Patents
Literature
68results about How to "Login security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
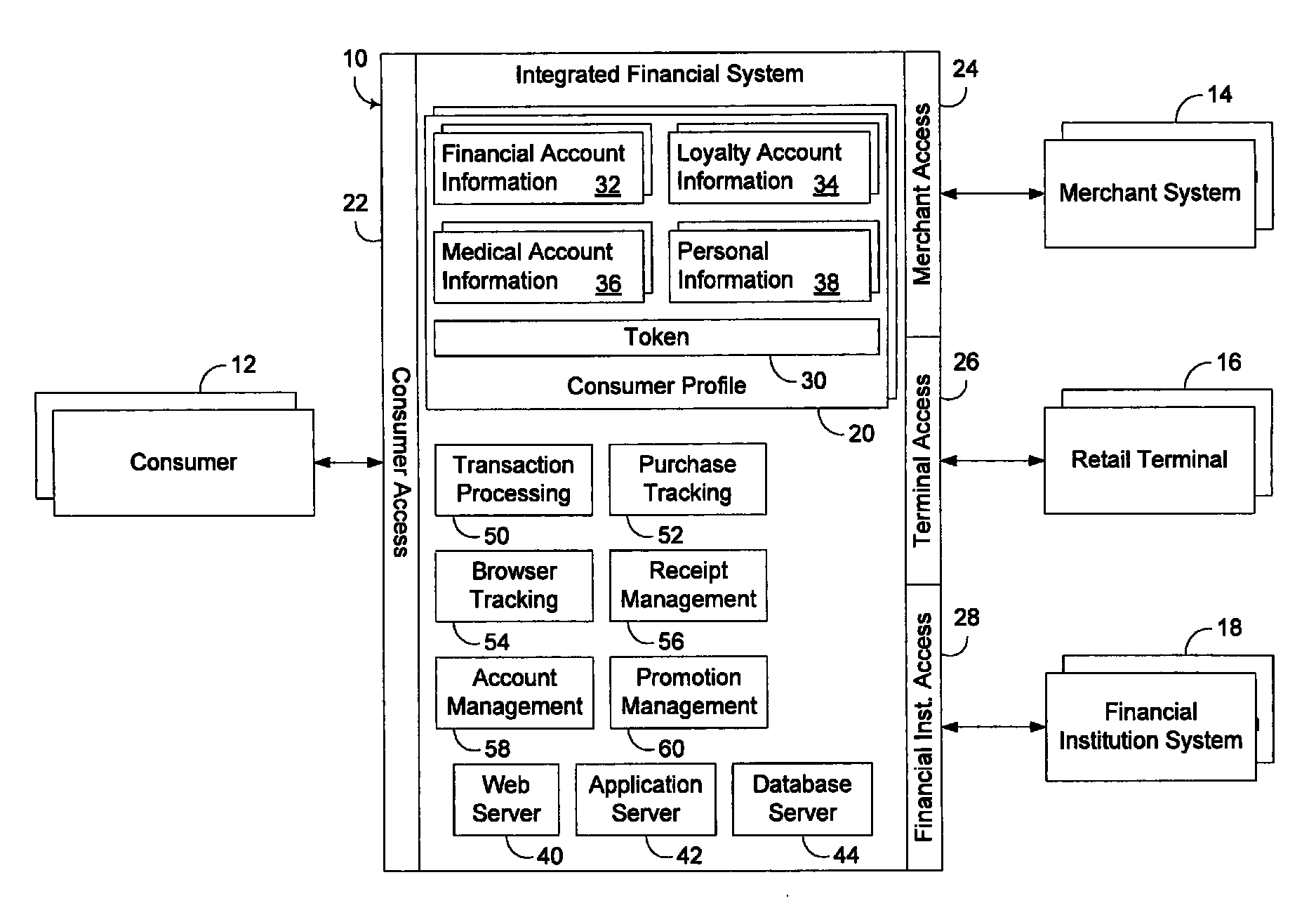
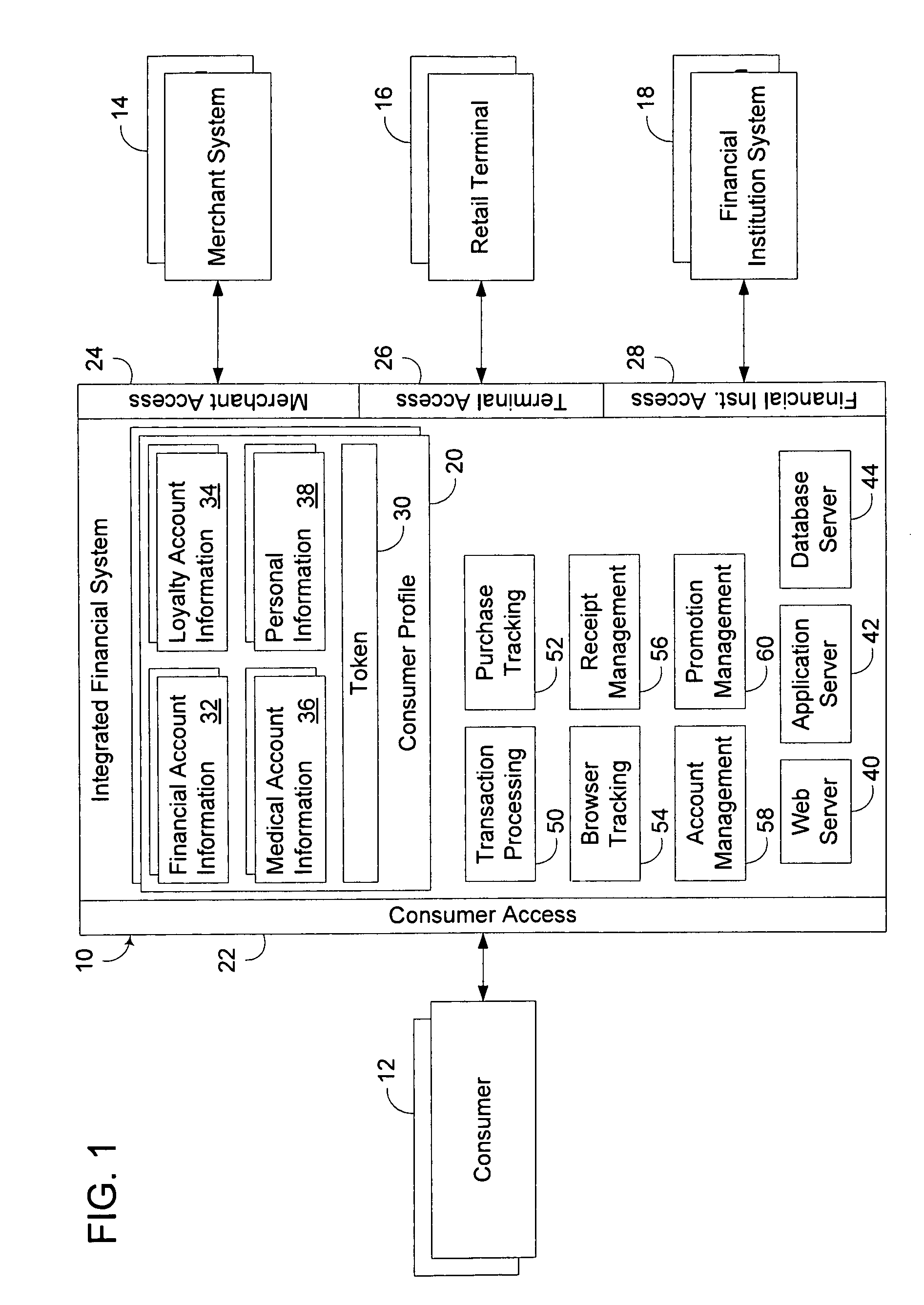
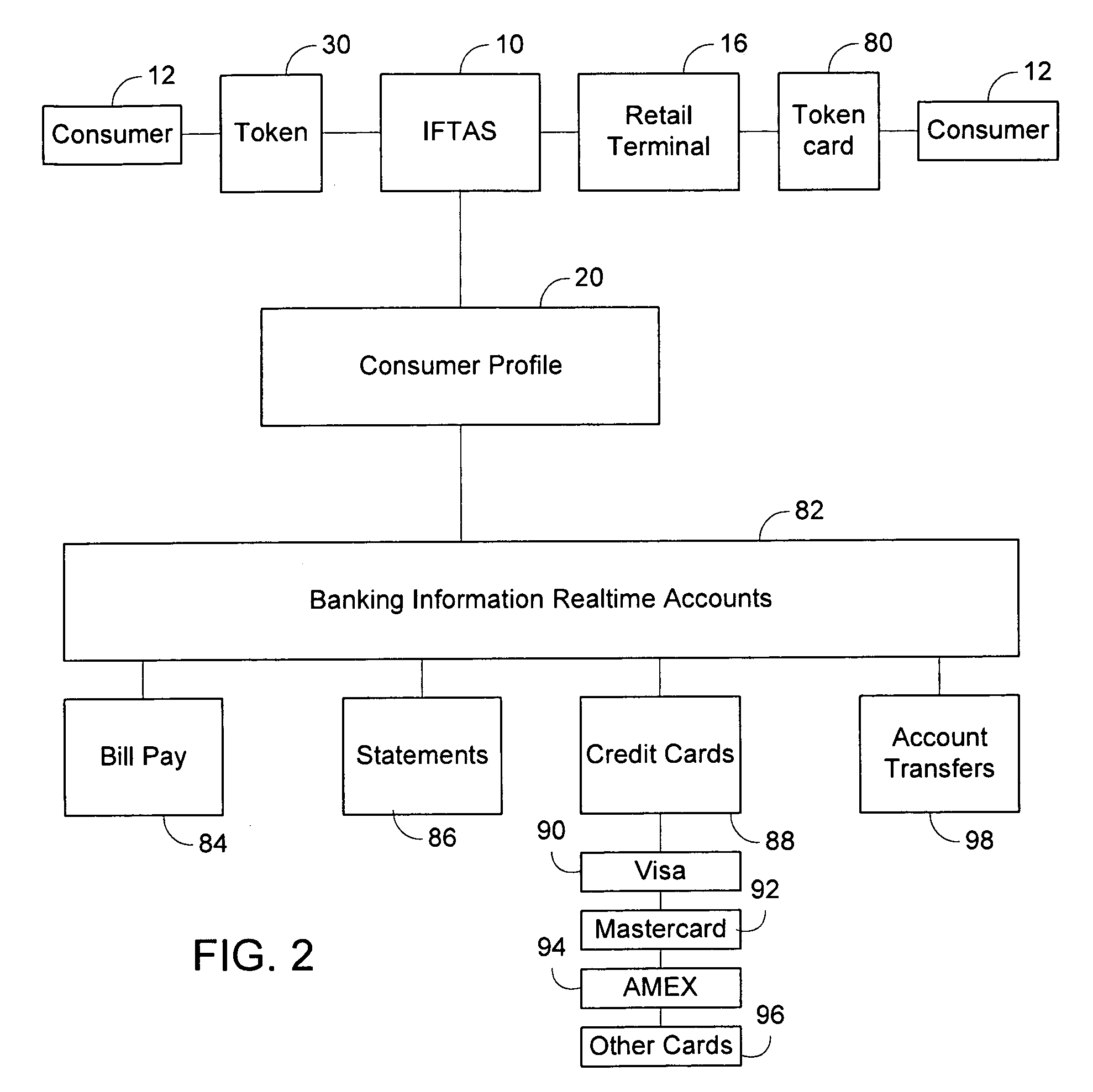
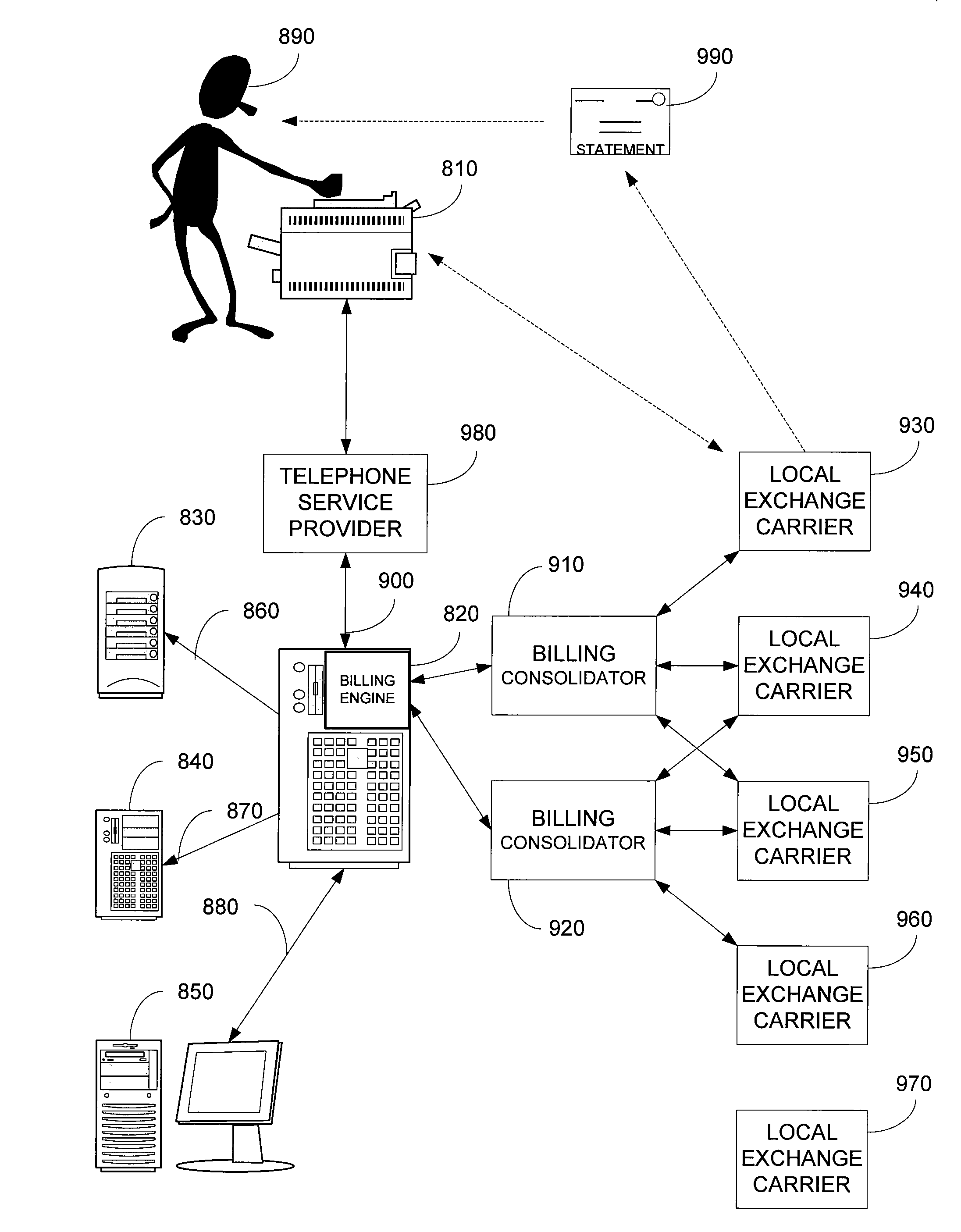
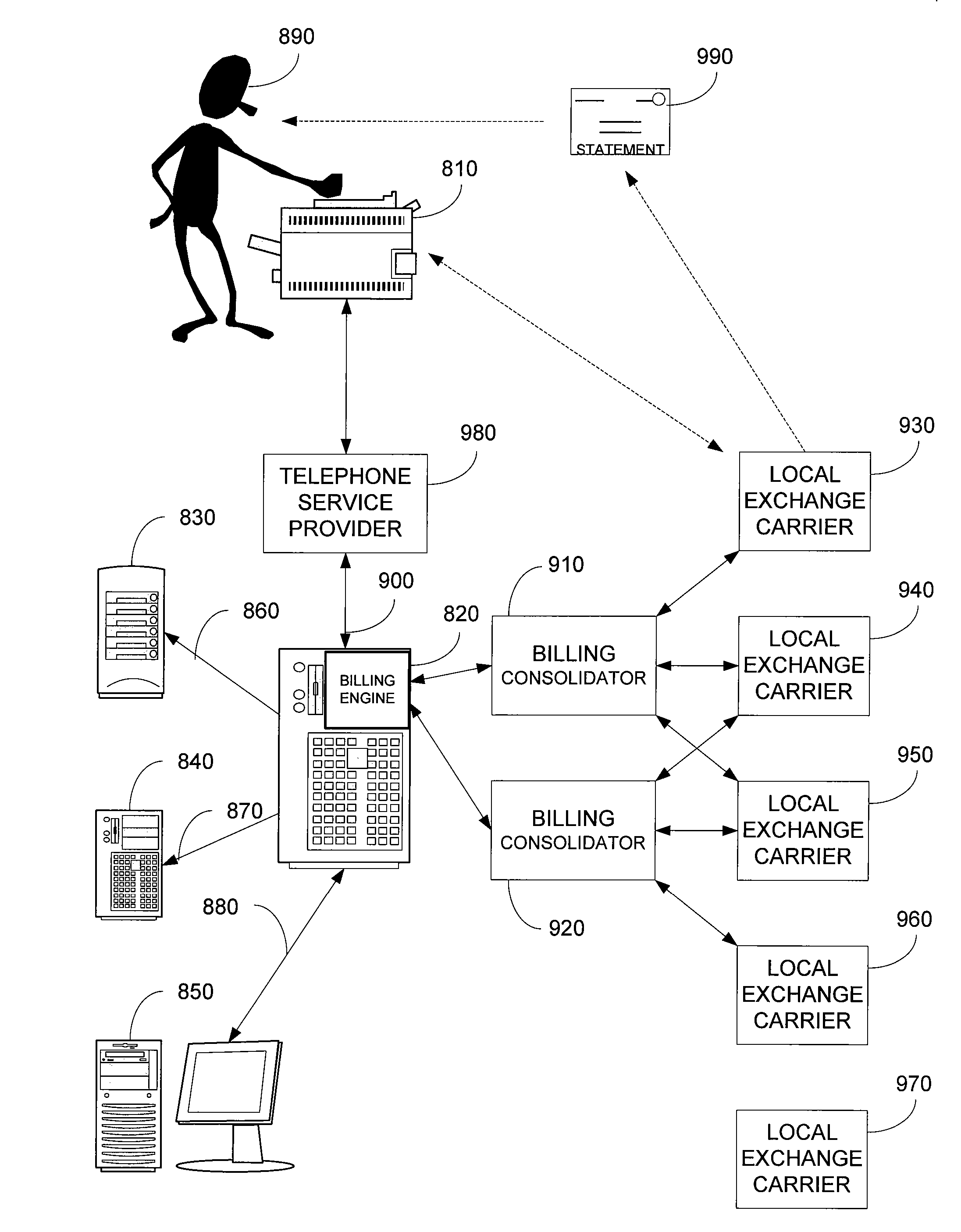
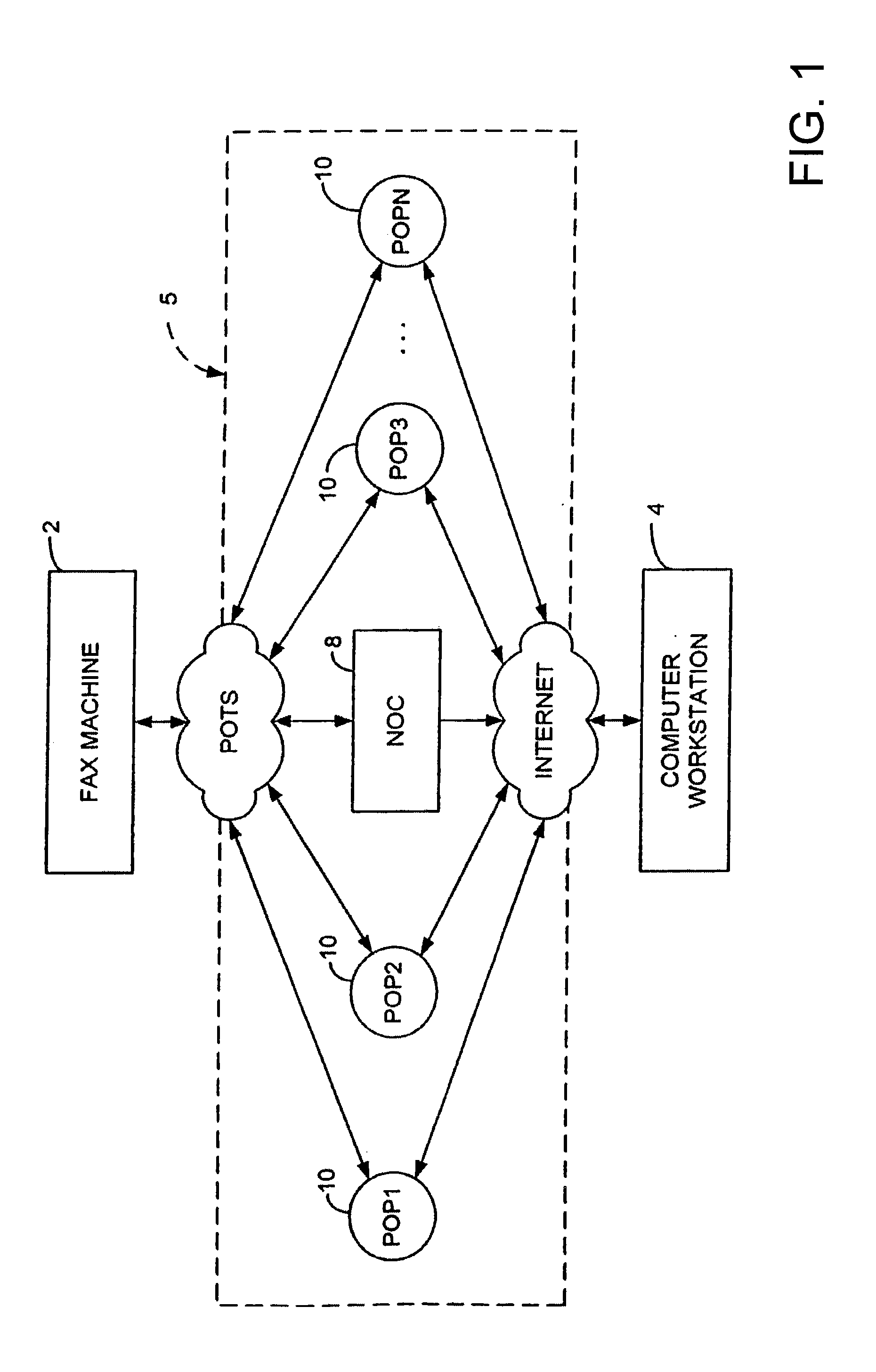
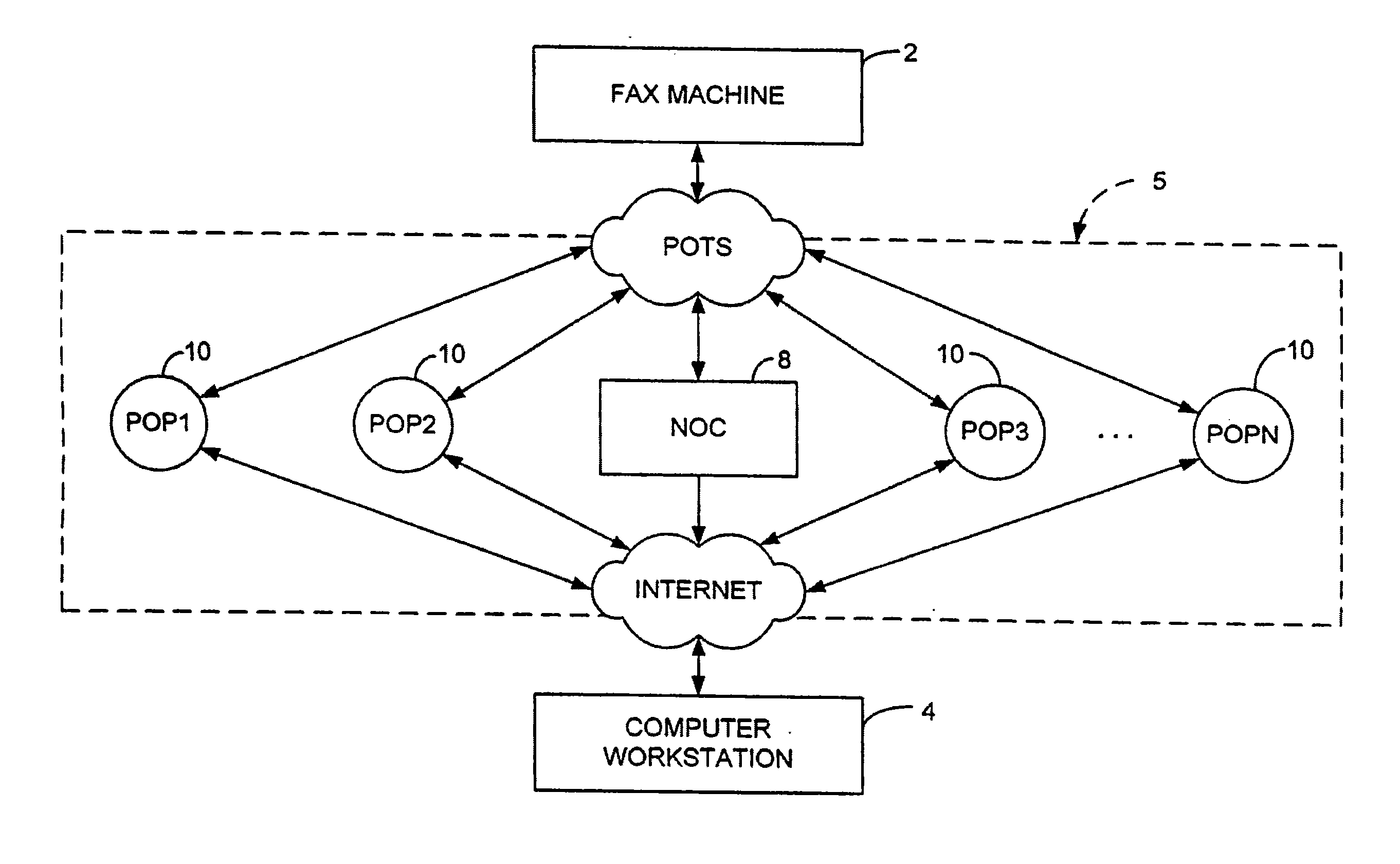
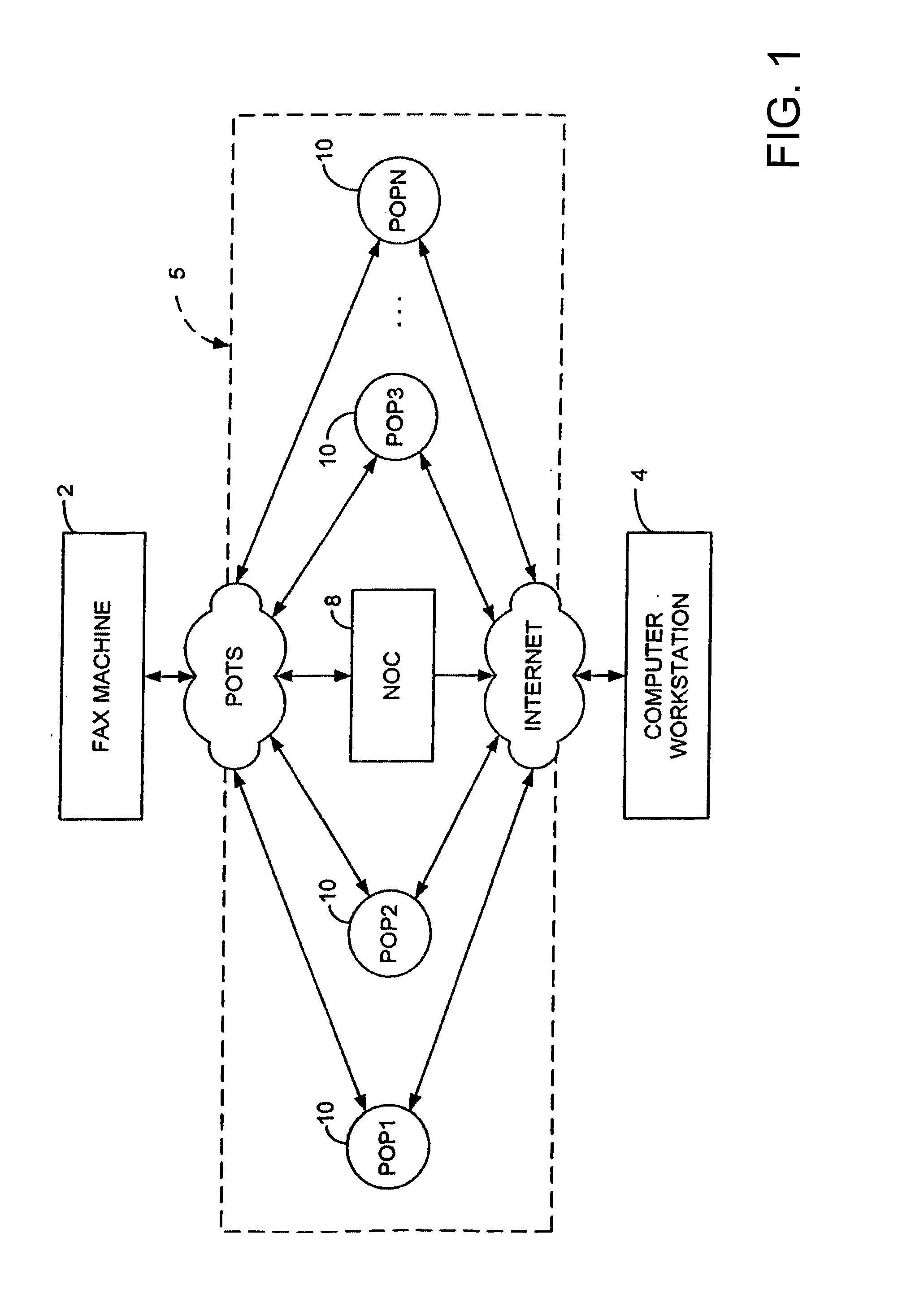
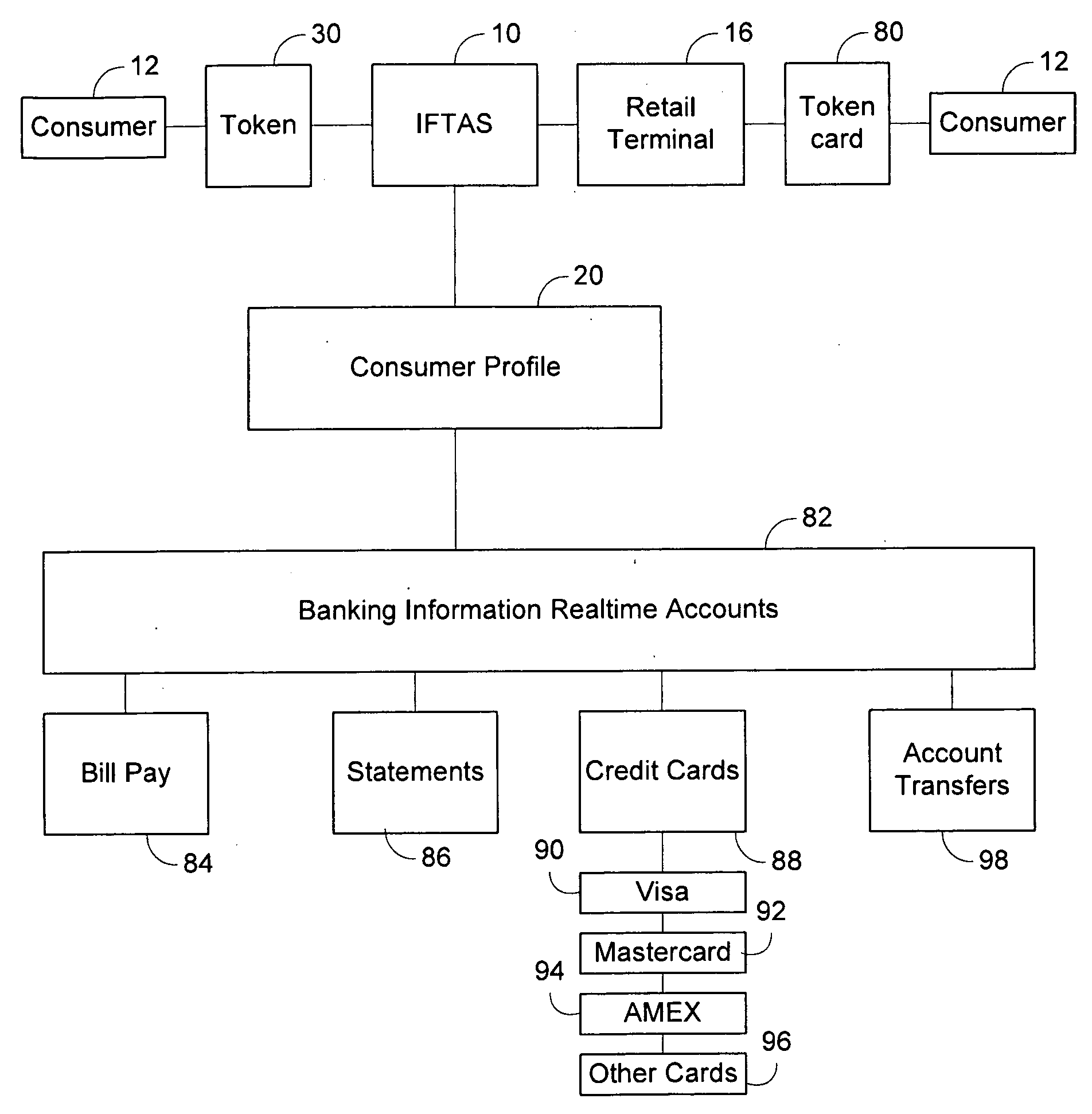
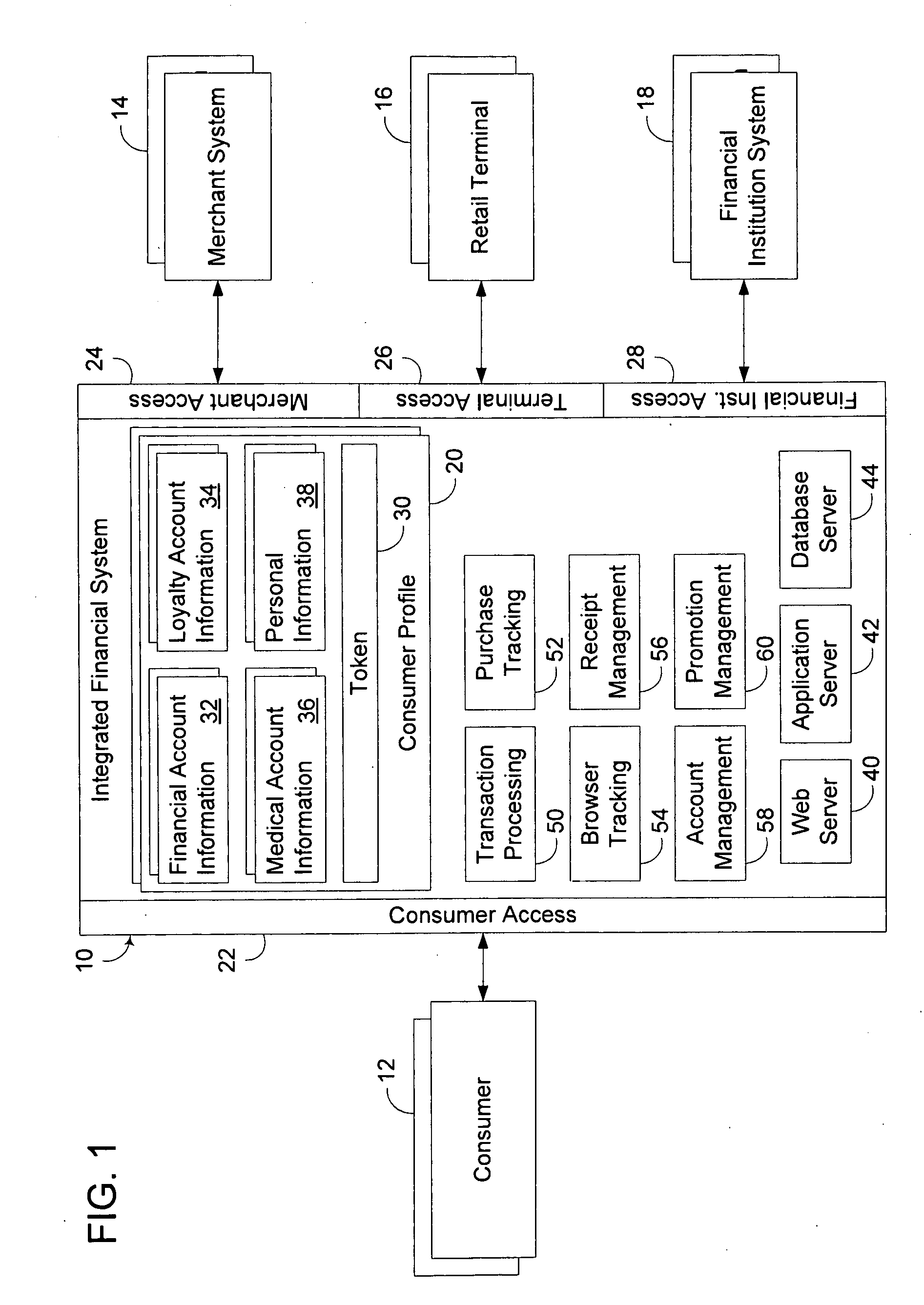
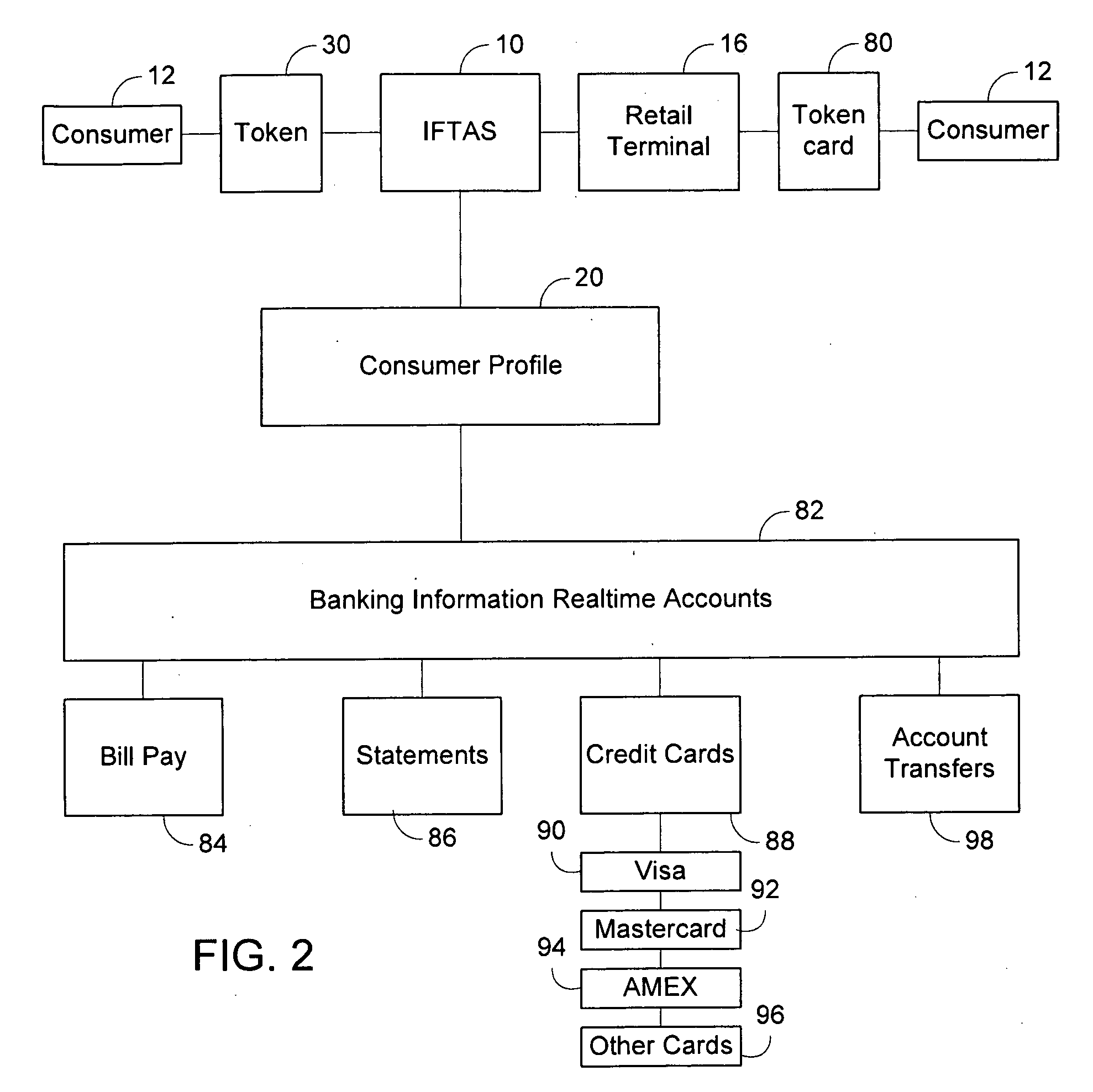
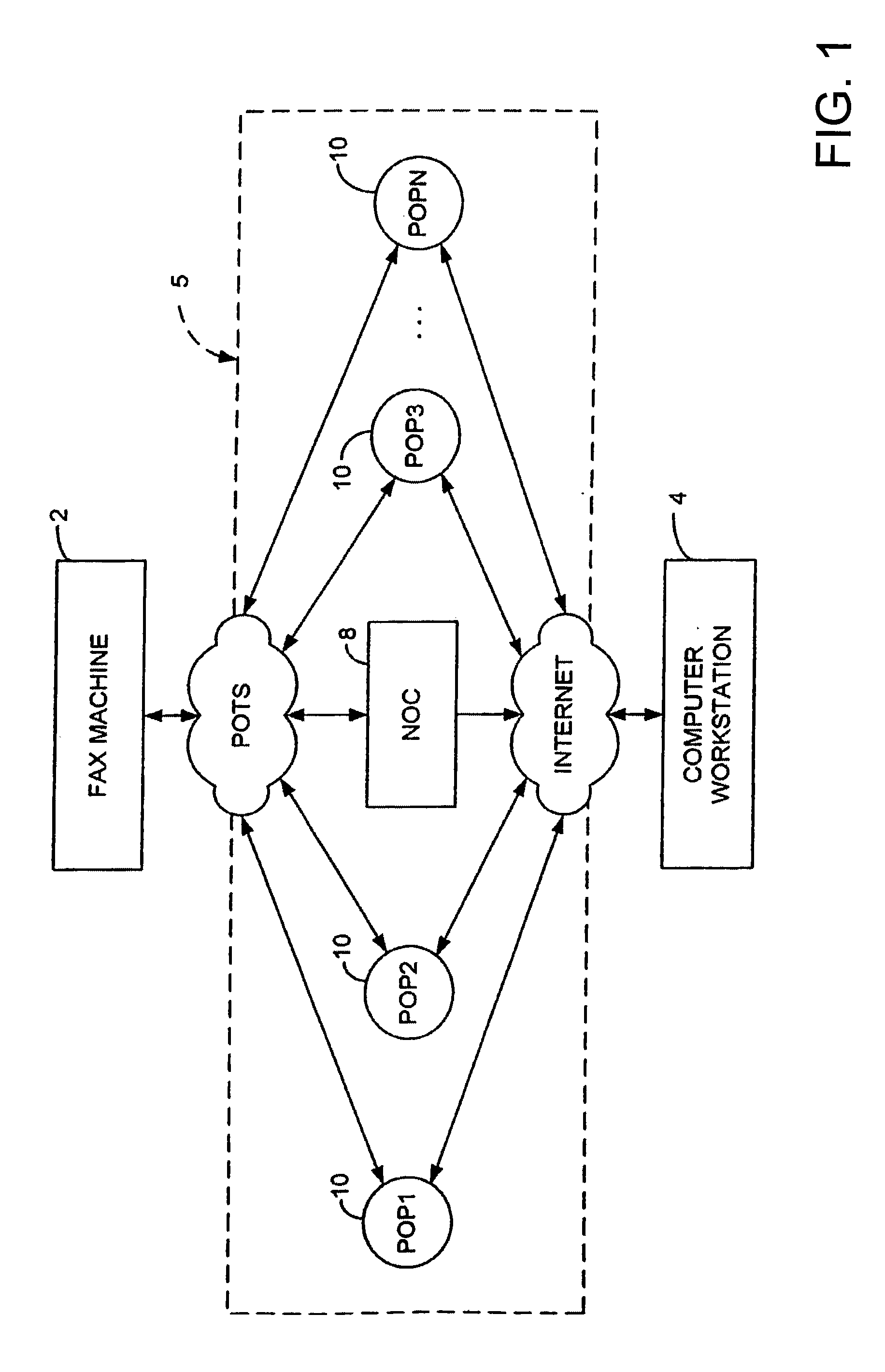
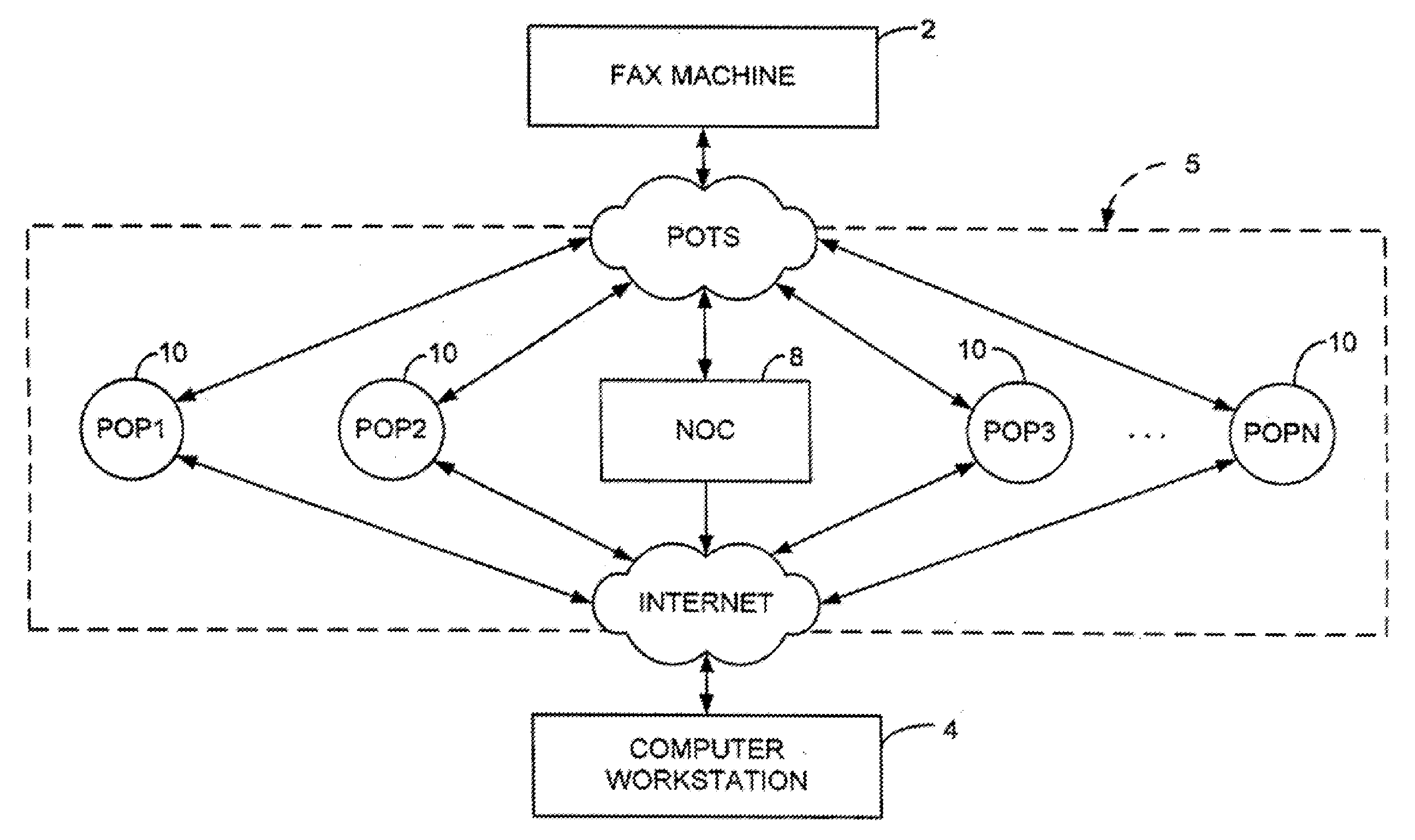
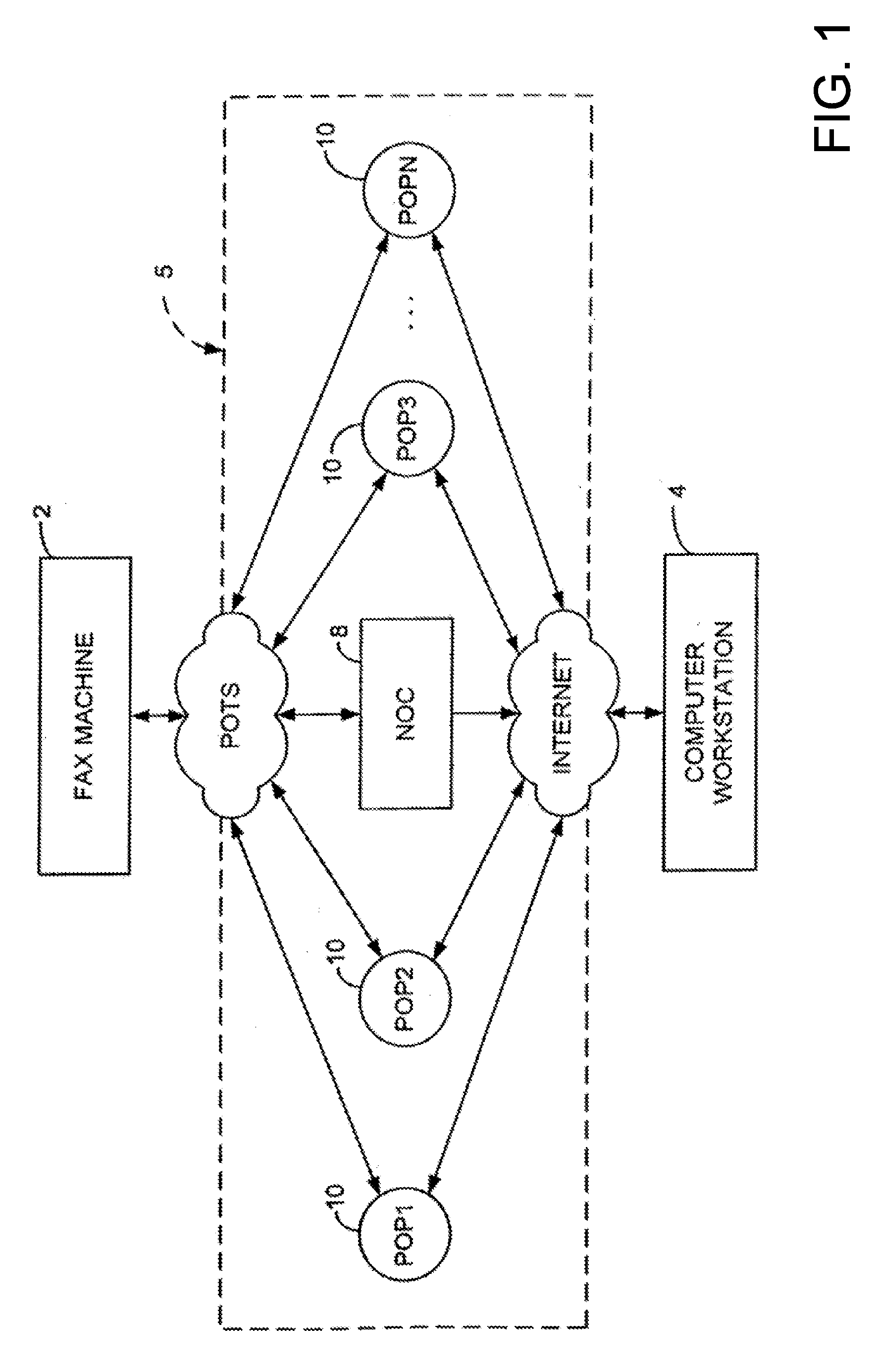
Integrated financial transaction and access system
InactiveUS8261974B2Improve abilitiesEasy to useComplete banking machinesFinanceRelevant informationInternet privacy
A universal digital information management and transaction system facilitates a consumer's ability to organize, use and obtain personal data related to a consumer, including for example, the consumer's financial, health, and personal records. A consumer is provided with an online profile that stores all of the relevant consumer information, with a token associated with the consumer's profile to enable the consumer to securely login remotely to the system to access and manage all of their relevant information.
Owner:HULL ROBERT E
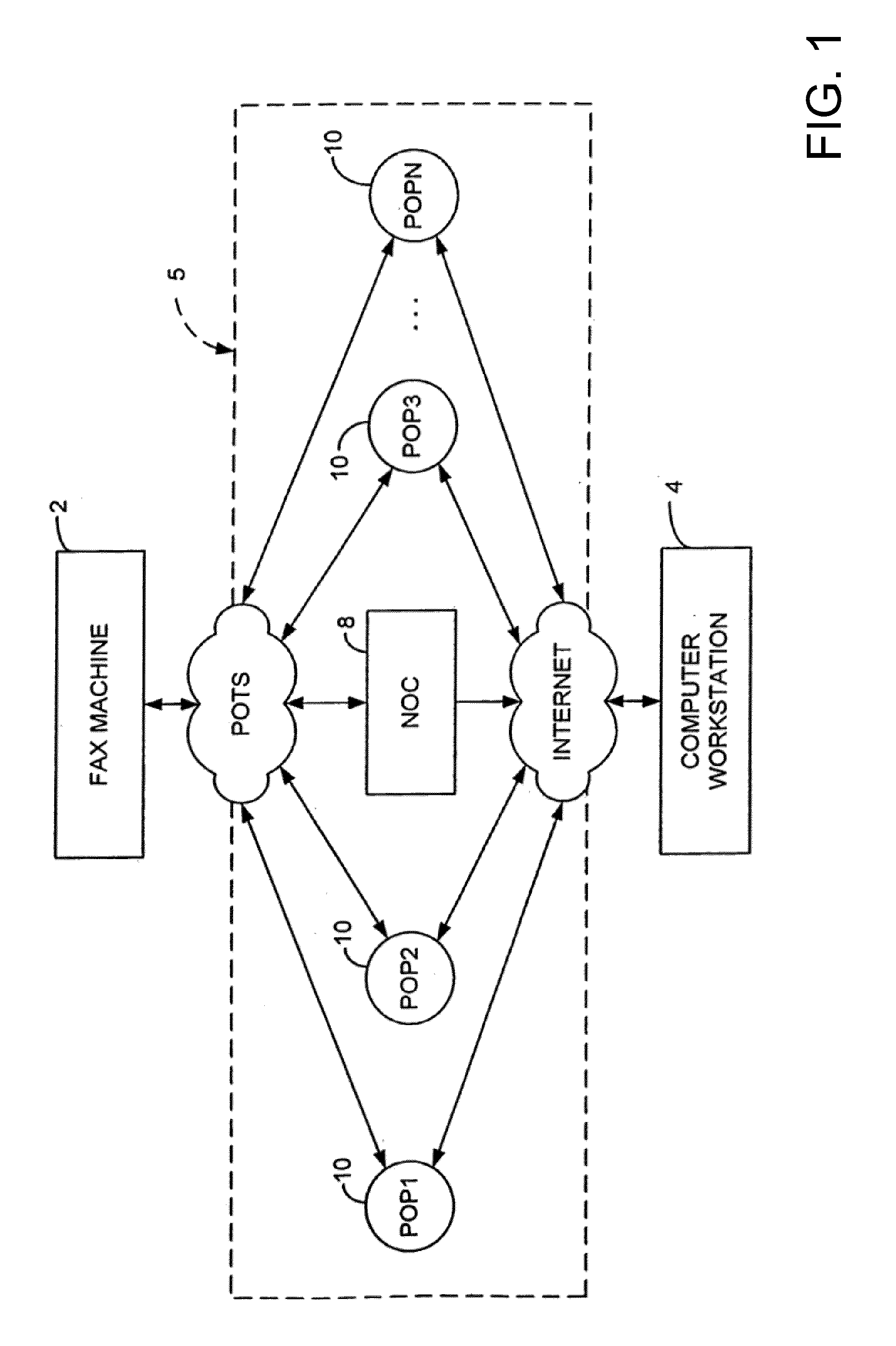
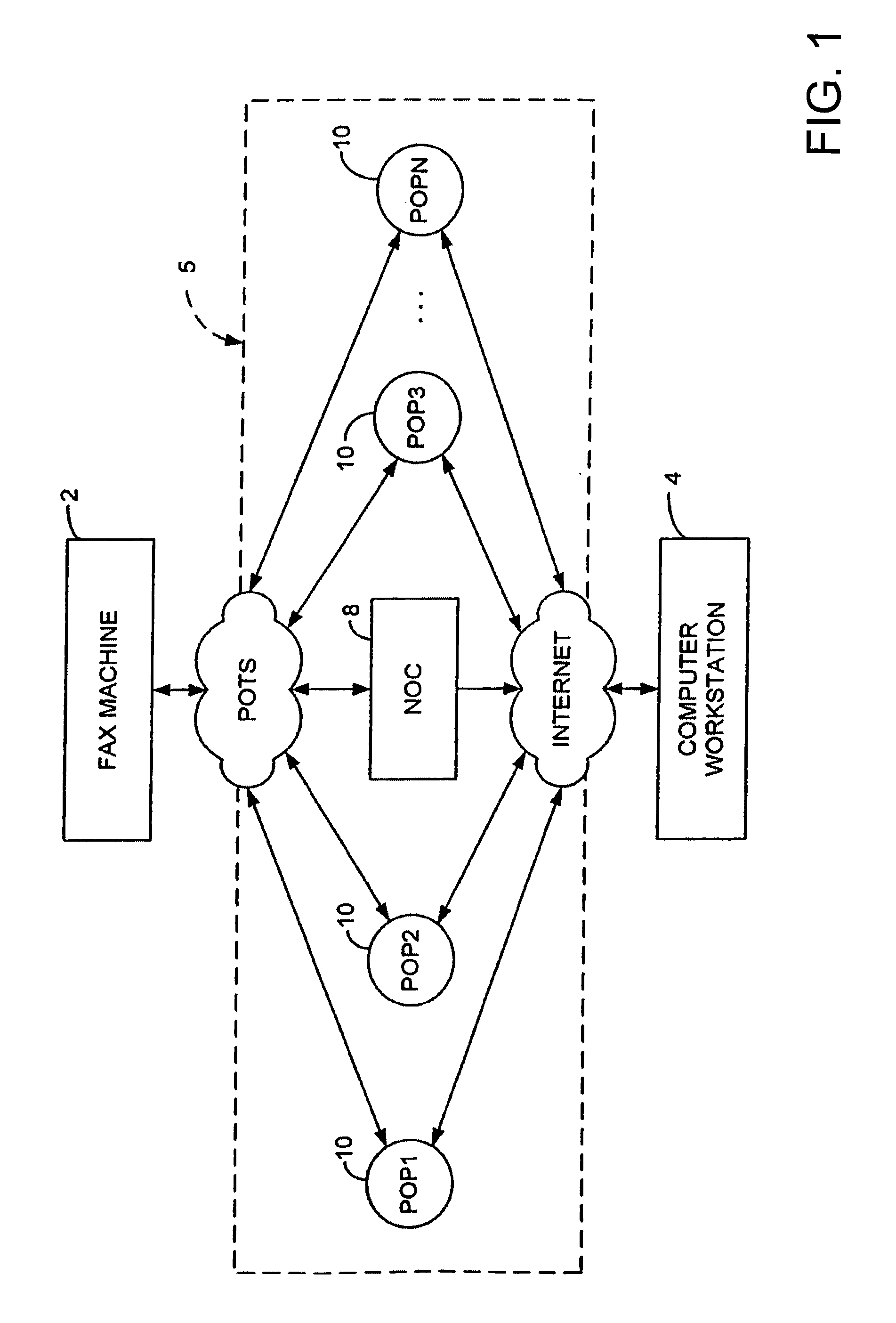
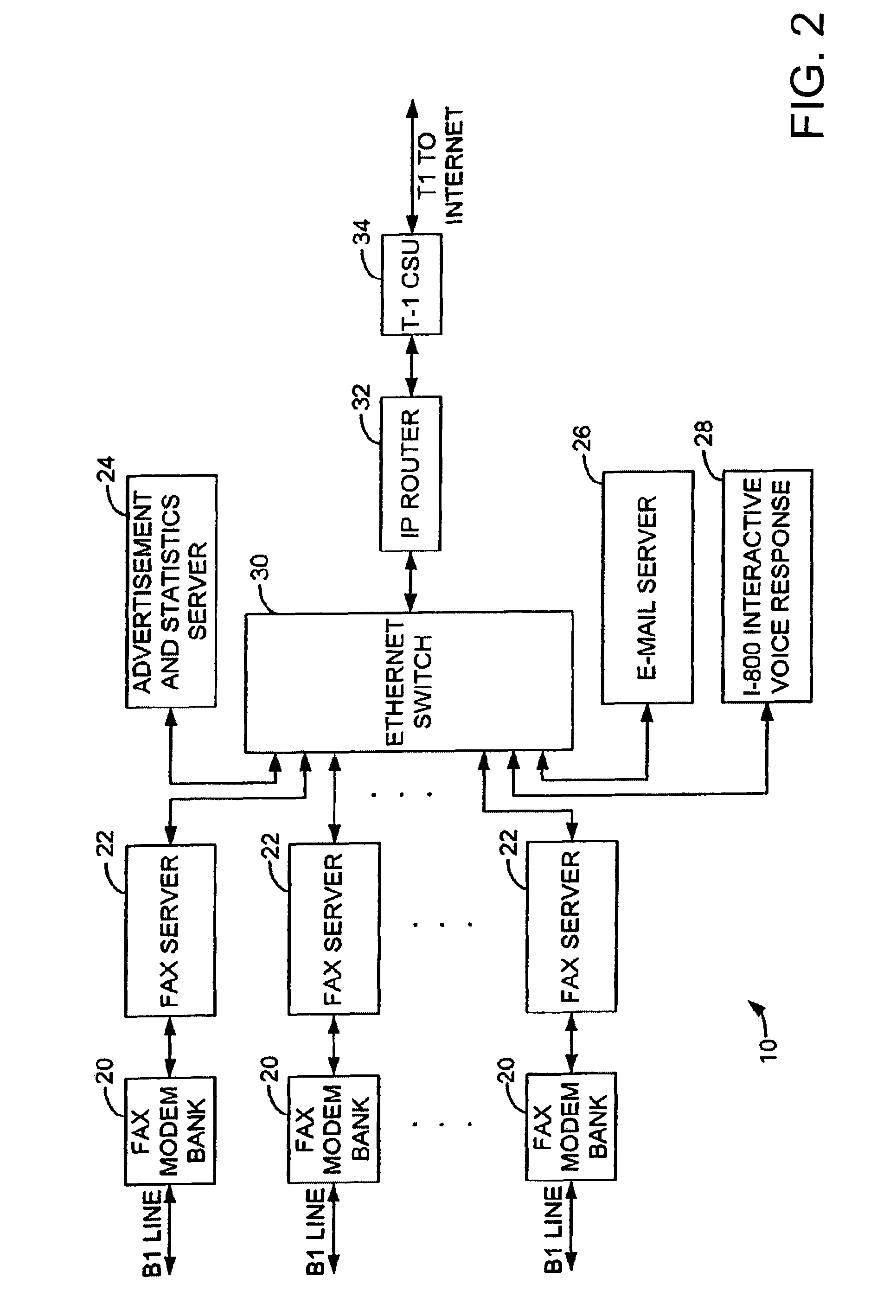
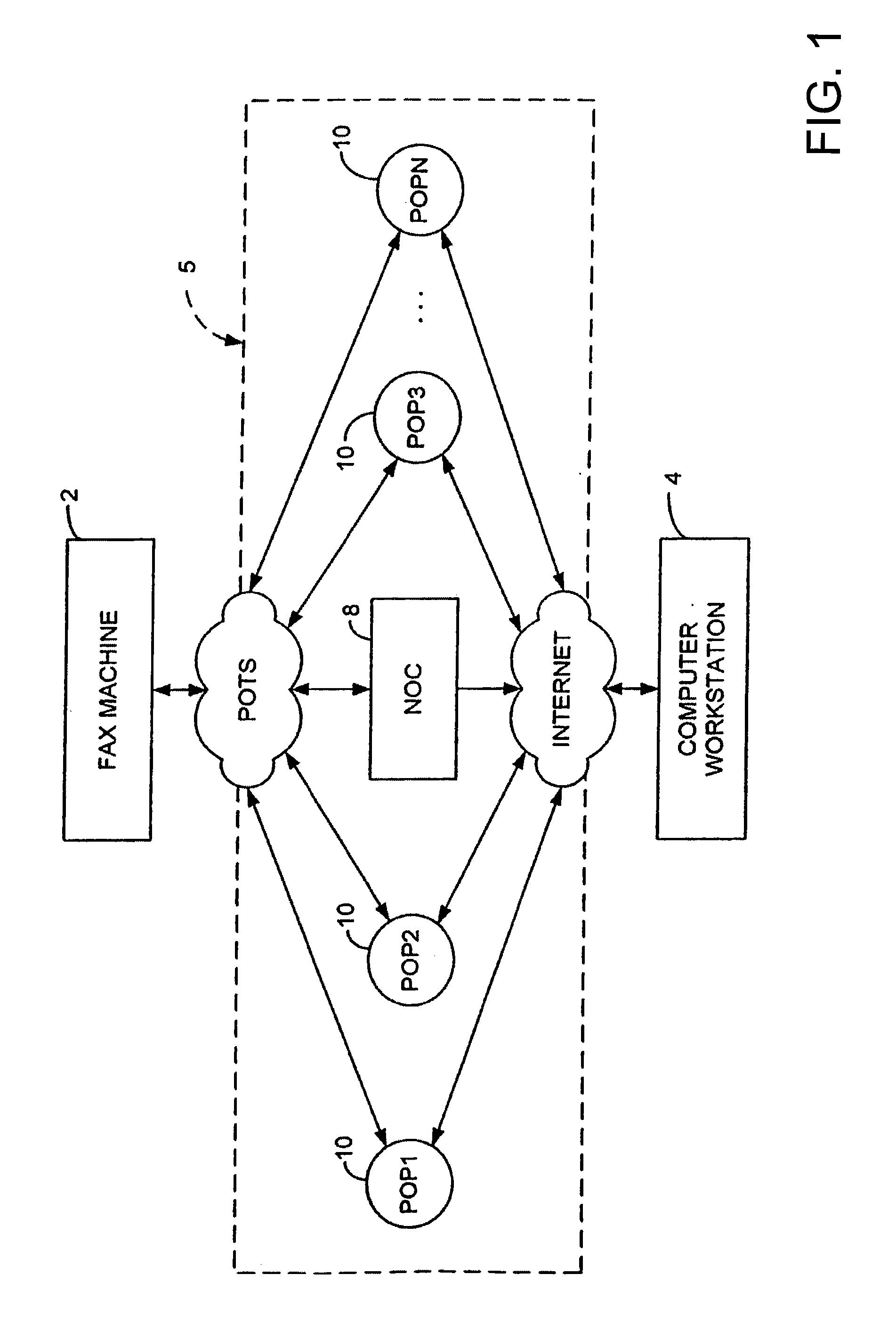
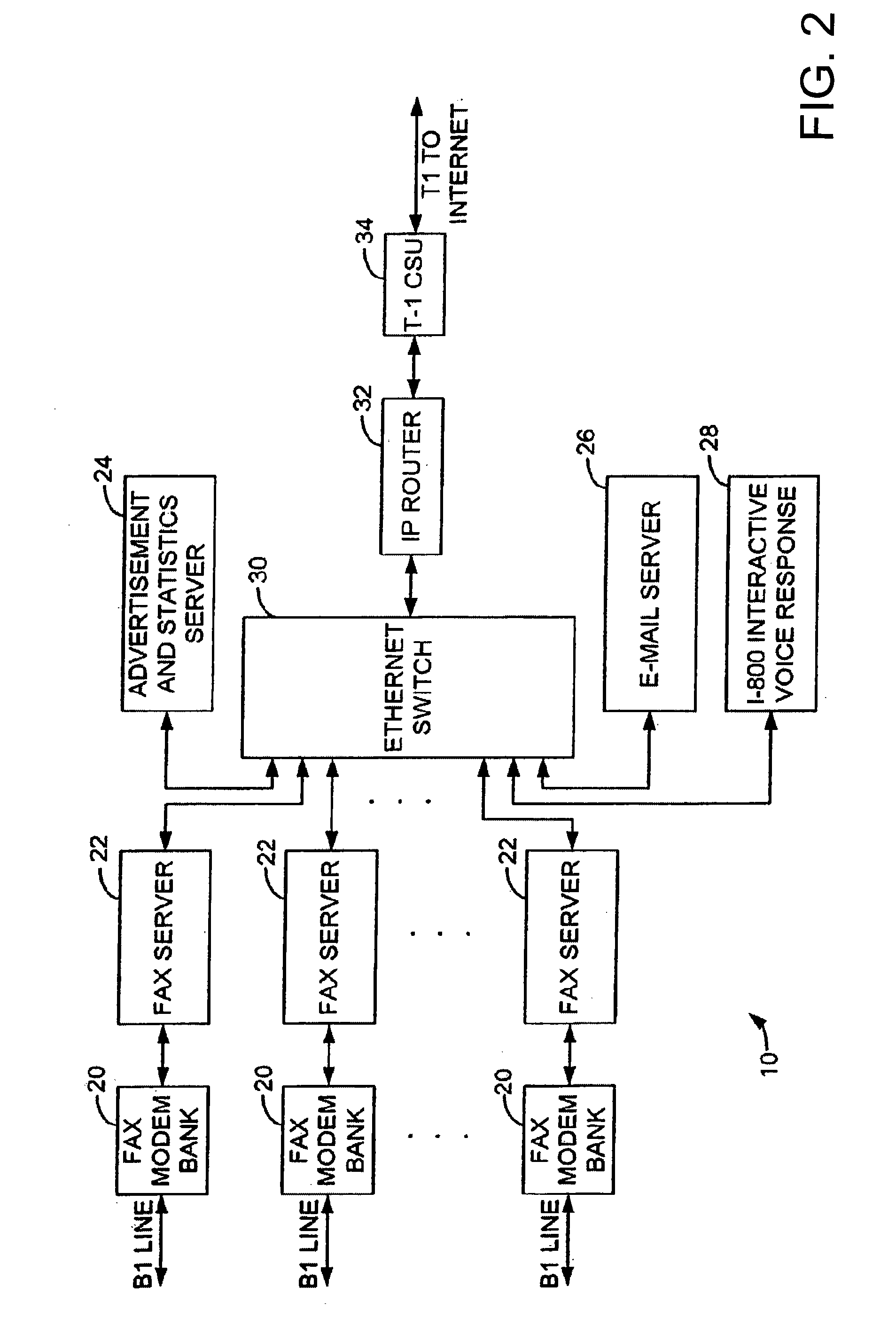
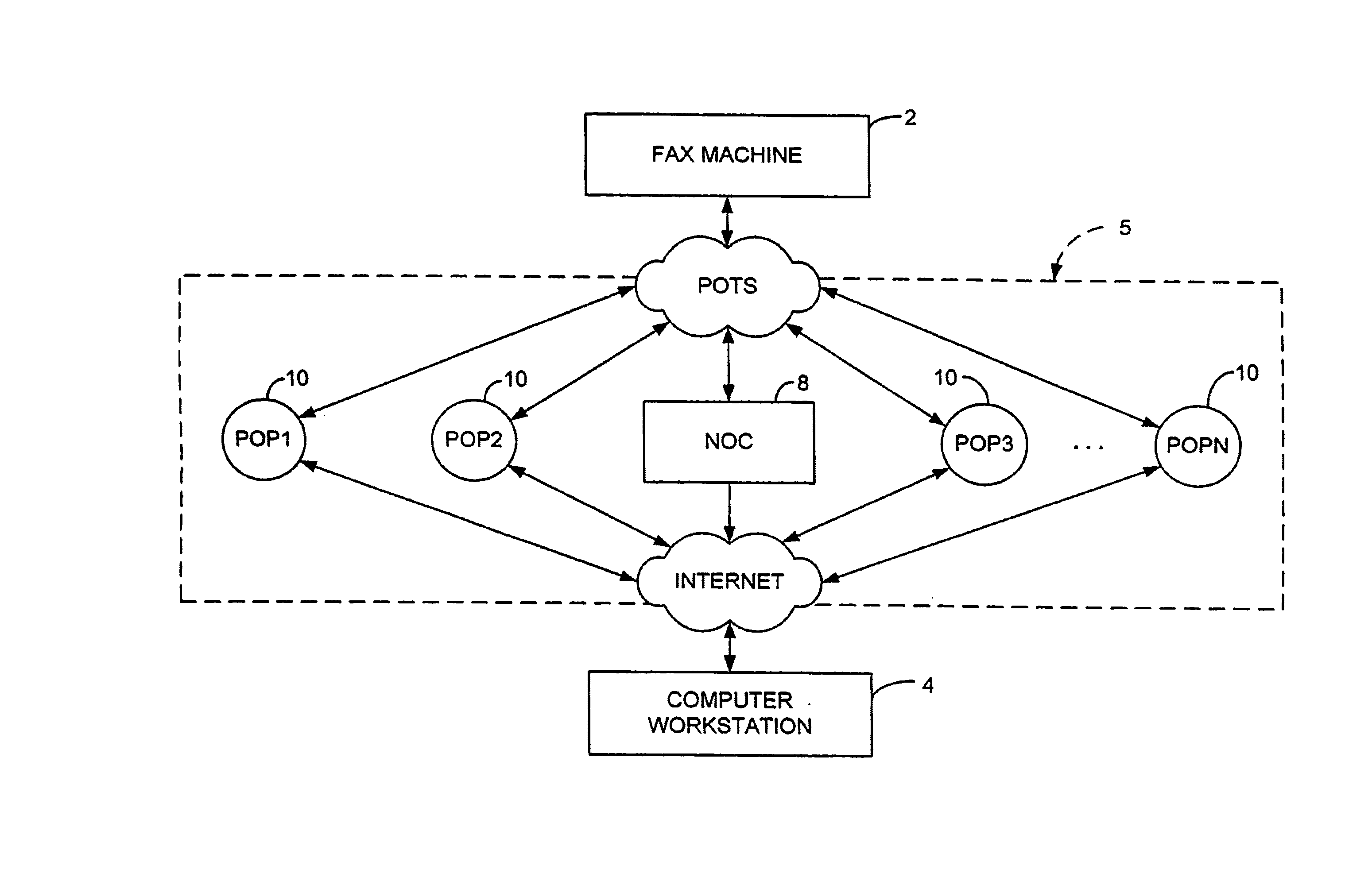
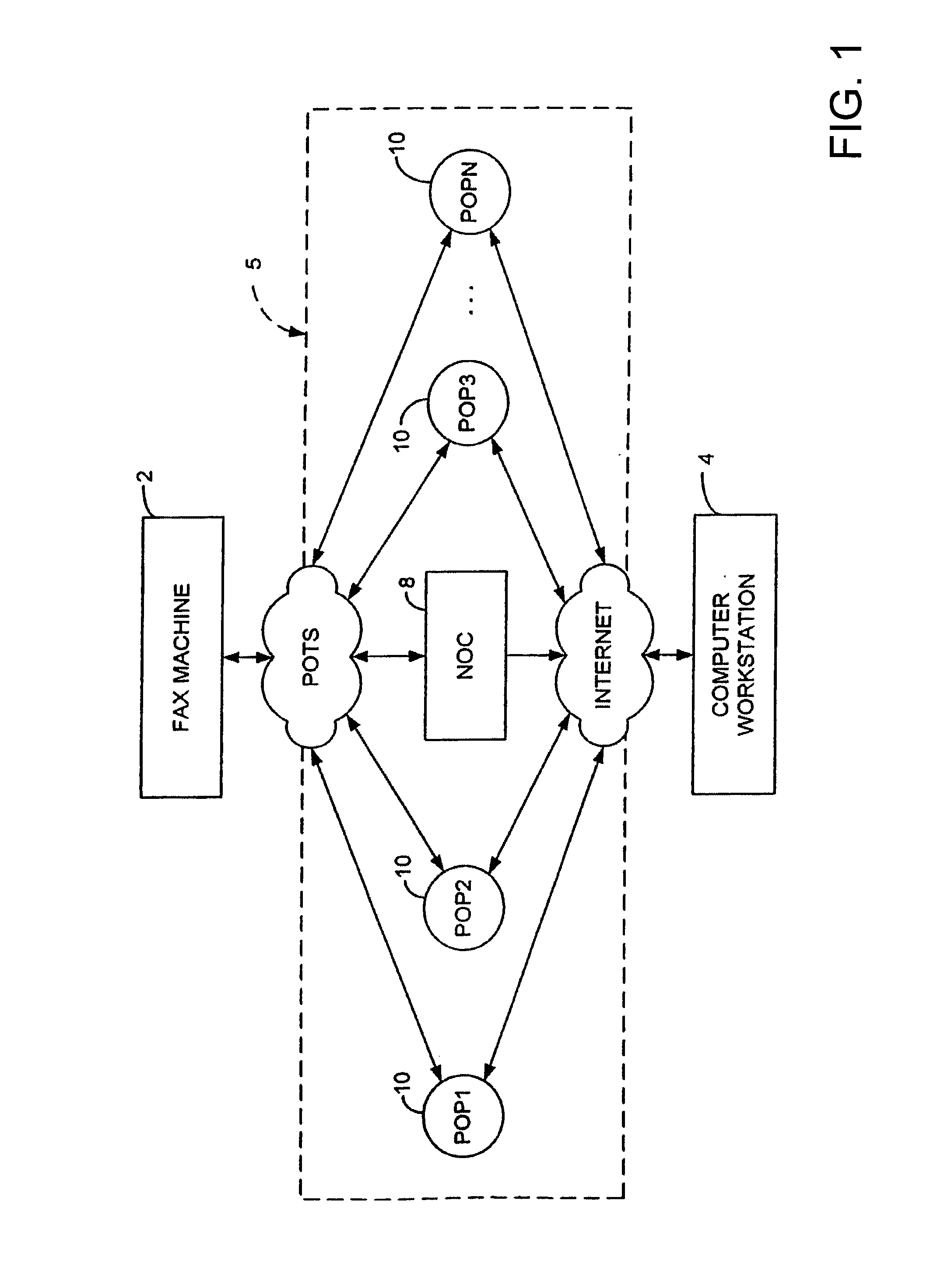
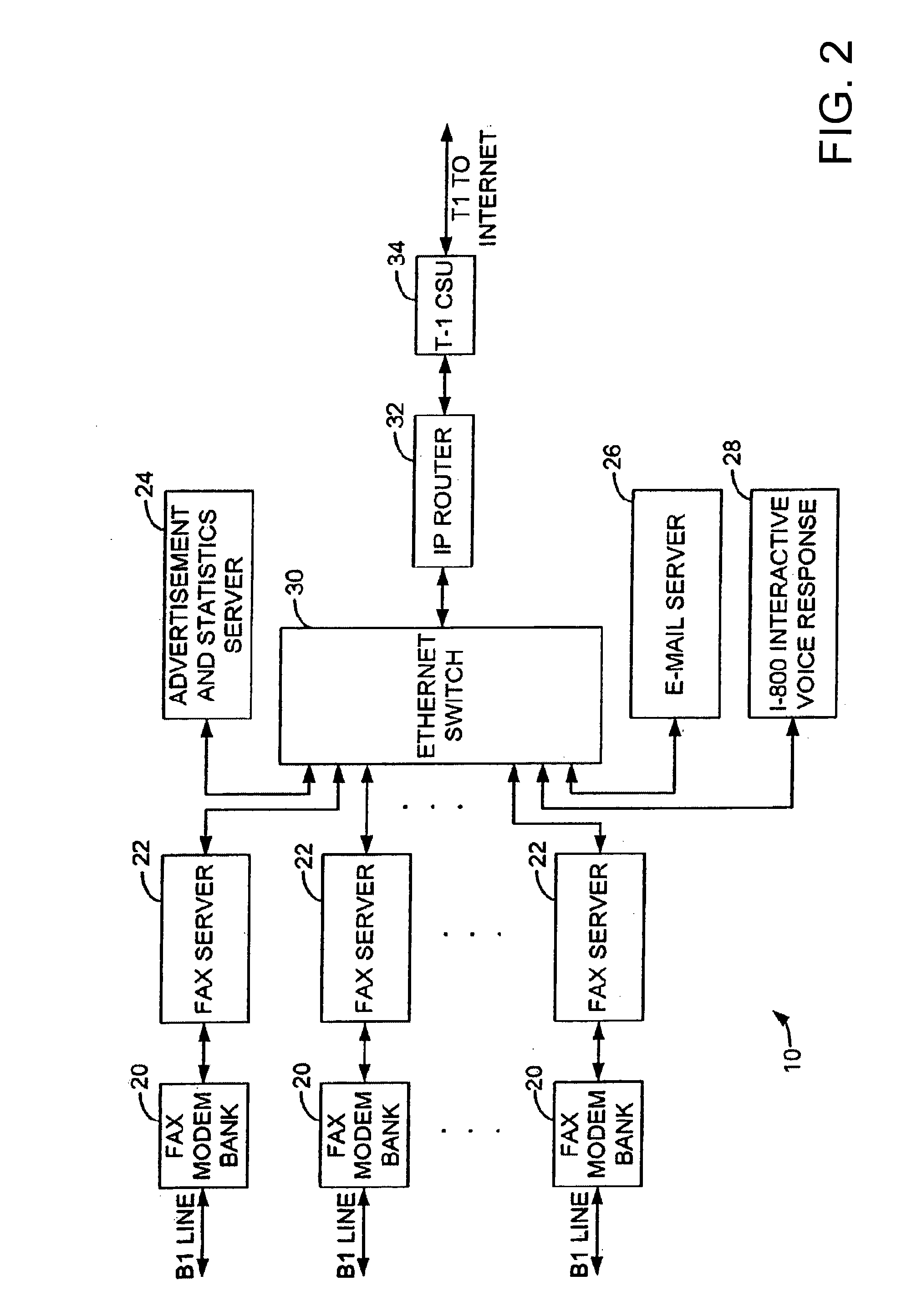
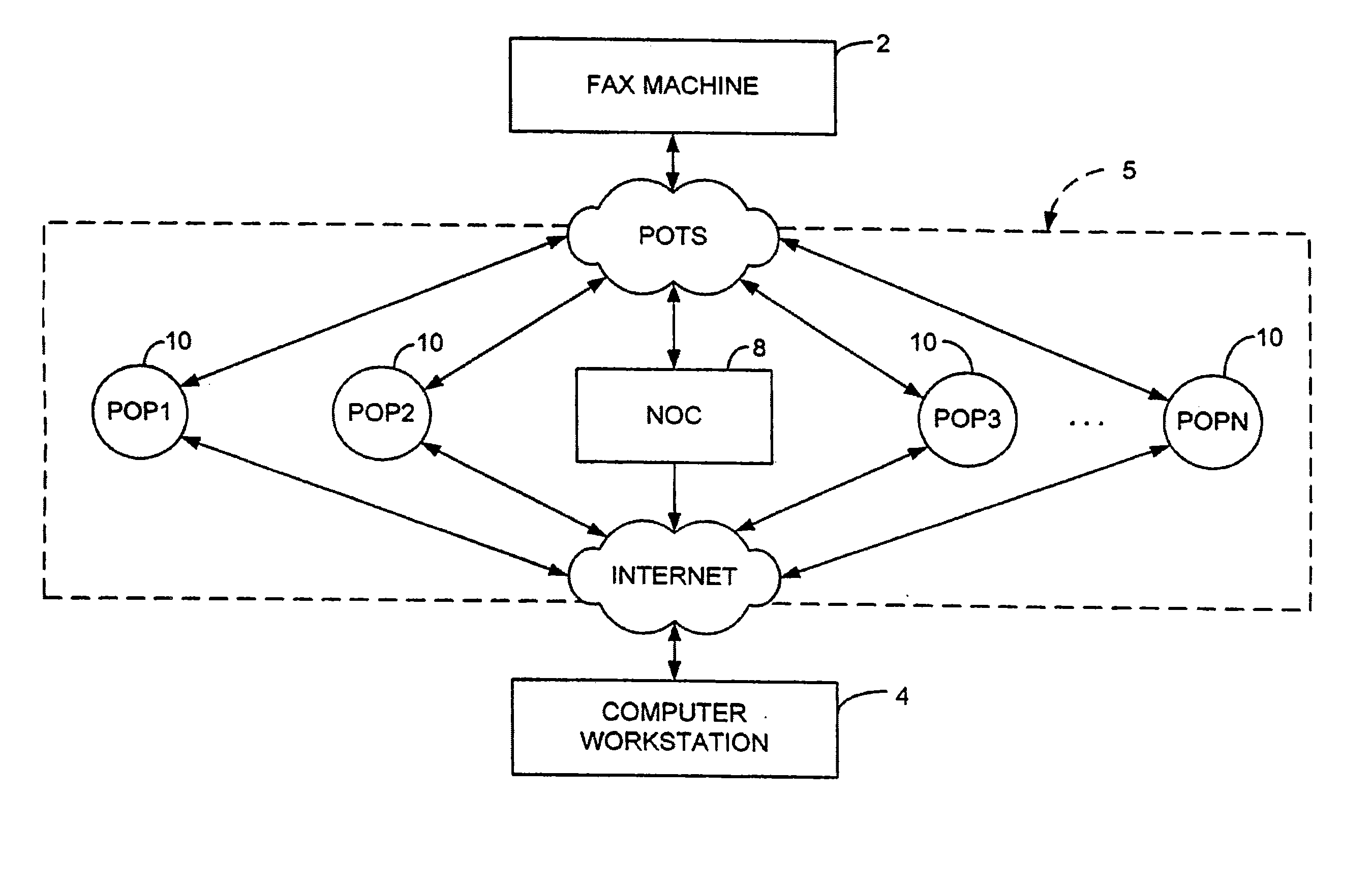
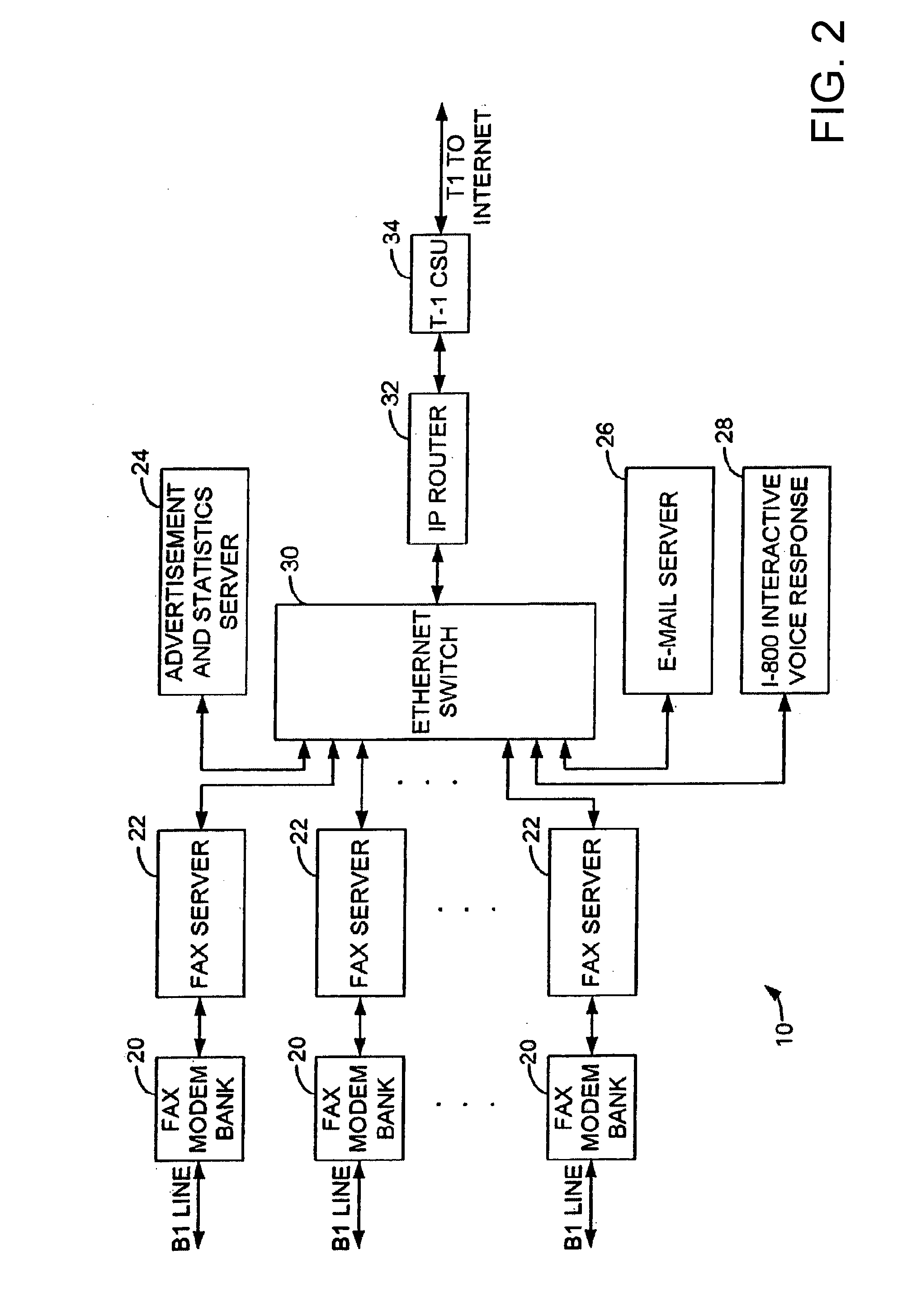
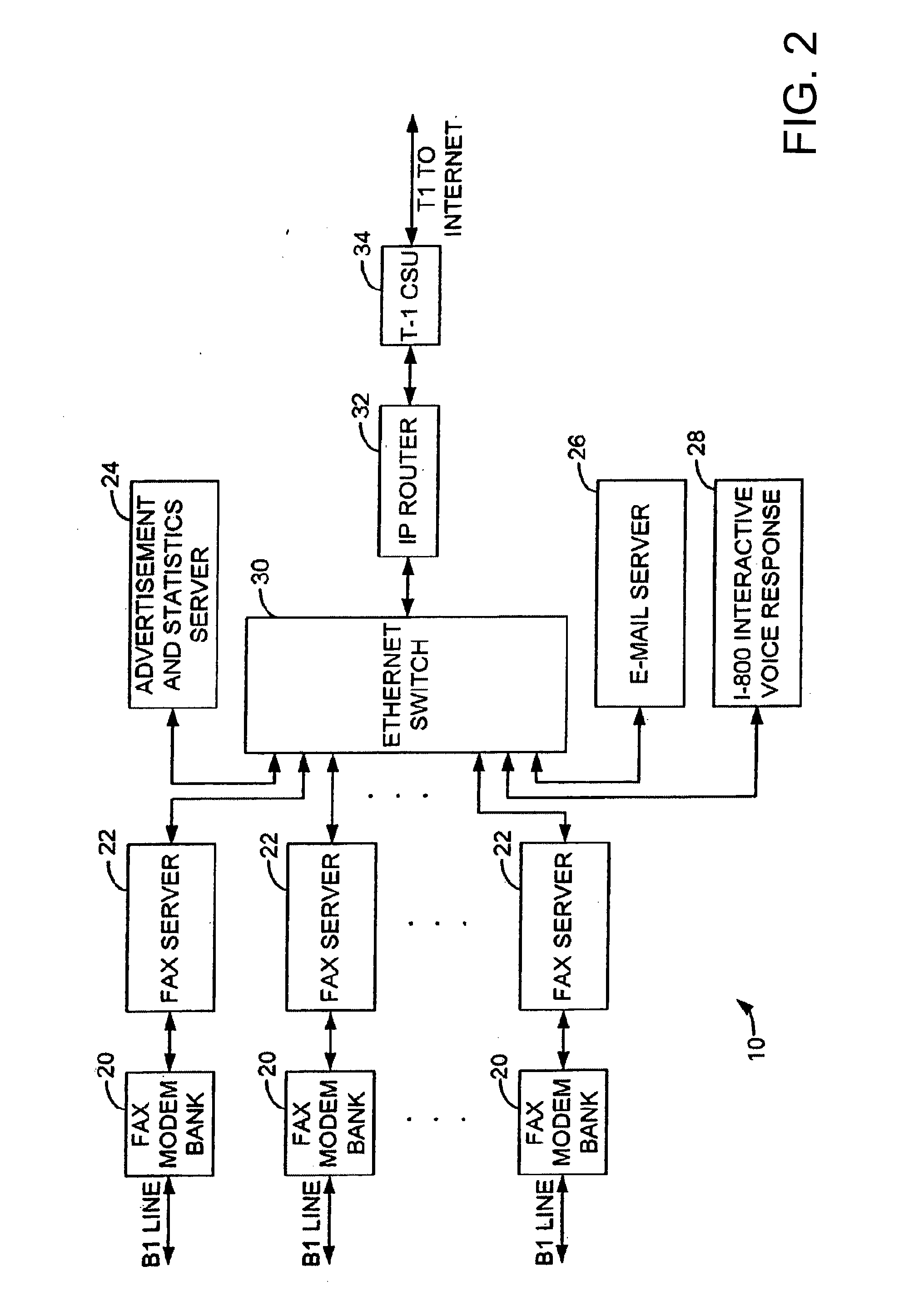
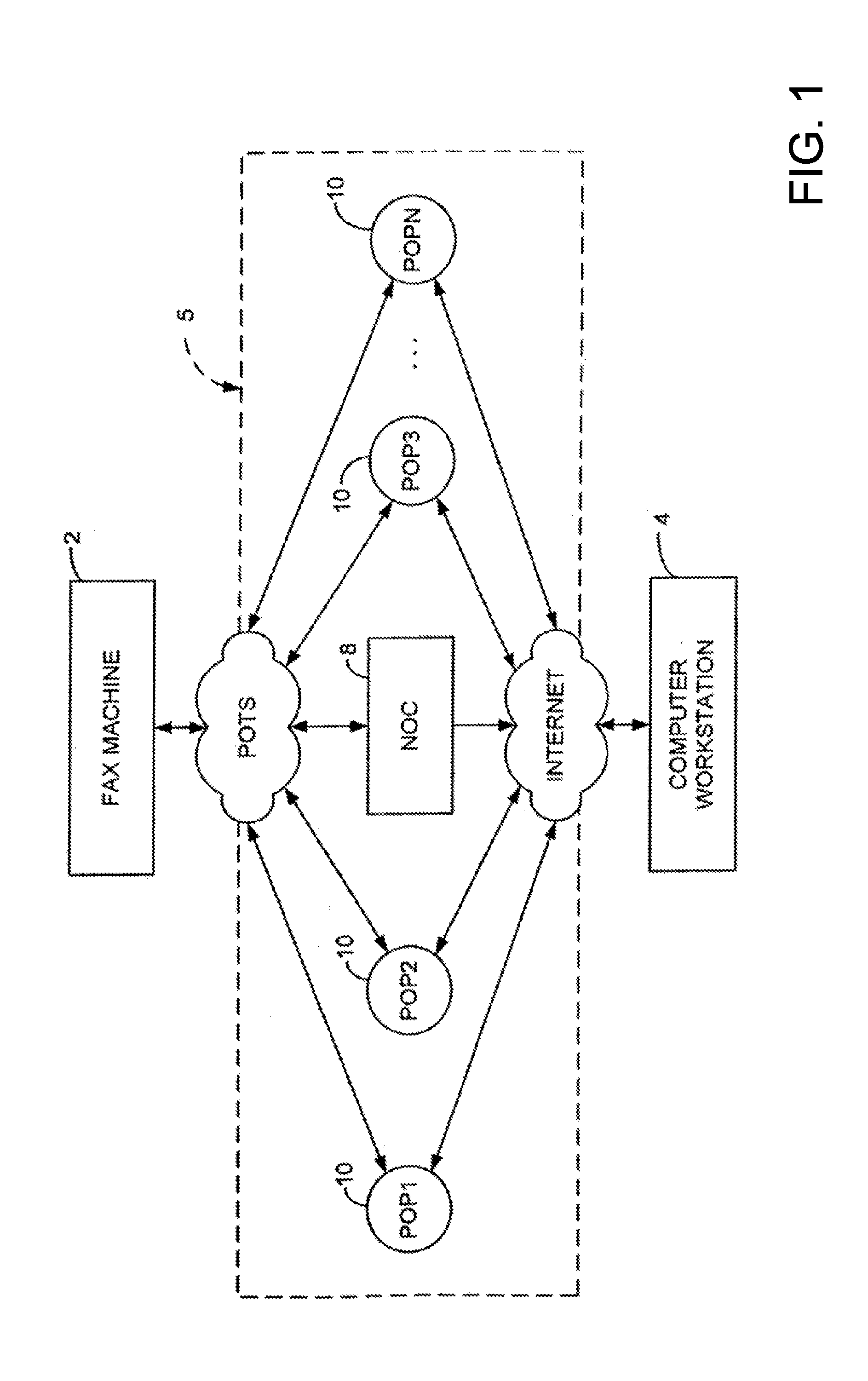
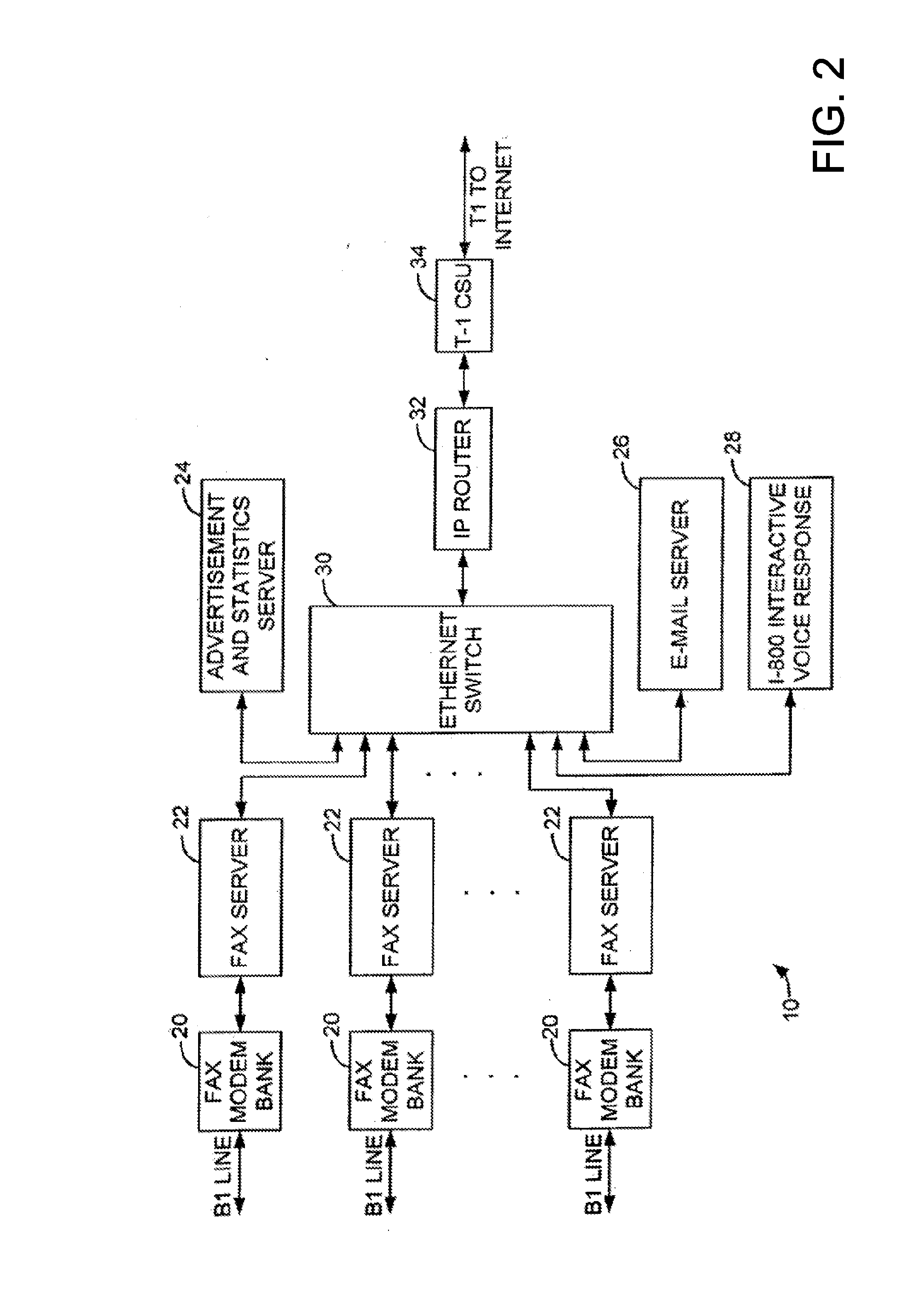
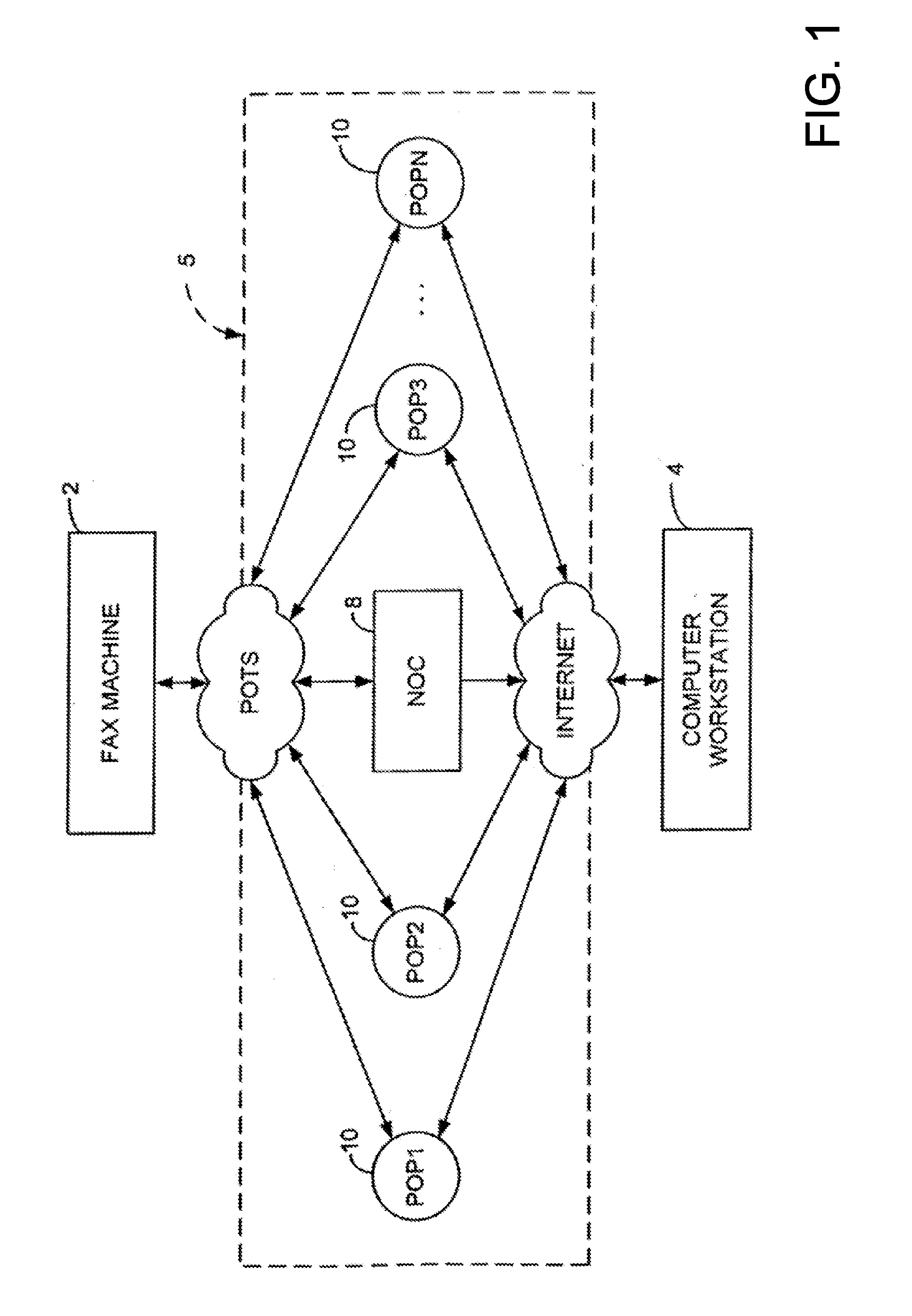
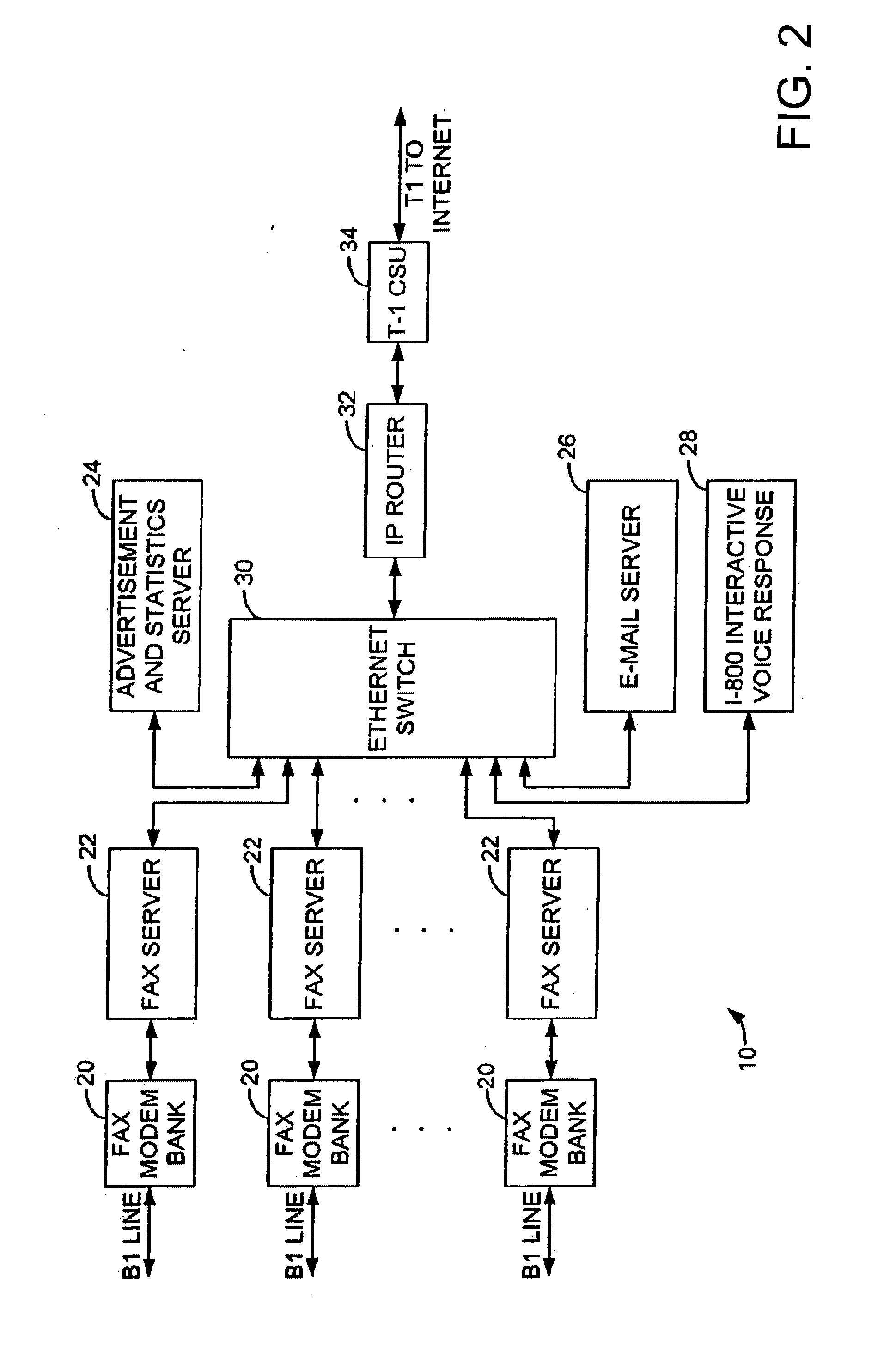
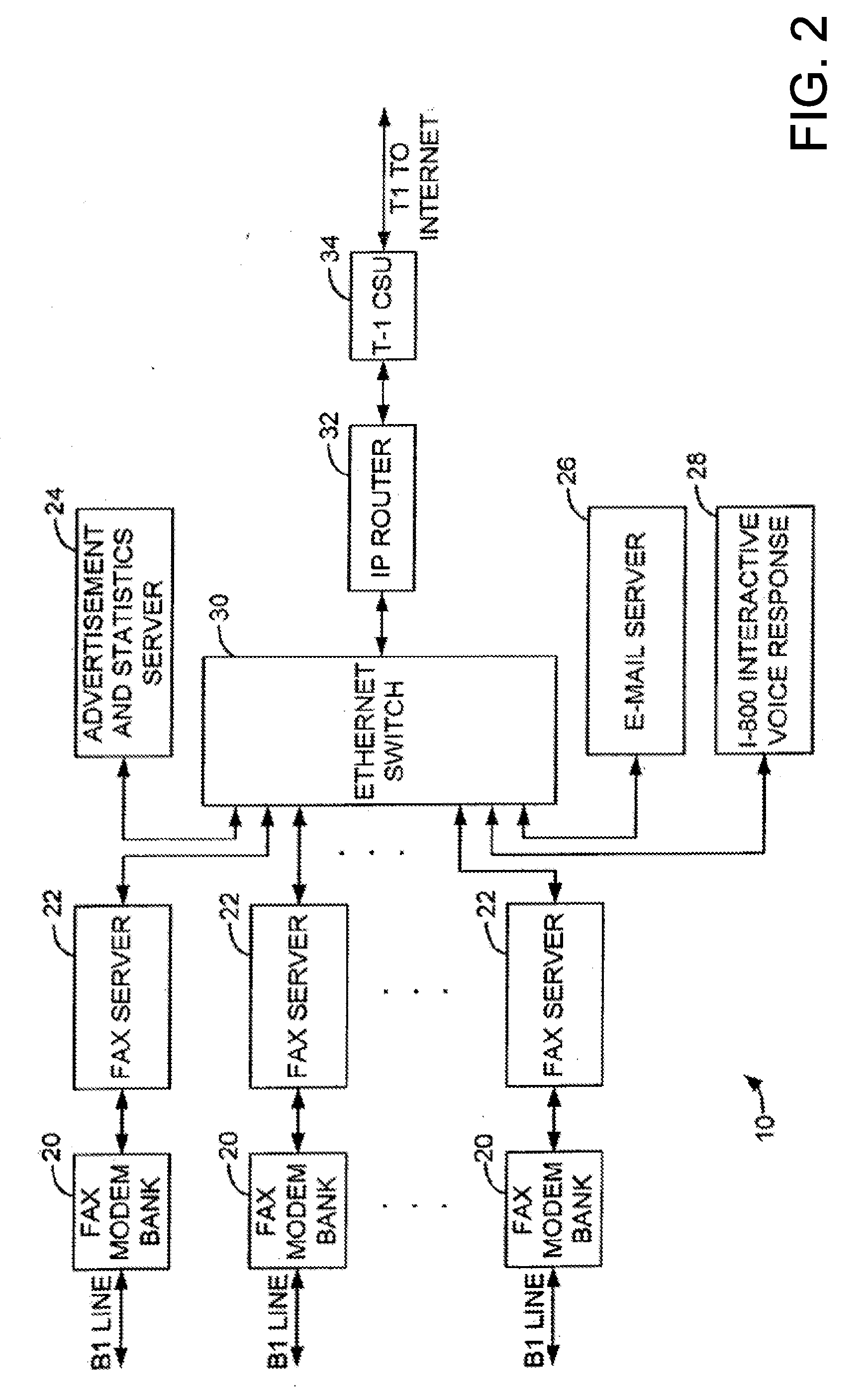
