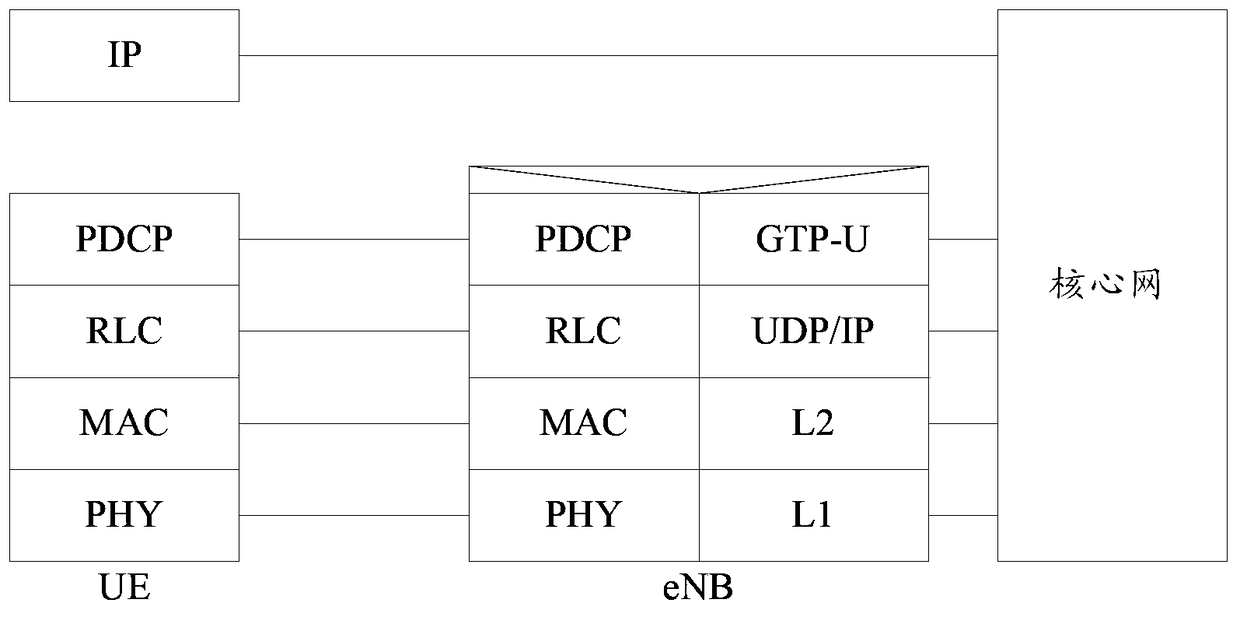
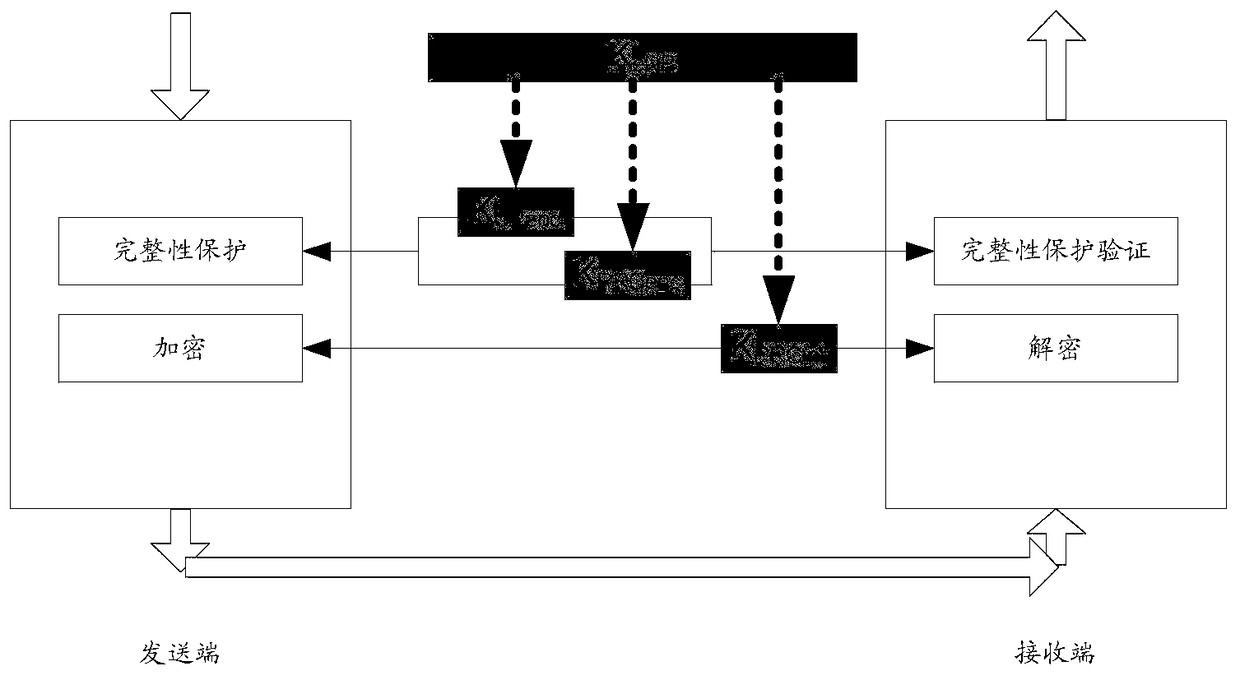
A security key management method, device and system
A security key management and key technology, applied in the field of security key management methods, devices and systems, can solve problems such as inability to support security protection mechanisms, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
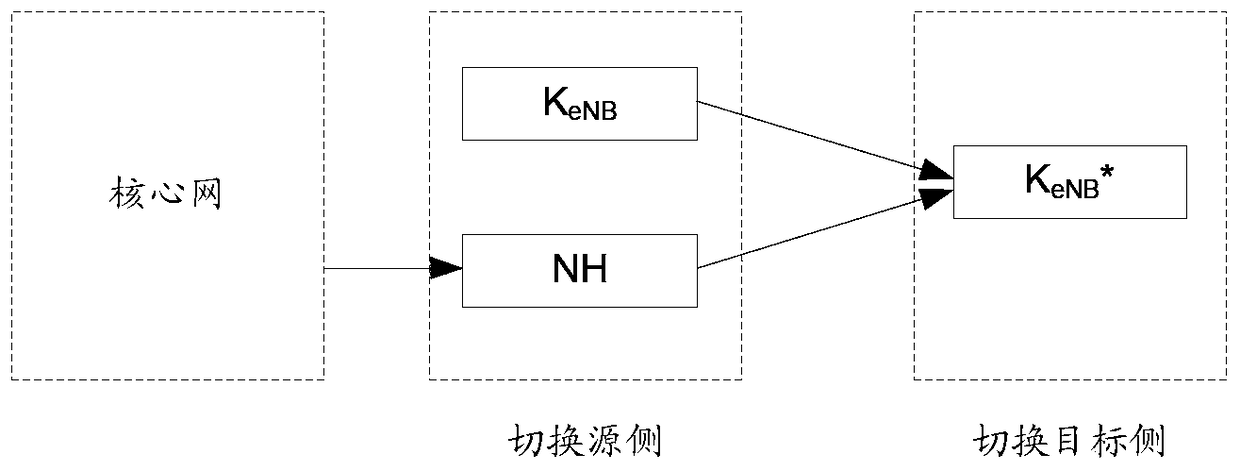
[0051] Specific embodiment one: as Figure 7 As shown, there are macro base stations (i.e. master base stations) and several micro base stations (i.e. controlled base stations) in the deployment network, where terminal 1 is in the coverage of the macro base station and the first controlled base station at the same time, and maintains double connection. In this embodiment, the key management of the terminal 1 in the master base station and the first controlled base station is taken as an example.
[0052] Terminal 1 has a security context in Macro, which includes the current master base station key KeNB. Macro base station and terminal 1 derive control plane and / or user plane keys based on KeNB to protect the information transfer between terminal 1 and macro base station.
[0053] The macro base station derives the controlled base station key KeNB* according to KeNB or NH, and transmits it to the first controlled base station. Wherein, if there is an unused NH on the macro ba...
specific Embodiment 2
[0056] Specific embodiment 2: based on the scenario of specific embodiment 1. This embodiment further takes key management when a key update occurs as an example.
