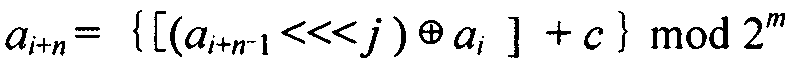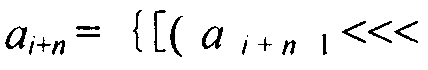Lightweight stream cipher LSNRR based on non-linear cyclic shift register
A technology of shift registers and stream ciphers, which is applied to encryption devices with shift registers/memory, etc., can solve the problems of poor unpredictability and achieve high security and high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
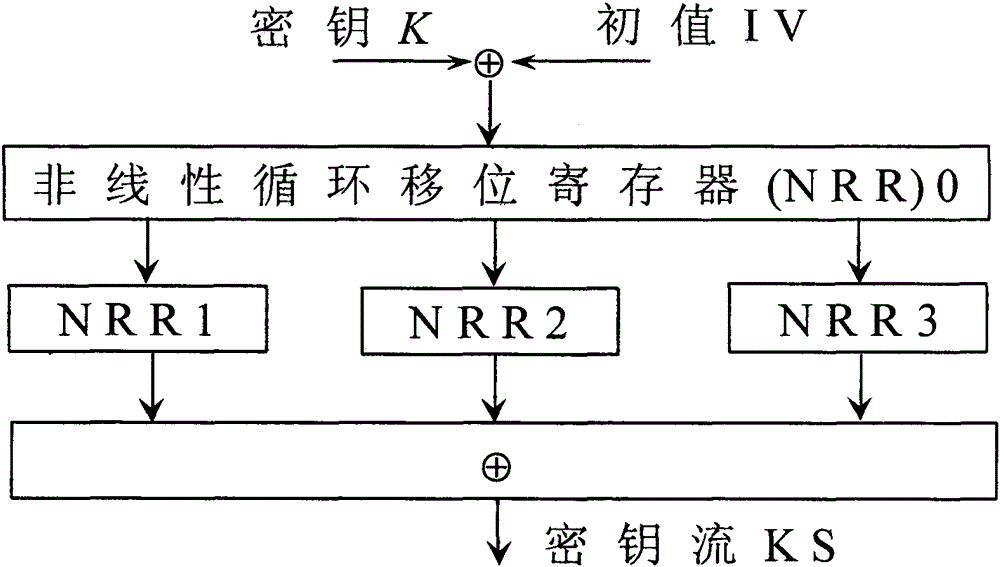
[0049] The specific implementation manner of nonlinear cyclic shift register NRR among the present invention is: when the word length is m bits, n-level NRR adopts the following feedback mode to be formed by the previous n words a i ~a i+n-1 The first and last two characters in the recursively push the next word a i+n
[0050] a i + n = { [ ( a i + n - 1 j ) ⊕ a i ] + c } mod 2 m
[0051] Among them, n≥2, the word length m takes the number of digits of the platform; Indicates modular addition; c is 1~2 m An odd number between...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com