Patents
Literature
31results about How to "Guaranteed security strength" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
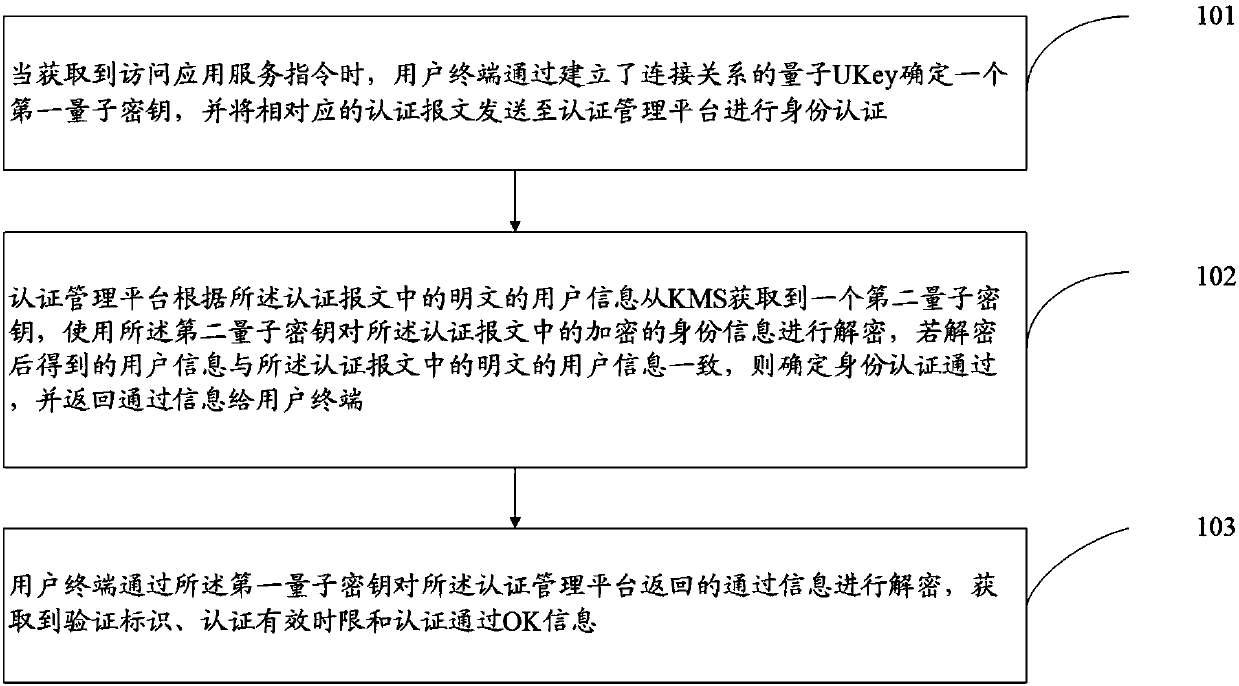
Communication method and system based on quantum Ukey
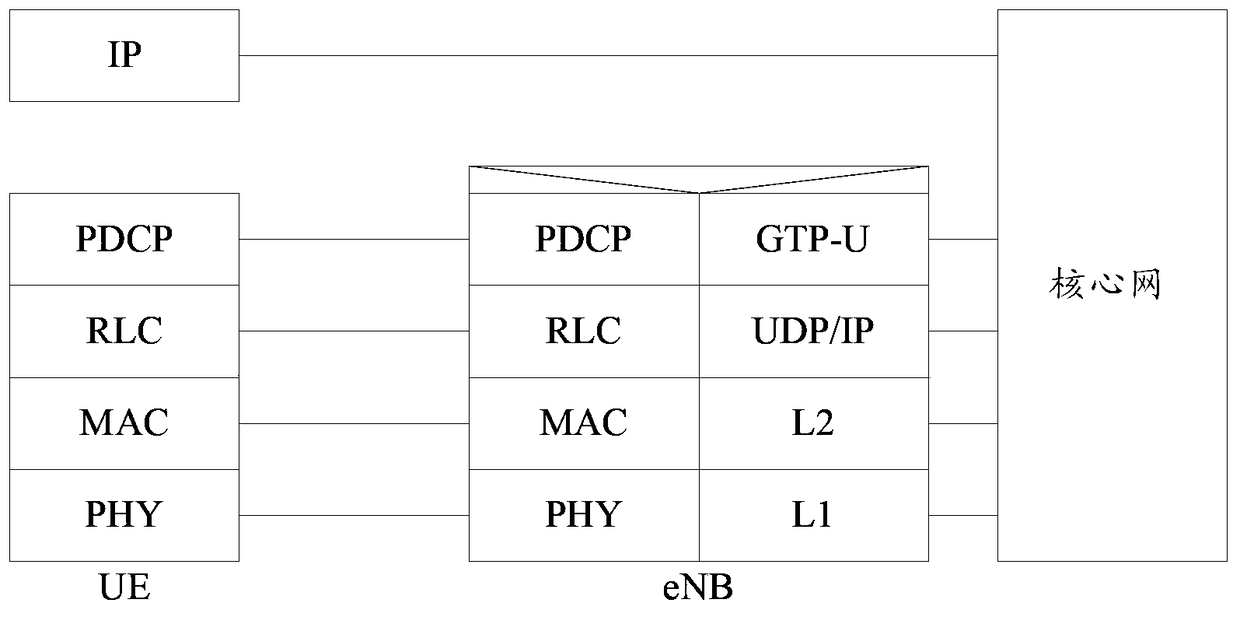
ActiveCN107769913ATo achieve an organic combinationImprove securityKey distribution for secure communicationPlaintextApplication server
The invention discloses a communication method and system based on the quantum Ukey, aiming to solve the potential safety hazards that the algorithm is not safe, the user password strength is not highenough, the user password plaintext input, secret key distribution and management are difficult, and the secret key cannot be automatically updated in the aspects of current identity authentication and security access cloud service application. The communication method based on the quantum Ukey comprises the following steps that when an access application service instruction is acquired, a user terminal determines a first quantum key by the quantum Ukey established the connection relation, and sending the corresponding authentication message to an authentication management platform for identity authentication; the authentication management platform obtains a second quantum key from the KMS according to the authentication message, and decrypting the encrypted information in the authentication message, if the decrypted information is consistent with the plaintext information in the authentication message, the identity authentication is determined to pass, and the passing information isreturned to the user terminal, so that the user terminal accesses the application server through the first quantum key.
Owner:QUANTUMCTEK GUANGDONG CO LTD
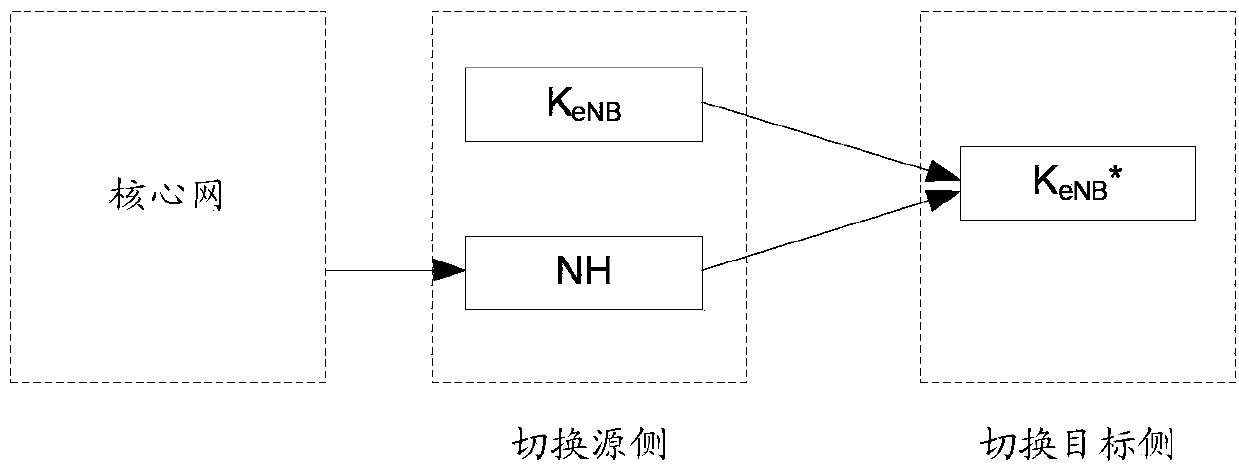
Security key management method, device and system
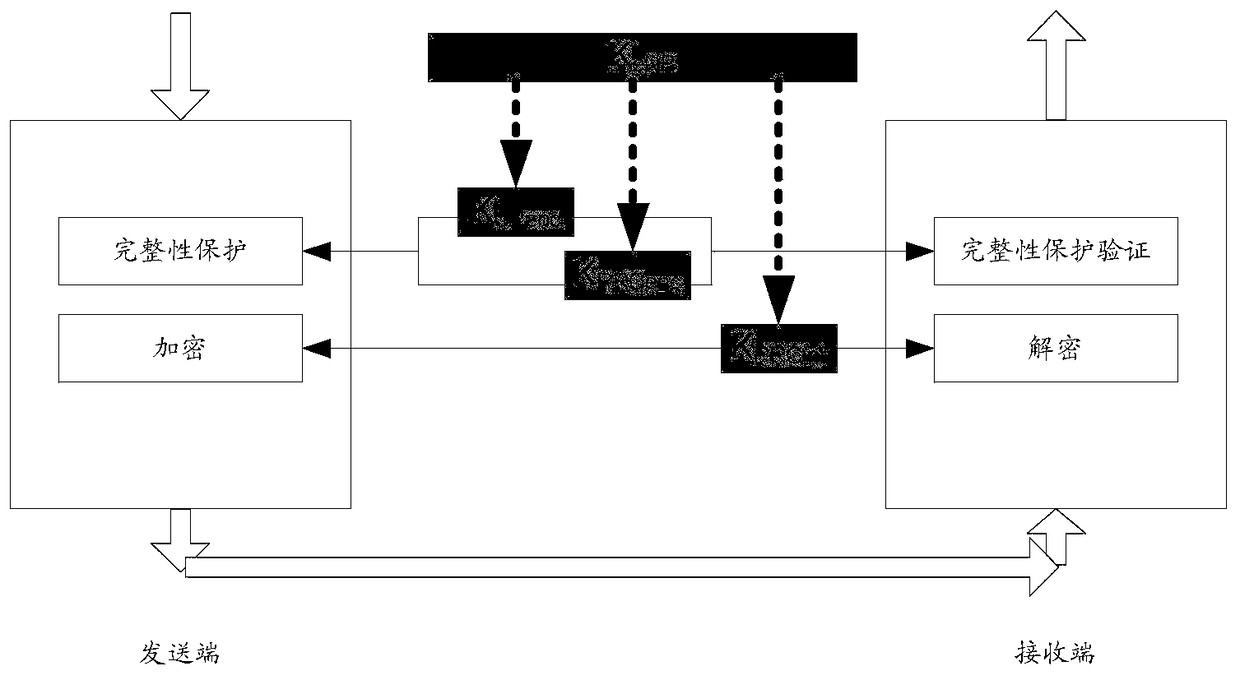
InactiveCN104185177AImprove securityGuaranteed security strengthSecurity arrangementBase stationKey management
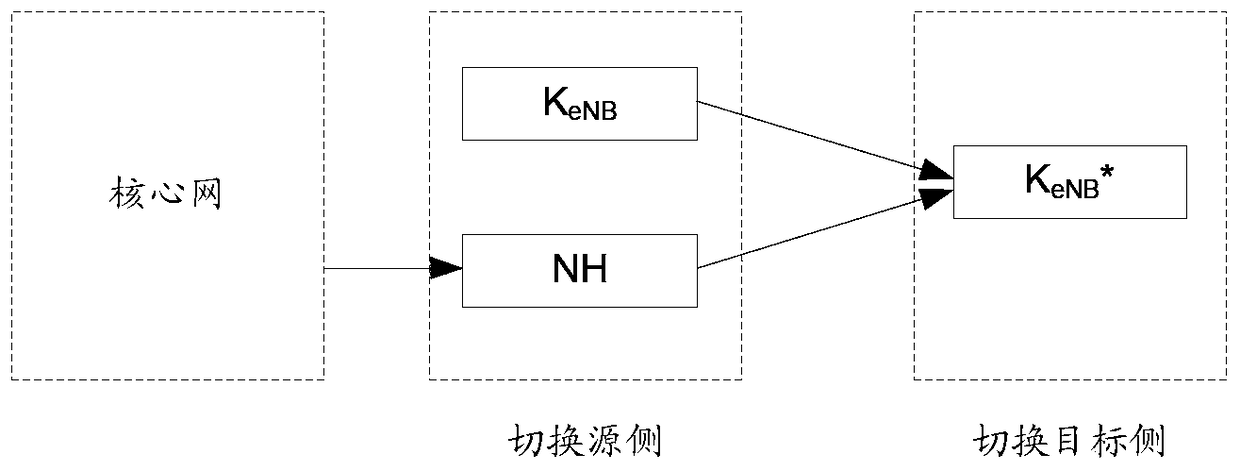
Disclosed are a method, apparatus and system for security key management. A master control base station and / or a terminal maintain / maintains two sets of base station key for the master control base station: a present base station key and a non-present base station key. The non-present base station key is the key not used by the master control base station and the terminal at present, and is derived from the present base station key or Next Hop (NH) or a prior non-present base station key. The present base station key is the key used by the master control base station and the terminal at present, and is used for deriving other control panel and / or user panel keys. There exists one and only one present base station key simultaneously.