[0057] During the connection process of the first controlled base station, the terminal 1 needs to update the key. The specific reason may be that the serial number of the PDCP layer will be reversed, or the network side algorithm or security requirements. Then the macro base station derives a new controlled base station key KeNB** according to the controlled base station key KeNB* of the first controlled base station, and sends the key to the first controlled base station. Correspondingly, terminal 1 also performs the same key derivation operation to obtain the same KeNB**.
[0058] The terminal 1 and the first controlled base station respectively derive control plane and / or user plane keys according to KeNB** as the base station key to protect information transfer between the terminal 1 and the first controlled ...
specific Embodiment 3
[0061] Specific embodiment three: as Figure 7 As shown, there are macro base stations (that is, master base stations) and several micro base stations (that is, controlled base stations) in the deployment network. Terminal 2 first establishes dual connections with the macro base station and the first controlled base station, and then terminal 2 moves to the second controlled base station. within the coverage of the controlled base station, and re-complete the dual connection with the macro base station and the second controlled base station. This embodiment takes the key management of the terminal 2 in the master base station and the second controlled base station as an example.
[0062] Terminal 2 has a security context in the macro base station, which includes the current master base station key KeNB, and is used to protect the information transfer between terminal 2 and the macro base station according to the control plane and / or user plane keys derived from KeNB.
[0063]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com