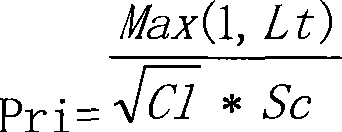Patents
Literature
79 results about "Information audit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The information audit (IA) extends the concept of auditing holistically from a traditional scope of accounting and finance to the organisational information management system. Information is representative of a resource which requires effective management and this led to the development of interest in the use of an IA.
Method and system for detecting hostile attack on Internet information system
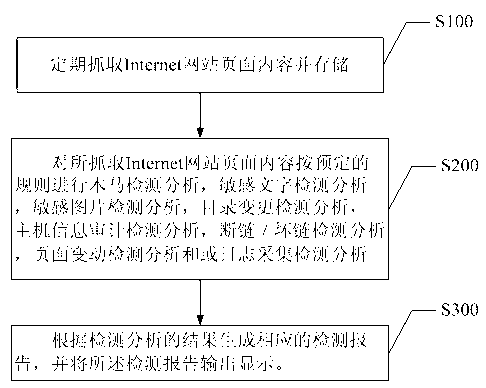
ActiveCN103281177AComprehensive detectionImprove securityMultiple keys/algorithms usagePlatform integrity maintainanceText detectionThe Internet
The invention discloses a method and a system for detecting a hostile attack on an Internet information system. The method comprises the following steps: A, regularly crawling and saving the content of an Internet web page; B, conducting a Trojan detection analysis, a sensitive word detection analysis, a sensitive image detection analysis, a directory change detection analysis, a host information audit detection analysis, a broken link / wrong link detection analysis, a page change detection analysis and / or log collection detection analysis to the crawled content of the Internet web page according to a predefined rule; and C, according to the results of the detection analyses, generating corresponding detection reports, and outputting and displaying the detection reports. The method for detecting the hostile attack on the Internet information system has the advantages that the detection is comprehensive, the defection safety is increased, the workload is reduced, the human cost is reduced, and the method provides convenience for users.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
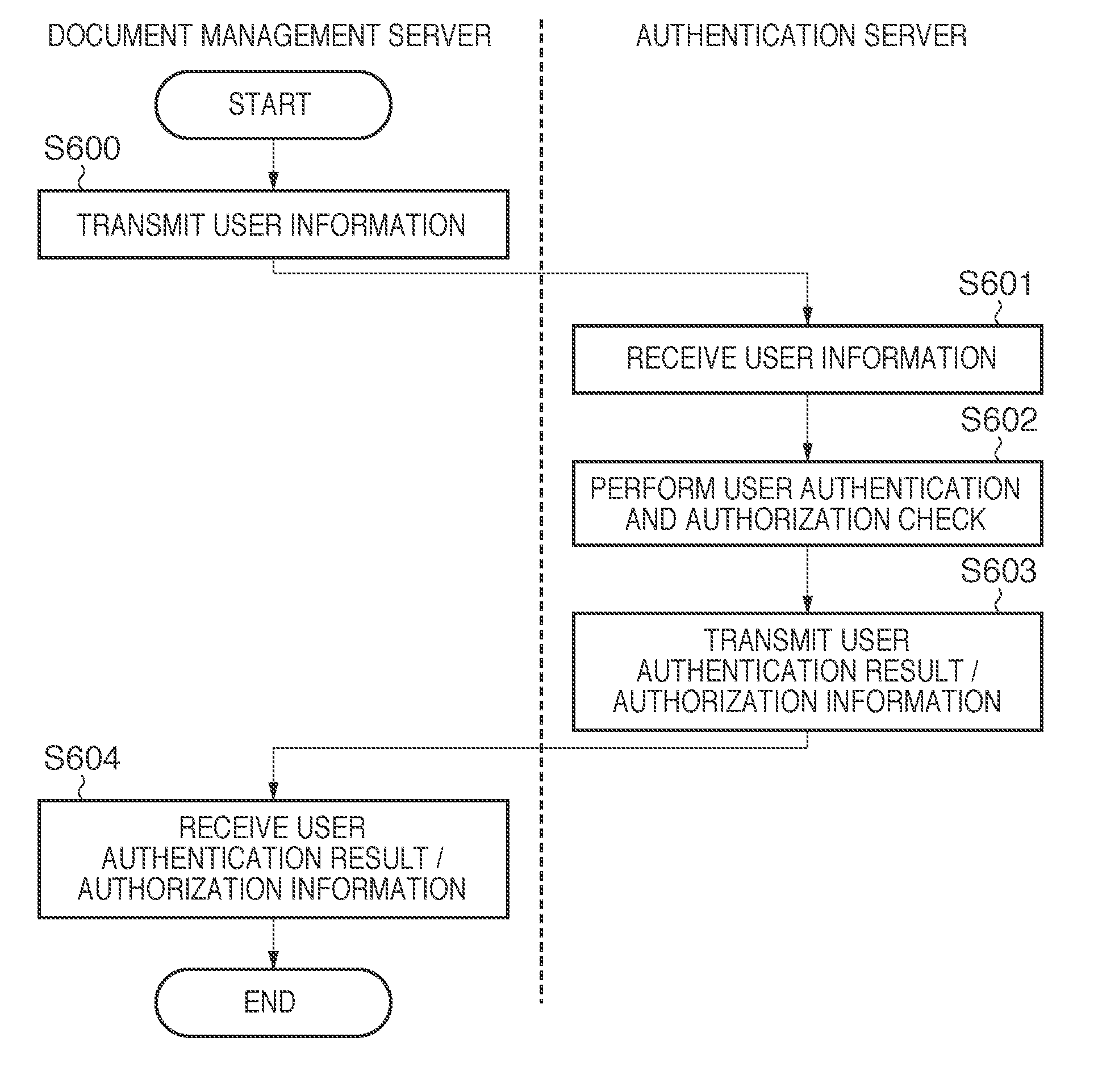
Job history information audit system, information processing apparatus, printing apparatus, and audit method
InactiveUS20110286026A1Visual presentation using printersDigital data protectionInformation processingPaper document
An apparatus comprises a unit configured to acquire identification information for identifying a document management server from a cooperation server; a data reception unit configured to receive data including information concerning a job from a printing apparatus, a unit configured to determine; based on the received data and the identification information, whether document data of the received data is document data; a unit configured to store the received data when the determination unit determines that the document data is document data managed by a first document management server; a unit configured to transmit the received data to the cooperation server when the determination unit determines that the document data is carry-in document data which is not managed by the first document management server; a unit configured to receive the instruction associated with permission / inhibition of printing; and a unit configured to transmit the instruction associated with permission / inhibition of printing.