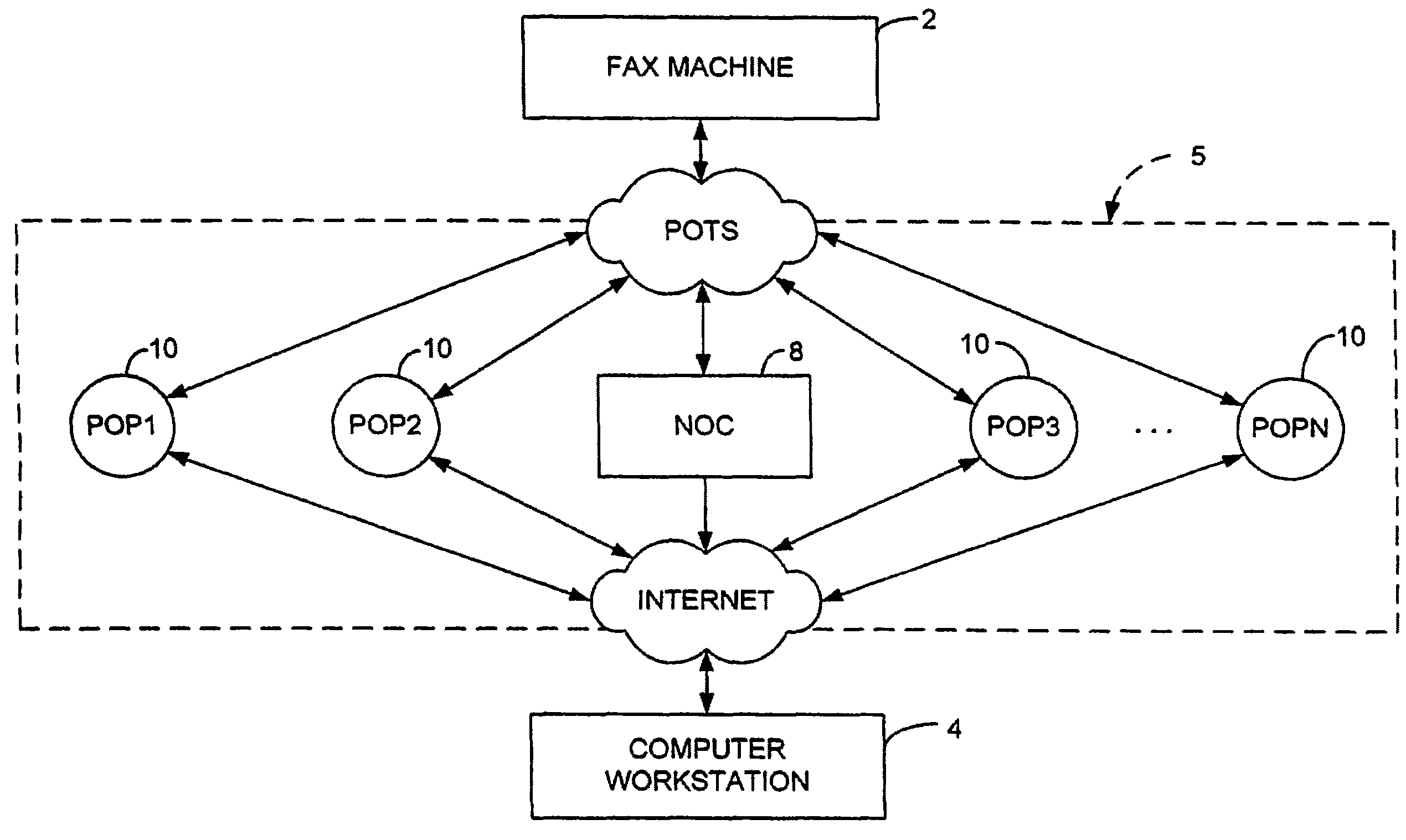
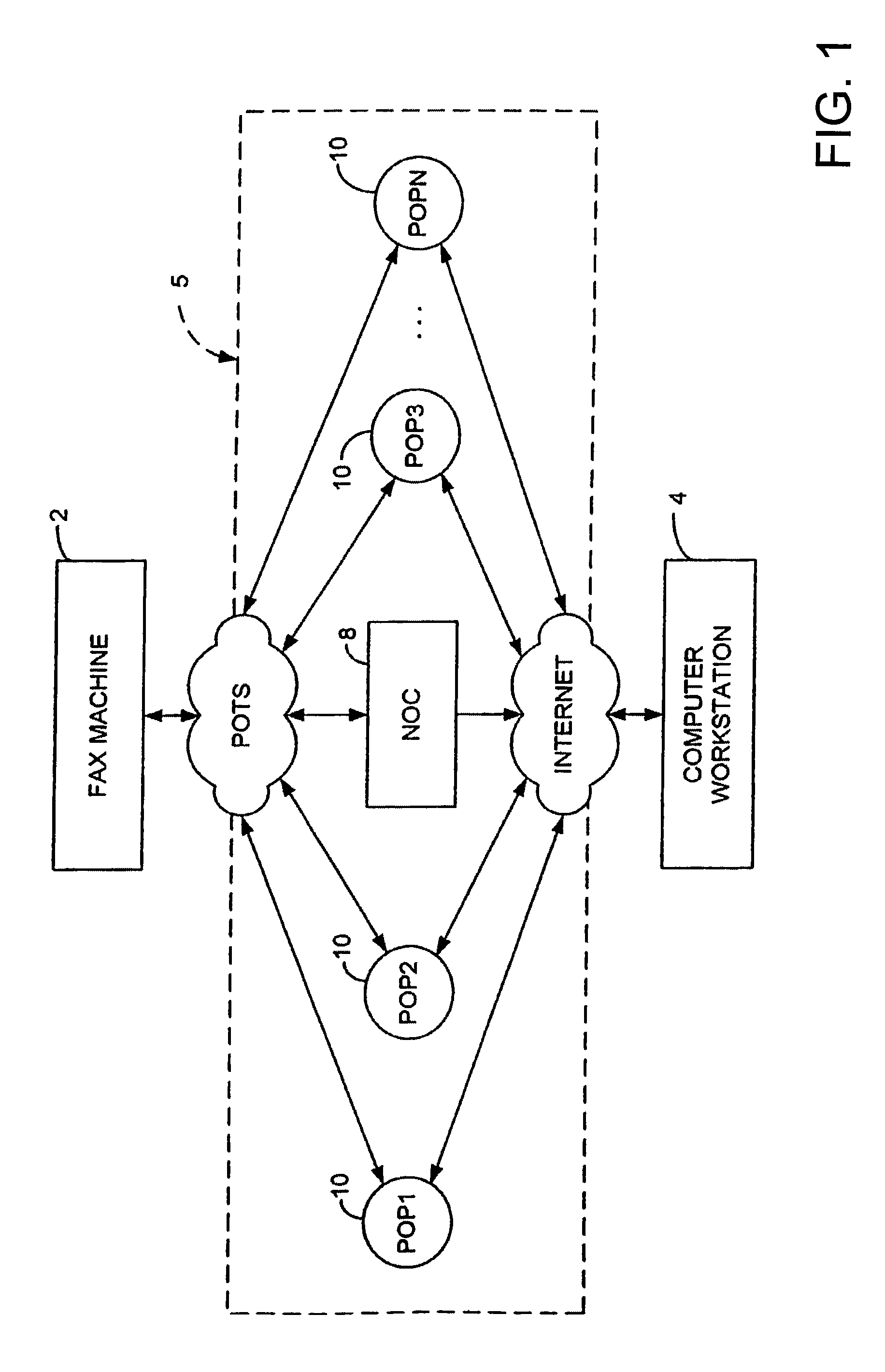
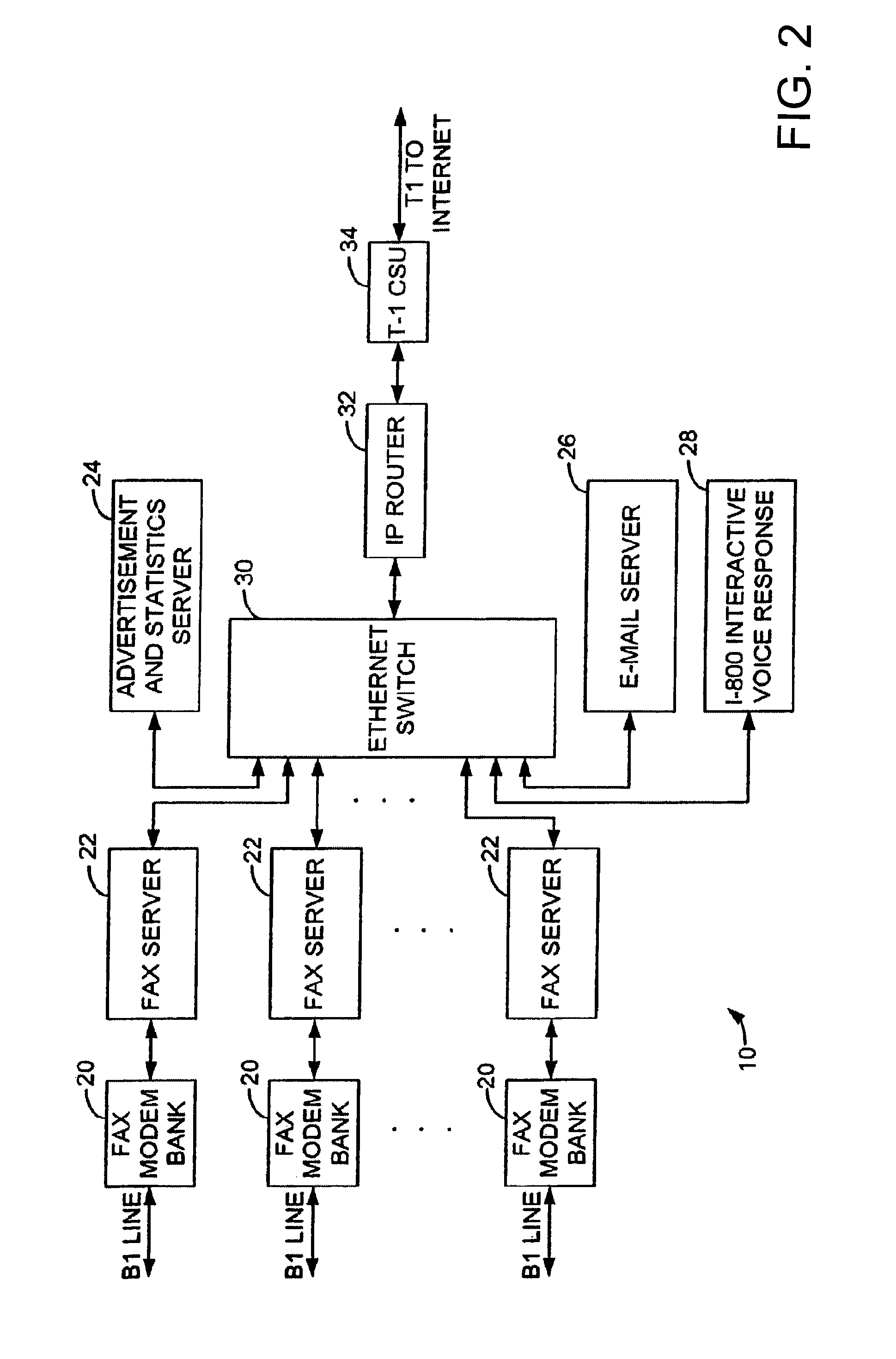
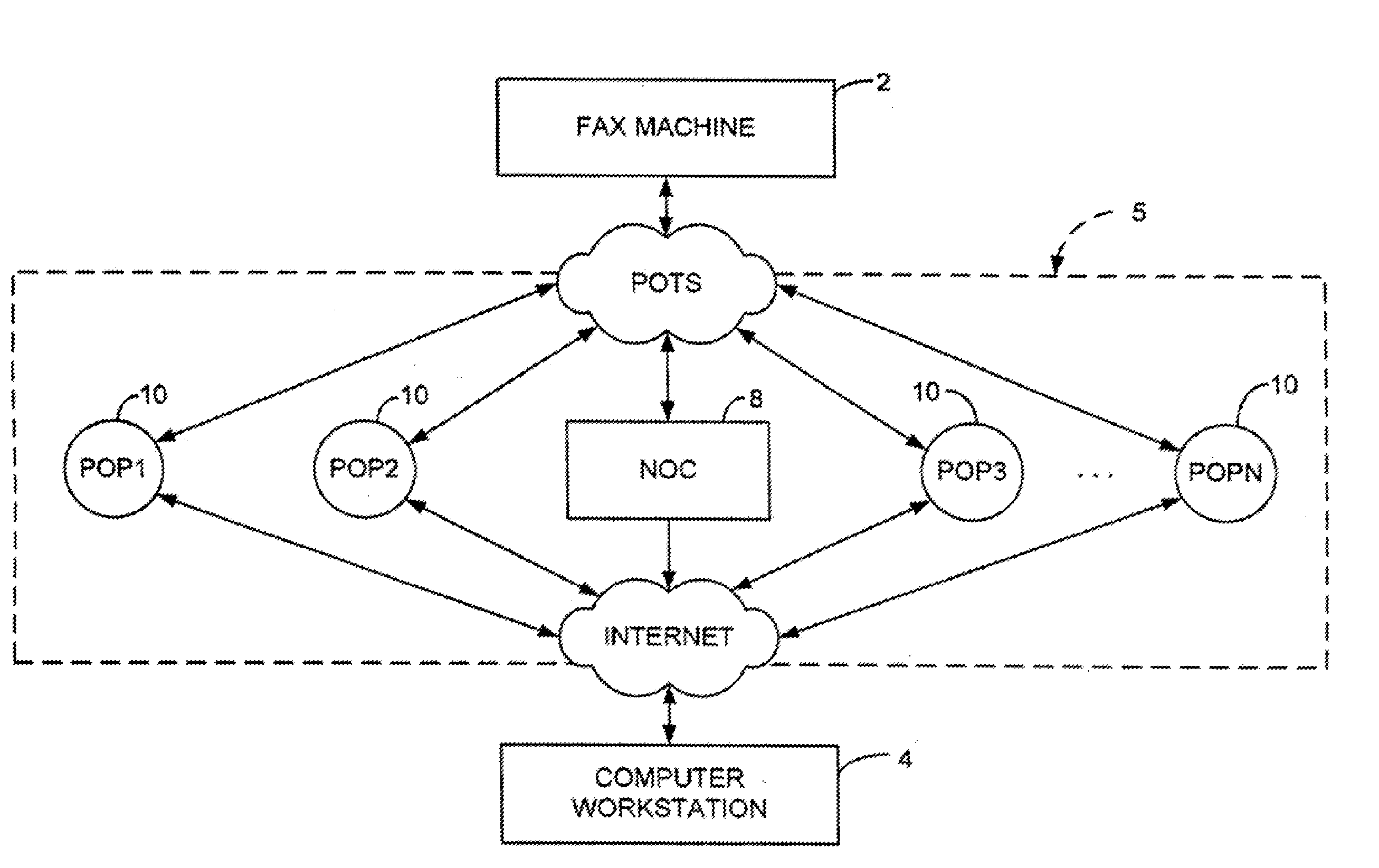
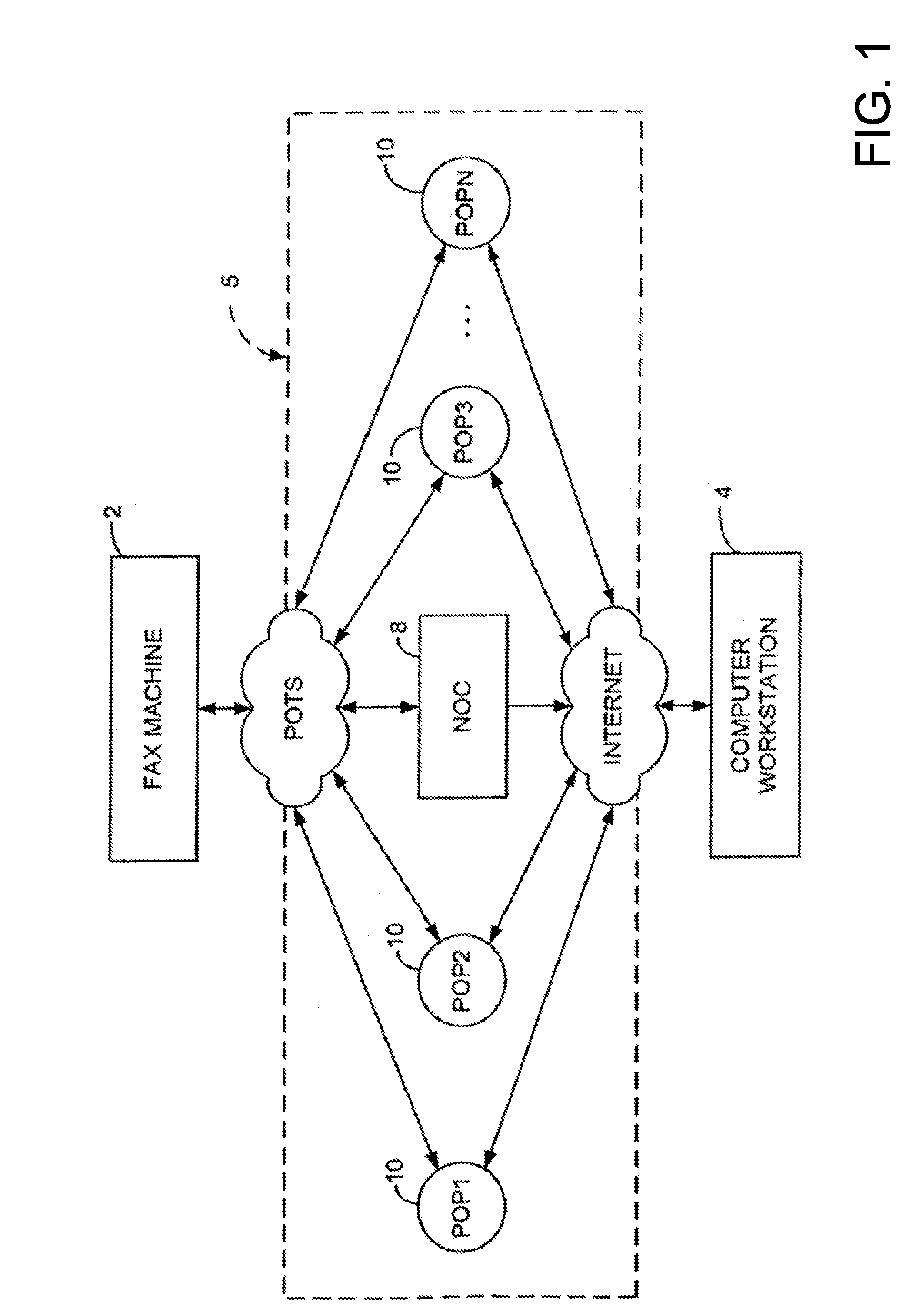
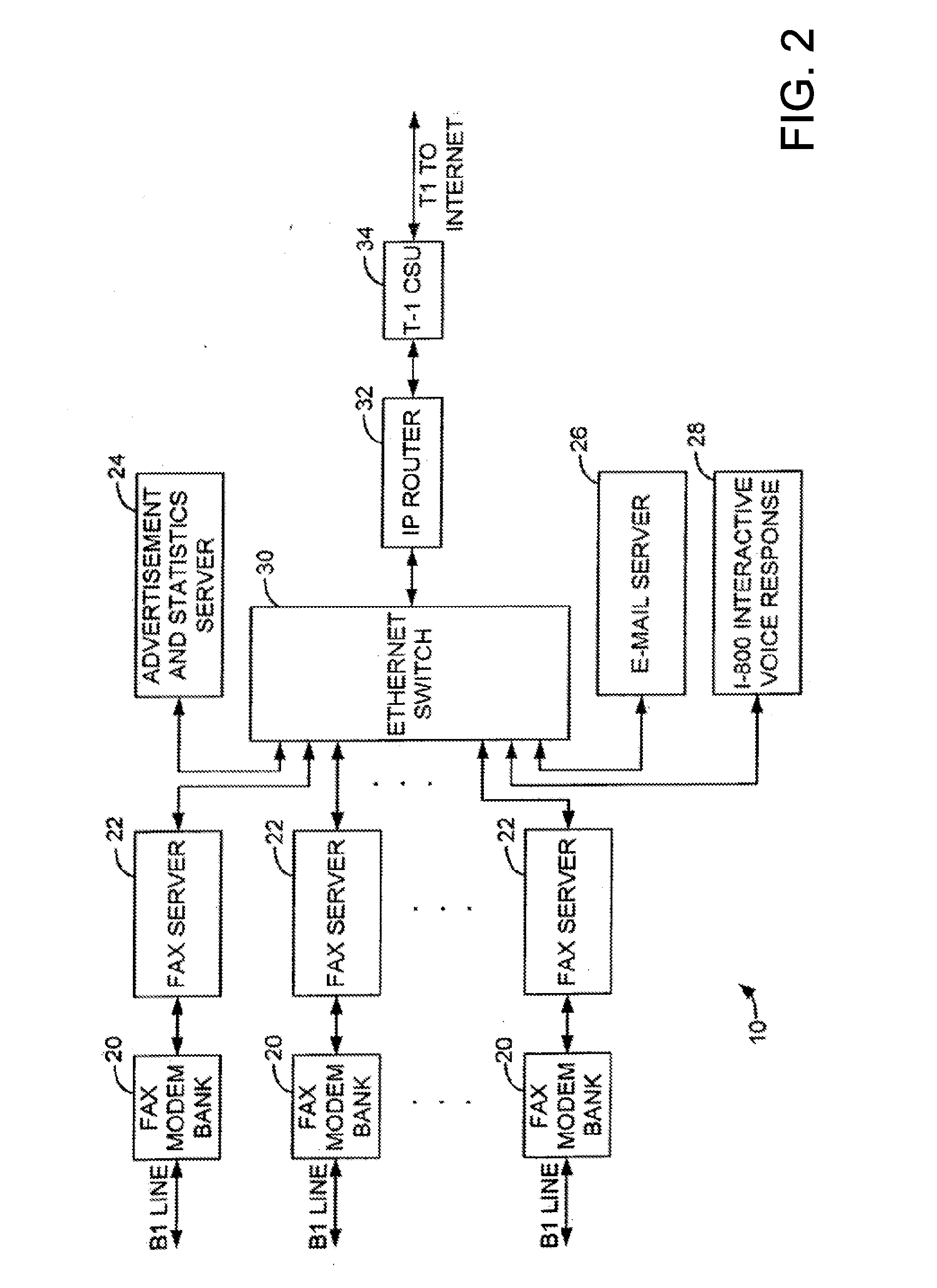
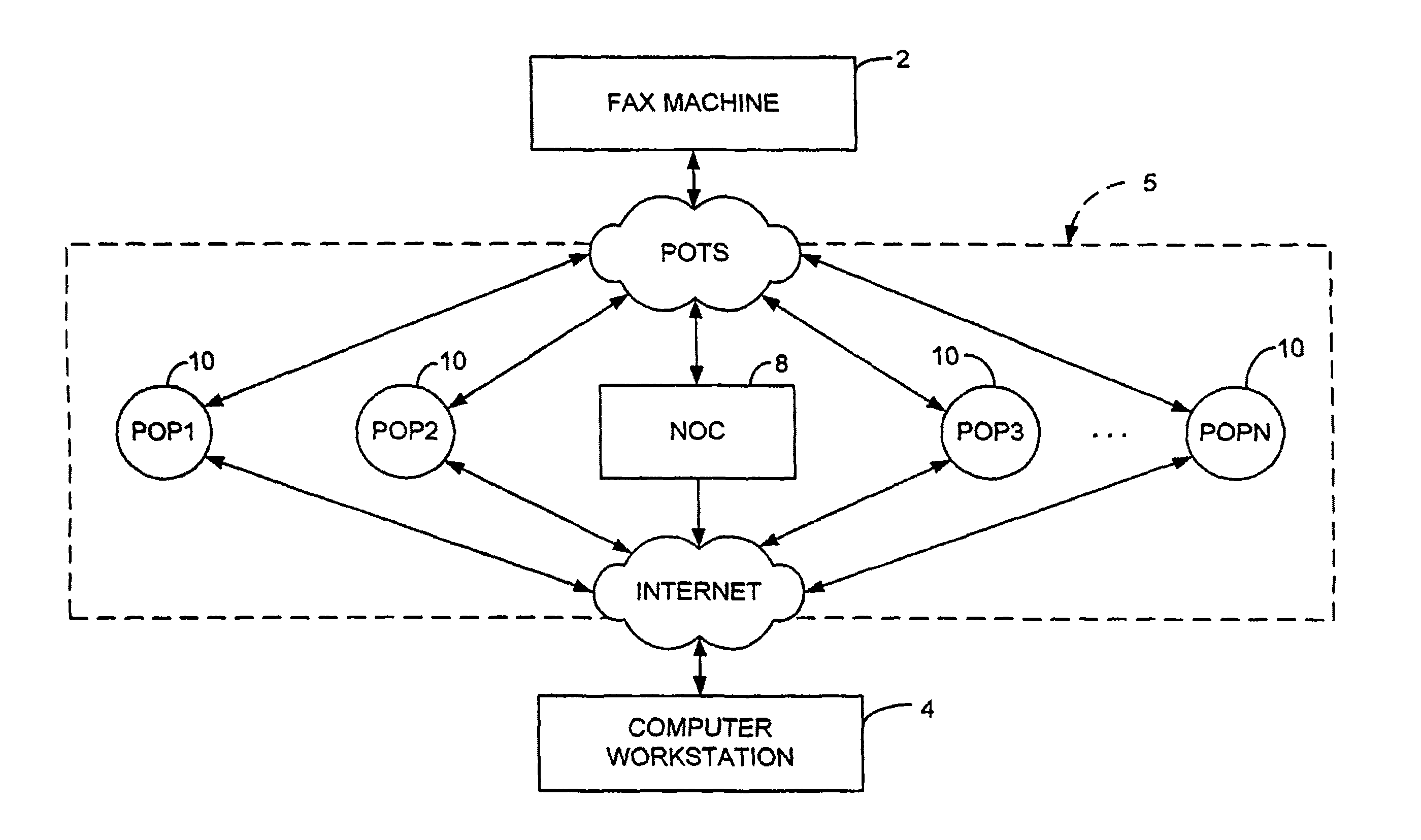
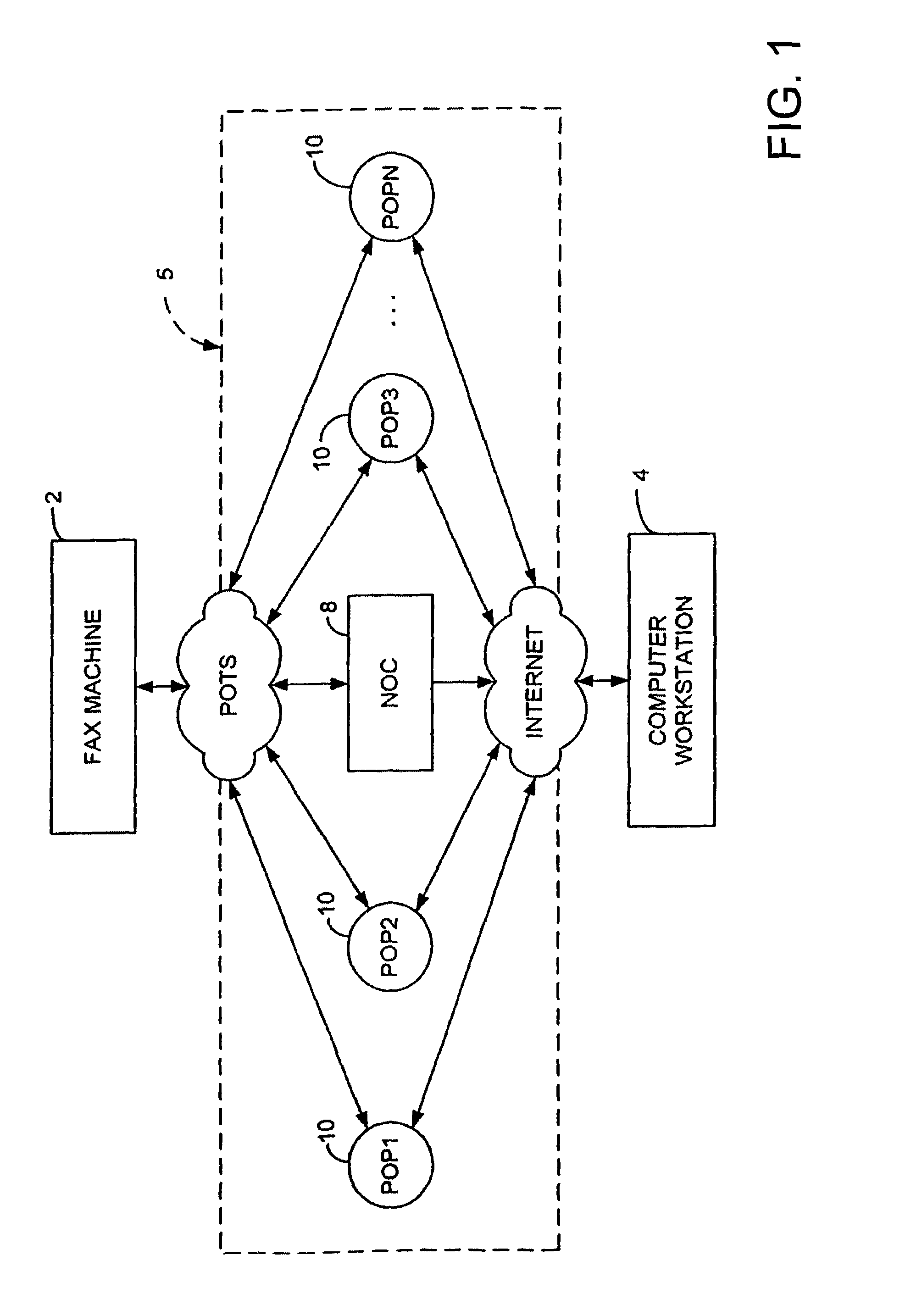
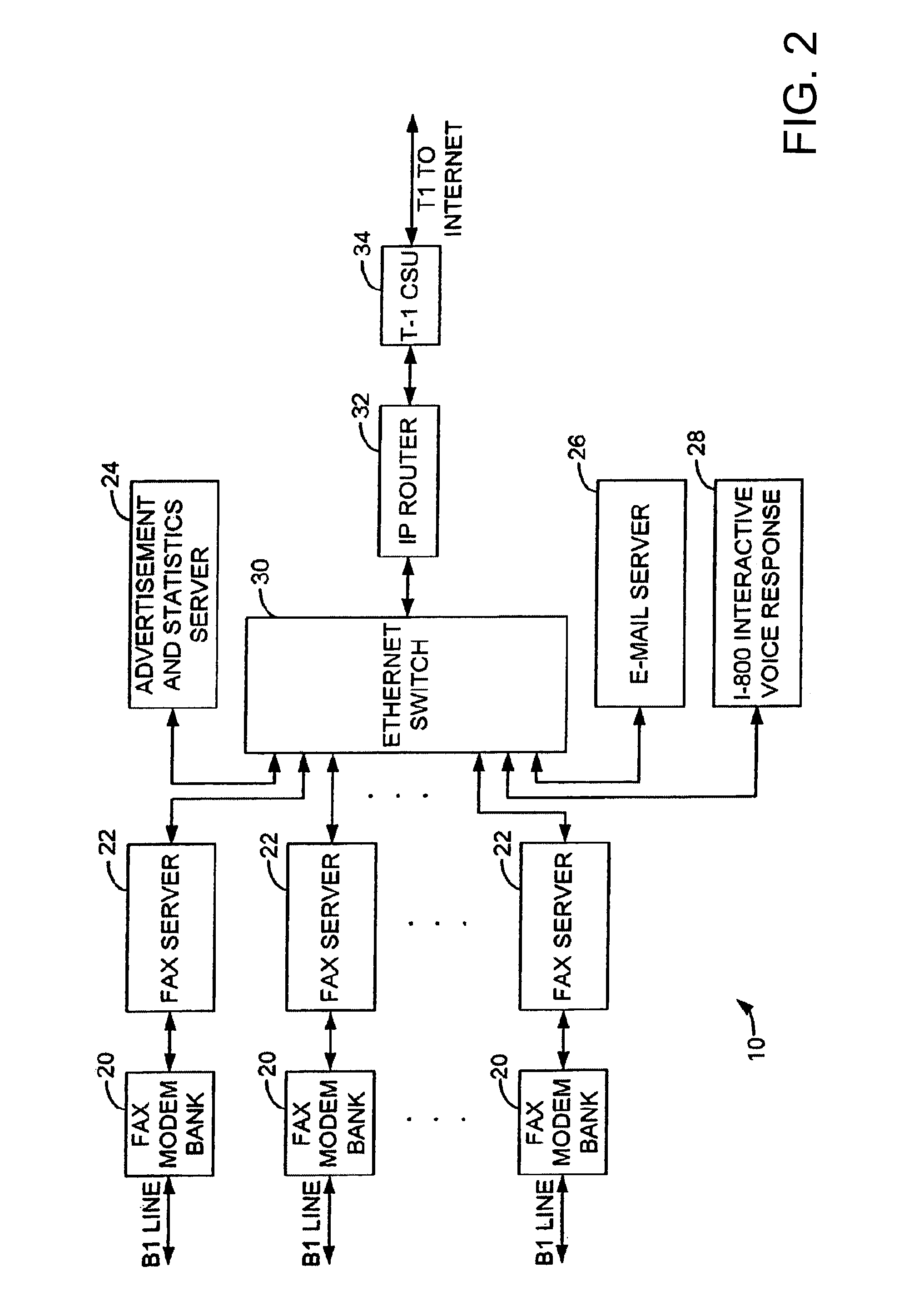
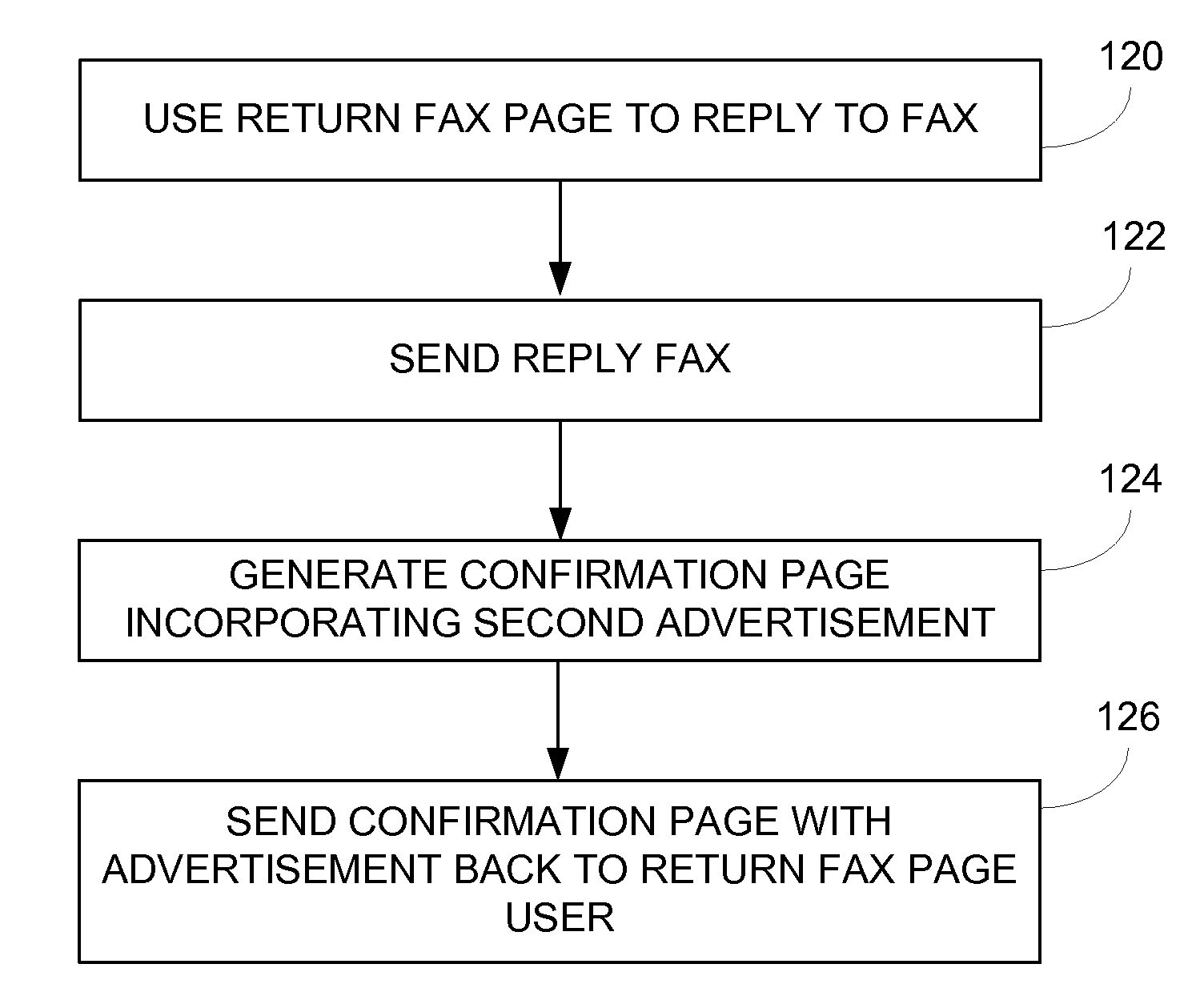
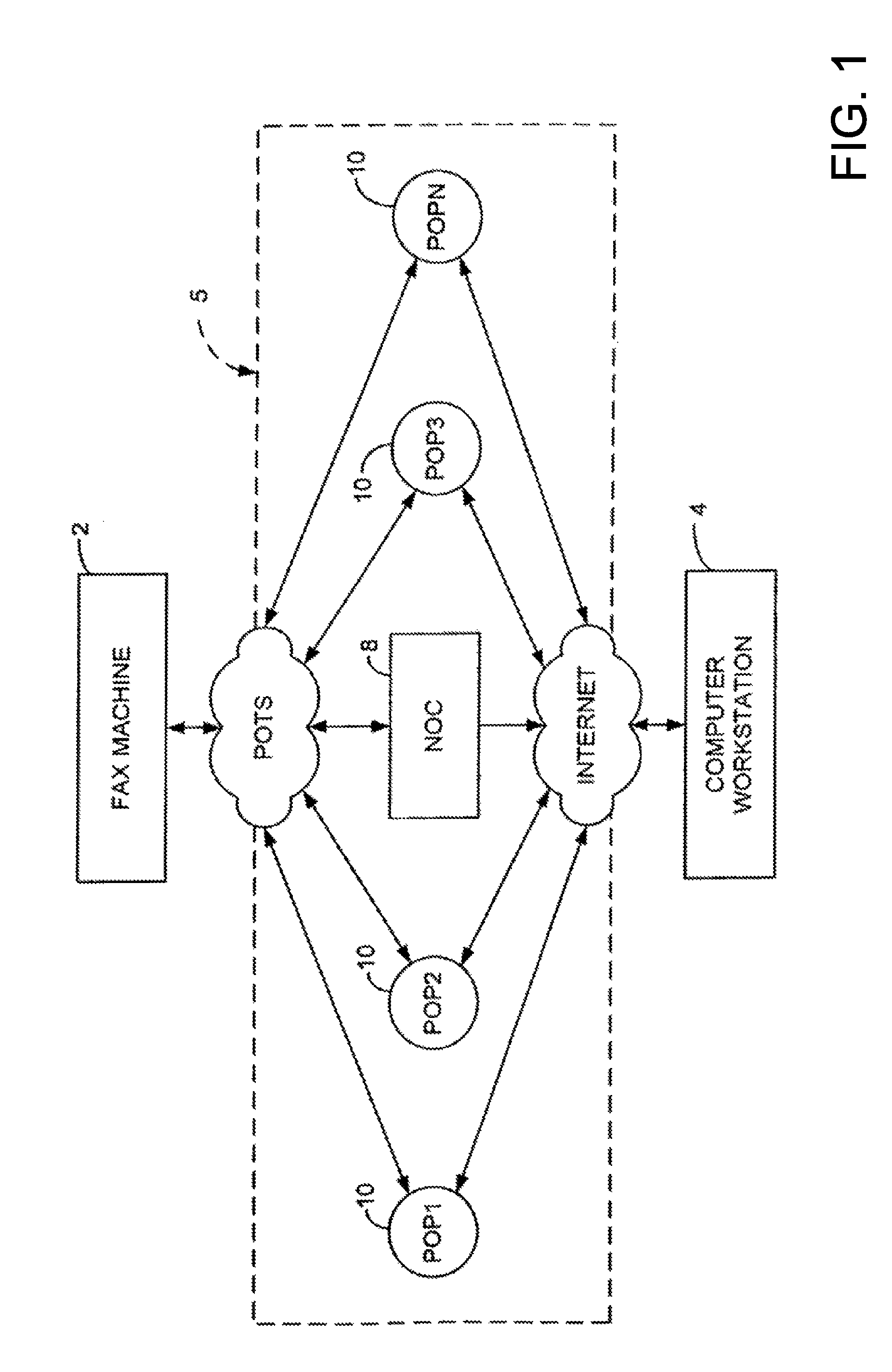
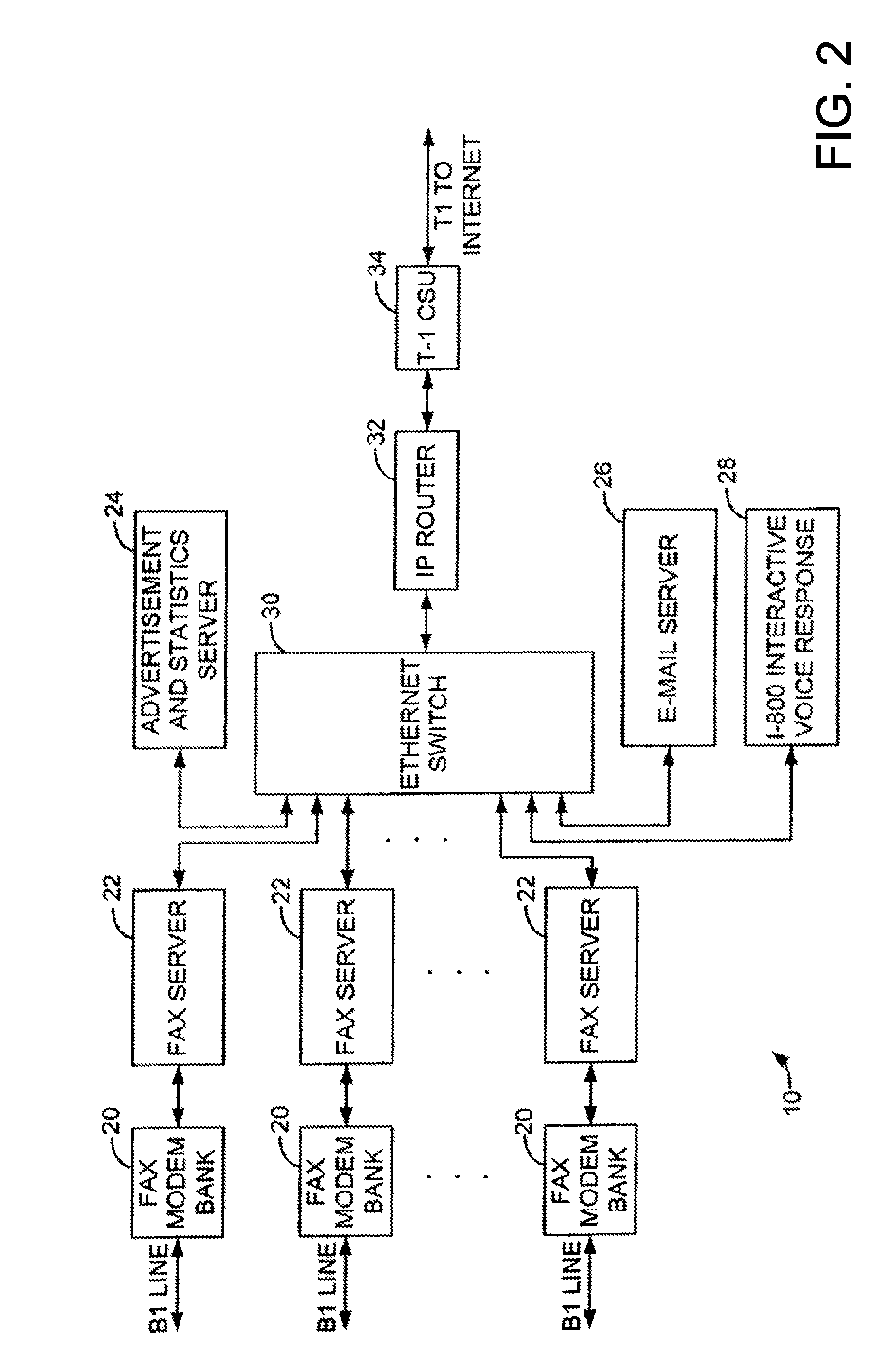
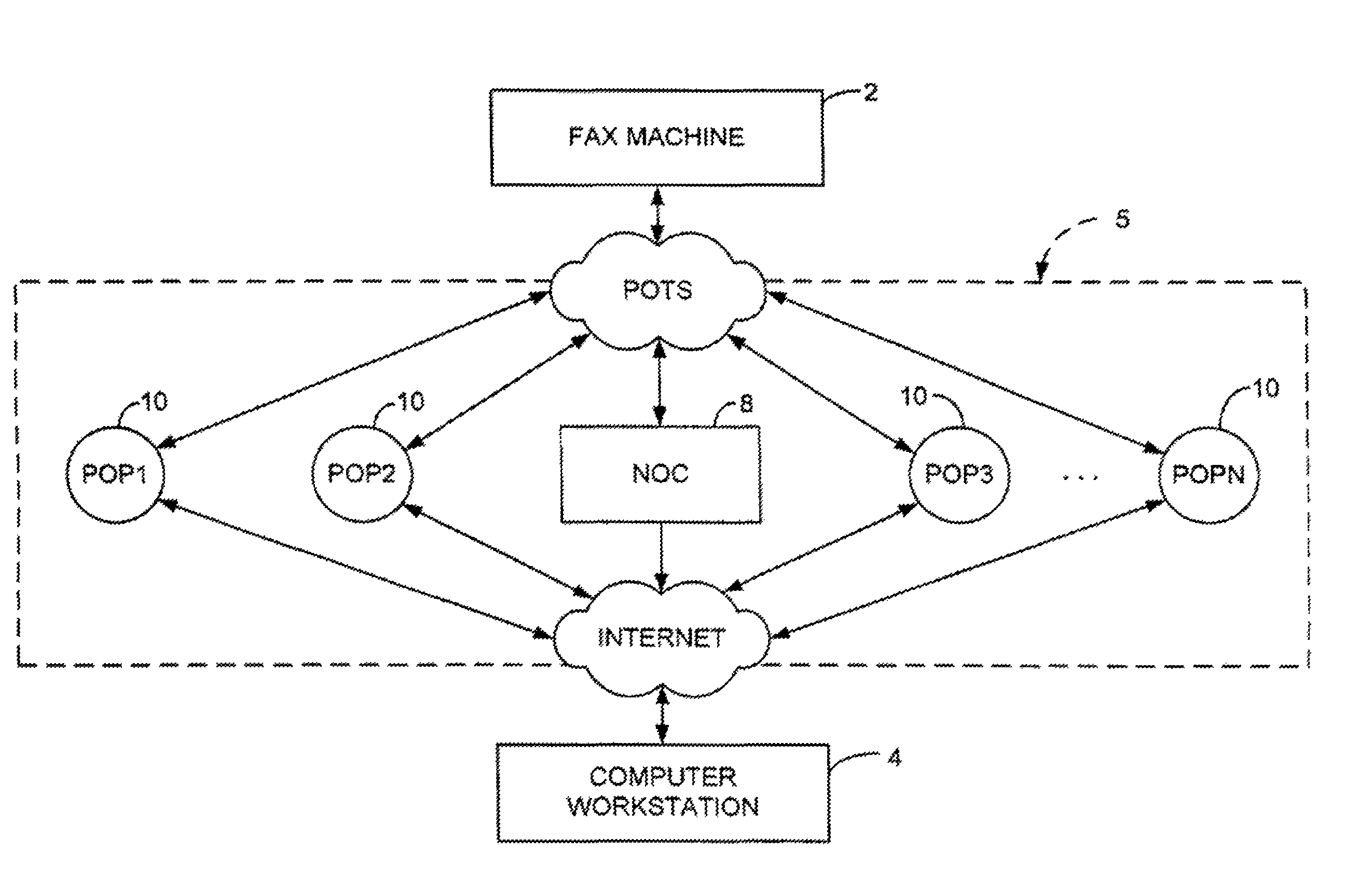
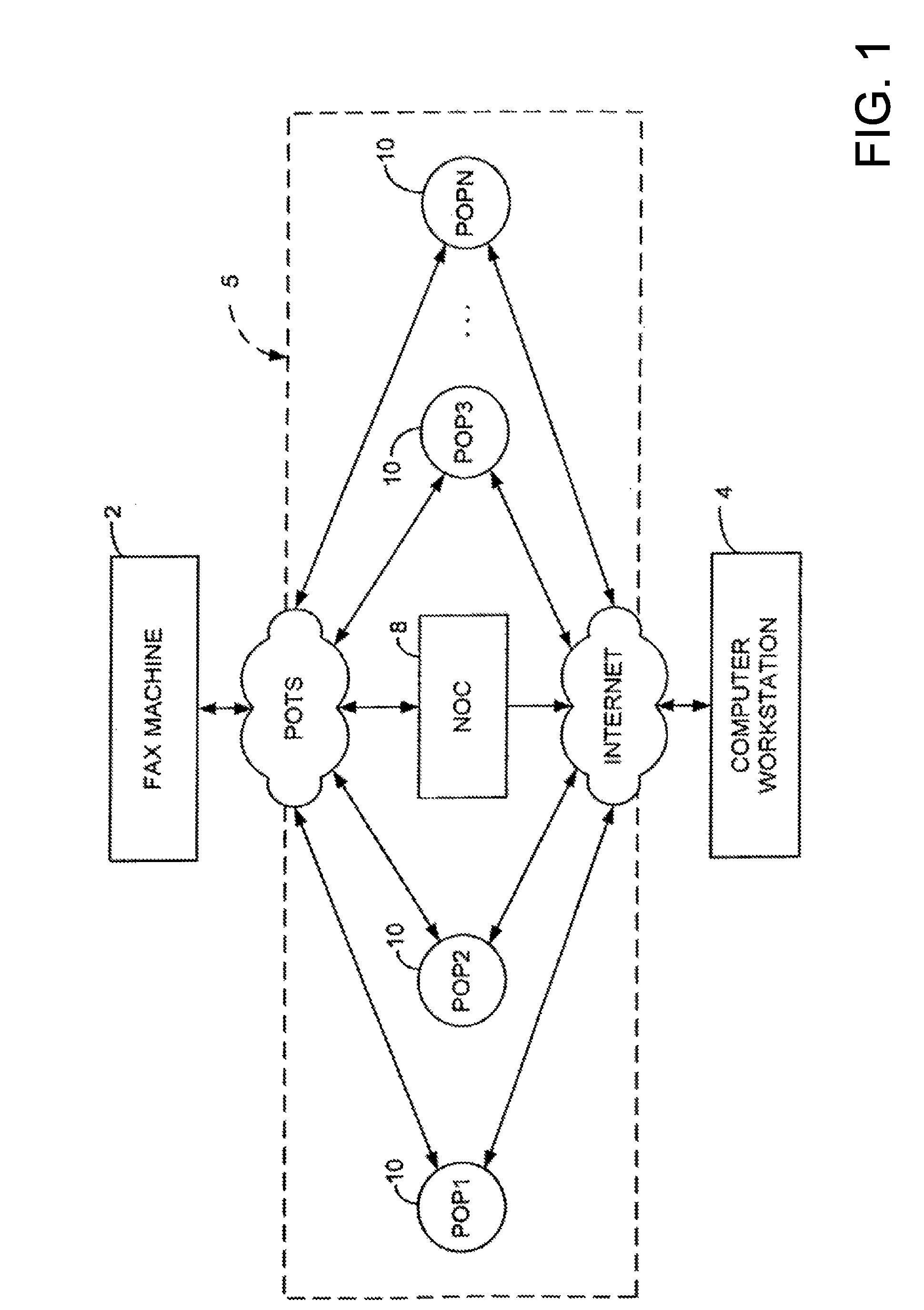
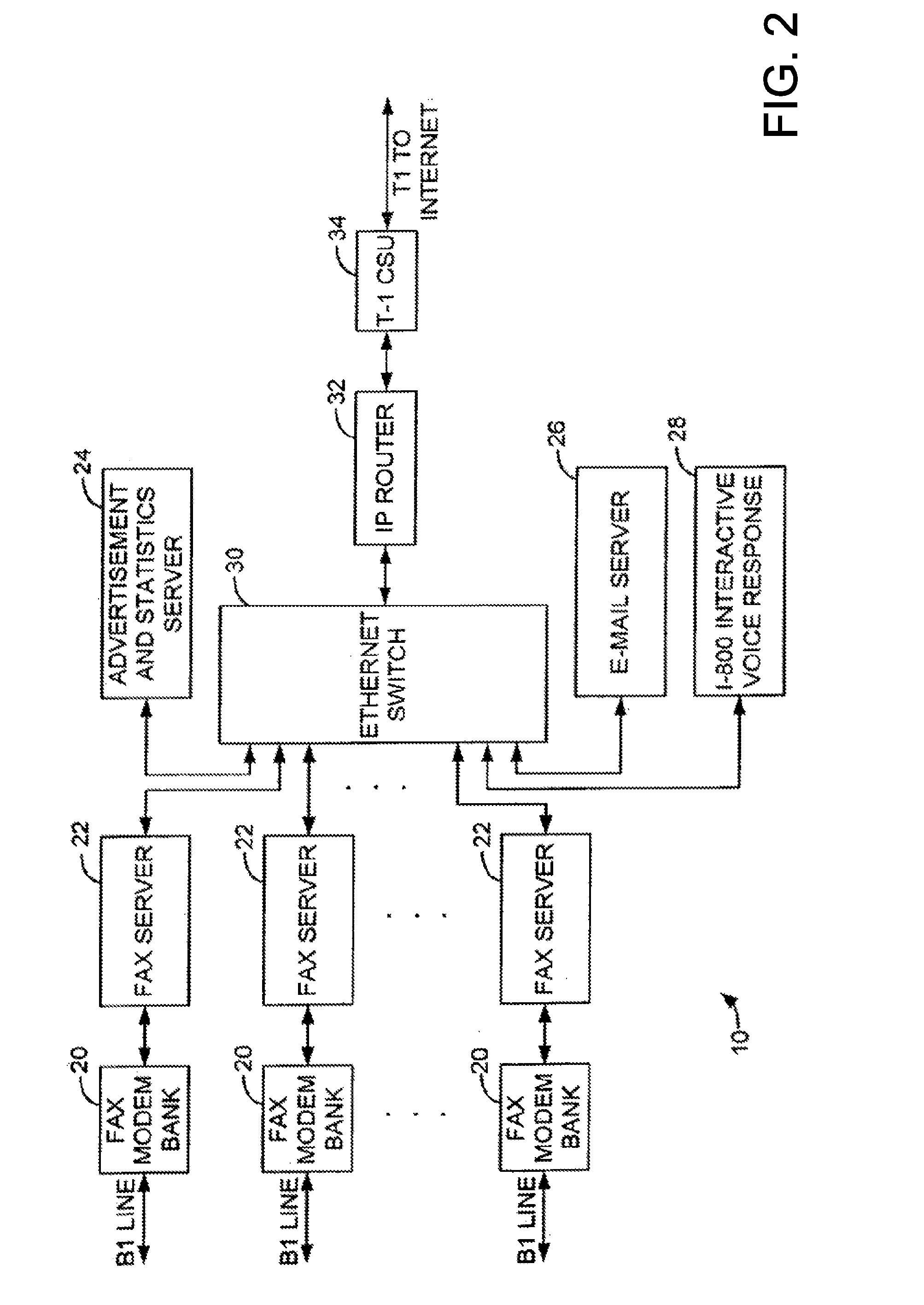
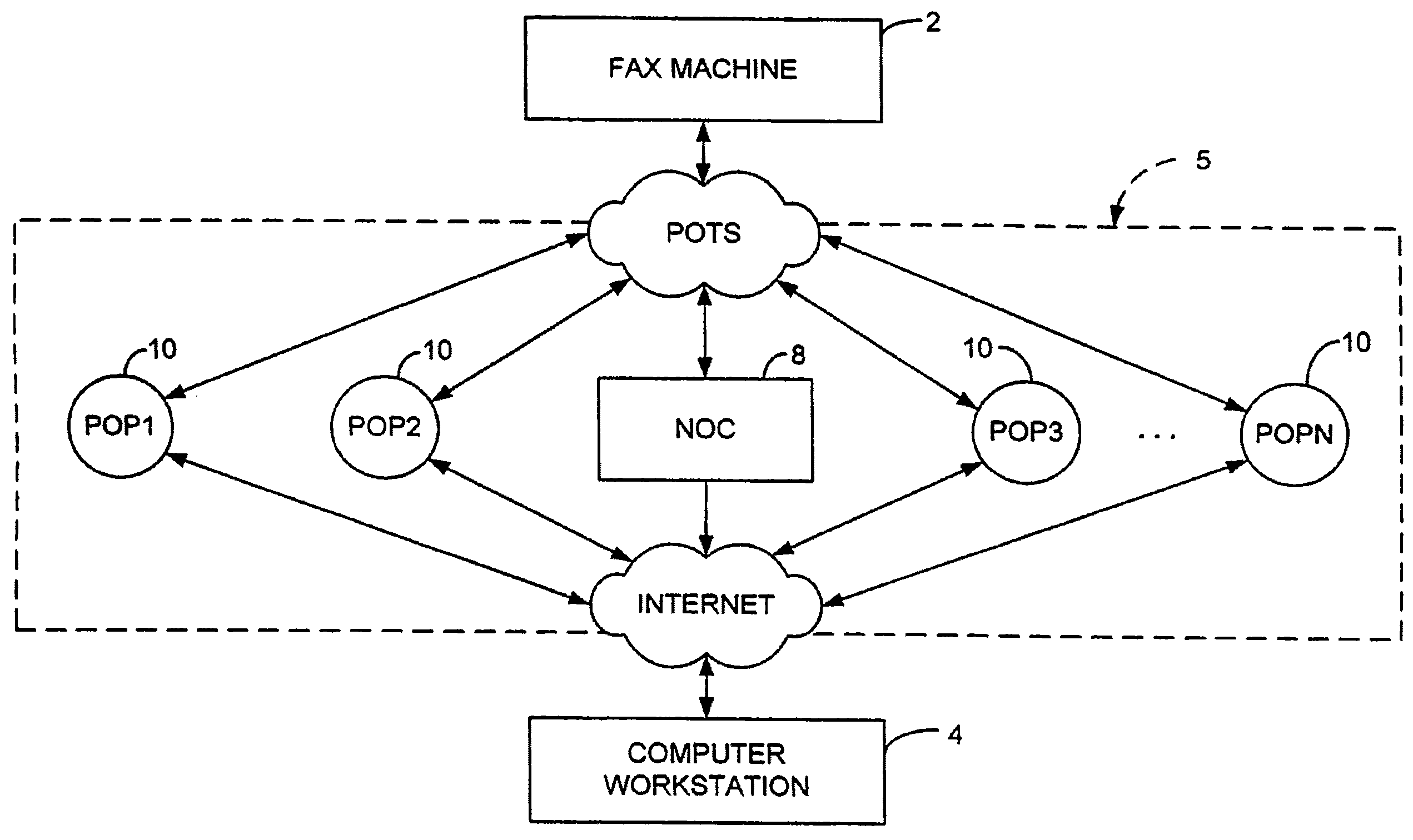
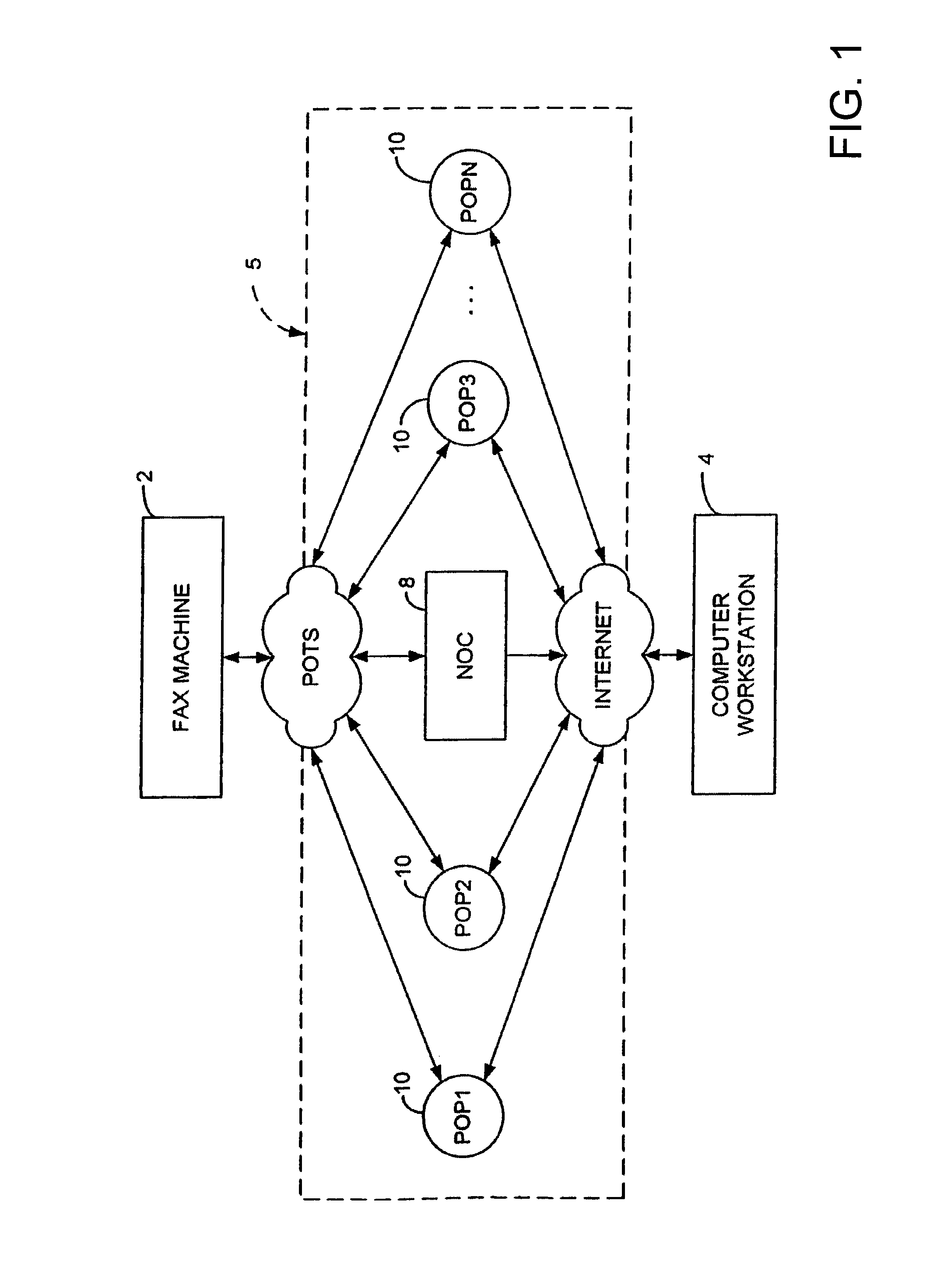
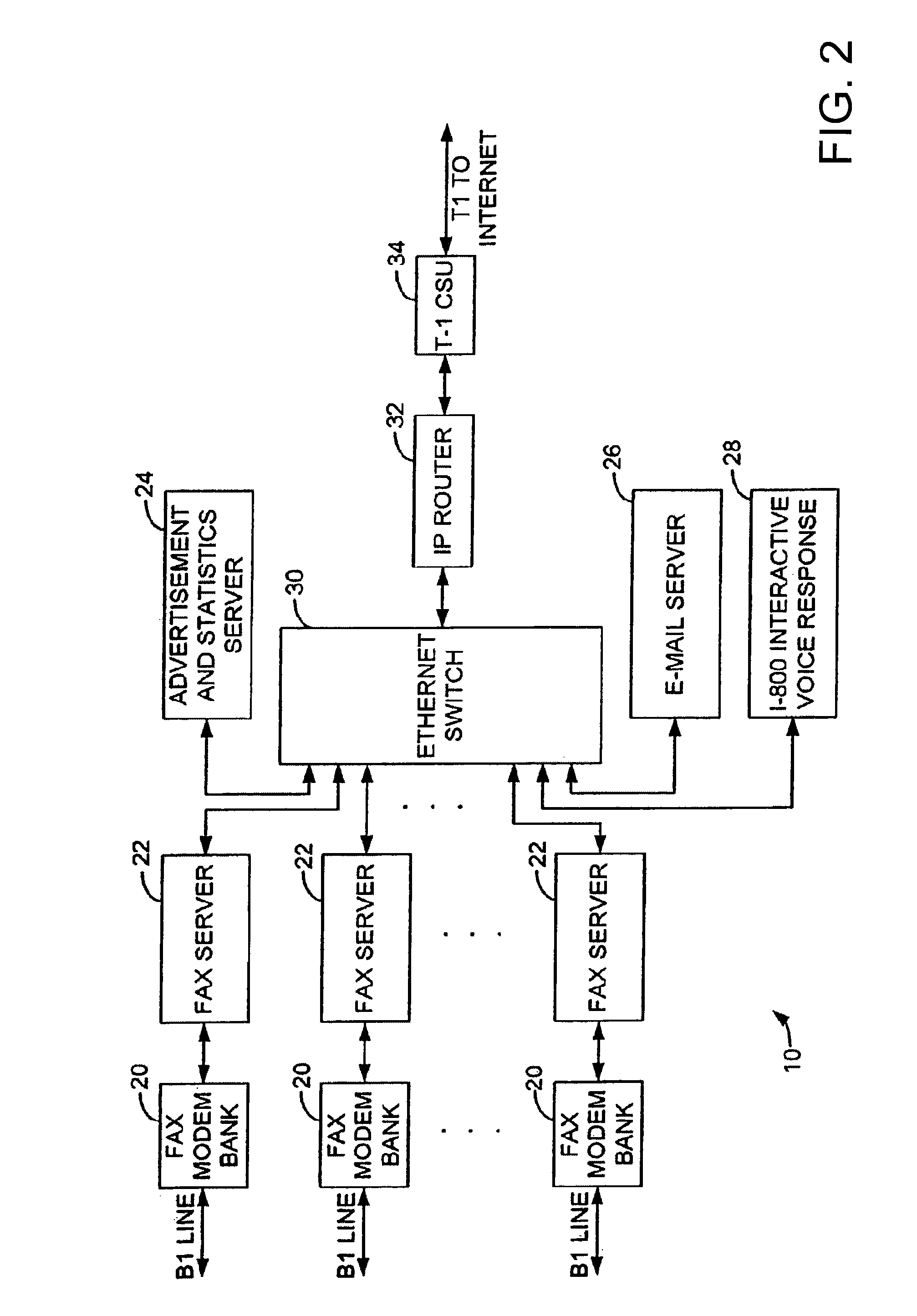
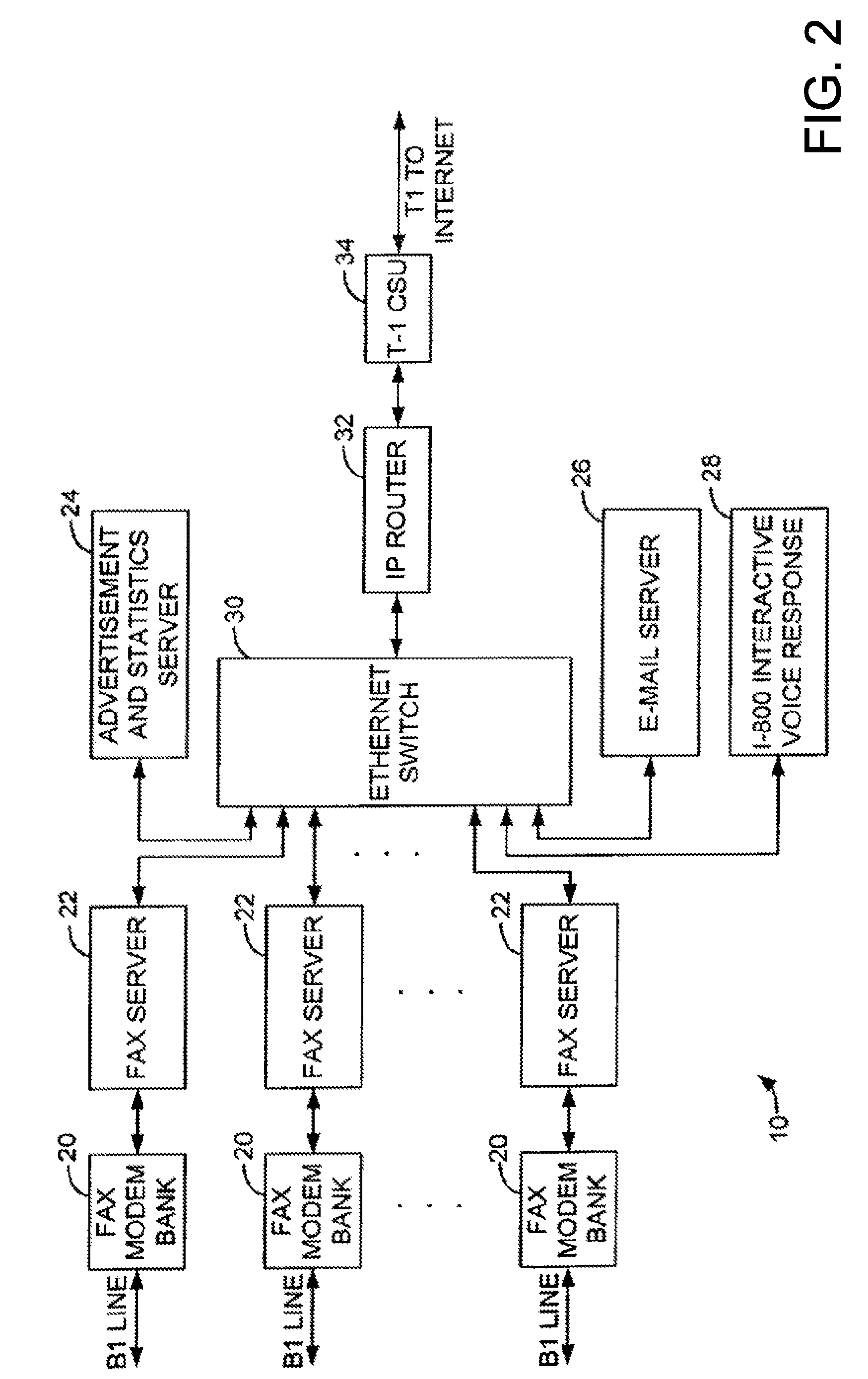
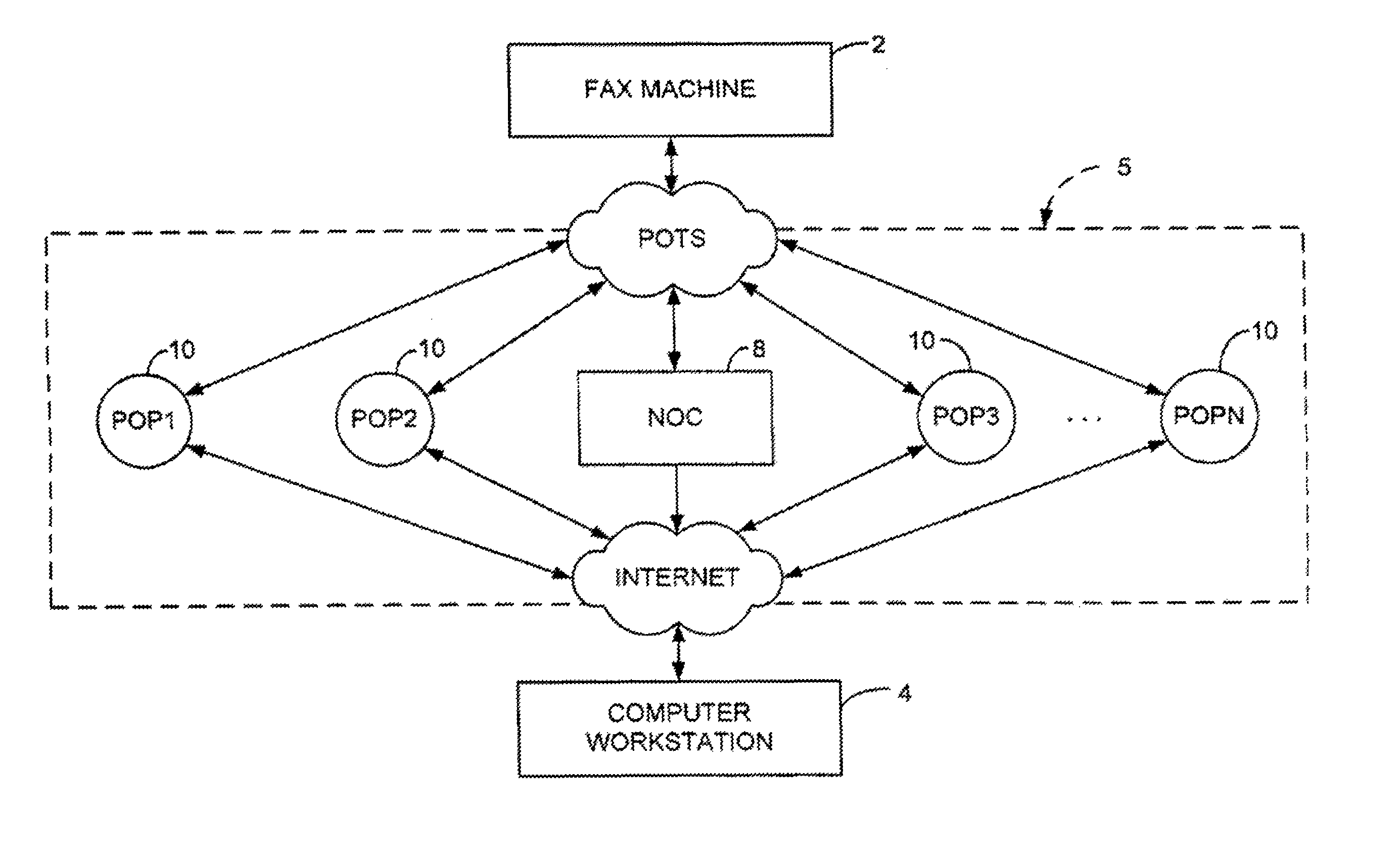
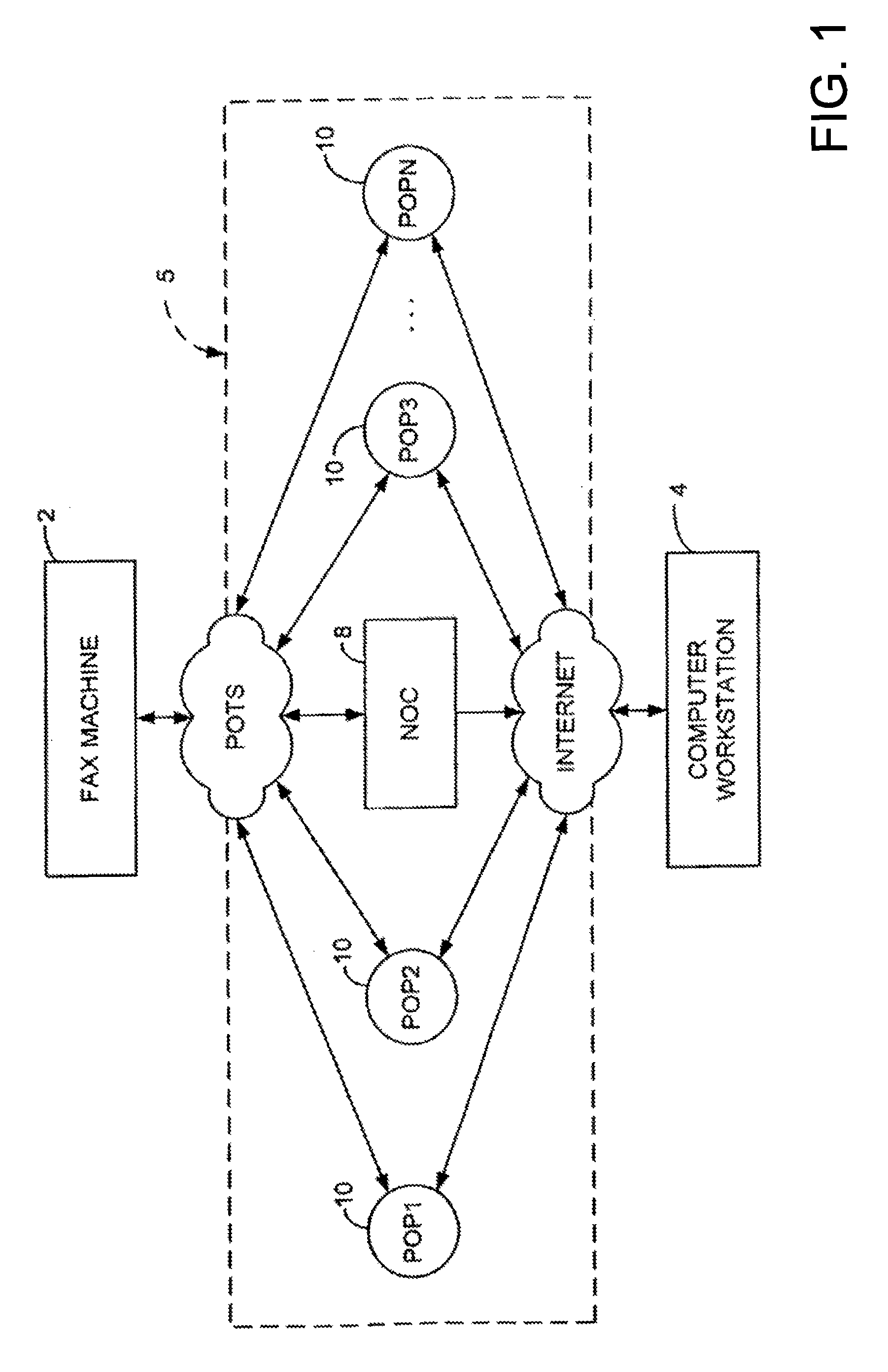
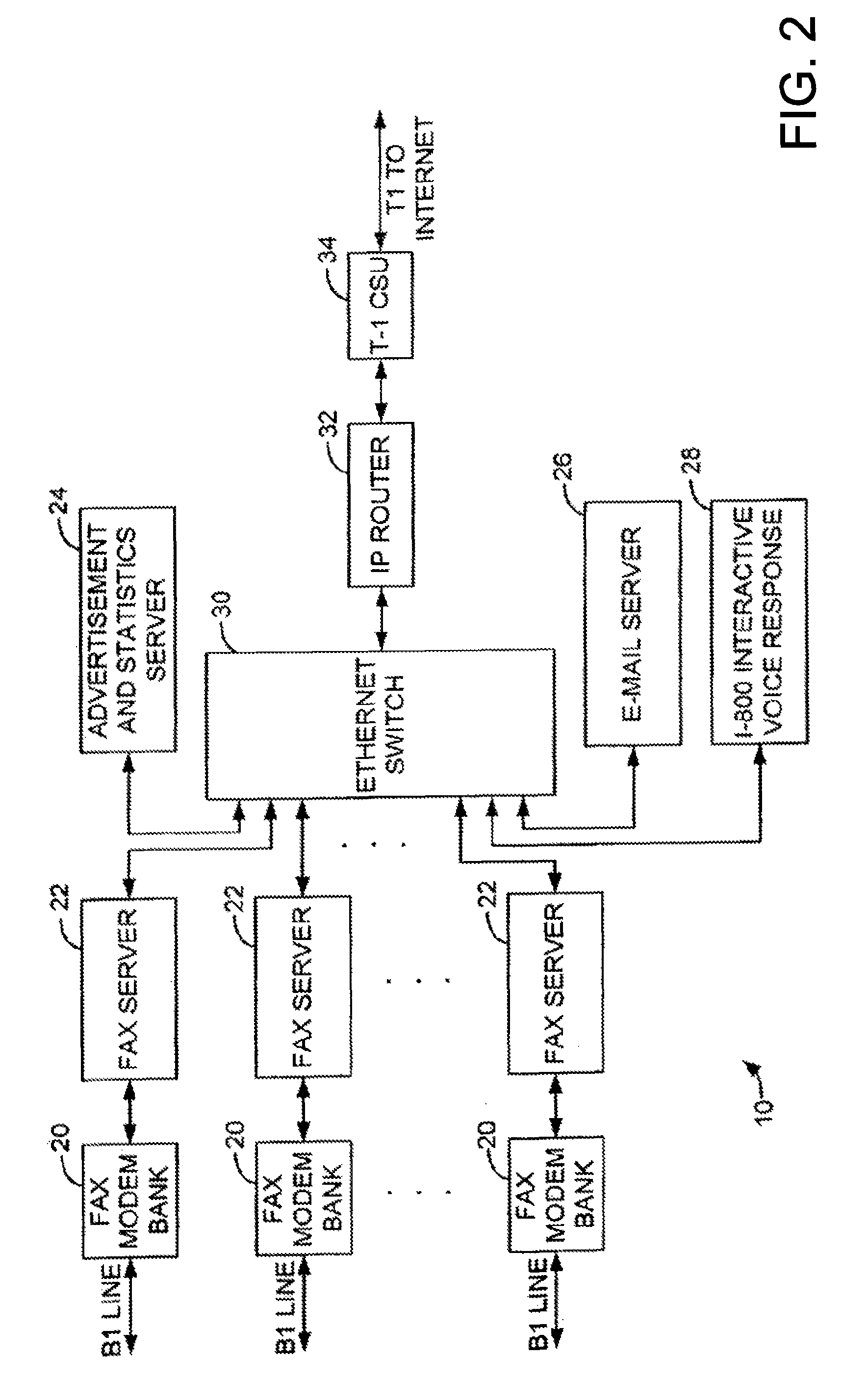
Sponsored Facsimile to E-Mail Transmission Methods and Apparatus
ActiveUS20100042523A1Shorten the timeReduce exposureComplete banking machinesFinanceEmail addressUser input
A method for sending an e-mail message comprises receiving a transmission instruction page, entering a plurality of text entries from a user on the transmission instruction page to form a filled-in transmission instruction page, wherein the plurality of text entries includes an e-mail address, and sending a facsimile to a facsimile server, wherein the facsimile includes the filled-in transmission instruction page and one or more pages of a document, wherein the facsimile server converts the facsimile into an e-mail attachment, wherein the facsimile server sends the e-mail message including a service provider indicator and the e-mail attachment to the e-mail address, wherein the facsimile server optically derives the e-mail address from the transmission instruction page of the facsimile, and wherein facsimile server need not know the e-mail address prior to receiving the facsimile.
Owner:J2 CLOUD SERVICES LLC
