Method for realizing safe access of terminal of internet of thing
An IoT terminal and secure access technology, applied in the IoT field, can solve the problem of a large number of IoT terminals, achieve fast automatic access, and prevent illegal terminal access.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
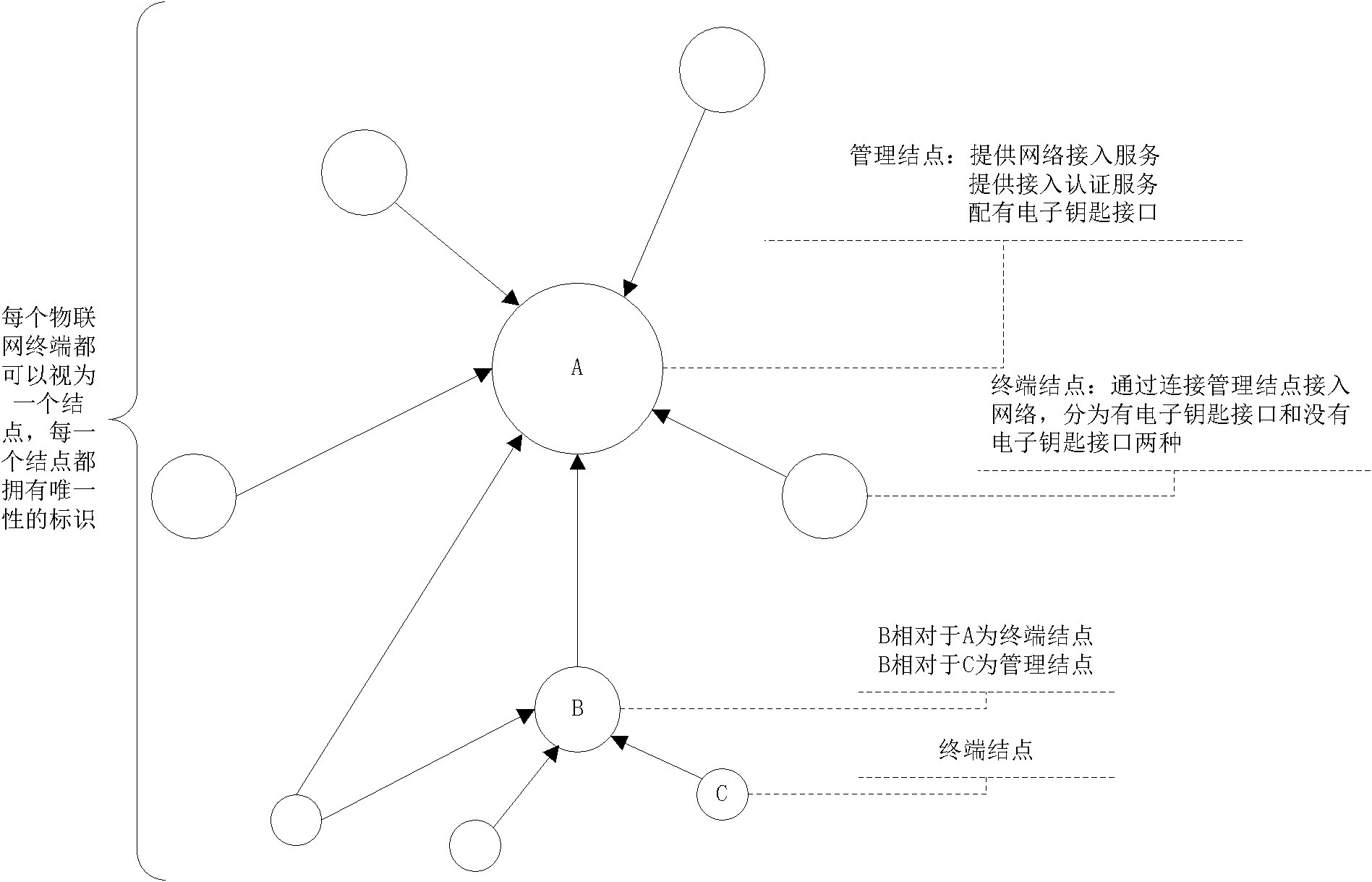
[0049] see figure 1 , the present invention discloses a method for realizing secure access of Internet of Things terminals, by formulating an interconnection scheme of Internet of Things nodes and cooperating with electronic keys to achieve security management of Internet of Things nodes, so as to realize secure access of Internet of Things terminals. The content of the interconnection scheme includes defining node attributes, electronic key attributes, electronic key authorization lists, terminal authorization lists, formulating authentication methods, authorization methods and access methods.
[0050] After each terminal is connected to the network, it is a node in the network. Such as figure 1 As shown, each node has a unique identifier, and the node providing network access service can be used as a management node, and the management node must be equipped with an electronic key interface. Nodes that are directly connected to the management node to access the network are ...