Owner:CANON KK
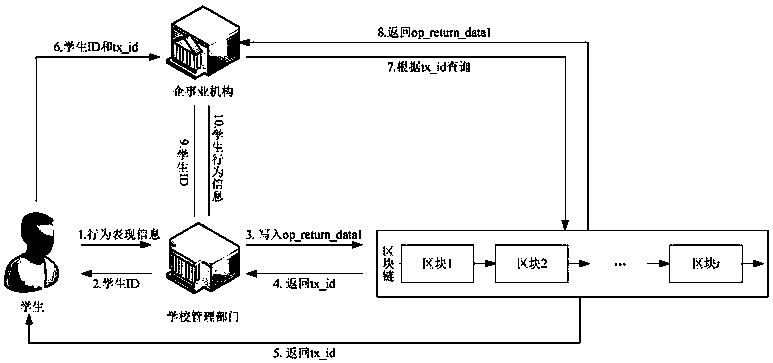
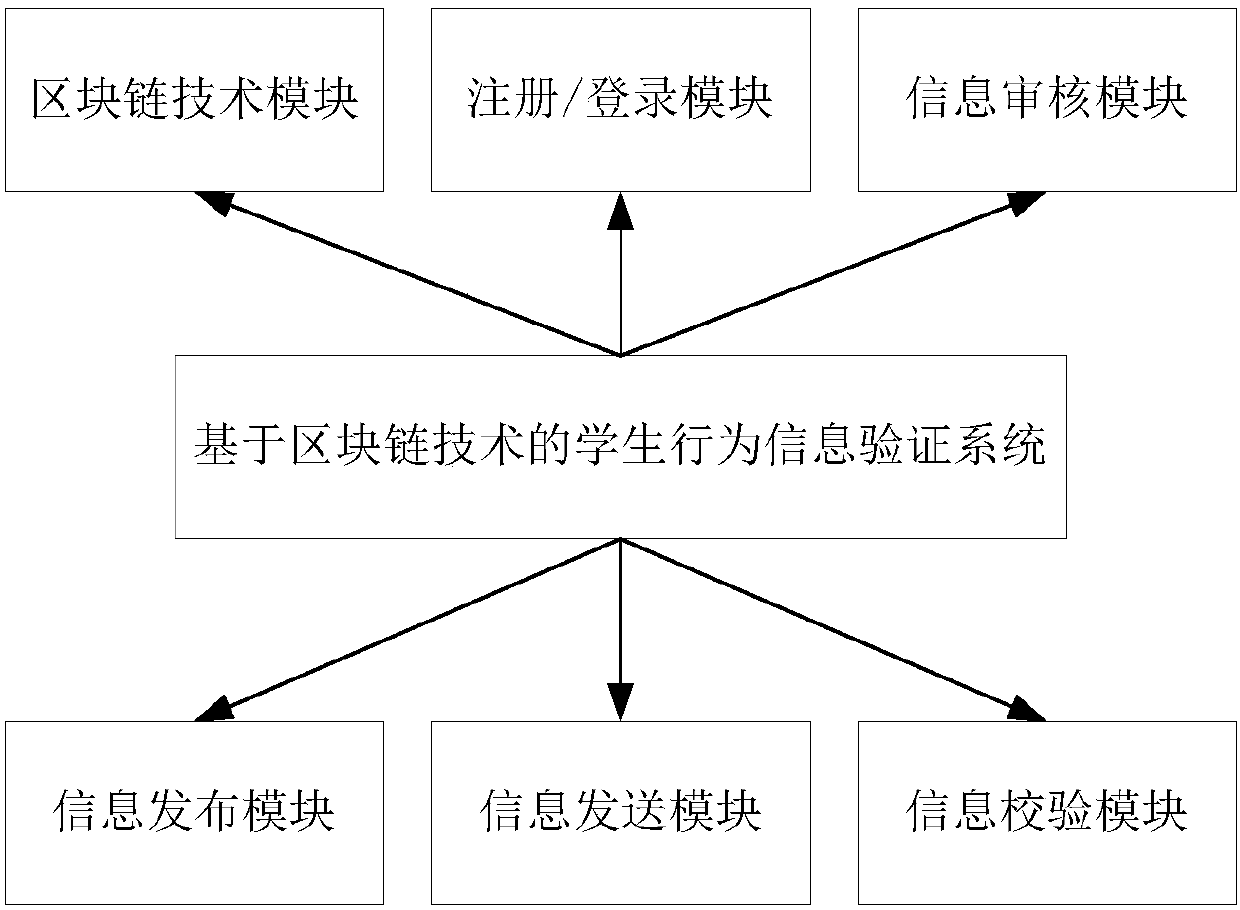
Student behavior information verification system based on blockchain technology
InactiveCN107832907AImprove reliabilityReduce human resource consumptionEncryption apparatus with shift registers/memoriesResourcesTamper resistanceInformation support
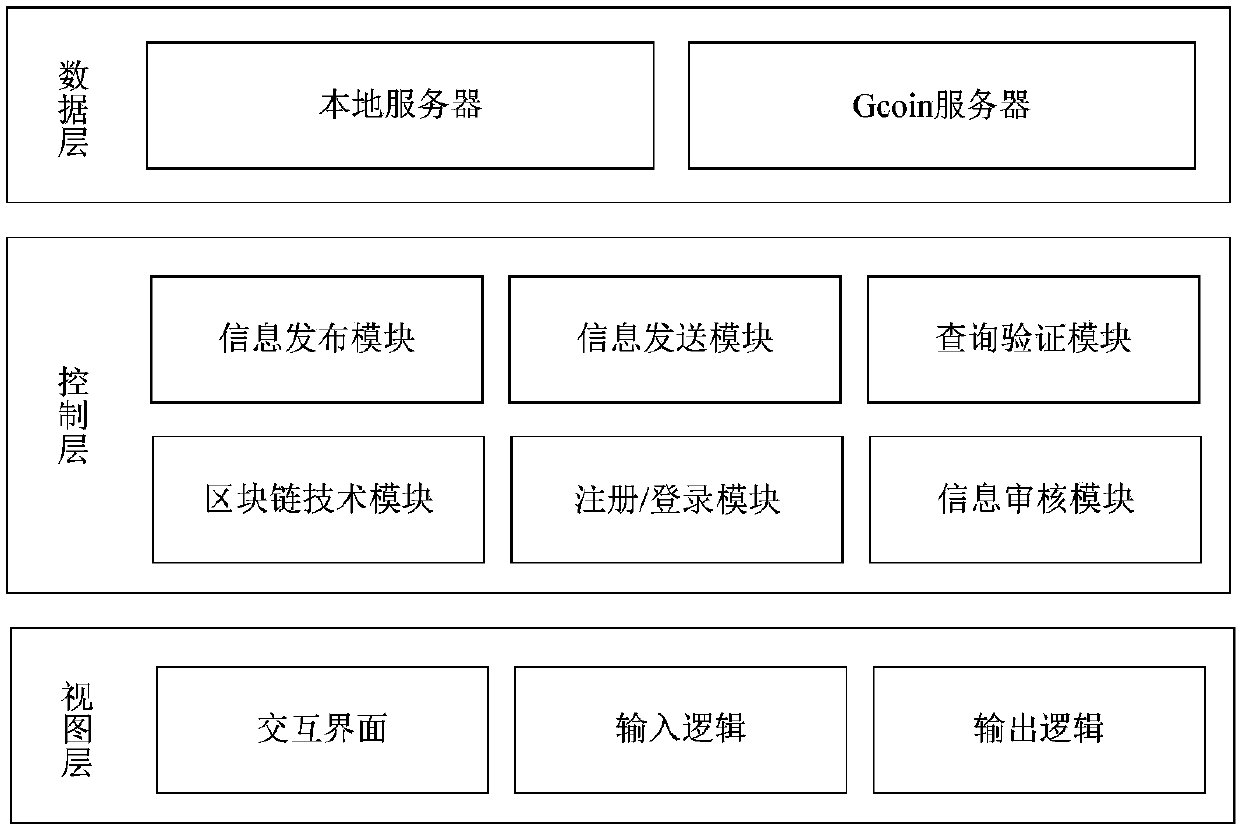
The invention discloses a student behavior information verification system based on a blockchain technology. The characteristics of distributed structure, automatic trust establishment, tamper-proofing, anti-counterfeiting, traceability and the like are used to solve the problems of high information verification cost, low efficiency, insecure security and the like, which are caused by damage or loss of student behavior information supporting materials. The system consists of a blockchain technology module, a registration / login module, an information release module, an information audit module,an information sending module and a query verification module. A relatively complete student behavior information chain is formed, and a unified interface service is provided for external parties. Onthe basis of ensuring the validity and reliability of student behavior information verification, the system greatly improves the work efficiency of tedious self-certification and verification of students, school management departments, enterprises, institutions and the like, and reduces the human resource cost of student behavior information maintenance.
Owner:CENTRAL UNIVERSITY OF FINANCE AND ECONOMICS
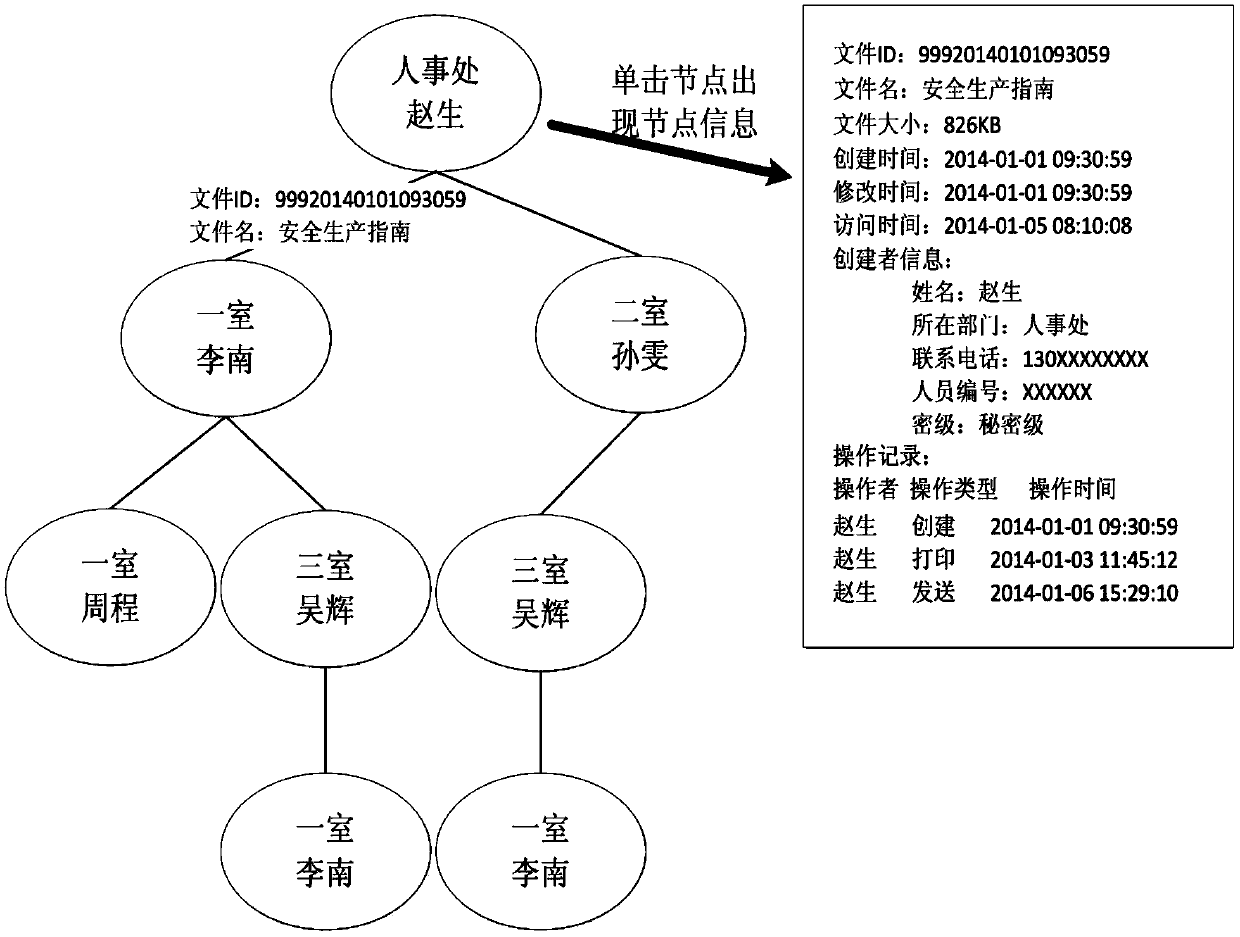
Audit and analysis method based on file trajectory tracking trees
The invention belongs to the field of electronic file security control, and provides an audit and analysis method based on file trajectory tracking trees. Millions of pieces of file tag information are dynamically stored in a database of an electronic file security control system, and an efficient and reliable tag information audit and analysis technique needs to be developed to meet the requirement for audit and analysis of electronic