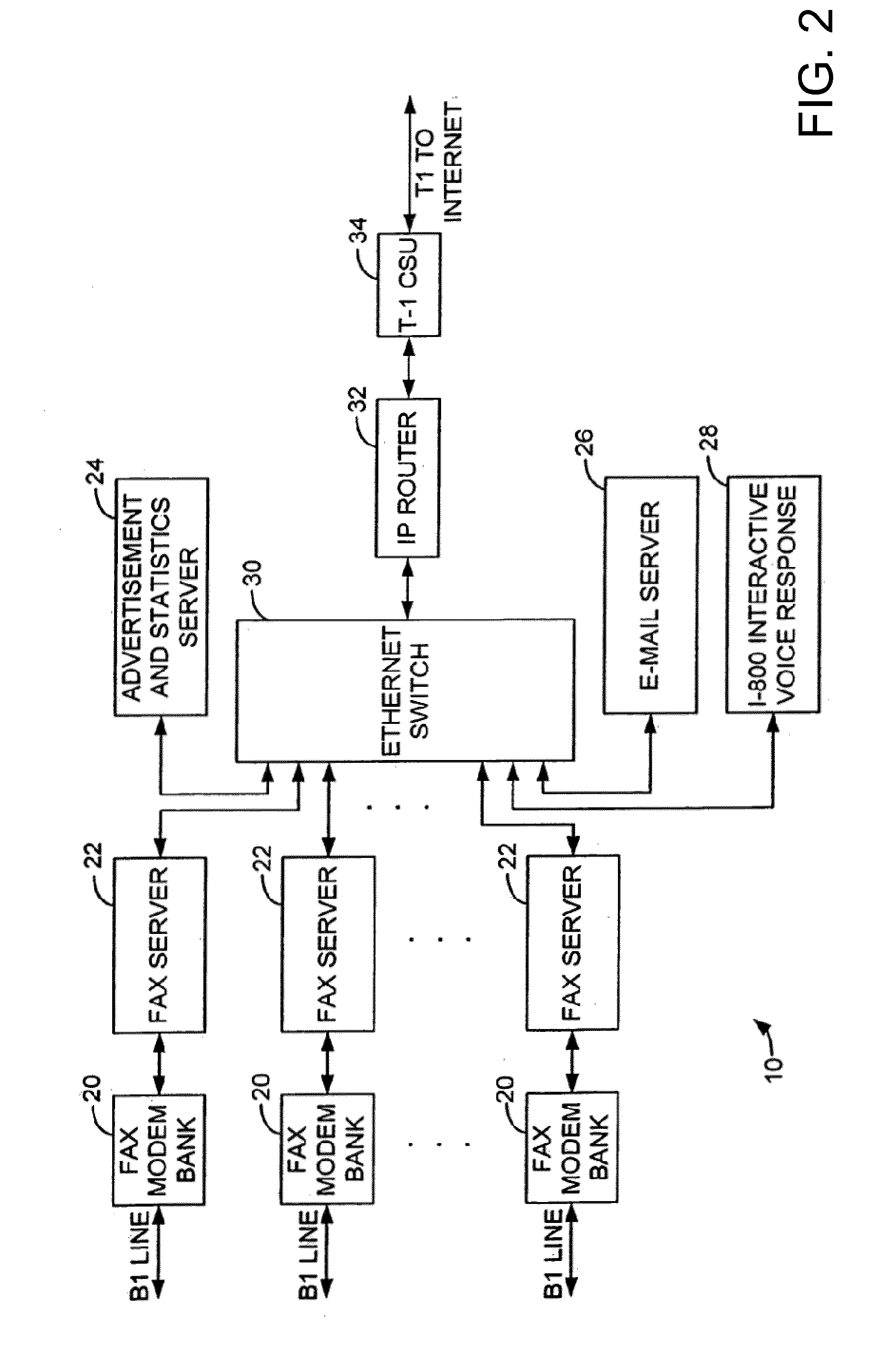
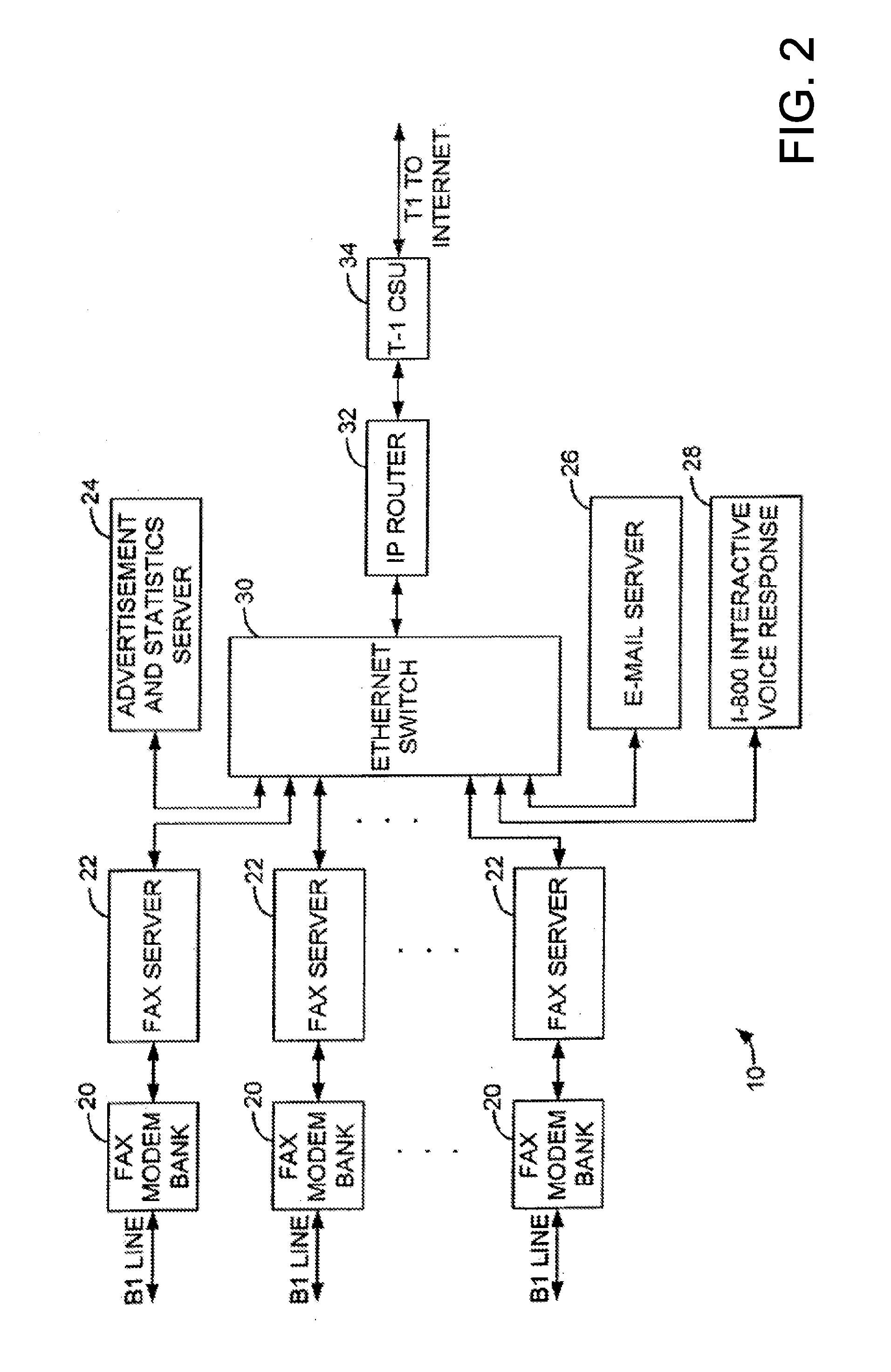
Method and system for pay per use document transfer via computer network transfer protocols
InactiveUS7746496B2Reduce probabilityShorten the timeTelephonic communicationDigital computer detailsService provisionFacsimile transmission
A system includes a portion for receiving a transmission comprising a digitized document including a digitized computer network destination associated with a recipient from a user using a facsimile device, a portion for determining a telephone number for the facsimile device, an OCR portion for determining the computer network destination for the recipient from the digitized computer network destination for the recipient, a portion for determining an attachment from the digitized document, and a portion for sending the attachment to the computer network destination for the recipient including a service provider name, wherein the transmission is associated a pay-per-use service charge that may be asserted against the telephone number associated with the facsimile transmission device.
Owner:ADVANCED MESSAGING TECH INC
Method and system for pay per use document transfer via computer network transfer protocols
InactiveUS20070229889A1Reduce probabilityShorten the timeDigital computer detailsCharacter and pattern recognitionService provisionPaper document
A system includes a portion for receiving a transmission comprising a digitized document including a digitized computer network destination associated with a recipient from a user using a facsimile device, a portion for determining a telephone number for the facsimile device, an OCR portion for determining the computer network destination for the recipient from the digitized computer network destination for the recipient, a portion for determining an attachment from the digitized document, and a portion for sending the attachment to the computer network destination for the recipient including a service provider name, wherein the transmission is associated a pay-per-use service charge that may be asserted against the telephone number associated with the facsimile transmission device.
