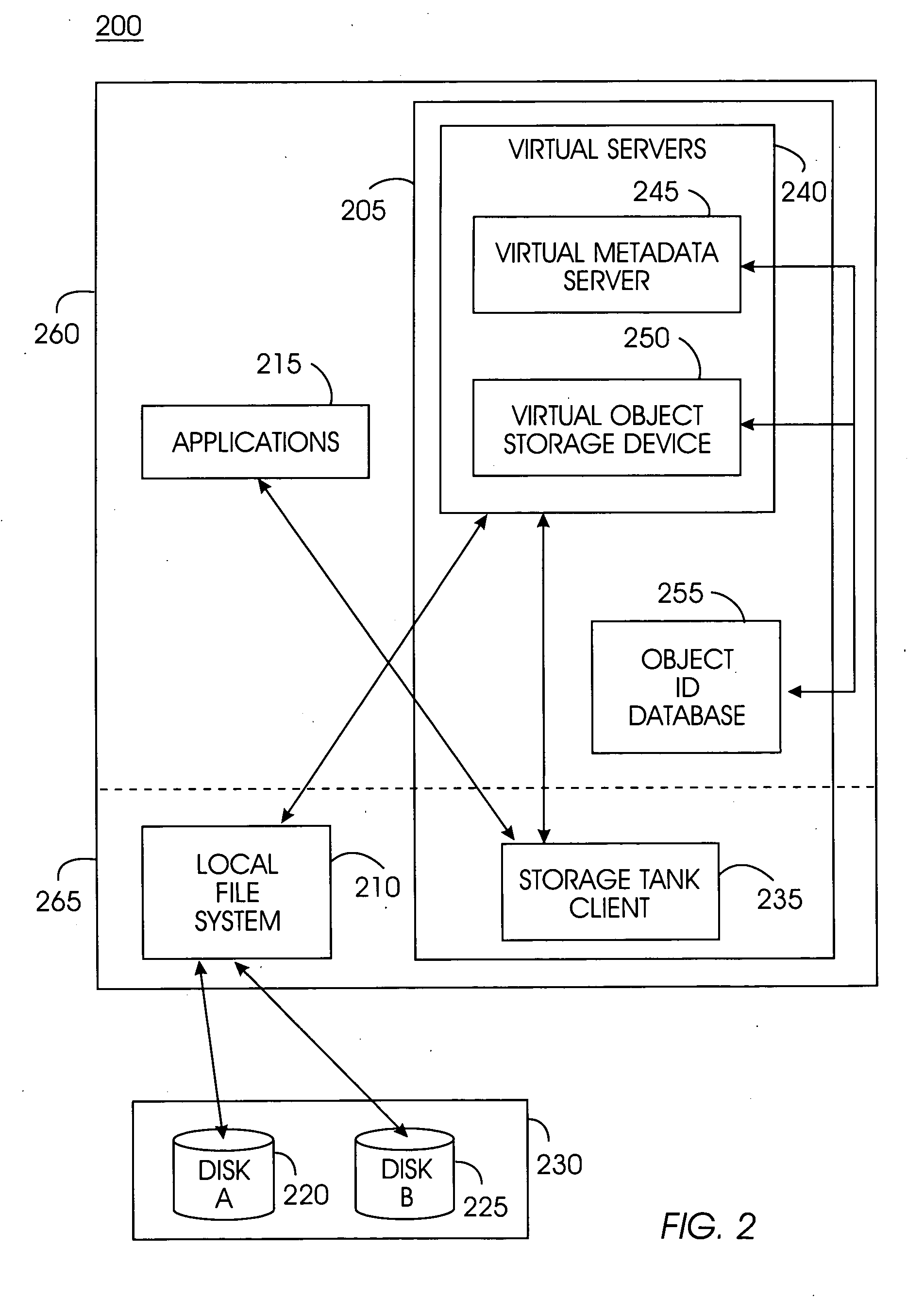
System, method, and service for federating and optionally migrating a local file system into a distributed file system while preserving local access to existing data
ActiveUS20050114291A1Minimal disruptionData processing applicationsDigital data processing detailsFile systemDowntime
Indirect access to local file systems is provided using storage tank protocols, allowing federation of a local file system into a distributed file system while preserving local access to the existing data in the local file system. The goal of the present system is to federate and migrate the data on a computer system with minimum disruption to applications operating on the computer system. Existing applications on a computer system continue to operate during data federation and migration and require little or no reconfiguration either when the data migration starts or when it ends. Data consistency is maintained: existing applications may modify data in the file system during migration or federation. During federation, other computer systems (or hosts) may modify the data in the file system if access control information allows them to do so. All changes in the file system are seen consistently on all hosts. Minimal downtime is required to install the present system and reconfigure the existing applications to communicate with the present system.