Owner:ZTE CORP
Safety helmet
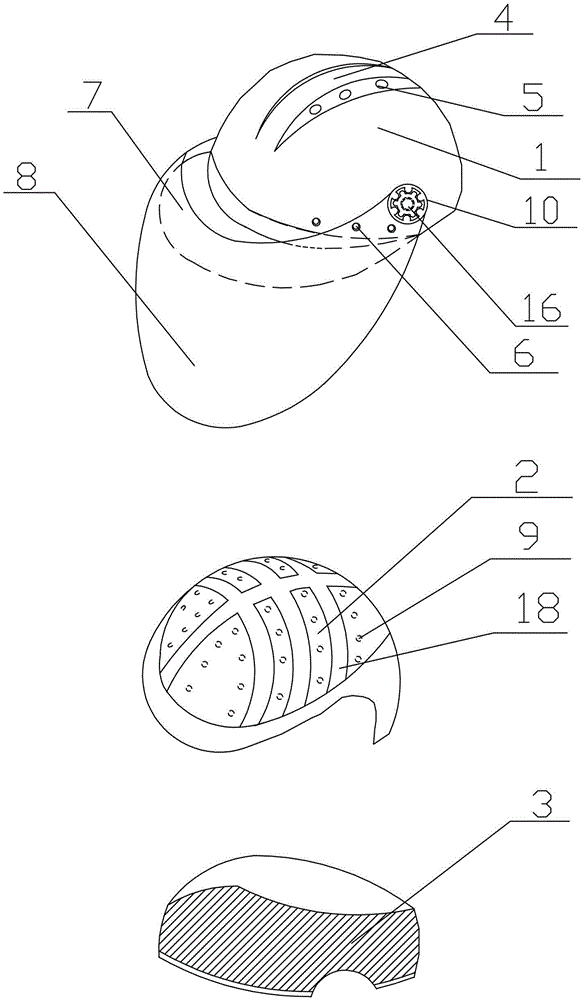
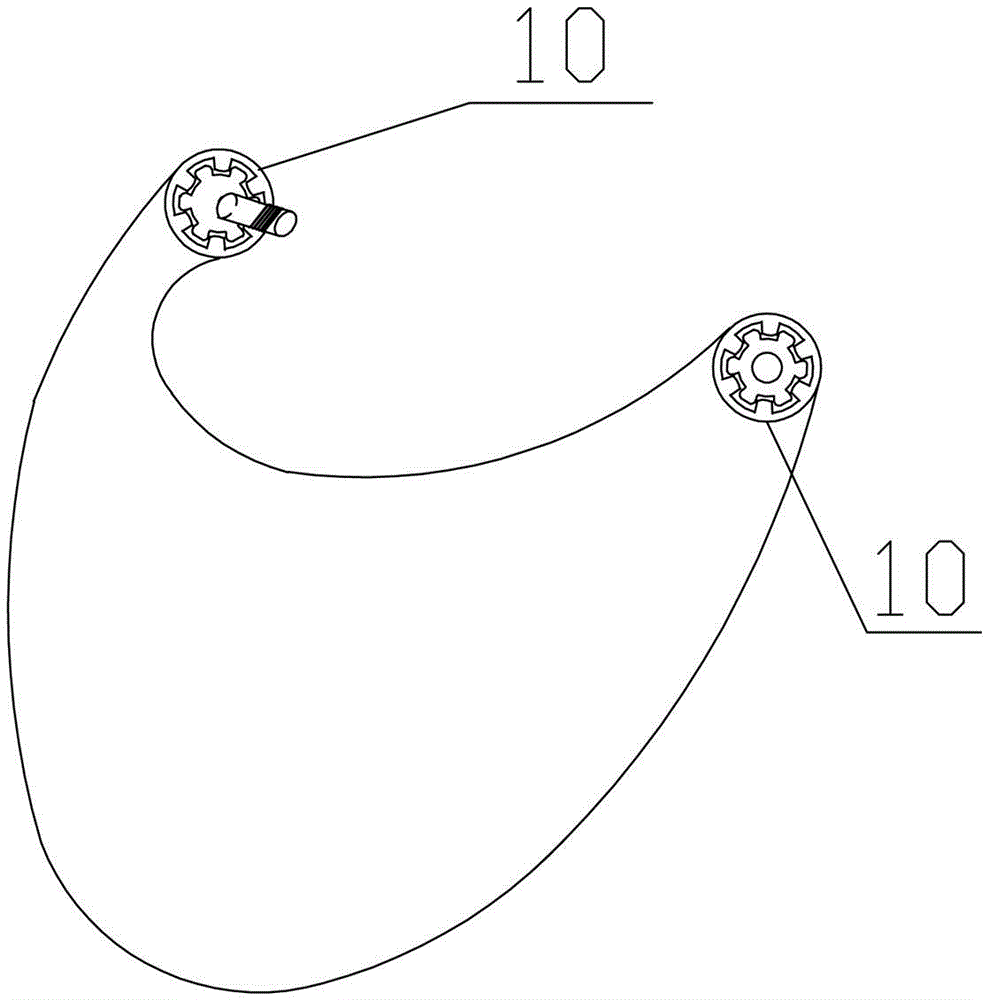
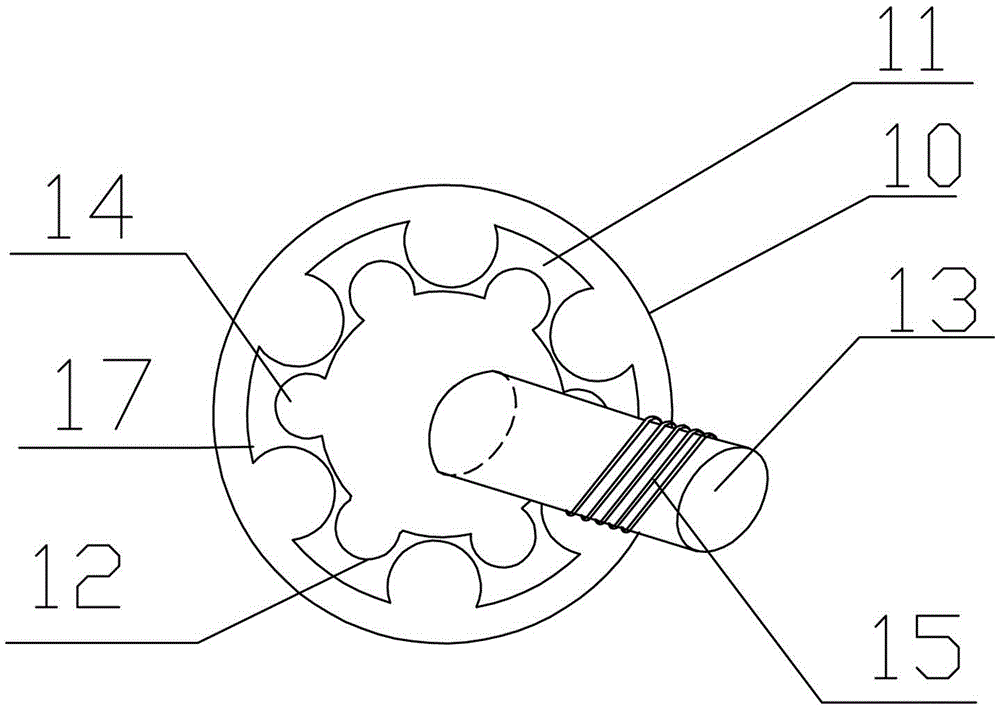
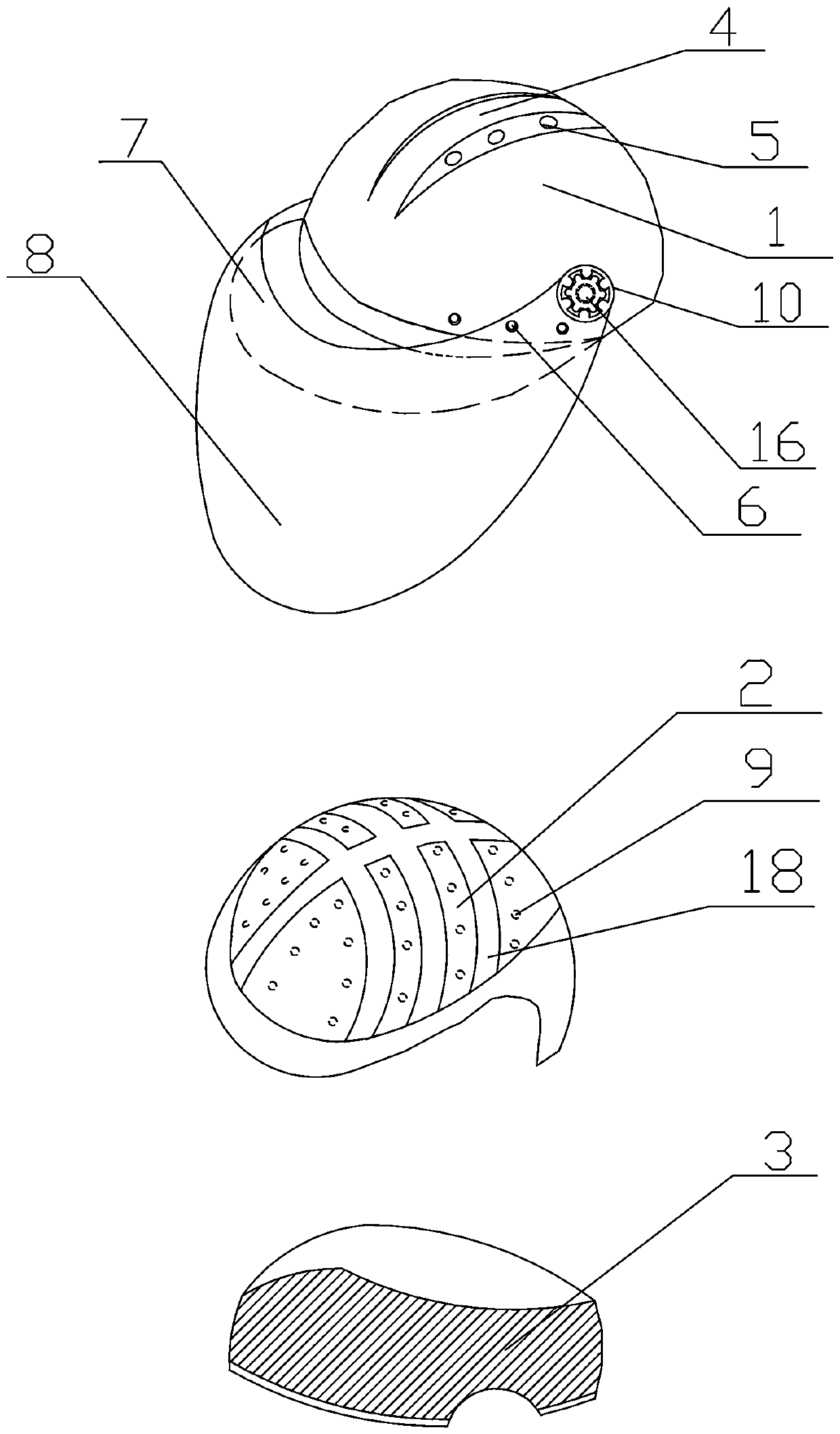
The invention discloses a safety helmet. The safety helmet comprises a helmet shell (1), an elastic buffer layer (2) and an inner layer (3), wherein a helmet brim (7) is arranged on the helmet shell (1), a bulge (4) is arranged on the top of the helmet shell (1), a first air hole (5) is formed at the joint of the bulge (4) and the top of the helmet shell (1), a second air hole (6) is formed in the side part of the edge of the helmet shell (1), and a protective cover (8) is arranged on the helmet shell (1); the elastic buffer layer (2) is made of silicone rubber, and massage bulges (9) are arranged on the elastic buffer layer (2); and the inner layer (3) is in an annular structure. The safety helmet is high in safety performance, good in protective effect, and rapid in heat dissipation, and can massage the head.
Owner:XICHUAN COUNTY POWER BUREAU
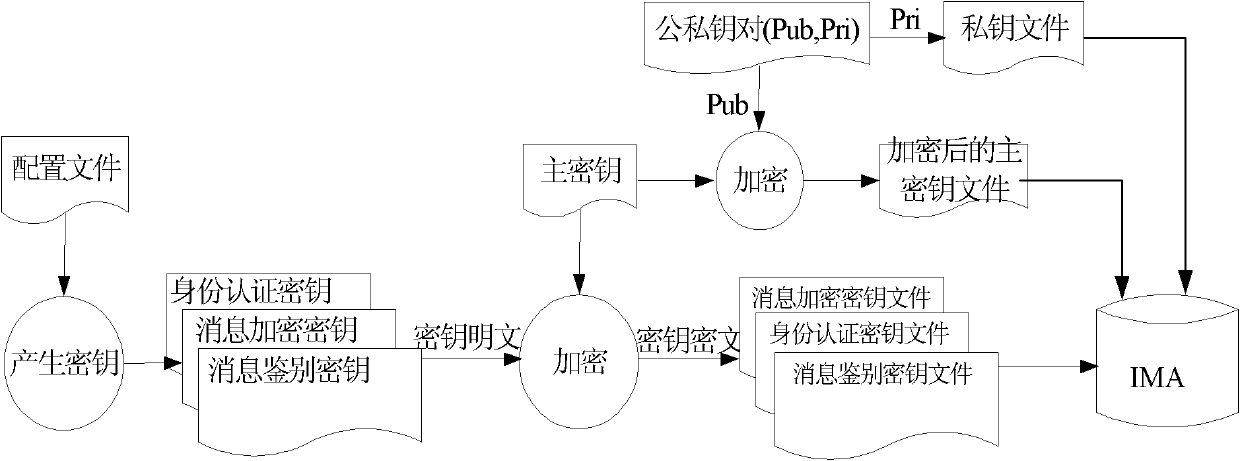
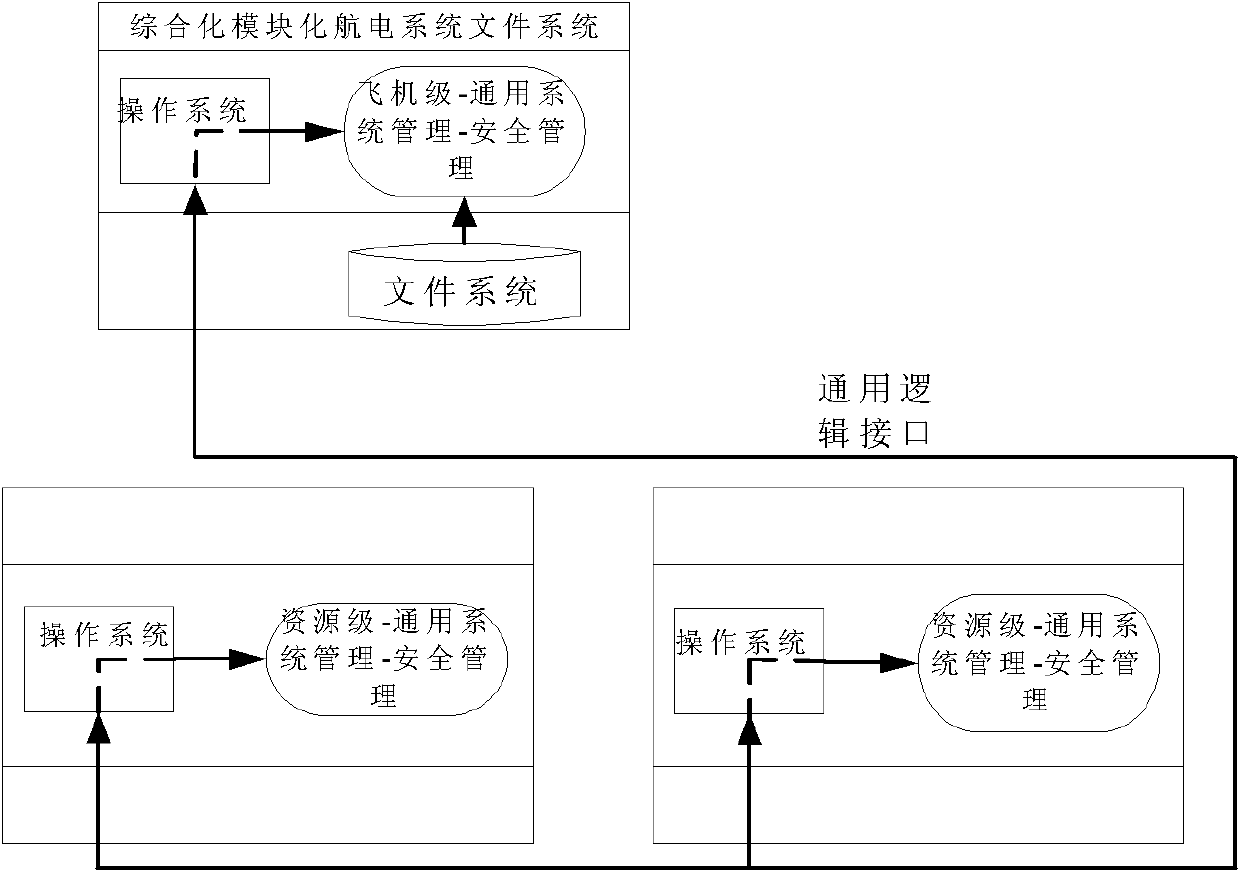
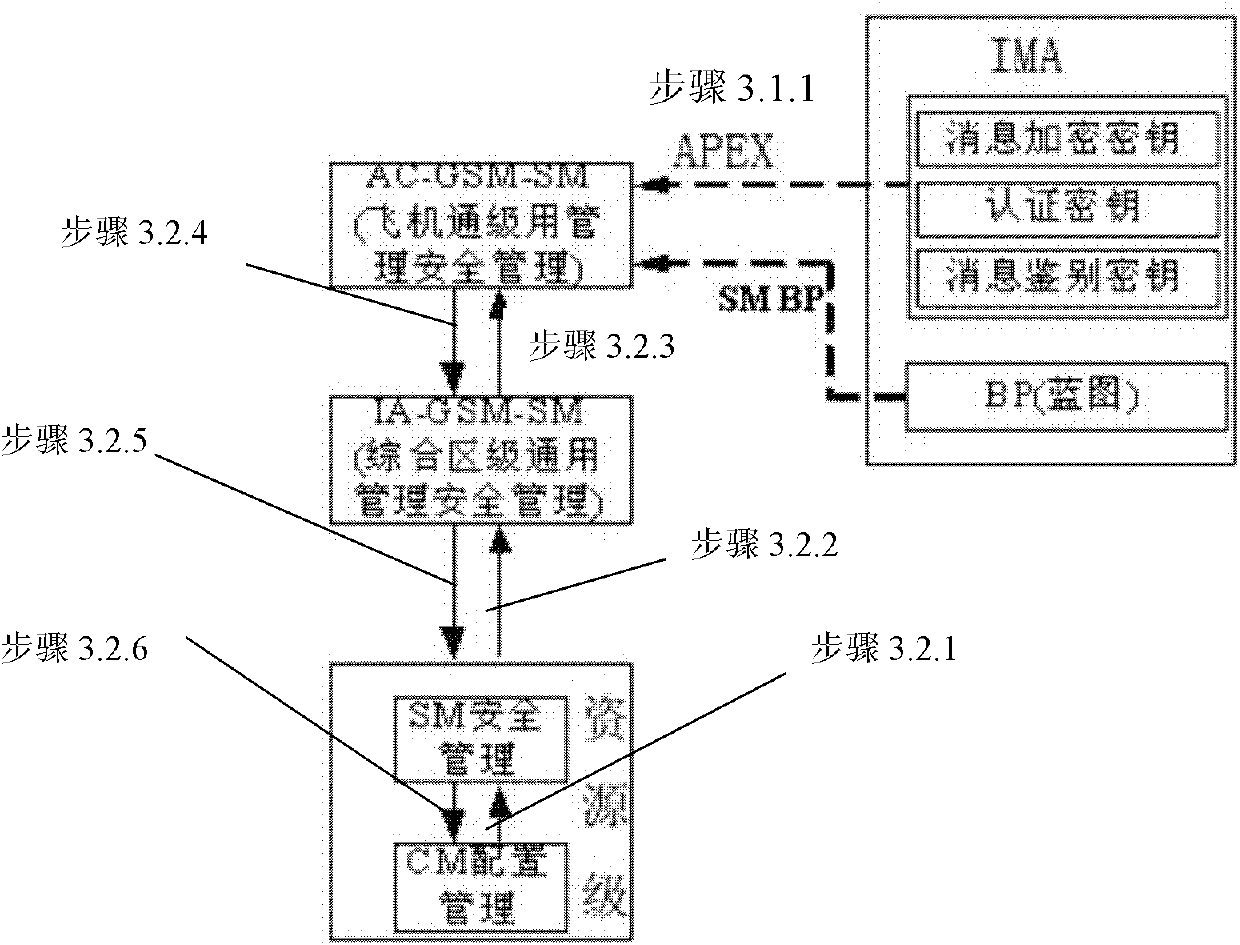
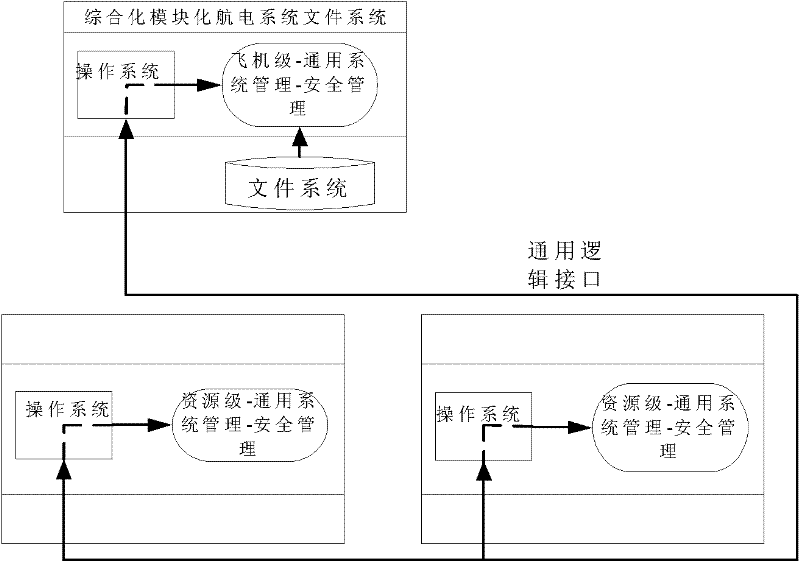
Key management method for integrated avionic system
ActiveCN101908962AImprove efficiencyImprove computing efficiencyKey distribution for secure communicationUser identity/authority verificationIntegrated modular avionicsKey distribution
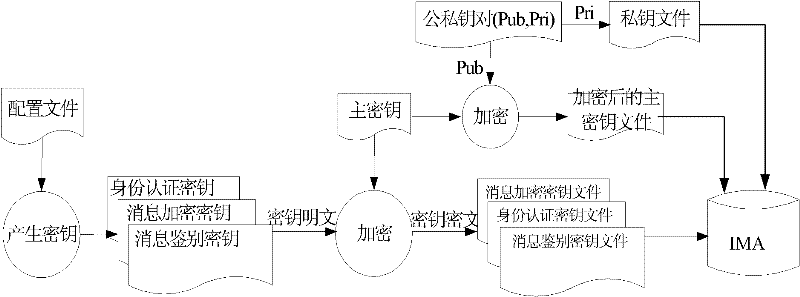
The invention relates to a key management method for an integrated avionic system. The key management functions in the entire process from the generation to final destruction of a key and is realized as a functional component for the safety management (GSM-SM) of system management in an integrated modular avionic (IMC) system to perform unified management on all keys in the system; and the key management mainly comprises the following steps of: 1) generating the keys; 2) loading the keys; 3) distributing the keys; and 4) using the keys. The method is favorable for improving the active defense level of airborne embedded systems of China, constructing and perfecting a safety guarantee system of the integrated avionic system, defending an equipment system against foreign threats and improving the destruction resistance of the aviation equipment system.
