Sequence cipher realization device and sequence cipher realization method thereof
A serial cipher and implementation method technology, applied in the field of cryptography, can solve the problems of high power consumption and communication speed, high hardware overhead, etc., and achieve the effect of low hardware cost, strong environmental applicability, and guaranteed security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
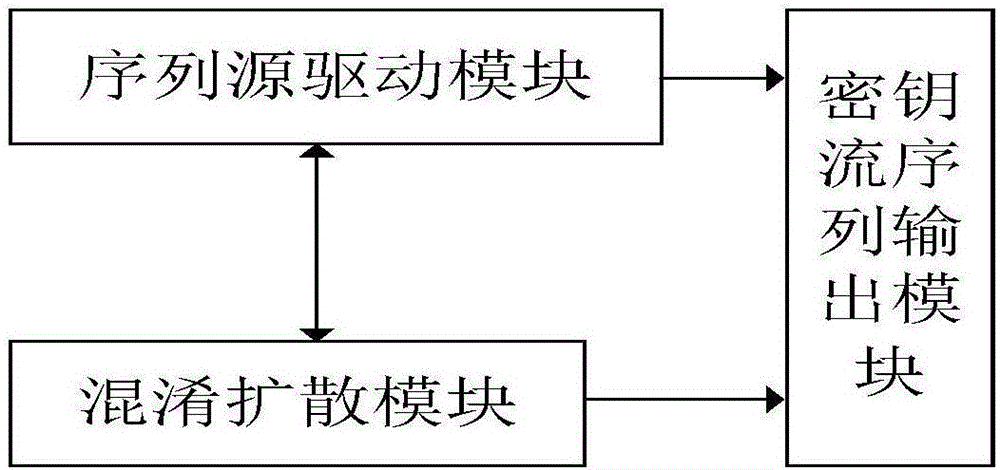
[0035] Embodiment one, see figure 1 As shown, a column cipher implementation device includes: a sequence source driver module, a confusion diffusion module, and a key stream sequence output module;
[0036]The sequence source driving module generates a sequence source through a non-linear feedback shift register of Galois structure, wherein the non-linear feedback shift register includes k shift registers, and each time a beat is performed, the feedback terminals of the k shift registers simultaneously Update, each feedback terminal is connected to the confusion diffusion module, k is an integer greater than 1;
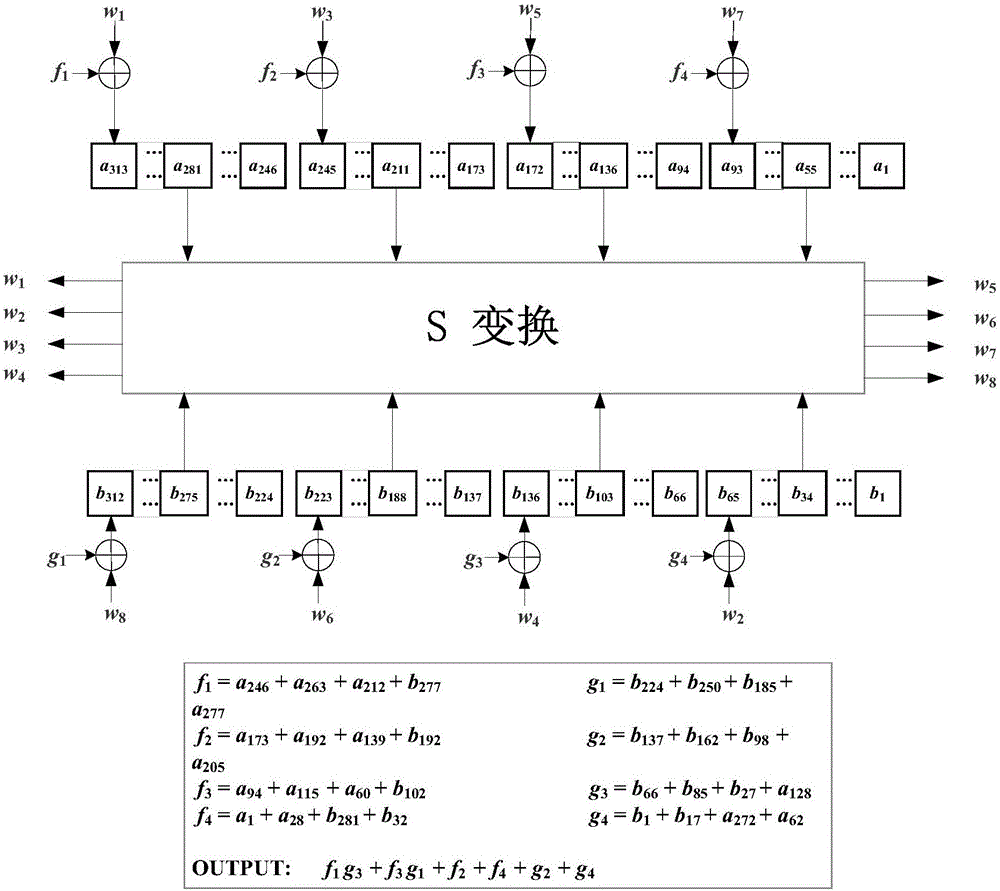
[0037] The confusion diffusion module includes a confusion unit and a diffusion unit, and the confusion unit includes an S-transform, wherein the S-transform is a nonlinear Boolean function of k-bit input and k-bit output, and a double-layer structure combination is performed by S-box and P replacement Confusion; the diffusion unit contains k linear functions; the in...
