Apparatus and method for identity-based encryption within a conventional public-key infrastructure
a public key and identity-based encryption technology, applied in the trust model of public key infrastructure, television system, instruments, etc., can solve the problems of public keys that are far too large for people to remember, elliptic curve keys, and certificates that are much shorter than traditional ones, so as to avoid security problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
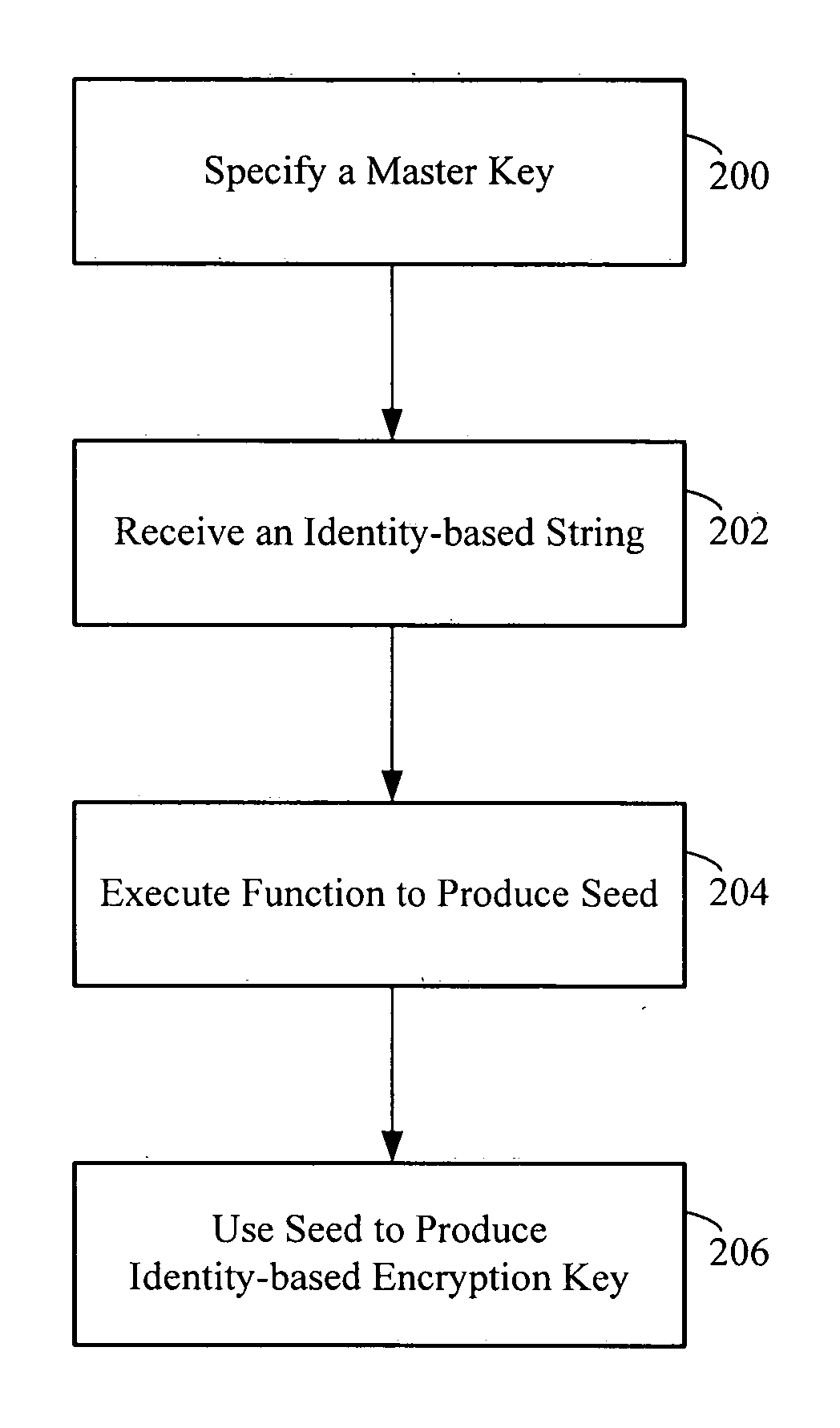
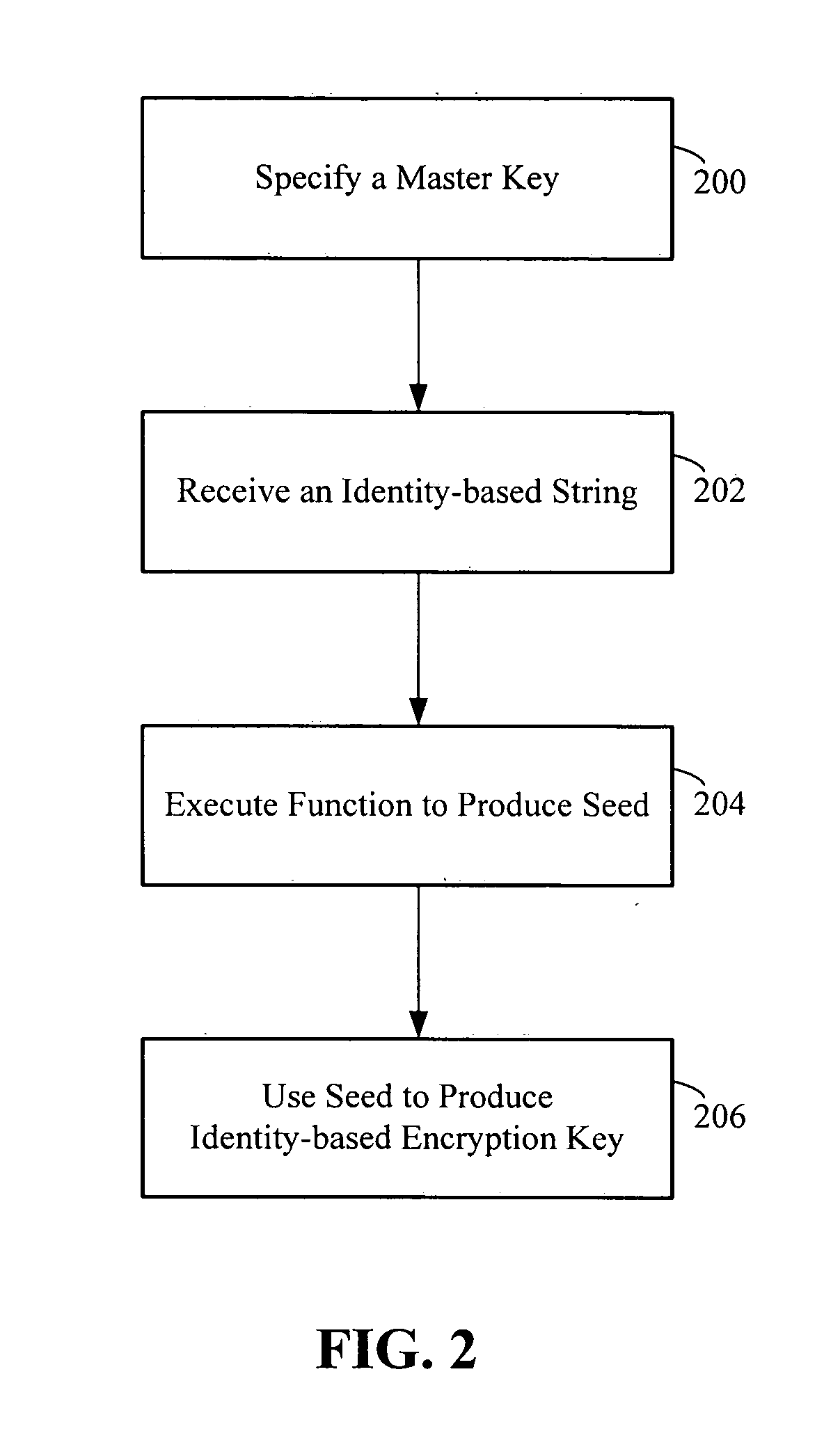
[0028] Identity-Based Encryption (IBE) can also be thought of as an Attribute-Based Enrollment mechanism. Its goal is to reduce the overhead required to bring an entity into the system. The overhead is reduced by taking some attribute of the entity and use that attribute as a functional equivalent to a public key. An embodiment of the invention is directed toward the enrollment aspect of IBE. This enrollment mechanism results in many of the advantages associated with the invention. The invention constructs an IBE from well-known components that have easily-understood security constraints, including proofs of security. Thus, the invention provides an adaptive framework for constructing an IBE system that is not bound to a single algorithm and is functional even in the face of security advances such as new attacks on hash functions.