files under the circumstances of large data volume, dynamic updating and multi-dimensional circulation. The file trajectory tracking trees are located between a database layer and an audit and analysis layer, a data storage structure body in the form of a file trajectory spreading tree graph is formed through certain association, partition and recombination of data after the tag information is extracted from an updating database table, the peak of each tree represents a file builder, child nodes of each tree represent the spreading range of the corresponding file, and branches of each tree represent the spreading trajectory of the corresponding file. Next, the audit and analysis layer directly operates the file trajectory tracking trees, so that the calculated quantity is reduced.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
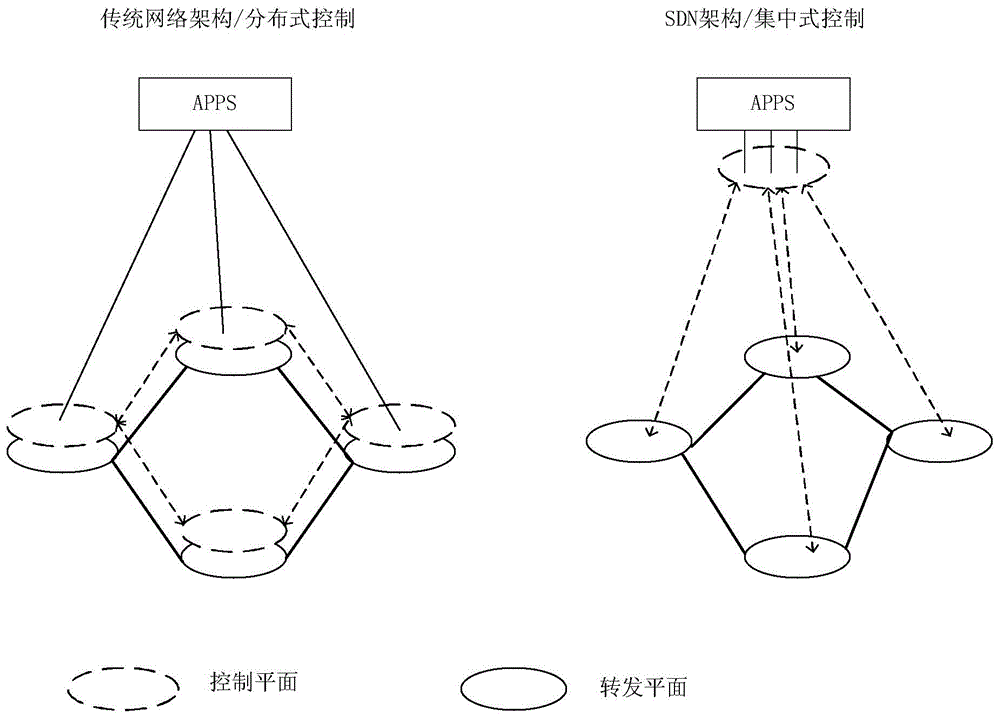
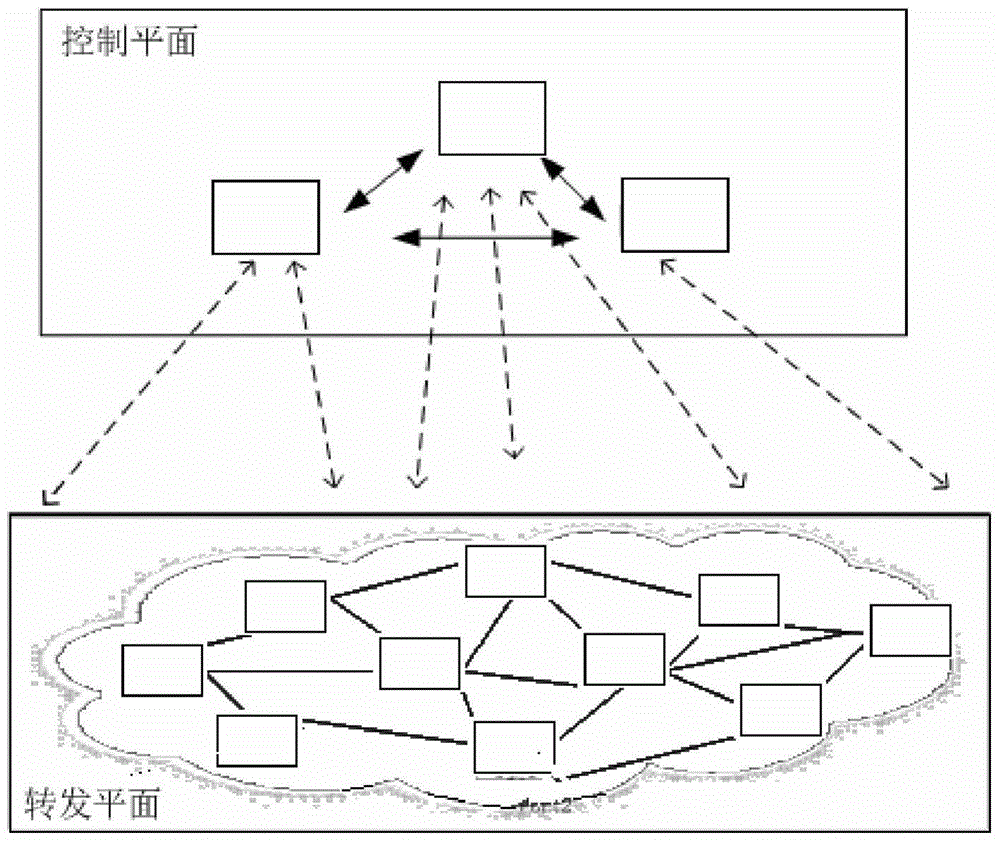
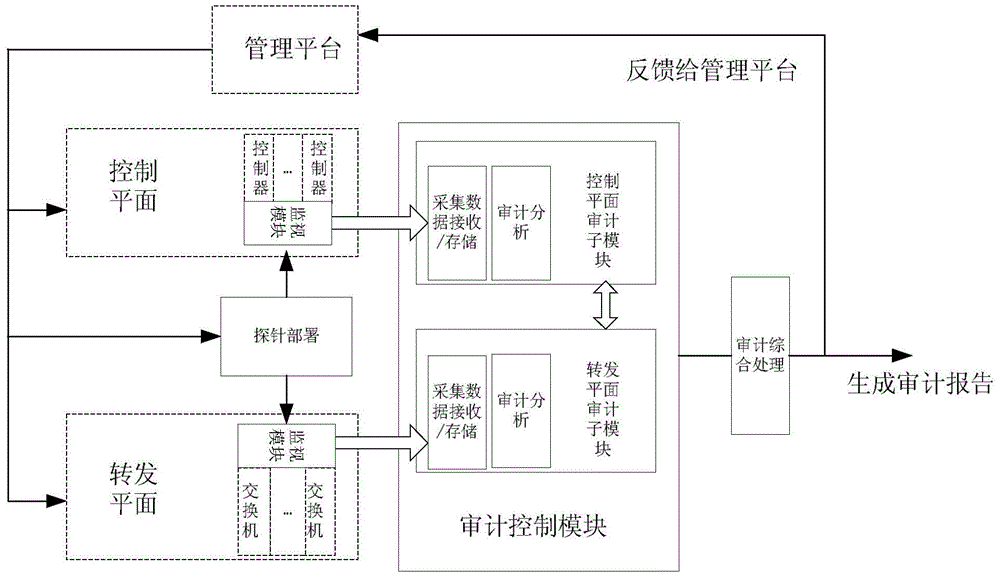
Method for auditing SDN
The invention discloses a method for auditing an SDN, and belongs to the field of information auditing. The method comprises the steps that 1 probes / monitoring modules used for conducting monitoring and counting on the flow and events of the SDN are arranged on a control plane and a transmitting plane of the SDN through a management platform respectively; 2 the monitoring module arranged on the control plane is used for collecting data and sending the data to an audit control module, a control plane sub-module in the audit control module is used for receiving / storing the data and conducting further audit analysis according to a preset rule, and an audit result / log / report is output to an audit comprehensive processing module; 3 the monitoring module arranged on the transmitting plane is used for collecting data and transmitting the data to the audit control module, a transmitting plane sub-module in the audit control module is used for receiving / storing the data and conducting further audit analysis according to a preset rule, and an audit result / log / report is output to the audit comprehensive processing module.