Owner:ADVANCED MESSAGING TECH INC
Methods and apparatus for authenticating facsimile transmissions to electronic storage destinations
InactiveUS20070236749A1Shorten the timeReduce exposureCharacter and pattern recognitionPictoral communicationComputer hardwareService provision
A method for a computer system comprises receiving the facsimile or scanned image comprising a digitized instruction page and document, wherein the instruction page includes an optical representation of an electronic destination address, and wherein the document is encoded in a first format, determining the electronic destination address from the optical representation of the electronic destination address, wherein the electronic destination address need not be known before receiving the facsimile or scanned image, converting the document encoded from the first format to a second format and adding a watermark, determining service provider data, and transmitting the service provider data and the document encoded in the second format to the electronic destination address.
Owner:J2 CLOUD SERVICES LLC
Methods and apparatus for compositing facsimile transmissions to electronic storage destinations
InactiveUS20070236732A1Reduce exposureHigh level of privacyCharacter and pattern recognitionPictoral communicationService providerCompound Document Format
A method for a computer system includes receiving a facsimile including a digitized transmission page including an optical representation of the electronic destination address encoded in a facsimile format, determining the electronic destination address from the optical representation of the electronic destination address, combining the transmission page with a graphics template to form a composite document, formatting the composite document into a second format, determining additional service provider data in response to the facsimile, and transmitting the additional service provider data and the composite document in the second format to the electronic destination address.