Embodiment 2
[0040] Embodiment 2 is basically the same as Embodiment 1, except that k is an integer greater than or equal to 8.
[0041] According to actual usage requirements, k is set to 8, and the S-box is 4 different non-linear Boolean functions with 4-bit input and 4-bit output. The distance between the taps of the nonlinear feedback shift register and the distance between each tap and the corresponding feedback terminal are different.
Embodiment 3
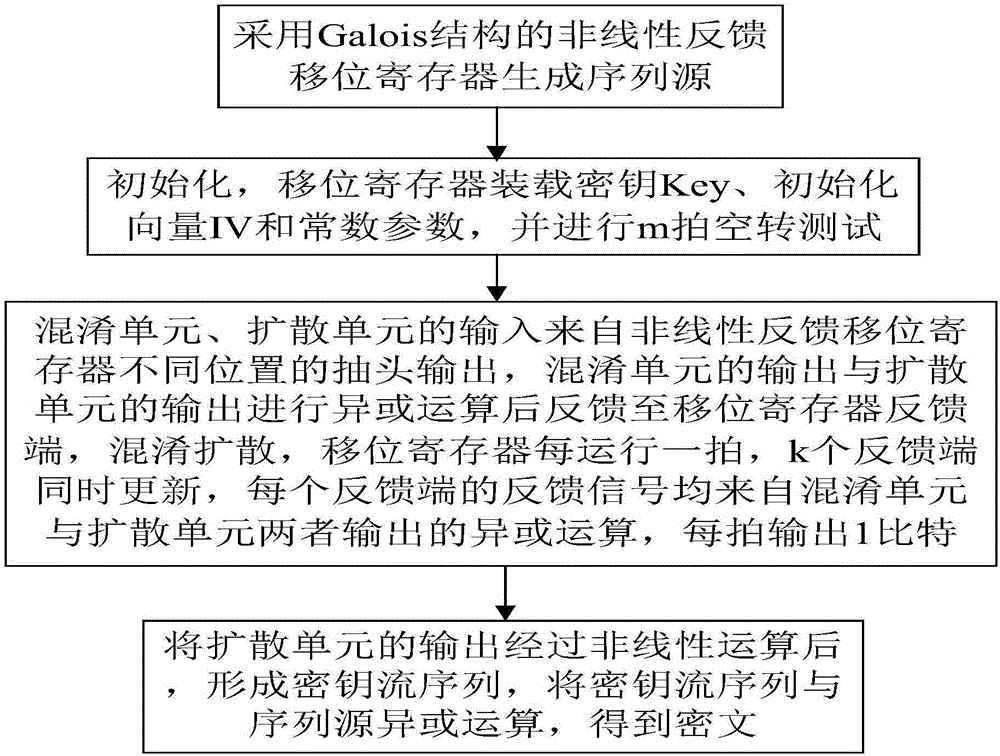
[0042] Embodiment three, see Figure 1~4 As shown, a serial cipher implementation method, based on the serial cipher implementation device described in Embodiment 1, specifically includes the following steps:
[0043] Step 1. Use the nonlinear feedback shift register of Galois structure to generate the sequence source, wherein the total length of the nonlinear feedback shift register is n levels, and the n-level nonlinear feedback shift register is divided into k shift registers to form k feedback end, the lengths of the k shift registers are respectively {i 1 ,i 2 ,...,i k-1 ,i k}, and i 1 + i 2 +...+i k-1 + i k =n, according to the number of feedback terminals k, determine the set of feedback terminal positions: {j 1 ,j 2 ,...,j k-1 ,j k}, where j k =n-1,0≤j 1 2 k-1 ≤n-2, 2≤k≤n;
[0044] Step 2, initialization, the shift register is loaded with the key Key, the initialization vector IV and constant parameters, and performs m idling, and m is determined through ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com