Owner:国都兴业信息审计系统技术(北京)有限公司
Security detection and monitoring system applicable to industrial control system
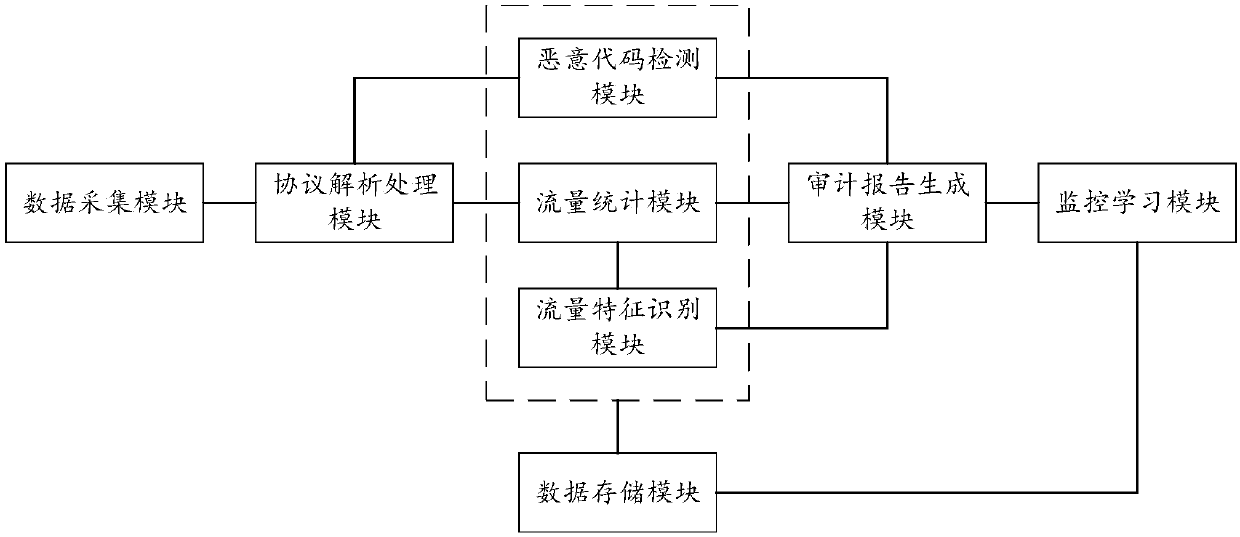
InactiveCN109639733AImprove applicabilityImprove detection efficiencyTransmissionData informationSecure state
The invention discloses a security detection and monitoring system applicable to an industrial control system. The security detection and monitoring system comprises a data collection module, a data storage module, a protocol analysis processing module, a malicious code detection module, a traffic statistical module, a traffic feature recognition module, an audit report generation module and a monitoring learning module; the protocol analysis processing module receives and analyzes data to be detected; the data to be detected is stored in the data storage module; the malicious code detection module recognizes malicious code information; the traffic statistical module makes statistics on traffic data information of the data to be detected after analysis; the traffic feature recognition module recognizes traffic feature information of the traffic data information; the audit report generation module generates an audit report and sends the same to an audit office; and the monitoring learning module acquires a final audit result according to the audit report and a processing result of the audit office. According to the system provided by the invention, the security state of the industrial control system can be monitored, the network security protection capacity of the industrial control system can be enhanced, and the labor cost can be reduced.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD
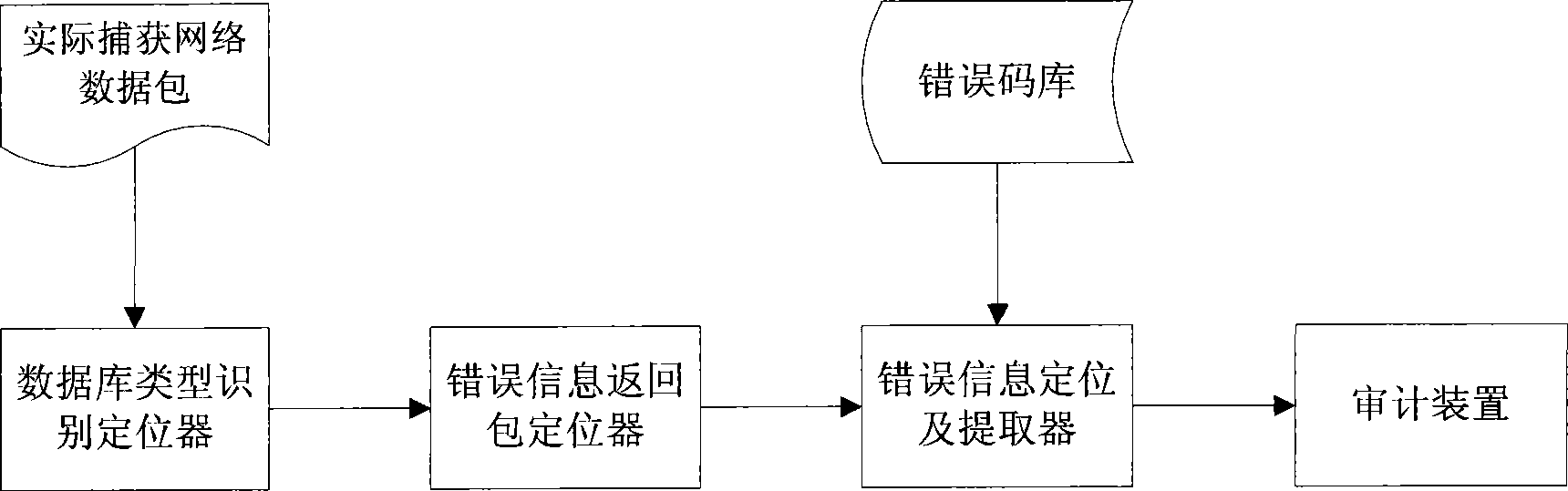
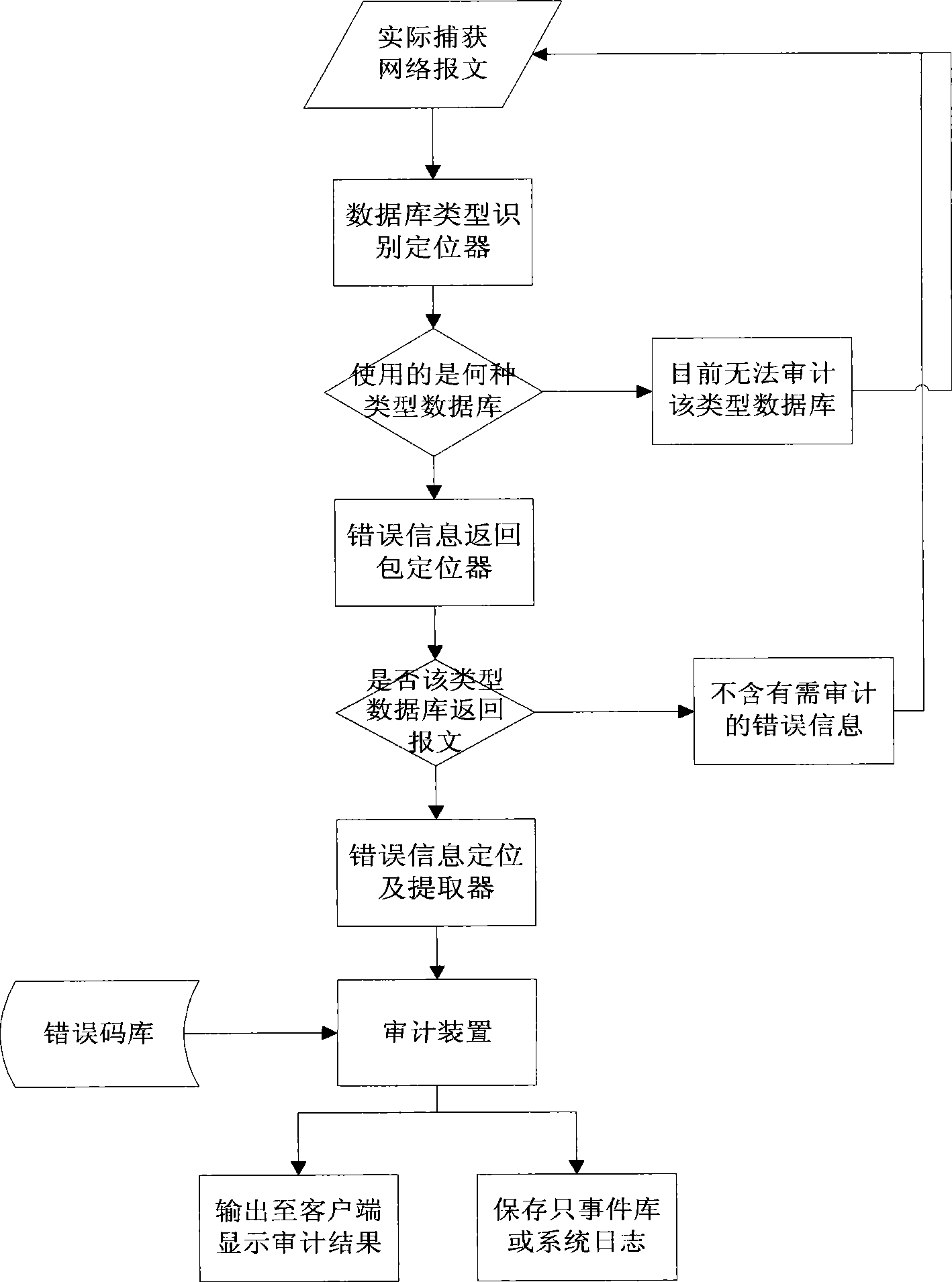
Database error information extracting method and system
InactiveCN101453359AExpand the scope of the auditImprove extraction efficiencyData switching networksSpecial data processing applicationsServer-sideExtraction methods
The invention relates to a method and a system for extracting database error message, in particular to a method and a system for extracting the error message returned from a server side during the operation of six frequently-used databases and carrying out related operation audit used in network business audit product. The system comprises a database type identification locator, an error message return package locator, an error message locating and extracting device, an error code library and an audit device. The invention solves the problem that the audit of the error message returned from the server side in the database operation process is lacked in the prior audit product, and overcomes the defects that the error message audit is difficult because different database types use different protocols. The invention has very good expansibility. For new database types, the system and the method have flexible expansibility to expand audit range and very high extraction efficiency and accuracy for the error message of the different database types, and can be widely applied to network business audit products.
