Method and device for having access to webpage safely and downloading data through intelligent terminal
A smart terminal and secure access technology, applied in the field of network security, can solve problems such as insecurity, leakage of user private information, and insecurity of important data, and achieve the effect of preventing theft and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
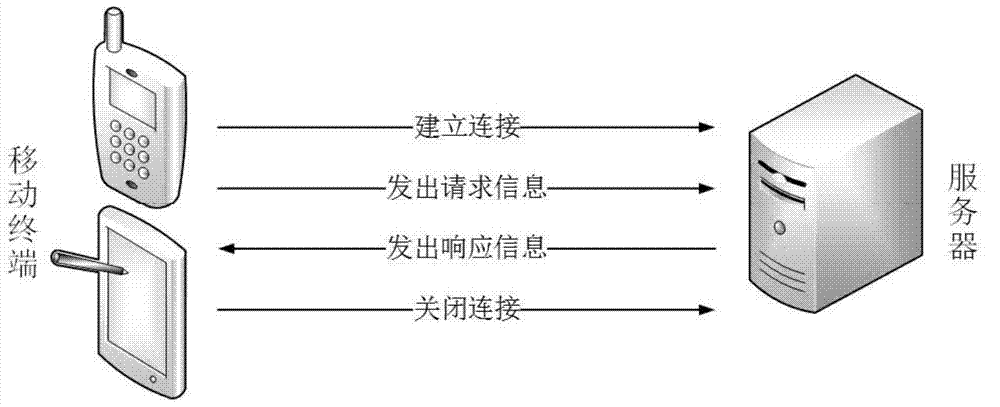
[0067] Embodiment 1 provides a secure communication method between the smart terminal and the server of the present invention.
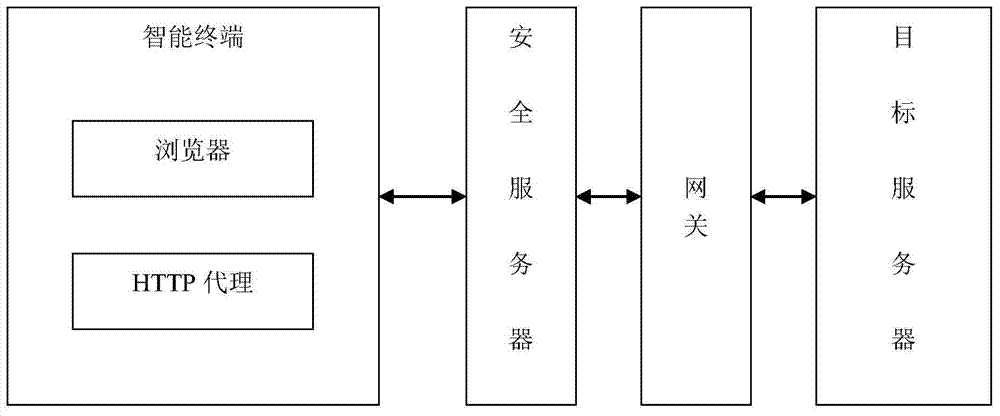
[0068] Such as image 3 As shown, it shows the overall structure diagram of the communication between the client and the target server of the present invention. Wherein, the client represents the current mobile smart terminal device, which may be a smart phone, a PDA, a tablet computer, a notebook computer or any other portable mobile communication device. And in order to solve the problem that the secure browser can send and receive ciphertext data normally, it is necessary to set up an HTTP proxy server locally on the client side, which is responsible for deciphering the data instead of the browser, sending the encrypted data to the target server through the gateway, and at the same time responsible for the target server. The data sent by the server to the client is decrypted, the decrypted data is sent to the client, and finally to the browser. ...
Embodiment 2
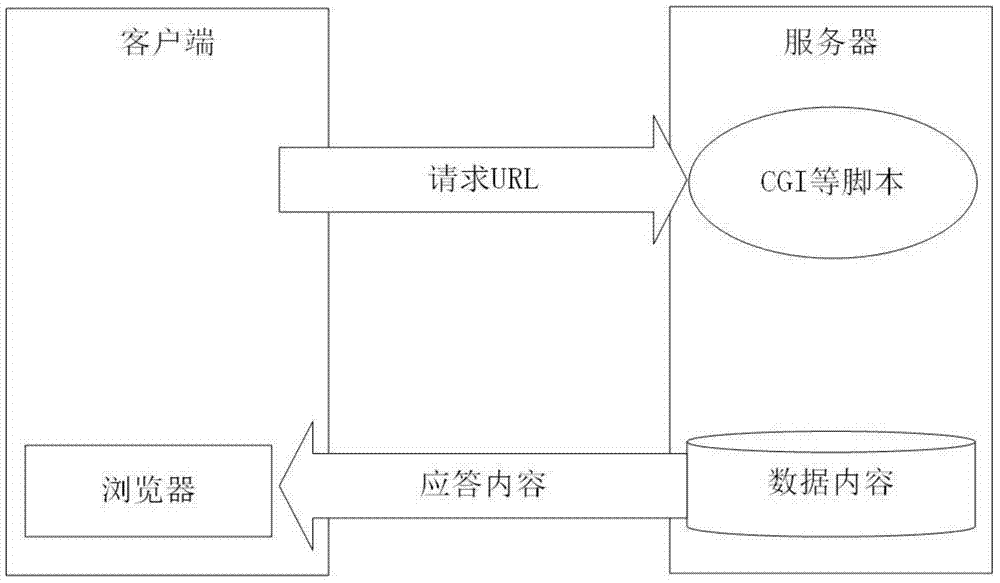
[0082] attached Figure 5 shows through Figure 4 A method for downloading files through a public secure browser data channel, the method comprising the following steps:
[0083] 1. The user visits the page with a secure browser and clicks on a link to request to open a file
[0084] 2. First judge whether the file already exists locally, if it exists, ask whether it needs to be overwritten and downloaded, if not, decrypt the file and display it. If the download is overwritten, it is as follows in point 3.
[0085] 3. Request the file from the target server, encrypt and store the returned request data locally, and use the ADE encryption algorithm to encrypt the file data stored locally.
[0086] 4. Decrypt and display the local files.
[0087] The files downloaded through the secure browser are encrypted and stored locally, and the files can only be viewed after identification. Therefore, if the mobile terminal is lost, the authorized user of the terminal cannot view the f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com