Communication method and system based on quantum Ukey
A communication method and quantum technology, applied in the field of communication, can solve the problems of insecure authentication and encryption algorithms, insufficient strength of user passwords, and difficulties in key distribution and management, so as to achieve rich applications and development, wide protection range, and enhanced security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
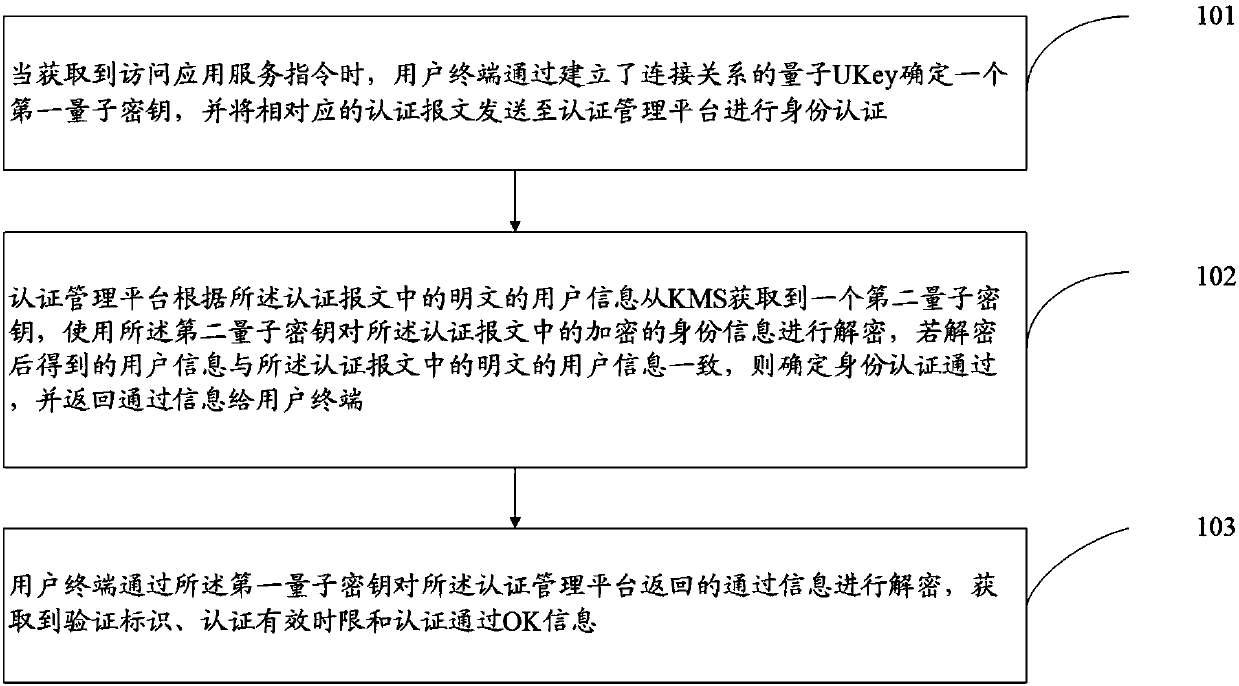
[0045] See figure 1 , The first embodiment of the present invention provides a schematic flow chart of a quantum UKey-based communication method, the method specifically includes the following steps:
[0046] 101. When an instruction to access the application service is obtained, the user terminal determines a first quantum key through the quantum UKey that has established the connection relationship, and sends a corresponding authentication message to the authentication management platform for identity authentication, the authentication report The text includes user information in plain text and identity information encrypted using the first quantum key, and the identity information includes user information in the plain text and a time stamp;
[0047] In this embodiment, in order to improve the security of the user when accessing the application server, first, when the instruction to access the application service is obtained, the user terminal determines a first quantum key throu...
Embodiment 2
[0063] See figure 2 , The second embodiment of the present invention provides a schematic flow chart of a quantum UKey-based communication method, which specifically includes the following steps:
[0064] 201. When an instruction to access an application service is obtained, the user terminal determines a first quantum key through the quantum UKey that has established a connection relationship, and sends a corresponding authentication message to the authentication management platform for identity authentication, the authentication report The text includes user information in plain text and identity information encrypted using the first quantum key, and the identity information includes user information in the plain text and a time stamp;
[0065] 202. The authentication management platform obtains a second quantum key from KMS according to the user information in the plain text in the authentication message, and uses the second quantum key to decrypt the encrypted identity informat...
Embodiment 3
[0081] See image 3 , The third embodiment of the present invention provides a schematic flow diagram of a quantum UKey-based communication method, which specifically includes the following steps:
[0082] 301. When an instruction to access an application service is obtained, the user terminal determines a first quantum key through the quantum UKey that has established a connection relationship, and sends a corresponding authentication message to the authentication management platform for identity authentication, the authentication report The text includes user information in plain text and identity information encrypted using the first quantum key, and the identity information includes user information in the plain text and a time stamp;
[0083] 302. The authentication management platform obtains a second quantum key from KMS according to the user information in the plain text in the authentication message, and uses the second quantum key to decrypt the encrypted identity informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com