Owner:BEIJING VENUS INFORMATION TECH
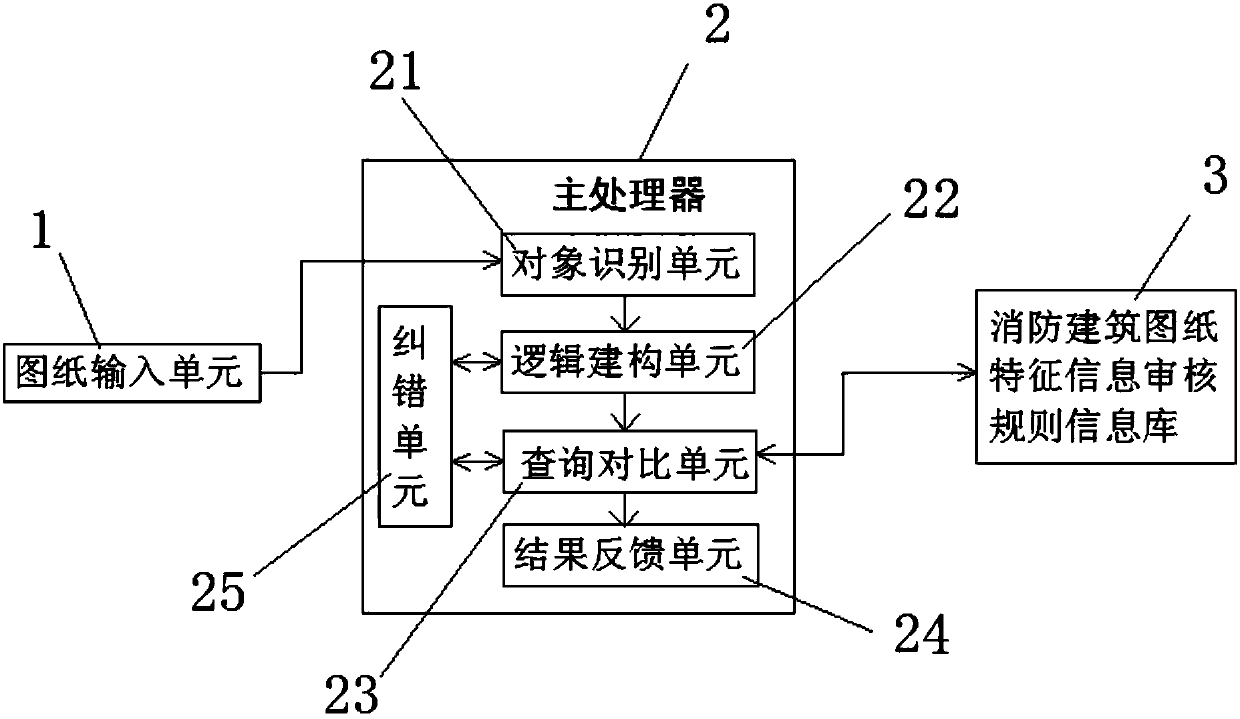
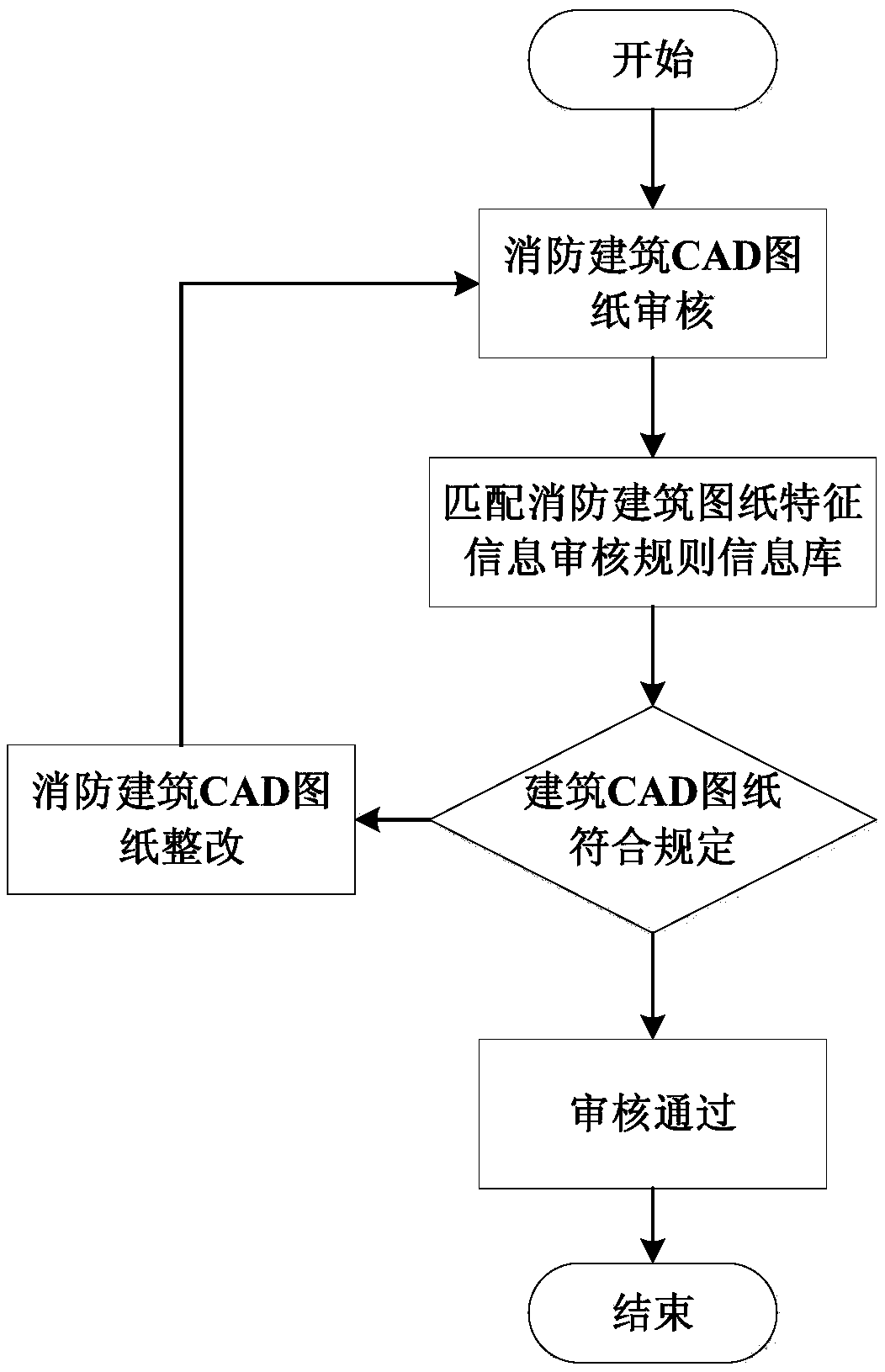
Intelligent fire-fighting building drawing audit system and method based on artificial intelligence
InactiveCN107633261AImprove review efficiencyImprove accuracyCharacter and pattern recognitionOffice automationInformation repositorySymbolic artificial intelligence
The invention relates to the fire-fighting inspection technology field and provides an intelligent fire-fighting building drawing audit system and method based on artificial intelligence. The system comprises a drawing input unit, a main processor and a fire-fighting building drawing characteristic information audit rule information database, wherein the main processor comprises an object identification unit, a logic construction unit, a query comparison unit and a result feedback unit, and the main processor is connected with the drawing input unit and the fire-fighting building drawing characteristic information audit rule information database. The invention further provides a drawing audit method based on the system. The system is advantaged in that fire-fighting building drawings can be automatically audited according to the fire-fighting building drawing characteristic information audit rule information database, the accurate determination result is made, rectification proposal isprovided for drawings which are not in accord with acceptance prescriptions, drawing audit efficiency and accuracy are improved, the intelligence degree is high, and application prospect is wide.
