User authentication and authorization method and system for implementing user authentication and authorization method
A user authentication and user-end technology, applied in the field of communication, can solve the problem that user services and information cannot be effectively guaranteed, and achieve the effect of ensuring security
Active Publication Date: 2011-06-29
王冬梅
View PDF6 Cites 31 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
In the above-mentioned network user authentication method, as long as the user has a mobile phone, the service provided by the network service provider can be used. If the user's mobile phone is lost, stolen or not carried with him, there is a possibility that the person using the mobile phone may not be the user himself. problems, resulting in users' services and information not being effectively guaranteed
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment 1
Embodiment 2
Embodiment 3
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
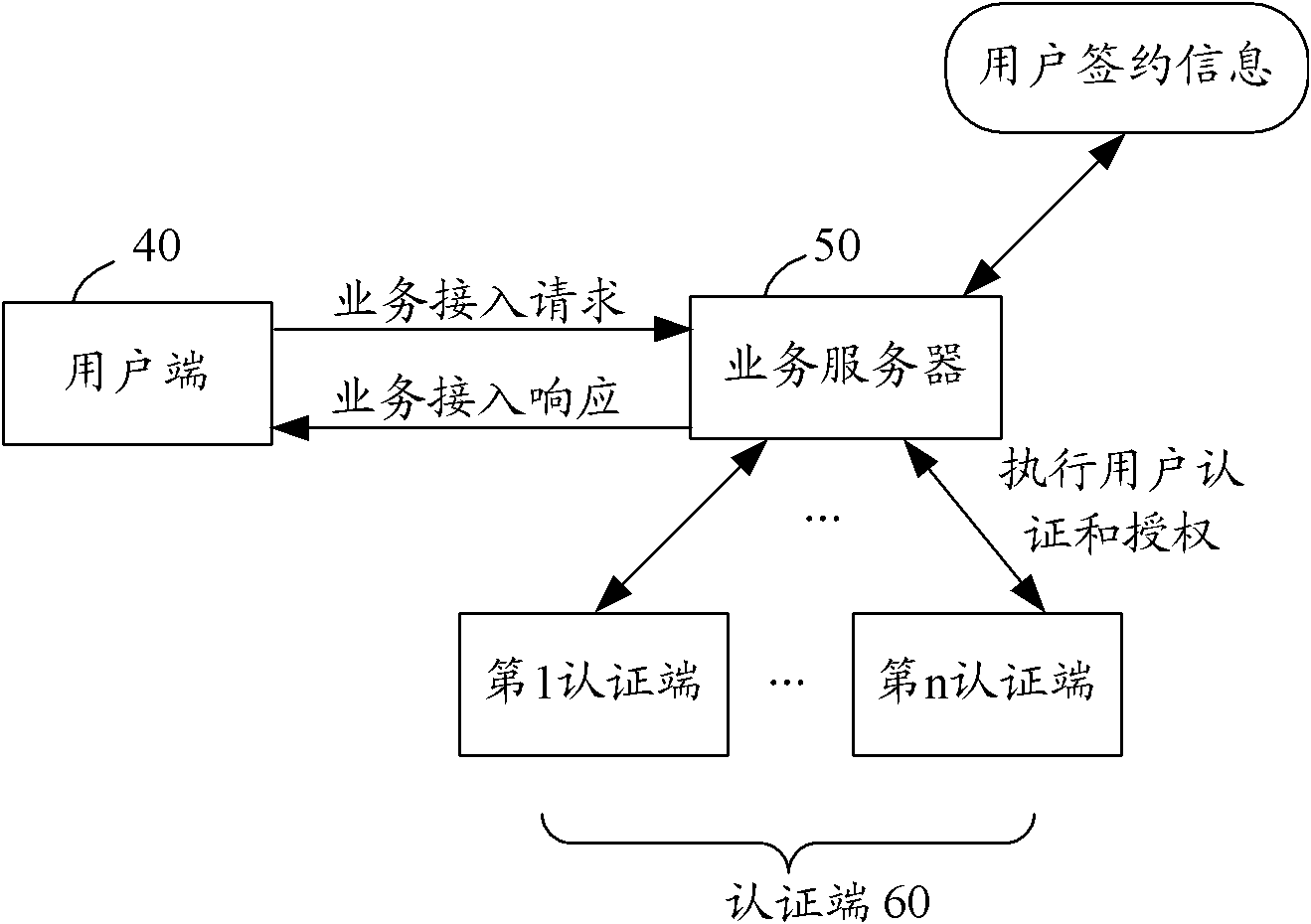
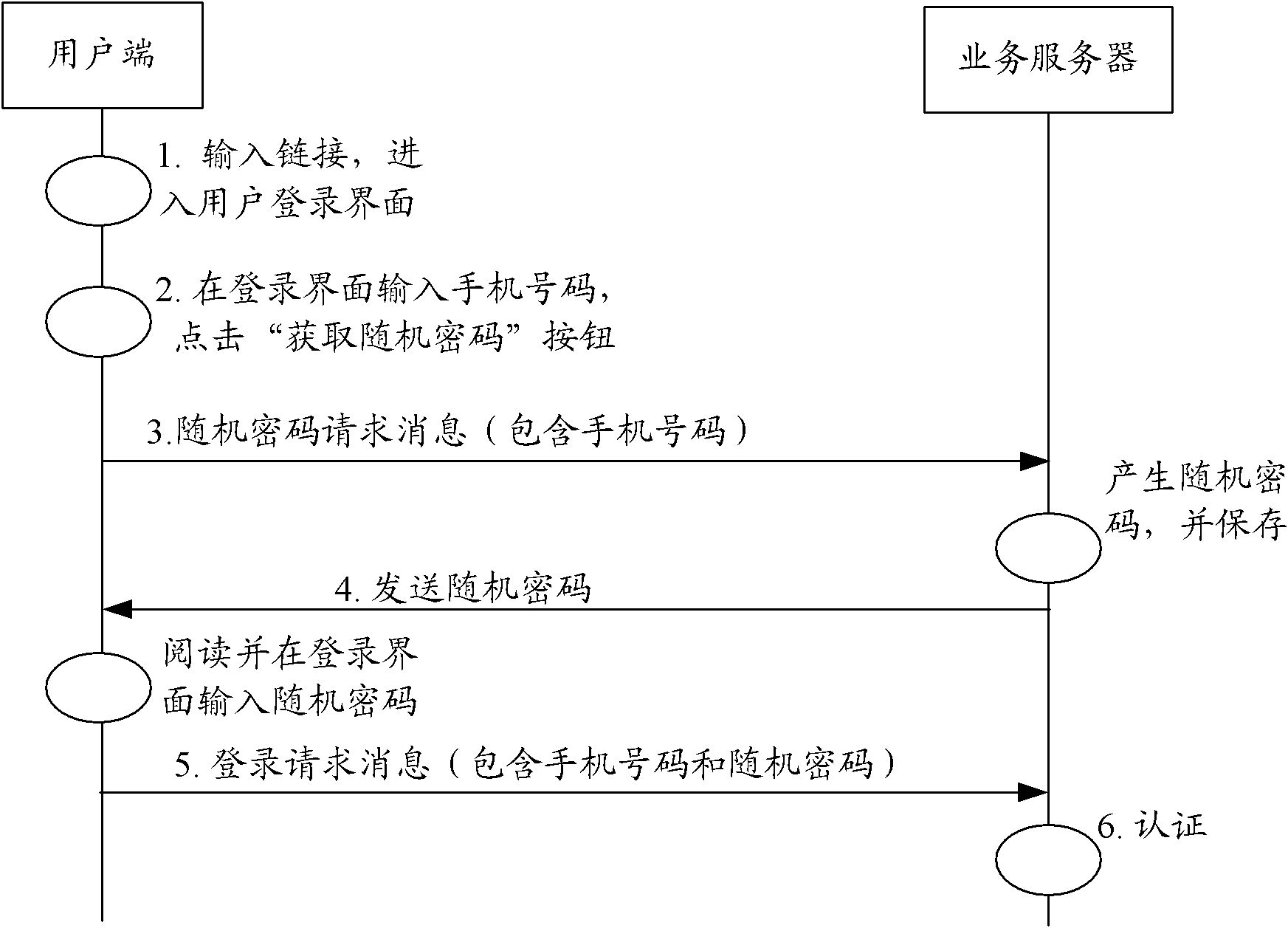
The invention provides a user authentication and authorization method and a system for implementing the user authentication and authorization method. When a user end launches a business access request, a business server checks whether the user is a contracted user in accordance with identity information of the user; if the user is the contracted user based on the user identity information, the communication mode of at least one social relation user is selected from the user contracted information as an authentication end; the business server judges the validity of the user identity in accordance with information provided by the authentication end; and if the user identity is valid, the business server authorizes a user end and carries out corresponding business access responses. The method and the system for implementing the method provided by the invention are used to overcome the defects in a background technology and effectively ensure the security of user information and network services by using a mode that the communication mode of at least one social relation user is selected from the contracted information which is kept at the time of signing a business service by the user as the authentication end, and the business server judges the validity of the user end identity in accordance with the information provided by the authentication end and authorizes the user end.