Embodiment 2
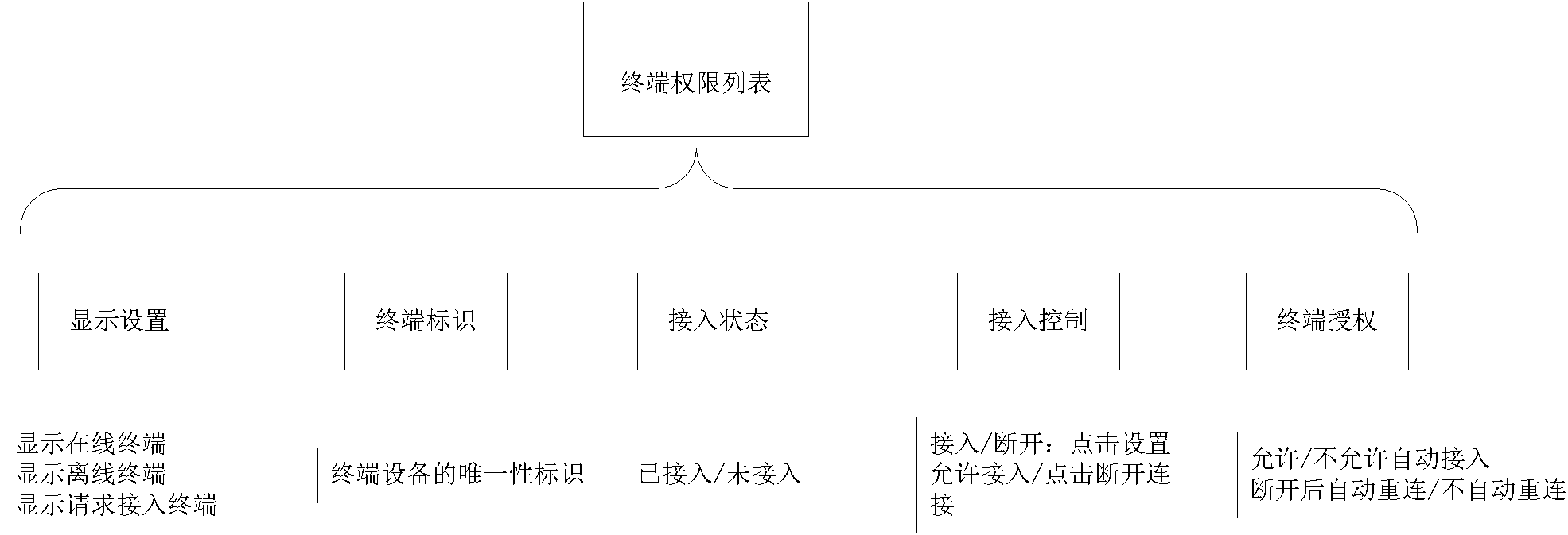
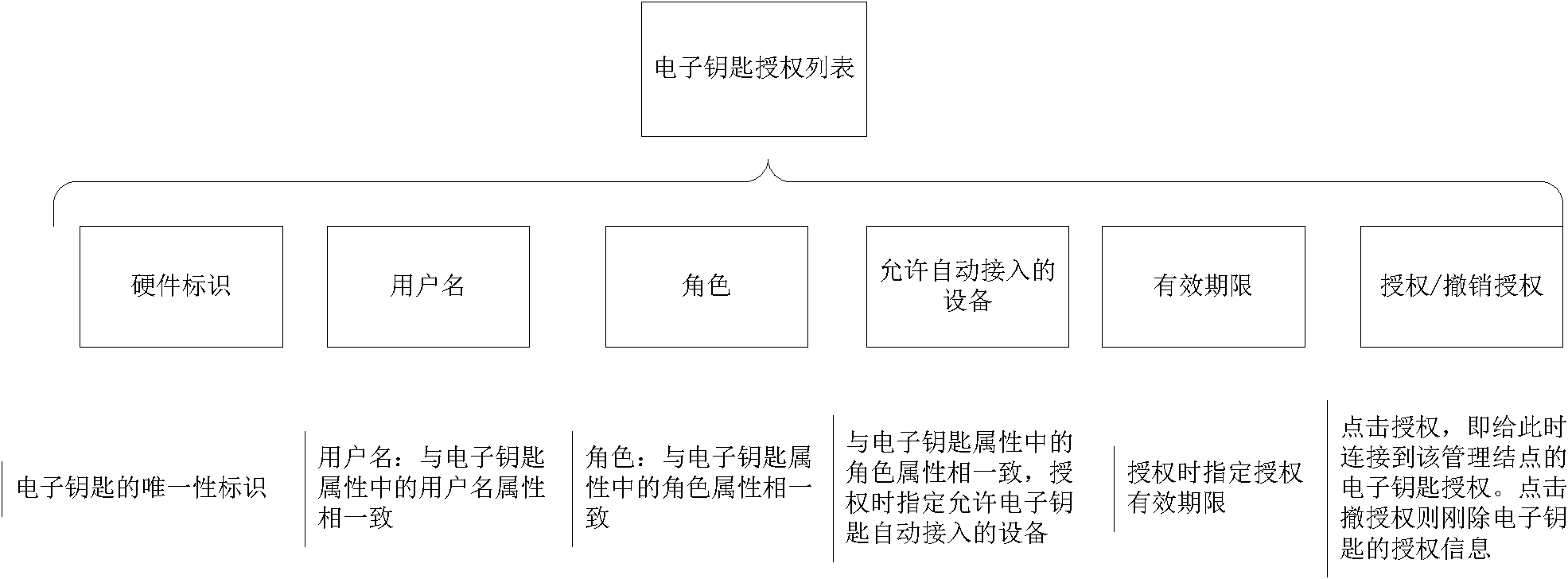
[0077] According to the requirements of the rules, the standard electronic key interface is specified. This example uses the USB2.0 interface, and the electronic key uses a USB dongle. The management program is installed in the management node to provide a web management interface. The management program provides authentication, authorization and maintenance authorization information. features (including figure 2 , image 3 shown). Install the USB dongle interactive program on the terminal node.
[0078] Terminal access method without USB interface:
[0079] 1. Set to allow the automatic access in the terminal permission list of the management node
[0080] 2. Manually access in the management node terminal permission list
[0081] Terminal access method with USB interface:
[0082] 1. Set to allow the automatic access in the terminal permission list of the management node
[0083] 2. Manually access in the management node terminal permission list
[0084] 3. Authorize...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com