Owner:上海网罗电子科技有限公司
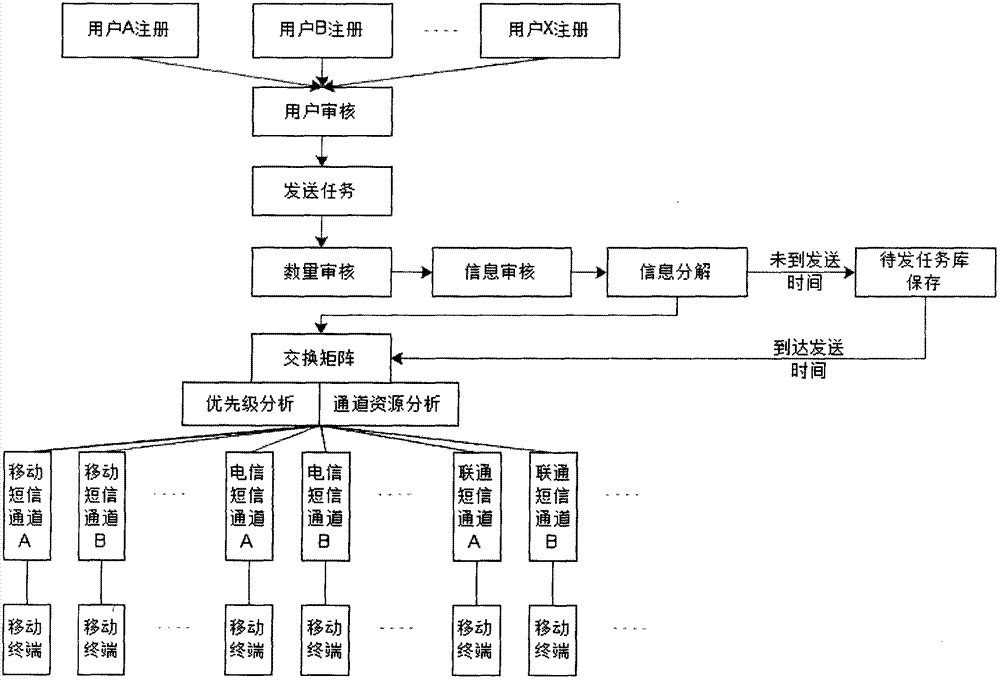
Short and multimedia message sending method based on middleware platform
InactiveCN102970662AConvey accuratelyRealize SMS communicationMessaging/mailboxes/announcementsDecompositionComputer science
The invention discloses a short and multimedia message sending method based on a middleware platform. The short and multimedia message sending method comprises the following steps that: a user submits tasks for sending short messages and / or multimedia messages through the middleware platform; the middleware platform receives the tasks and then performs quantity audit and information audit and decomposition on the tasks; the tasks subjected to the information decomposition are delivered to an exchange matrix; the exchange matrix computes the priorities of the tasks and analyzes channel resources so as to match the tasks with corresponding channels; and the sending tasks are submitted into the sending channels of corresponding operators according to the matching results. By virtue of the short and multimedia message sending method, the user can rapidly and conveniently send a large number of short and multimedia messages in a mass manner to terminals with numbers belonging to the different operators.
Owner:内蒙古华腾科技股份有限公司
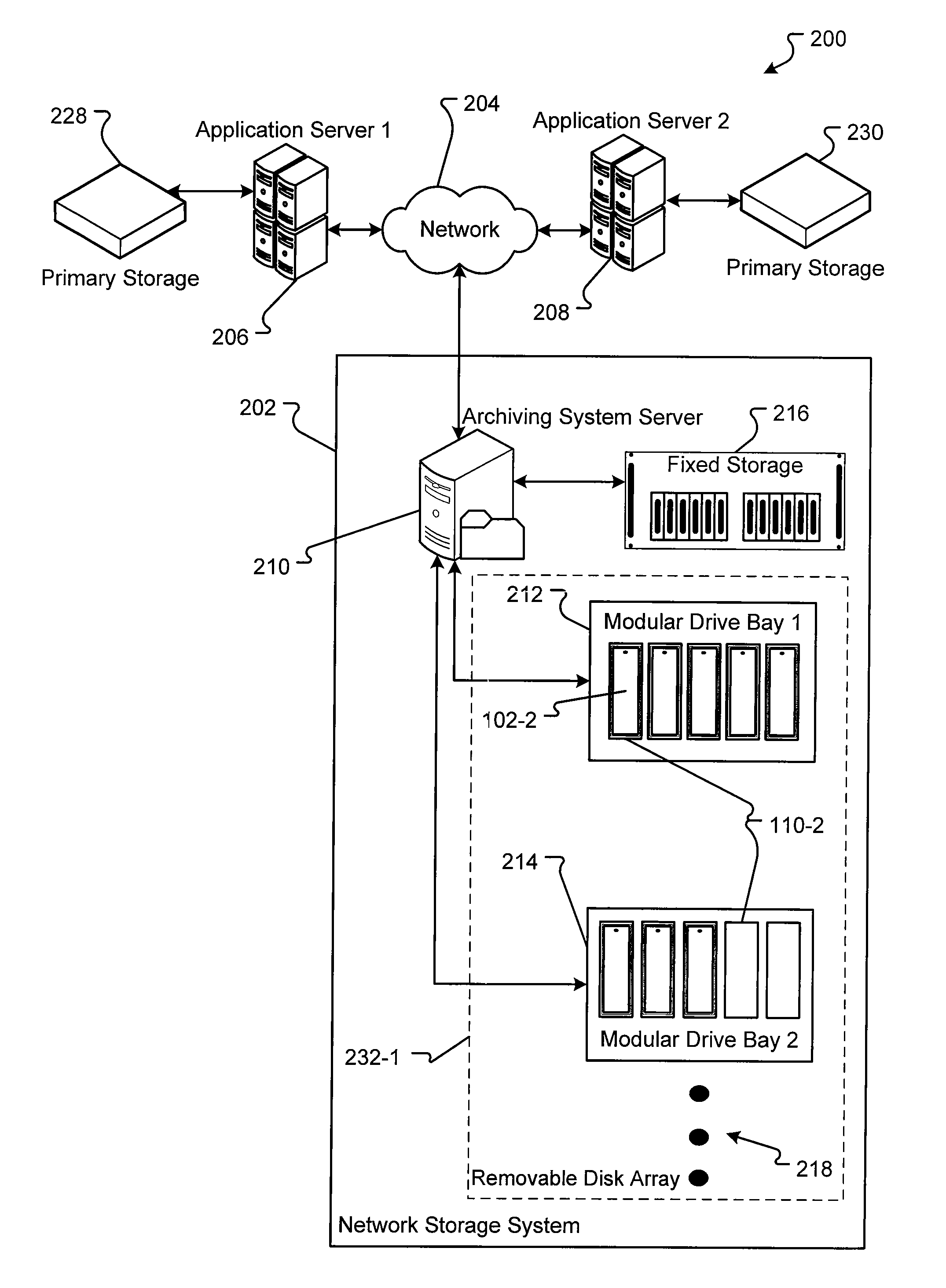
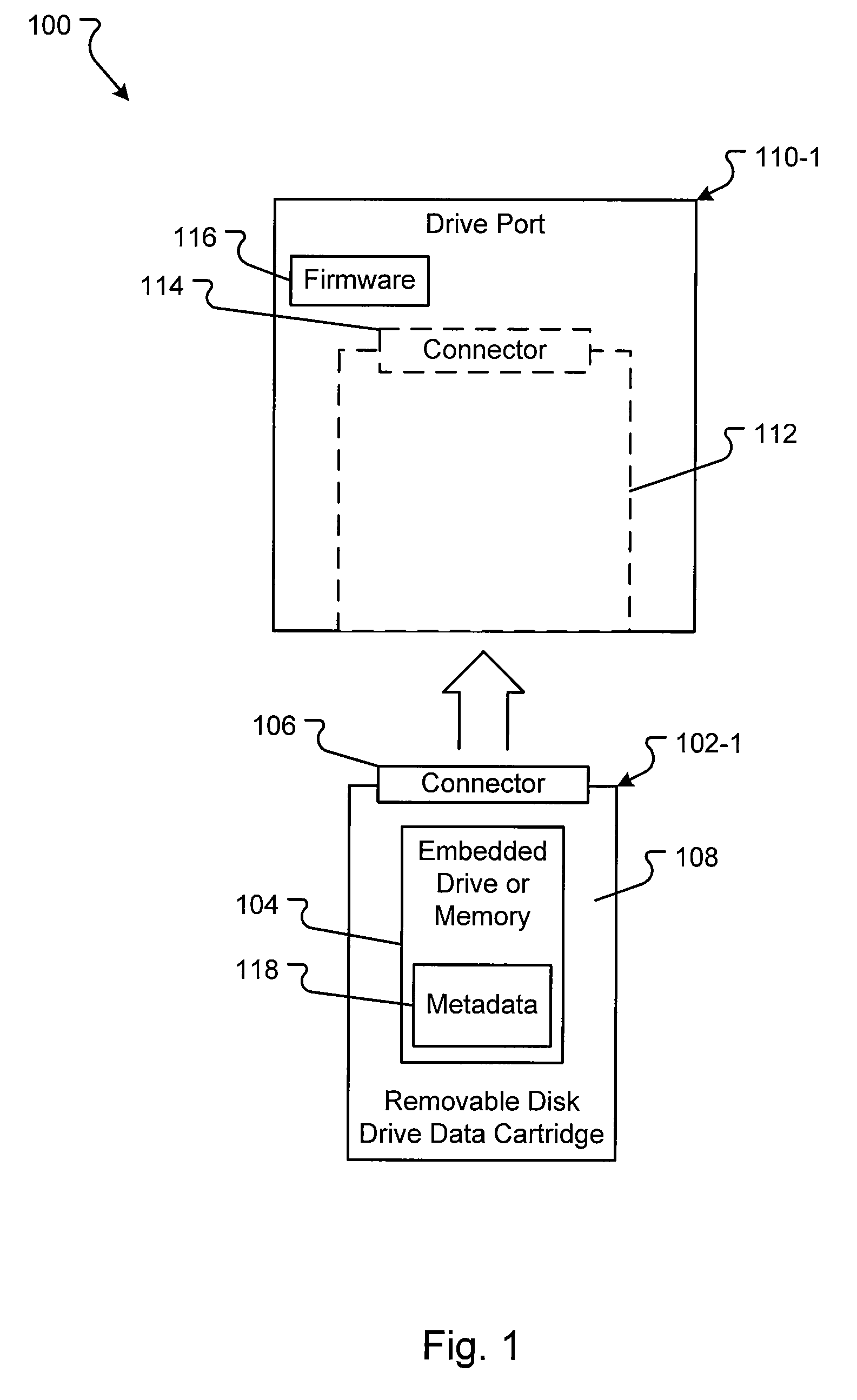
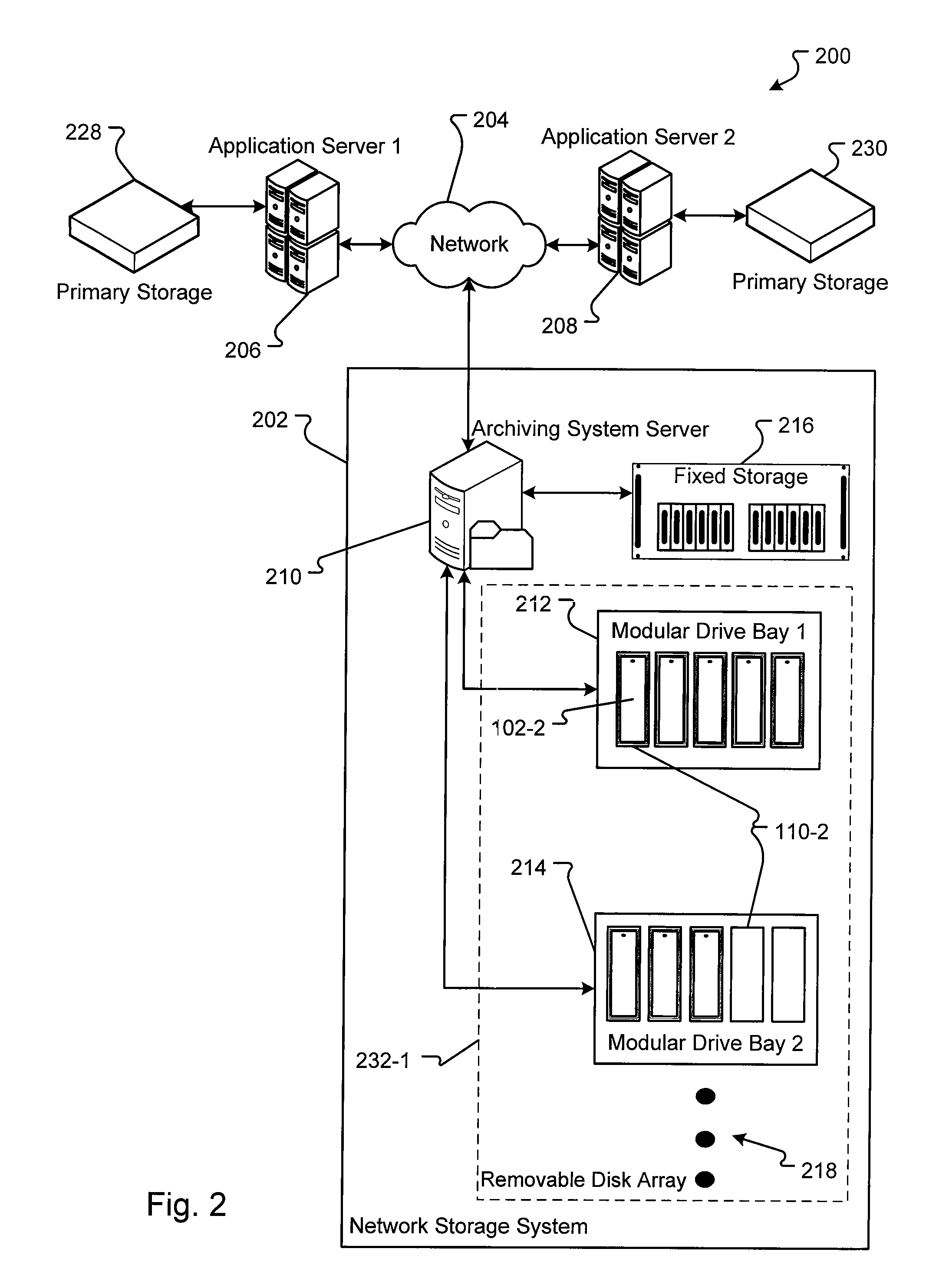
Methods for implementation of information audit trail tracking and reporting in a storage system
InactiveUS20090094245A1Digital data information retrievalDigital data processing detailsApplication serverArchival storage