Owner:AVIC NO 631 RES INST
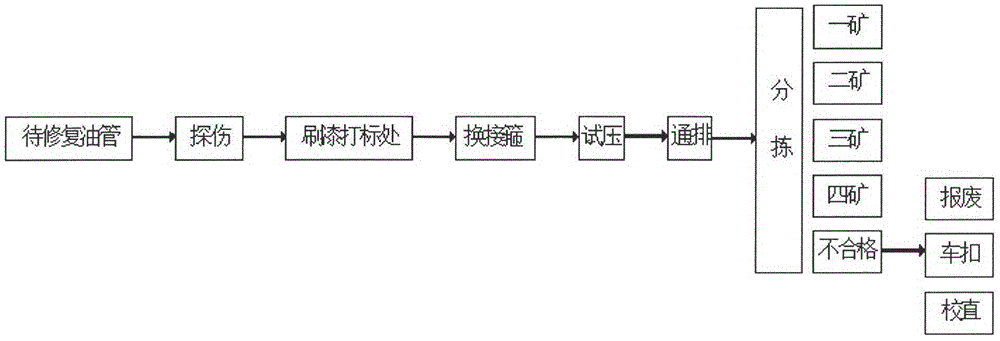
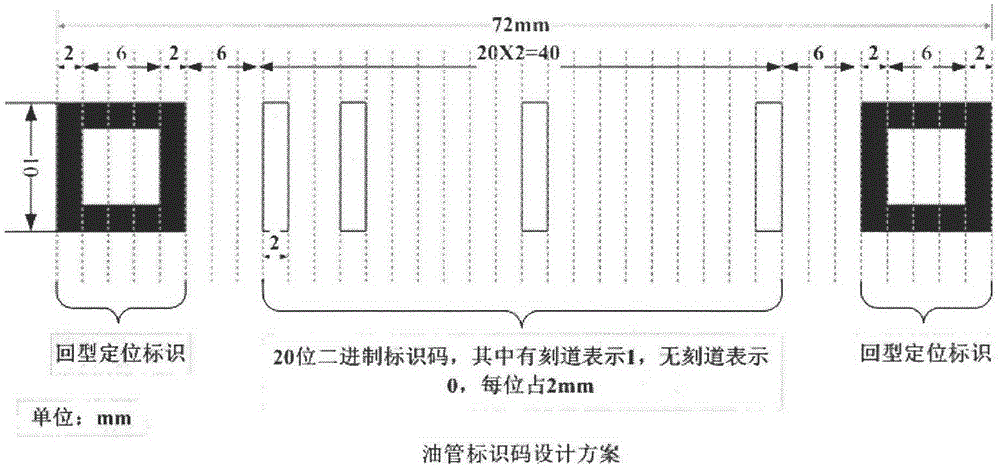
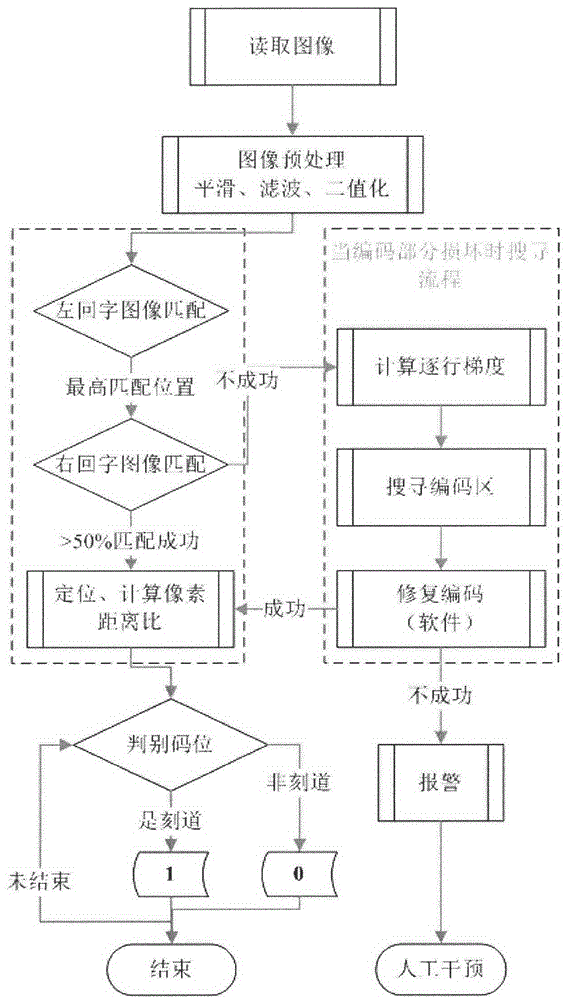
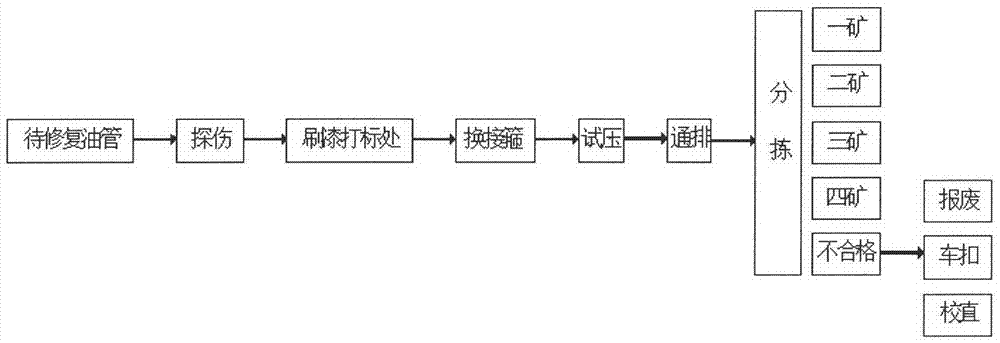
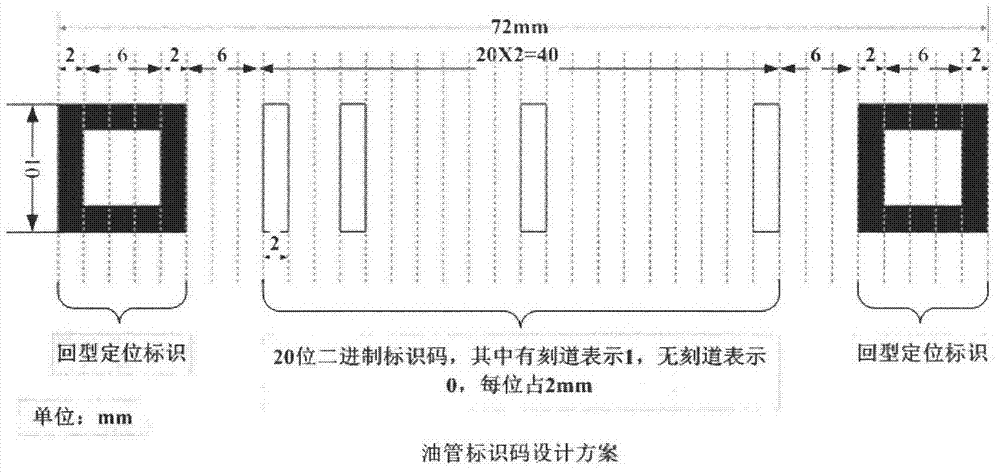
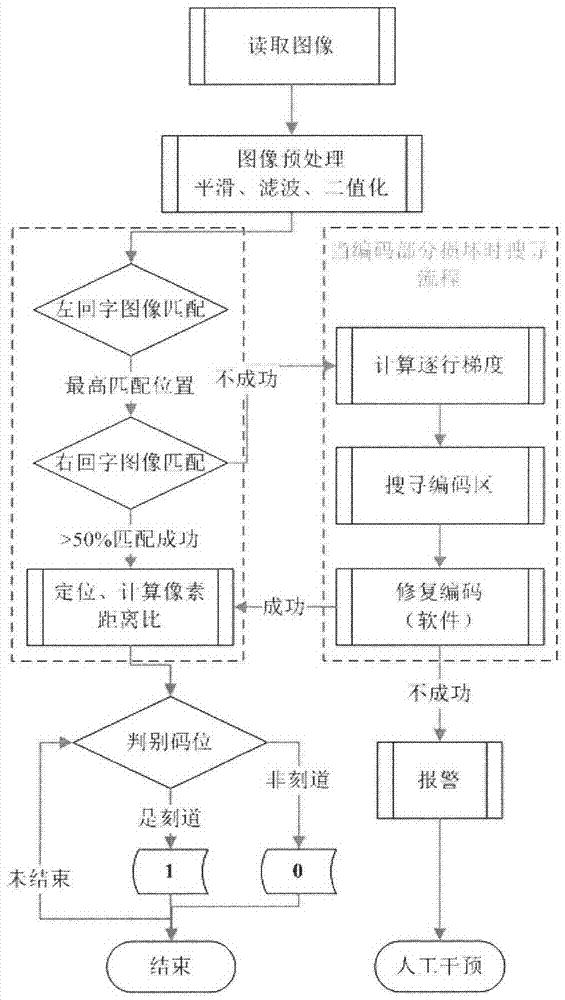
Method for encoding and identifying thick oil environment working device and management system
ActiveCN104598953AGuaranteed security strengthIntegrated highRecord carriers used with machinesSensing by electromagnetic radiationRecognition algorithmGlyph
The invention relates to a thick oil environment working device with a logo and a manufacturing method of the logo on the thick oil environment working device. The manufacturing method includes the step of recording a rectangular-ambulatory-plane shaped positioning icon and a long strip icon on the working device. Furthermore, the invention discloses a method and a device for identifying the logo. The method for identifying the logo includes the step: performing multi-information synchronization and identification on a code by using a two-dimensional searching and matching recognition algorithm, and realizing the digital management of the working device. Besides, the invention discloses an identity identification management system of an oil tube. According to the method for encoding and identifying the thick oil environment working device and the management system, the rectangular-ambulatory-plane shaped icon is convenient to position and identify, and also easy to record; the long strip icon is easy to record, clean and identify, and matched up with the principle of binary code; the recognition algorithm of the invention takes the two-dimensional searching and matching as the principle; by sampling a specific sampling point, the sampling frequency is reduced, the recognition scale is effectively improved and the integration of the encoding information is added; moreover, the recognition rate is greatly improved.