Owner:J2 CLOUD SERVICES LLC
Method and system for entry of electronic data via fax-to-email communication
InactiveUS20070237314A1Shorten the timeReduce exposureTelephonic communicationCharacter and pattern recognitionEmail addressService provision
A method for a computer system for transmitting a facsimile to an e-mail destination, comprises receiving a facsimile transmission comprising an instruction page and a document page, wherein the instruction page includes an optical representation of an e-mail address, using an optical character recognition process to determine the e-mail address from the optical representation of the e-mail address, wherein the e-mail address need not be known to the computer system before receiving the facsimile transmission, converting the facsimile transmission into an e-mail attachment, and sending an e-mail message including the additional service provider data and the e-mail attachment to the e-mail address, wherein the additional service provider data is selected from a group consisting of: a service provider identifier, a service sponsor identifier.
Owner:ADVANCED MESSAGING TECH INC
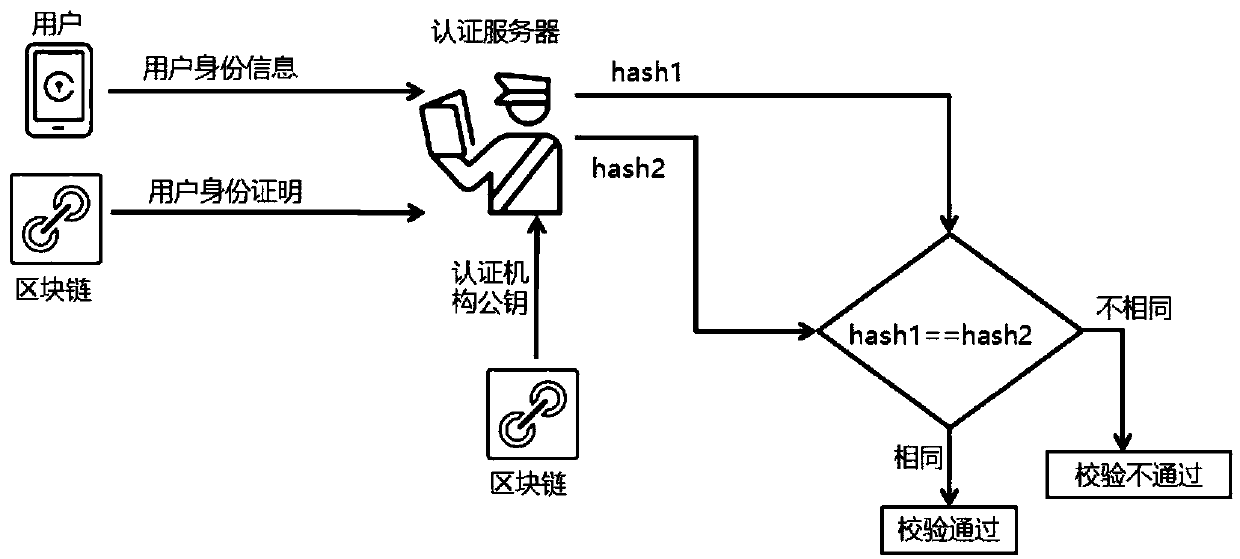
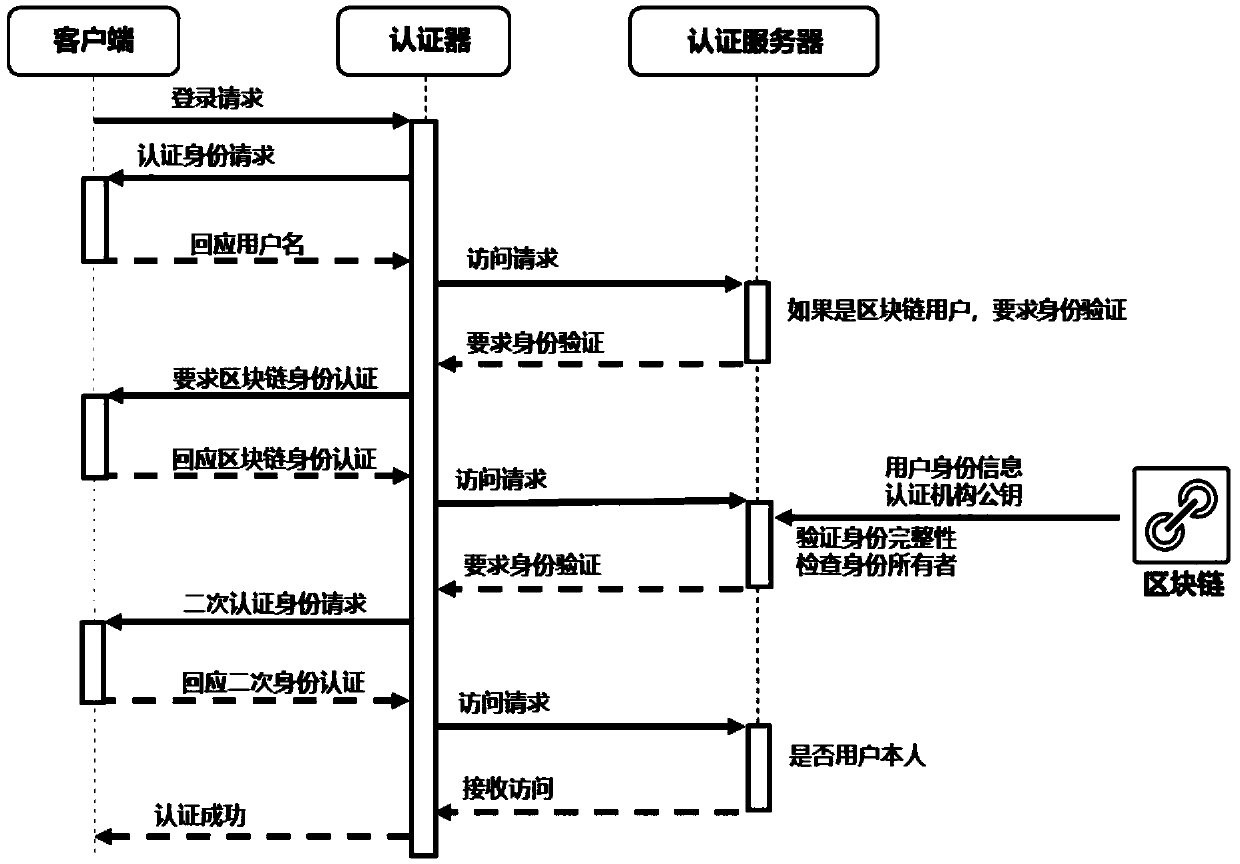
System and method for login authentication
The invention provides a system and a method for login authentication. The method comprises the steps of: sending login request information by a login end, wherein the login request information comprises a user name; receiving the login request information by an authentication end, after confirming that the login end is a blockchain user, initiating blockchain identity authentication for the loginend; performing second authentication on the login end by the authentication end after the blockchain identity authentication is passed; acquiring user identity information of the login end by the authentication end, and