Owner:IBM CORP
Maintaining consistency within a federation infrastructure
InactiveUS20080288659A1Well formedInput/output to record carriersDigital data information retrievalComputer scienceComputer program
The present invention extends to methods, systems, and computer program products for a joining node to join a ring of nodes within a rendezvous federation. Embodiments include detecting a neighborhood of nodes on the ring of nodes. The joining node indicates its intent to take id-space ownership for a portion of the id-space between the joining node and a selected immediately adjacent node. The joining node indicates an intent to monitor the selected node. The joining node receives three indications, the first indicating acceptance of the joining node's intent to take id-space ownership for a portion of the id-space between the joining node and the selected node, the second indicating acceptance of the joining node's intent to monitor the selected node, the third indicating the first selected node's intent to monitor the joining node. The joining node indicates acceptance of the selected node's intent to monitor the joining node.
Owner:MICROSOFT TECH LICENSING LLC
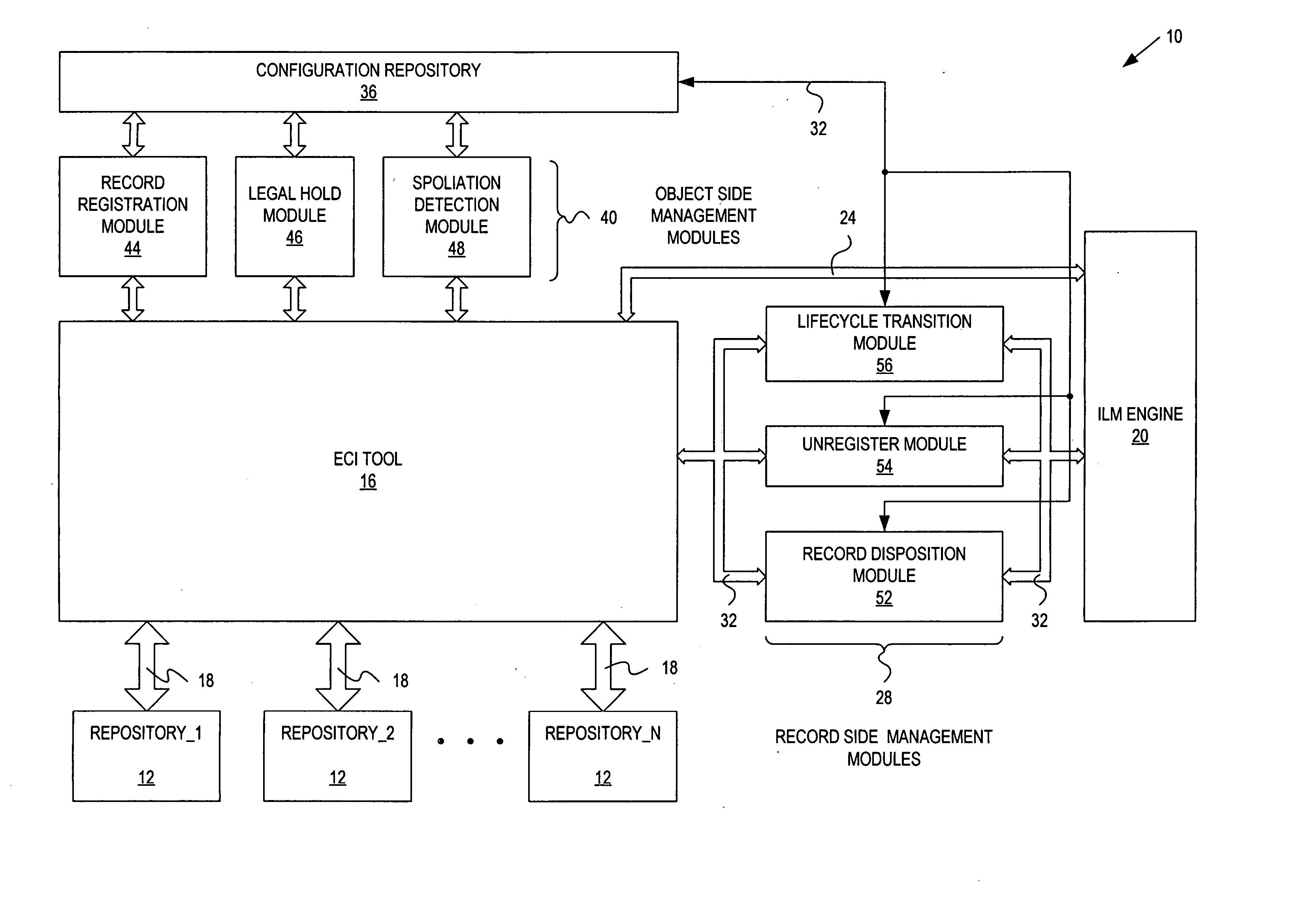
Records management federation
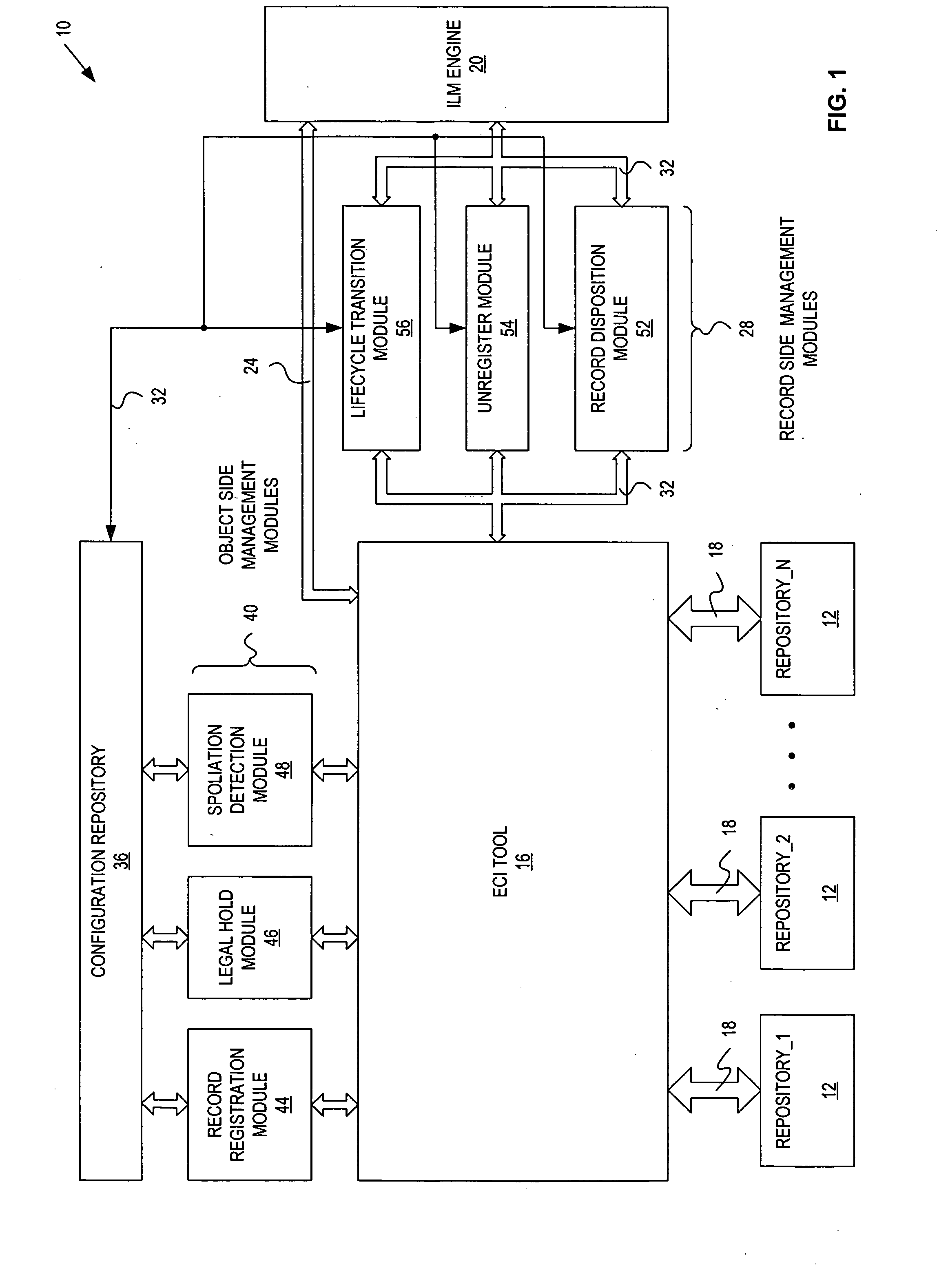
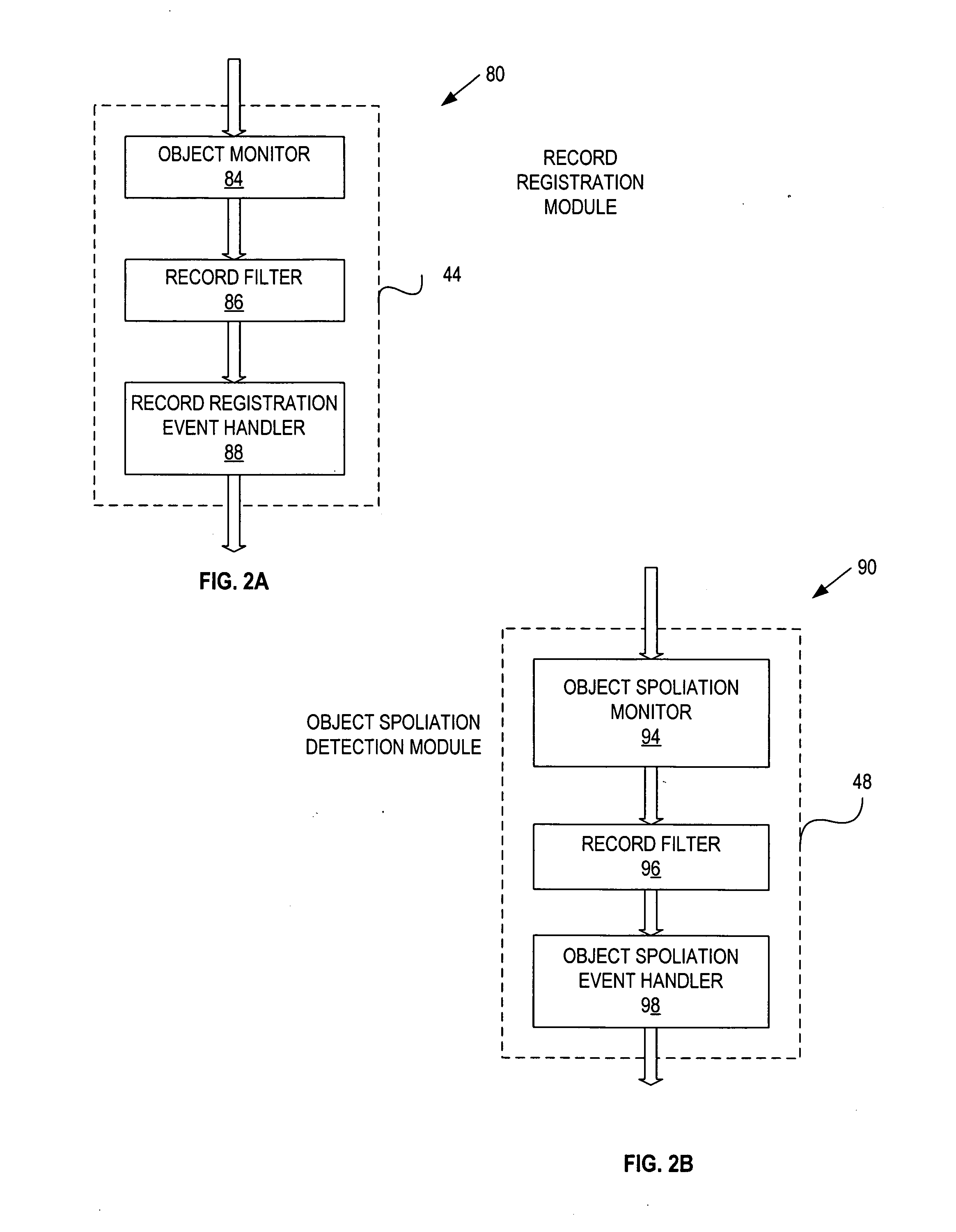
InactiveUS20060230044A1Database updatingDatabase management systemsInformation repositoryRecords management
A record management system includes: a configuration repository providing a mapping between object information and record management information for each of a plurality of record management actions; at least one object side record management module communicatively coupled with an ECI tool, an ILM engine and the configuration repository, and being responsive to object events, and operative to initiate and control at least one of the record management actions based on the mapping provided by the configuration repository; and at least one record side record management module communicatively coupled with the ILM engine and the configuration repository, and being responsive to record events, and operative to initiate and control at least one of the record management actions based on the mapping provided by the configuration repository.