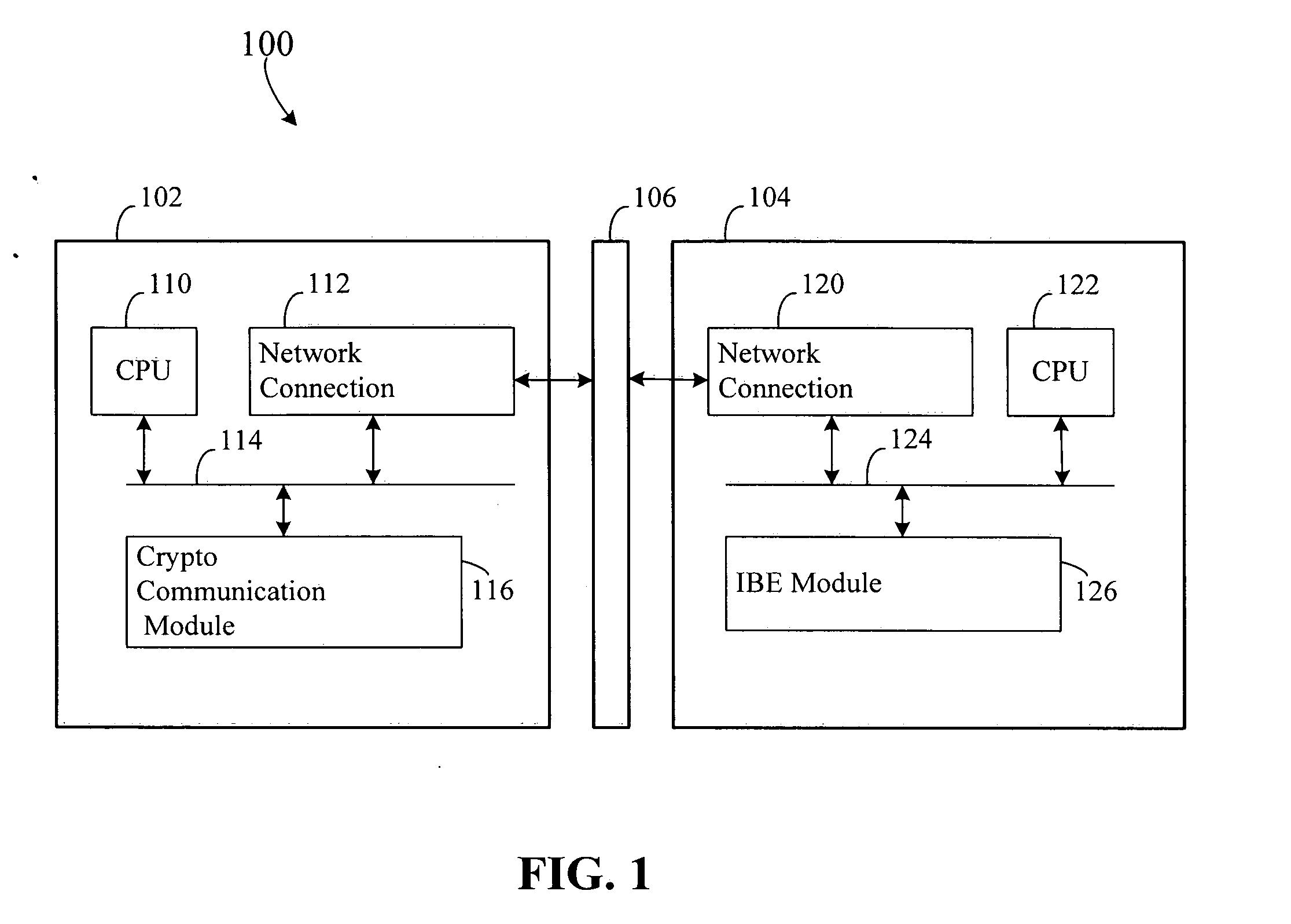
[0029]FIG. 1 illustrates a network 100 configured in accordance with an embodiment of the invention. The network 100 includes a client computer 102 connec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com