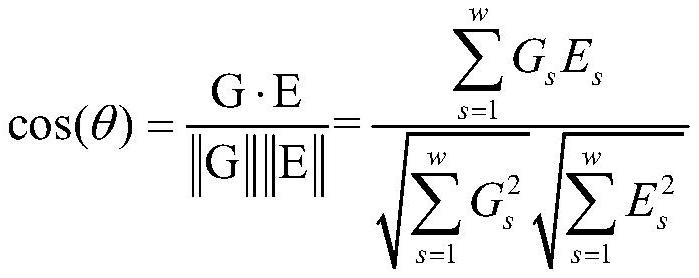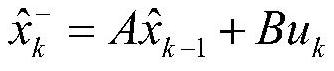Patents
Literature
61results about How to "Small memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
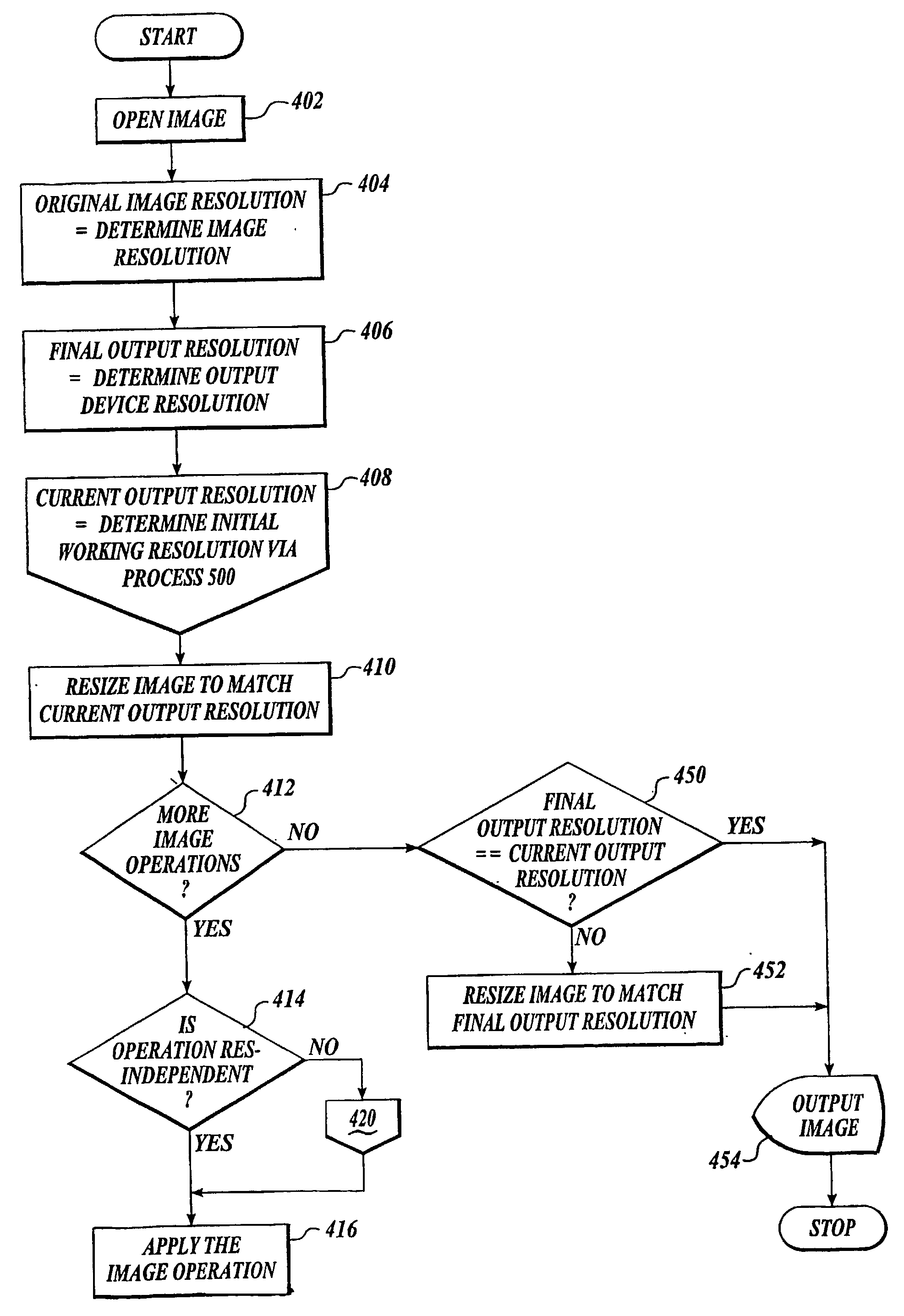
Techniques for resolution independent rendering of images
InactiveUS20040027593A1Low-processing powerSmall memoryDigitally marking record carriersGeometric image transformationPerformance improvementImage resolution
A method to improve the performance of rendering image data (402) by converting what would normally be considered resolution-dependent image behavior into behavior that is substantially resolution-independent. This allows significant performance improvement since the rendering (454) can be performed on the lower-resolution image data used, for example, for on-screen viewing and when the image effect is applied to a higher resolution rendering, the effect, as viewed, is substantially the same as the effect viewed at a lower resolution. This conversion of normally resolution-dependent behaviors into pseudo-resolution-independent behaviors also allows the image effects to be applied to be carried out on a lower resolution image with confidence that when the image is rendered at a higher resolution that the image effects applied will substantially have the same appearance that the effect had at the lower resolution.
Owner:EASTMAN KODAK CO
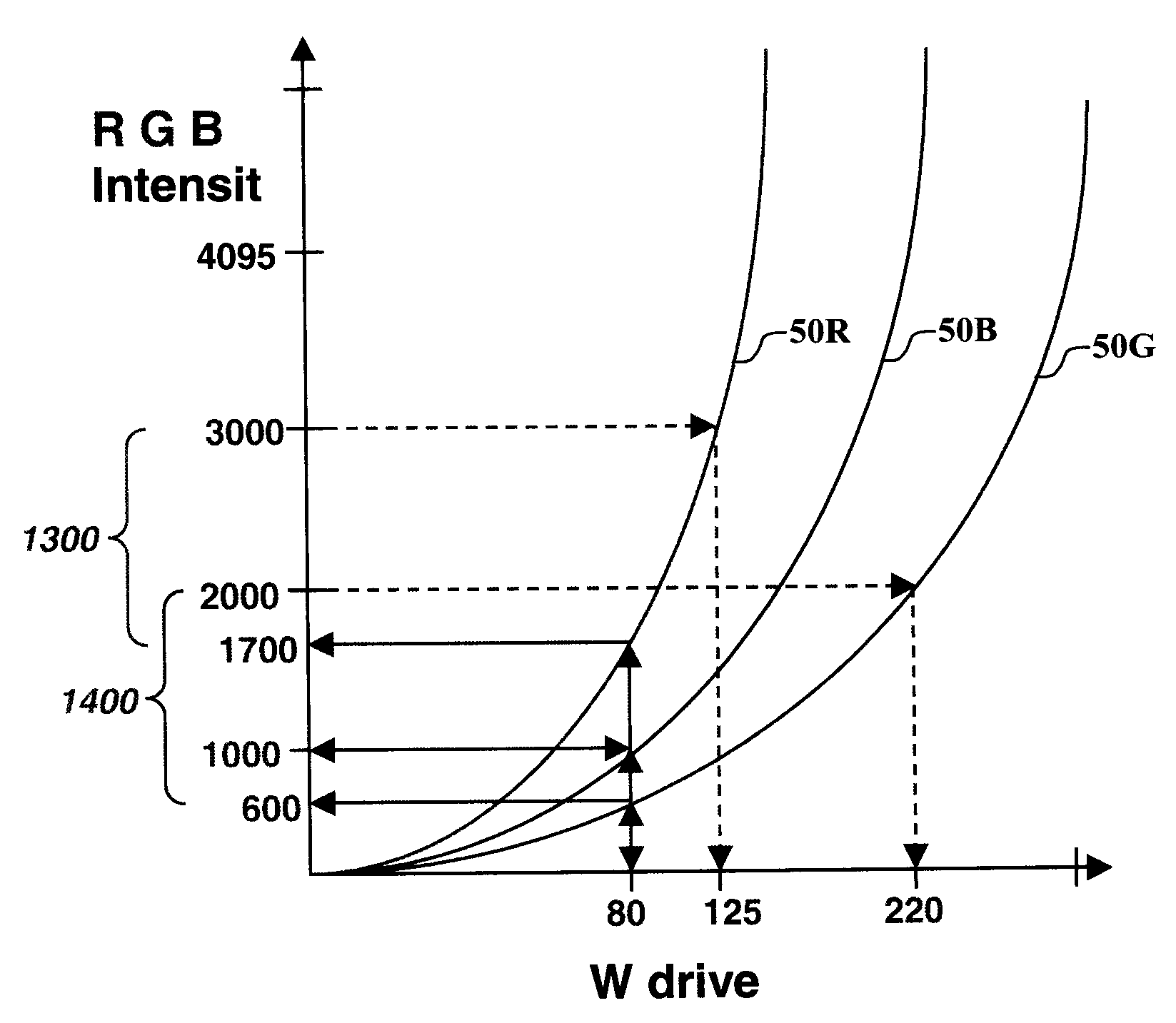
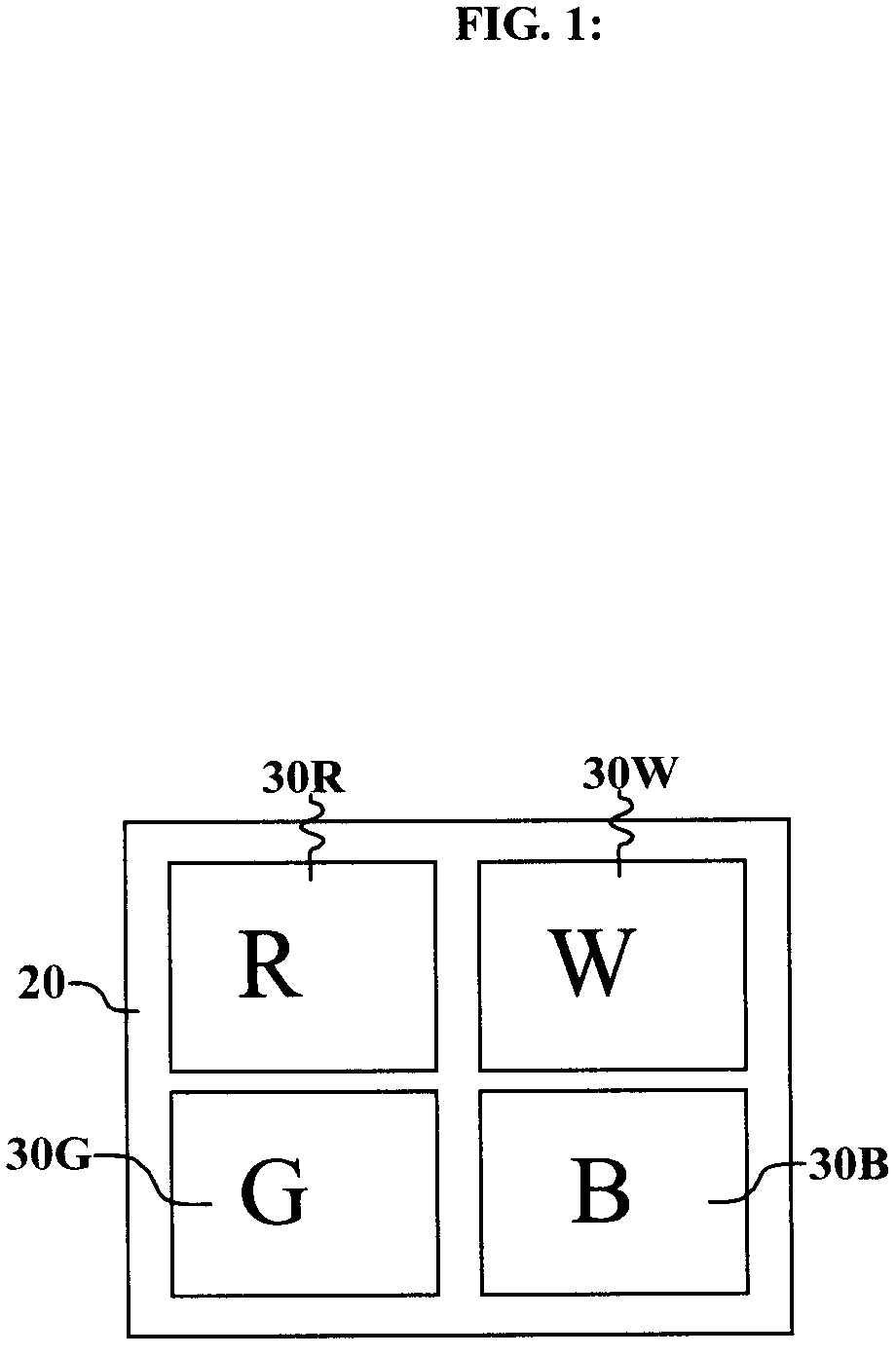
Method for input-signal transformation for rgbw displays with variable w color
InactiveUS20080252797A1Easy to measureSmall memoryColor signal processing circuitsStatic indicating devicesGamutDisplay device
A method for transforming three color-input signals (R, G, B) corresponding to three gamut-defining color primaries of a display to four color-output signals (R′, G′, B′, W) corresponding to the gamut-defining color primaries and one additional primary of the display, where the additional primary has color that varies with drive level, comprising: a) determining a relationship between drive level of the additional primary and intensities of the three gamut-defining primaries which together produce equivalent color over a range of drive levels for the additional primary; and b) employing the three color-input signals R, G, B and the relationship defined in a) to determine a value for W of the four color-output signals, and modification values to be applied to one or more of the R, G, B components of the three color-input signals to form the R′, G′, B′ values of the four color-output signals.
Owner:GLOBAL OLED TECH
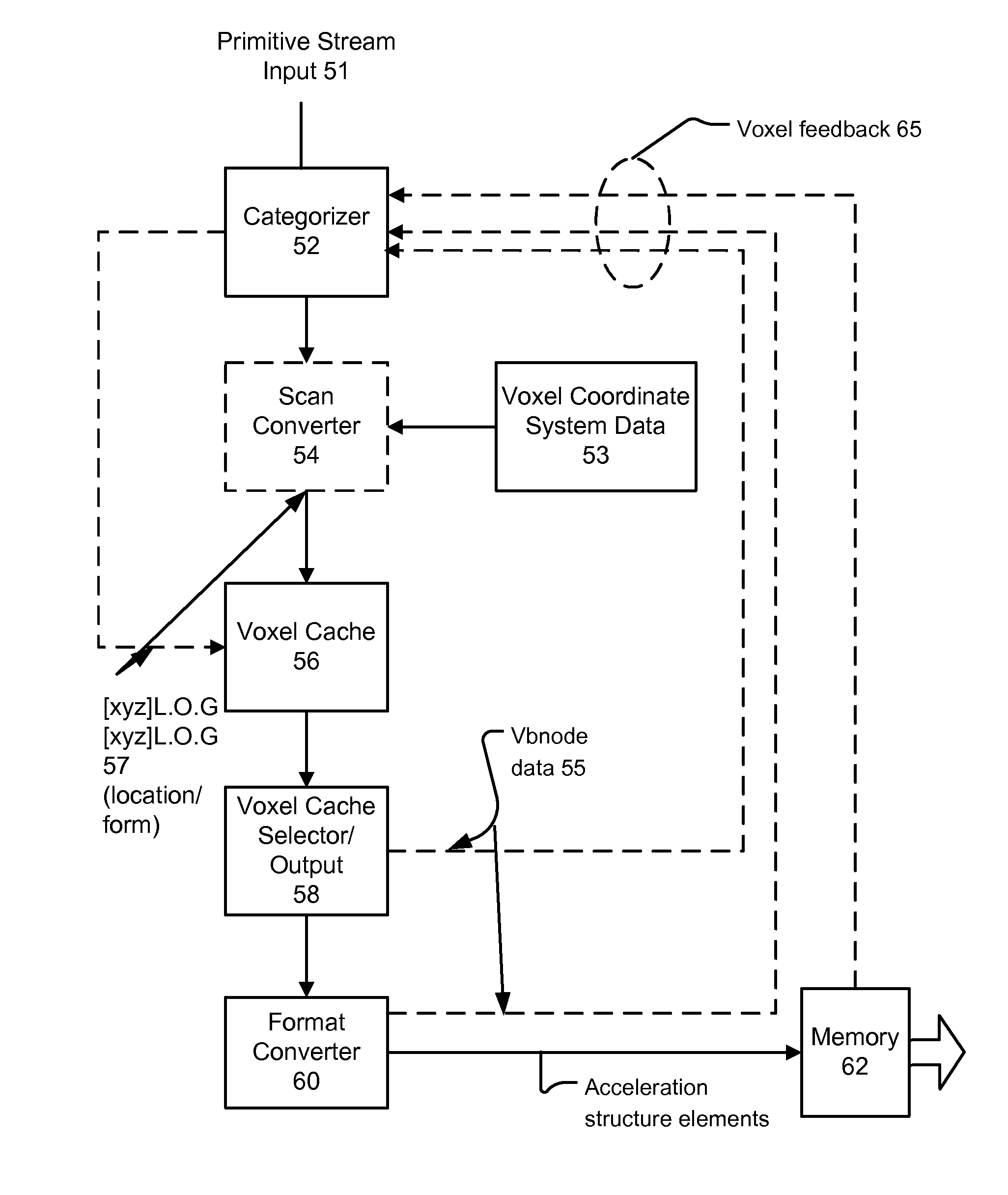
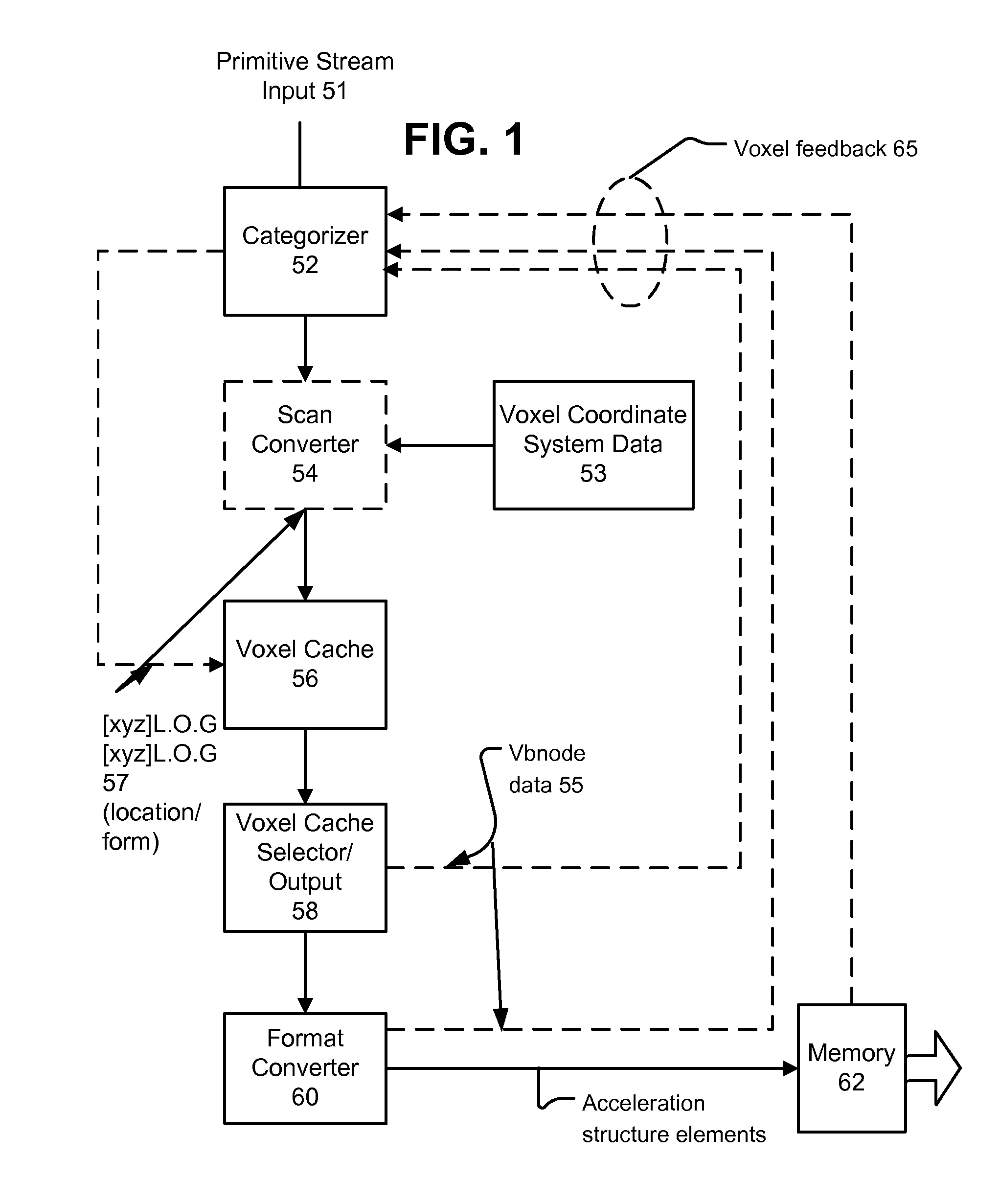
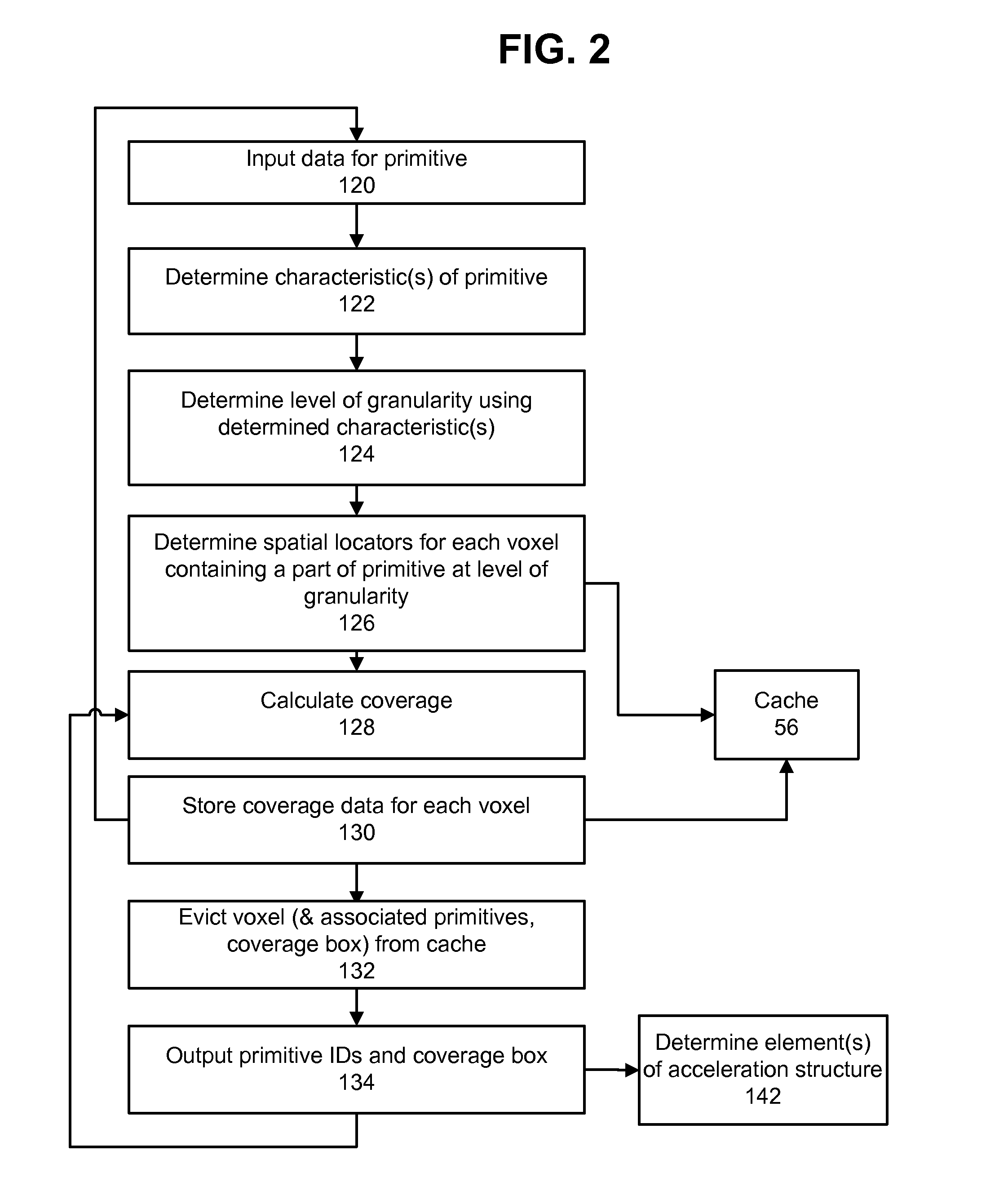
Systems and methods for 3-d scene acceleration structure creation and updating
ActiveUS20130113800A1High bandwidth linkImplemented cost-effectivelyImage generation3D-image renderingParallel computingCache locality
Systems and methods for producing an acceleration structure provide for subdividing a 3-D scene into a plurality of volumetric portions, which have different sizes, each being addressable using a multipart address indicating a location and a relative size of each volumetric portion. A stream of primitives is processed by characterizing each according to one or more criteria, selecting a relative size of volumetric portions for use in bounding the primitive, and finding a set of volumetric portions of that relative size which bound the primitive. A primitive ID is stored in each location of a cache associated with each volumetric portion of the set of volumetric portions. A cache location is selected for eviction, responsive to each cache eviction decision made during the processing. An element of an acceleration structure according to the contents of the evicted cache location is generated, responsive to the evicted cache location.
