Security risk control method of raising card identification by using big data and equipment fingerprint
A device fingerprint and security risk technology, applied in security devices, electrical components, wireless communications, etc., can solve the problems of low accuracy and large workload of the maintenance card identification method, and achieve small memory, fast running speed, and low error rate. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
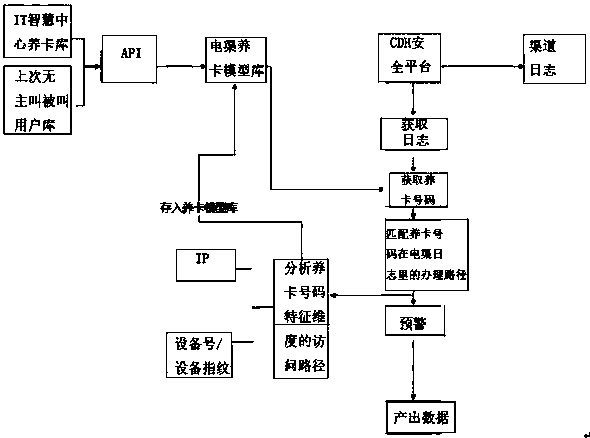
[0018] The present invention is described below in conjunction with accompanying drawing: As shown in the figure, this method first utilizes existing maintenance card warehouse, and directly introduces the resource in the maintenance card warehouse into the database of this platform so as to distinguish the maintenance card that has been recorded in the database Number. And re-identify the number that is not in the original card maintenance model library, and if it meets the conditions for card maintenance, the number will also be stored in the card maintenance database of this platform. The main process is:
[0019] S1 establishes the maintenance card database; the maintenance card database obtains the data information of the maintenance card library of the IT wisdom center and the database of no calling and no called last month through the API interface, and obtains the maintenance card number and the number of the maintenance card in the maintenance card warehouse of the IT...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com