Owner:胜利油田胜利自动化开发有限责任公司
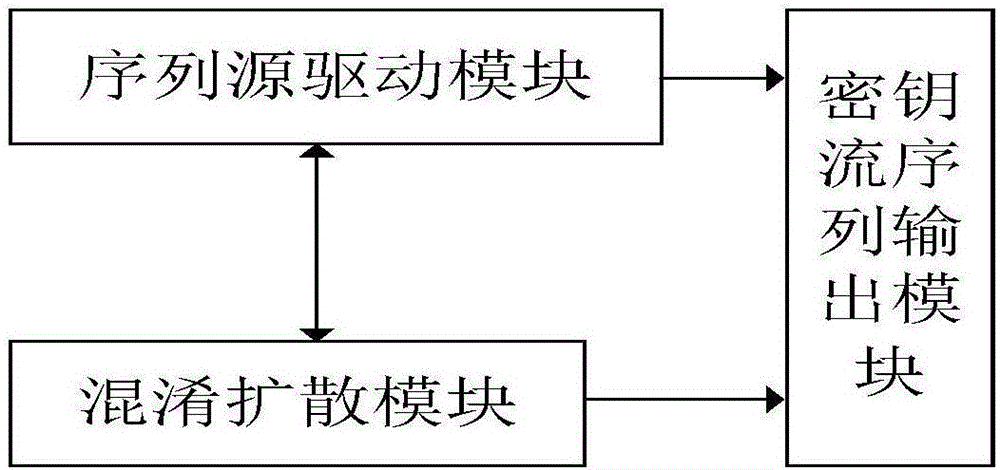
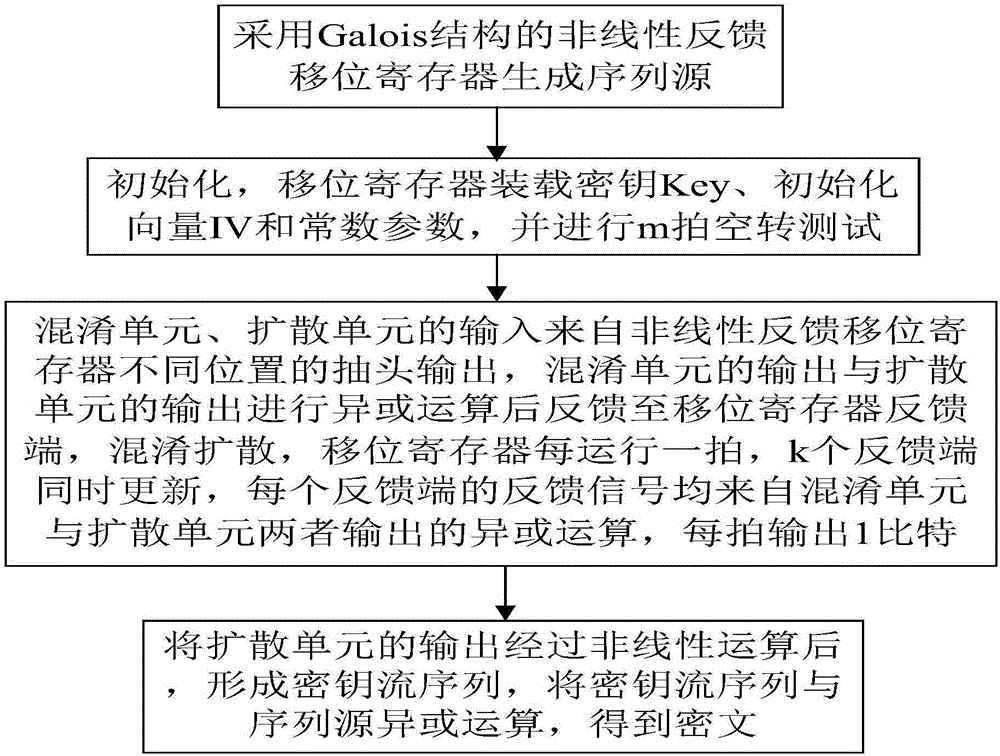
Sequence cipher realization device and sequence cipher realization method thereof
ActiveCN106254062AFlexible deploymentImprove environmental applicabilityEncryption apparatus with shift registers/memoriesNonlinear feedback shift registerCiphertext
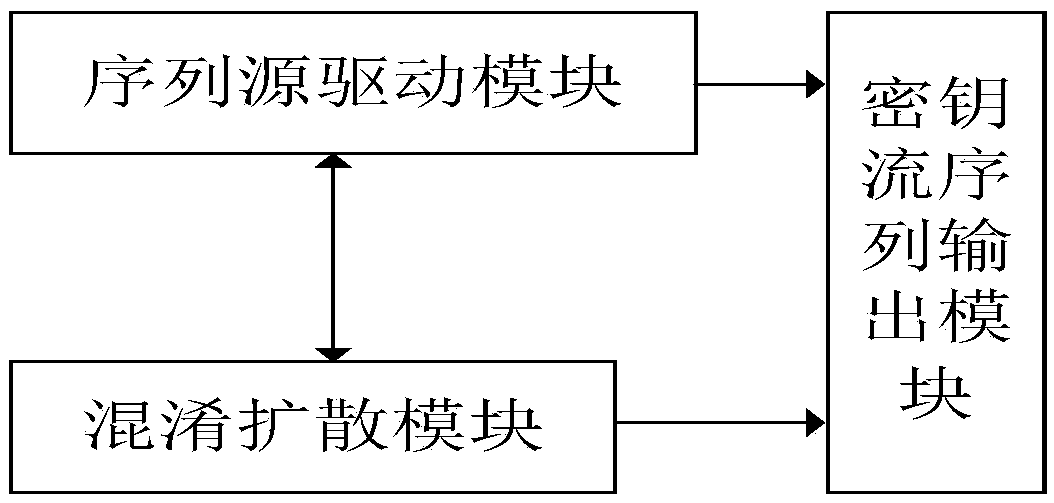
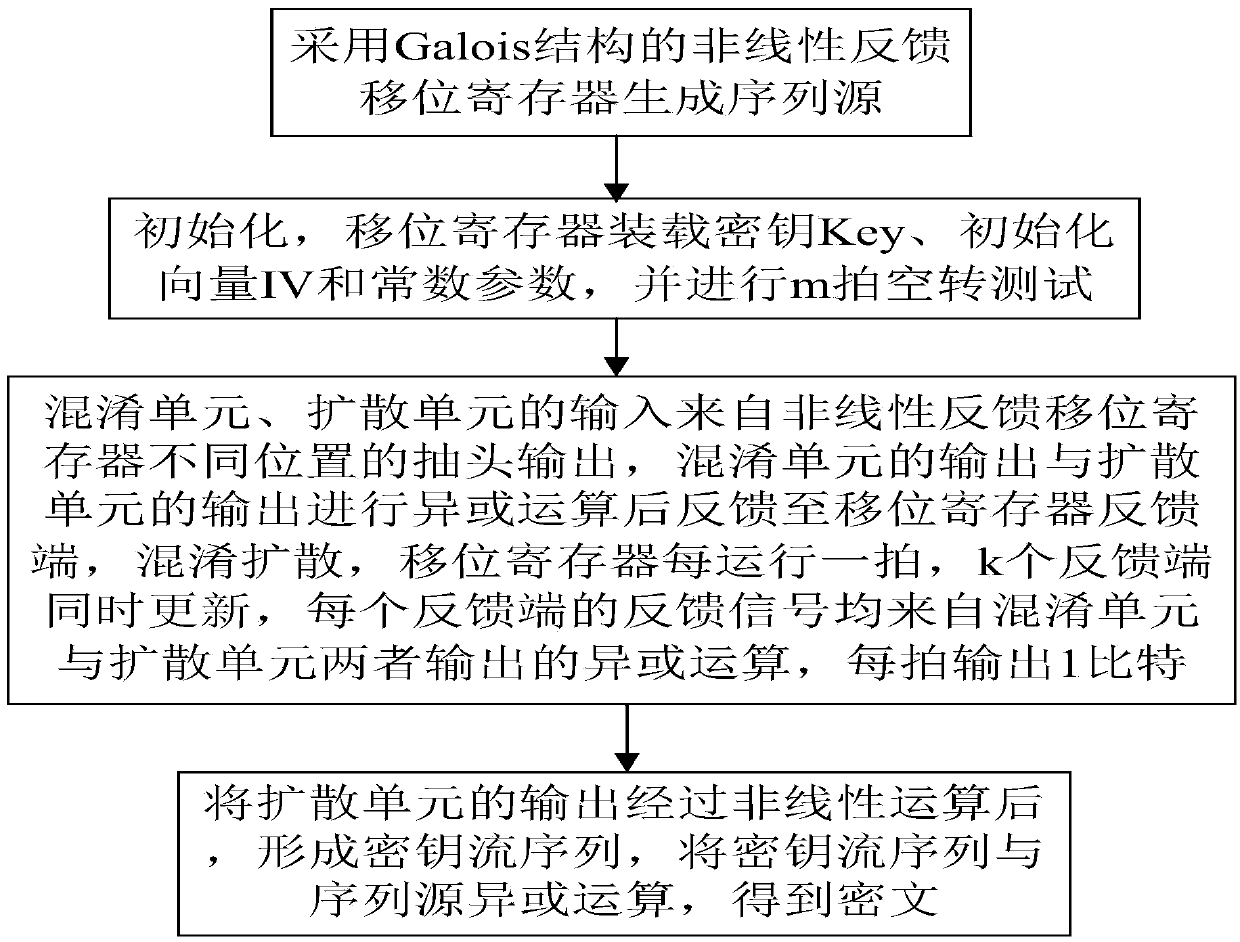
The invention relates to a sequence cipher realization device and a sequence cipher realization method thereof. The method comprises the following steps: firstly, generating a sequence source by adopting Galois-structure nonlinear feedback shift registers designed based on mixing and diffusion parts as a sequence source drive; and then, after the registers load keys, initialization vectors and constant parameters completely, carrying out idle operation for a certain number of beats, carrying out nonlinear operation on an output of the diffusion unit so that the output is taken as a key stream sequence, and carrying out exclusive or operation on the key stream sequence together with a plaintext sequence to form a ciphertext. According to the sequence cipher realization device and the sequence cipher realization method thereof disclosed by the invention, relatively less operation and hardware cost can be used; through combined use of the mixing unit and the diffusion unit, after multiple times of iterations, a pseudorandom sequence is output; according to hardware resource and speed requirements, the deployment and the implementation are flexible; and the requirements of communication for diverse networks and devices are met.
Owner:THE PLA INFORMATION ENG UNIV
Method for establishing 6LoWPAN (6 Local Wireless Personal Area Network) key
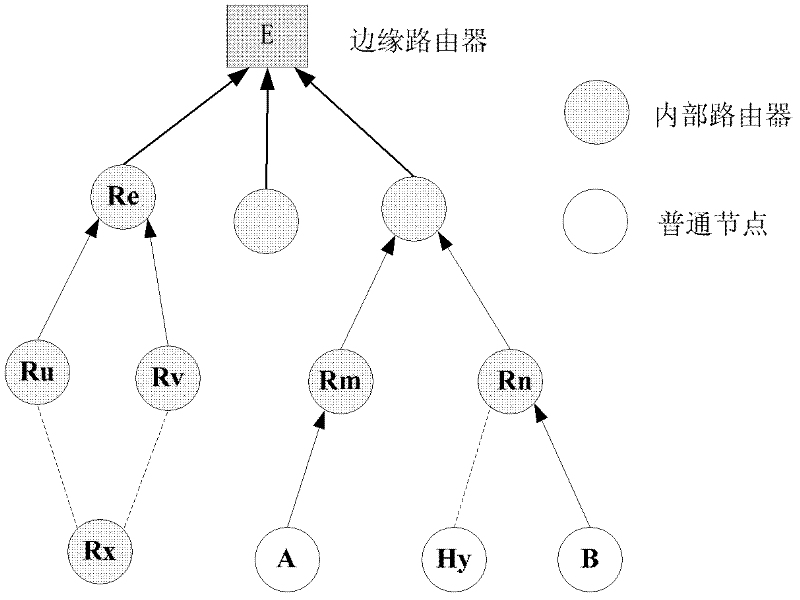
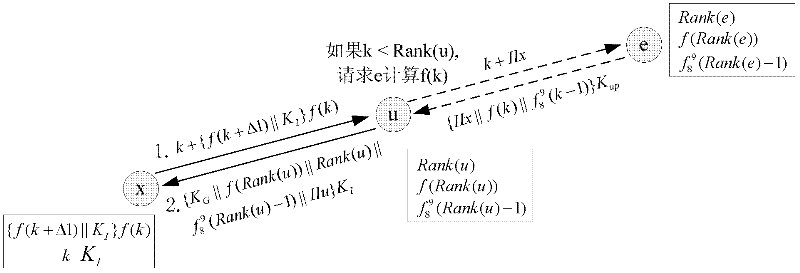
ActiveCN102448062ASmall amount of calculationGuaranteed security strengthSecurity arrangementHigh level techniquesComputer hardwareRelationship - Father
The invention provides a method for establishing a 6LoWPAN (6 Local Wireless Personal Area Network) key. The method comprises the following steps of: step 1, after receiving a first DIO (Direct Input / Output) message from a router node Ru, an internal router node Rx sends a message request to the node Ru to obtain a group key; step 2, after receiving the message, Ru calculates f(k) and f(k+delta1) according to a k value in the message; step 3, Ru decrypts {f(k+delta 1) / / KI}f(k) information by using f(k) and then compares the decrypted f(k+delta1) with a value calculated by Ru, if the decrypted f(k+delta 1) is equal to the calculated value, Rx passes through authentication of Ru; otherwise Rx does not pass through authentication; step 4, if Rx passes through the authentication, Ru saves KI as the key between Ru and Rx and sends a response message to Rx; step 5, after receiving the response message, Rx decrypts the whole message through KI to obtain an interface identifier IIu of Ru and then compares the interface identifier IIu with an interface identifier in a data package source address to authenticate Ru; and step 6, if Ru passes through authentication, Rx obtains the group key KG and takes Ru as a pair key KI between a father node and a storage of Rx. In the method for establishing a key, Hash is used repeatedly, therefore calculation amount is small.
Owner:SHANGHAI YINGLIAN SOMATOSENSORY INTELLIGENT TECH CO LTD
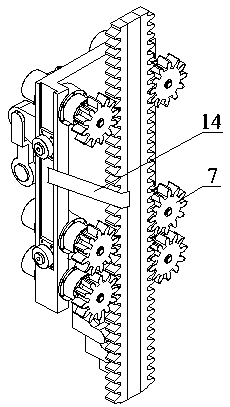
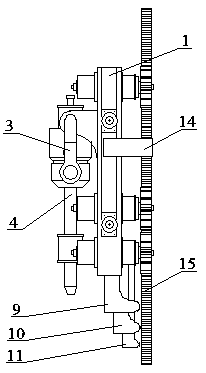
Gear rack drilling machine lifting device
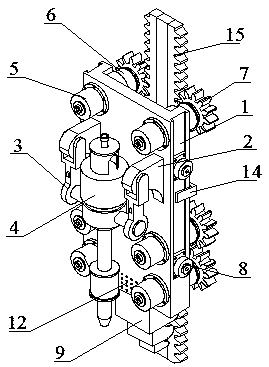
PendingCN107842318ASolve the problem of meshing misalignmentEasy meshDrilling rodsDerricks/mastsHydraulic motorReduction drive
The invention relates to a gear rack drilling machine lifting device, and belongs to the technical field of mining and drilling tools for petroleum and nature gas. The gear rack drilling machine lifting device is composed of a mounting plate, driving machines, hydraulic motors, a retarder, gears and an alignment machine; multiple groups of hydraulic motors and retarders in a symmetric state are fixedly arranged at the two sides of the mounting plate through bolts, the retarders are provided with gears by splines; and the driving machines are arranged at fixed lugs and lifting rings symmetrically arranged at the mounting plate between the hydraulic motors, end surfaces of two sides of the mounting plate are symmetrically provided with guidance rollers, and the alignment machine is arrangedat the lower end of the mounting plate through bolts. According to the gear rack drilling machine lifting device, the problem of meshing and dislocating of gear racks caused by the deflection of an existing lifting device can be solved, right meshing of the gear racks is guaranteed to run the lifting device smoothly, the drilling efficiency is improved, the drilling cost is lowered, the security strength of the lifting device is guaranteed simultaneously, and further greater load and anti-thrust force can be provided.
Owner:SINOPEC OILFIELD EQUIP CORP +1
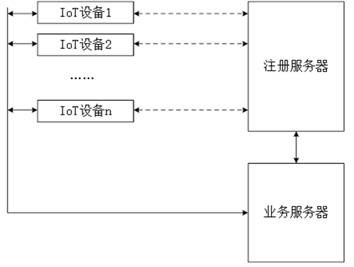
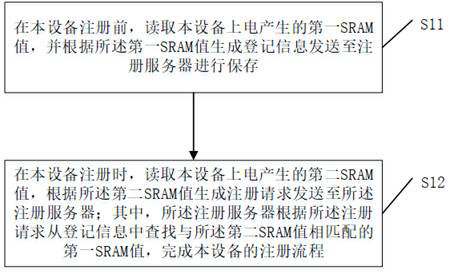
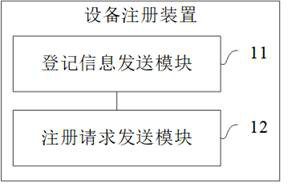
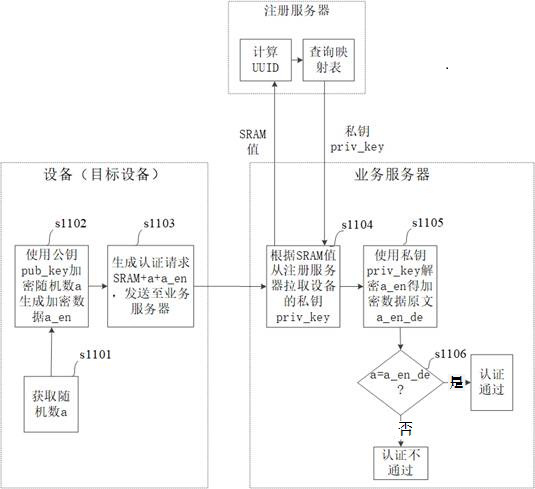
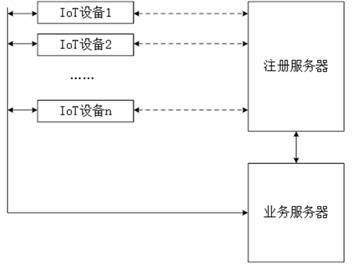
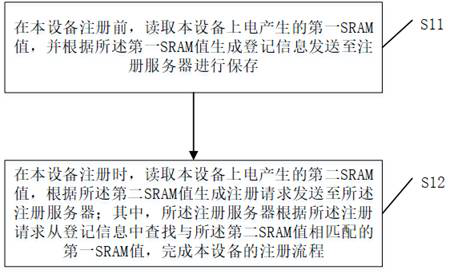
Equipment registration, authentication and data transmission method and device
ActiveCN112804678APrevent or enable core functionsEasy accessSecurity arrangementComputer hardwareData transmission
The embodiment of the invention provides an equipment registration method and device, an equipment authentication method and device, an equipment data transmission method and device, electronic equipment and a computer readable storage medium. The registration method comprises the following steps: before registration of the equipment, reading a first SRAM value generated by electrification of the equipment, generating registration information according to the first SRAM value, and sending the registration information to a registration server for storage; when the equipment is registered, reading a second SRAM value generated by electrifying the equipment, generating a registration request according to the second SRAM value, and sending the registration request to the registration server, wherein the registration server searches a first SRAM value matched with the second SRAM value from the registration information according to the registration request, and completes the registration process of the equipment. According to the technical scheme, when the equipment is registered, only the SRAM value needs to be read out and registered to the registration server, operations such as certificate burning on the equipment on a production line are not needed, equipment access is facilitated, and the flexibility of equipment authentication access is improved.