Owner:DATA EMPOWERMENT GRP
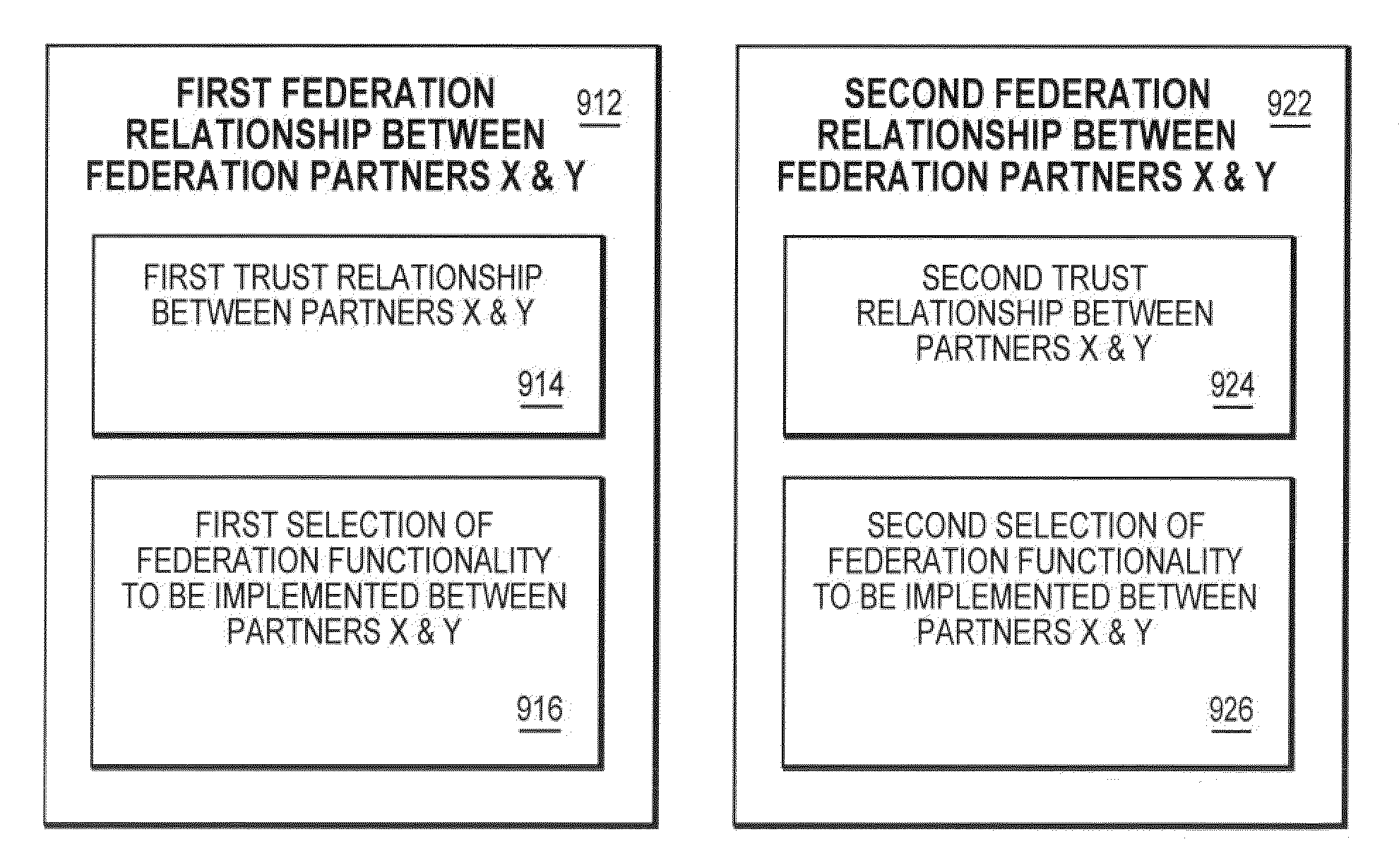
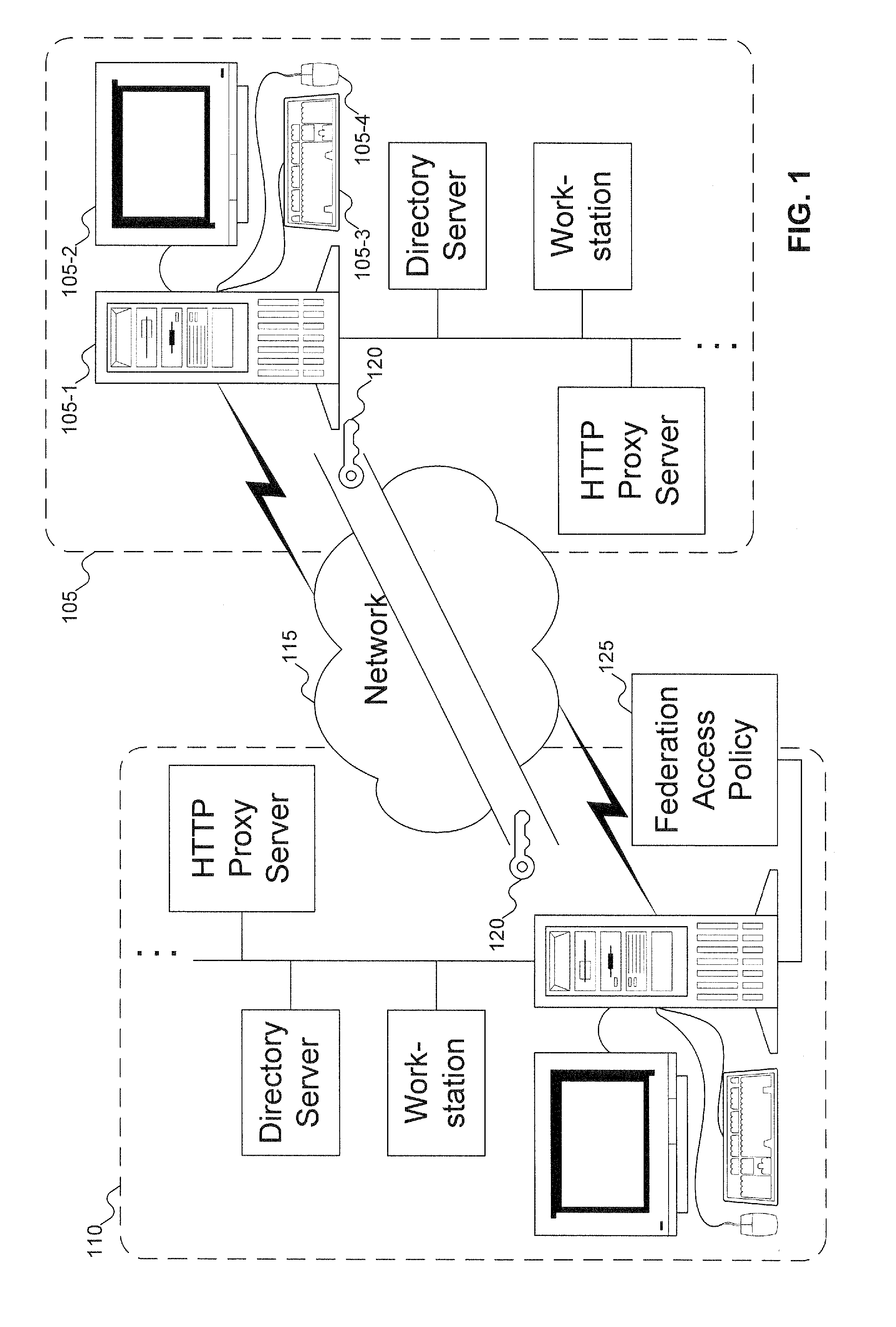
Method and system for establishing federation relationships through imported configuration files
InactiveUS20060021017A1Digital data processing detailsUser identity/authority verificationService provisionTrust relationship
A method is presented in which federated domains interact to complete transactions within a federated environment. A point-of-contact server within a domain relies upon a trust service to manage trust relationships. An administrative user can build a federation relationship between a first service provider and a second service provider, which includes a trust relationship between the first service provider and the second service provider and a selection of federation-related operations, i.e. federation functionality. During configuration of the federation relationship, a file is dynamically generated based on the selection of federation functionality for the federation relationship. The file is exported to the second service provider, which provides additional configuration information by inserting it into the file. The modified file is imported at the first service provider from the second service provider, and the additional configuration information are extracted for subsequent use in federated transactions.
