Internal threat real-time detection method based on agent
A technology of real-time detection and detection system, applied in the field of information system security, can solve problems such as difficulty in guaranteeing practicability, improve agility and reliability, enhance intelligence and adaptive ability, and facilitate real-time detection and operational intervention. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The specific embodiment of the present invention is described below:
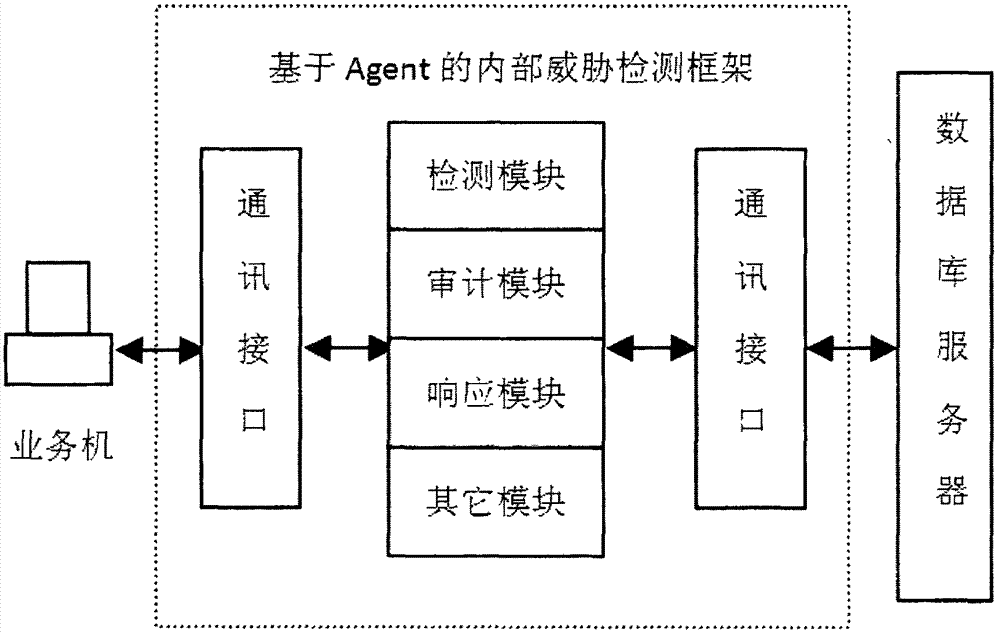
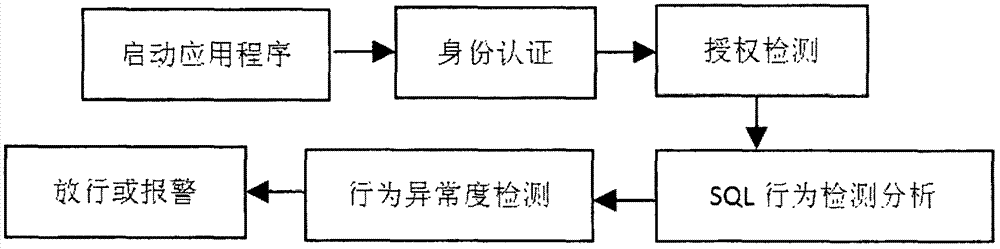
[0026] The specific design idea of the present invention is, before the user accesses the business data on the database server mainframe, the identity and authority of the user are judged by the Agent agent program, and only the user who has passed the authentication can access the data; During the process, the Agent agent monitors the user's behavior in real time and records the user's behavior in the log file; The processing part is signed, so that the user's modification of the business data is non-repudiable.
[0027] system structure
[0028] Logical structure:
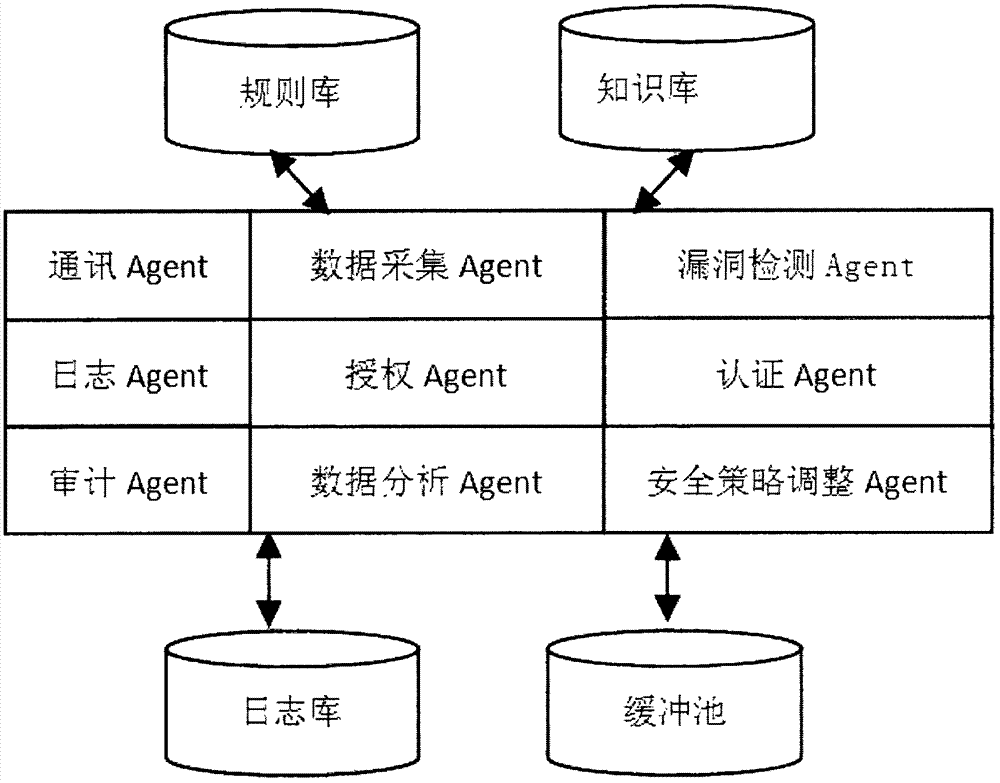
[0029] The logical structure of the Agent agent program is divided into three layers: the first layer is the interface between the detection system and the customer business host, which realizes the communication and data collection with the client; the second layer is the collection of internal security modules of the detection sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com