Owner:ZHEJIANG KOUBEI NETWORK TECH CO LTD
Coding and identification method and management system for heavy oil environmental work equipment
ActiveCN104598953BGuaranteed security strengthIntegrated highRecord carriers used with machinesSensing by electromagnetic radiationAmbulatoryRecognition algorithm
The invention relates to a thick oil environment working device with a logo and a manufacturing method of the logo on the thick oil environment working device. The manufacturing method includes the step of recording a rectangular-ambulatory-plane shaped positioning icon and a long strip icon on the working device. Furthermore, the invention discloses a method and a device for identifying the logo. The method for identifying the logo includes the step: performing multi-information synchronization and identification on a code by using a two-dimensional searching and matching recognition algorithm, and realizing the digital management of the working device. Besides, the invention discloses an identity identification management system of an oil tube. According to the method for encoding and identifying the thick oil environment working device and the management system, the rectangular-ambulatory-plane shaped icon is convenient to position and identify, and also easy to record; the long strip icon is easy to record, clean and identify, and matched up with the principle of binary code; the recognition algorithm of the invention takes the two-dimensional searching and matching as the principle; by sampling a specific sampling point, the sampling frequency is reduced, the recognition scale is effectively improved and the integration of the encoding information is added; moreover, the recognition rate is greatly improved.
Owner:胜利油田胜利自动化开发有限责任公司
Data security system and method suitable for sharing encrypted files and recovering keys
ActiveCN102291234AKey recoveryGuaranteed security strengthKey distribution for secure communicationMultiple keys/algorithms usageKey storageKey recovery
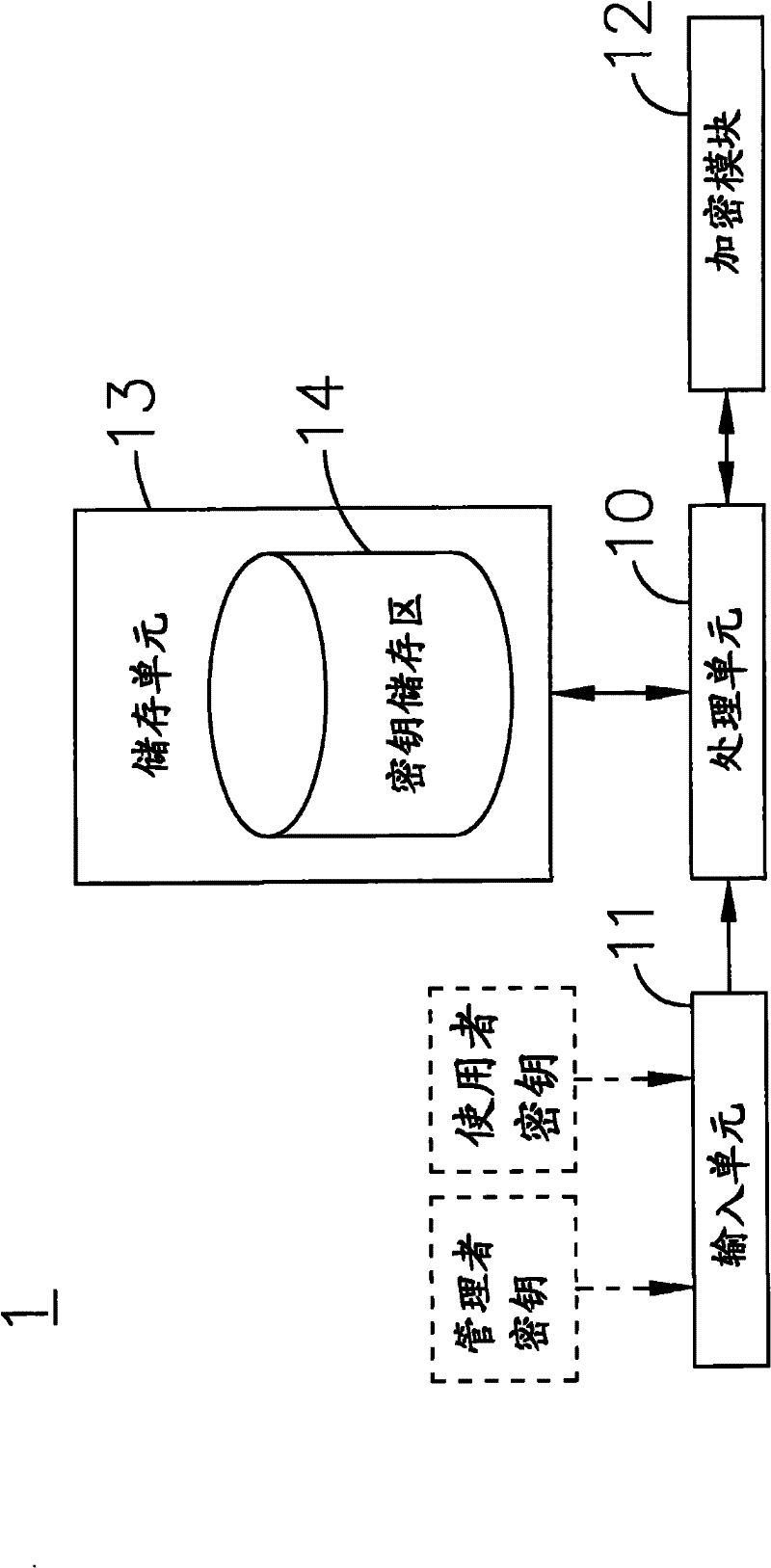
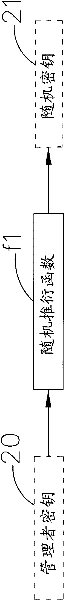
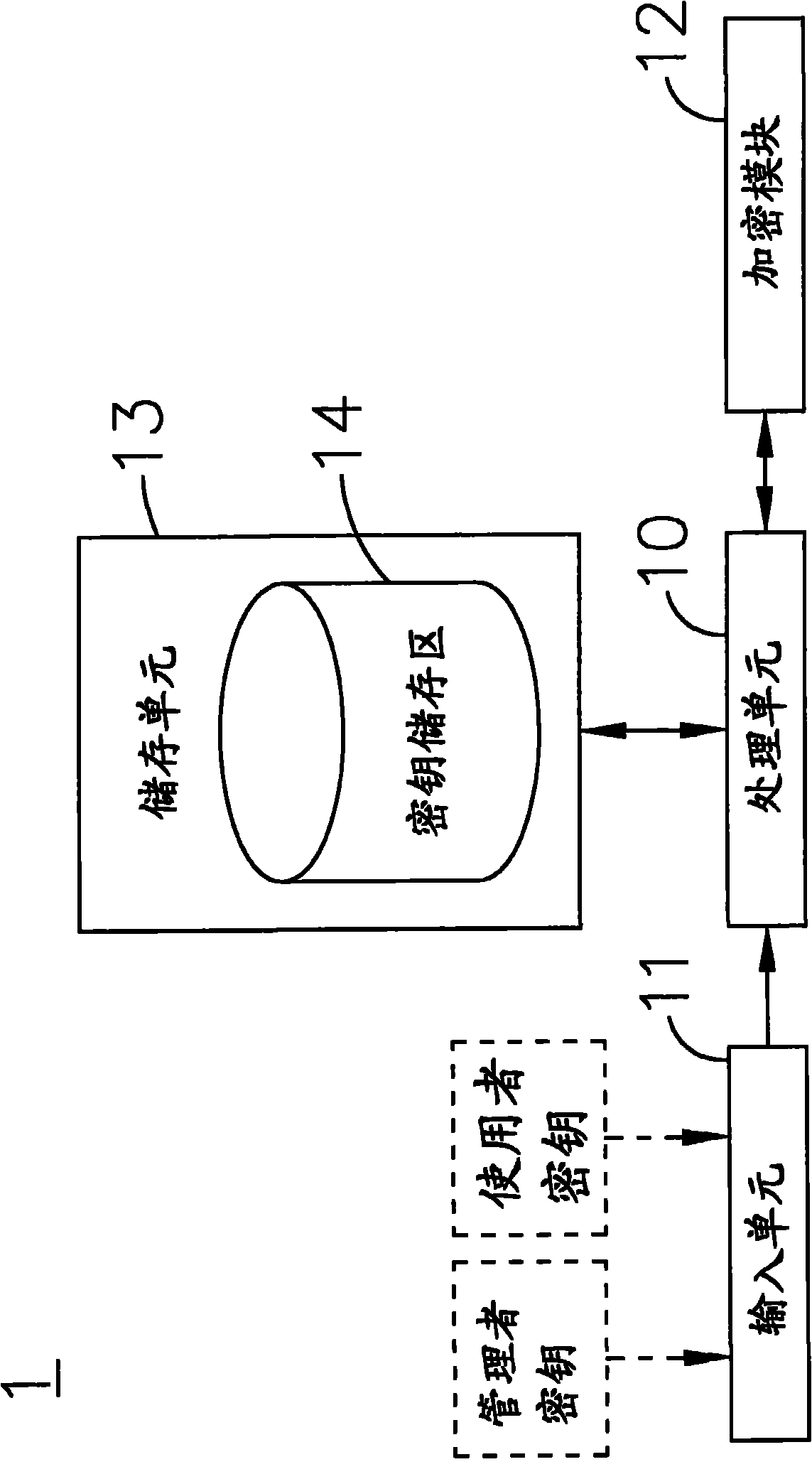
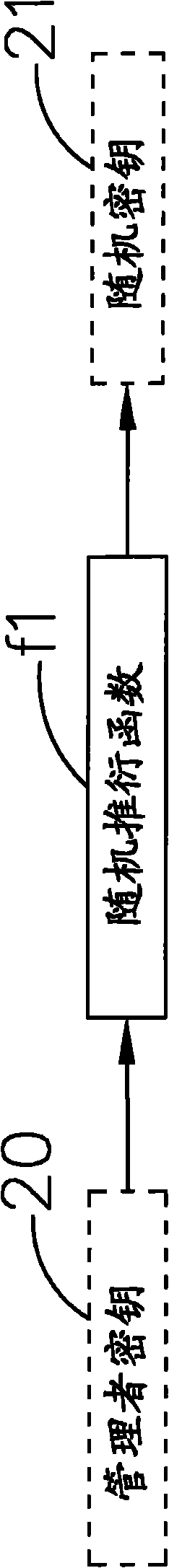
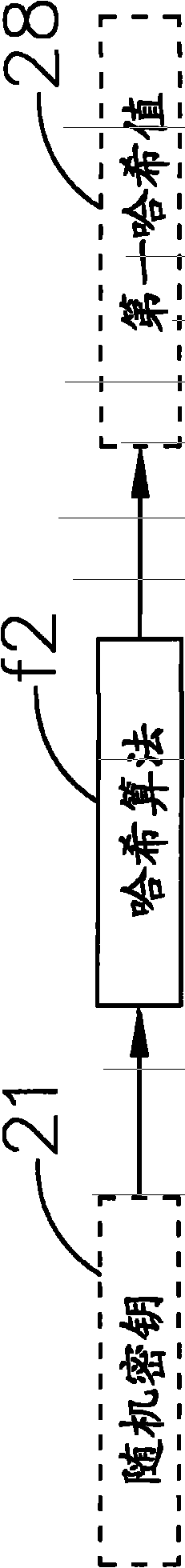
The invention relates to a data security system applicable to sharing an encrypted file and recovering a secrete key and a method thereof, which are used for converting a source file into the encrypted file, wherein an administrator secrete key and a user secrete key are input through an input unit; a random secrete key is generated through a processing unit with a random derivation function according to the administrator secrete key; and a secrete key storage area is provided for storing the random secrete key and the user secrete key, which are encrypted and protected through the administrator secrete key. In the encryption process, an encryption module randomly generates a session secrete key so that the content of the source file is encrypted into encrypted data; the session secrete key is encrypted through the administrator secrete key or the user secrete key so that an encrypted session secrete key is generated; and the encrypted session secrete key and the encrypted data are packed into the encrypted file. Thereby, the encrypted file only has one encrypted session secrete key so that the safety strength of the encrypted file can be ensured. In the decryption process, the administration secrete key can be used by an administrator to decrypt the secrete key storage area, and consequently the random secrete key and the user secrete key are taken out to decrypt the encrypted file.
Owner:EGIS TECH
Key management method for integrated avionic system
ActiveCN101908962BWith graded safety featuresImprove efficiencyKey distribution for secure communicationUser identity/authority verificationAviationElectronic systems
The invention relates to a key management method for an integrated avionic system. The key management functions in the entire process from the generation to final destruction of a key and is realized as a functional component for the safety management (GSM-SM) of system management in an integrated modular avionic (IMC) system to perform unified management on all keys in the system; and the key management mainly comprises the following steps of: 1) generating the keys; 2) loading the keys; 3) distributing the keys; and 4) using the keys. The method is favorable for improving the active defenselevel of airborne embedded systems of China, constructing and perfecting a safety guarantee system of the integrated avionic system, defending an equipment system against foreign threats and improving the destruction resistance of the aviation equipment system.