Embodiments of archival storage system are disclosed. The archival storage system includes one or more removable disk drives that provide random access and are readily expandable. One or more application servers can store archival data to the one or more removable disk drives. Further, the archival storage system provides an audit trail that stores information about actions taken on the archival data. The audit trail data providing a list of the actions and information about the actions that can be used to determine changes to the archival data.
Owner:IMATION +1
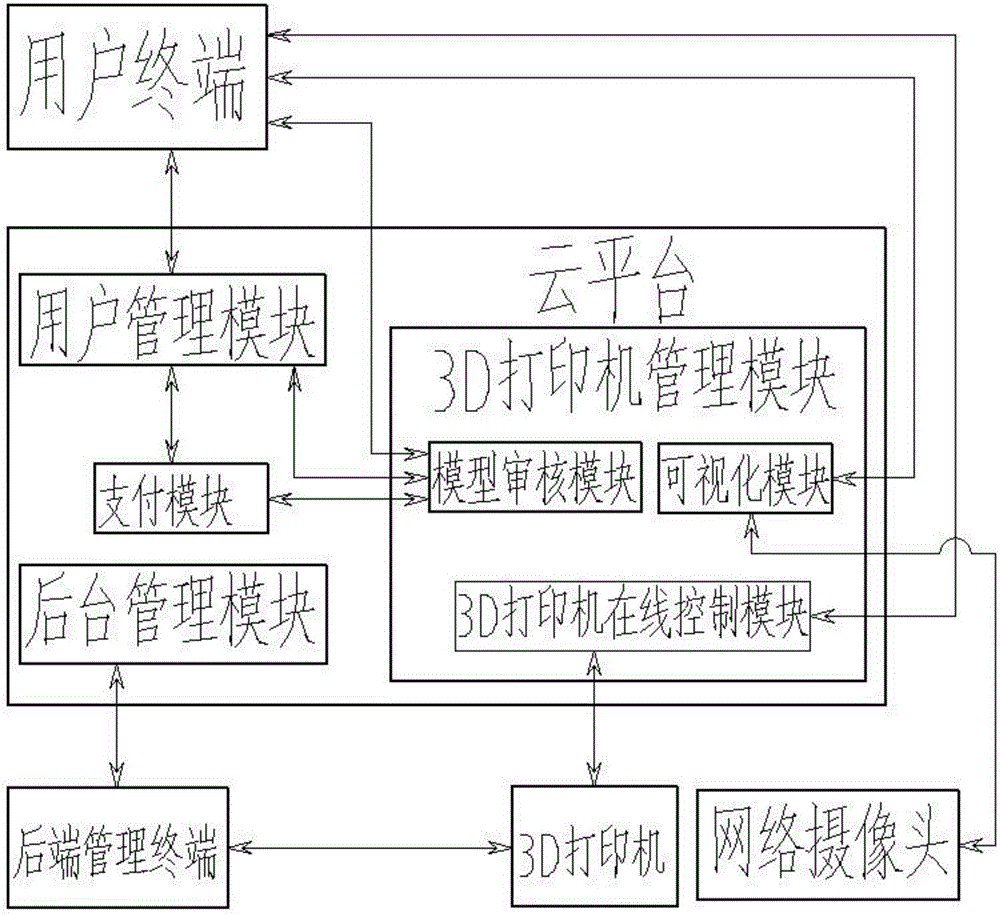
Controllable visual online 3D printing system
InactiveCN106126130ARealize online visual experienceImprove experienceDigital output to print unitsPaymentPayment order
The invention discloses a controllable and visualized online 3D printing system, which includes a user terminal, a cloud platform, and a background management terminal. The cloud platform includes a user management module, a 3D printer management module, and a background management module. The 3D printer management module communicates with the user management module. , the 3D printer management module includes a model review module, a visualization module and a 3D printer online control module, the model review module communicates with the user management module, the visualization module is used for communication between the user terminal and the network camera monitoring the 3D printer, and the payment module will The information to be paid reviewed by the model review module is sent to the user management module, and the user management module sends the payment information to the user terminal to remind the user terminal of the payment and the feedback information of whether the payment is successful; the online control module of the 3D printer is used for the user terminal Communication of information with the 3D printer. The present invention can bring an unprecedented sense of control and visual sense to the user when using the 3D printer online.