Owner:IMAGINATION TECH LTD
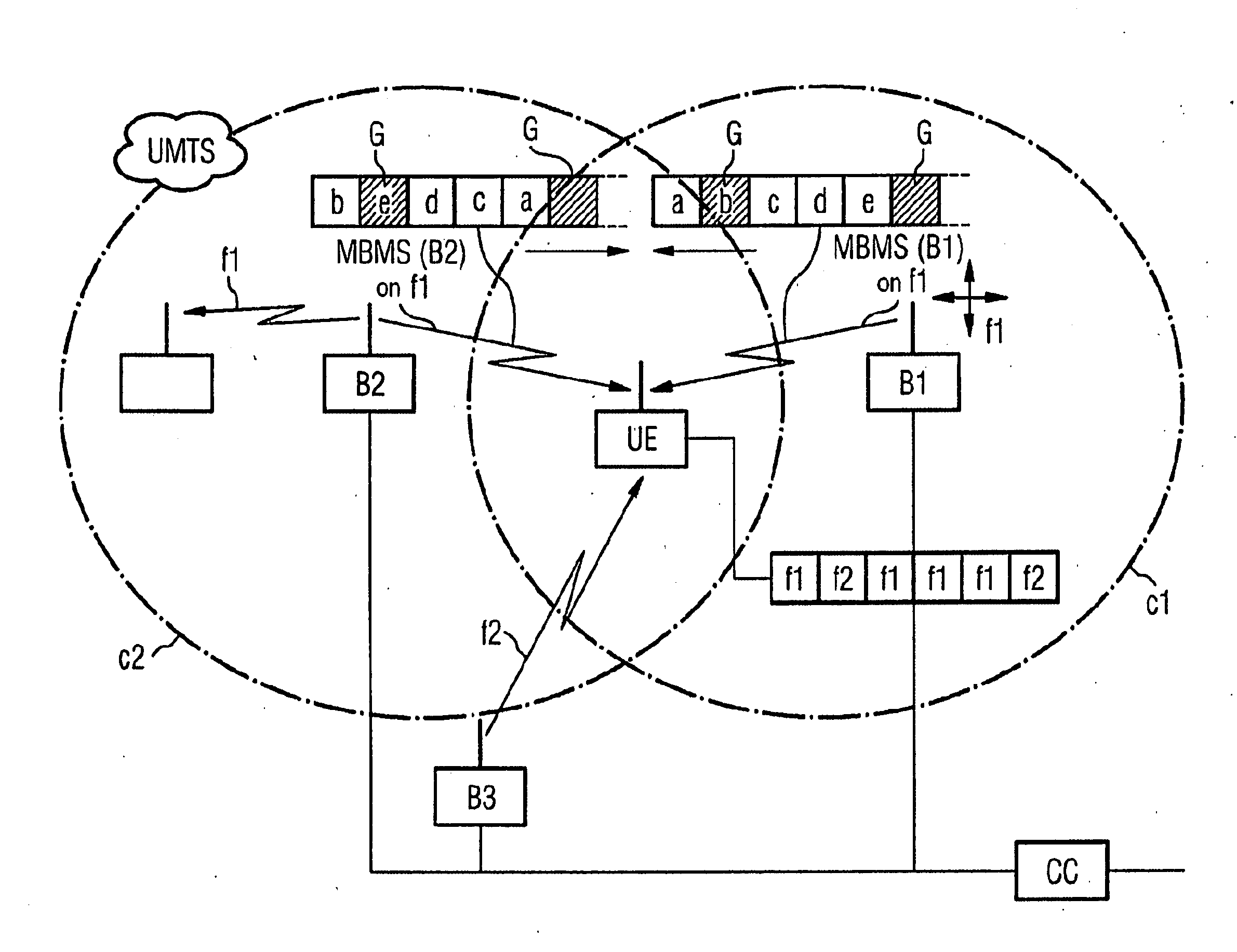
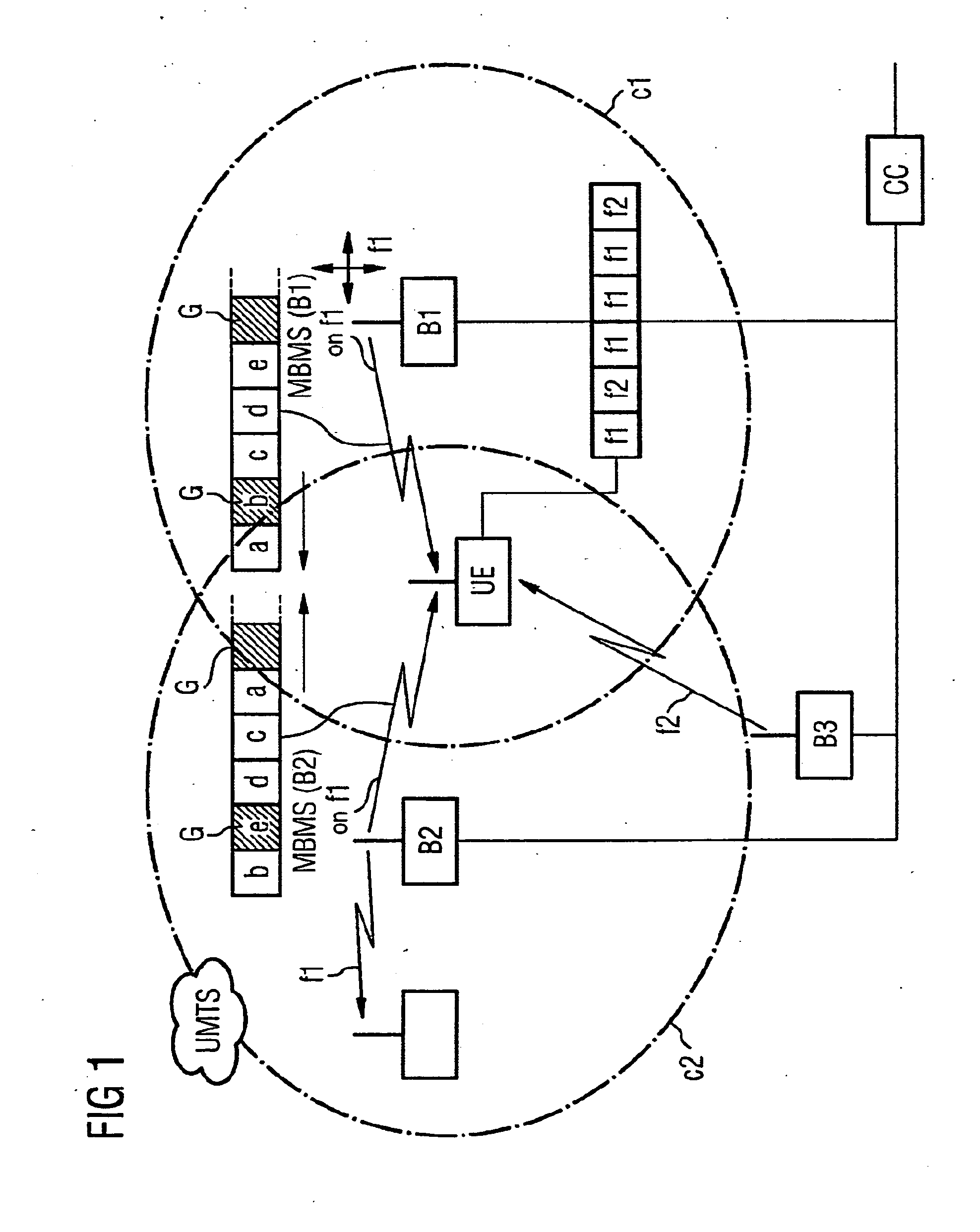
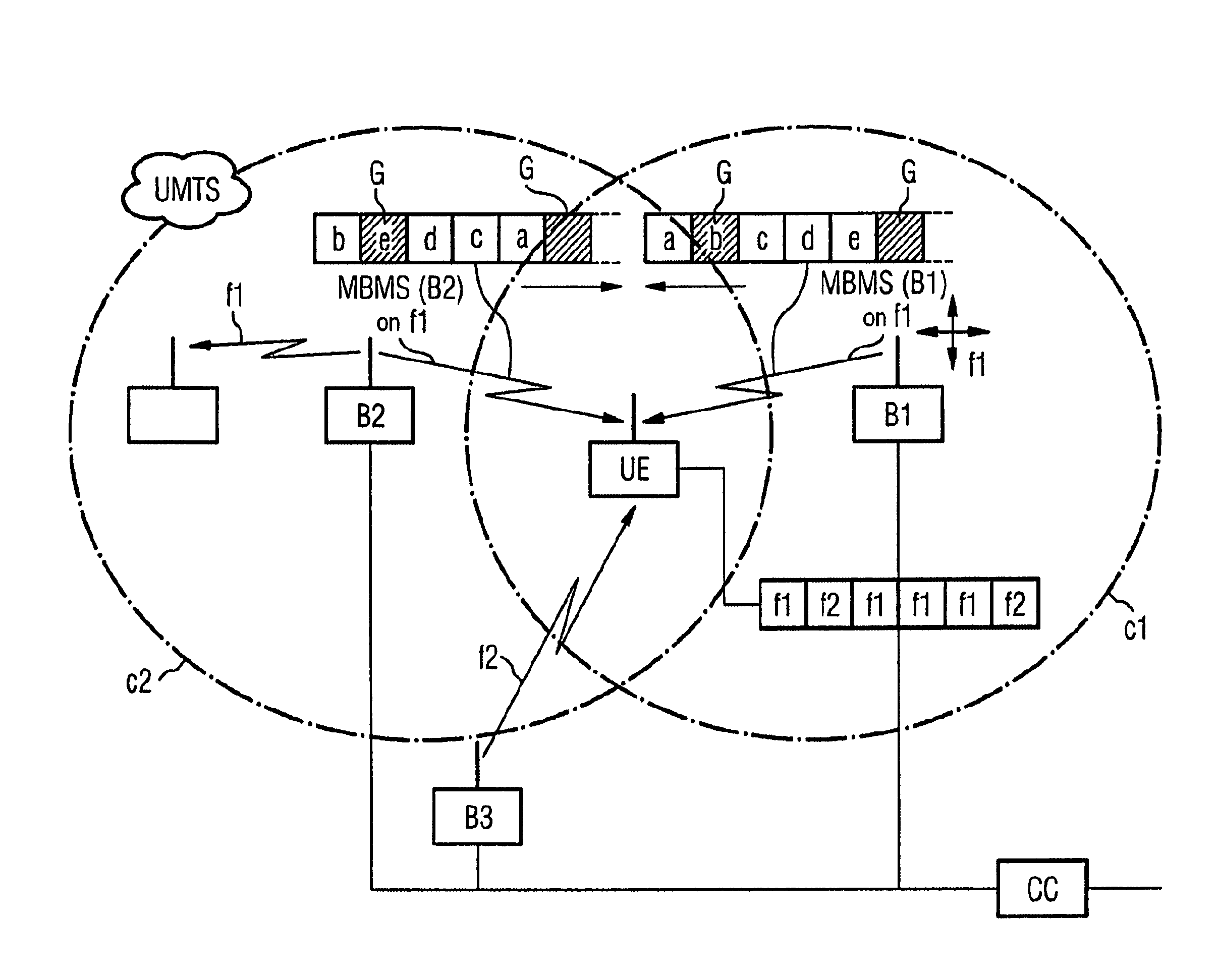
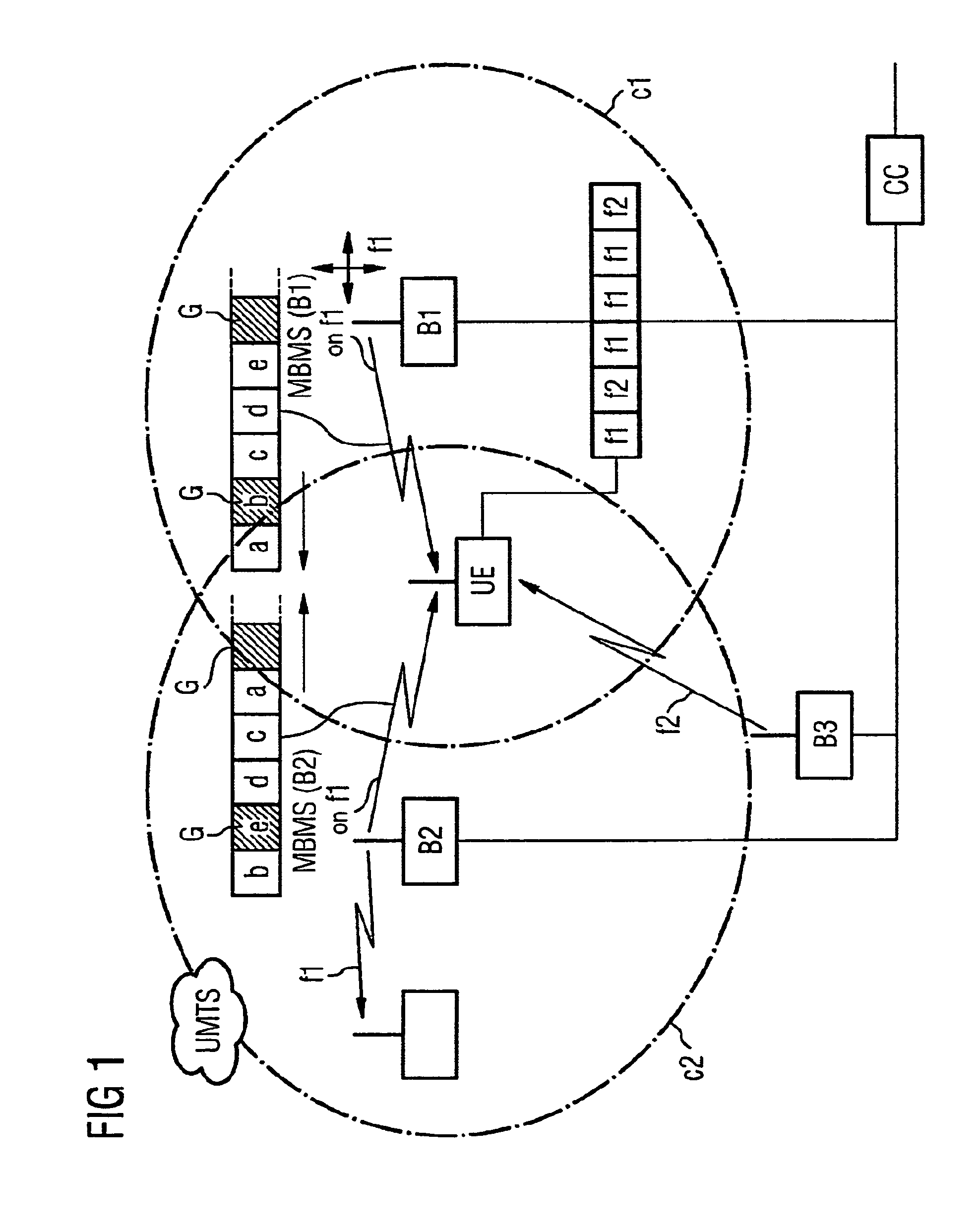
Method for Receiving Data Sent in a Sequence in a Mobile Radio System with Reception Gaps
ActiveUS20070218835A1Simplifying reorderingAvoid spreadingSite diversityNetwork traffic/resource managementMobile Telephone ServiceResource element
Methods for receiving data sent by a first emitter of a mobile telephony system to a first resource element of a resource, via a receiver, radiopockets being created during the reception, and data which is not received during the creation of the radiopockets being reconstructed by the receiver are provided. The data which is not received by the first emitter is received by a second emitter, in a temporarally offset manner, on the same resource element of the resource, between the radiopockets, and is used to reconstruct the sequence of data. A conversion is especially advantageous for carrying out a receiving method in UMTS compression mode during the reception of data which is sent continuously independently of the compression mode.
Owner:SIEMENS AG
Equalization based on digital signal processing in downsampled domains
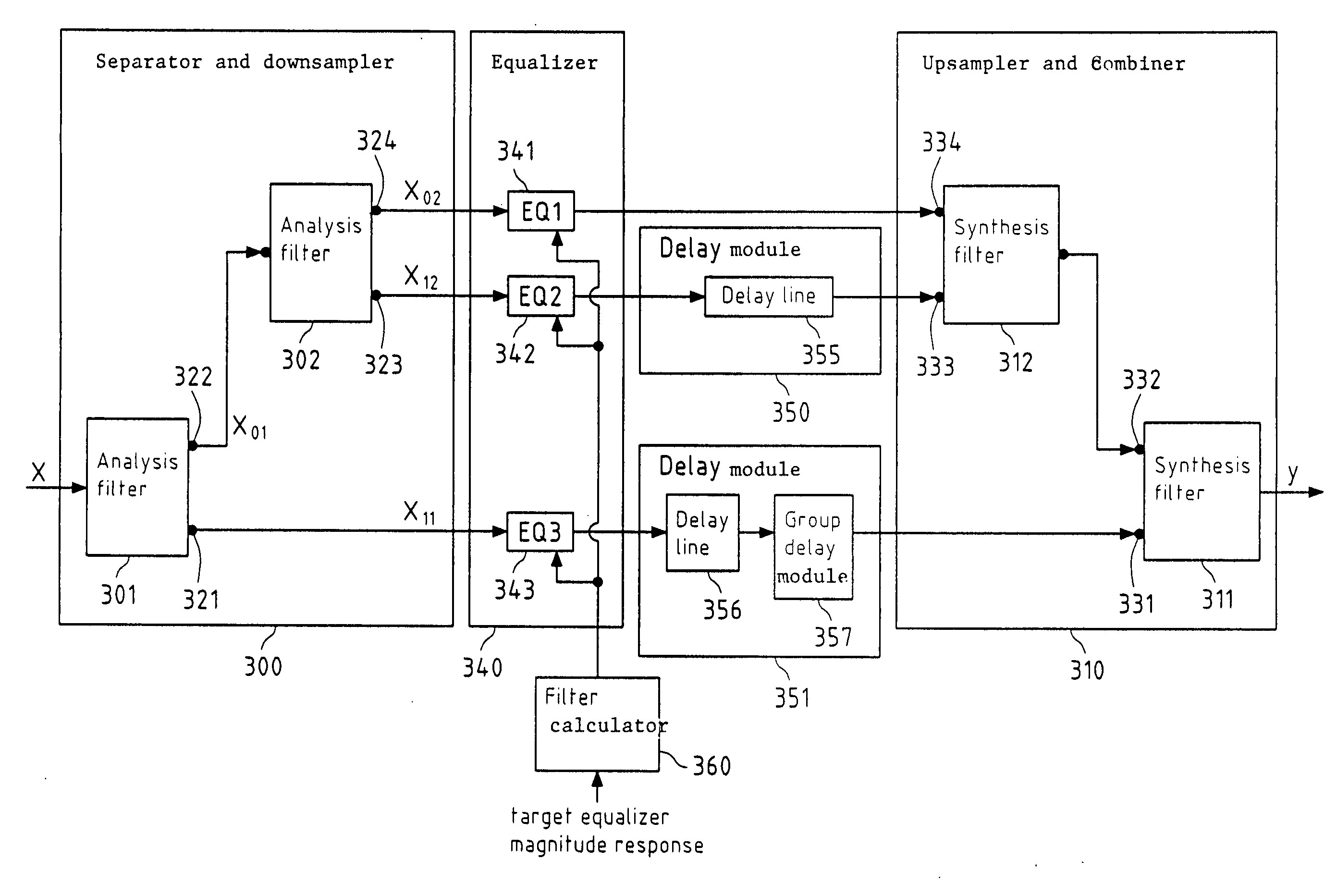
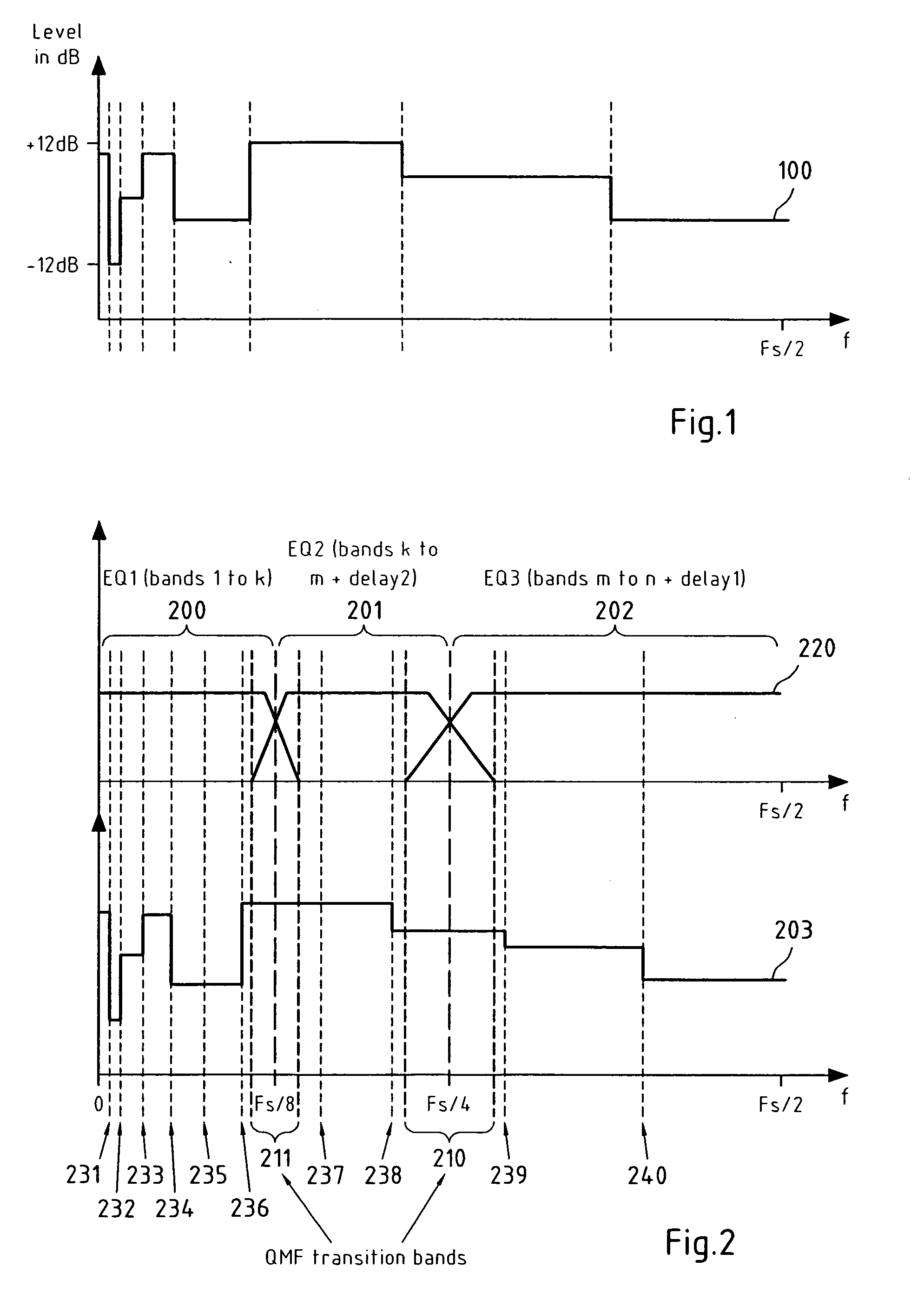
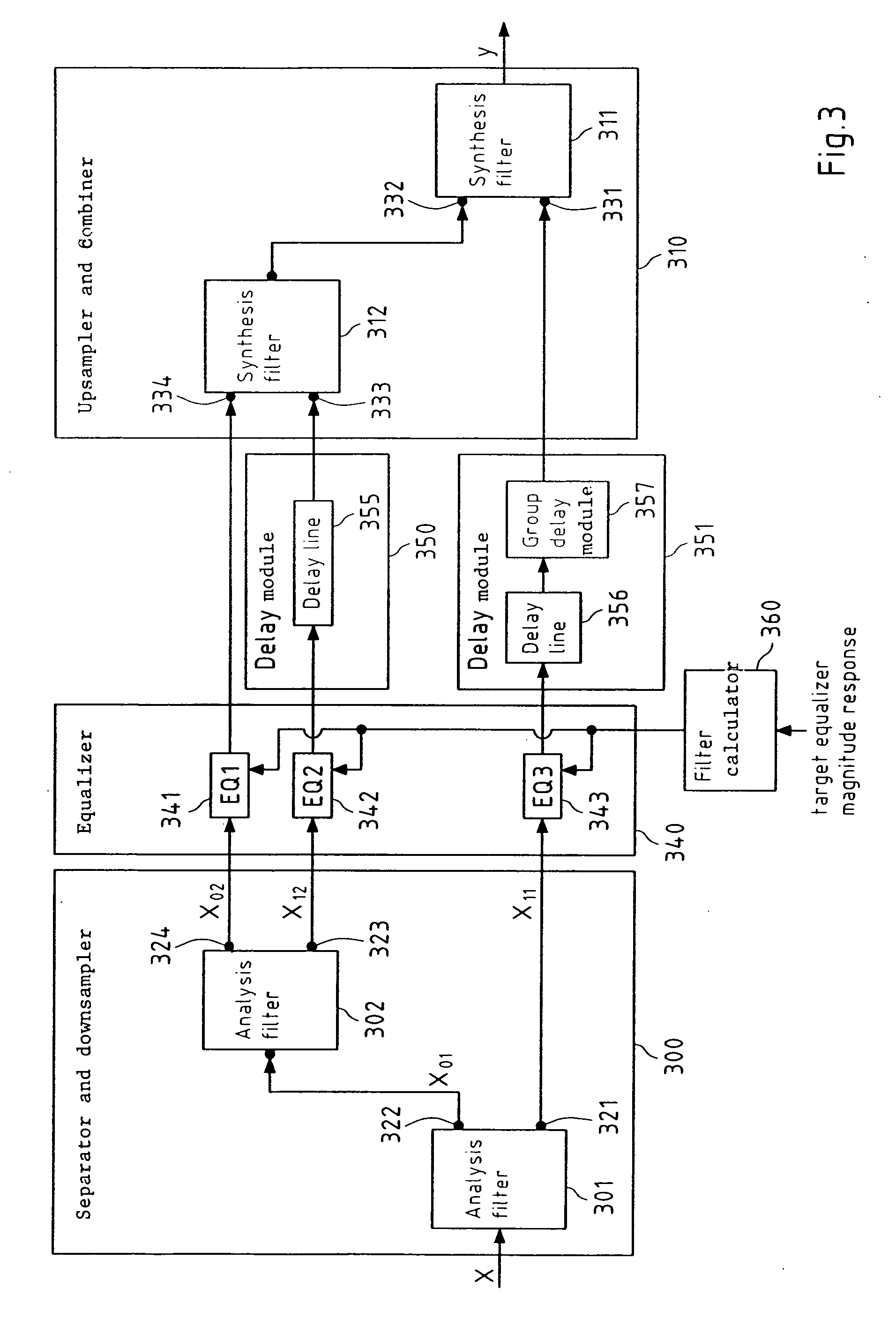
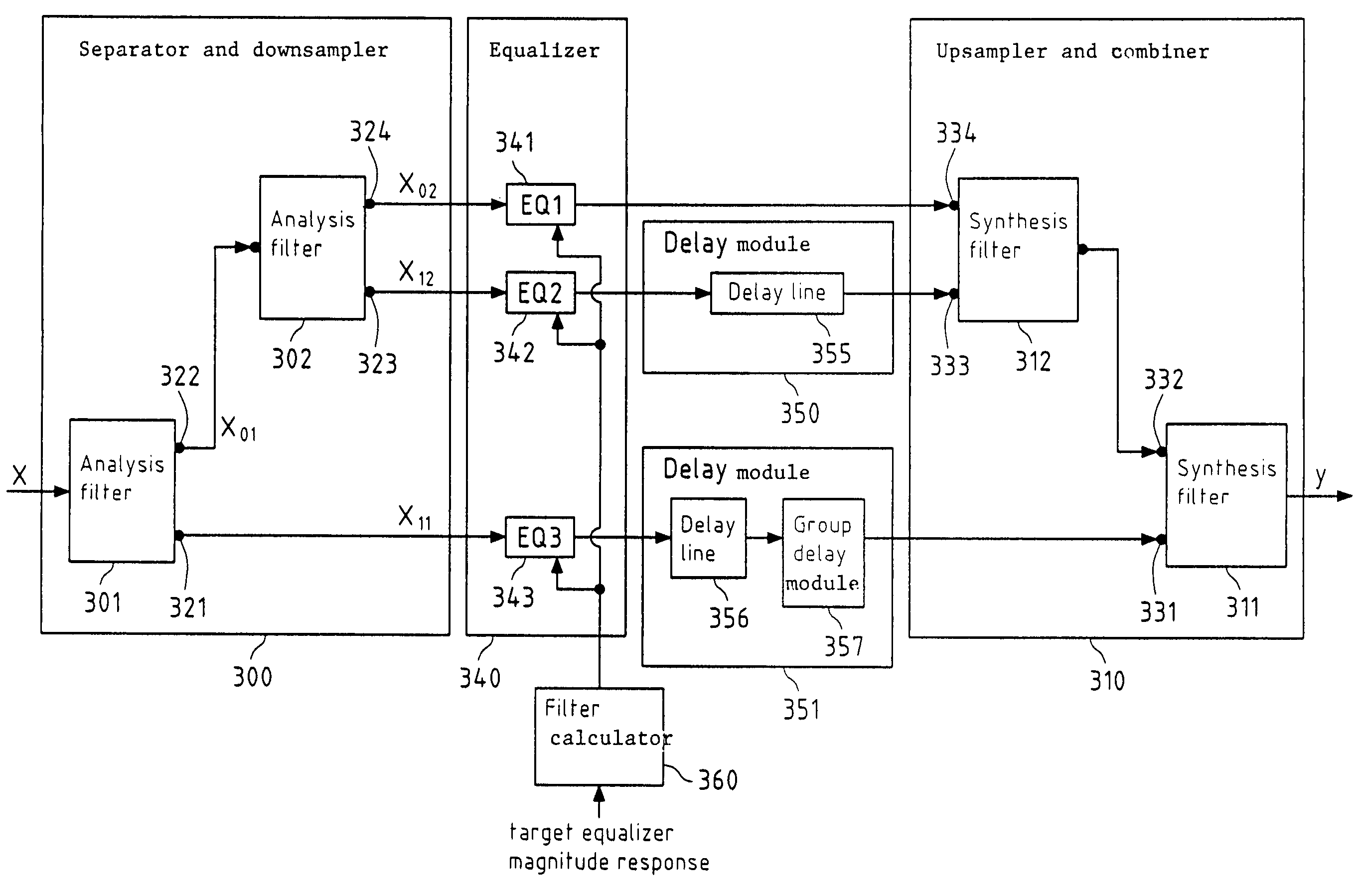
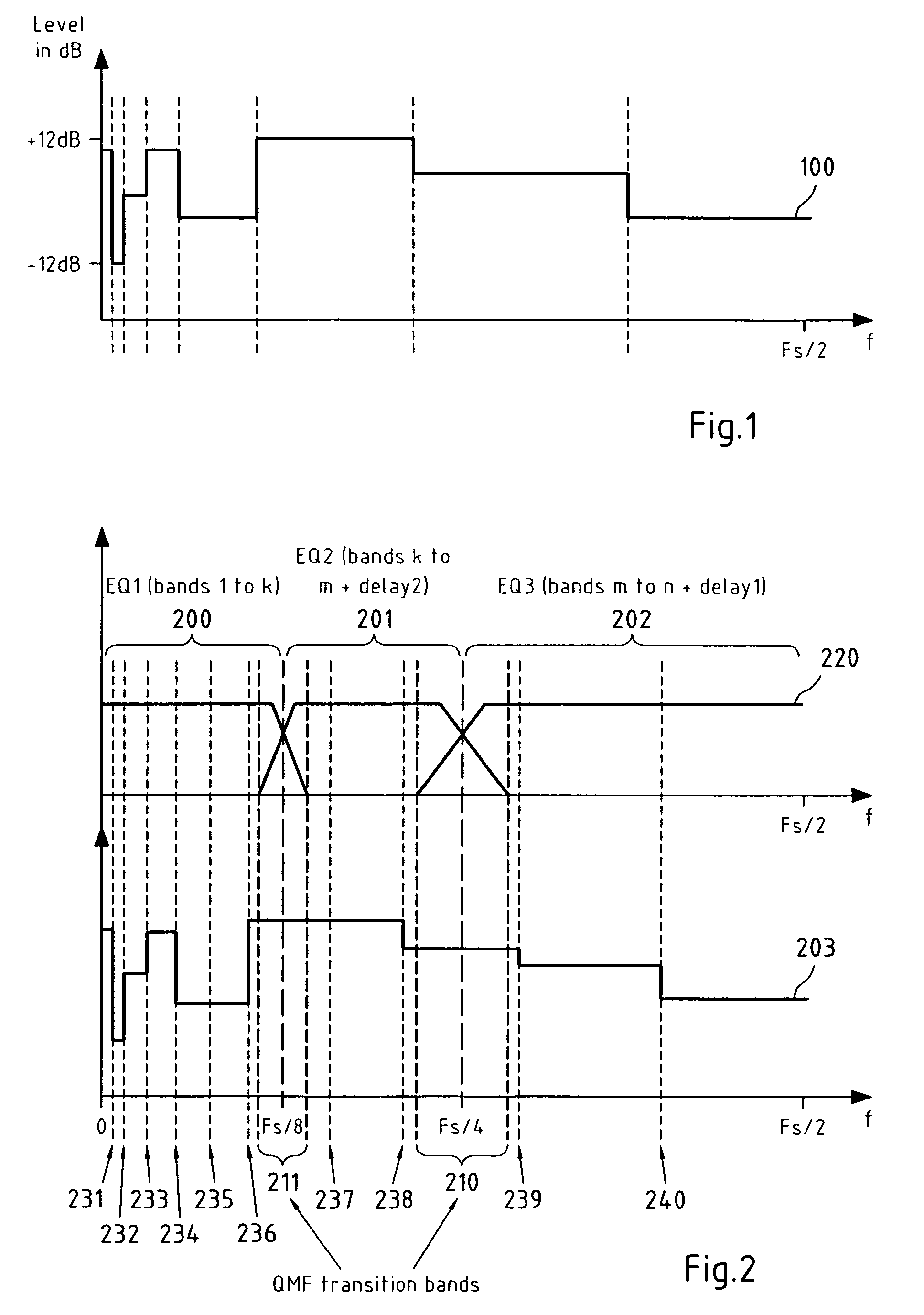
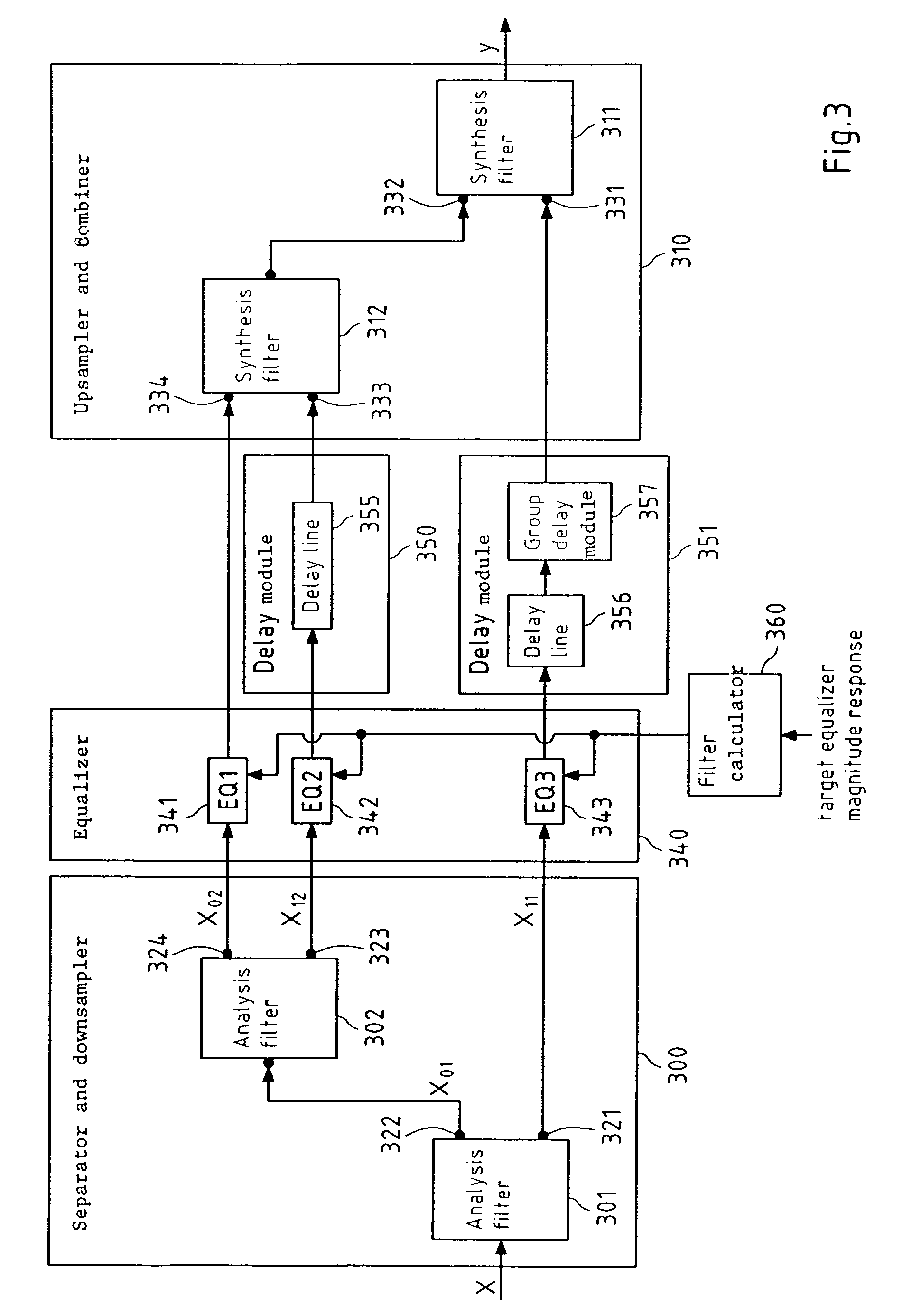
InactiveUS20070288235A1Reduce complexitySmall memorySpeech analysisTwo-channel systemsDigital signal processingEqualization
This invention relates to a device, a method, a software application program, a software application program product and an audio device for processing a digital signal, wherein the digital signal is separated and downsampled into at least two downsampled subband signals, wherein at least one of the at least two downsampled subband signals is equalized, and wherein the at least two downsampled subband signals are upsampled and combined into a digital output signal.