Owner:AVIC NO 631 RES INST
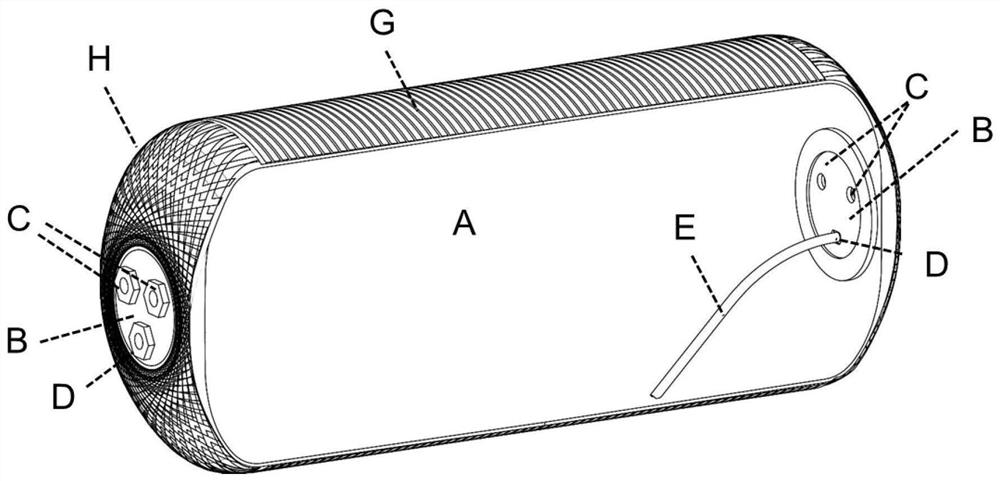
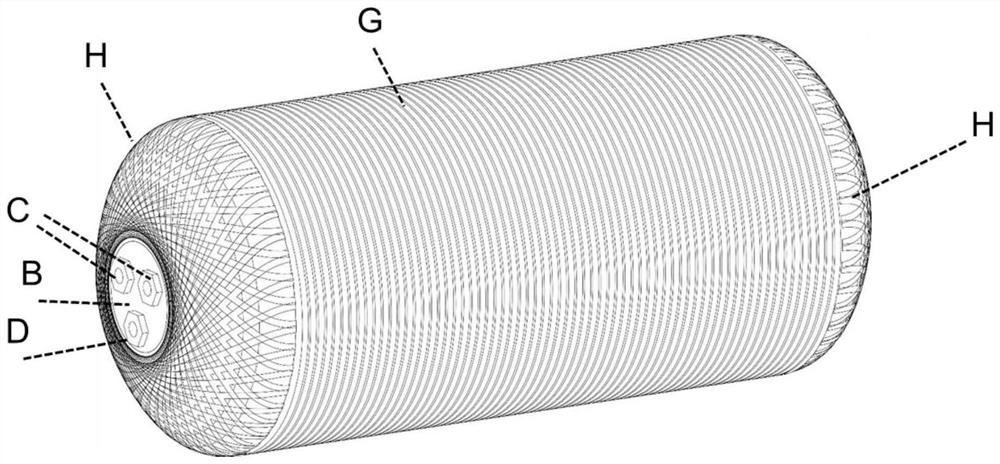
Air reservoir adopting composite material
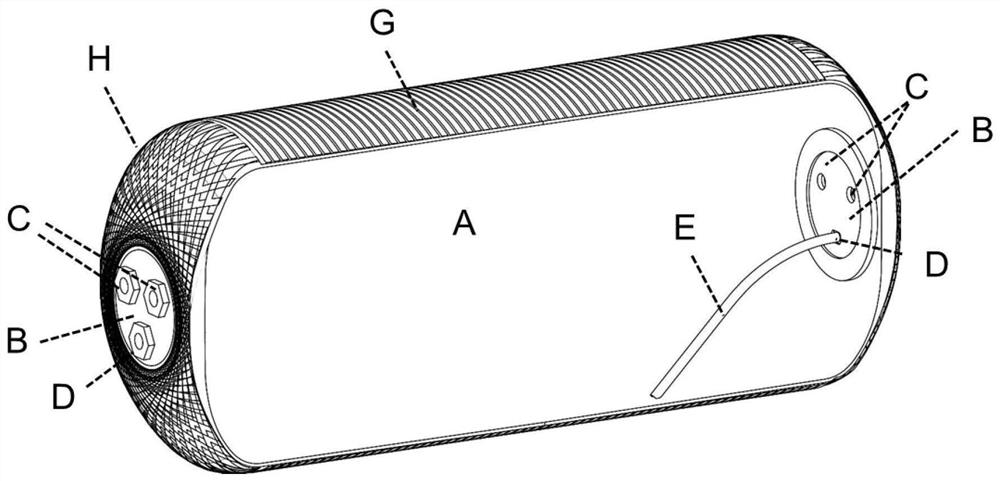
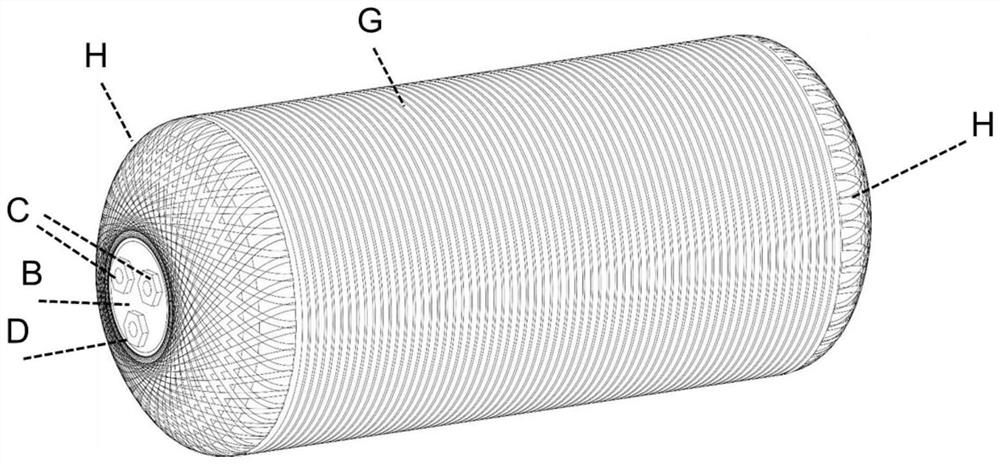
ActiveCN112124284ASolve the defects of hidden strengthHigh strengthReservoir arrangementsFiberDrainage tubes
The invention relates to an air reservoir adopting a composite material. The air reservoir comprises an inner container, inserts are arranged at the ends of the two sides of the inner container, exhaust pipe connectors and drainage pipe connectors are arranged on the inserts on the two sides, internal drainage pipes are connected to the drainage pipe connectors on the two sides, the tail ends of the internal drainage pipes are connected to the bottommost portion in the inner container, and a fiber resin composite winding layer is arranged on the outer layer of the inner container and comprisesan axial winding layer and a radial winding layer. According to the air reservoir adopting the composite material, full coverage of radial and axial winding of a cylinder body is realized; and in addition, the exhaust pipe connectors and drainage pipe connectors are arranged on the aluminum alloy inserts at the ends, the inserts have good strength as a metal piece, the inserts can further be wrapped by the projection axially wound in the axis direction of the cylinder body, and the safety strength of the two sides of the air reservoir is guaranteed.
Owner:DONGFENG COMML VEHICLE CO LTD
Error sampling method for lattice public key password
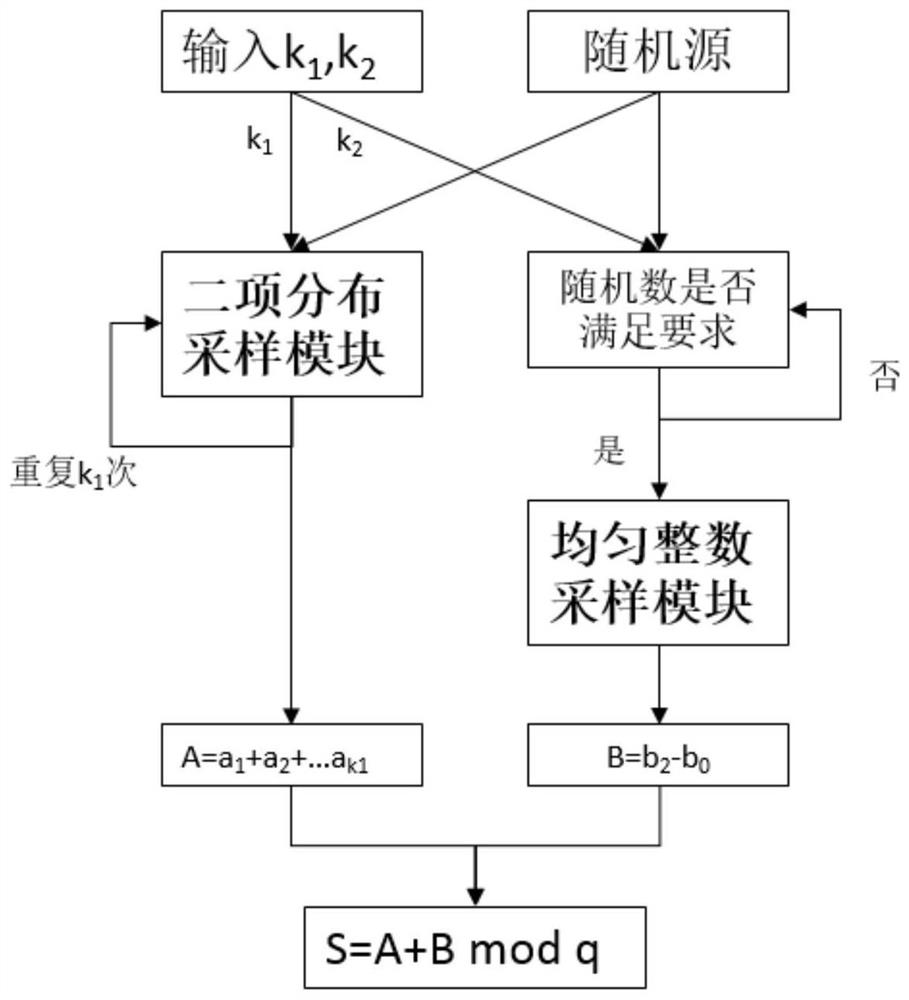
ActiveCN109889321AImprove efficiencyWide selectionKey distribution for secure communicationPublic key for secure communicationPasswordComputer science
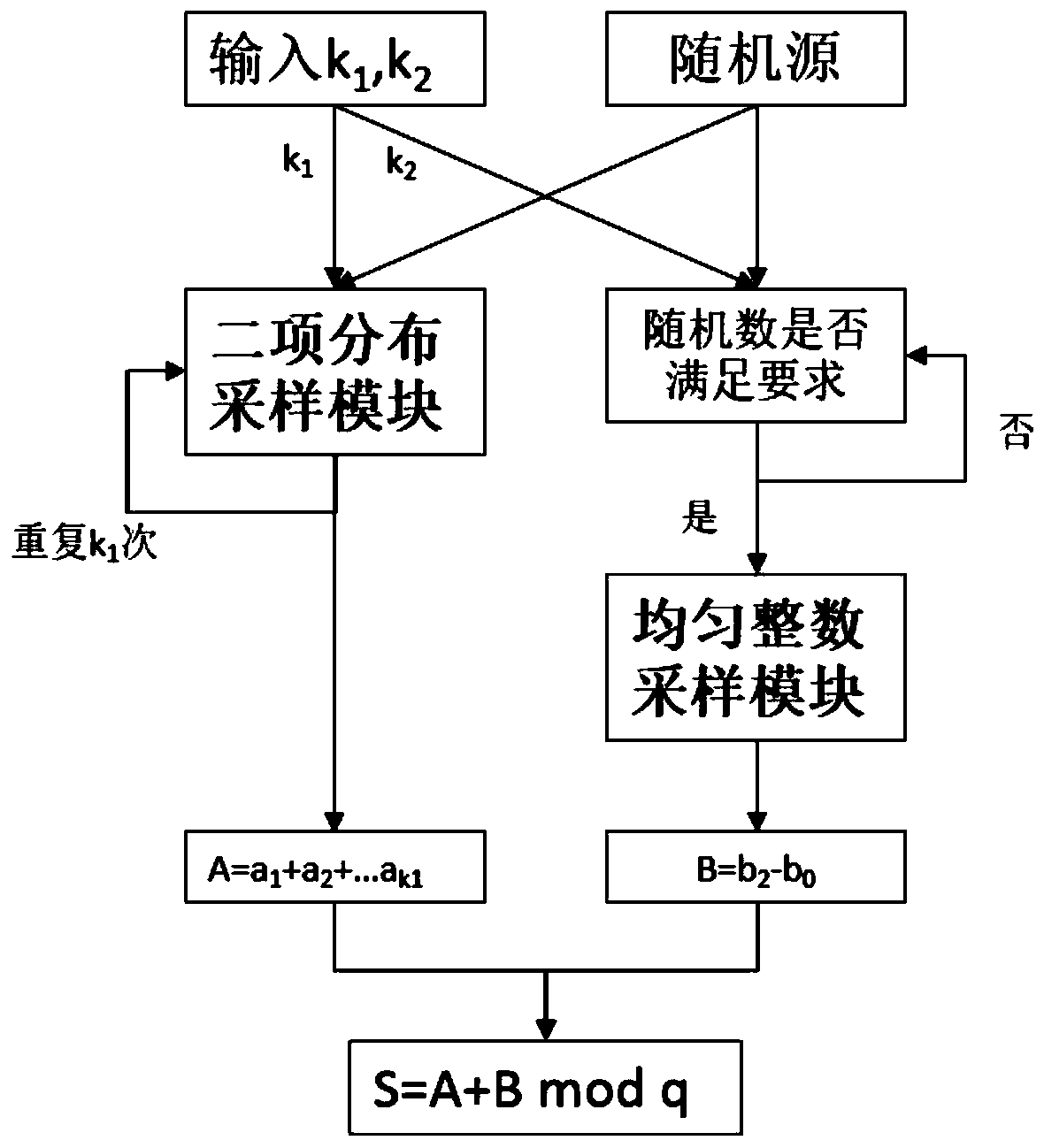
The invention discloses an error sampling method for a lattice public key password. The error sampling method comprises the following steps: step 1, receiving input parameters k1 and k2, and operatinga k1-time binomial distribution sampling module and a k2-time integer uniform sampling module for representing a result of a sampling algorithm; step 2, outputting an integer a conforming to binary distribution through a random number generated by an input 2-bit random source by using a binary distribution sampling module; step 3, repeating the binomial distribution sampling module k1 times, andcalculating the output sum A of the binomial distribution sampling module k1 times; step 4, an integer uniform sampling module is used; outputting a structure B conforming to integer uniform samplingfor k2 times through a random number generated by an input bit random source (shown in the specification); and outputting the structure B conforming to the integer uniform sampling for k2 times through the random number generated by the input bit random source, and step 5, outputting a sampling result S = A + B mod q. According to the method, two different sampling algorithms are combined with each other, when the parameters k1 and k2 are selected properly, the good balance between the efficiency and the safety can be achieved, and meanwhile the flexibility is high.
Owner:TSINGHUA UNIV
Lightweight text encryption method based on improved Feistel structure
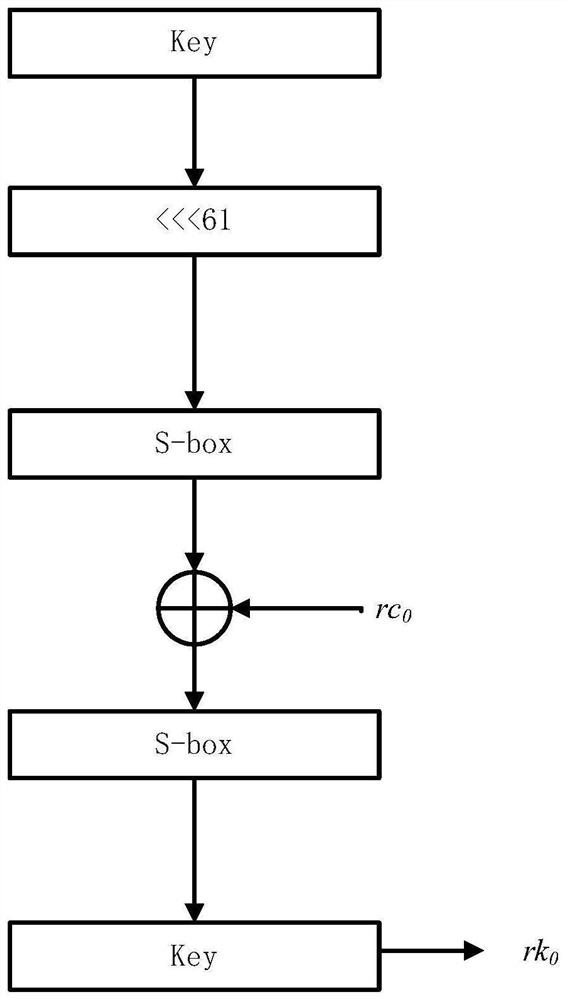
PendingCN114866224AGuaranteed StrengthHigh speedEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsResource assignmentAlgorithm
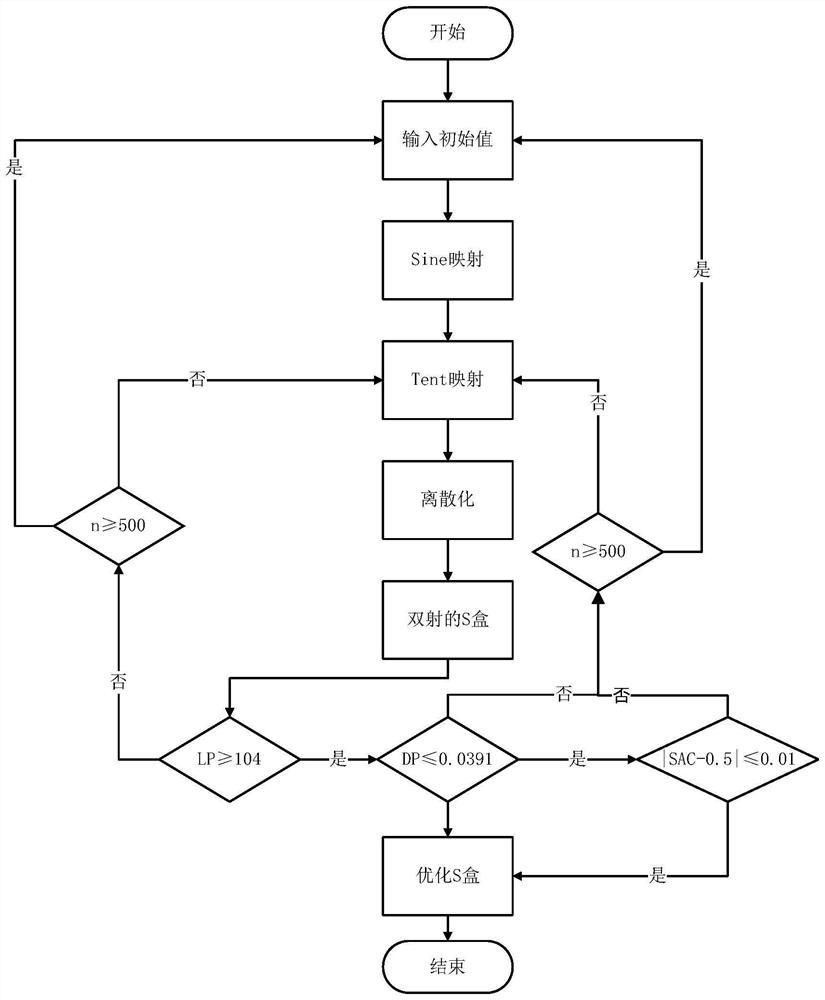
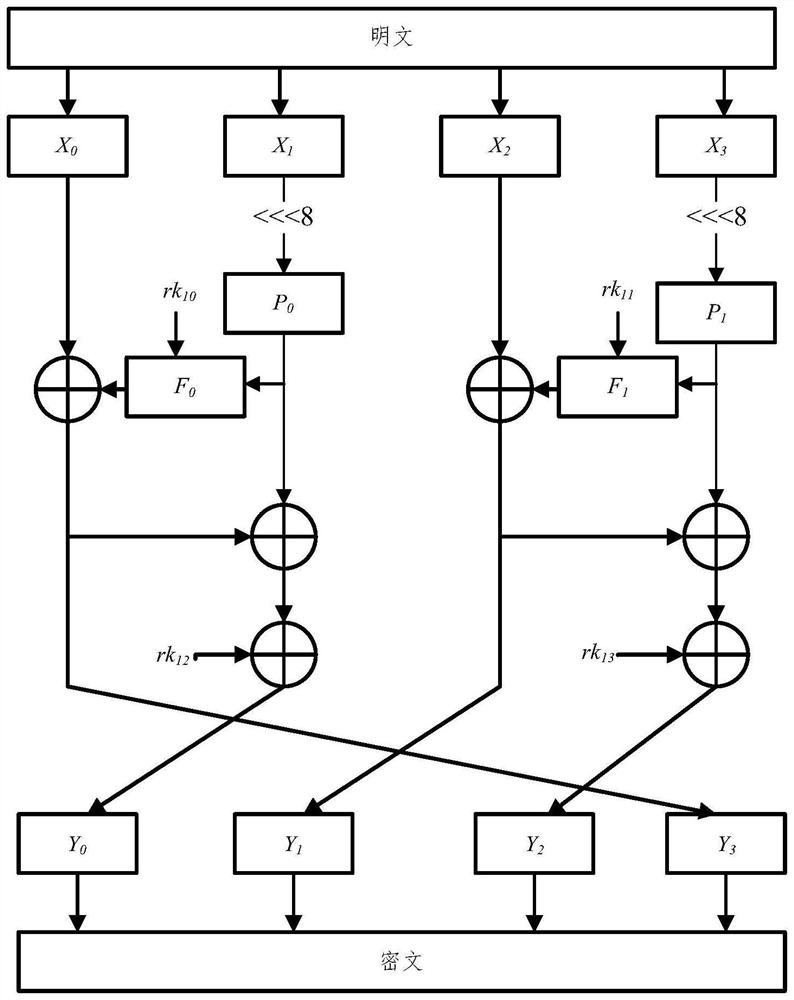
The invention discloses a text lightweight encryption method based on an improved Feistel structure, and belongs to the technical field of information security. Due to the fact that a traditional encryption method needs a large amount of resource allocation, the encryption and decryption speed is low, and the standards of rapidity and real-time performance cannot be met, the text-oriented lightweight grouping encryption and decryption method is designed. The S box with the nonlinearity of 110, the differential approximation probability of 0.0391 and the strict avalanche criterion correlation matrix average value of 0.5066 is generated and optimized by applying two chaotic mappings. According to the method, a generalized Feistel structure is correspondingly improved, so that the improved structure can process all intermediate states at a time, and a text-oriented lightweight grouping encryption and decryption algorithm is formed by combining an optimized S box, a newly designed key expansion algorithm, a P box and the like. The GE number of the algorithm meets the lightweight standard, and the algorithm is tested, analyzed and compared to obtain better results, so that the algorithm is suitable for providing encryption and decryption functions for limited equipment.