acquiring user identification and a certification organization public key from a blockchain; and verifying the user identity information by using the user identification and thecertification organization public key by the authentication end. The system and the method of the invention have the beneficial effects that: the identification stored in the blockchain can not be tampered, thereby improving security and reducing IT maintenance cost of an enterprise; the second authentication is performed after the identity authentication is passed, thereby greatly improving enterprise level Wi-Fi security; and verification is based on the user identity information, the user does not need to input a Wi-Fi login key, thereby effectively preventing a stealing behavior of a Wi-Fiall-purpose key app.
Owner:上海邑游网络科技有限公司
Methods and apparatus for web-based status of facsimile transmissions to electronic storage destinations
InactiveUS20090059271A1Shorten the timeReduce exposurePictoral communicationDigital output to print unitsGraphicsFacsimile transmission
A method for a computer includes determining a call-in fax telephone number called by a facsimile transmission device, receiving the facsimile transmission from a facsimile transmission device including a digitized representation of a transmission page including an optical representation of data associated with an e-mail address, determining the data optically, which is independent of the call-in number, determining a graphics template associated with the call-in number, combining a digitized representation of the transmission page with the graphics template to form a digitized representation of a composite page, formatting the digitized representation of the composite page into a second format, determining additional service provider data in response to the facsimile or the scanned image, and transmitting the additional service provider data and the digitized representation of the composite page in the second format to the electronic destination address.