Owner:RPX CORP
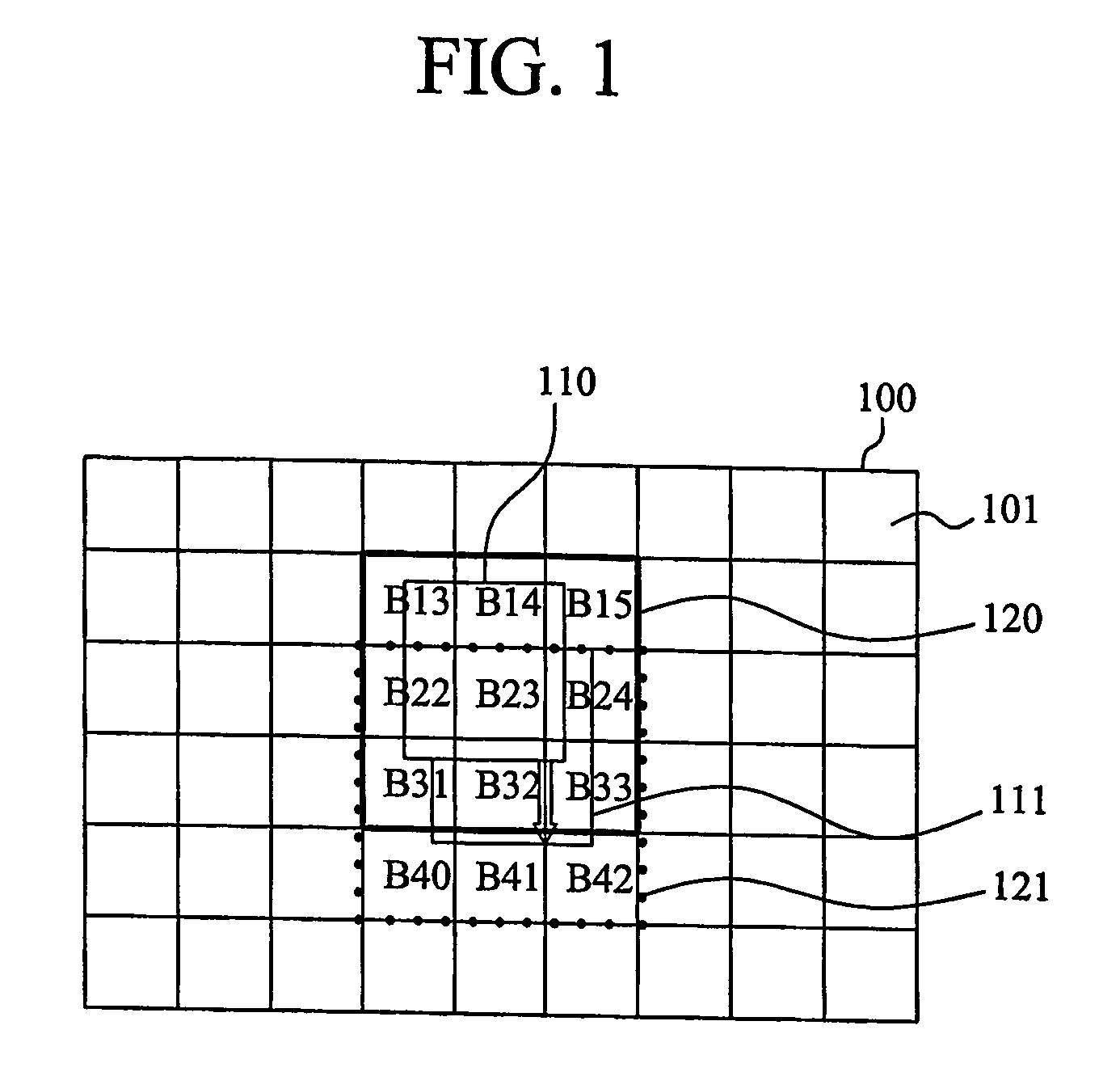
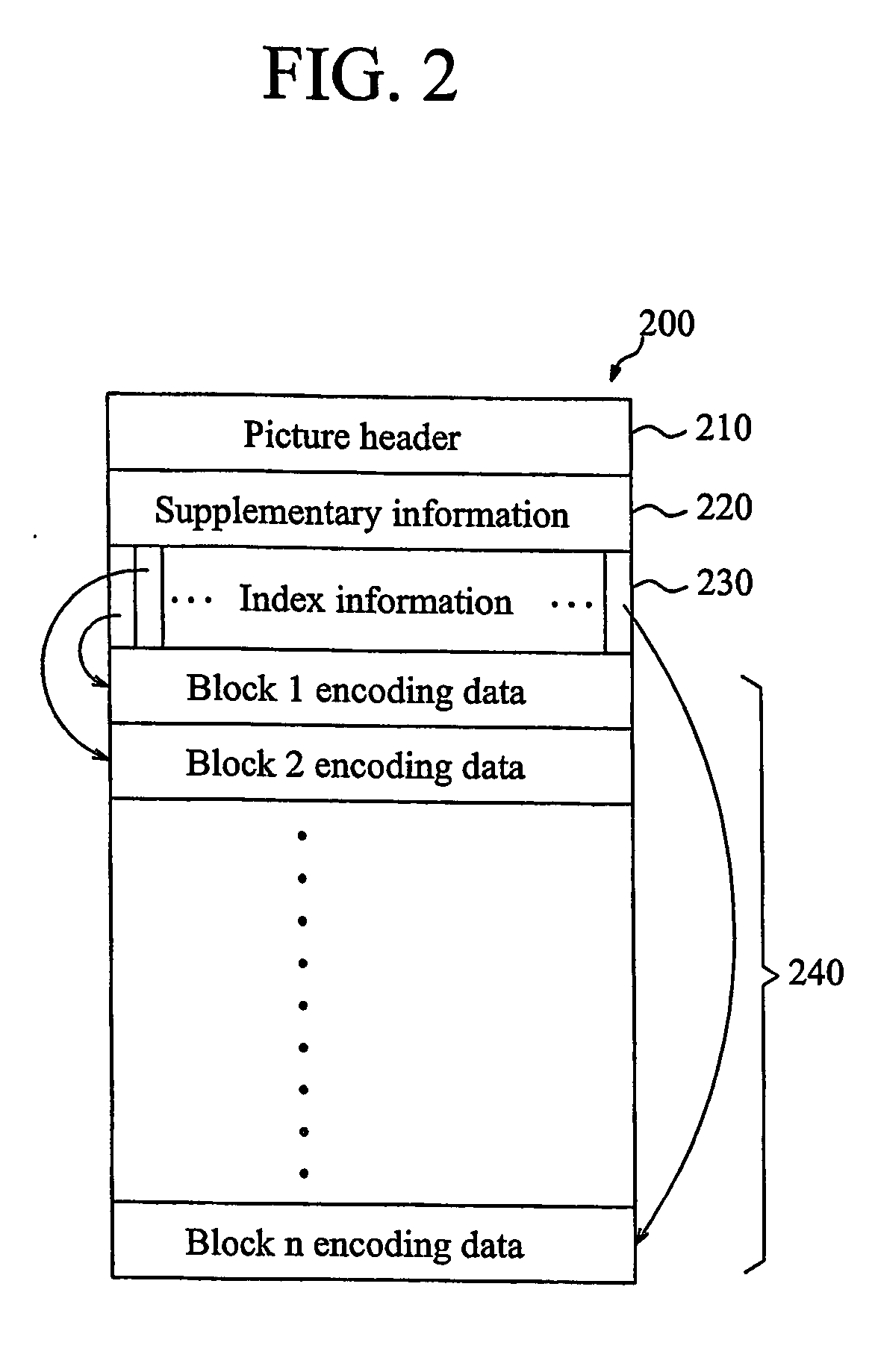
Method for displaying high resolution picture in mobile communication terminal, mobile communication terminal and system for converting picture file format therefor
ActiveUS20070046698A1High resolutionIncrease speedTelevision system detailsDigital data information retrievalComputer graphics (images)Data conversion
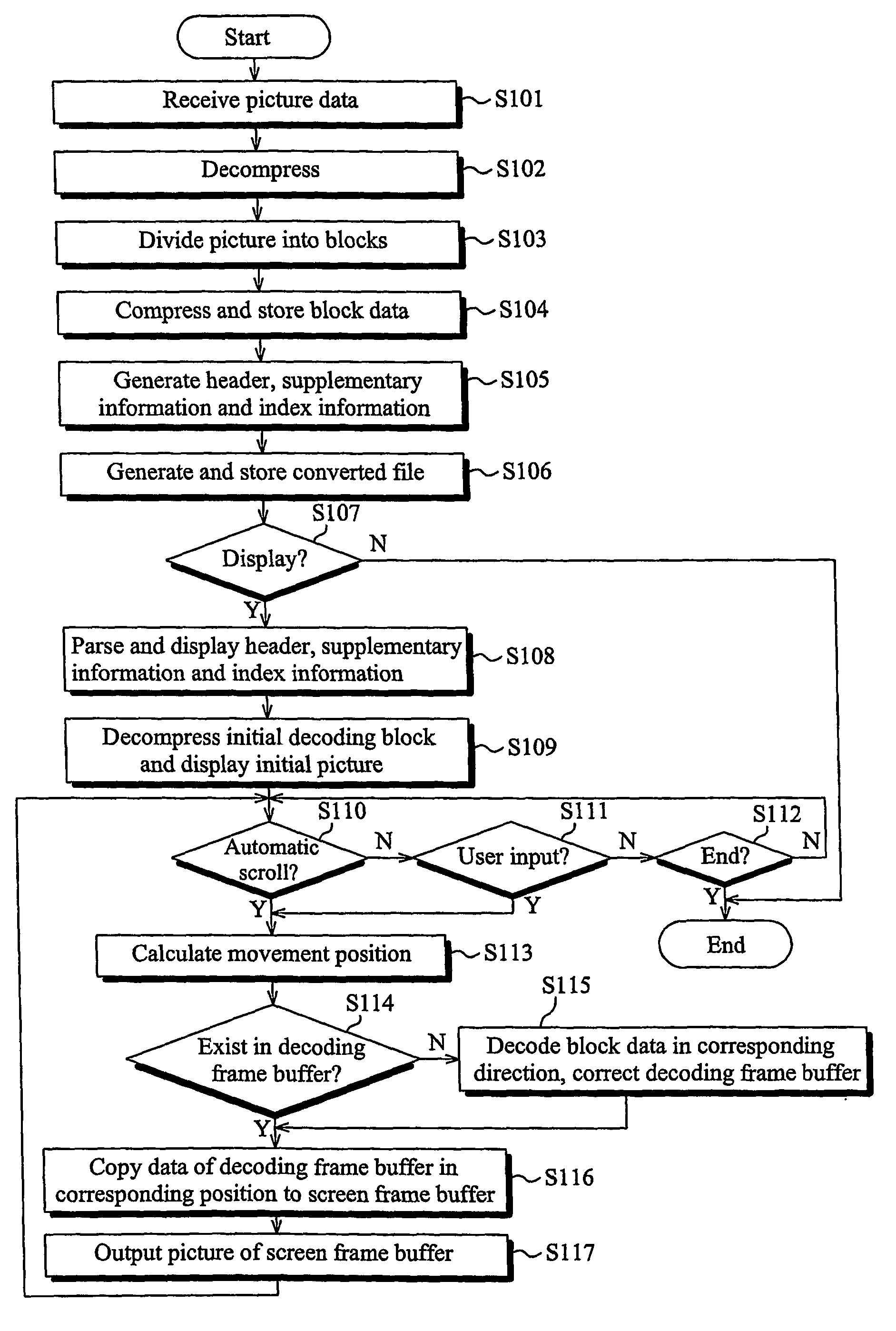
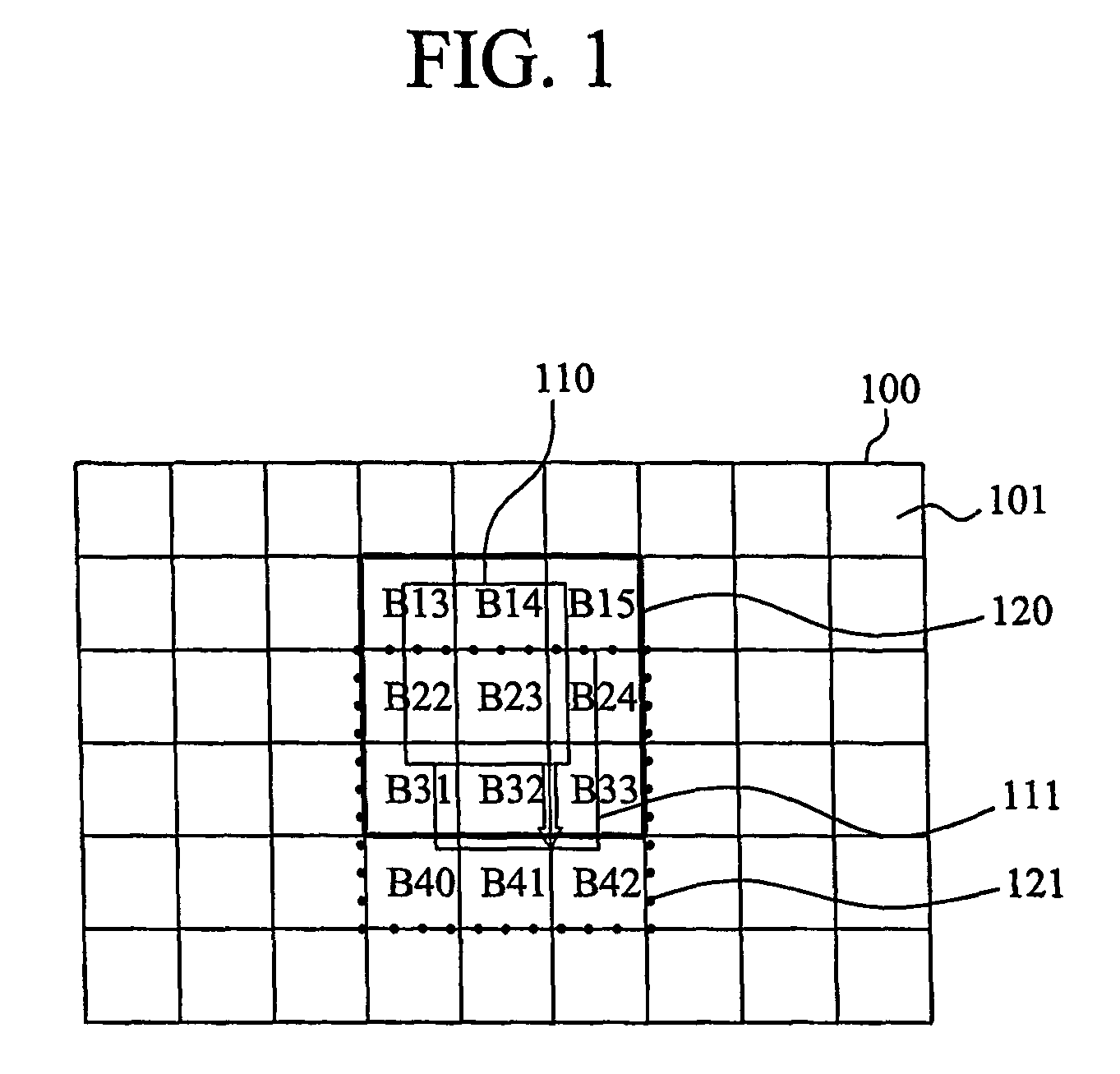
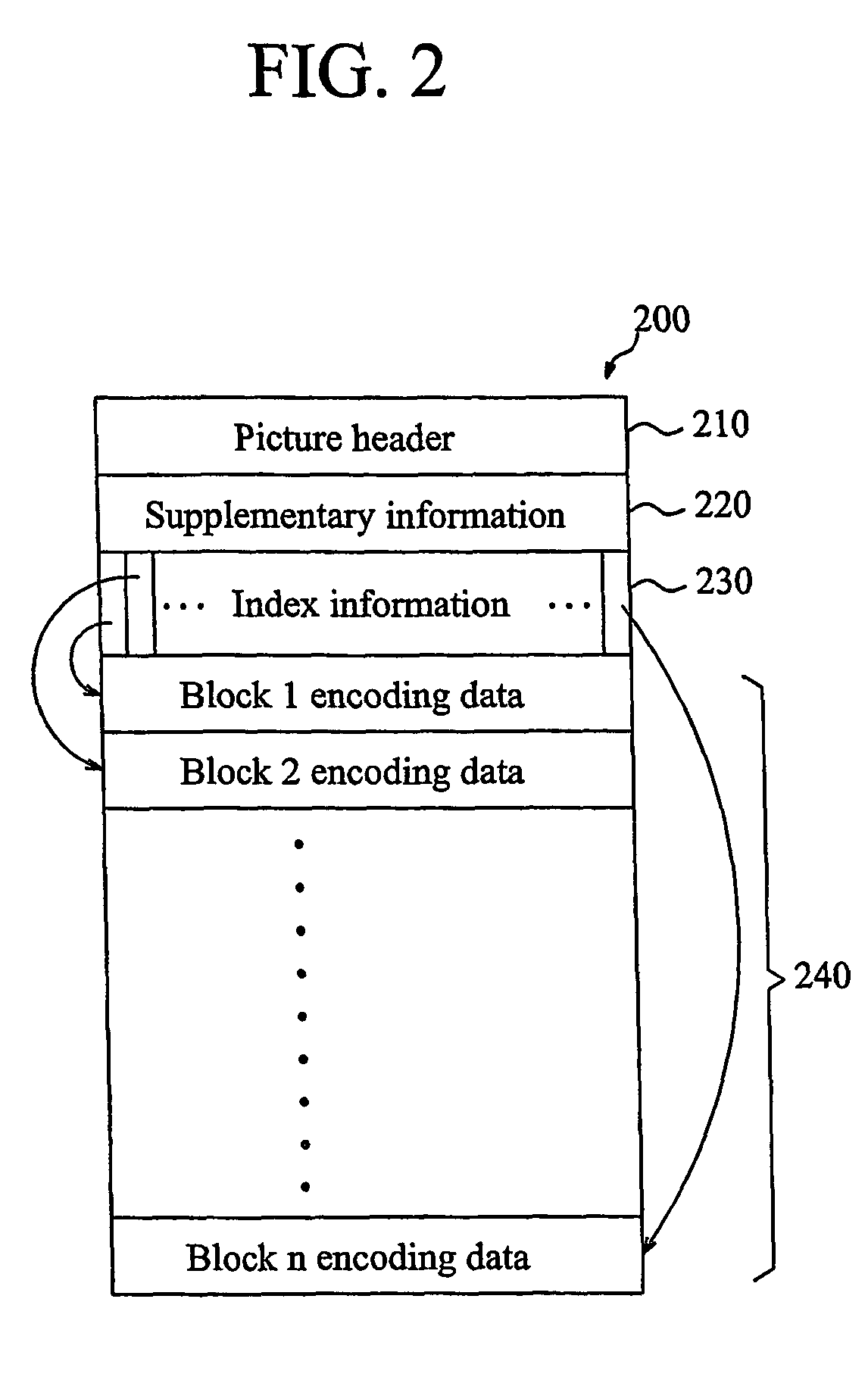
The present invention discloses a method for displaying a high resolution picture in a mobile communication terminal having a low resolution display means, the mobile communication terminal and a system for converting a picture file format therefor. The method for displaying the high resolution picture in the mobile communication terminal includes the steps of: dividing picture data into a plurality of unit blocks, and converting the picture data into a picture file format including the plurality of unit block picture data and indexes for access to each of the block picture data; extracting minimum unit block picture data composing a partial picture which will be initially outputted to a display unit from the picture file by using the index information of the picture file format, and outputting the initial picture; and extracting the corresponding unit block picture data from the picture file in the movement direction by using the index information of the picture file format in accordance with generation of scroll action during the display of the picture, and outputting the position-moved picture.
Owner:SK PLANET CO LTD +1
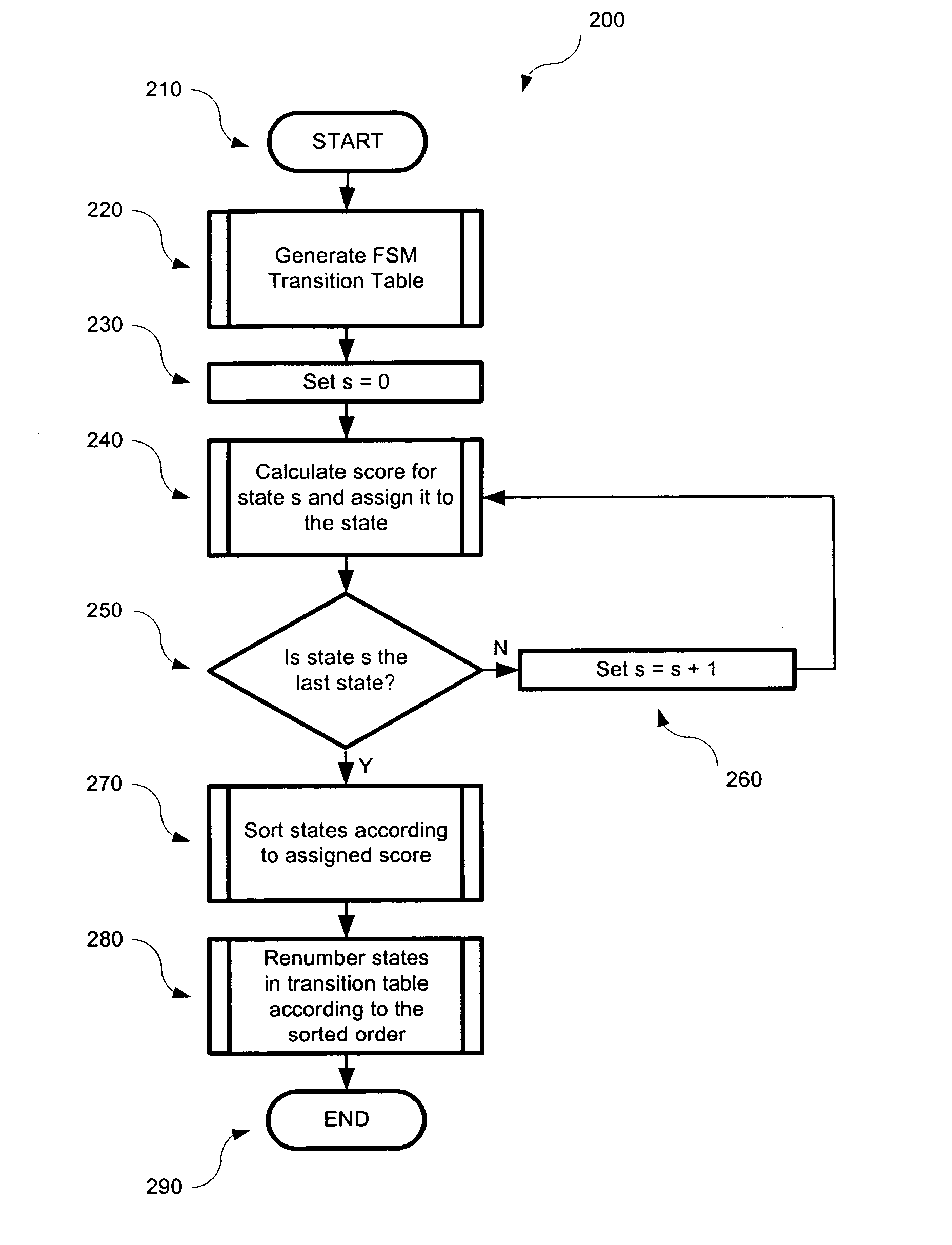
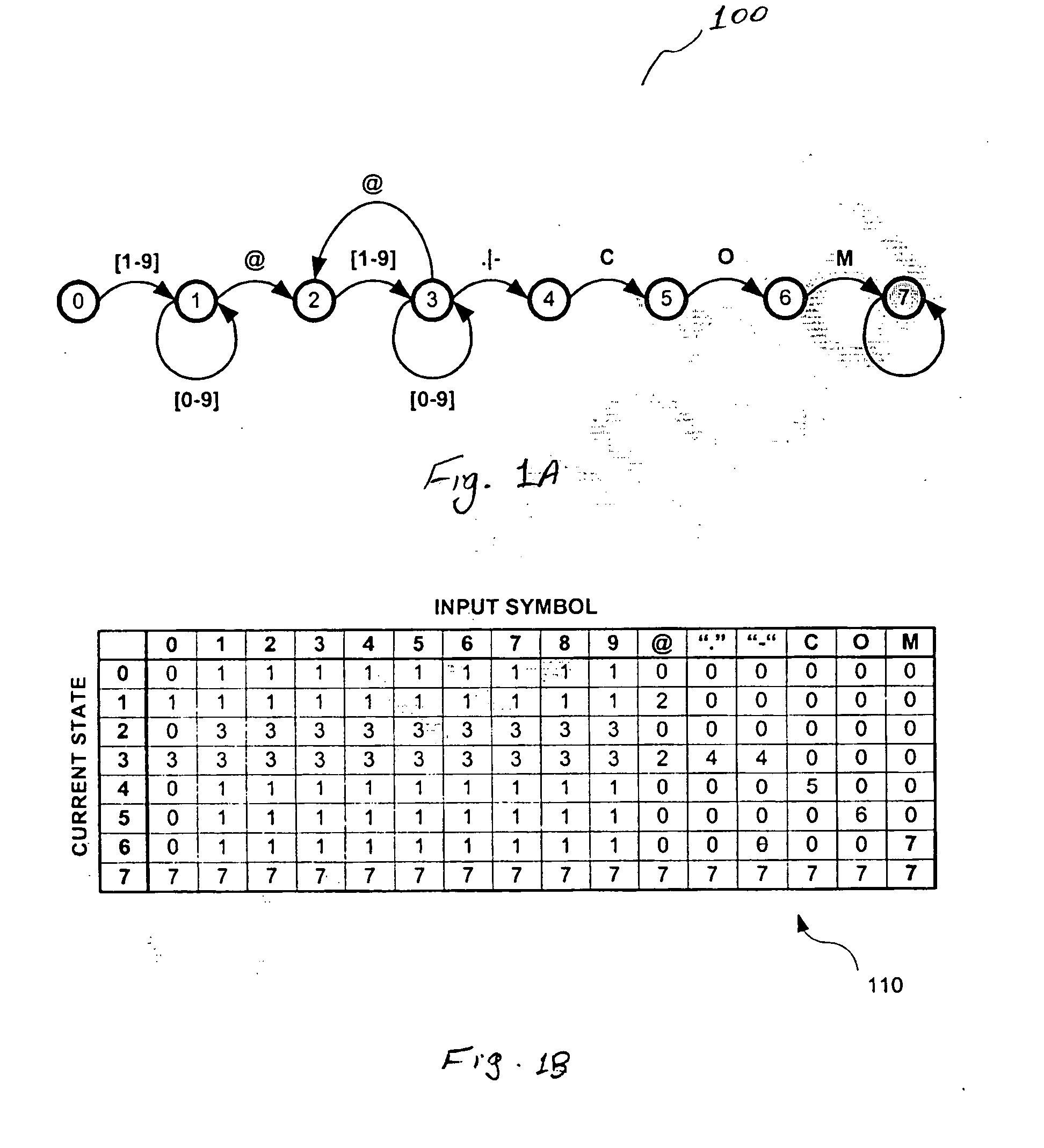
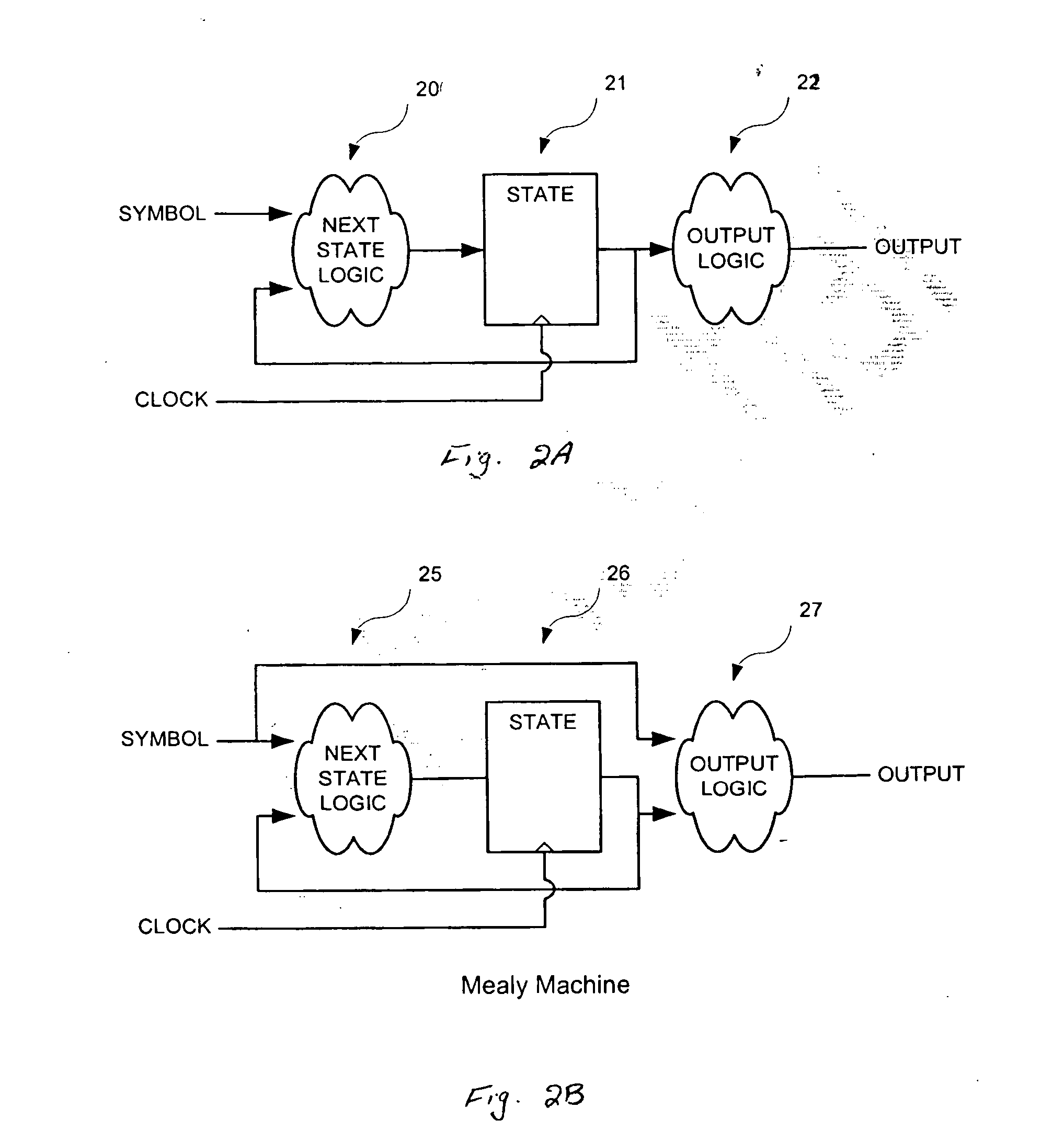
Efficient representation of state transition tables
InactiveUS20050028114A1Small memoryImprove data throughputKnowledge representationSpecial data processing applicationsTheoretical computer scienceState transition table
The states associated with a programmable state machine are reordered to compress the storage of transitions which define the state machine. To reorder the states, a score is computed and assigned to each of the states. Next, the states are sorted according to their computed scores. In some embodiments, to compute the score for each current state based on the received input symbol, the number of times that the input symbol causes transition to similar states is added. The sum of the scores in each row of the table is representative of the score for the associated current state associated with that row. The states are sorted according to their score and a new state transition table is generated in accordance with the reordered states.