Owner:HARBIN INST OF TECH AT WEIHAI
Vehicle front pillar assembly and automobile
ActiveCN109591894BReduce deformationImprove structural strengthSuperstructure subunitsSuperstructure connectionsStructural engineeringMechanical engineering
The invention discloses a vehicle front column assembly and an automobile. The vehicle front column assembly comprises an upper reinforcing plate, a lower reinforcing plate, an upper hinge plate, a front column supporting plate, a lower hinge plate and a front wall supporting plate, wherein the upper reinforcing plate and the lower reinforcing plate are independently molded and connected with eachother; the upper hinge plate is arranged on the upper reinforcing plate; the front column supporting plate and the lower hinge plate are independently molded and connected with each other; the frontcolumn supporting plate is connected to one side, facing away from the upper reinforcing plate, of the lower reinforcing plate; the lower hinge plate faces away from the lower reinforcing plate; and the front wall supporting plate is connected to the connecting part of the lower hinge plate and the front column supporting plate. The automobile comprises a front wheel cover side sill outer panel and the vehicle front column assembly; and the upper reinforcing plate and the lower reinforcing plate are both connected with the front wheel cover side sill outer panel in a laminated manner. According to the vehicle front column assembly and the automobile, the anti-bending capacity of a front column during high speed frontal collision or biasing collision is improved, the stress is effectively dispersed, the deformation of the front column during high speed frontal collision or biasing collision is reduced, the stability of the front column is kept, and the safety of the whole automobile isenhanced.
Owner:WM MOTOR TECH GRP CO LTD
A liquefied natural gas cylinder for vehicles and its valve protection device
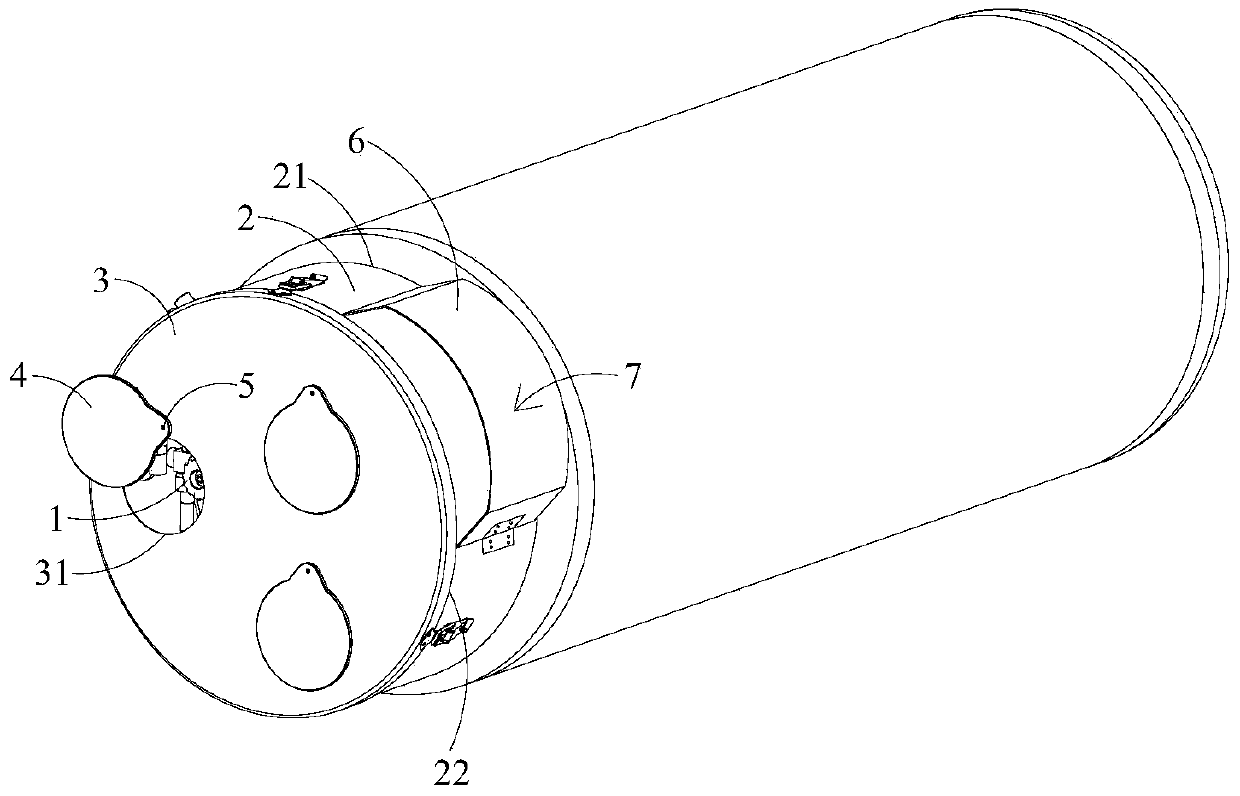
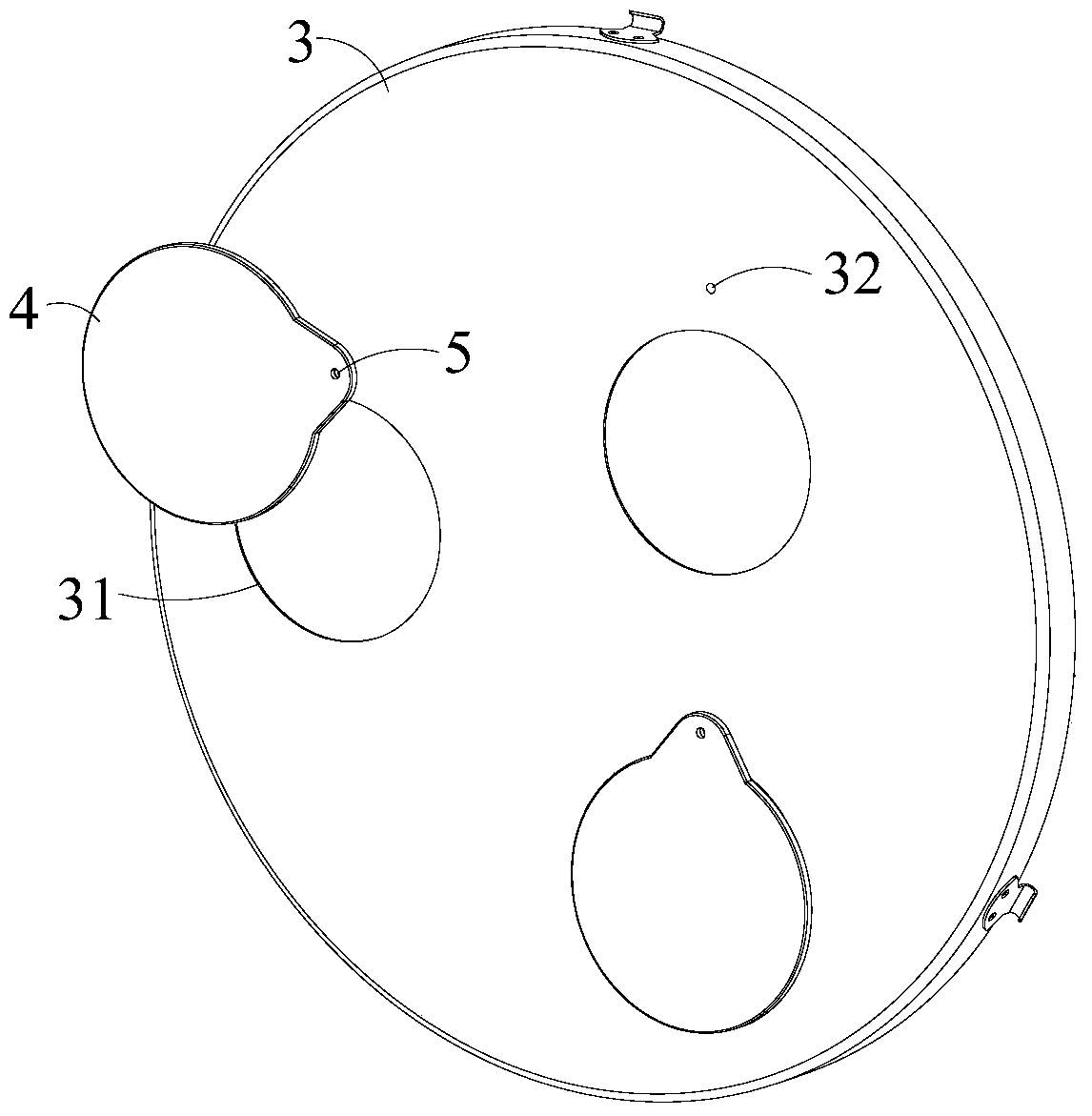
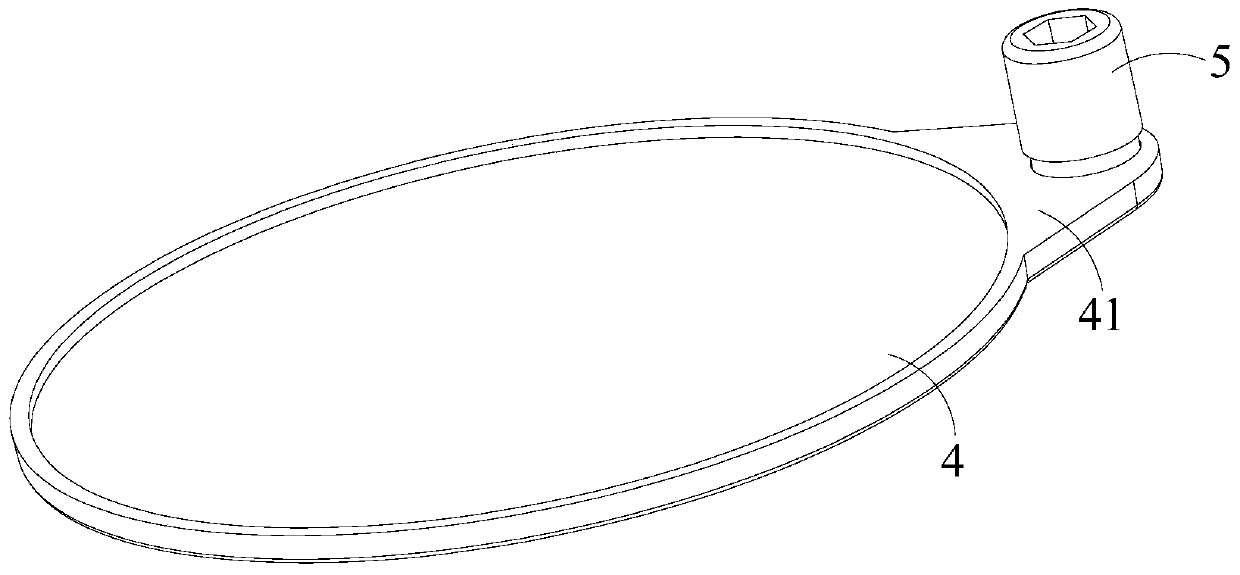
ActiveCN105650464BGuaranteed security strengthLow costContainer filling methodsContainer discharging methodsGas cylinderEngineering
The invention relates to a liquefied natural gas cylinder and a valve protection device thereof, in particular to a valve protection device of a liquefied natural gas cylinder for vehicles. At least one end of the air cylinder is provided with a valve. An air cylinder protection device is located at the end, with the valve, of the air cylinder. The air cylinder protection device comprises a metal protection ring, a protection ring cover plate and a hand wheel cover plate. The valve protection device is characterized in that one end of the metal protection ring is fixedly connected with a front seal of the air cylinder; the metal protection ring surrounds the valve of the air cylinder; the protection ring cover plate is detachably mounted at the other end of the metal protection ring; the protection ring cover plate shields the valve of the air cylinder; the protection ring cover plate is provided with at least one through hole; the hand wheel cover plate is rotationally mounted on the protection ring cover plate through a positioning mechanism and can shield the through hole selectively; and the positioning mechanism can position the hand wheel cover plate at any angle.
Owner:ZHANGJIAGANG CIMC SANCTUM CRYOGENIC EQUIP +2
A communication method and system based on quantum ukey
ActiveCN107769913BTake advantage of secure communicationsOvercome deficienciesKey distribution for secure communicationPlaintextApplication server
The invention discloses a communication method and system based on the quantum Ukey, aiming to solve the potential safety hazards that the algorithm is not safe, the user password strength is not highenough, the user password plaintext input, secret key distribution and management are difficult, and the secret key cannot be automatically updated in the aspects of current identity authentication and security access cloud service application. The communication method based on the quantum Ukey comprises the following steps that when an access application service instruction is acquired, a user terminal determines a first quantum key by the quantum Ukey established the connection relation, and sending the corresponding authentication message to an authentication management platform for identity authentication; the authentication management platform obtains a second quantum key from the KMS according to the authentication message, and decrypting the encrypted information in the authentication message, if the decrypted information is consistent with the plaintext information in the authentication message, the identity authentication is determined to pass, and the passing information isreturned to the user terminal, so that the user terminal accesses the application server through the first quantum key.