Owner:MONGONET INC
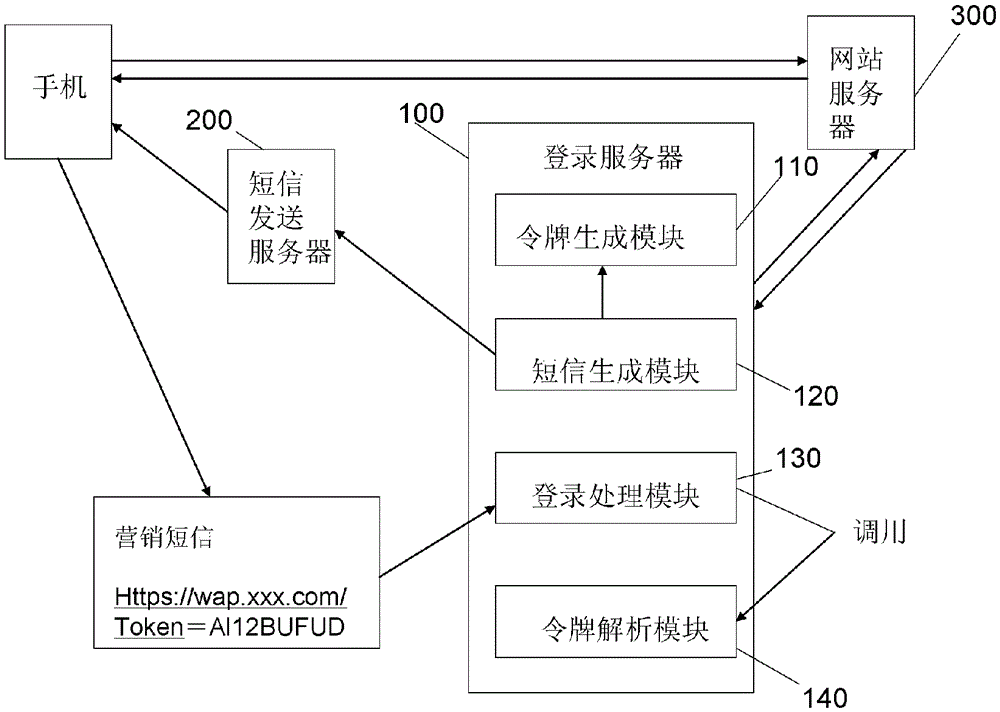
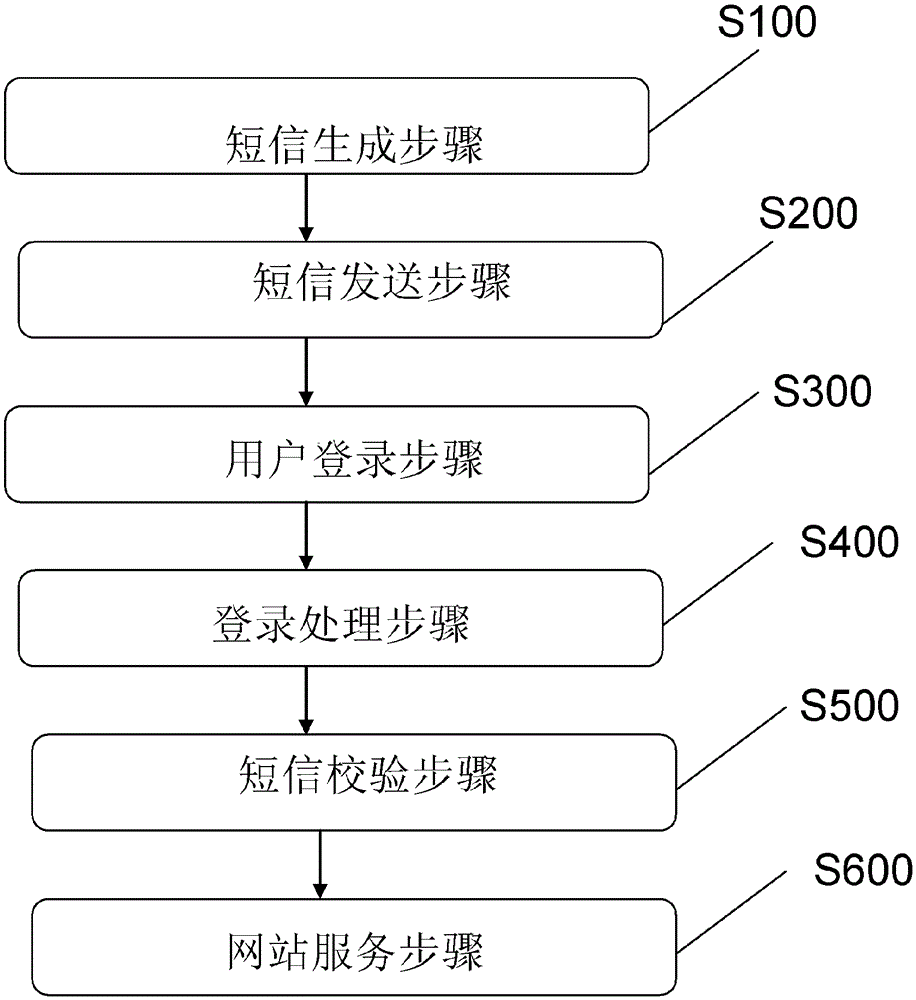
Method and system for website registration on the basis of mobile phone message
ActiveCN105592065AImprove the effect of marketing promotionHigh activityInformation formatContent conversionMobile Telephone NumberWorld Wide Web
The present invention relates to a method and system for website registration on the basis of a mobile phone message. The method comprises the following steps: generating a short message containing a website when generating the only token for each mobile phone number and generating the website containing the token for registration; sending the short message generated in the short message generation step to an object mobile phone number; clicking the website included in the short message and sending a registration request after a user receives the short message; verifying the registration request, obtaining the object mobile phone number according to the registration request in the condition of successful verification, and prompting the error information in the condition of the failure of verification; and taking the mobile phone number obtained in the registration processing step as a user identification, and providing a website service for the user mobile phone. According to the invention, a method and system for website registration on the basis of a mobile phone message capable of ensuring the registration security and rapid and simple website registration are provided.
Owner:CHINA UNIONPAY
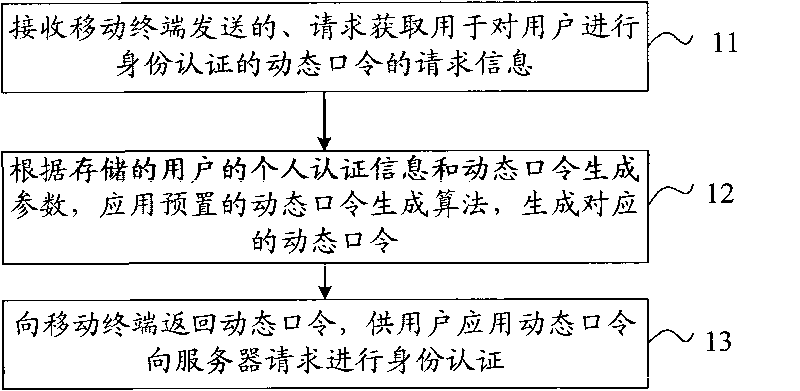
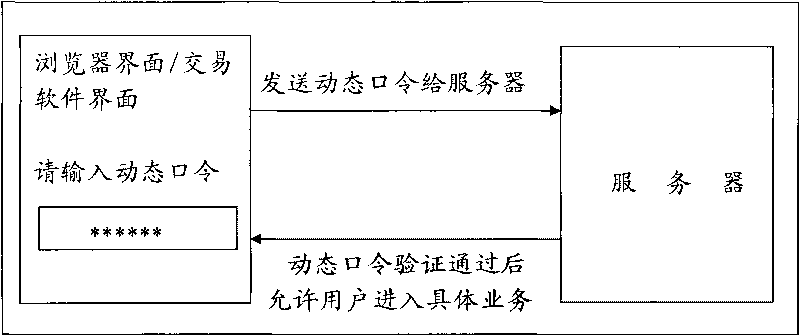
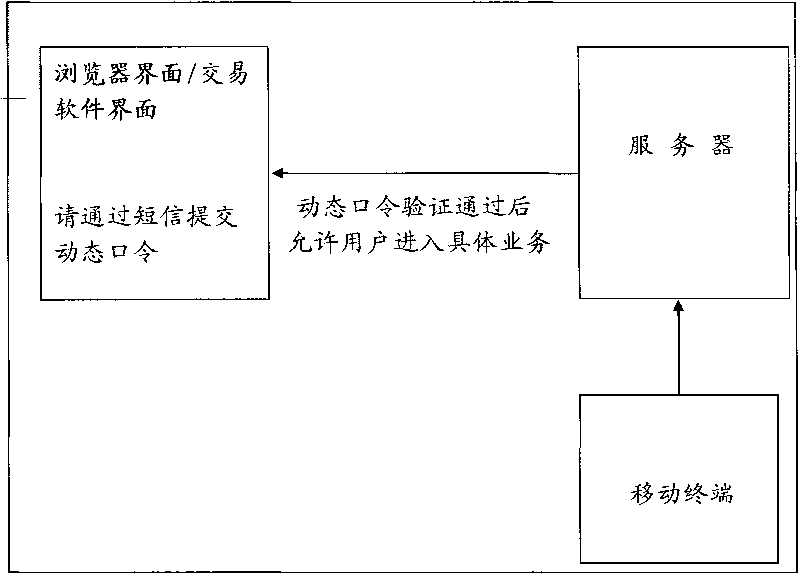
Method and device for generating dynamic passwords and network system
ActiveCN101699892ALogin securitySecure Electronic TransactionsSecurity arrangementPasswordNetworked system
The invention discloses a method and a device for generating dynamic passwords and a network system. The method for generating the dynamic passwords comprises the following steps: receiving request information for acquiring a dynamic password used for the authentification of a user, wherein the request information is sent by a mobile terminal, wherein the request information is sent by the mobile terminal and carries dynamic password generation parameters when the user triggers the mobile terminal to acquire the dynamic password after a server prompts the user to submit the dynamic password; generating a corresponding dynamic password by using a preset dynamic password generating algorithm according to the stored personal certification information of the user and the dynamic password generation parameters; and returning the dynamic password to the mobile terminal, wherein the dynamic password is used by the user to request the server to authenticate the identity. The method and the device are suitable for the user to submit the dynamic password to the server for the identity authentication when the user logs in and visits the server through a client browser or client software, or performs an electronic transaction.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
Methods and apparatus for facsimile transmissions to electronic storage destinations including embedded barcode fonts
A method for a computer includes determining a call-in fax telephone number called by a facsimile transmission device, receiving the facsimile transmission from a facsimile transmission device including a digitized representation of a transmission page including an optical representation of data associated with an e-mail address, determining the data optically, which is independent of the call-in number, determining a graphics template associated with the call-in number, combining a digitized representation of the transmission page with the graphics template to form a digitized representation of a composite page, formatting the digitized representation of the composite page into a second format, determining additional service provider data in response to the facsimile or the scanned image, and transmitting the additional service provider data and the digitized representation of the composite page in the second format to the electronic destination address.
Owner:J2 CLOUD SERVICES LLC
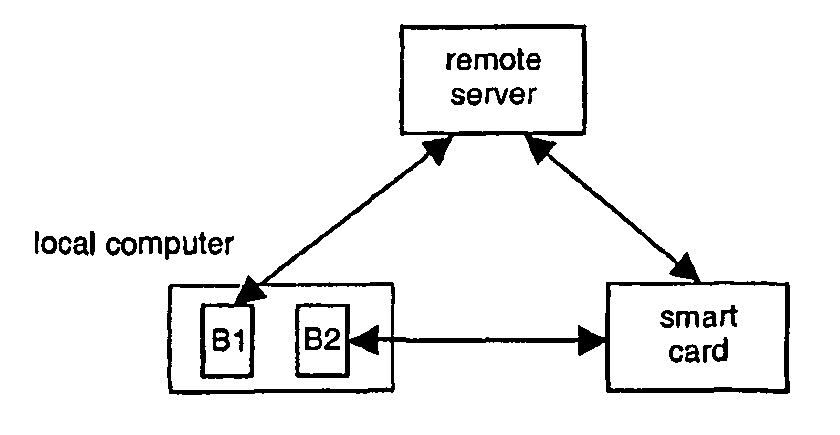
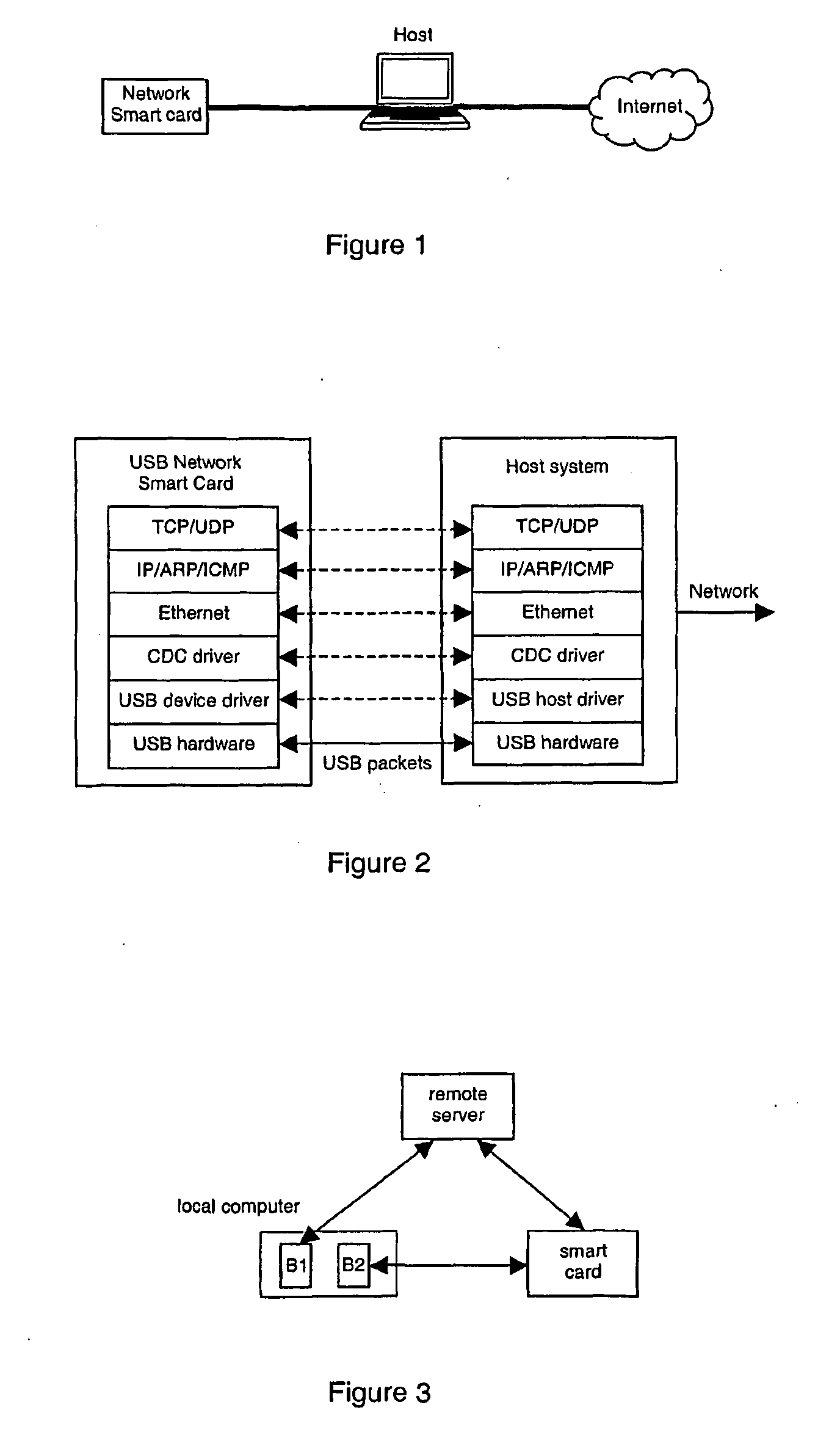
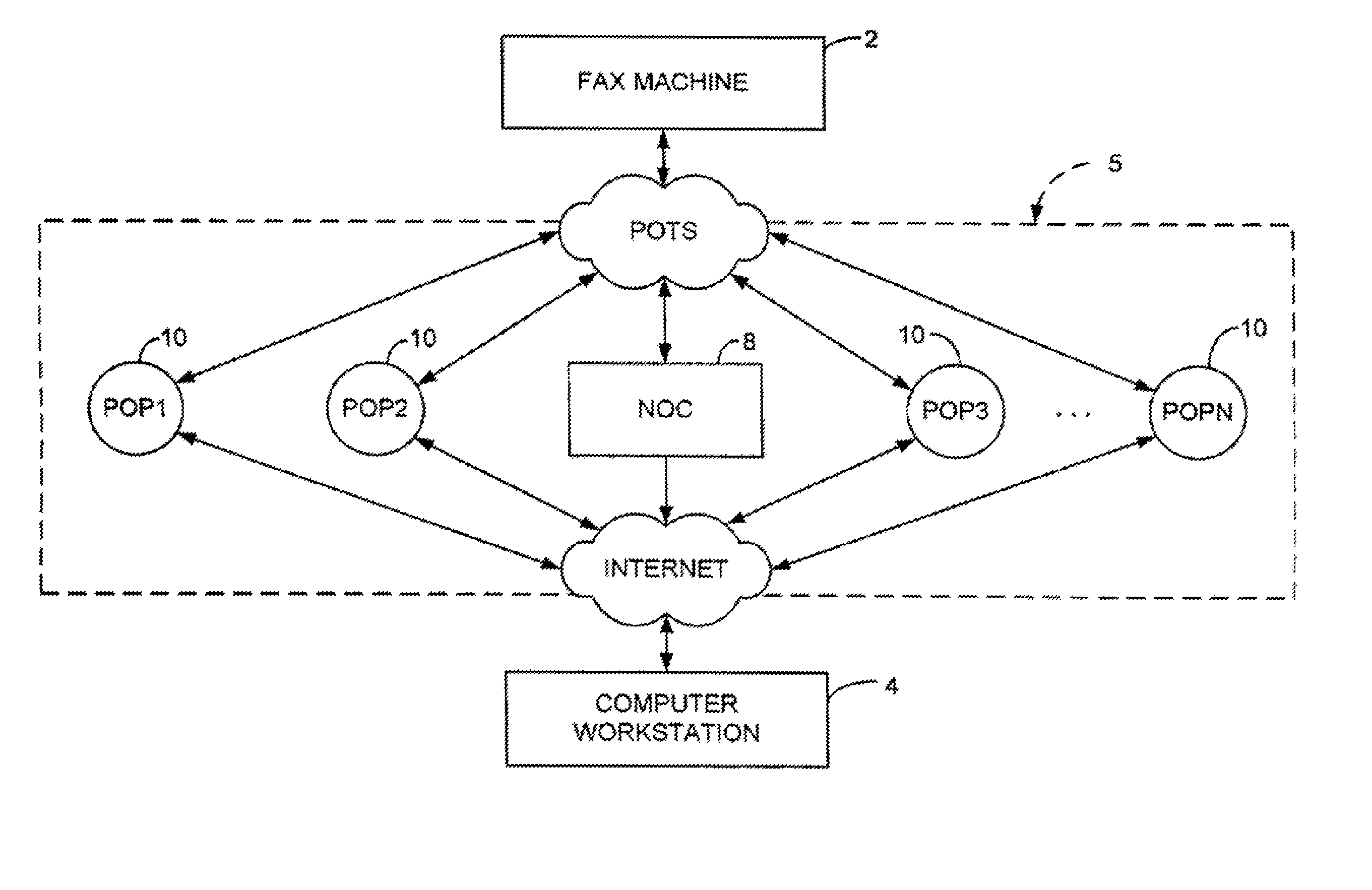
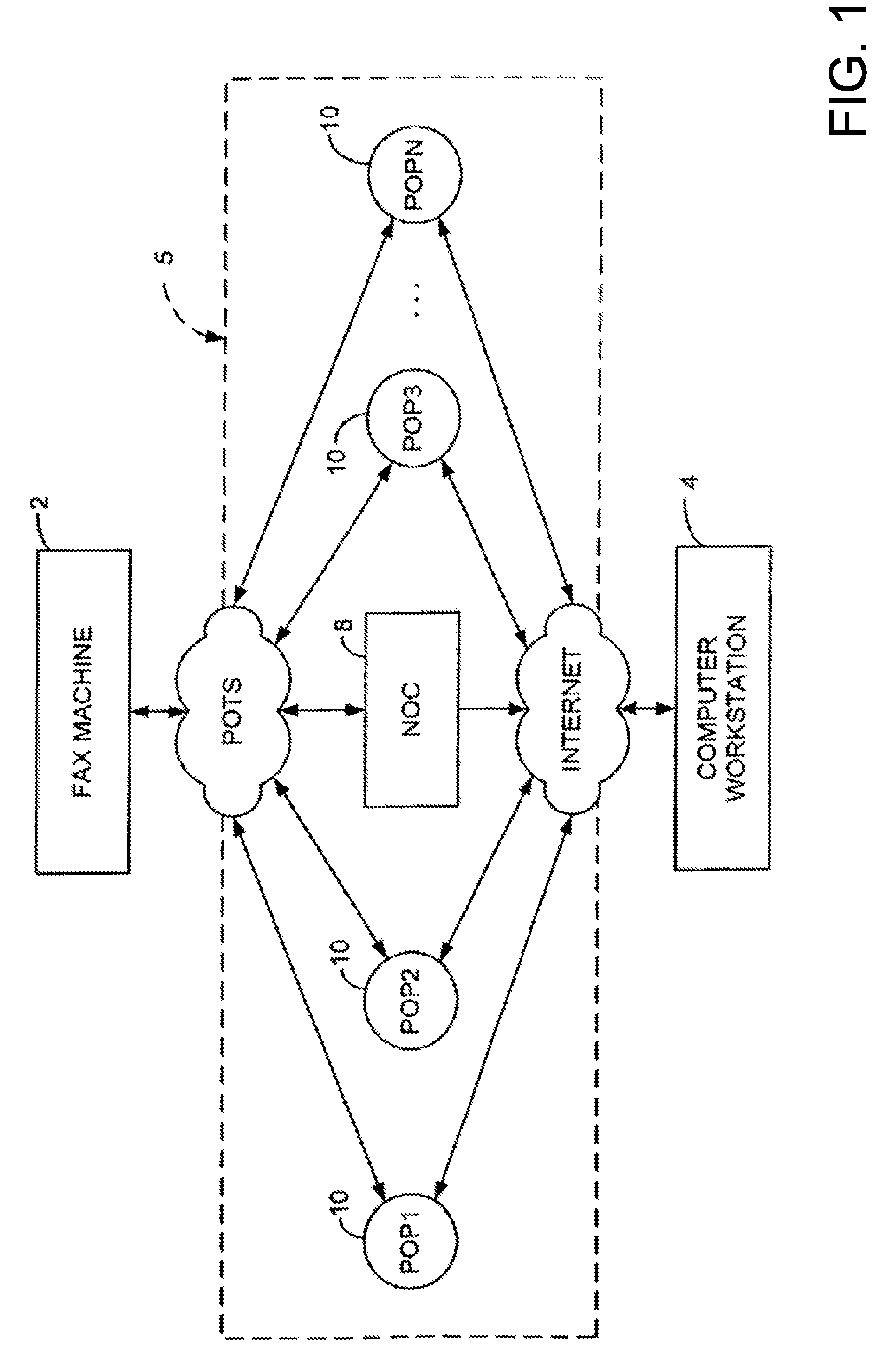
Method of Securely Logging Into Remote Servers
InactiveUS20100169962A1Login securityProvide convenienceDigital data processing detailsAnalogue secracy/subscription systemsNetwork connectionWeb service
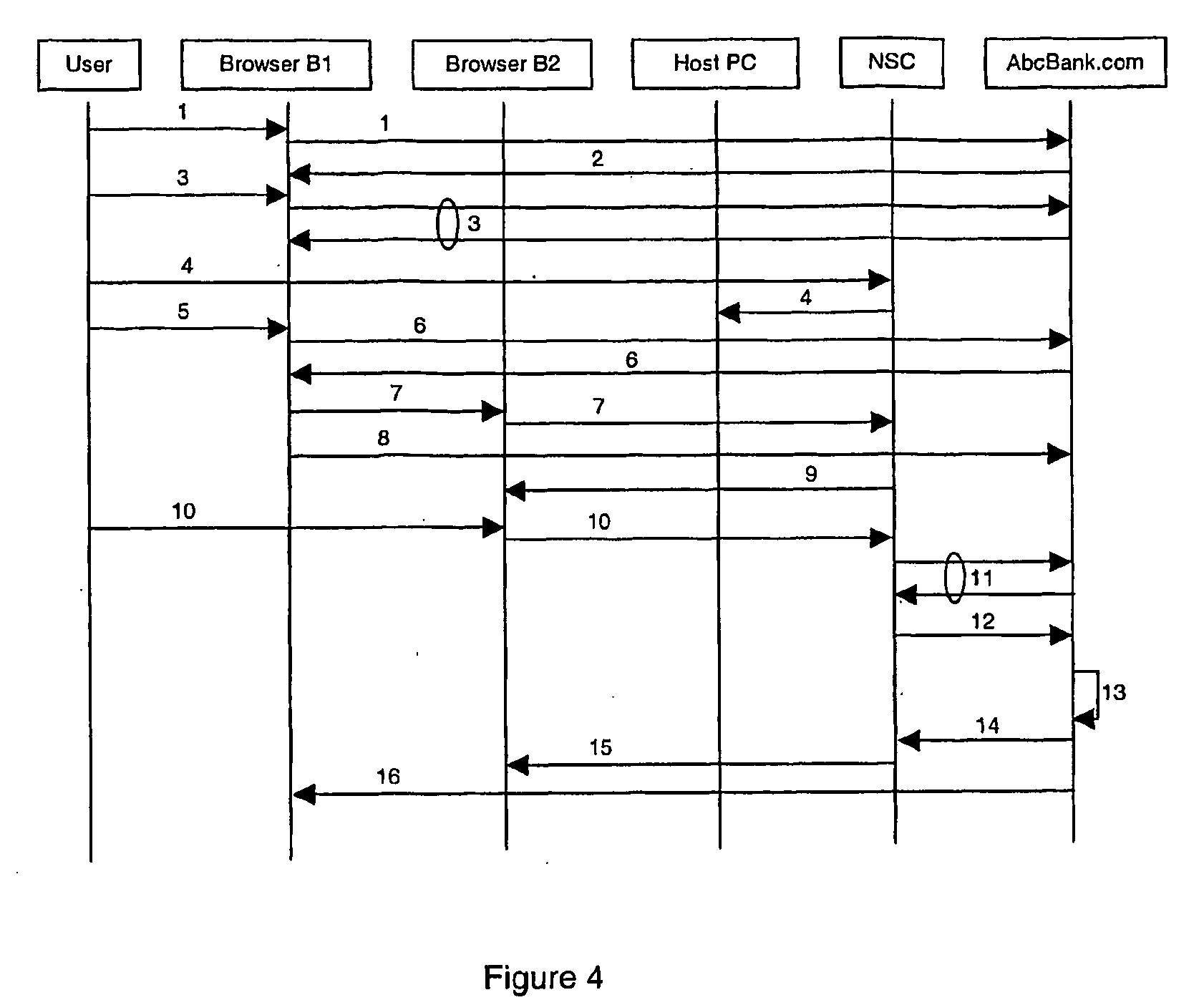
The invention relates to a system comprising a network device (NSC), a host computer (HOST) and a remote server remote (SRV). The host computer (HOST) and the network device (NSC) server are connectable through a network. The host computer (HOST) and the remote server (SRV) are connectable through the Internet. The smart network device (NSC) comprises a web server accessible from the host computer (HOST). The network device (NSC) is set to store a user's authentication credential. The host computer (HOST) is set to display a web page produced by the remote server (SRV) to the user. The remote server (SRV) is set to include a login link in said web page, the login link pointing to said web server. The web server is set to display a login page to the user on the host computer (HOST) when the user clicks on said login link, in order to authenticate the user. Upon authentication of the user, the network device (NSC) is set to send the user's authentication credential to the remote server (SRV) in order to authenticate the user to the remote server (SRV).
Owner:GEMPLU
Methods and apparatus for facsimile transmissions to electronic storage destinations including tracking data
InactiveUS20080130040A1Shorten the timeReduce exposureDigital computer detailsCharacter and pattern recognitionGraphicsFacsimile transmission
A method for a computer includes determining a call-in fax telephone number called by a facsimile transmission device, receiving the facsimile transmission from a facsimile transmission device including a digitized representation of a transmission page including an optical representation of data associated with an e-mail address, determining the data optically, which is independent of the call-in number, determining a graphics template associated with the call-in number, combining a digitized representation of the transmission page with the graphics template to form a digitized representation of a composite page, formatting the digitized representation of the composite page into a second format, determining additional service provider data in response to the facsimile or the scanned image, and transmitting the additional service provider data and the digitized representation of the composite page in the second format to the electronic destination address.
Owner:J2 CLOUD SERVICES LLC
Integrated financial transaction and access system
InactiveUS20090072020A1Improve abilitiesEasy to useComplete banking machinesFinanceInternet privacyIndividual data
A universal digital information management and transaction system facilitates a consumer's ability to organize, use and obtain personal data related to a consumer, including for example, the consumer's financial, health, and personal records. A consumer is provided with an online profile that stores all of the relevant consumer information, with a token associated with the consumer's profile to enable the consumer to securely login remotely to the system to access and manage all of their relevant information.
Owner:HULL ROBERT E
Method and system for modified document transfer via computer network transfer protocols
InactiveUS20070223051A1Reduce probabilityShorten the timeCharacter and pattern recognitionPictoral communicationComputer hardwareService provision
A method transmitting a facsimile or scanned image to an electronic destination address includes receiving the facsimile or scanned image including a digitized instruction page including an optical representation of the electronic destination address, wherein the digitized instruction page is encoded in a first format, determining the electronic destination address from the optical representation of the electronic destination address, wherein the electronic destination address need not be known prior to receiving the facsimile or scanned image, converting the digitized instruction page to a second format, determining additional service provider data, and transmitting the additional service provider data and the digitized representation of the instruction page encoded in the second format to the electronic destination address.
Owner:ADVANCED MESSAGING TECH INC
Methods and apparatus for billing of facsimile transmissions to electronic storage destinations
InactiveUS20090034701A1Shorten the timeReduce exposureTelephonic communicationPictoral communicationGraphicsFacsimile transmission
A method for a computer includes determining a call-in fax telephone number called by a facsimile transmission device, receiving the facsimile transmission from a facsimile transmission device including a digitized representation of a transmission page including an optical representation of data associated with an e-mail address, determining the data optically, which is independent of the call-in number, determining a graphics template associated with the call-in number, combining a digitized representation of the transmission page with the graphics template to form a digitized representation of a composite page, formatting the digitized representation of the composite page into a second format, determining additional service provider data in response to the facsimile or the scanned image, and transmitting the additional service provider data and the digitized representation of the composite page in the second format to the electronic destination address.
Owner:J2 CLOUD SERVICES LLC
Method and system for modified document transfer via computer network transfer protocols
InactiveUS7817295B2Reduce probabilityShorten the timeDigital computer detailsTelephonic communicationComputer hardwareNetworked Transport of RTCM via Internet Protocol
A method transmitting a facsimile or scanned image to an electronic destination address includes receiving the facsimile or scanned image including a digitized instruction page including an optical representation of the electronic destination address, wherein the digitized instruction page is encoded in a first format, determining the electronic destination address from the optical representation of the electronic destination address, wherein the electronic destination address need not be known prior to receiving the facsimile or scanned image, converting the digitized instruction page to a second format, determining additional service provider data, and transmitting the additional service provider data and the digitized representation of the instruction page encoded in the second format to the electronic destination address.
Owner:ADVANCED MESSAGING TECH INC
Methods and apparatus for secure facsimile transmissions to electronic storage destinations
InactiveUS20080212144A1Reduce probabilityShorten the timeCharacter and pattern recognitionData switching by path configurationGraphicsEmail address
A method for a computer includes determining a call-in fax telephone number called by a facsimile transmission device, receiving the facsimile transmission from a facsimile transmission device including a digitized representation of a transmission page including an optical representation of a e-mail address, determining the e-mail address optically, which is independent of the call-in number, determining a graphics template associated with the call-in number, combining a digitized representation of the transmission page with the graphics template to form a digitized representation of a composite page, formatting the digitized representation of the composite page into a second format, determining additional service provider data in response to the facsimile or the scanned image, and transmitting the additional service provider data and the digitized representation of the composite page in the second format to the electronic destination address.
Owner:J2 CLOUD SERVICES LLC
Method and system for entry of electronic data via fax-to-email communication
InactiveUS7940411B2Reduce probabilityShorten the timeTelephonic communicationCharacter and pattern recognitionEmail addressService provision
A method for a computer system for transmitting a facsimile to an e-mail destination, comprises receiving a facsimile transmission comprising an instruction page and a document page, wherein the instruction page includes an optical representation of an e-mail address, using an optical character recognition process to determine the e-mail address from the optical representation of the e-mail address, wherein the e-mail address need not be known to the computer system before receiving the facsimile transmission, converting the facsimile transmission into an e-mail attachment, and sending an e-mail message including the additional service provider data and the e-mail attachment to the e-mail address, wherein the additional service provider data is selected from a group consisting of: a service provider identifier, a service sponsor identifier.
Owner:ADVANCED MESSAGING TECH INC
Methods and apparatus for facsimile transmissions to electronic storage destinations including tracking data
InactiveUS8045204B2Reduce probabilityShorten the timeDigital computer detailsCharacter and pattern recognitionGraphicsFacsimile transmission
A method for a computer includes determining a call-in fax telephone number called by a facsimile transmission device, receiving the facsimile transmission from a facsimile transmission device including a digitized representation of a transmission page including an optical representation of data associated with an e-mail address, determining the data optically, which is independent of the call-in number, determining a graphics template associated with the call-in number, combining a digitized representation of the transmission page with the graphics template to form a digitized representation of a composite page, formatting the digitized representation of the composite page into a second format, determining additional service provider data in response to the facsimile or the scanned image, and transmitting the additional service provider data and the digitized representation of the composite page in the second format to the electronic destination address.
Owner:J2 CLOUD SERVICES LLC
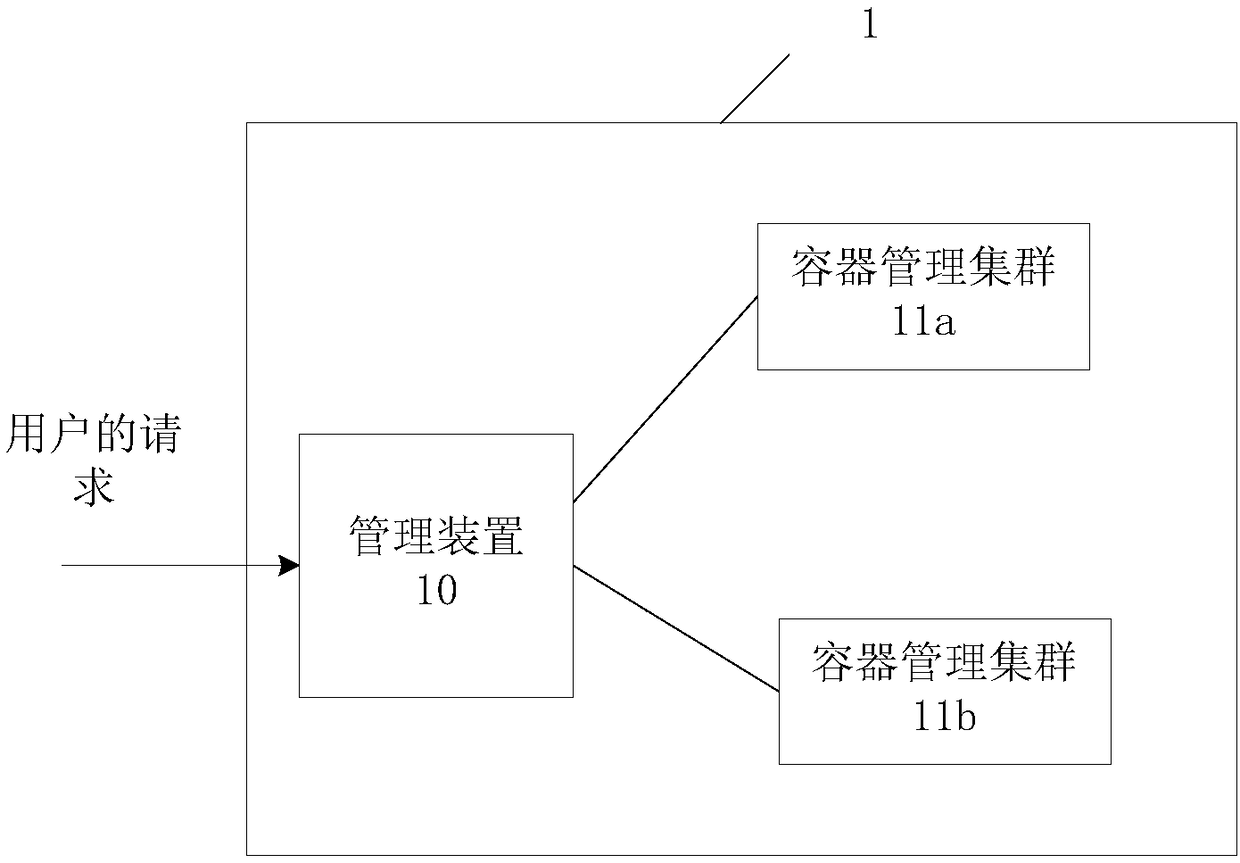
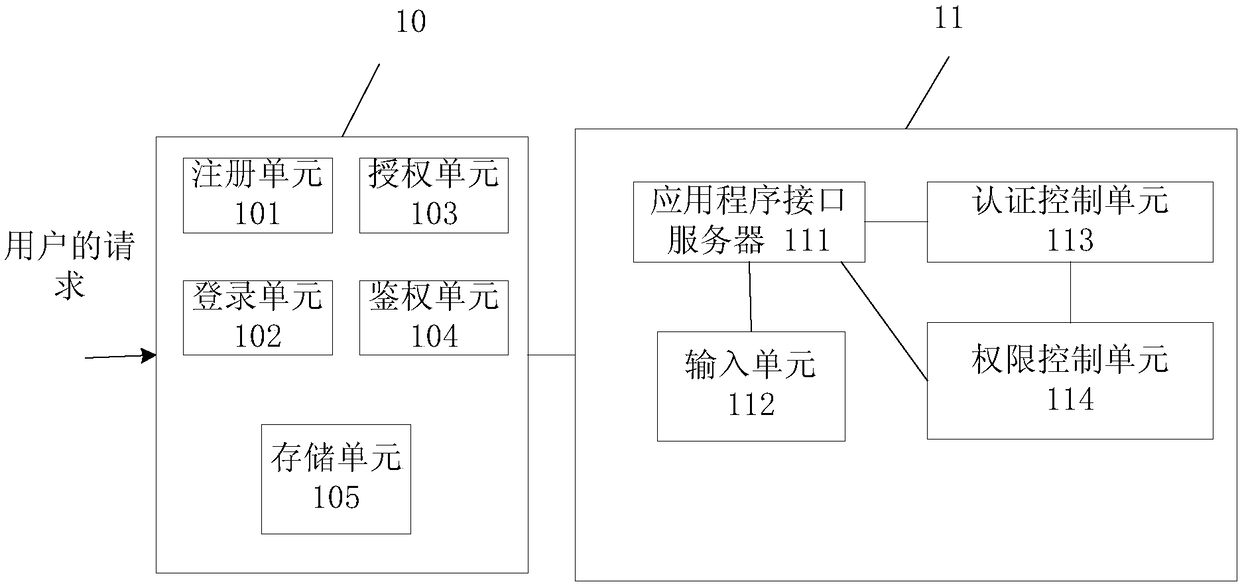
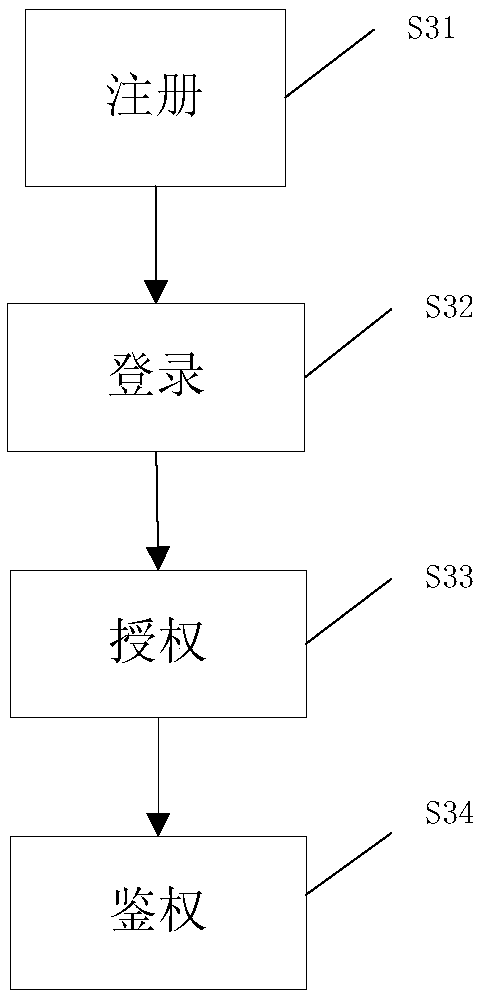
Method, device and system for performing authentication and authority management on user, and medium
The invention provides a method, device and system for performing authentication and authority management on a user using a container management cluster, and a medium. The method comprises the following steps: a registration step: sending a registration request to the container management cluster, and storing a service account and authentication information created by the container management cluster for the user; a login step: responding to a login request, taking out authentication information of the user, and authenticating whether the user successfully logs in according to the authentication information by the container management cluster; an authorization step: after determining that the user has successfully logged in, creating one or more items for an authorization request of the user, storing a namespace created by the container management cluster, and sending the service account and space of the user to the container management cluster for authorization; and an authenticationstep: responding to an operation request, taking out namespaces in one-to-one correspondence with items in the operation request, and authenticating the operation request by the container management cluster based on an authorization result of the service account and the namespaces.