Owner:INTEL CORP +1
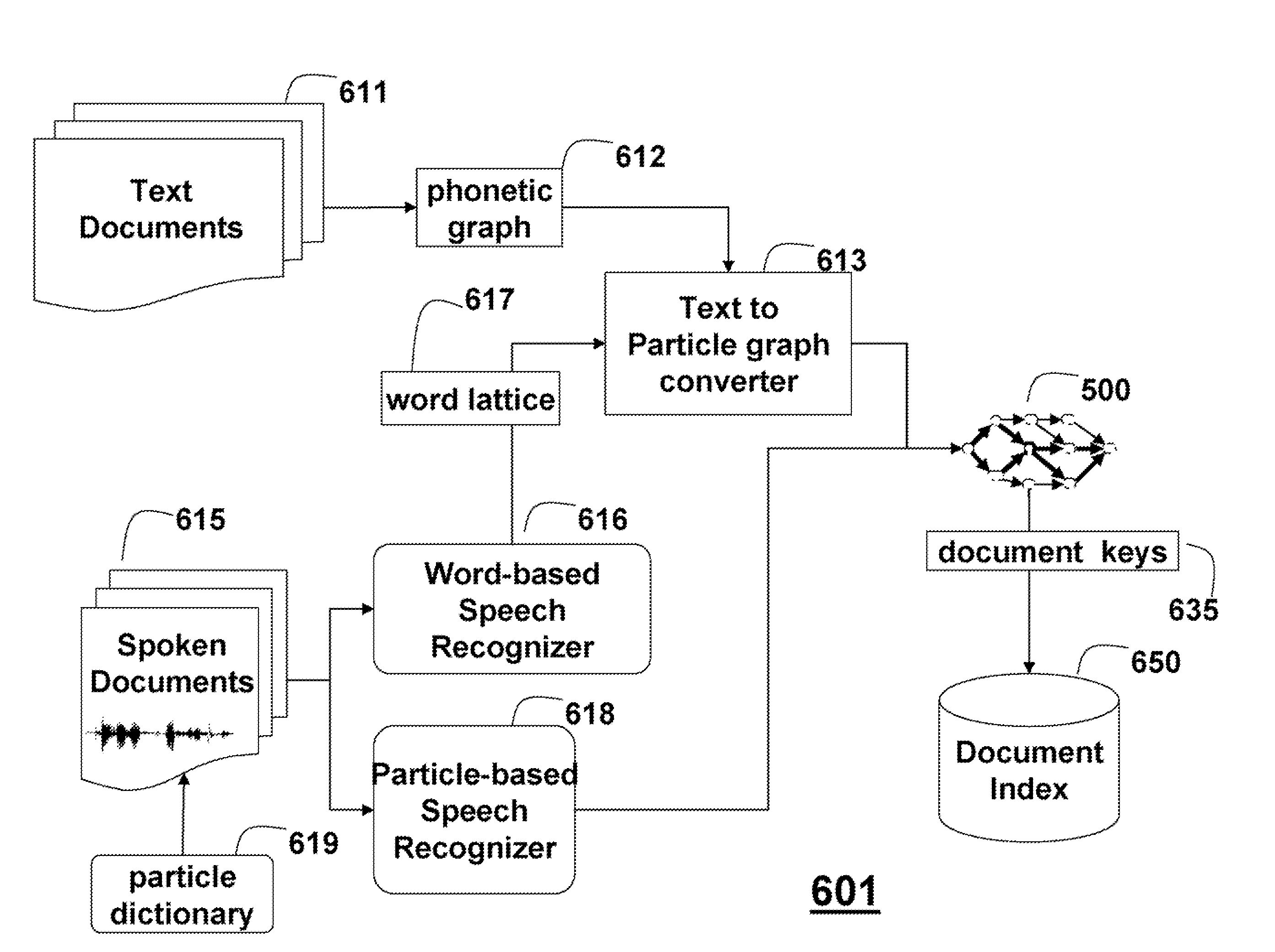
Method for Indexing for Retrieving Documents Using Particles
InactiveUS20090216740A1Avoid any limitationAvoid restrictionsDigital data information retrievalDigital data processing detailsDocument preparationSystem usage
An information retrieval system stores and retrieves documents using particles and a particle-based language model A set of particles for a collection of documents in a particular language is constructed from training documents such that a perplexity of the particle-based language model is substantially lower than the perplexity of a word-based language model constructed from the same training documents. The documents can then be converted to document particle graphs from which particle-based keys are extracted to form an index to the documents. Users can then retrieve relevant documents using queries also in the form of particle graphs.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Defining a data structure for pattern matching
ActiveUS20100017397A1Reduce memory usageImprove computing efficiencyDigital data information retrievalDigital data processing detailsInformation processingPattern matching
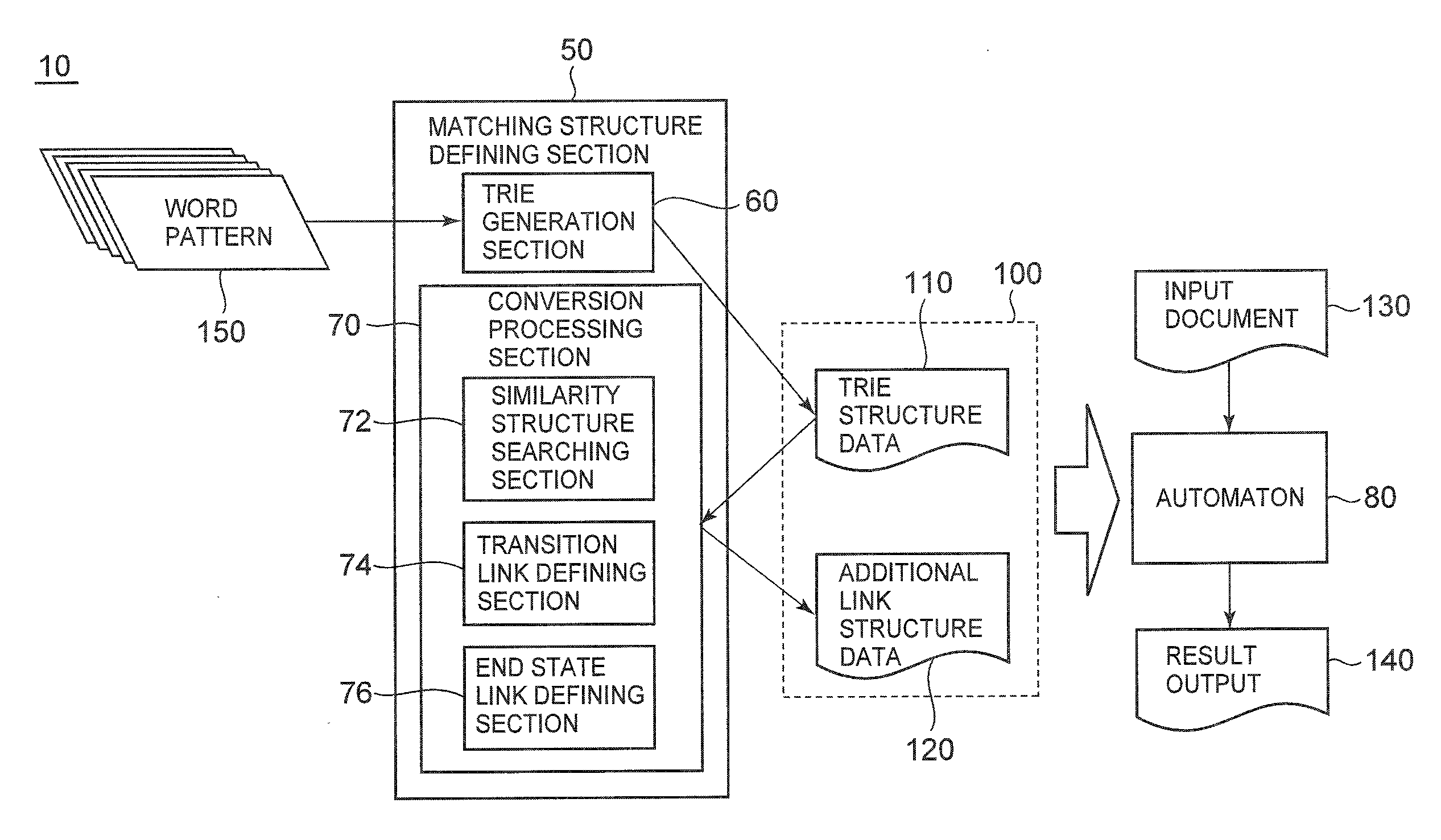
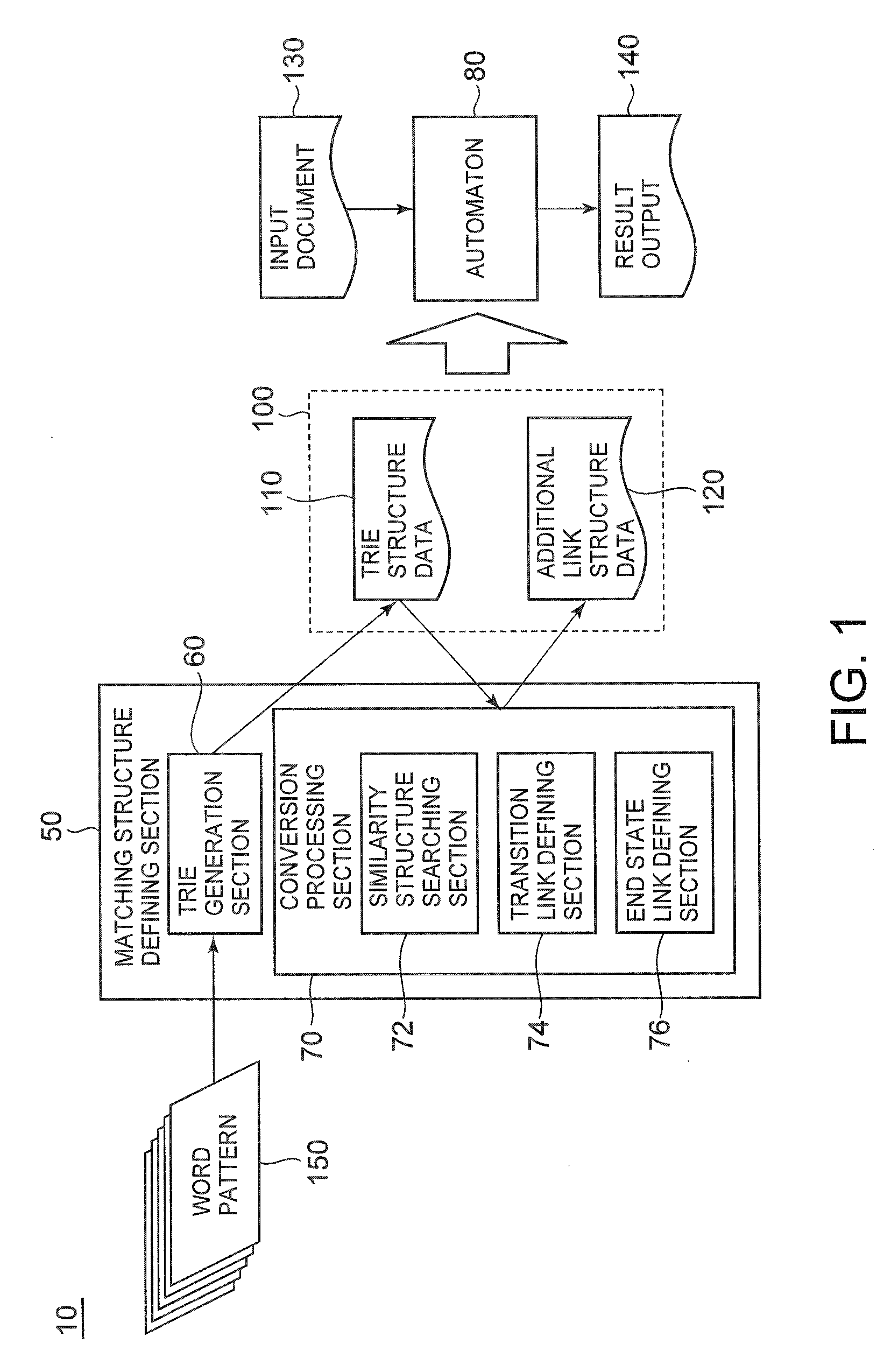
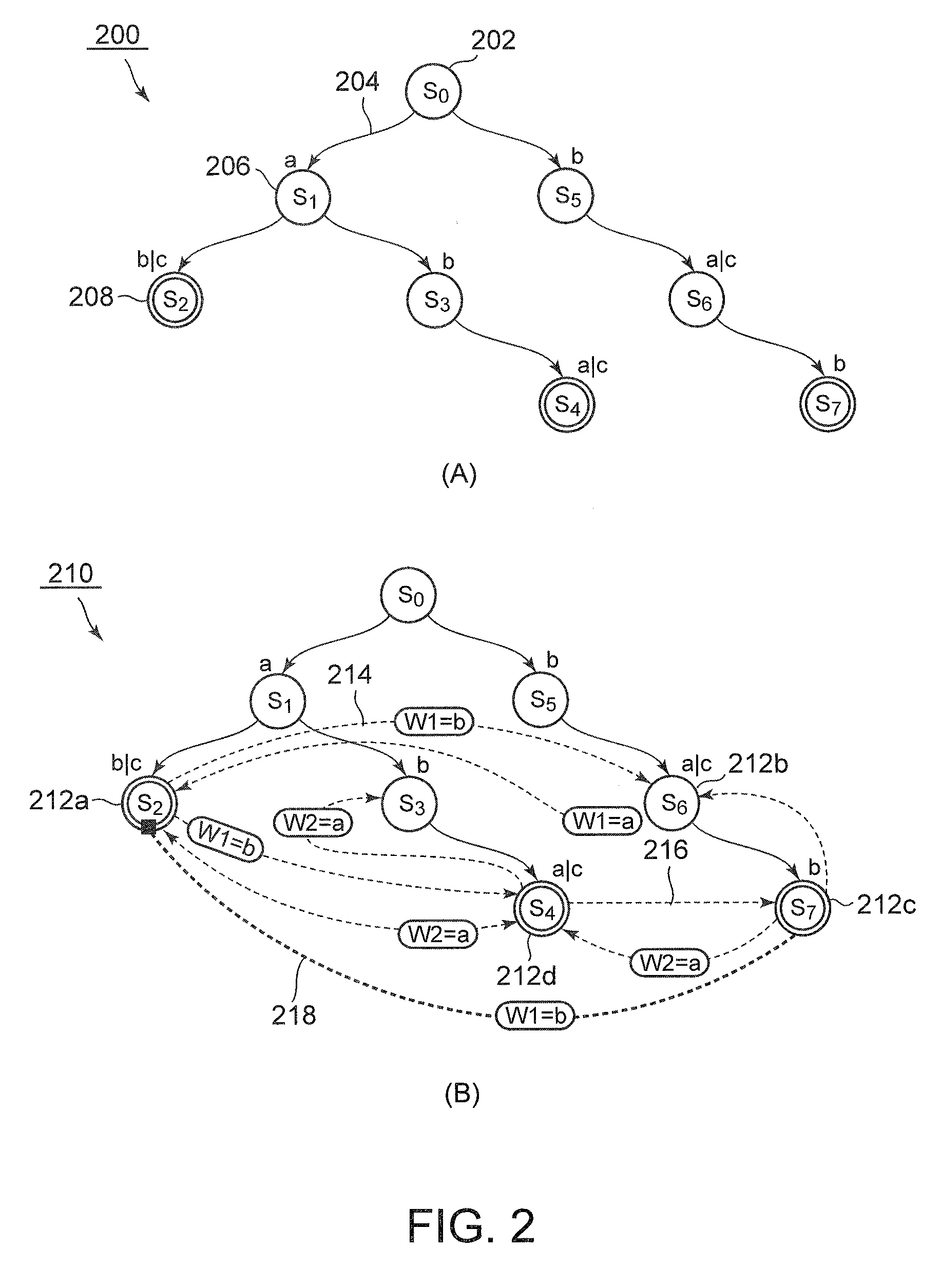
An information processing apparatus according to the present invention comprises a generation section configured to generate an ordered tree structure by defining transition edges between nodes using, as transition conditions, respective constraints from one or more constraint pattern each including plural constraints, a search section configured to search for a second substructure K similar to a first substructure P from a root node by determining a set relation between transition conditions of respective transition edges, and a transition defining section configured to define an additional transition link from a tail node sKn of the second substructure K to a child node sPn+1 of the first substructure P, the additional transition link adding a constraint to be met by an indeterminant identified from the set relation, wherein a data structure for pattern matching is defined.
Owner:BREAKWATER SOLUTIONS LLC
Image data compression method and apparatuses, image display method and apparatuses
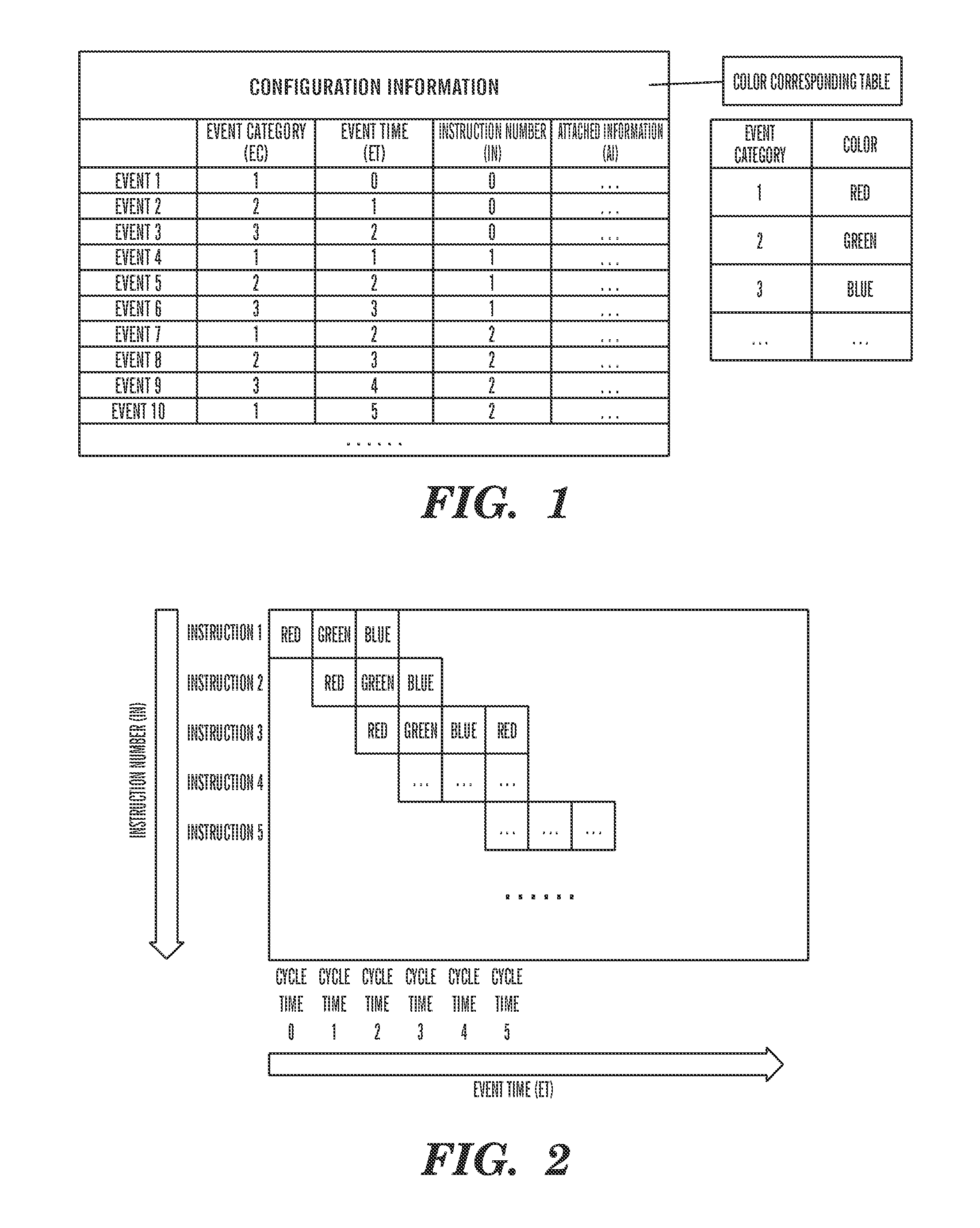
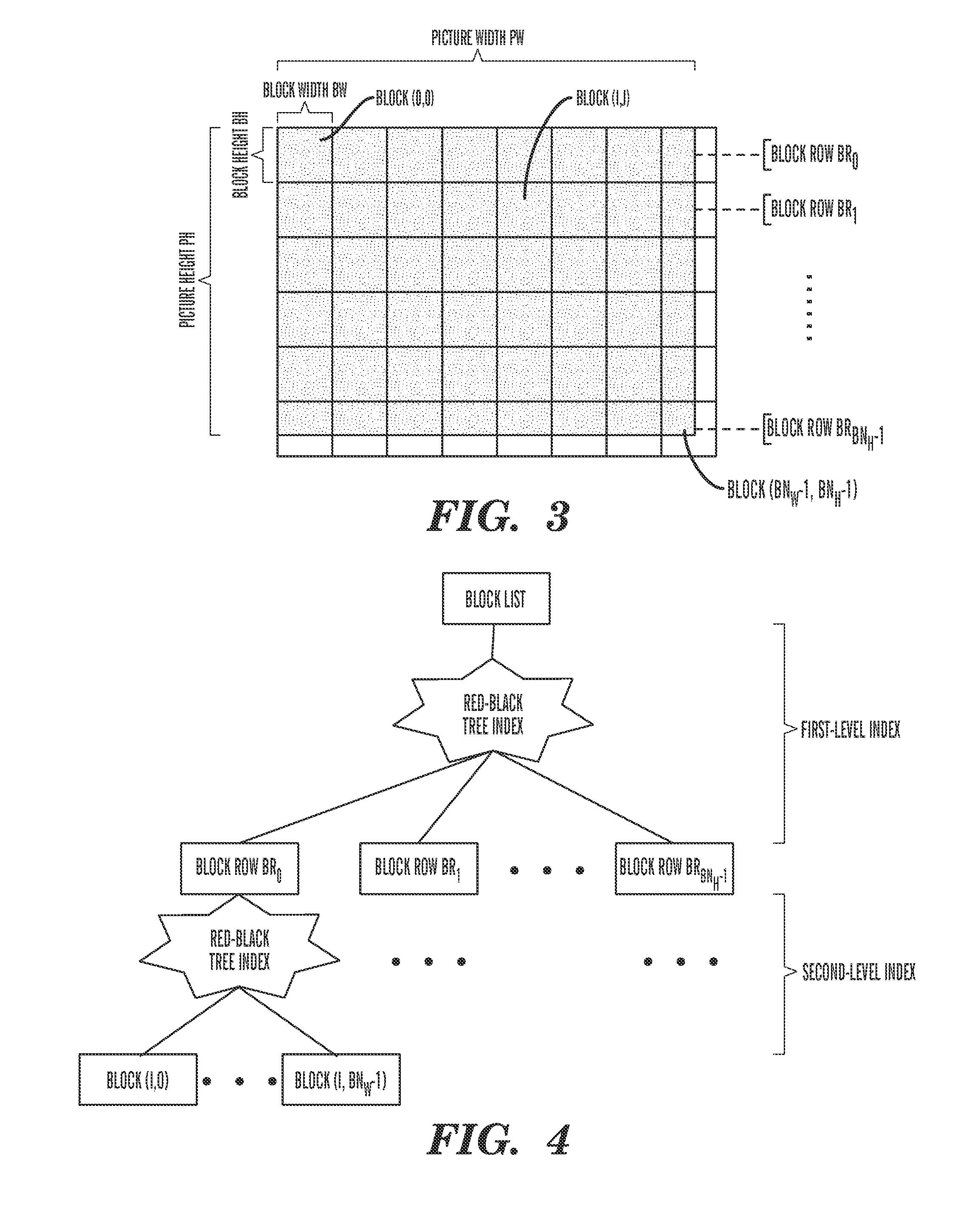
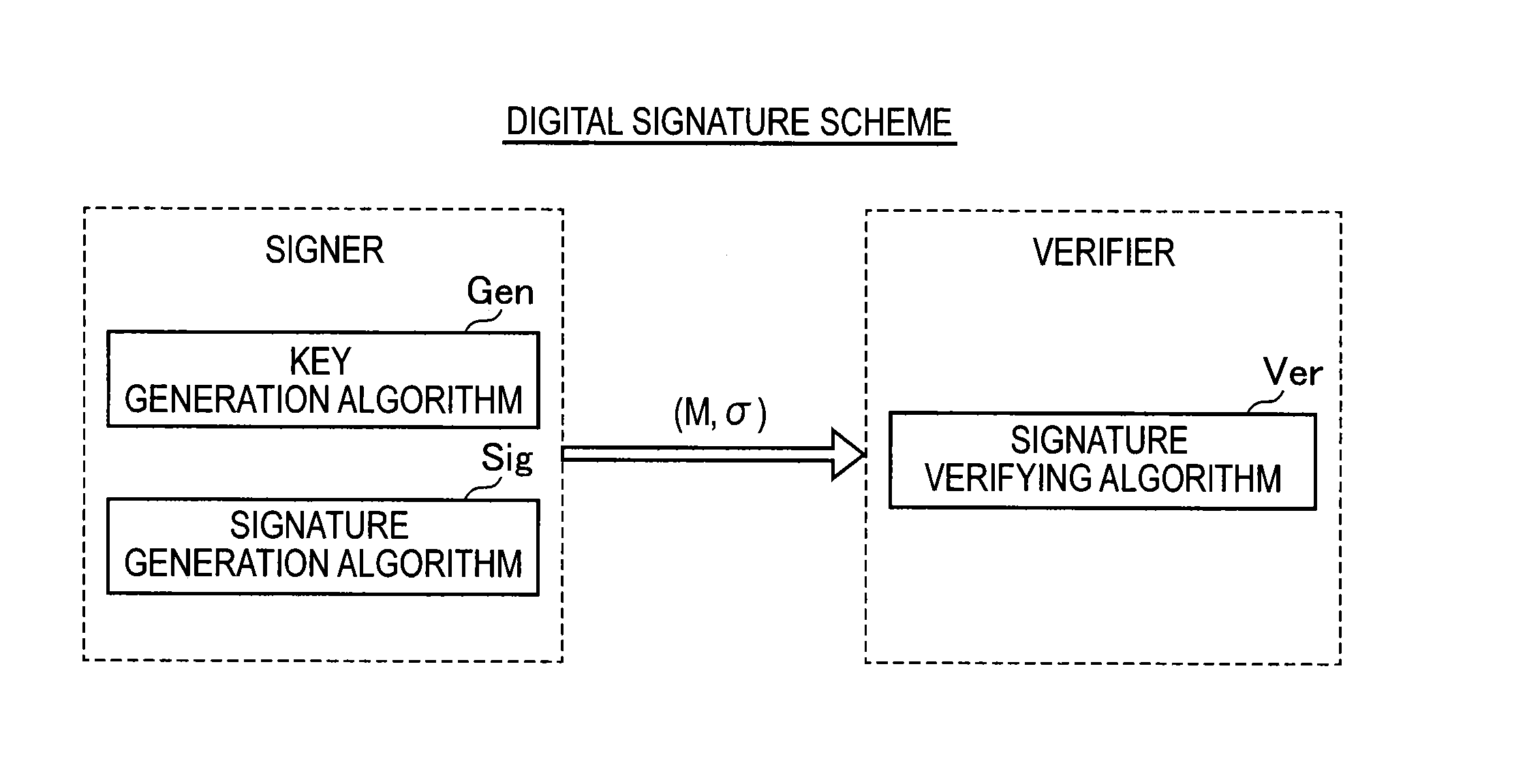
InactiveUS8019166B2Small memoryCharacter and pattern recognitionCathode-ray tube indicatorsData compressionComputer graphics (images)
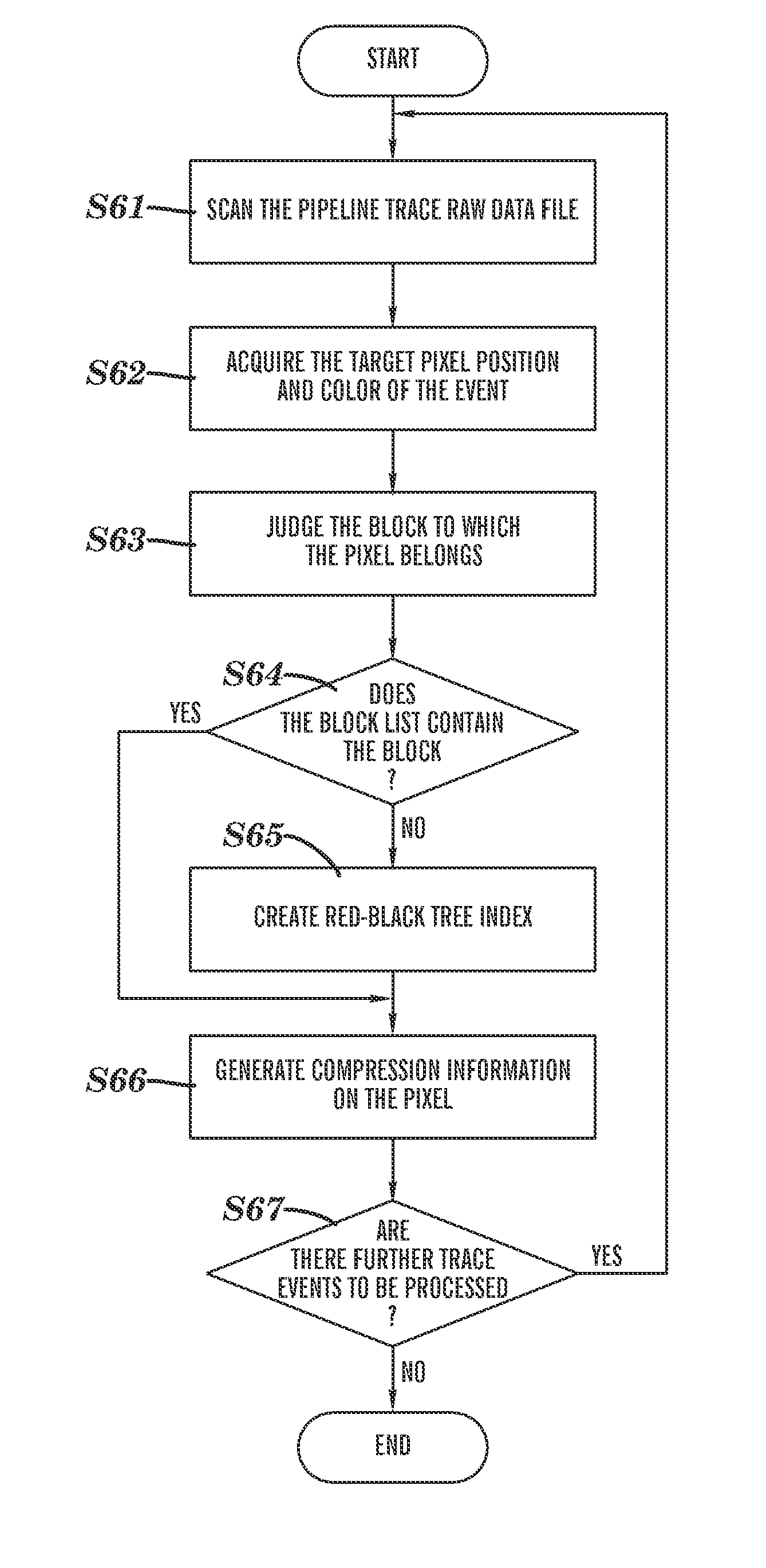
The image data compression method involves the performing of steps: a block dividing step for dividing a computer processor pipeline statistic image to be displayed into a plurality of blocks with predetermined block width and block height; a block list creating step for creating a block list for indexed blocks containing meaningful pixels in the divided blocks such that the indexed blocks are associated with each other, wherein the meaningful pixels are pixels corresponding to the computer processor pipeline raw trace data; and a pixel information compressing step for compressing original pixel information on the meaningful pixels in the indexed blocks and storing it in the block list. Apparatus for performing the method is also provided.
