Cross-equipment and cross-application identity authentication method based on data image coding
An identity authentication and cross-device technology, applied in the direction of user identity/authority verification, etc., can solve problems such as inability to provide personalized services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
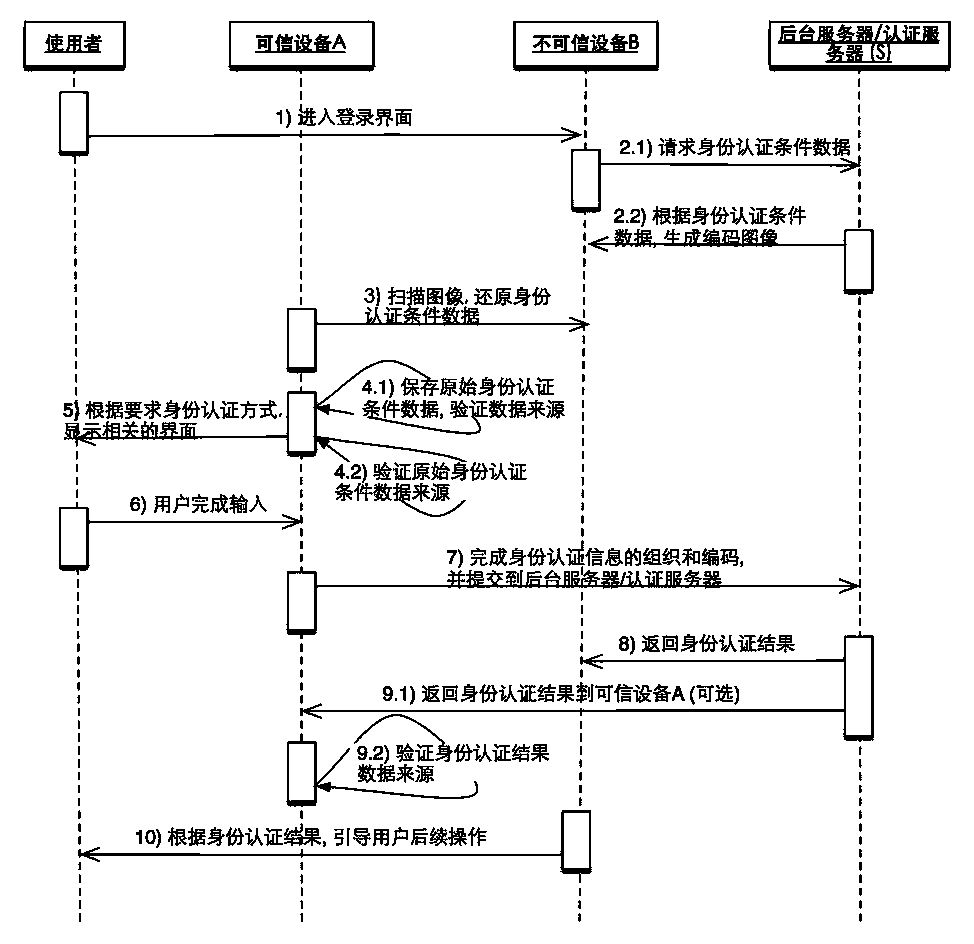
[0052] Example 1, such as figure 1 As shown, the identity authentication condition data image is generated in real time and the source authentication is completed on the A device itself:
[0053] 1 The user enters the login interface of the untrusted device B;
[0054] 2. The untrusted device B provides image-based identity authentication condition information through a display device such as a screen. The image is generated by encoded identity authentication condition data. For example, you can use a QR code as the image form of the final data representation, or you can use a barcode, or directly display the data, and identify it through OCR; and the identity authentication condition data can include: the address of the server that actually completed the authentication, verifiable Publisher identity information. It may also include: application identification, authentication method requirements, random number challenge (Challenge), etc.; image-based identity authentication...