Owner:UCLOUD TECH CO LTD
Methods and apparatus for secure facsimile transmissions to electronic storage destinations
InactiveUS8045203B2Reduce probabilityShorten the timeDigital computer detailsCharacter and pattern recognitionGraphicsEmail address
A method for a computer includes determining a call-in fax telephone number called by a facsimile transmission device, receiving the facsimile transmission from a facsimile transmission device including a digitized representation of a transmission page including an optical representation of a e-mail address, determining the e-mail address optically, which is independent of the call-in number, determining a graphics template associated with the call-in number, combining a digitized representation of the transmission page with the graphics template to form a digitized representation of a composite page, formatting the digitized representation of the composite page into a second format, determining additional service provider data in response to the facsimile or the scanned image, and transmitting the additional service provider data and the digitized representation of the composite page in the second format to the electronic destination address.
Owner:J2 CLOUD SERVICES LLC
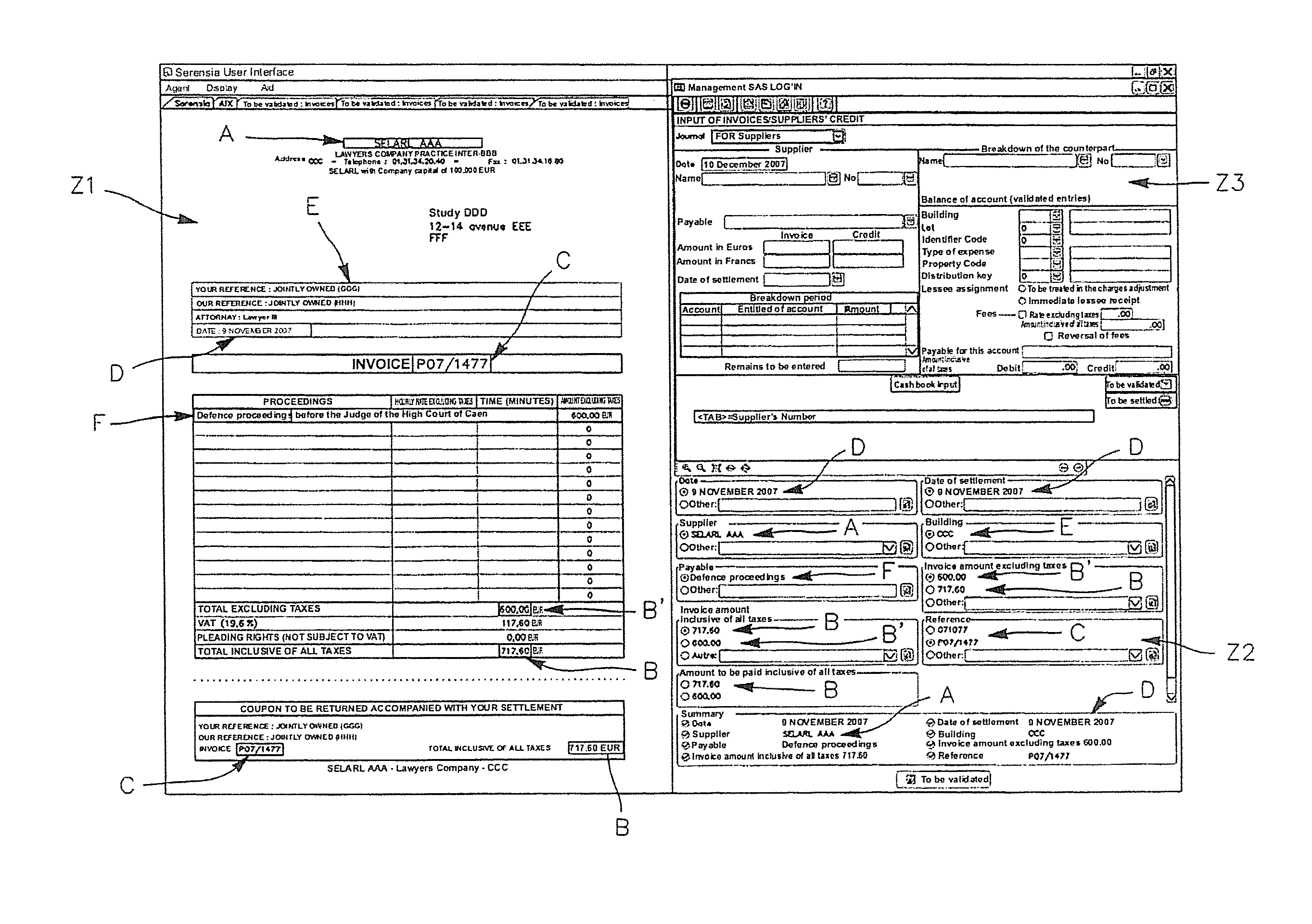
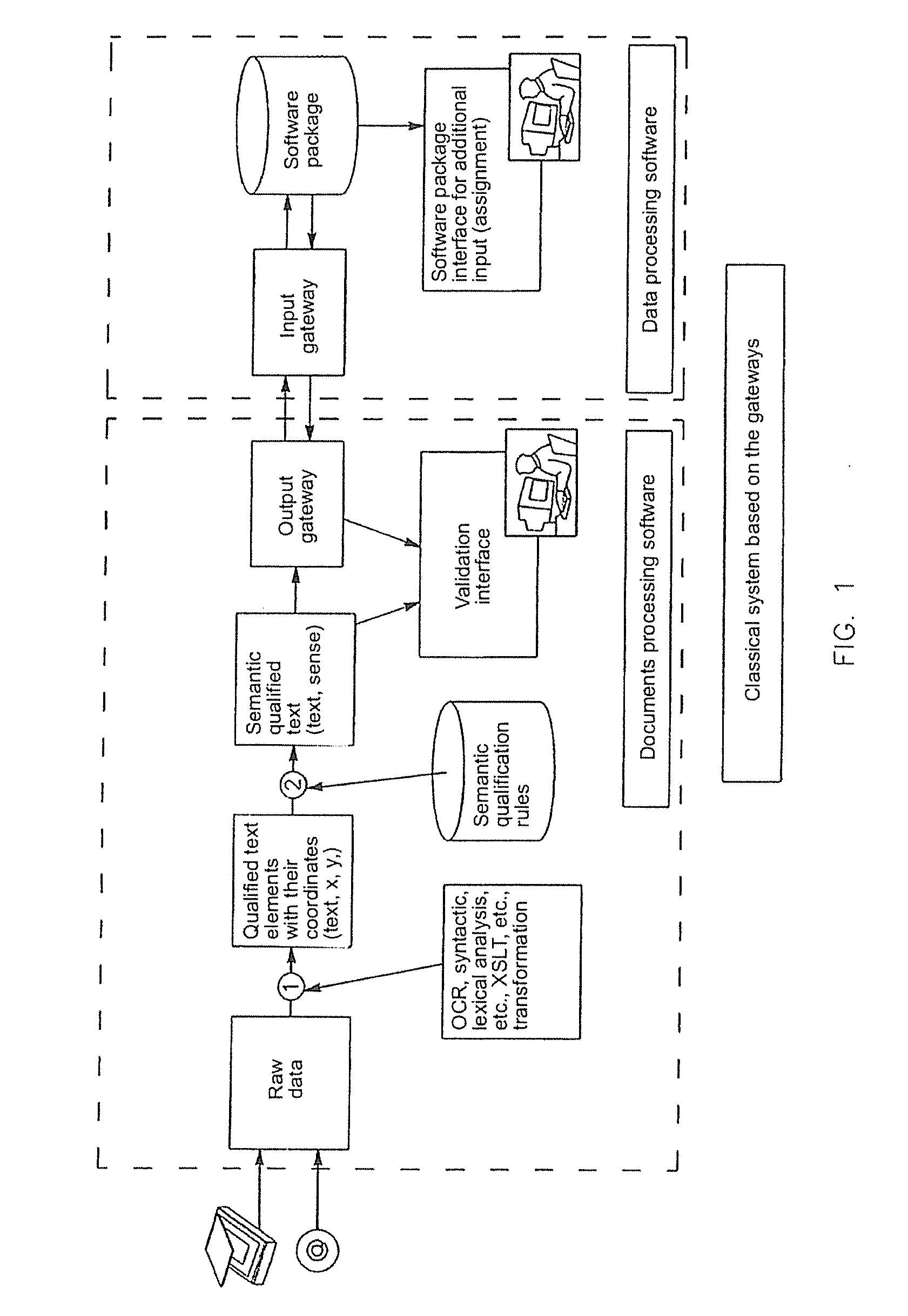
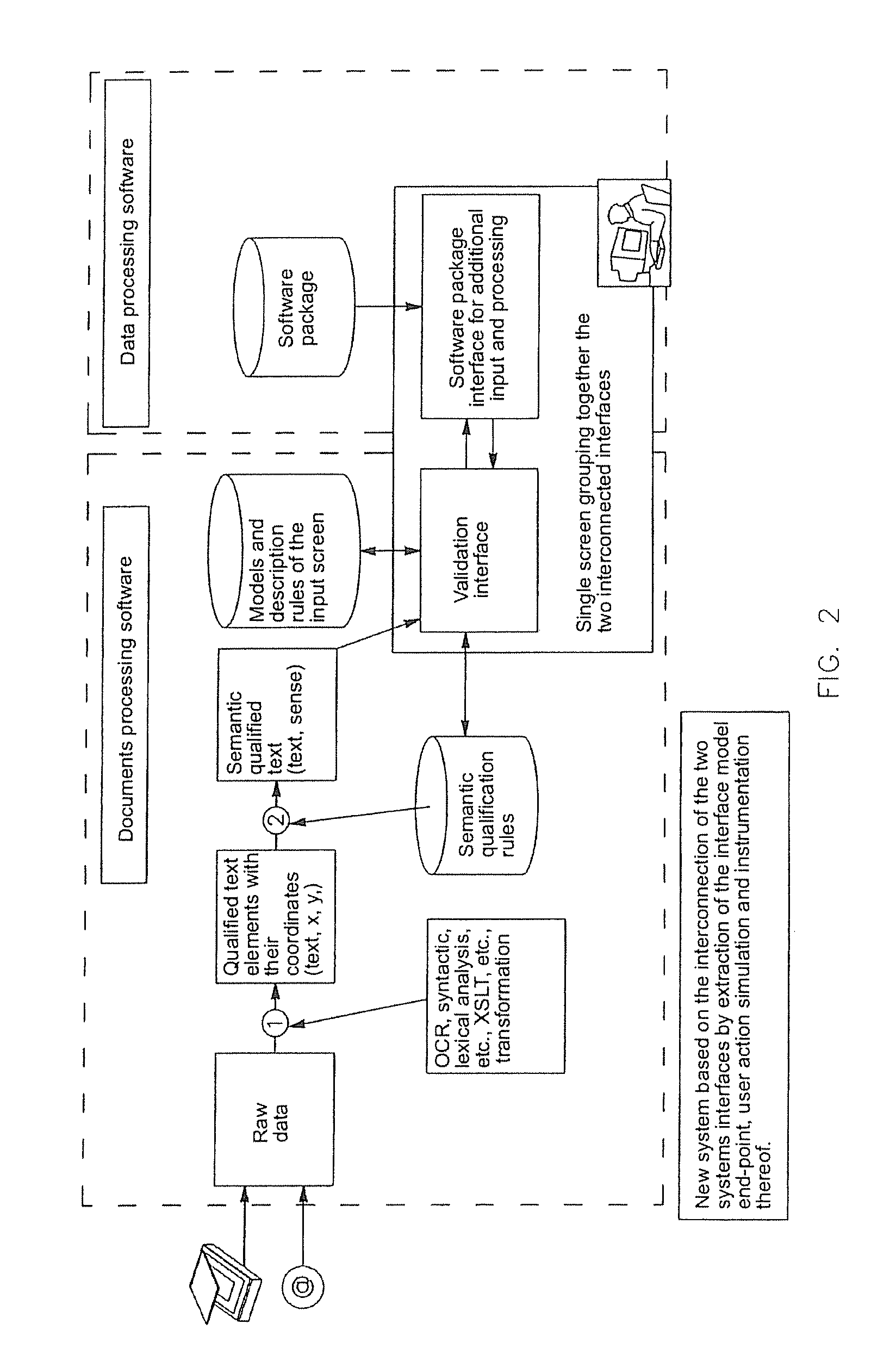
Method and system for aided input especially for computer management tools
ActiveUS20100254608A1Simplify and optimizeGain productivity timeCharacter and pattern recognitionNatural language data processingManagement toolOperational system
A method of aided input especially for a computer management tool, the management tool being executed in a computer system possessing an operating system furnished with instrumentation services, characterized in that it comprises the following steps: (a) entering raw data from an exterior source, (b) extracting relevant data from said raw data, (c) using said instrumentation services to transcribe said extracted data to corresponding fields of a preexisting input interface belonging to the management tool, with a view to allowing further inputs and overall validation. Application in particular to the semi-automated input of accounting items such as supplier invoices and the like.
Owner:SERENSIA
Methods and apparatus for authenticating facsimile transmissions to electronic storage destinations
InactiveUS7944573B2Reduce probabilityShorten the timeTelephonic communicationDigital computer detailsComputer hardwareService provision
A method transmitting a facsimile or scanned image to an electronic destination address includes receiving the facsimile or scanned image including a digitized instruction page including an optical representation of the electronic destination address, wherein the digitized instruction page is encoded in a first format, determining the electronic destination address from the optical representation of the electronic destination address, wherein the electronic destination address need not be known prior to receiving the facsimile or scanned image, converting the digitized instruction page to a second format, determining additional service provider data, and transmitting the additional service provider data and the digitized representation of the instruction page encoded in the second format to the electronic destination address.
Owner:J2 CLOUD SERVICES LLC
Methods and apparatus for facsimile transmissions to electronic storage destinations including embedded barcode fonts
InactiveUS7826100B2Reduce probabilityShorten the timeTelephonic communicationPictoral communicationGraphicsBarcode
A method for a computer includes determining a call-in fax telephone number called by a facsimile transmission device, receiving the facsimile transmission from a facsimile transmission device including a digitized representation of a transmission page including an optical representation of data associated with an e-mail address, determining the data optically, which is independent of the call-in number, determining a graphics template associated with the call-in number, combining a digitized representation of the transmission page with the graphics template to form a digitized representation of a composite page, formatting the digitized representation of the composite page into a second format, determining additional service provider data in response to the facsimile or the scanned image, and transmitting the additional service provider data and the digitized representation of the composite page in the second format to the electronic destination address.
Owner:J2 CLOUD SERVICES LLC
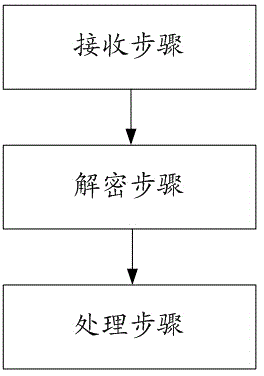
Link login method and system
The invention provides a link login method and system. The link login method comprises the steps of: a receiving step, including that a server receives an encrypted login message sent by a client; a decryption step, including that after the server receives the login message, a private key of an asymmetric cryptographic algorithm is used for decrypting; in the link login method, all communications of the client and the server are encrypted by a symmetric cryptographic algorithm using a random character string key as a secret key. The link login method and system have the advantages that, the secret keys are safely exchanged in an unsafe channel, so that a user can log in safely and reconnect after disconnection, all later communication contents cannot be monitored and sniffed by the network, a player is prevented from tampering and resending network packets, and the safety of the user is ensured.
Owner:深圳墨麟科技股份有限公司
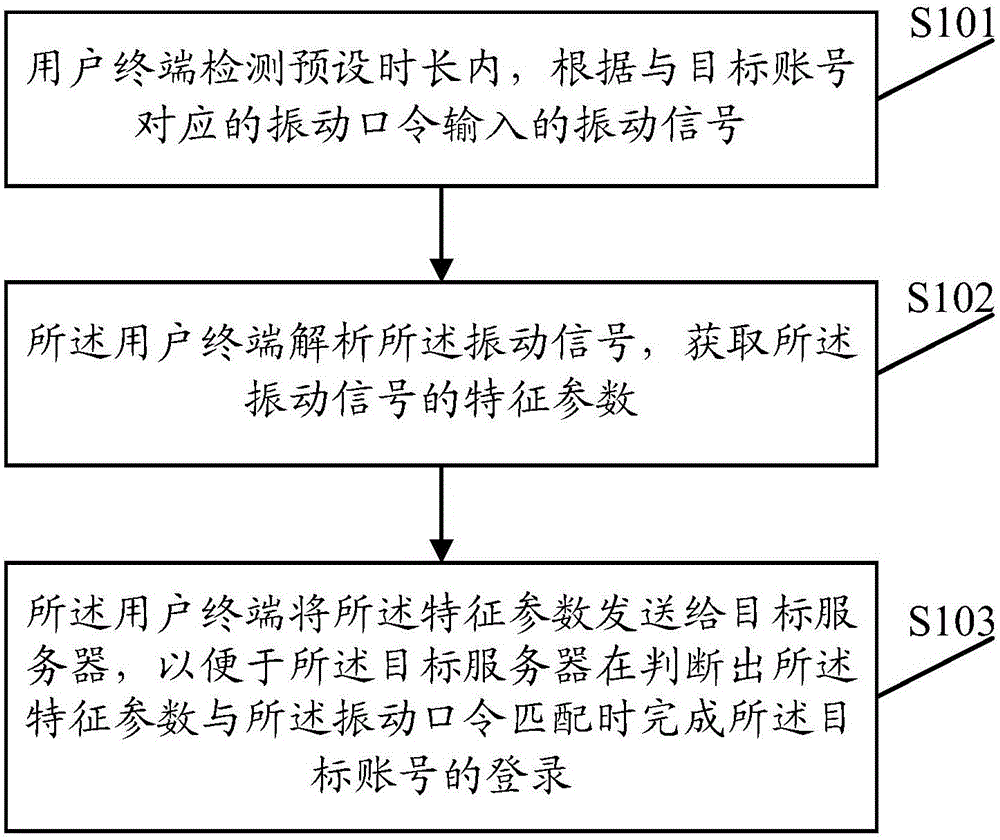
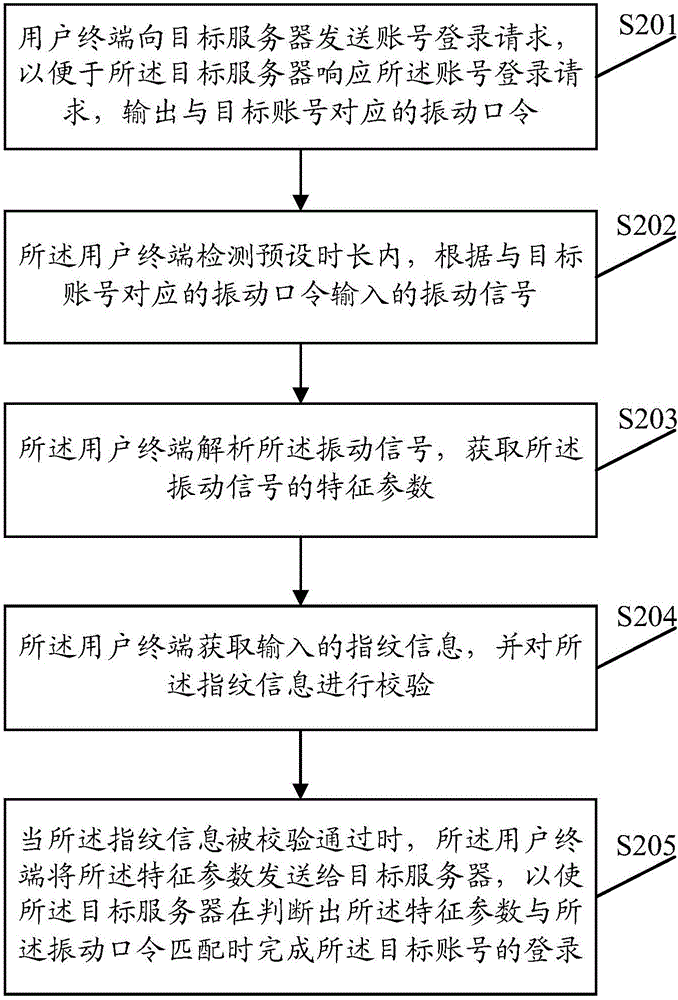
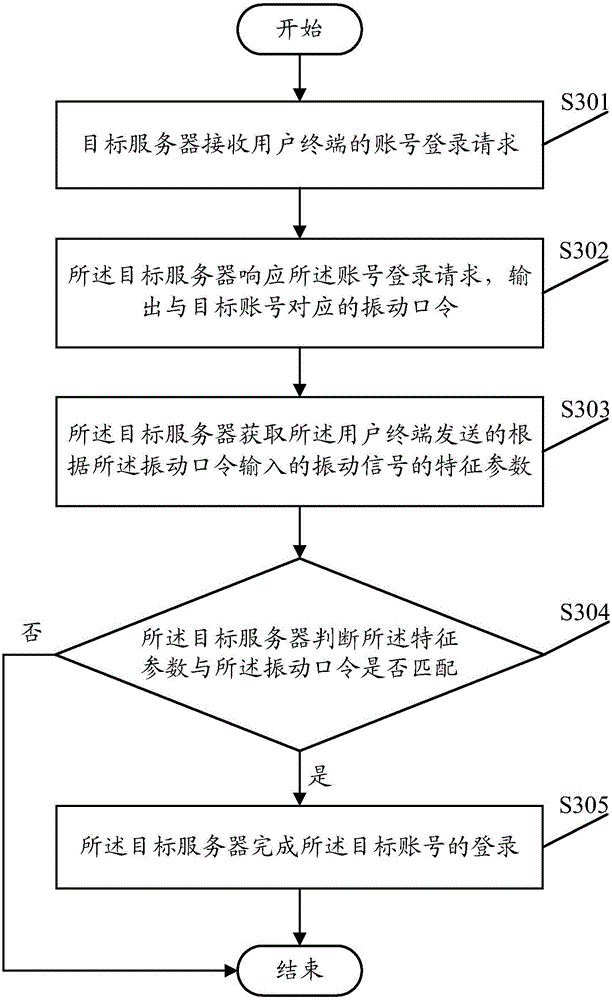
Account login method, system, user terminal and server
The embodiment of the invention provides an account login method, a system, a user terminal and a server. The account login method includes inputting vibration signals within a user terminal detection preset time period according a vibration password corresponding to a target account, the user terminal parsing the vibration signals to obtain the characteristic parameter of the vibration signals, and the user terminal sending the characteristic parameters to the target server, so that the target server completes the login of the target account when the characteristic parameters match with the vibration password. Safe and convenient login of an account can be realized by vibration, and the login means is interesting and flexible.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Methods and apparatus for billing of facsimile transmissions to electronic storage destinations
InactiveUS8275100B2Reduce probabilityShorten the timeTelephonic communicationPictoral communicationGraphicsFacsimile transmission
A method for a computer includes determining a call-in fax telephone number called by a facsimile transmission device, receiving the facsimile transmission from a facsimile transmission device including a digitized representation of a transmission page including an optical representation of data associated with an e-mail address, determining the data optically, which is independent of the call-in number, determining a graphics template associated with the call-in number, combining a digitized representation of the transmission page with the graphics template to form a digitized representation of a composite page, formatting the digitized representation of the composite page into a second format, determining additional service provider data in response to the facsimile or the scanned image, and transmitting the additional service provider data and the digitized representation of the composite page in the second format to the electronic destination address.
Owner:J2 CLOUD SERVICES LLC
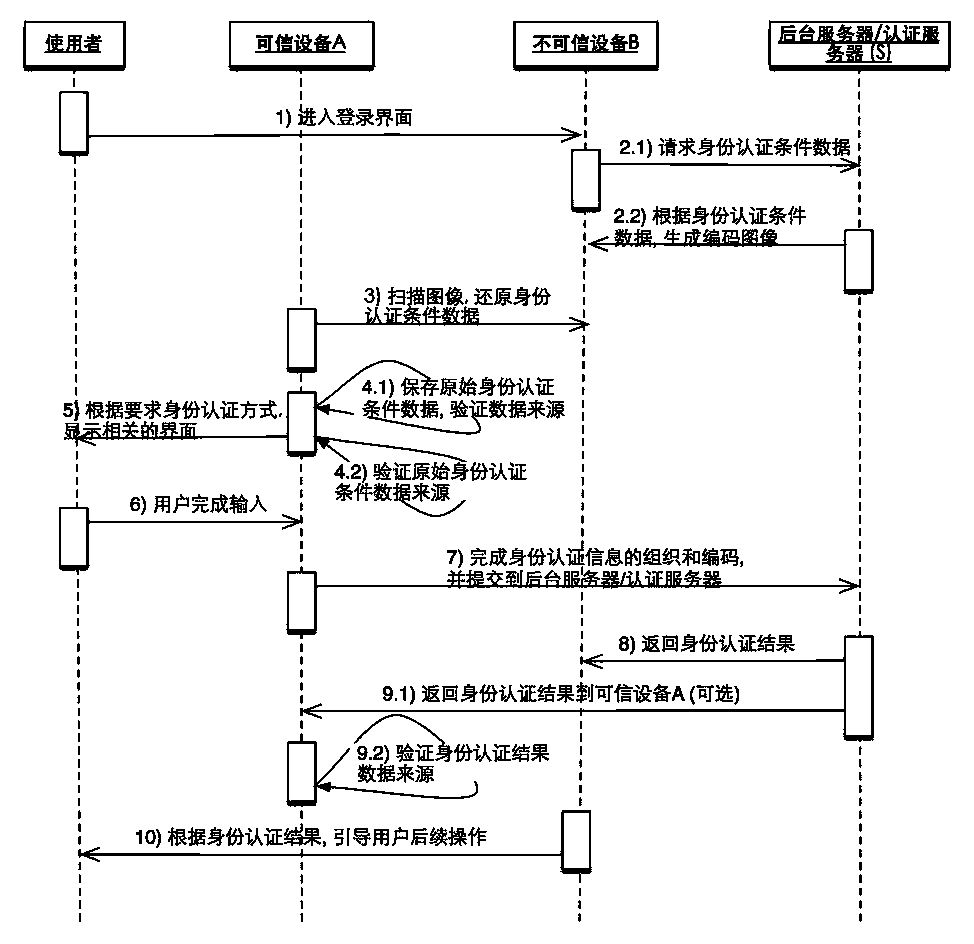
Cross-equipment and cross-application identity authentication method based on data image coding
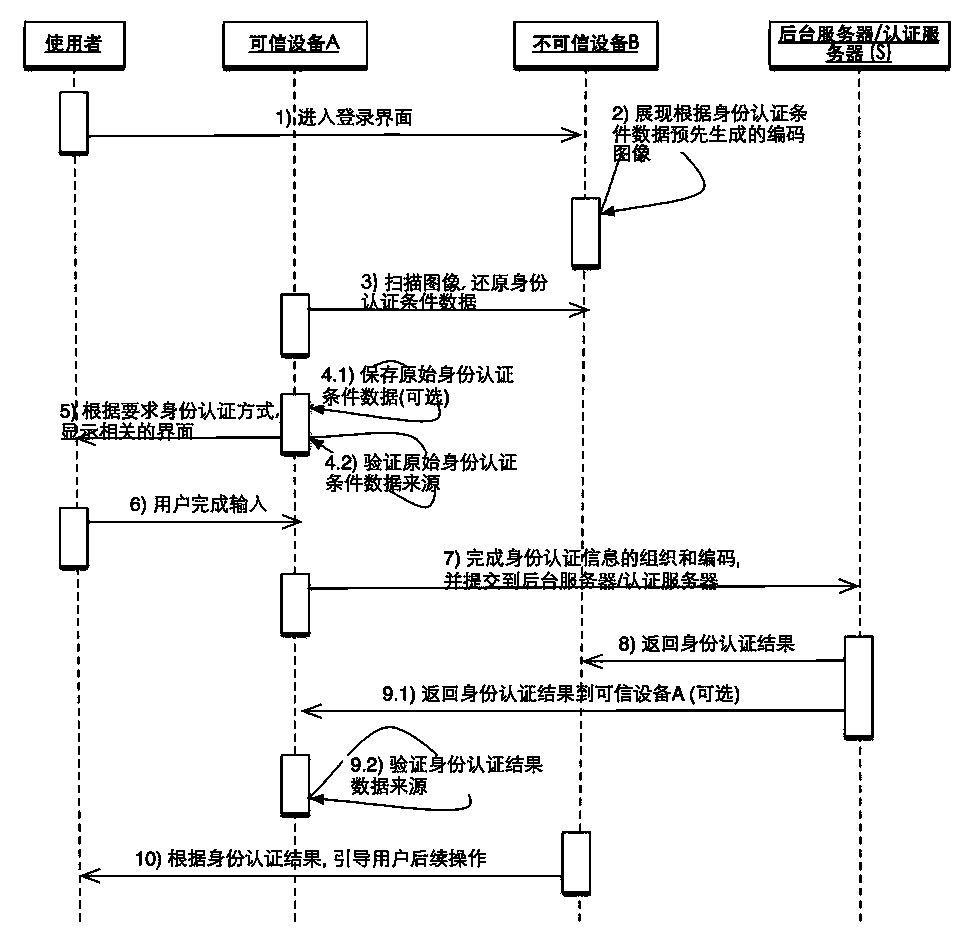
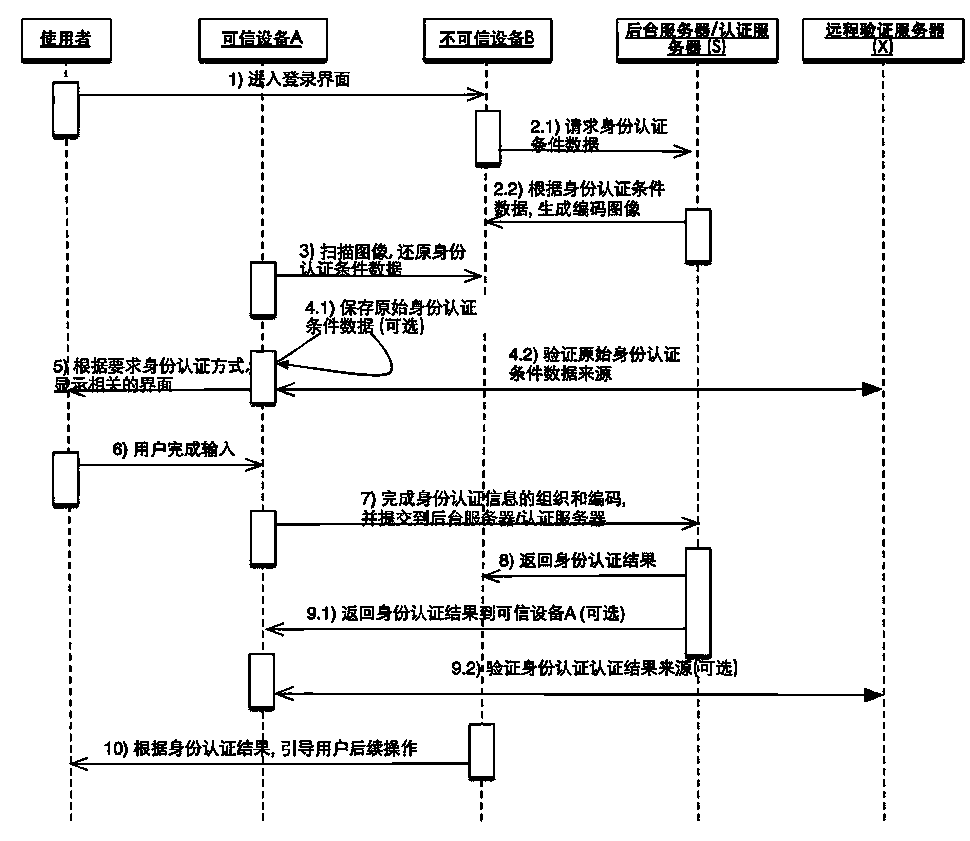
InactiveCN103905206ALogin securityUser identity/authority verificationAuthentication serverImage mode
The invention relates to a cross-equipment and cross-application identity authentication method based on data image coding. Identity authentication condition information is provided by equipment B, but an actual authentication process is finished on equipment A; the identity authentication condition information provided by the equipment B comprises actually authenticated server addresses and publisher identity information capable of being verified; the identity authentication condition information is coded in a data to image mode and displayed on the equipment B in an image form finally; identity authentication condition image information on the equipment B is scanned by the equipment A, identity authentication condition data are restored through image decoding, the identity of a publisher is verified, and identity information is obtained from a user and sent to an authentication server; the identity of the user is verified by the authentication server and fed back to the equipment B, and the equipment B allows or refuses the process that the user logs in according to a feedback result; after finishing operation, the user can log out through the equipment B or the equipment A. It is guaranteed that authentication information of the identity of the user cannot be leaked or hijacked.
Owner:江苏先安科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com