Owner:IBM CORP
Signature verification apparatus, signature verification method, program, and recording medium
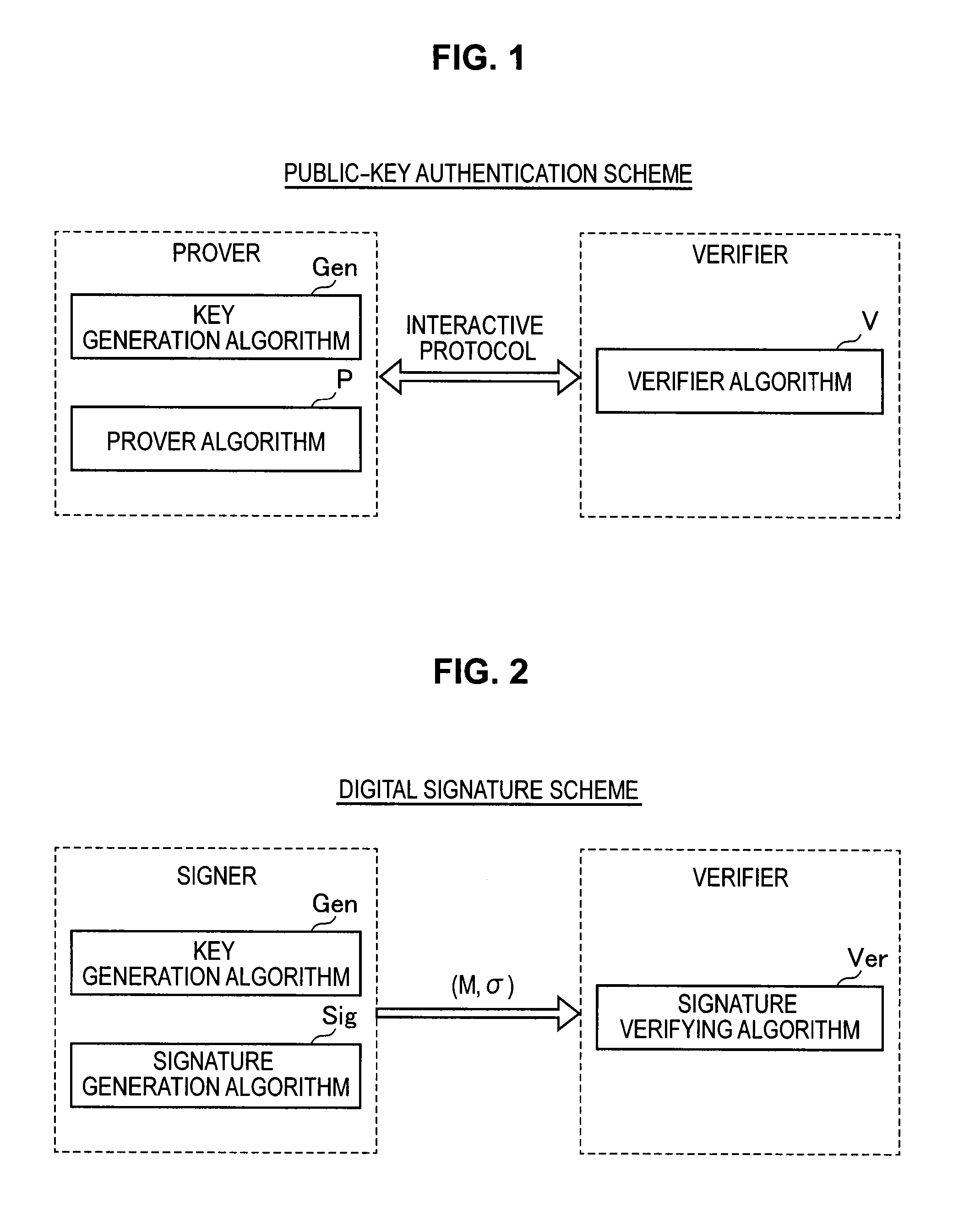
ActiveUS20140223193A1High safetySmall memoryUnauthorized memory use protectionHardware monitoringKey generationCommon key
A signature verification apparatus including a signature acquisition unit configured to acquire a digital signature including first information generated based on a pair of multi-order multivariate polynomials F=(f1, . . . , fm) defined in a ring K, a signature key s which is an element of a set Kn, and a document M and a plurality of pieces of second information for verifying that the first information is generated using the signature key s based on the data M, the pair of multi-order multivariate polynomials F, and vectors y=(f1(s), . . . , fm(s)), and a signature verification unit configured to verify legitimacy of the document M by confirming whether or not the first information is restorable using the plurality of pieces of second information included in the digital signature. The pair of multivariate polynomials F and the vectors y are public keys.
Owner:SONY CORP
Communication device and method of operation
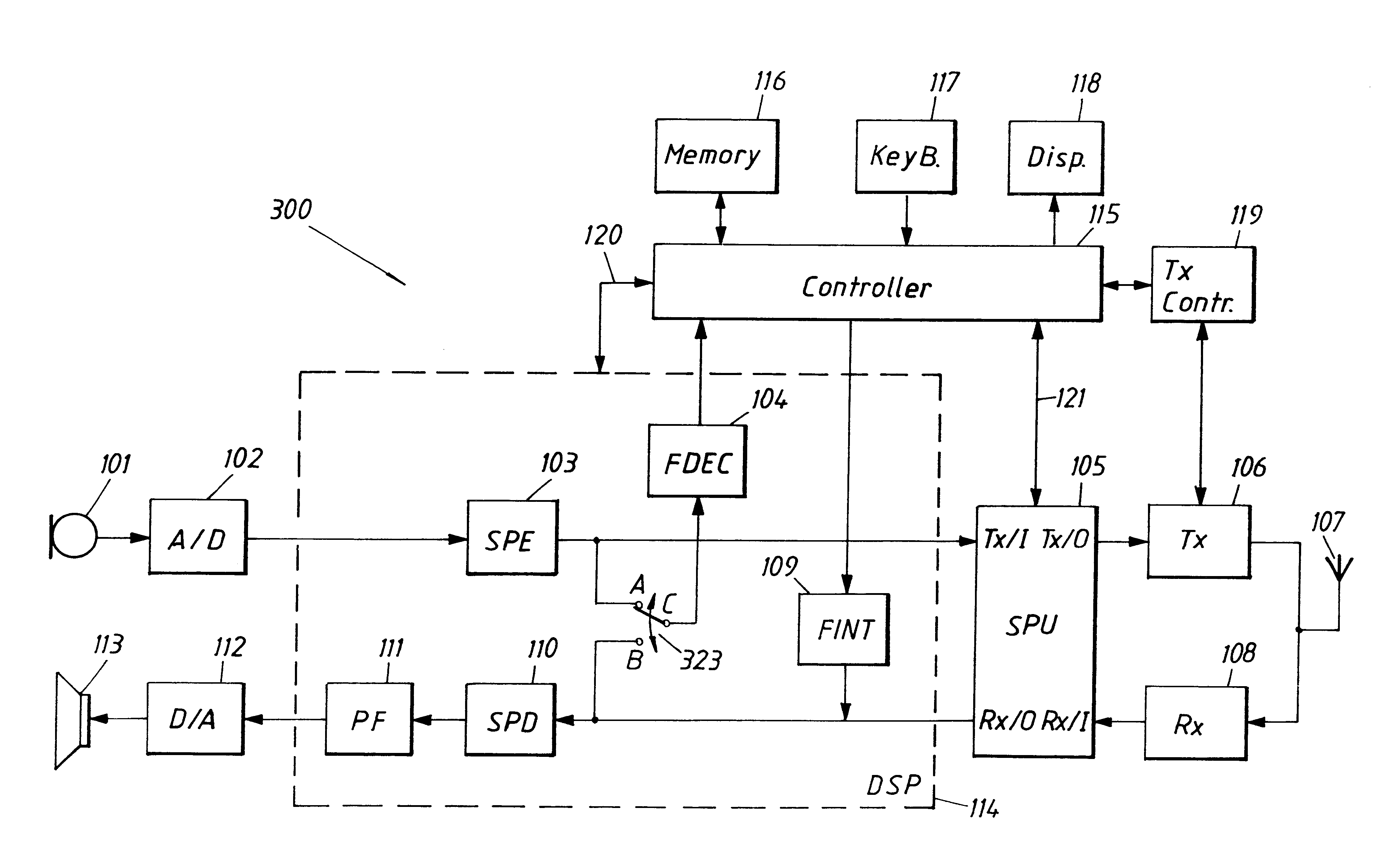
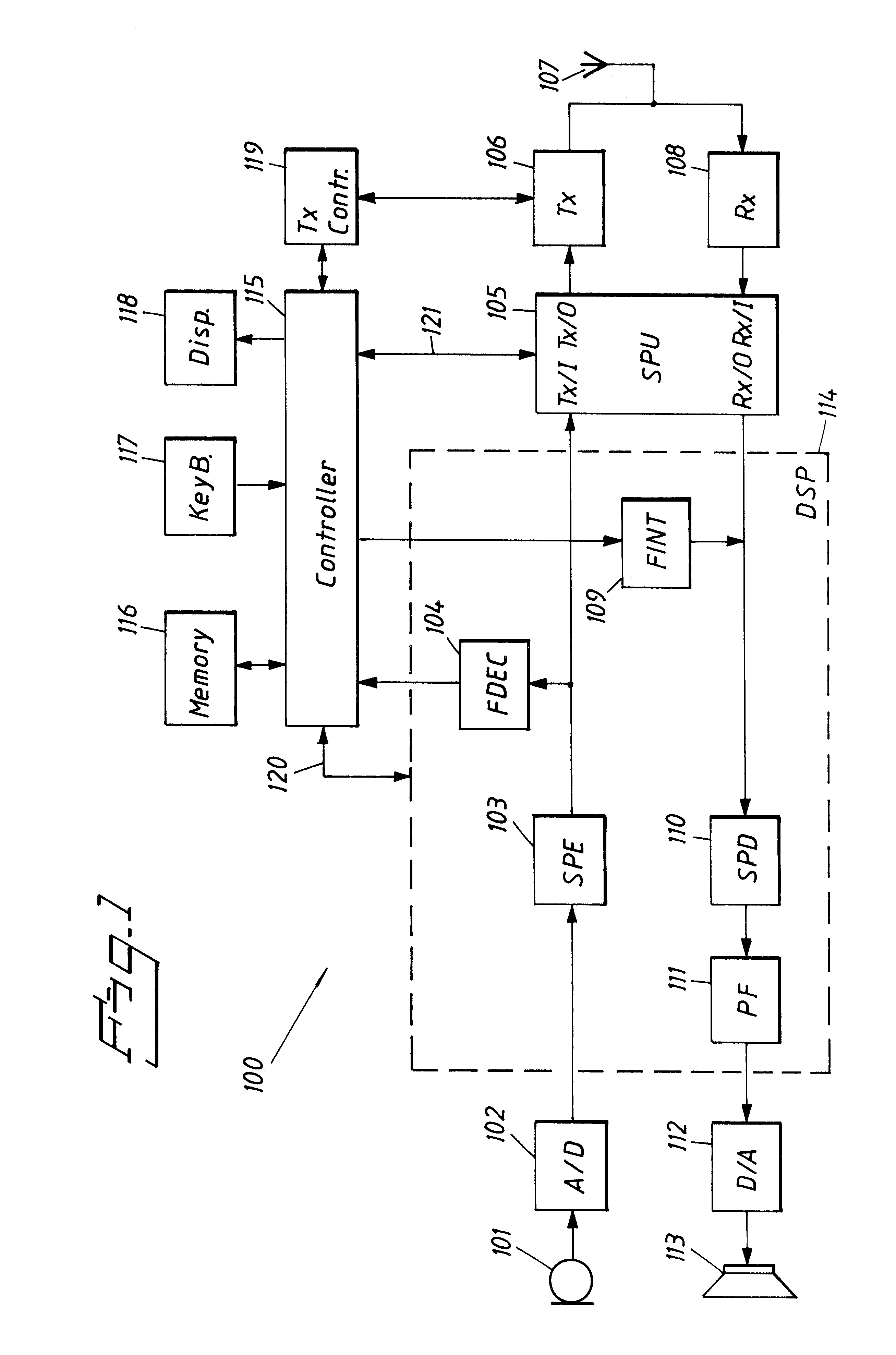
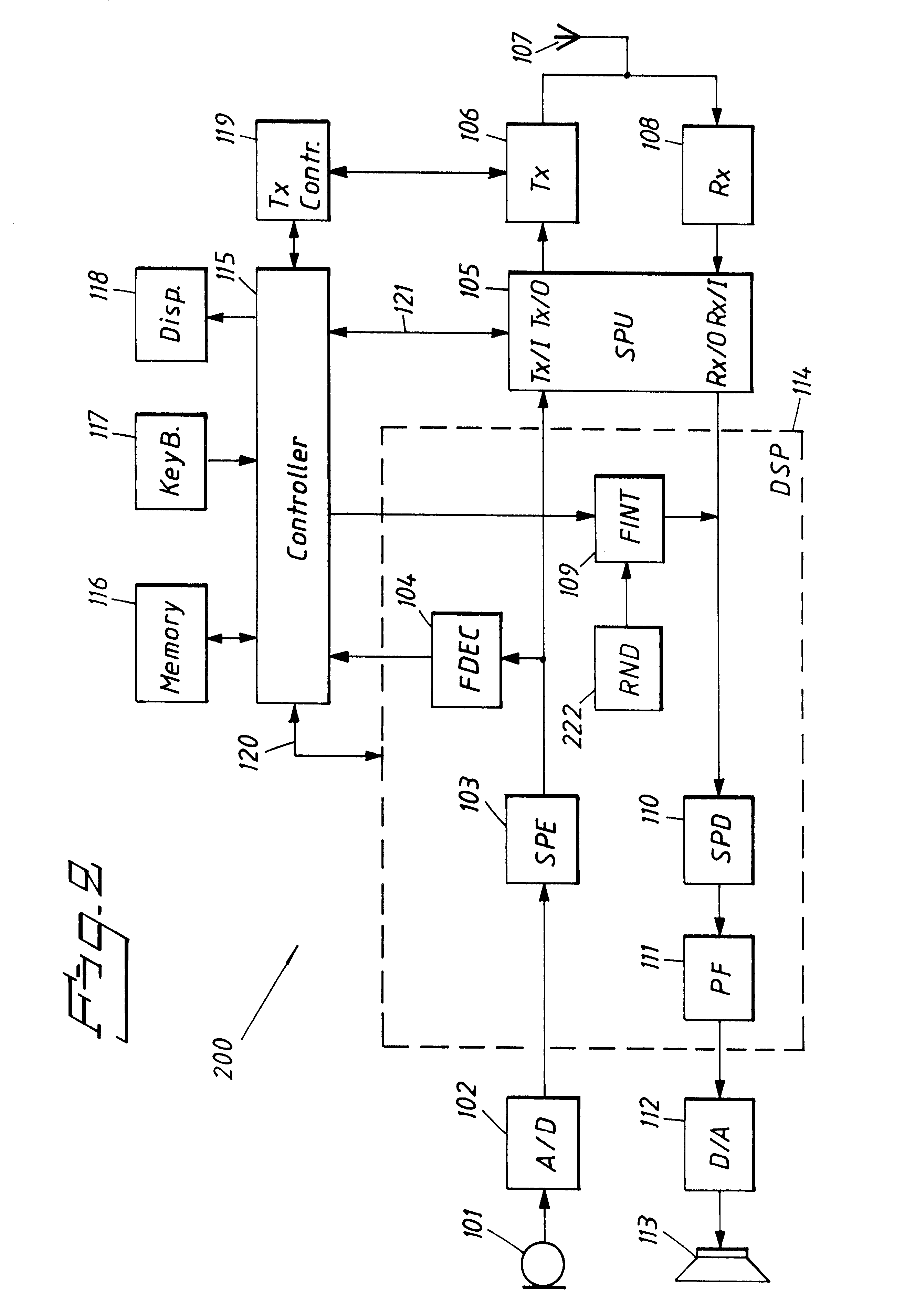
InactiveUS6424822B1Small memoryLess memoryCordless telephonesSpeech analysisSpeech soundCommunication device
A communication device is provided having a speech encoder and a speech decoder and being able to retrieve and store voice messages in a memory. The messages are stored in the memory according to a message format. This format is more compressed than the speech encoding format which is provided by the speech encoder. The device includes a frame interpolation block for decompressing a stored message and thereby creating a signal according to the speech encoding format. A frame decimation block is also provided for compressing a speech encoded signal thereby allowing a corresponding voice message to be stored in the memory according to the message format.
Owner:TELEFON AB LM ERICSSON (PUBL)
Crossbar switch and recursive scheduling
ActiveUS20120033662A1Reduce switching delaySmall memoryMultiplex system selection arrangementsData switching by path configurationCrossbar switchDecomposition
A crossbar switch has N input ports, M output ports, and a switching matrix with N×M crosspoints. In an embodiment, each crosspoint contains an internal queue, which can store one or more packets to be touted. Traffic rates to be realized between all Input / Output (IO) pairs of the switch are specified in an N×M traffic rate matrix, where each element equals a number of requested cell transmission opportunities between each IO pair within a scheduling frame of F time-slots. An efficient algorithm for scheduling N traffic flows with traffic rates based upon a recursive and fair decomposition of a traffic rate vector with N elements, is proposed. To reduce memory requirements shared row queue (SRQ) may be embedded in each row of the switching matrix, allowing the size of all the XQs to be reduced. To further reduce memory requirements, a shared column queue may be used in place of the XQs. The proposed buffered crossbar switches with shared row and column queues, in conjunction with the now scheduling algorithm and the DCS column scheduling algorithm, can achieve high throughout with reduced buffer and VLSI area requirements, while providing probabilistic guarantees on rate, delay and jitter for scheduled traffic flows.
Owner:SZYMANSKI TADEUSZ H
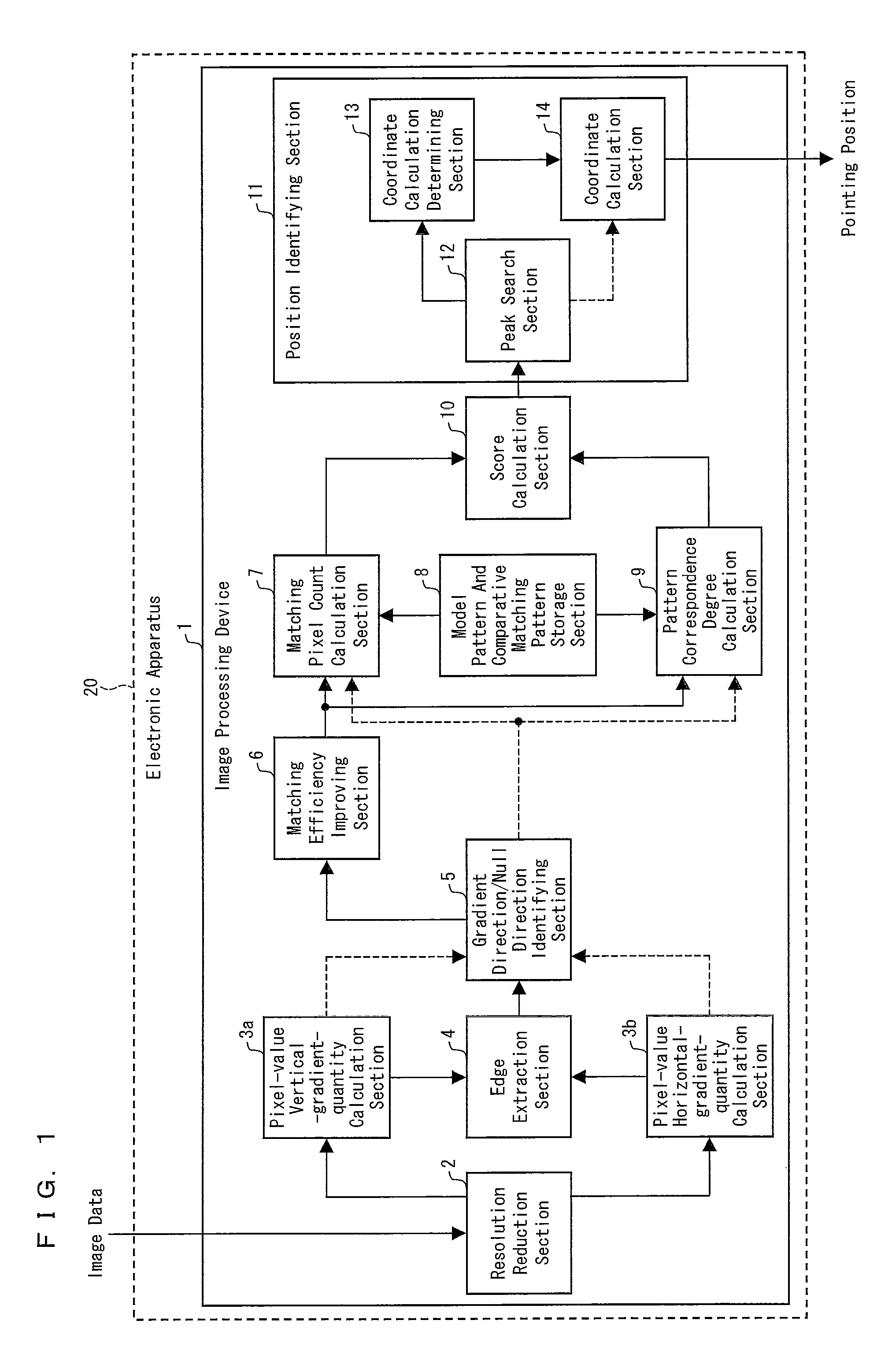
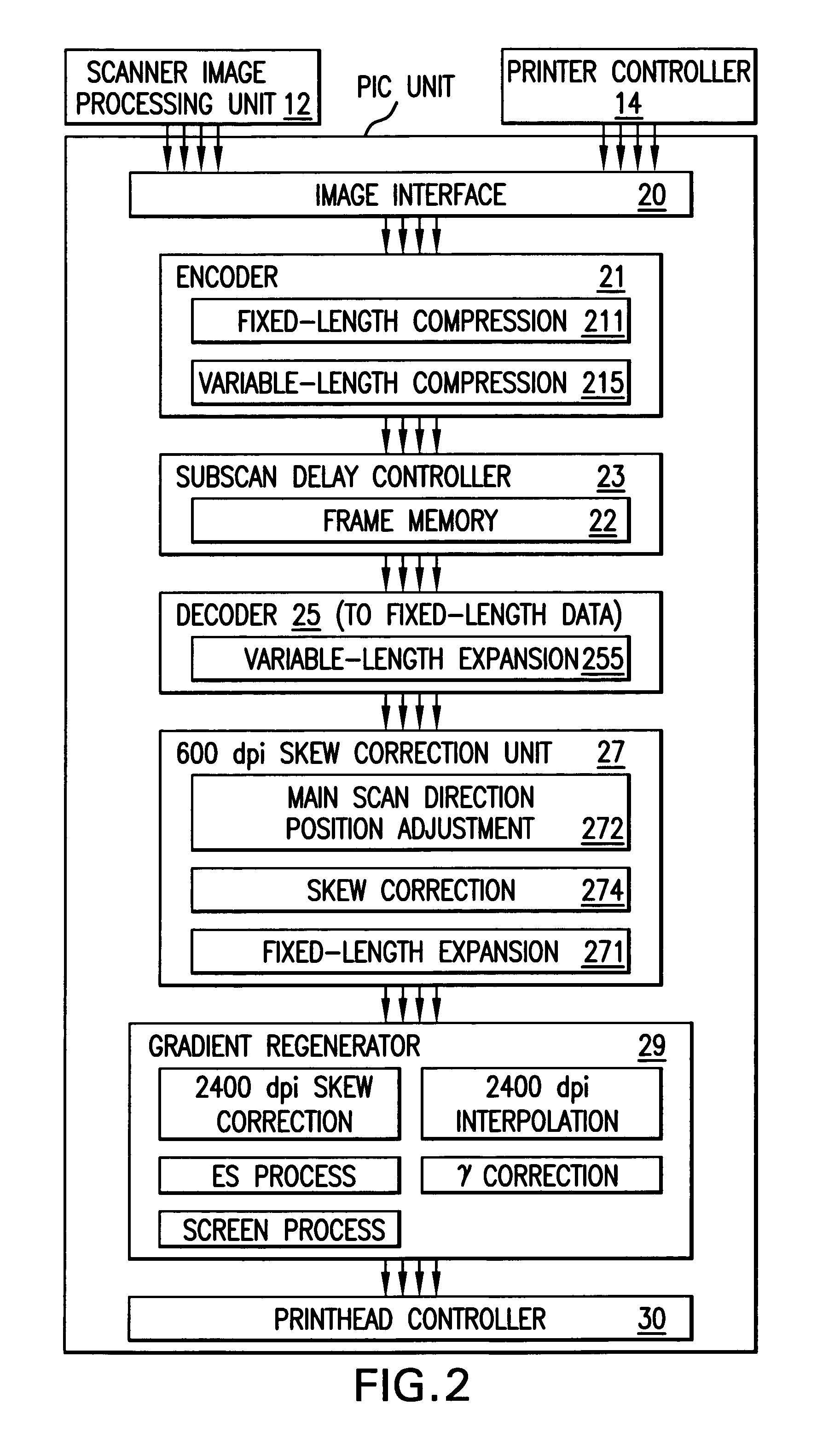
Image processing device, control program, computer-readable storage medium, electronic apparatus, and image processing device control method
InactiveUS20100134444A1Reduce the amount requiredMaintain precisionImage analysisStatic indicating devicesImaging processingVertical gradient
The invention includes: a pixel-value vertical-gradient-quantity calculation section (3a) and a pixel-value horizontal-gradient-quantity calculation section (3b) for calculating a vertical-direction gradient quantity (Sy) and a horizontal-direction gradient quantity (Sx) for a pixel value; a gradient direction / null direction identifying section (5) for identifying, for each pixel, either a gradient direction or null direction; a score calculation section (10) for calculating an correspondence degree for a matching region and a predetermined model pattern from a number of matches of a gradient direction for each pixel contained in the matching region with a gradient direction in the model pattern; a peak search section (12) for searching a search area for a peak pixel which is a pixel for which the correspondence degree calculated by the score calculation section (10) is a maximum; and a coordinate calculation section (14) for calculating a position in a captured image pointed at with an image capture object by using the correspondence degree for each pixel in a peak pixel region.
