Multiple real-time data encryption method for information security assurance in smart community and system
A technology for security assurance and community information, applied in the field of information security, it can solve the problems that the security and reliability of core data cannot be guaranteed, and password transmission is not performed, so as to achieve the effect of improving confidentiality and ensuring security and reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
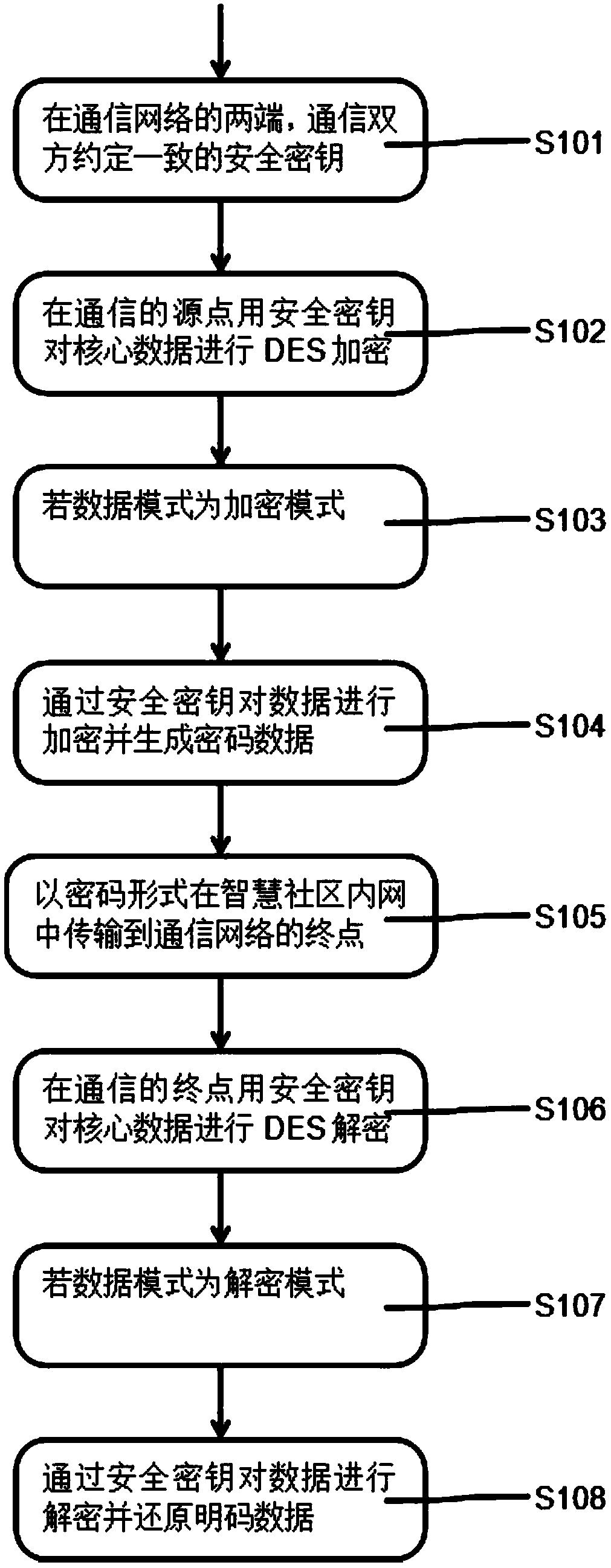
[0054] This embodiment: as figure 1 As shown, a multiple real-time data encryption method for smart community information security assurance, including:
[0055] At both ends of the communication network, both communication parties agree on a consistent security key S101;
[0056] Encrypt the core data with a security key at the source point of the communication with DES S102: if the data mode is the encryption mode S103, encrypt the data with the security key and generate password data S104;
[0057] In the form of password, it is transmitted in the smart community intranet to the end point S105 of the communication network;
[0058] At the end of the communication, use the security key to perform DES decryption on the core data S106: if the data mode is the decryption mode S107, then use the security key to decrypt the data and restore the plaintext data S108.
[0059] Since the two ends of the communication network are used, the two parties agree on the same security key;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com