Method for registration and verification of Internet of Things identity based on blockchain
A technology of identity registration and verification methods, applied in the blockchain field, can solve problems such as incompleteness, huge amount of transaction data, privacy leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
[0077] Simulate user A to initiate a transaction to user B, transaction sender A, transaction receiver B, and the transaction is verified by the entire network nodes.
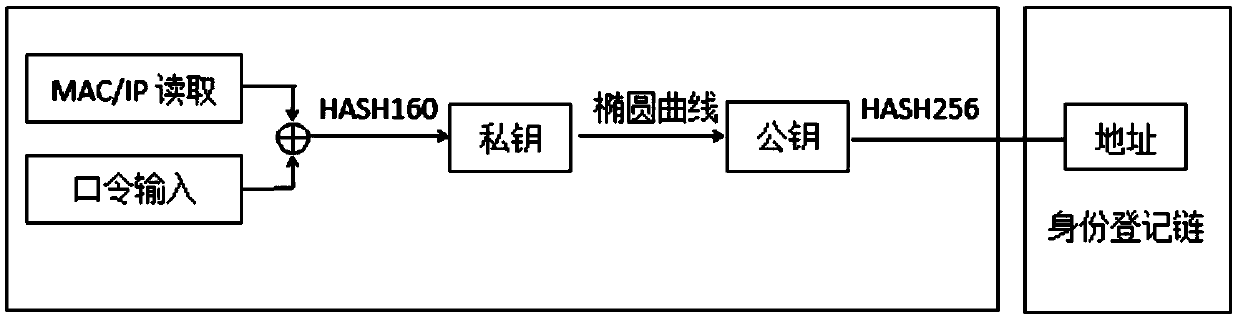
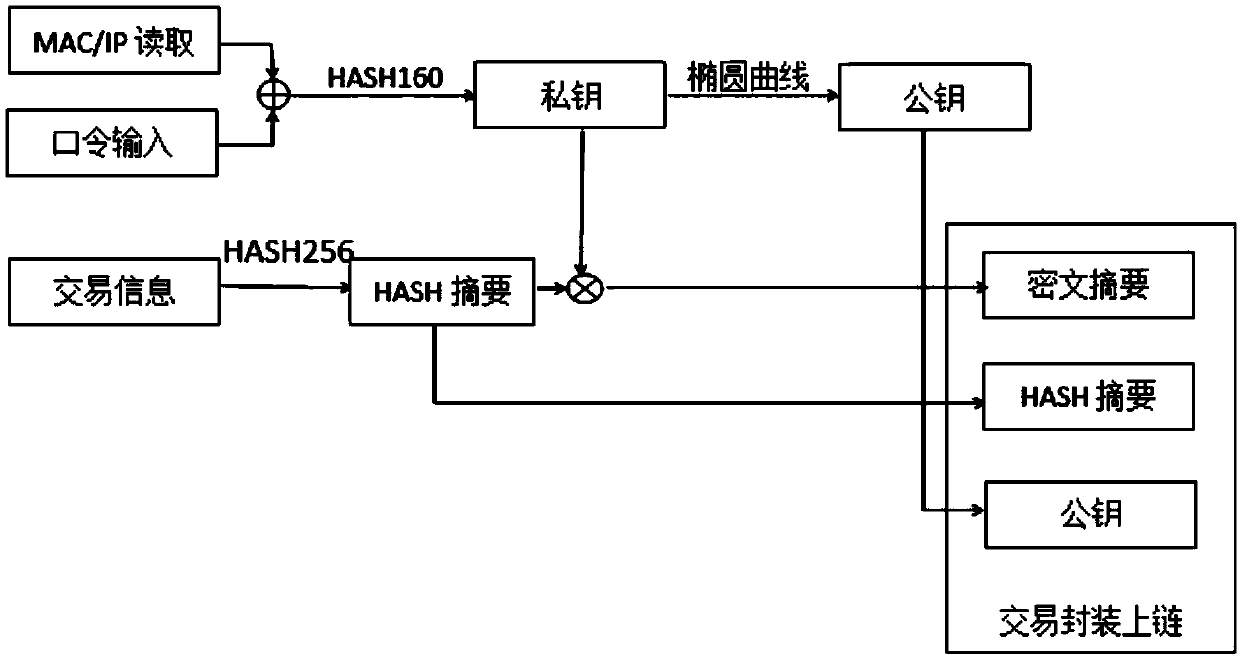
[0078] First, if figure 2 As shown, A reads and inputs its identity information through MAC, uses "MAC address + password" as a private key, and the public key corresponding to the private key is generated by an elliptic curve, and then uses the HASH256 hash algorithm to convert the public key into an identity Address, and uploaded to the identity registration chain, A completes the identity registration; then, if image 3 As shown, A uses the HASH256 hash algorithm to hash the transaction information, generates a hash summary, which is recorded as Y1, and encrypts it with a private key to generate a digital signature; A initiates a transaction, and sends the signature, hash summary Y1 and public The key is sent to the whole network; if Figure 4 As shown, the nodes of the whole network jointly verify the tr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com