Owner:SHARP KK
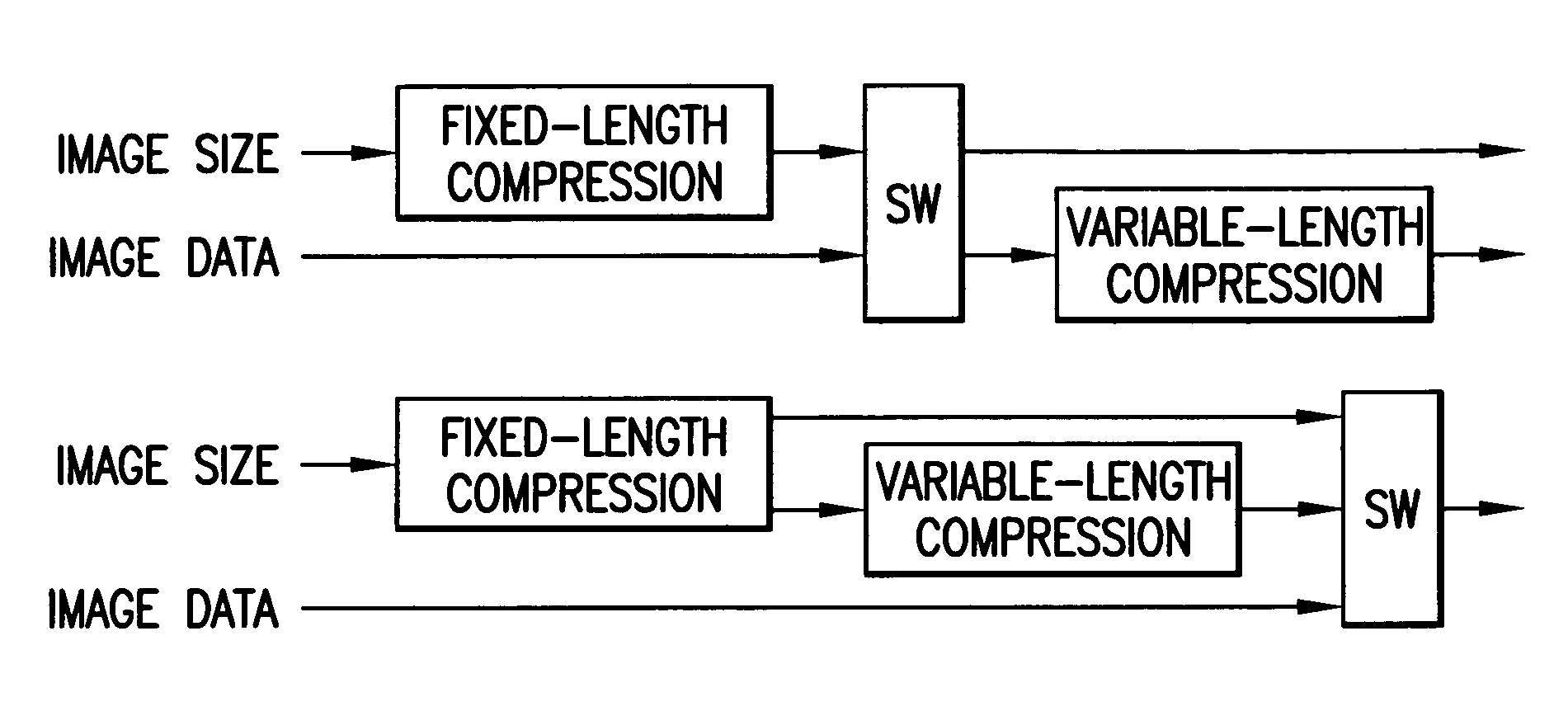
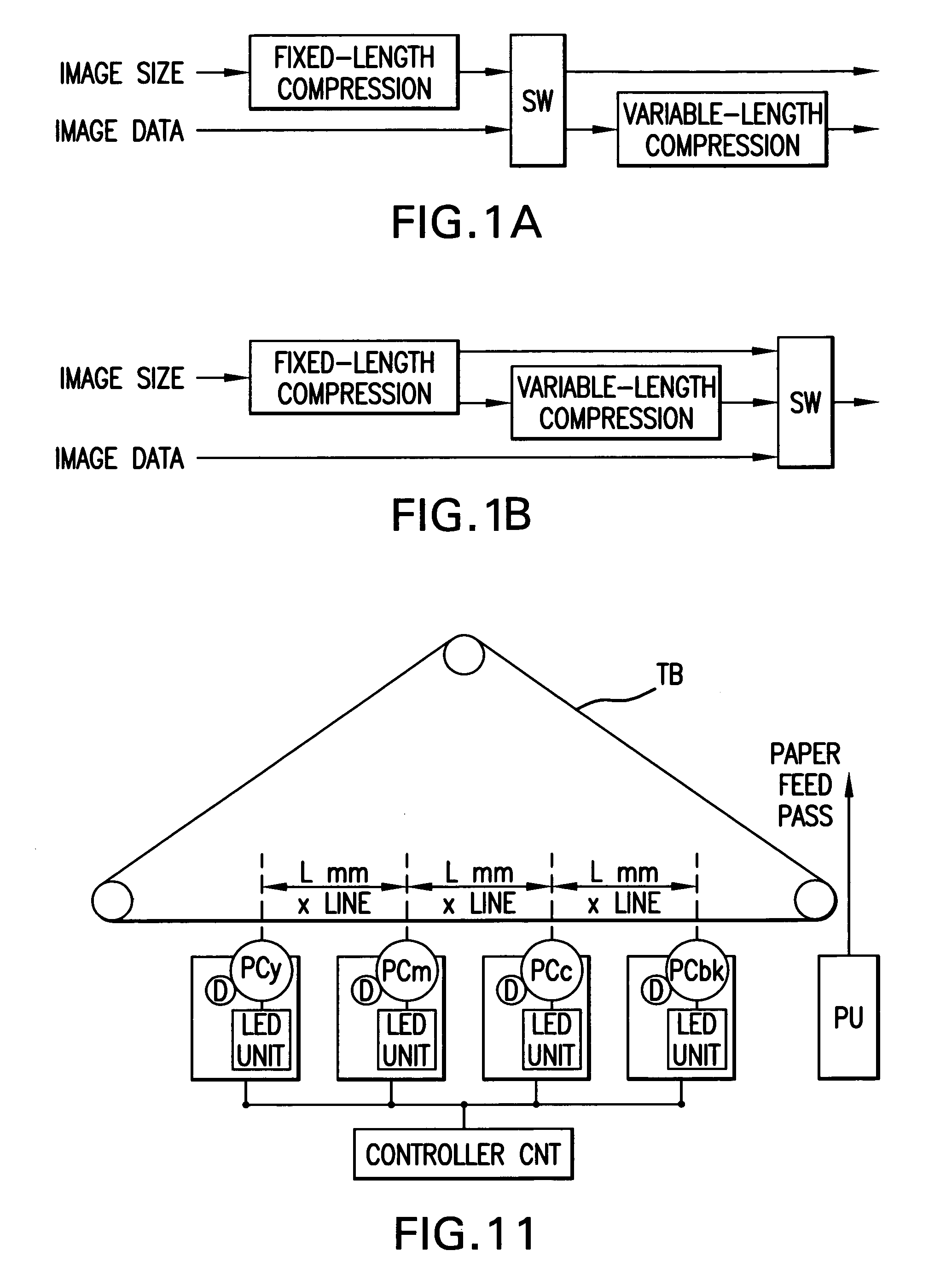
Image processing apparatus for compressing image data with optimum compression method corresponding to image size thereof
InactiveUS7009722B1Low costHigh image formationDigitally marking record carriersVisual presentation using printersImaging processingComputer graphics (images)
An image processing apparatus for storing image data in a memory, reading image data stored in a memory, and generating print data, and is provided with a size designating means for designating an image size, and a memory control means for storing in memory the image data compressed by a compression method corresponding to a specified image size.
Owner:MINOLTA CO LTD
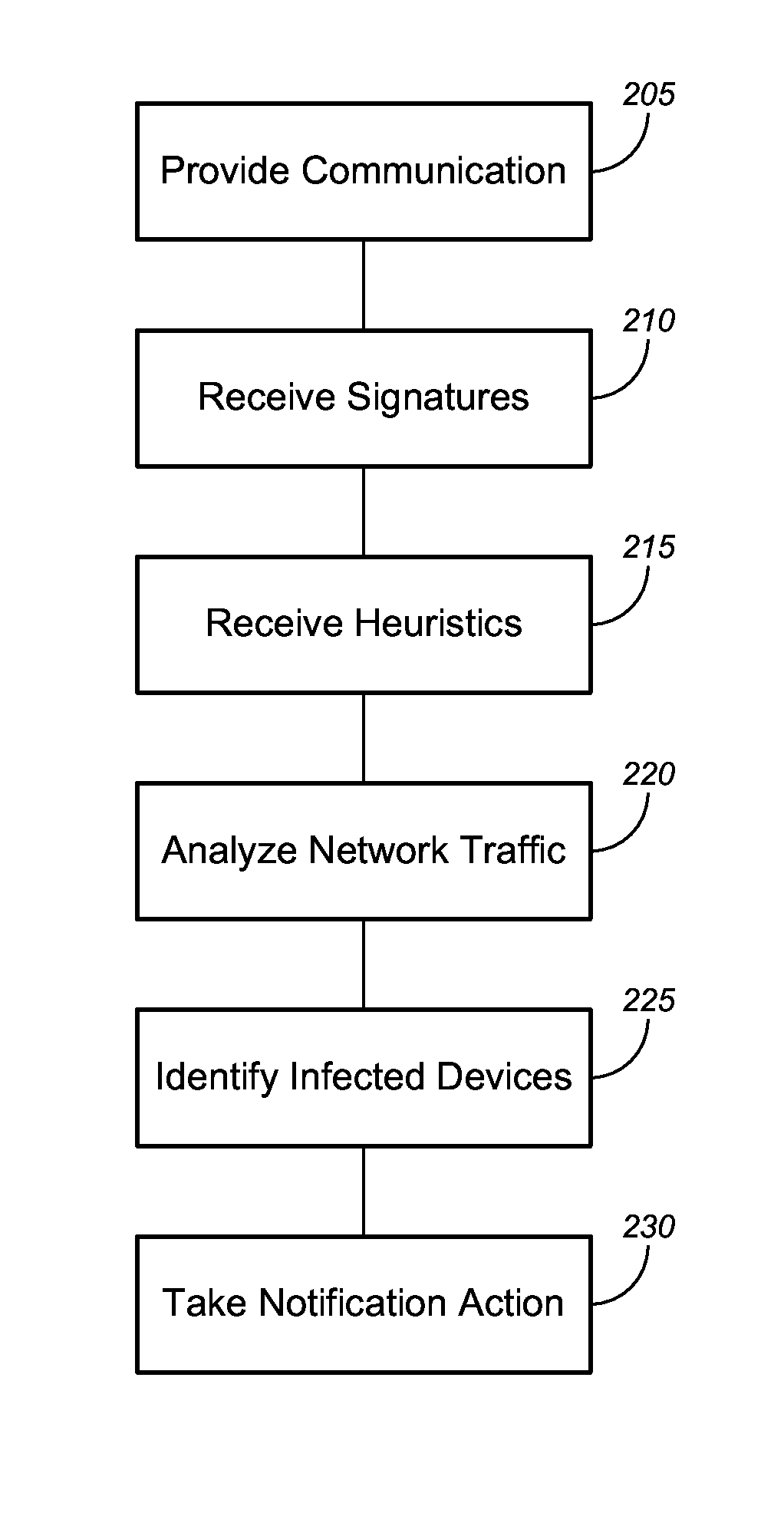
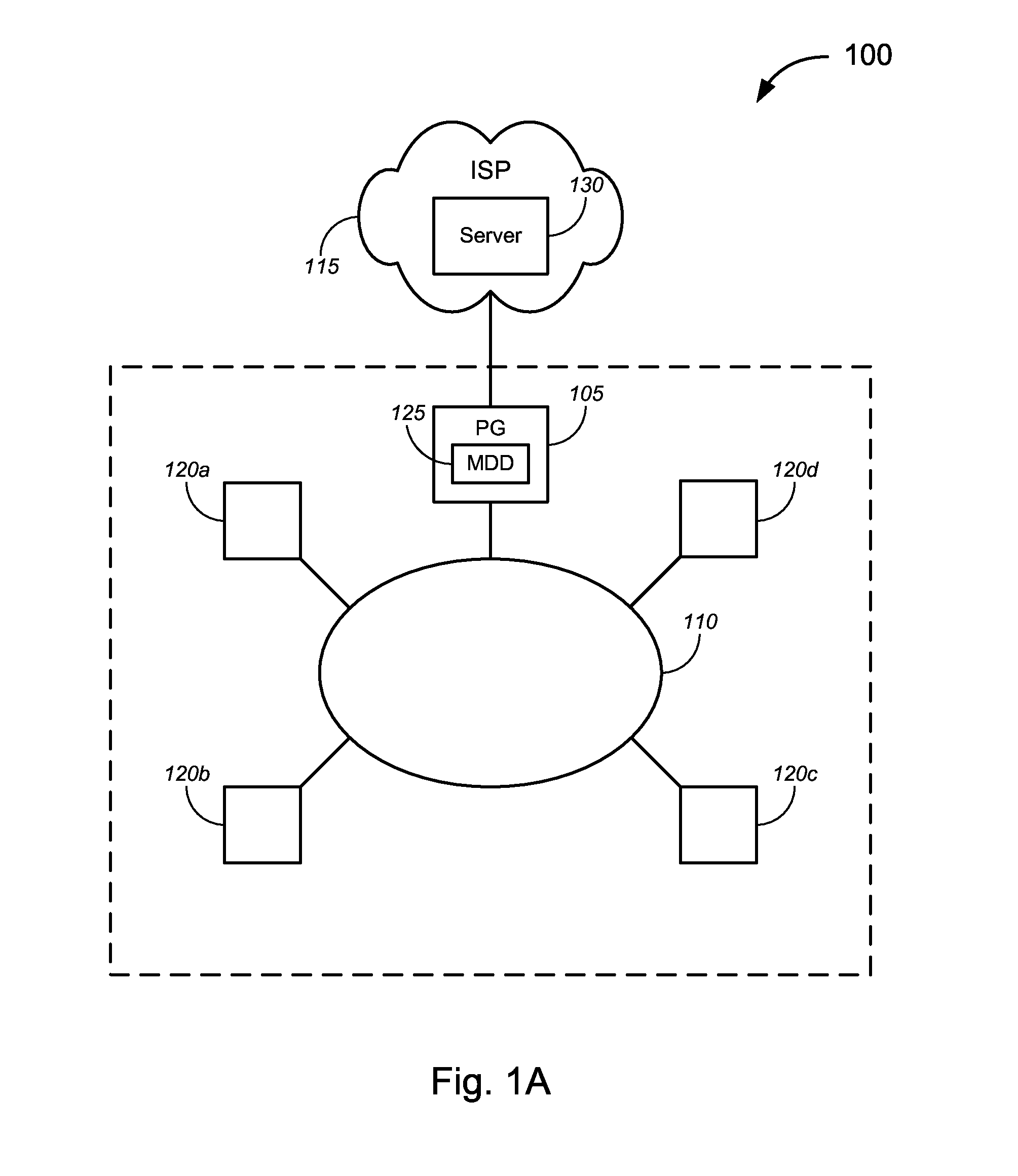
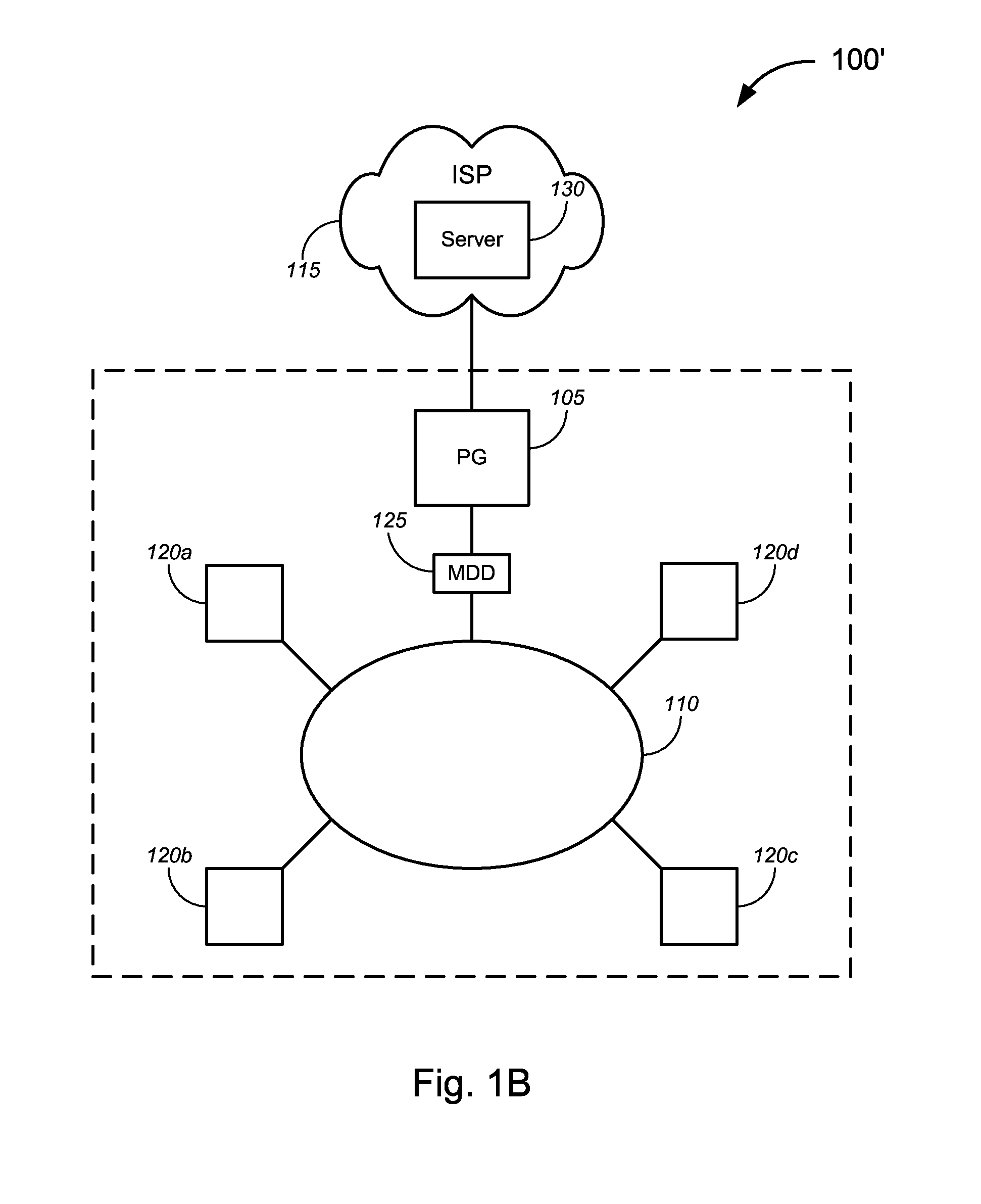
Identification of infected devices in broadband environments
ActiveUS9027138B2Small memoryEasy to disassembleMemory loss protectionUnauthorized memory use protectionComputer networkBroadband
Novel solutions for detecting and / or treating malware on a subscriber's premise network. Such solutions can include, but are not limited to, tools and techniques that can detect, and / or enable the detection of, malware infections on individual subscriber devices within the subscriber's network. In a particular embodiment, for example, a premise gateway, or other device on the subscriber's premise network, is configured to analyze packets traveling through the premise gateway and, based on that analysis, identify one or more subscriber devices that are infected with malware.
Owner:CENTURYLINK INTPROP
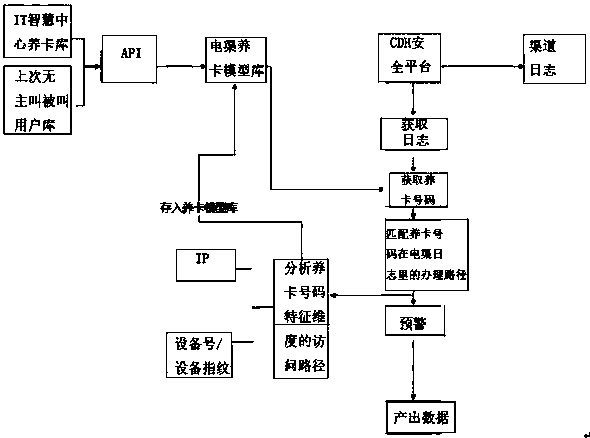
Security risk control method of raising card identification by using big data and equipment fingerprint
The invention relates to a security risk control method of raising card identification by using big data and equipment fingerprint. The method comprises the following steps: S1, establishing a raisingcard database; S2, when a user enters a platform to handle service, calling a service log of the user on the platform, obtaining a number of a telephone card associated with the user, a login equipment number and an IP according to the contents recorded in the service log, and comparing the obtained telephone card number with the number of a raising card model base; S3, obtaining the handling path of the raising card number in a telecommunication channel log, reading the equipment fingerprint used for handling the service in the log, and storing the data information of the equipment fingerprint and the handling path in a record of the raising card number; and S4, obtaining the service handling path of the user in the telecommunication channel log, and analyzing whether the service handling is preset service involving interest arbitrage. The method is small in memory occupation, high in operation speed and very low in error rate.
Owner:NANJING XINWANG VIDEO NETWORK TECH +1
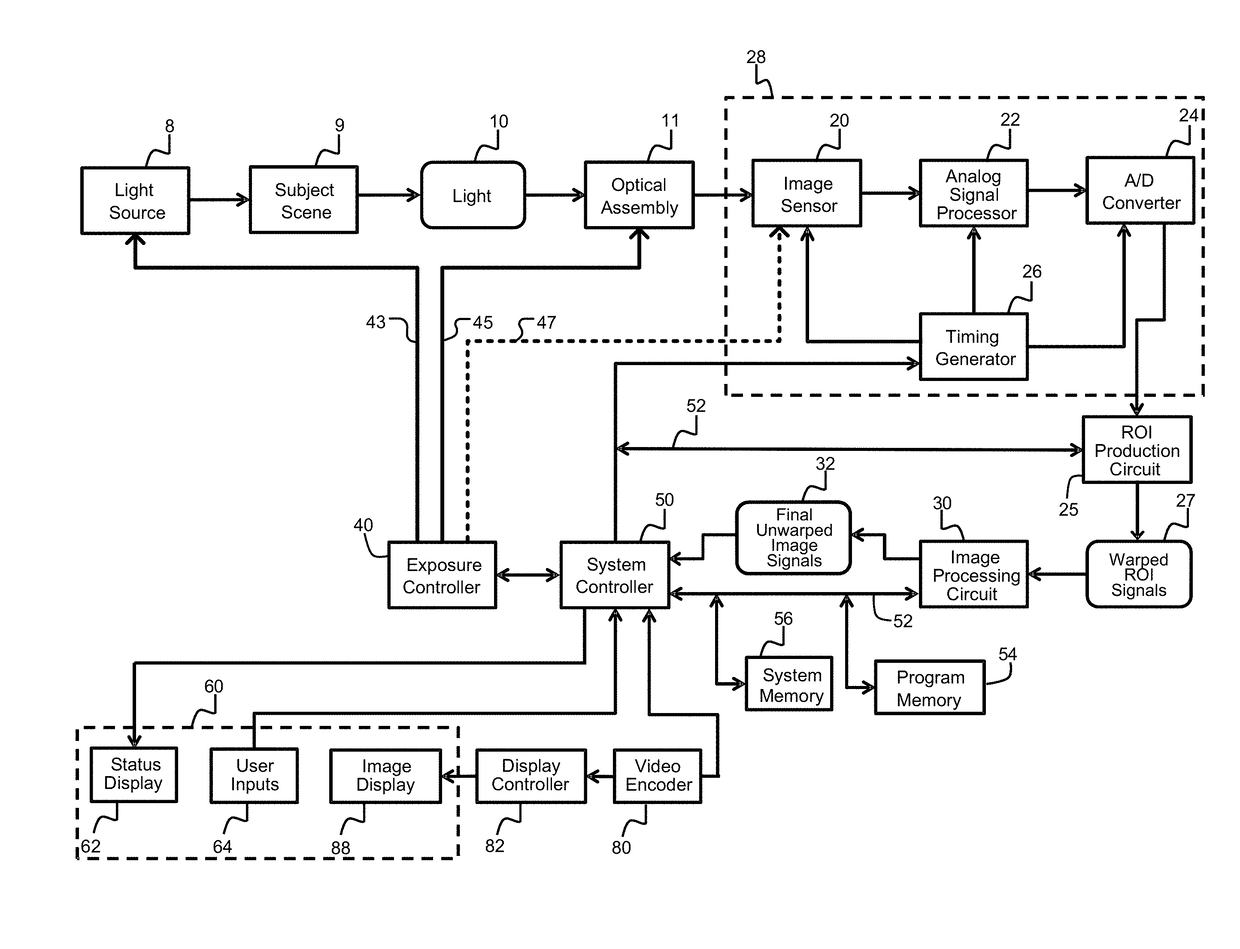
Exposure control method and system for an image capture device
ActiveUS20170230558A1Easy to controlQuick controlImage enhancementTelevision system detailsControl signalExposure control
Improved exposure control processes, devices, and systems are provided for wide angle lens imaging systems that suffer from image distortion. The exposure control uses a model of the wide angle lens distortion that estimates the weights that respective pixels of the image would have when producing an undistorted version of the image signal, and then scales pixel intensity values by the respective weights to produce weighted pixel values. The weighted pixel values are provided to an exposure control pixel counting process to produce one or more exposure feedback control signals, which control exposure features of the imaging system.