Owner:IBM CORP
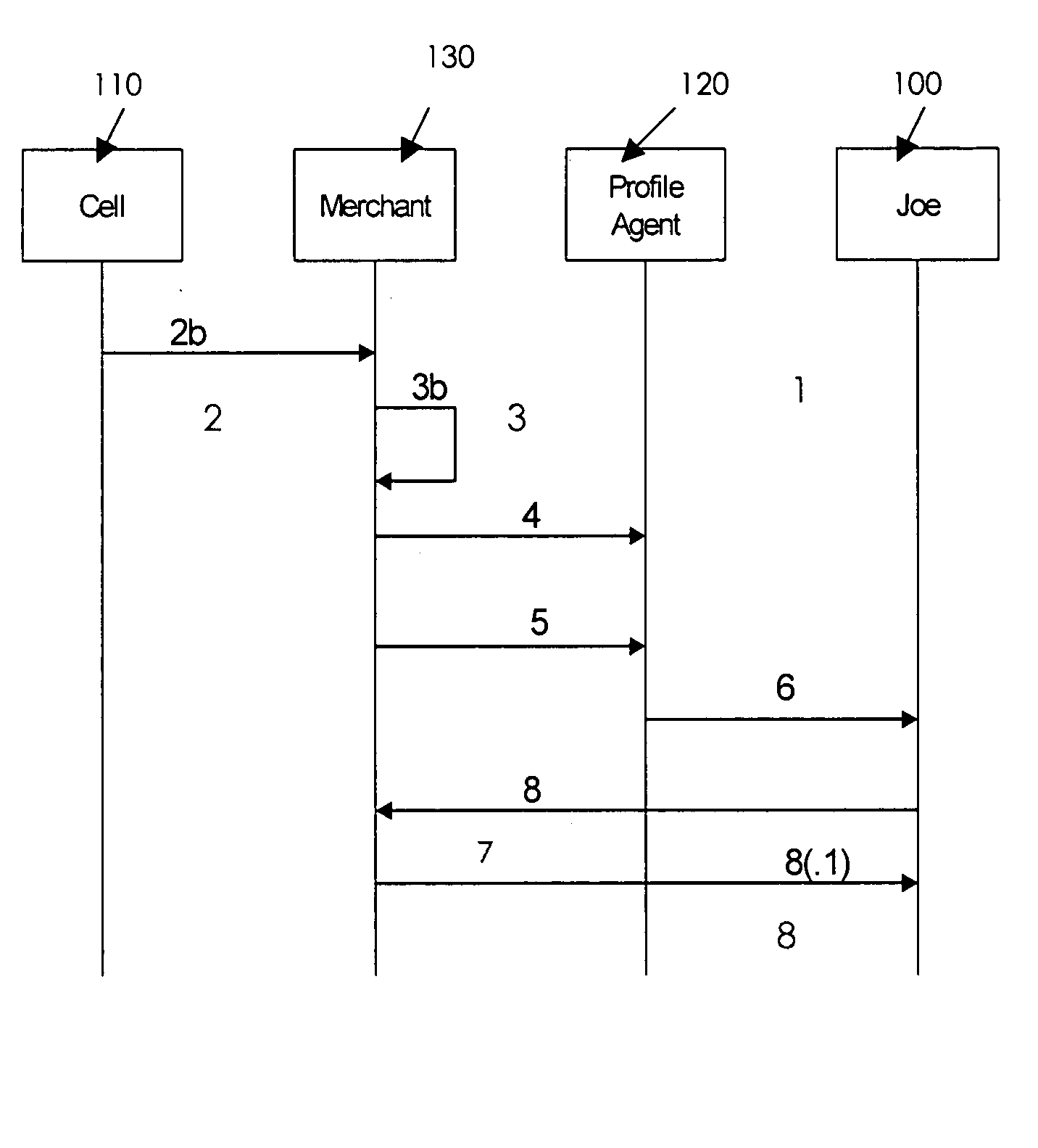
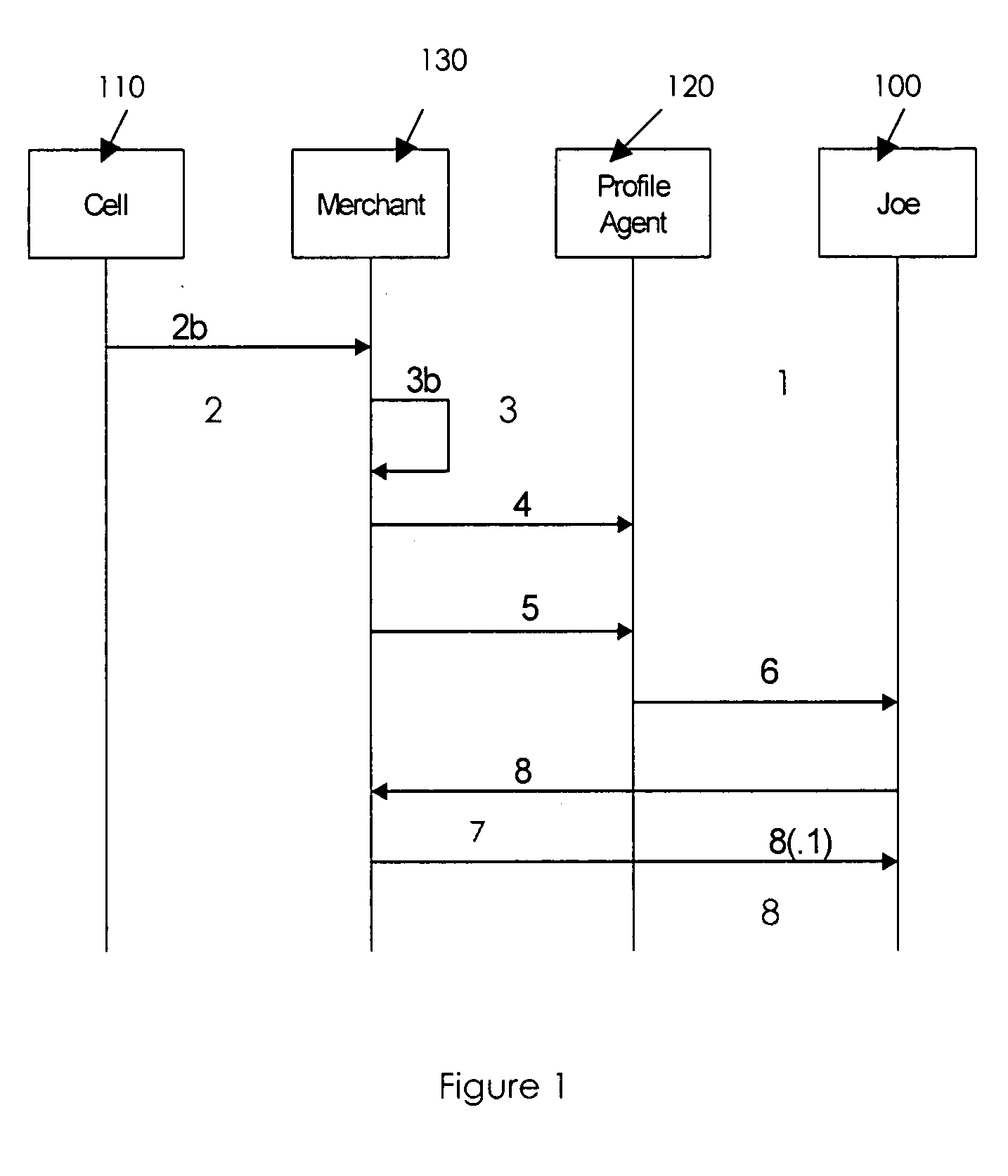
Proxy-based profile management to deliver personalized services
A third-party profile service based on a proxy server model is described, where a user's profile service resides at a URL, in contrast to a profile service that requires federation identity. A profile service is provided that augments location-based services offered by service providers targeting mobile users via, for example, wireless and Wifi Networks. Additional personalization is driven by identity / profile services. Participants in the scenario are not required to share an identity or profile (i.e., static federation is not required). The user establishes a single profile with a trusted provider, hands-off solicitations to a profile agent that operates on behalf of the user to apply policies and preferences. The agent also provides privacy and anonymity (opaqueness).
Owner:AT&T INTPROP I L P
Authentication of a principal in a federation
InactiveUS20070143829A1Increase flexibilityRandom number generatorsUser identity/authority verificationIdentity providerAuthentication
Methods, systems, and computer program products are disclosed that give entities flexibility to implement custom authentication methods of other entities for authentication of a principal in a federation by authenticating the principal by an identity provider according to a service provider's authentication policy and recording in session data of the identity provider an authentication credential satisfying the service provider's authentication policy. Authentication of a principal in a federation is also carried out by authenticating the principal by the identity provider according to an identity provider's authentication policy. Authentication of a principal in a federation is further carried out by receiving in the identity provider an authentication request from the service provider, the authentication request specifying the service provider's authentication policy.
Owner:IBM CORP
Method and system for pluggability of federation protocol runtimes for federated user lifecycle management
InactiveUS20060020679A1Highly fashionMultiple digital computer combinationsDigital data authenticationApplication serverTrust relationship
A method and a system are presented in which federated domains interact within a federated environment. Domains within a federation can initiate federated operations for a user at other federated domains. A point-of-contact server within a domain relies upon a trust proxy within the domain to manage trust relationships between the domain and the federation. The point-of-contact server receives incoming requests directed to the domain and interfaces with a first application server and a second application server, wherein the first application server responds to requests for access to controlled resources and the second application server responds to requests for access to federated user lifecycle management functions, which are implemented using one or more pluggable modules that interface with the second application server.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com