Embodiment 2
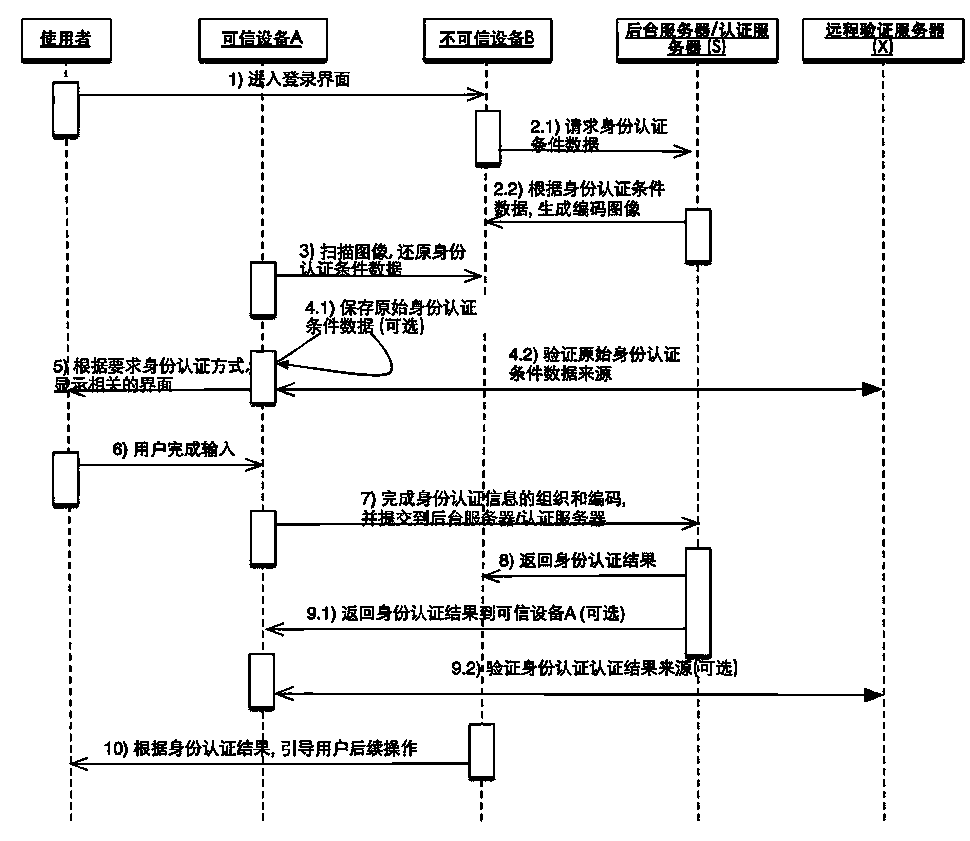
[0066] Example 2, such as figure 2 As shown, the identity authentication condition data image is generated in real time and the source authentication is completed by the remote authentication server:
[0067] 1 The user enters the login interface of the untrusted device B;
[0068] 2. The untrusted device B provides image-based identity authentication condition information through a display device such as a screen. The image is generated by encoded identity authentication condition data. For example, you can use a QR code as the image form of the final data representation, or you can use a barcode, or directly display the data, and identify it through OCR; and the identity authentication condition data can include: the address of the server that actually completed the authentication, verifiable Publisher identity information. It may also include: application identification, authentication method requirements, random number challenge (Challenge), etc.; image-based identity ...
Embodiment 3
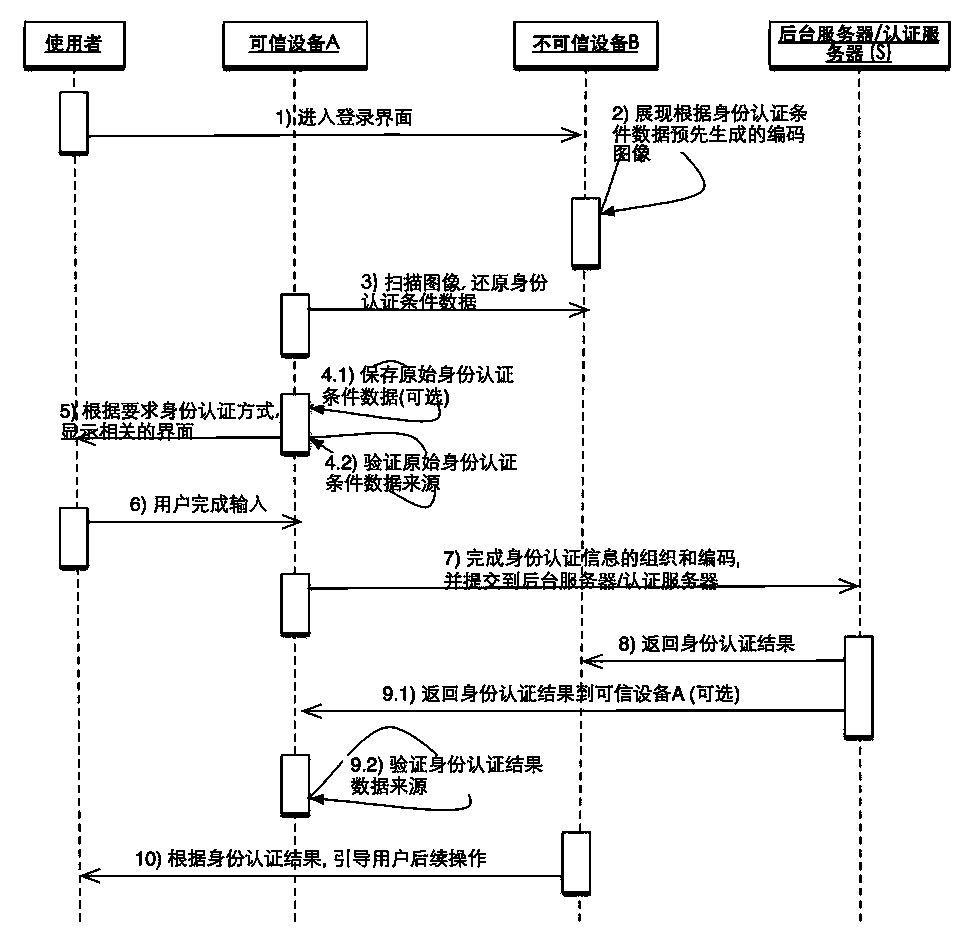
[0080] Example 3, such as image 3 As shown, use the static identity authentication condition data image and complete the source authentication on the A device itself:
[0081] 1 The user enters the login interface of the untrusted device B;
[0082] 2. The untrusted device B provides image-based identity authentication condition information through a display device such as a screen. The image is generated by encoded identity authentication condition data. For example, you can use a QR code as the image form of the final data representation, or you can use a barcode, or directly display the data, and identify it through OCR; and the identity authentication condition data can include: the address of the server that actually completed the authentication, verifiable Publisher identity information. It may also include: application identification, authentication method requirements, random number challenge (Challenge), etc.; image-based identity authentication condition informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com