Owner:KARL STORZ IMAGING INC
Protection method and system for distributing digital files whether new, second-hand, for rental, exchange or transfer
InactiveUS20150117641A1Easy to implementSmall memoryKey distribution for secure communicationPublic key for secure communicationDigital videoVideo player
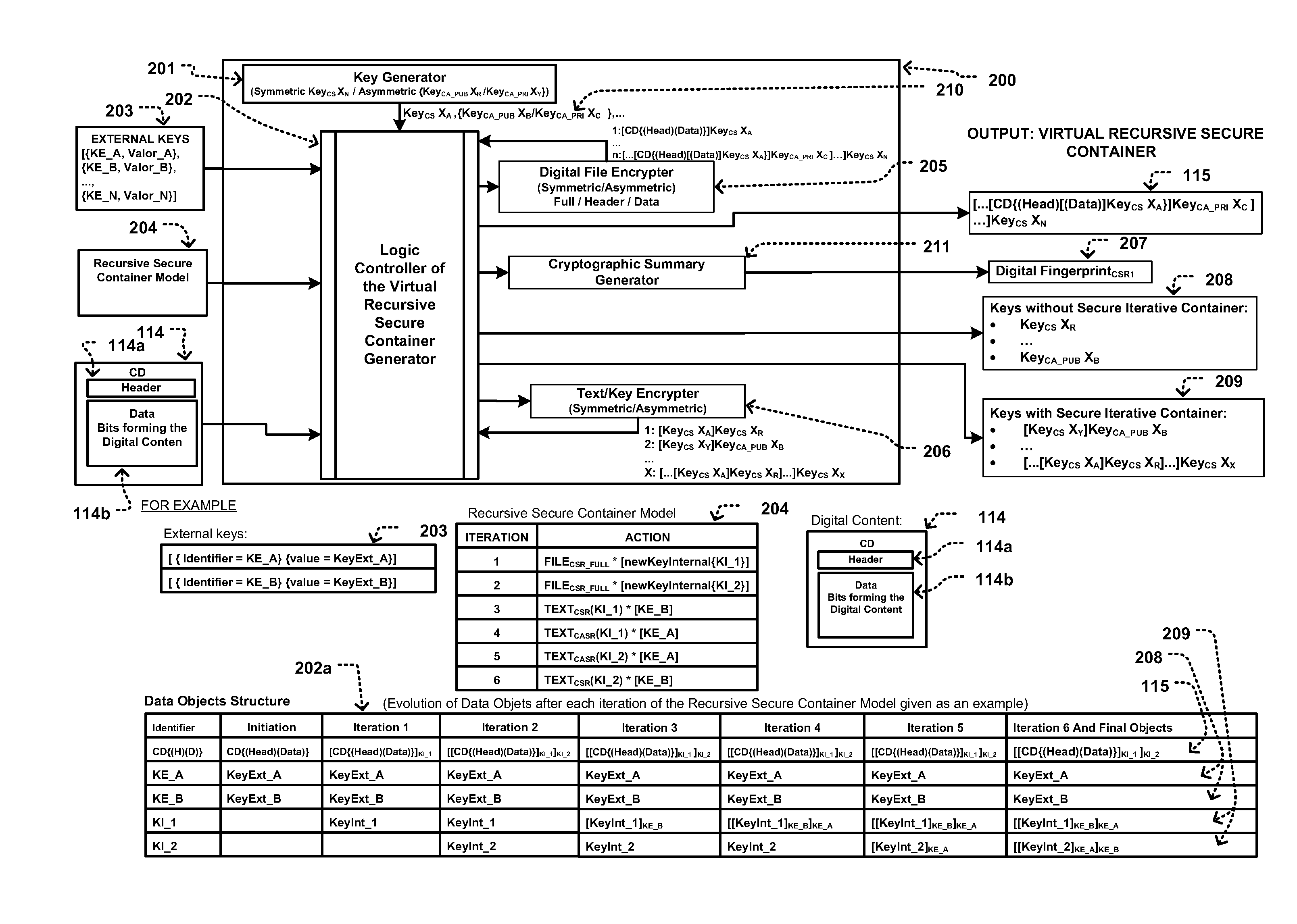
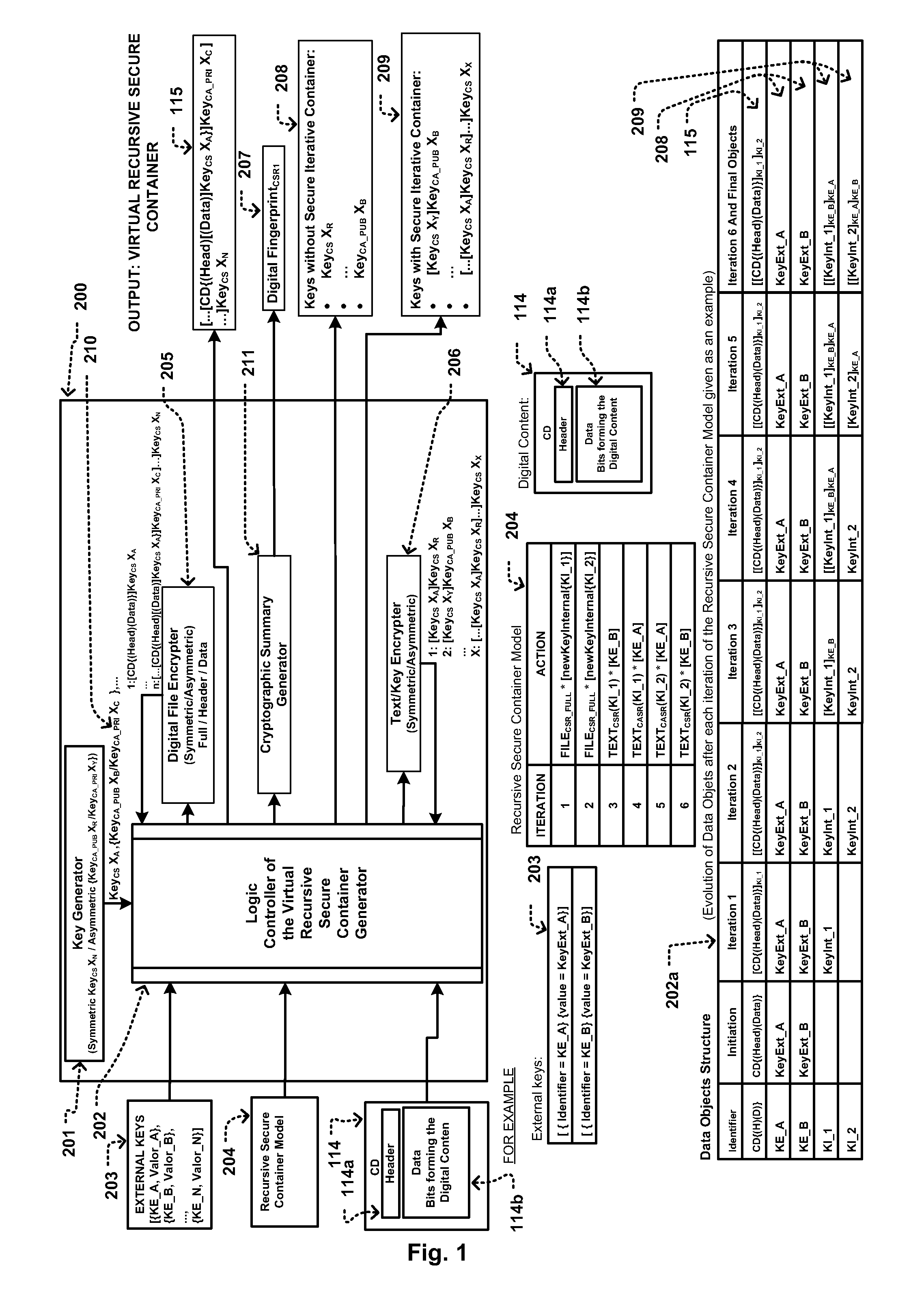
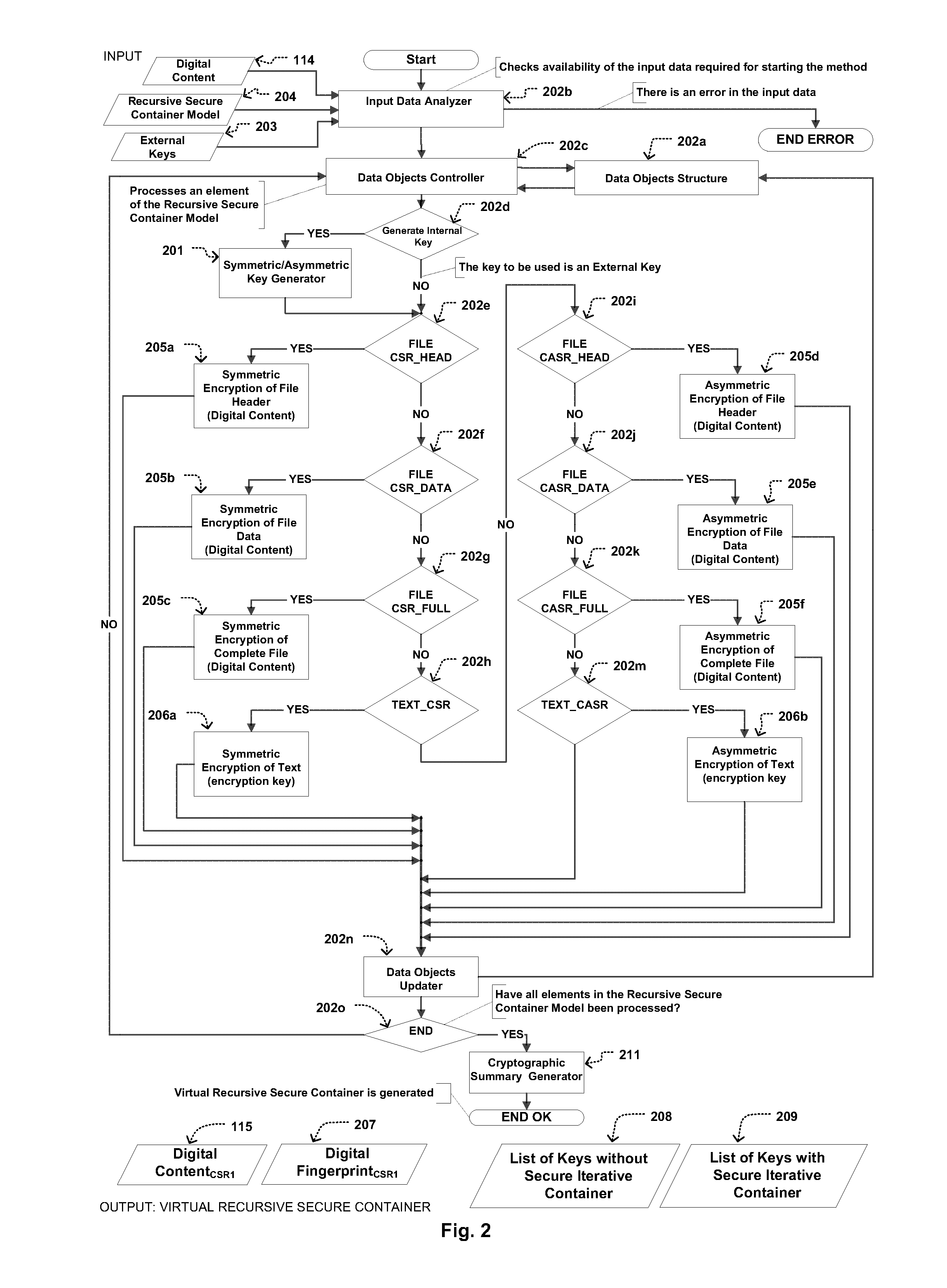
Methods for generating a virtual recursive secure container and for generating a virtual secure container of relationship of rights along with a system that distributes copyrighted digital content, respecting the legal framework for intellectual property when distributed electronically, either on the Internet or any other digital medium, and offering consumers their rights as buyers of digital content.The digital content can be of various natures, such as an electronic book, a digital video file, a digital music file, a computer application, a computer program or any digital work requiring an electronic device to be run or enjoyed, e.g. personal computer or laptop, mp3 or mp4 players, video players, mobile phones, tablets, electronic book readers, and other specialized devices.The following scenarios for digital content distribution to the user's digital device are allowed by the invention: Firsthand, secondhand (resale), rental, exchange, and temporary or permanent transfer (gift). Secondhand, exchange and transfer scenarios are only possible if the user has purchased the digital content in one of the following scenarios: Firsthand, secondhand, exchange, or transfer.The logical components of the invention, ‘Master Avatar ’ and ‘User Avatar’, which reside in the users' digital devices, create the virtual framework for relating rights of author and consumer, where the Master Avatar prevents author's rights from being violated, and the User Avatar maintains consumer's rights when purchasing digital content. By providing each avatar with a key to decrypt the data of digital content distributed through the system, the virtual link for relating the rights of author and consumer is created.The method for generating a virtual recursive secure container, that provides virtual links for relating a digital file, in combination with the distribution in a unique way of at least one of the encryption keys to a set of avatars, produces a virtual recursive secure container of relationship of rights.The invention only distributes digital content in a virtual secure container of relationship of rights of author and consumer if either the author or a licensed medium previously published that content in the system and authorized its distribution in the scenarios allowed by the system.
Owner:CARRILLO DE LA FUENTE MIGUEL ANGEL
Method for displaying high resolution picture in mobile communication terminal, mobile communication terminal and system for converting picture file format therefor
ActiveUS8379065B2Increase speedNot highly specificTelevision system detailsDigital data information retrievalComputer graphics (images)Computer terminal
The present invention discloses a method for displaying a high resolution picture in a mobile communication terminal having a low resolution display means, the mobile communication terminal and a system for converting a picture file format therefor. The method for displaying the high resolution picture in the mobile communication terminal includes the steps of: dividing picture data into a plurality of unit blocks, and converting the picture data into a picture file format including the plurality of unit block picture data and indexes for access to each of the block picture data; extracting minimum unit block picture data composing a partial picture which will be initially outputted to a display unit from the picture file by using the index information of the picture file format, and outputting the initial picture; and extracting the corresponding unit block picture data from the picture file in the movement direction by using the index information of the picture file format in accordance with generation of scroll action during the display of the picture, and outputting the position-moved picture.
Owner:SK PLANET CO LTD +1
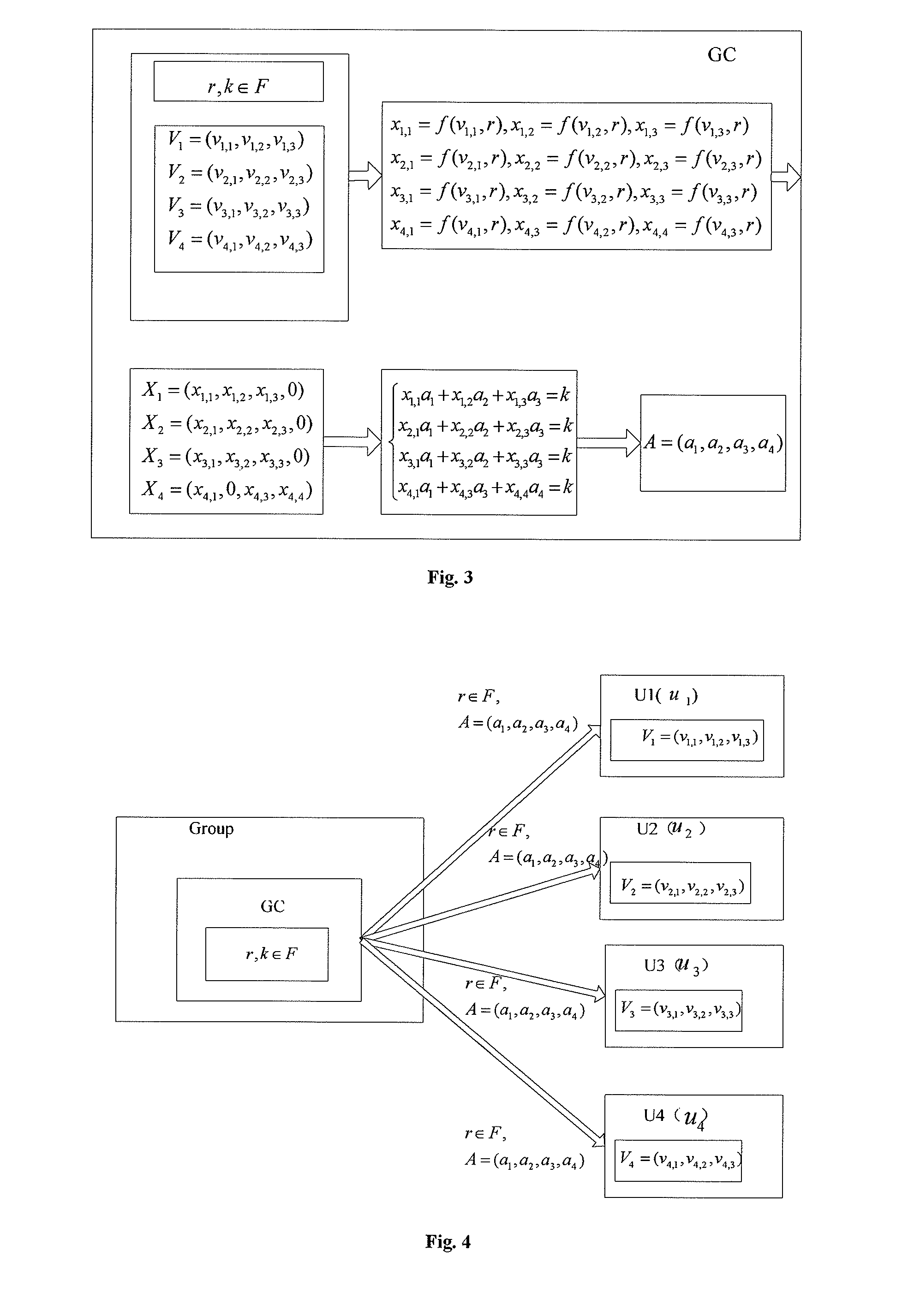
Group key management approach based on linear geometry
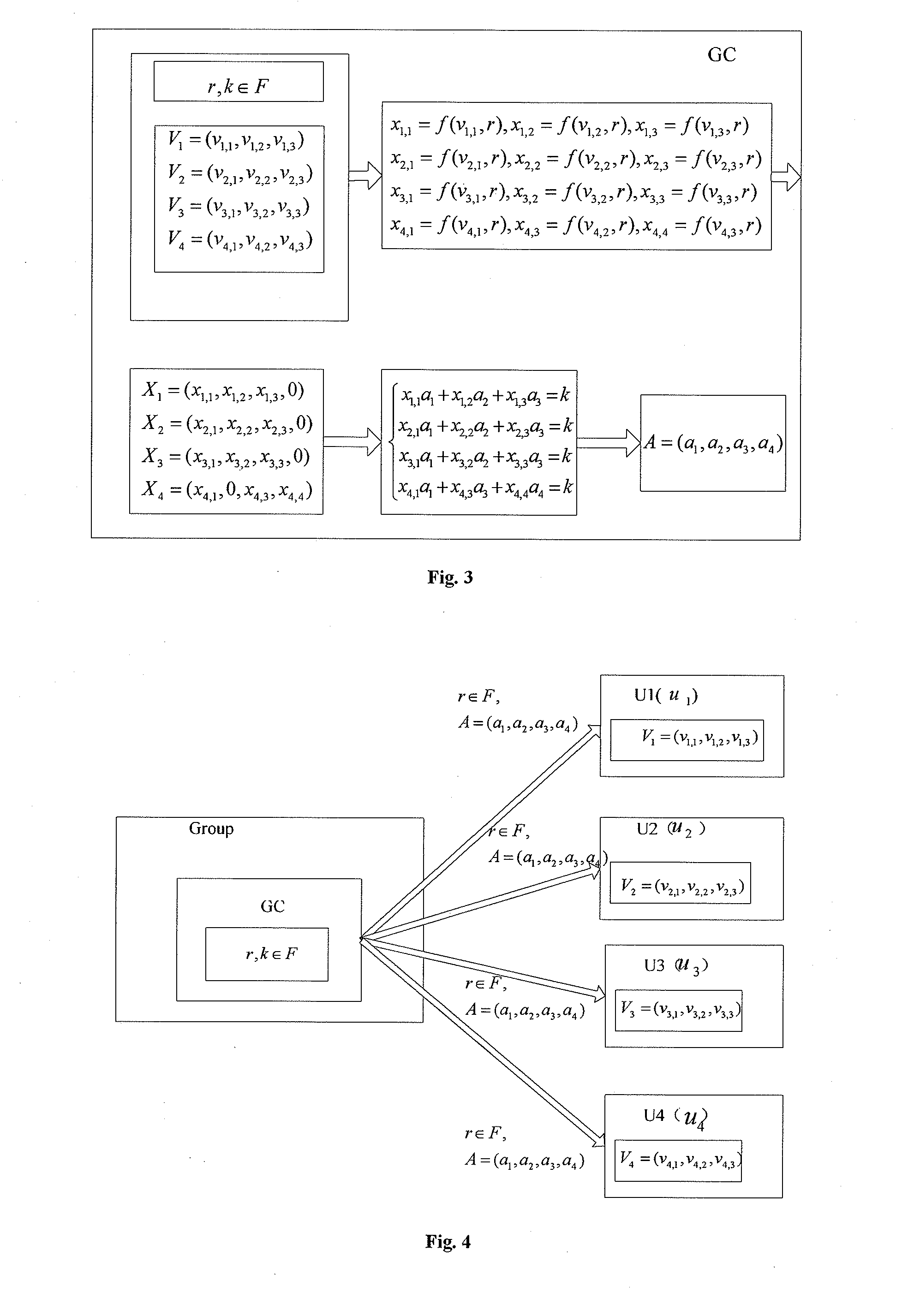
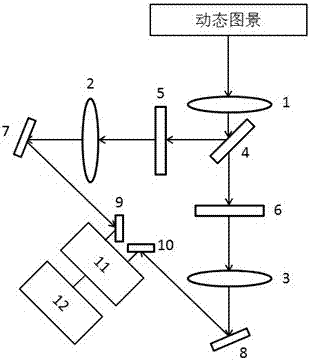
InactiveUS8848921B2Small memorySmall amount of calculationKey distribution for secure communicationComputer security arrangementsBrute forceGroup controller
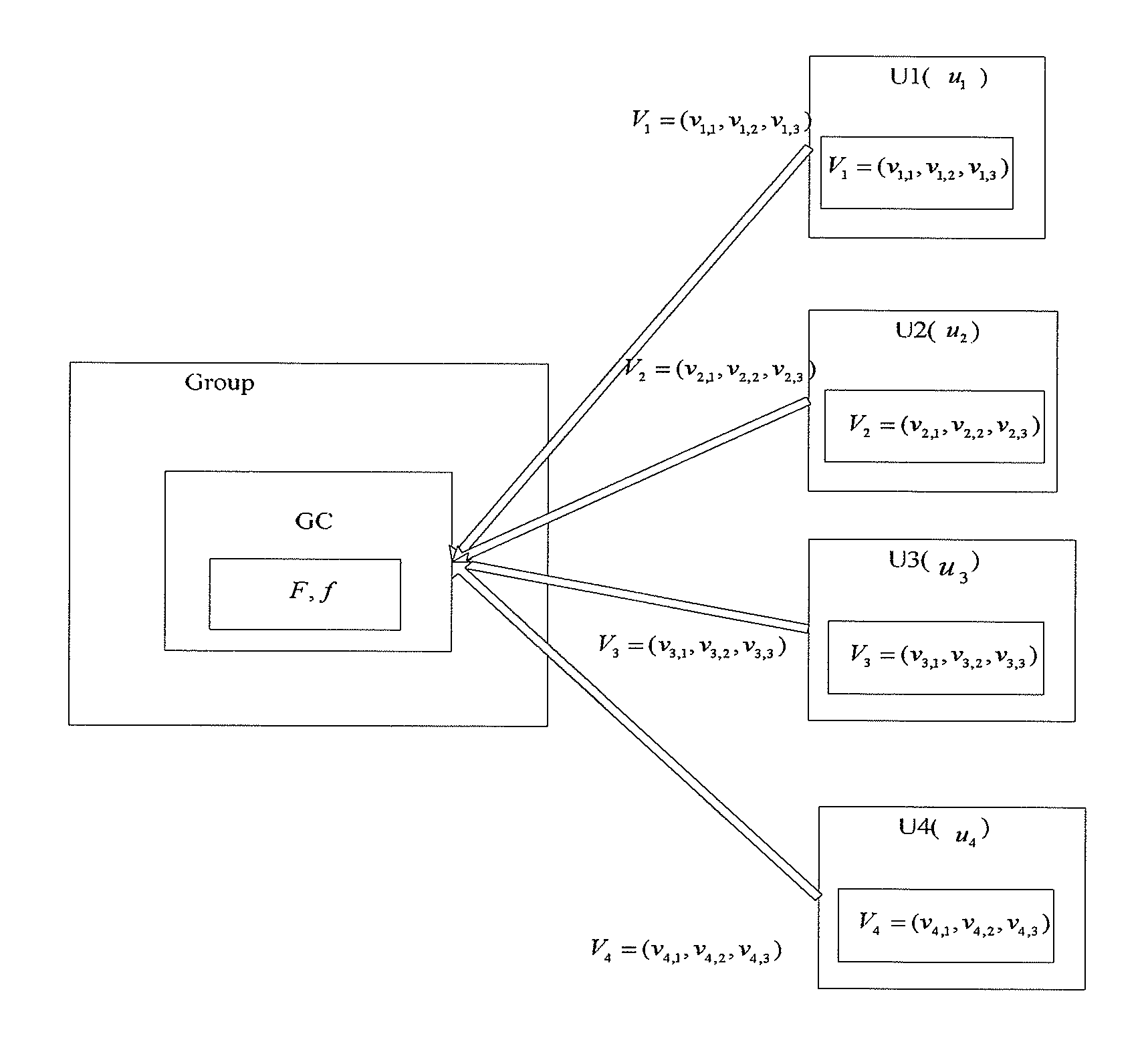
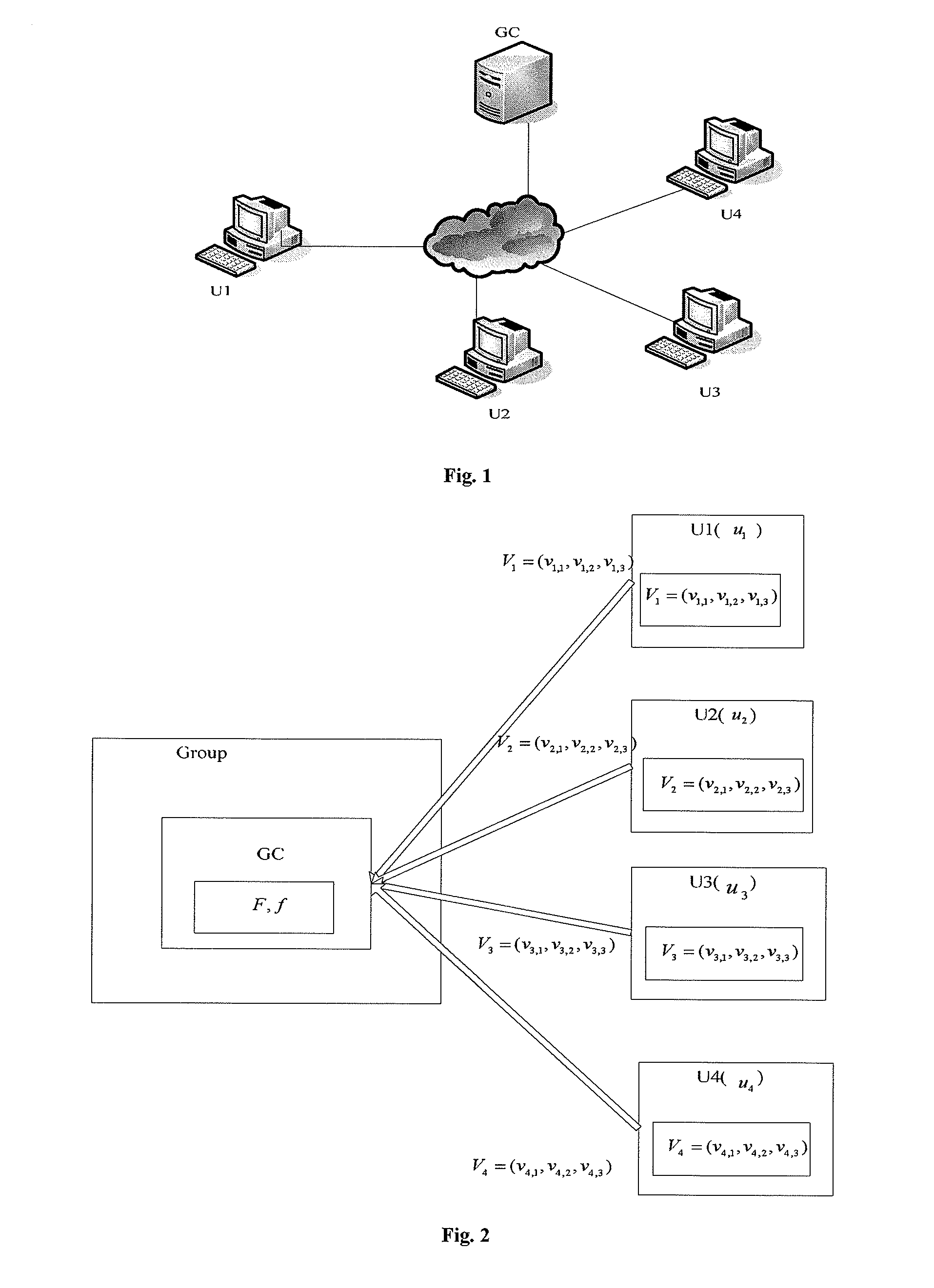
A group key management approach based on linear geometry is disclosed. The approach includes the following steps: step 1: a group controller selects a mapping f and a finite field F; each group member selects a m-dimensional private vector over the finite field F, and sends it to the group controller via secure channel; step 2: the group controller selects a mapping parameter in the finite field F randomly, and maps the private vectors of all the group members into a new set of vectors by using the mapping f according to the mapping parameter; step 3: the group controller selects a random number k in the finite field F as a group key, and constructs a system of linear equations by using the new set of vectors and the group key; the group controller computes the central vector, and sends the central vector and the mapping parameter to all the group members via open channel; step 4: after the group members receive the central vector and the mapping parameter, the private vector of each group member is mapped to a new vector in a vector space according to the mapping parameter, and the group key is obtained by calculating the inner product of the new vector and the central vector. This invention requires small memory and little computation, has high security property, and is effective against brute-force attacks.