Description
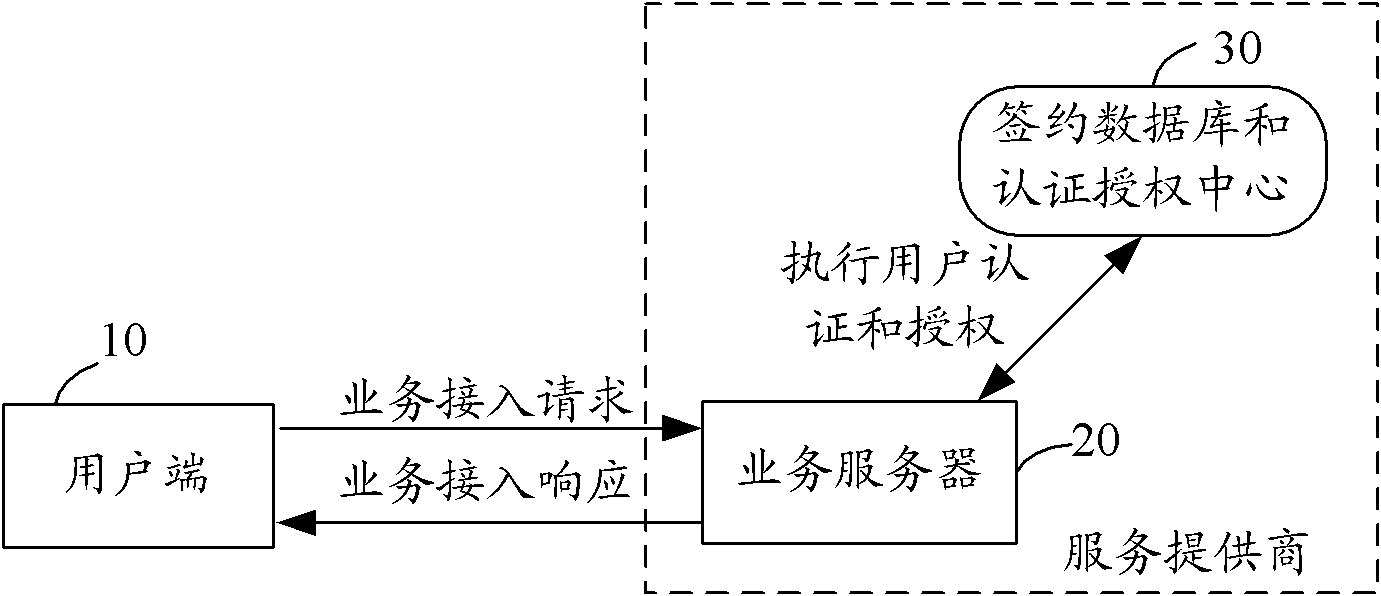
A method of user authentication and authorization and its realization system technical field The invention relates to the field of communication technology, in particular to a method for user authentication and authorization and a system for realizing it. Background technique While the popularity of network technology has brought great convenience to users, there are also problems of how to authenticate the legitimacy of user identities in the network, and how to ensure that users' services and information are not illegally stolen and used. As shown in Figures 1 and 2, general service providers have their own independent authentication and authorization centers in their networks responsible for managing subscriber information. After a user signs a contract, the authentication and authorization center stores the user's subscription information. When a user initiates a service access request, the service server performs user authentication through the authentication and a...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L9/32H04L29/06
CPCH04L9/321H04L63/102H04L63/08
Inventor 王冬梅
Owner 王冬梅
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com