Stream ciphering technique
A technology of key stream and data stream, which is applied in encryption devices with shift registers/memory, digital transmission systems, electrical components, etc., and can solve problems such as bottlenecks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
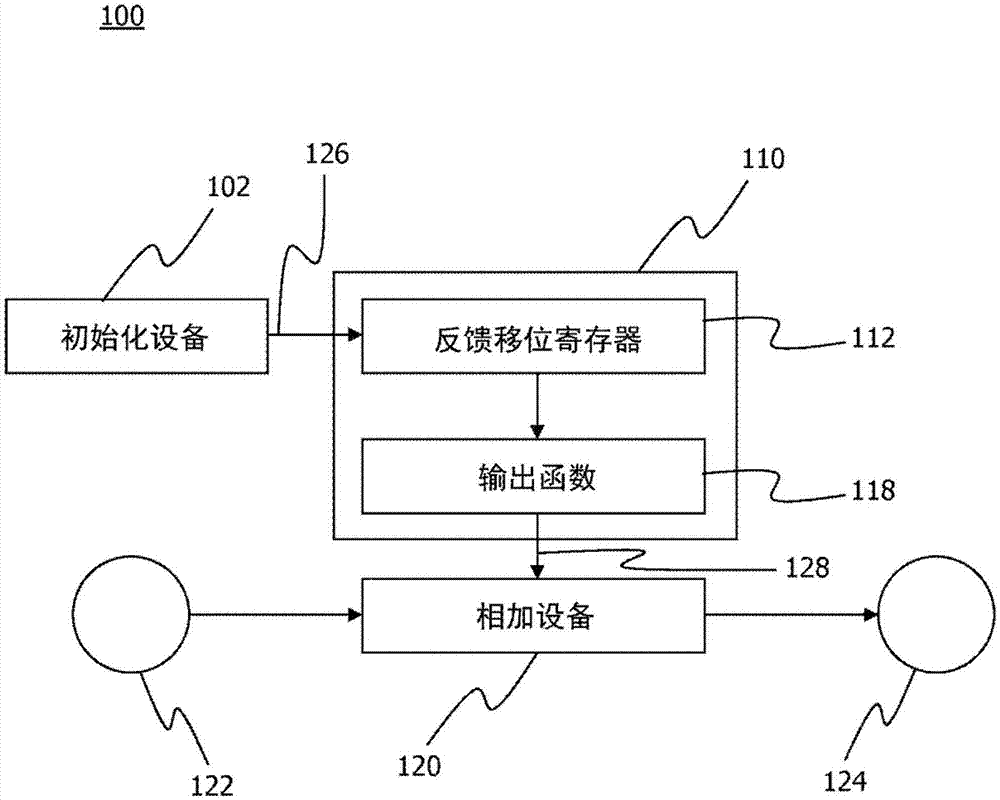
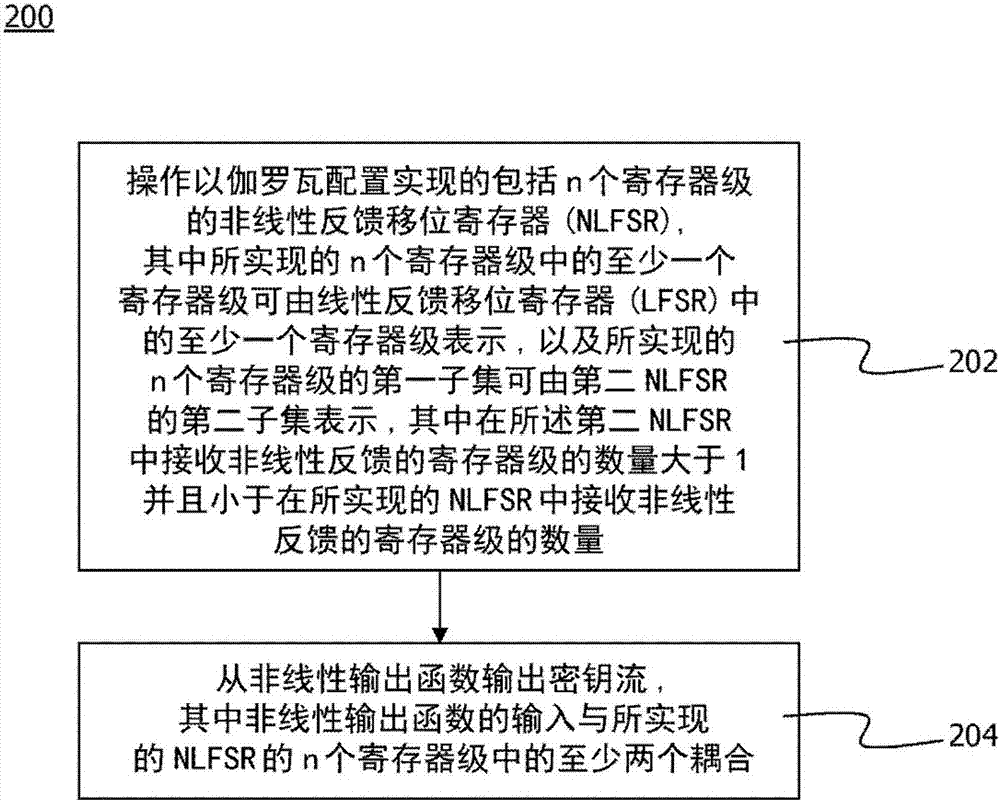
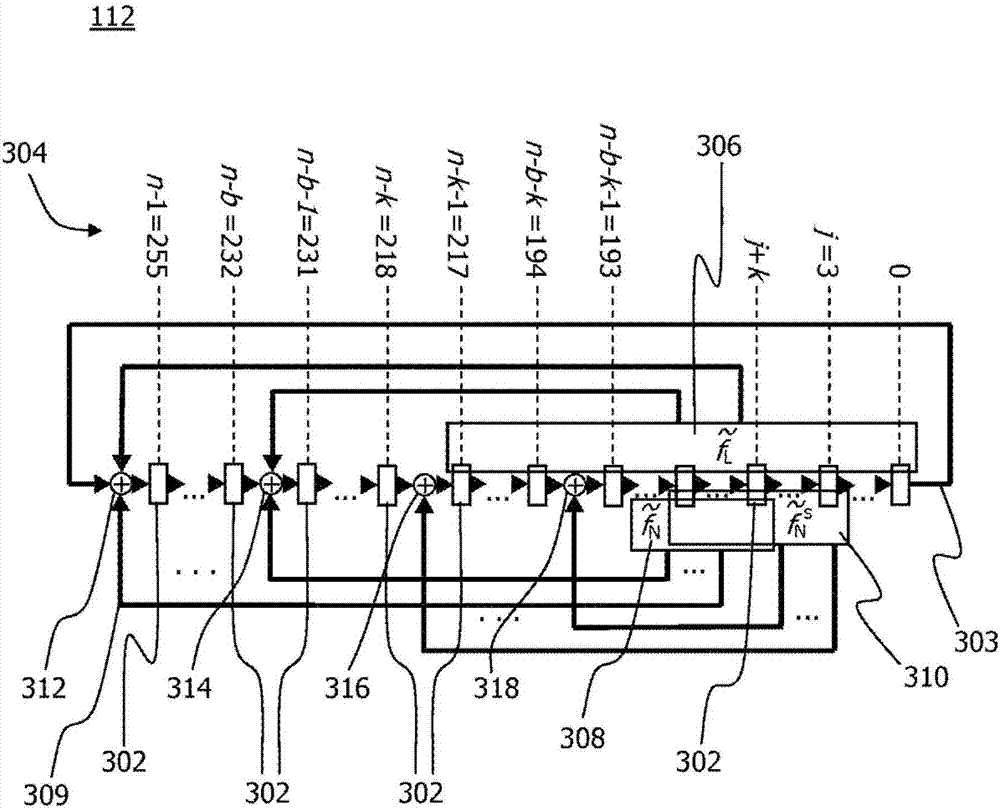
[0045] In the following description, for purposes of explanation and not limitation, specific details are set forth (eg, specific device contexts) in order to provide a thorough understanding of the technology disclosed herein. It will be apparent, however, to one skilled in the art that the technology may be practiced in other embodiments that depart from these specific details. Furthermore, although the following embodiments are described primarily with respect to wireless communication networks such as the successors of Long Term Evolution (LTE), it will be apparent that the techniques described herein may also be used in networks including 3rd Generation Partnership Project (3GPP) networks, non- Implemented in 3GPP networks (eg according to the IEEE 802.3 or IEEE 802.11 series of standards) and other mobile and fixed communication networks, wireless or wireline, and combinations thereof. Furthermore, the described techniques can be implemented at one or more layers of a pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com