Owner:SOUTH CHINA UNIV OF TECH
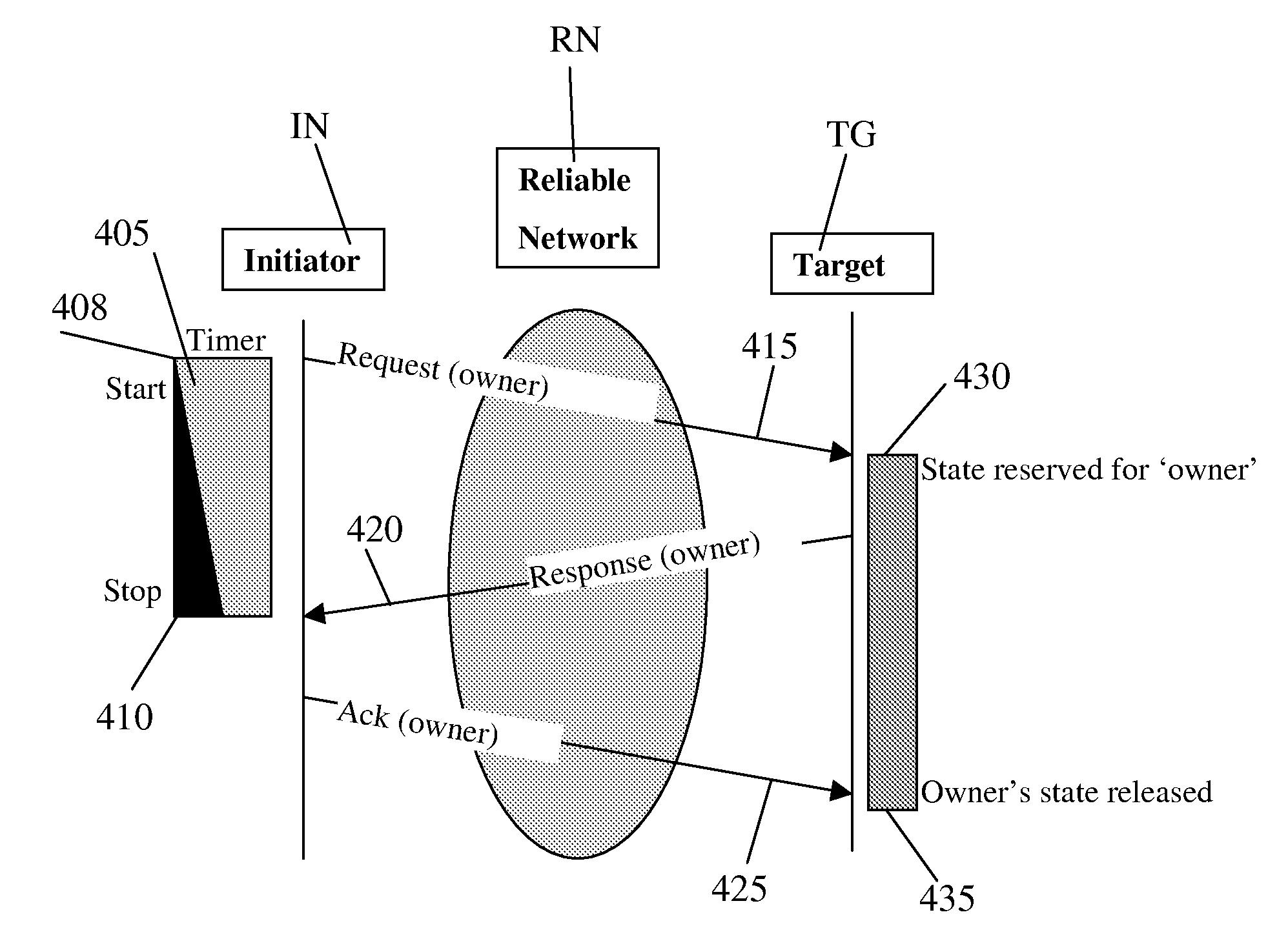
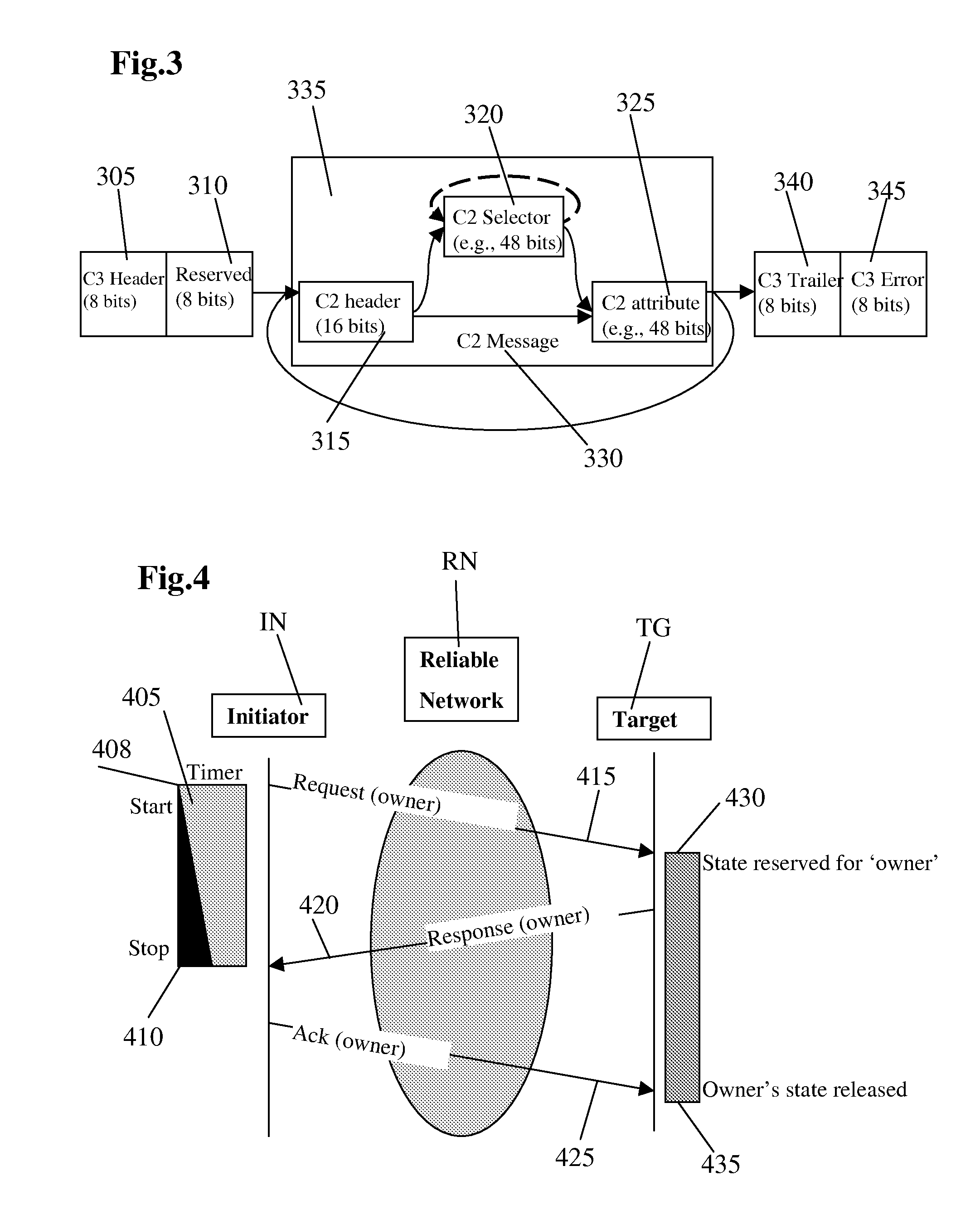
System and Method for Establishing Reliable Communication in a Connection-Less Environment
InactiveUS20120072520A1Large communication overheadComplete communication flowMultiple digital computer combinationsTransmissionTimerDistributed computing
The establishment of reliable communication, in particular in an environment of the mobile industry processor interface where communication is taking place based on the Unified Protocol is described. In this case based on the timer at the sender and based on maintaining an originator of a message at the receiver certain precautions are taken that messages are exchanged correctly and only once an acknowledgement is received from the sender, that a first and a second message have been exchanged correctly a maintained originator at the receiver is released. The same method can also be applied to sending a plurality of messages in sequence by using sequence numbers and replying to them in the same manner. In this case the timer is always restarted, once the message as a first type of message is sent from the sender side and an acknowledgement is sent after the last second type of message with a highest sequence number has been received from the receiver side. With the method and the system according to the present invention it is possible to implement the configuration protocol of the Unified Protocol even in a case where a connection-less service which is faster to use is selected. The method according to the present invention may be triggered by a bit that is set in a protocol data unit as one of the reserved bits in the header there.
Owner:ST ERICSSON SA
Method for receiving data sent in a sequence in a mobile radio system with reception gaps
ActiveUS7873051B2Simplifying reorderingAvoid spreadingSite diversityNetwork traffic/resource managementMobile Telephone ServiceResource element
Owner:SIEMENS AG
Device and method for fingerprints supervision
InactiveUS20040028261A1Simpler and cheaper device for checking fingerprintsReduce manufacturing costProgramme controlElectric signal transmission systemsFingerprintComputer hardware
A method and a device for checking fingerprints are described. The method comprises the steps of recording in succession at least two digital images of finger areas and comparing each of the recording images with a reference image that represents at least one previously recorded reference fingerprint from a reference finger areas. The device according to the invention is arranged to carry out the method.
Owner:PRECISE BIOMETRICS AB
Statement enquiring system and method capable of controlling display interface
InactiveCN101452381ASimplify the modification processSmall memorySpecific program execution arrangementsSpecial data processing applicationsStandardizationDatabase
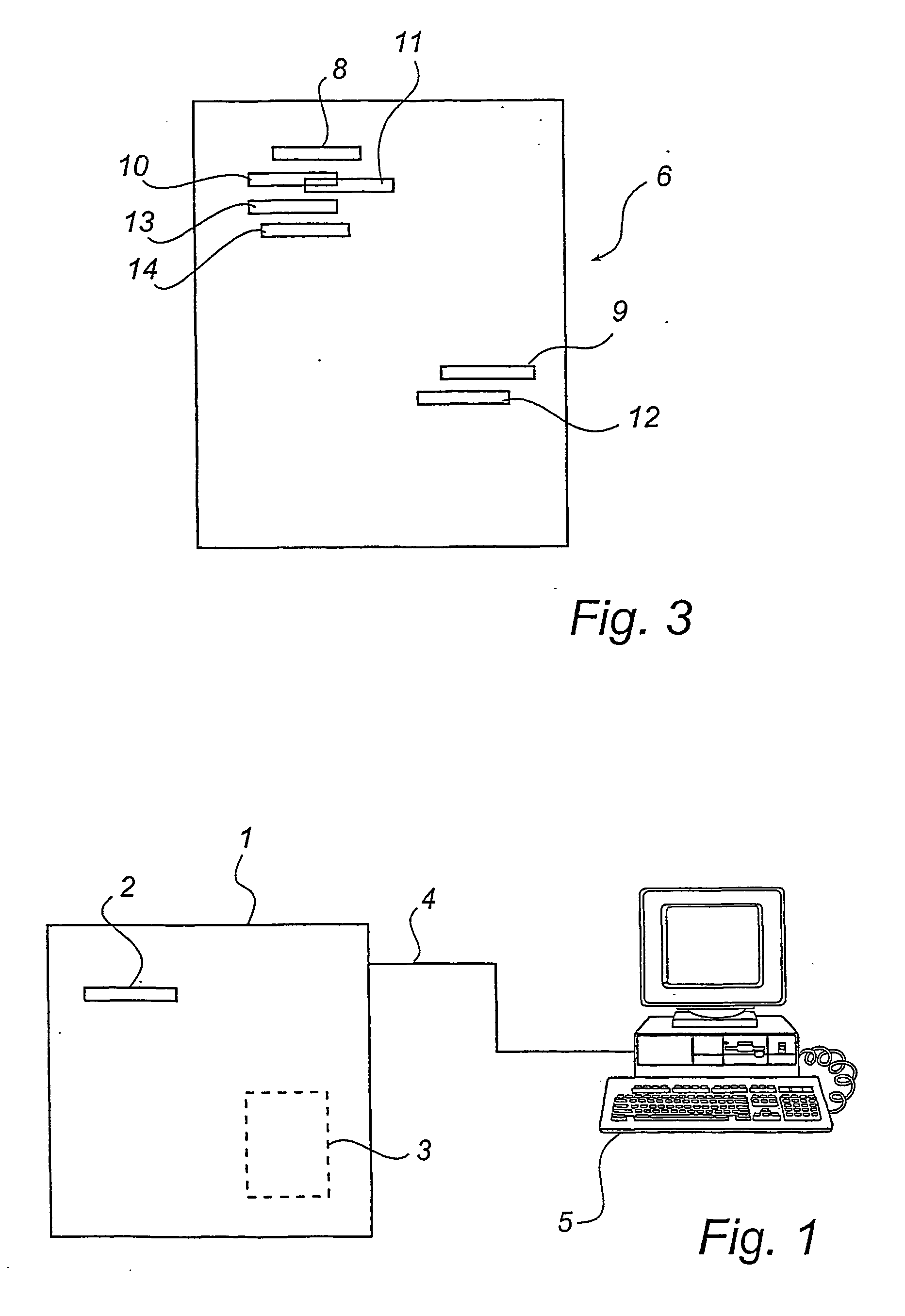
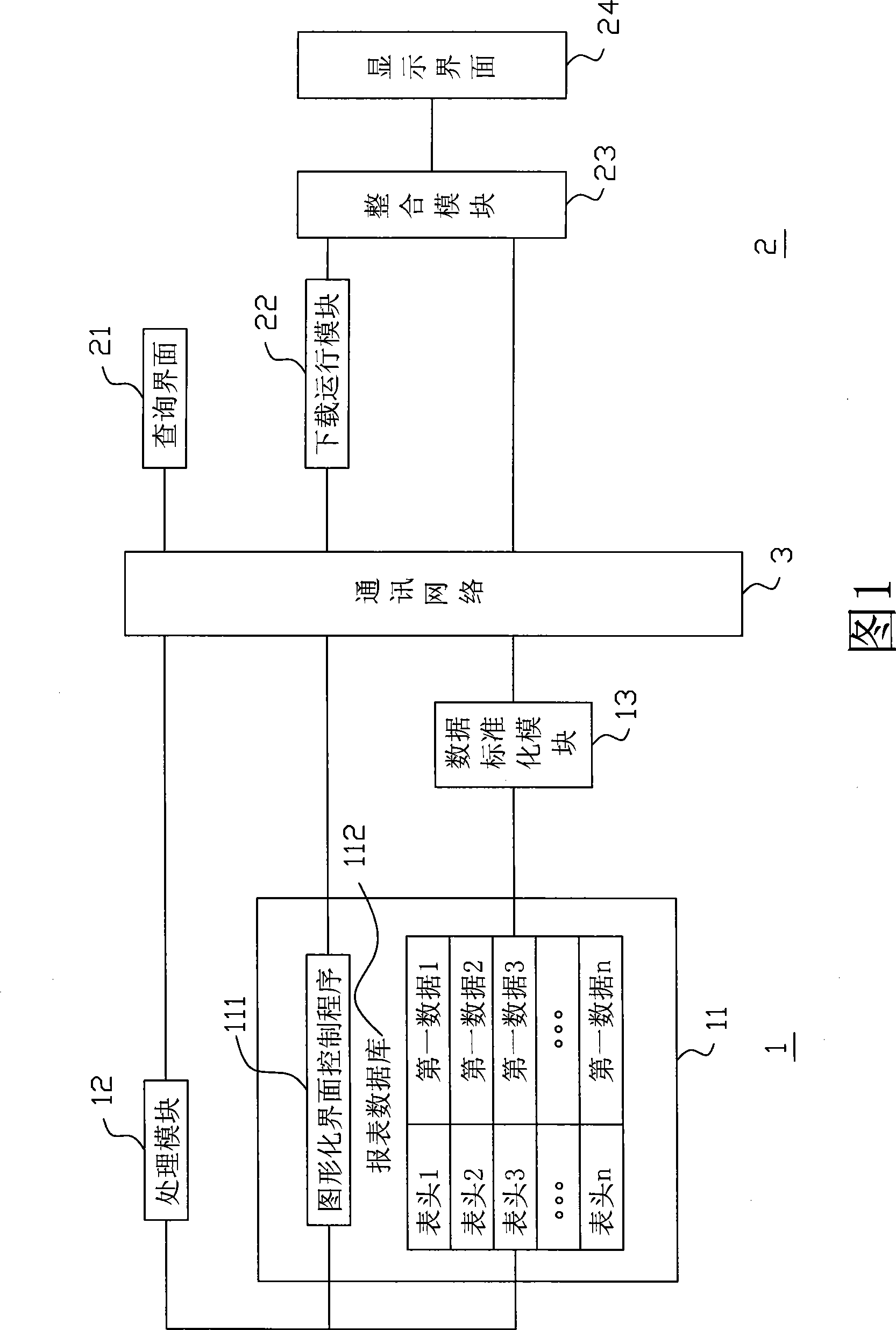
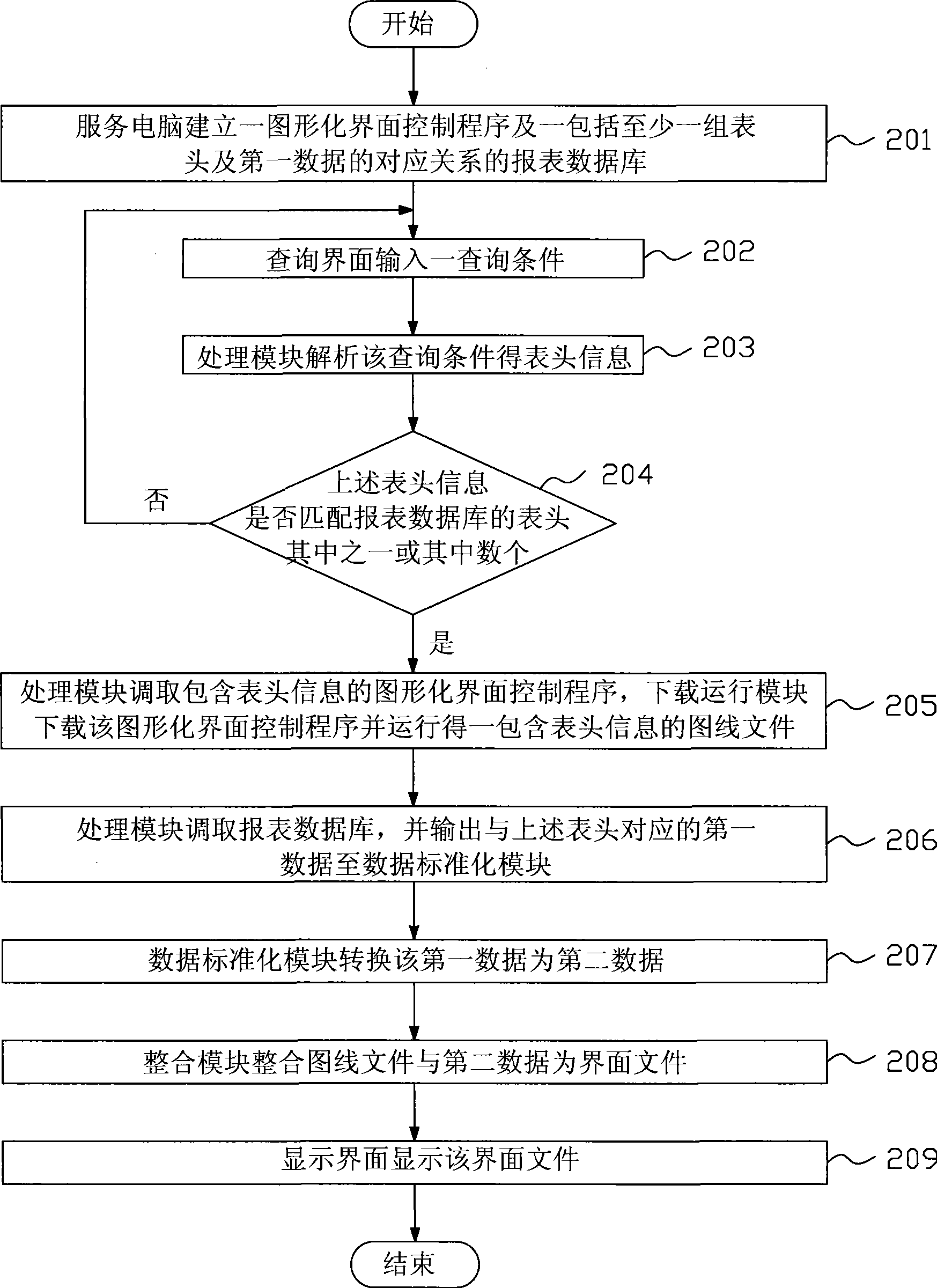
The invention provides a system and a method capable of controlling a display interface to inquire reports. The system comprises a plurality of query computers connected with a service computer through a communication network, wherein the service computer comprises a memory storing a report database and a graphic interface control program, a processing module and a data standardizing module; each query computer comprises a query interface, a download operation module, an integrating module and a display interface. The method comprises the following steps: inputting a query condition from the query interface; analyzing the query condition by the processing module to obtain header information; calling the graphic interface control program including the header information by the processing module and downloading the graphic interface control program by the download operation module to operate and obtain a figure line file; calling the report database by the processing module and outputting a first data corresponding to the header to the data standardizing module; converting the first data into a second data by the data standardizing module; and integrating the figure line file and the second data into an interface file by the integrating module and outputting the interface file to the display interface for operation and display.
Owner:HUANDA COMPUTER (SHANGHAI) CO LTD
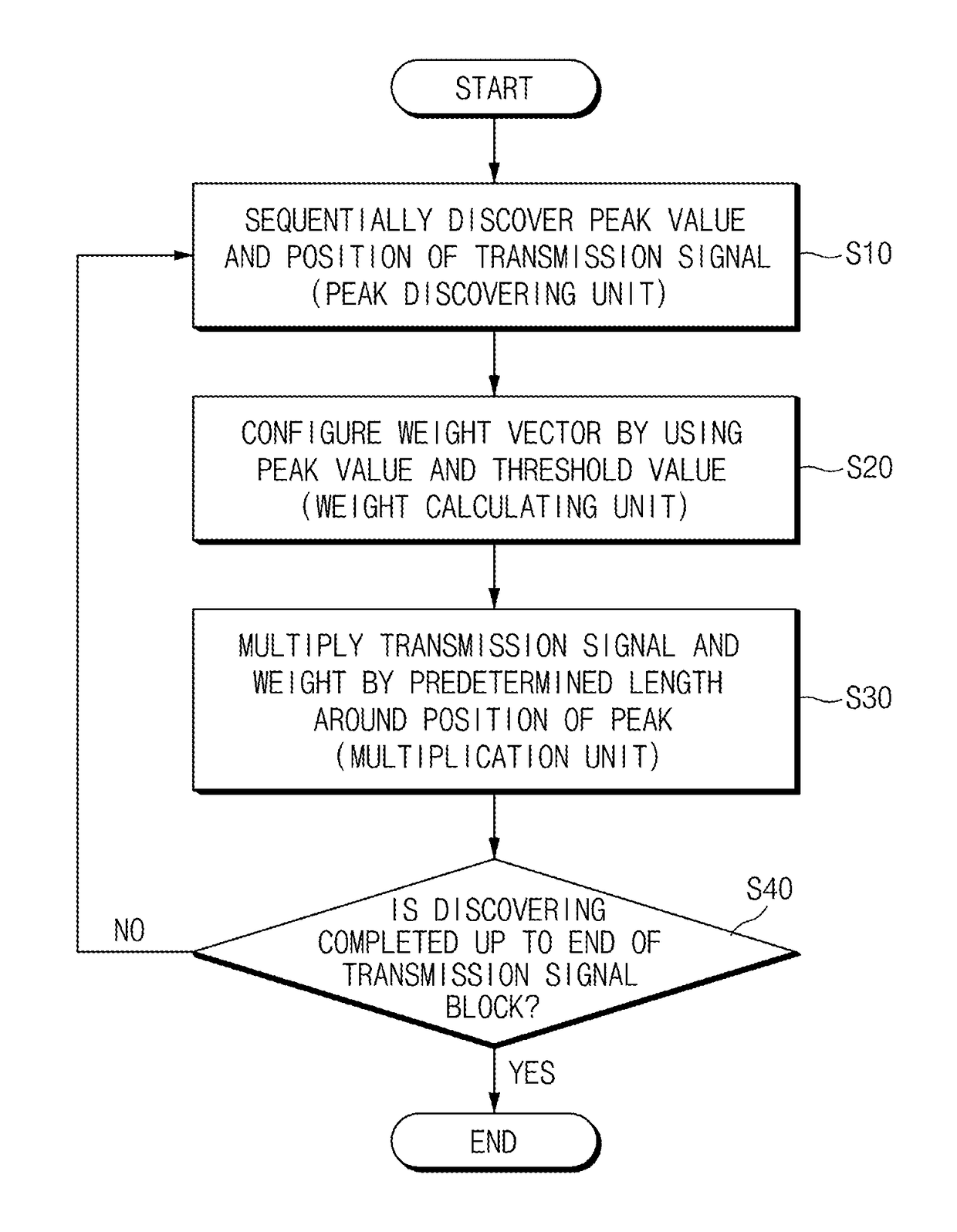
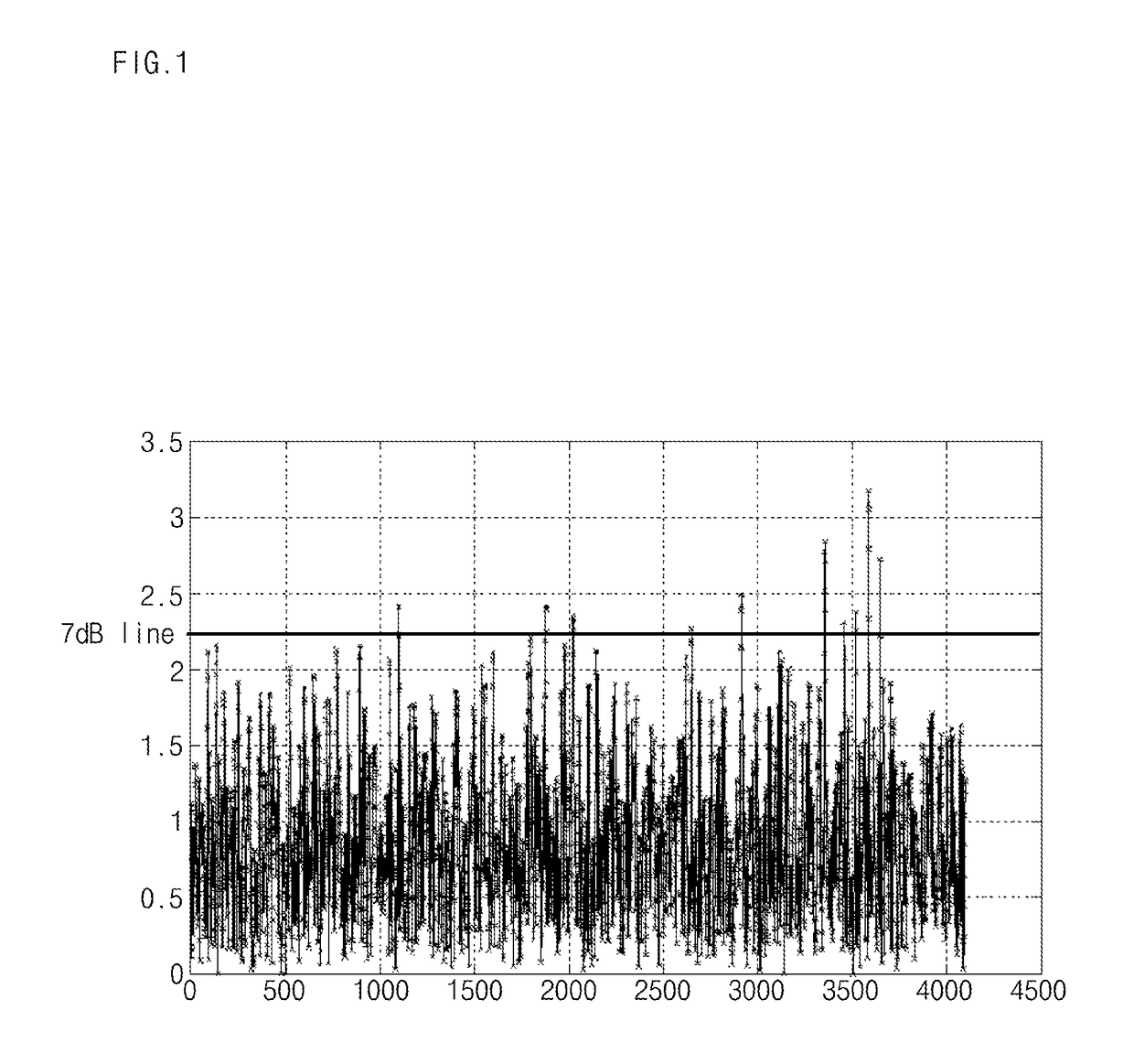
Method and apparatus for processing transmission signal for PAPR reduction in time region
ActiveUS9906392B2Small memorySmall amount of operationMulti-frequency code systemsTime domainPeak value
Provided are a method and an apparatus for processing a transmission signal, which reduce a peak value to an appropriate magnitude by appropriately distorting a final transmission signal through implementation into simple hardware having a small memory and a small operation amount to effectively reduce a peak-to-average power ratio (PAPR) by effectively processing a signal for wireless communication in real time.
Owner:ELECTRONICS & TELECOMM RES INST
Group key management approach based on linear geometry
InactiveUS20120263303A1Small memorySmall amount of calculationKey distribution for secure communicationGroup controllerBrute force
A group key management approach based on linear geometry is disclosed. The approach includes the following steps: step 1: a group controller selects a mapping f and a finite field F; each group member selects a m-dimensional private vector over the finite field F, and sends it to the group controller via secure channel; step 2: the group controller selects a mapping parameter in the finite field F randomly, and maps the private vectors of all the group members into a new set of vectors by using the mapping f according to the mapping parameter; step 3: the group controller selects a random number k in the finite field F as a group key, and constructs a system of linear equations by using the new set of vectors and the group key; the group controller computes the central vector, and sends the central vector and the mapping parameter to all the group members via open channel; step 4: after the group members receive the central vector and the mapping parameter, the private vector of each group member is mapped to a new vector in a vector space according to the mapping parameter, and the group key is obtained by calculating the inner product of the new vector and the central vector. This invention requires small memory and little computation, has high security property, and is effective against brute-force attacks.
Owner:SOUTH CHINA UNIV OF TECH
Ultrahigh-speed compression photographing device based on compression perception and streak camera principles
ActiveCN107205103AIncrease order of magnitudeImplement refactoringTelevision system detailsColor television detailsSpatial light modulatorBeam splitter
The invention provides an ultrahigh-speed compression photographing device based on compression perception and streak camera principles. The device comprises a lens, a beam splitter, a spatial light modulator, a flat mirror, a streak camera with a built-in CCD, and a decoder. Firstly, captured image information is coded through the spatial light modulator. Then the streak camera is utilized for superposing image information at different time points and performing compression sampling. Finally reconstruction is performed on the image based on a compression perception principle. According to the device, two-dimensional imaging can be performed on an ultrafast process on the condition of definite imaging speed of the streak camera; the image information is output to a decoder; a two-dimensional image dynamic process (x-y-t) is reconstructed through a TwIST algorithm; and the imaging speed can reach 10-12 frame / second. The ultrahigh-speed compression photographing device utilizes single-time photographing measuring technology which can measure un-repeated ultrafast events.
Owner:EAST CHINA NORMAL UNIV
Equalization based on digital signal processing in downsampled domains
InactiveUS7818079B2Reduce complexitySmall memorySpeech analysisTwo-channel systemsDigital signal processingEqualization
This invention relates to a device, a method, a software application program, a software application program product and an audio device for processing a digital signal, wherein the digital signal is separated and downsampled into at least two downsampled subband signals, wherein at least one of the at least two downsampled subband signals is equalized, and wherein the at least two downsampled subband signals are upsampled and combined into a digital output signal.
Owner:RPX CORP
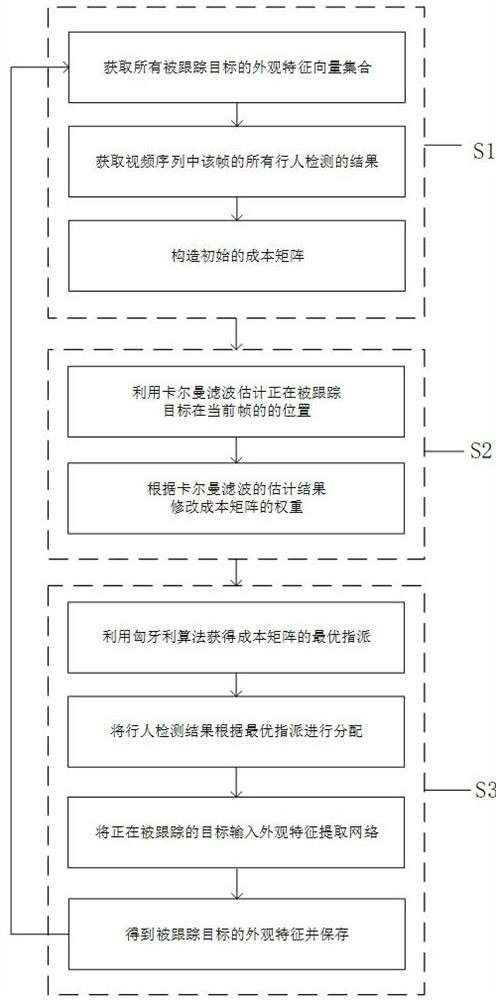
Cost matrix optimization method based on spatial constraint under Hungary algorithm
ActiveCN112528730AHigh predictive computing efficiencySmall memoryCharacter and pattern recognitionFeature vectorAlgorithm
The invention relates to a cost matrix optimization method based on spatial constraint under a Hungary algorithm, and the method comprises the steps: firstly obtaining a stored appearance feature vector set of all tracked targets, then obtaining the detection results of all pedestrians in a frame, and combining the detection results to construct an initial cost matrix; estimating the current position of the target by utilizing Kalman filtering according to the information of the tracked target, and modifying the weight of the cost matrix according to the relative relationship between the estimated position and the detection result for subsequent assignment tasks; and finally, obtaining the optimal assignment of a cost matrix by using a Hungary algorithm, allocating a detection result according to the optimal assignment, and updating and storing the appearance characteristics of the tracked target. According to the method, the matching effect of the Hungary algorithm can be effectivelyimproved according to the video scene, and some unreasonable matches are removed.
Owner:FUZHOU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com