Owner:QUANTUMCTEK GUANGDONG CO LTD
An Error Sampling Method for Lattice Public Key Cryptography
ActiveCN109889321BImprove efficiencyWide selectionKey distribution for secure communicationPublic key for secure communicationAlgorithmEngineering
The invention discloses an error sampling method for lattice public key cryptography, which comprises the following steps: Step 1, receiving an input parameter k 1 ,k 2 , indicating that the result of the sampling algorithm needs to run k 1 subbinomial sampling module and k 2 Sub-integer uniform sampling module; step 2, using the binomial distribution sampling module, and outputting an integer a that obeys the binomial distribution through the random number generated by the input 2-bit random source; step 3, repeating the binomial distribution sampling module k 1 times, calculate the binomial distribution sampling module k 1 The sum A of the secondary outputs; step 4, using the integer uniform sampling module, the random number generated by the input bit random source, the output obeys k 2 Structure B of sub-integer uniform sampling; step 5, output sampling result S=A+B mod q. The present invention combines two different sampling algorithms, and when the parameters k1 and k2 are properly selected, a good balance between efficiency and safety can be achieved, and at the same time, it has greater flexibility.
Owner:TSINGHUA UNIV
Plastic tank water treatment equipment
PendingCN112849803AHeat settableCreepableLarge containersUnderwater structuresStructural engineeringMechanical engineering
The invention discloses plastic tank water treatment equipment. The equipment comprises a tank body, end sockets are fixedly connected to the two ends of the tank body, reinforcing strips are installed in the end sockets, a plurality of evenly-spaced circular rings are arranged in the tank body and tightly attached to the inner wall, and a plurality of evenly-spaced reinforcing blocks are arranged at the position, located at the periphery of the rings, of the inner wall of the tank body. Circular holes are formed in the reinforcing blocks, the head ends of the circular rings penetrate through the circular holes and then are connected with the tail end into a whole, saddle bases are arranged at the bottom of the tank body, the saddle bases are welded to the two sides of the bottom of the tank body in a two-section split charging manner, and the bottom face, located between the saddle bases, of the tank body is tightly attached to the placing face. Lifting lugs are arranged at the outer side edges of the saddle bases, reinforcing lining plates are arranged at the inner side edges of the saddle bases, the reinforcing lining plates are fixedly connected with the outer side edges of the saddle bases through bolts, the lifting lugs are welded to the reinforcing lining plates, and a ladder stand is arranged on the outer wall of the tank body. According to the equipment, the production efficiency is high, the strength is high, various use occasions are met, and the environment-friendly effect is achieved.
Owner:JIANGSU JINSHAN ENVIRONMENTAL PROTECTION TECH
Device registration, authentication and data transmission method and device
ActiveCN112804678BPrevent or enable core functionsEasy accessSecurity arrangementComputer hardwareEngineering
Owner:ZHEJIANG KOUBEI NETWORK TECH CO LTD
Air-inflating tire lining type rapid shaping and heat-preserving building and construction mode thereof
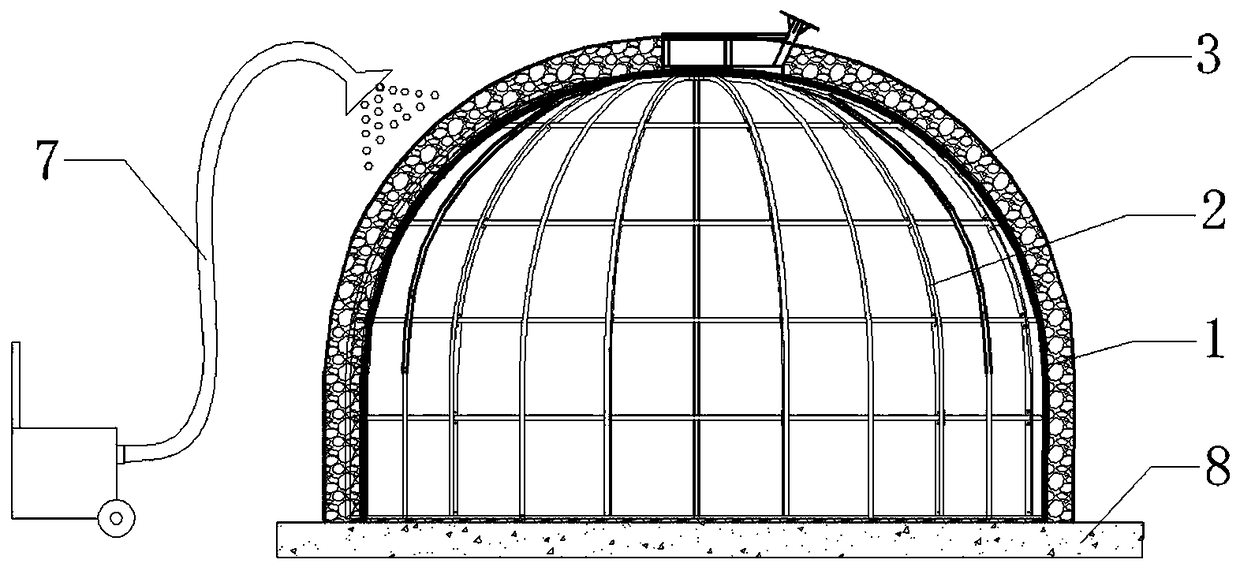
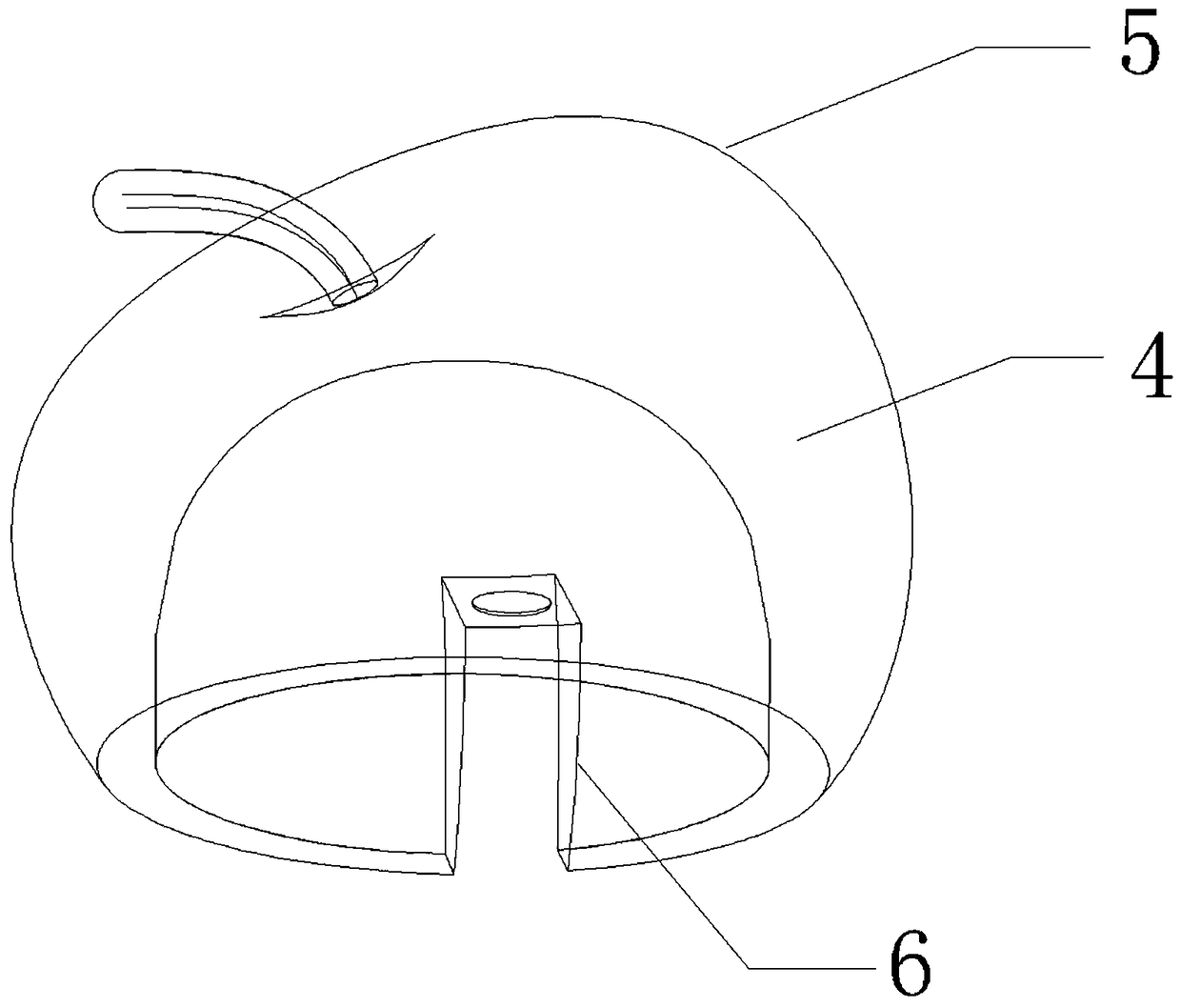
InactiveCN108533061AGuaranteed security strengthLow costTents/canopiesArchitectural engineeringMultiple layer
The invention discloses an air-inflating tire lining type rapid shaping and heat-preserving building structure. The structure sequentially includes an inner tire layer, a supporting layer, a shaping and heat-preserving layer and an outer decorating layer from inside to outside and the inner tire layer, the supporting layer and the shaping and heat-preserving layer are fixedly connected into a whole. According to the air-inflating tire lining type rapid shaping and heat-preserving building structure and the construction mode thereof, the building structure is compounded by multiple layers of structures; the advantage of a traditional tend which is constructed quickly is provided and the same well living experience of hotel type accommodation is provided; the cost of construction integral materials is lowered, modeling is beautiful and diversiform, any infrastructure is not needed in the process of construction, the construction mode is simple and the approval process is easy and simple;surroundings are not destroyed by building constructing, characteristics of heat-preserving, sound insulation and safety are provided and large area constructing and popularizing are suitable.
Owner:ZHENGZHOU WOLONG AMUSEMENT EQUIP
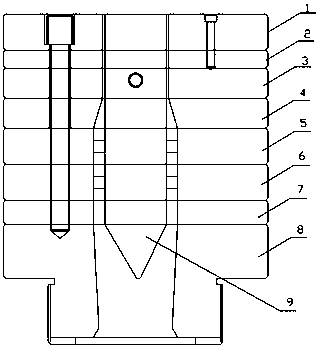
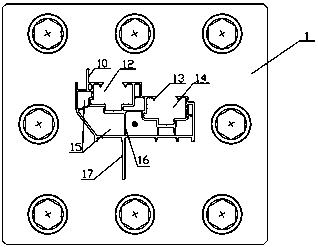
Wood-plastic window frame section bar forming mould
InactiveCN111204021ASimple structural designEasy to useDomestic articlesStructural engineeringMechanical engineering
Owner:HUANGSHI HONGDI PLASTIC MOLD
Composite Air Tank
ActiveCN112124284BSolve the defects of hidden strengthHigh strengthReservoir arrangementsFiberMechanical engineering
The invention relates to a composite material air storage cylinder. The air storage tank includes an inner tank, inserts are arranged at the ends of both sides of the inner tank, exhaust pipe joints and drain pipe joints are arranged on the inserts on both sides, internal drain pipes are connected to the drain pipe joints on both sides, and the internal The end of the drain pipe is connected to the bottom of the inner tank; the outer layer of the inner tank is provided with a fiber resin composite winding layer, and the fiber resin composite winding layer includes an axial winding layer and a radial winding layer. The present invention realizes the full coverage of the radial and axial winding of the barrel body; in addition, the drain hole and vent hole joints of the present invention are arranged on the aluminum alloy insert at the end, except that the insert itself has better strength as a metal part , The insert can also be covered by the projection of the axial winding along the axis of the cylinder body, which ensures the safety strength of both sides of the air storage cylinder.
Owner:DONGFENG COMML VEHICLE CO LTD
Small vascular bypass intra-operative auxiliary stoma forming device
PendingCN107595343AQuality assuranceGuaranteed efficiencyDiagnosticsSurgeryStomaEnd to side anastomosis
The invention provides a small vascular bypass intra-operative auxiliary stoma forming device. The traditional medical technologies for carrying out vascular end-to-side anastomosis by the aid of noninvasive sutures under microscopes are the most classic revascularization surgical technologies, but stomas are difficult to directly visualize along with diminishing of the diameters of blood vesselseven under the high-power microscopes, and the problems of vulnerability to missing suturing or mistaken suturing of vascular walls on opposite sides, blood leakage or blockage of stomas, multiplyingof difficulty of anastomosis technologies and great restriction on universal application of the anastomosis technologies can occur. The vascular bypass intra-operative auxiliary stoma forming device has the advantages that the vascular bypass intra-operative auxiliary stoma forming device is applied to small vascular bypass, two layers of vascular walls of blood vessels of a receptor can be separated from each other on the premise that damage on inner membranes of the blood vessels is not increased, the intra-operative microscopic visualization degrees can be upgraded, the purposes of optimizing suture programs, increasing the anastomosis speeds and shortening the operation time can be achieved, accordingly, the operating difficulty can be lowered, and the postoperative complication incidence rate can be reduced.
Owner:王刚
A security key management method, device and system
InactiveCN104185177BGuaranteed security strengthAdequate security protectionSecurity arrangementComputer terminalKey management
Disclosed are a method, apparatus and system for security key management. A master control base station and / or a terminal maintain / maintains two sets of base station key for the master control base station: a present base station key and a non-present base station key. The non-present base station key is the key not used by the master control base station and the terminal at present, and is derived from the present base station key or Next Hop (NH) or a prior non-present base station key. The present base station key is the key used by the master control base station and the terminal at present, and is used for deriving other control panel and / or user panel keys. There exists one and only one present base station key simultaneously.
Owner:ZTE CORP
Serial cipher realization device and its serial cipher realization method
ActiveCN106254062BFlexible deploymentImprove environmental applicabilityEncryption apparatus with shift registers/memoriesCiphertextNonlinear feedback shift register
Owner:THE PLA INFORMATION ENG UNIV
Data security system applicable to sharing encrypted file and restoring secrete key and method thereof
ActiveCN102291234BGuaranteed security strengthAddress the risk of being easily crackedKey distribution for secure communicationMultiple keys/algorithms usageKey storageSession key
The invention relates to a data security system applicable to sharing an encrypted file and recovering a secrete key and a method thereof, which are used for converting a source file into the encrypted file, wherein an administrator secrete key and a user secrete key are input through an input unit; a random secrete key is generated through a processing unit with a random derivation function according to the administrator secrete key; and a secrete key storage area is provided for storing the random secrete key and the user secrete key, which are encrypted and protected through the administrator secrete key. In the encryption process, an encryption module randomly generates a session secrete key so that the content of the source file is encrypted into encrypted data; the session secrete key is encrypted through the administrator secrete key or the user secrete key so that an encrypted session secrete key is generated; and the encrypted session secrete key and the encrypted data are packed into the encrypted file. Thereby, the encrypted file only has one encrypted session secrete key so that the safety strength of the encrypted file can be ensured. In the decryption process, the administration secrete key can be used by an administrator to decrypt the secrete key storage area, and consequently the random secrete key and the user secrete key are taken out to decrypt the encrypted file.
Owner:EGIS TECH
a helmet
ActiveCN105310162BGuaranteed security strengthTo achieve the effect of ventilationHatsHeadwear capsMassageEngineering
Owner:XICHUAN COUNTY POWER BUREAU
Liquefied natural gas cylinder for vehicles and valve protection device thereof
ActiveCN105650464AGuaranteed security strengthLow costContainer filling methodsContainer discharging methodsLiquefied natural gasProtection ring
The invention relates to a liquefied natural gas cylinder and a valve protection device thereof, in particular to a valve protection device of a liquefied natural gas cylinder for vehicles. At least one end of the air cylinder is provided with a valve. An air cylinder protection device is located at the end, with the valve, of the air cylinder. The air cylinder protection device comprises a metal protection ring, a protection ring cover plate and a hand wheel cover plate. The valve protection device is characterized in that one end of the metal protection ring is fixedly connected with a front seal of the air cylinder; the metal protection ring surrounds the valve of the air cylinder; the protection ring cover plate is detachably mounted at the other end of the metal protection ring; the protection ring cover plate shields the valve of the air cylinder; the protection ring cover plate is provided with at least one through hole; the hand wheel cover plate is rotationally mounted on the protection ring cover plate through a positioning mechanism and can shield the through hole selectively; and the positioning mechanism can position the hand wheel cover plate at any angle.
Owner:ZHANGJIAGANG CIMC SANCTUM CRYOGENIC EQUIP +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com