Owner:INST OF OPTICAL MASCH CHONGQING CITY
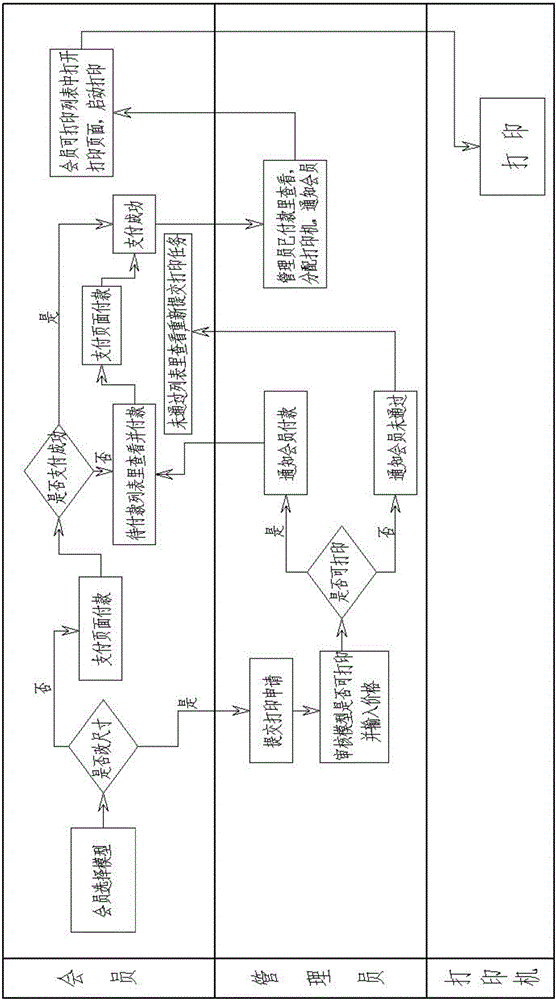
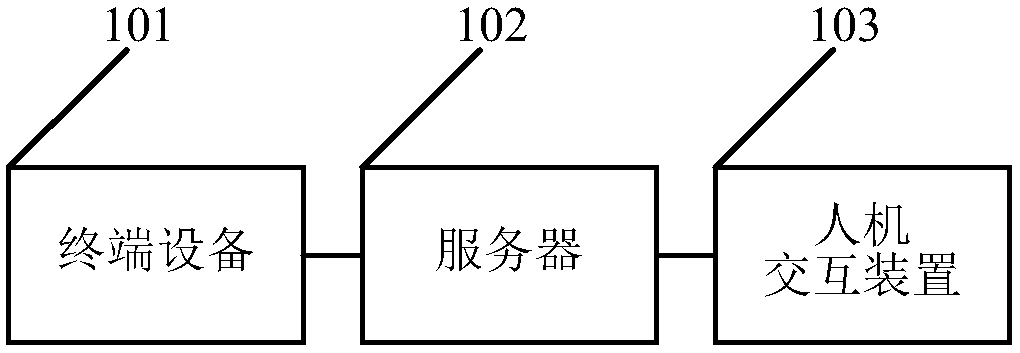
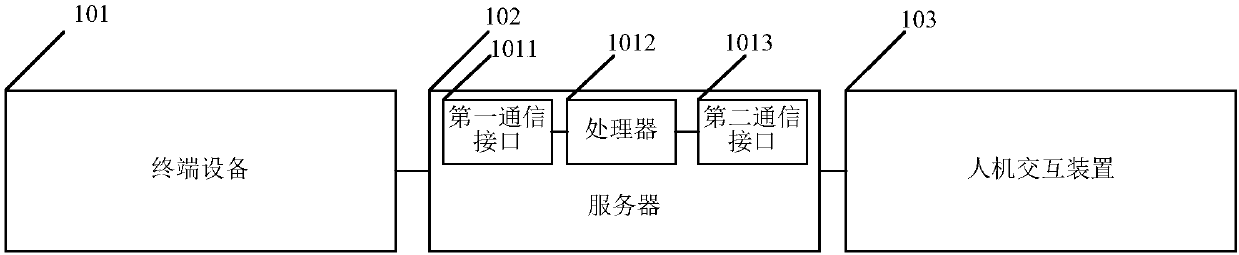
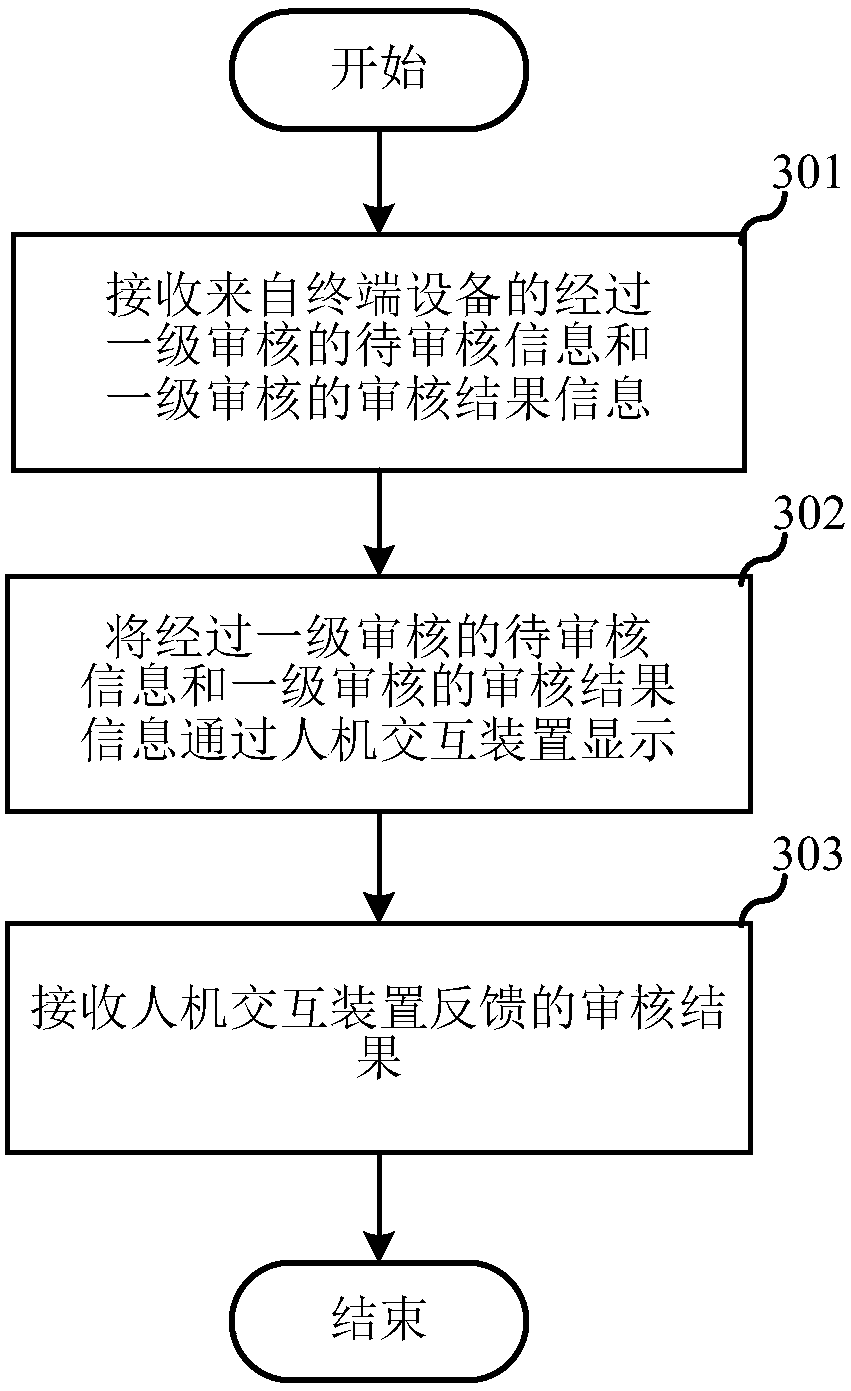
Information audit system and method
InactiveCN107622466AGuarantee information qualityReduce workloadData processing applicationsSpecial data processing applicationsInteraction deviceTerminal equipment
An embodiment of the invention relates to the technical field of information and discloses an information audit system and method. The information audit system comprises a terminal device, a server and a man-machine interaction device. The terminal device is in communication connection with the server, and is used for obtaining information to be audited, carrying out first stage of audit on the information to be audited locally, and uploading audit result information of the first stage of audit and the information to be audited to the server; the server is in communication connection with theman-machine interaction device, and is used for outputting the received audit result information and the information to be audited to the man-machine interaction device; and the man-machine interaction device is used for displaying the received information to be audited to allow an audit staff to carry out manual audit on the information to be audited according to the audit result information, andafter receiving an audit result of the information to be audited and obtained by the audit staff, feeding back the audit result to the server. Therefore, quality of information passing the audit is guaranteed, and meanwhile, manual audit workload can be reduced effectively, and manpower resources are saved.
Owner:SHANGHAI YUDE TECH CO LTD
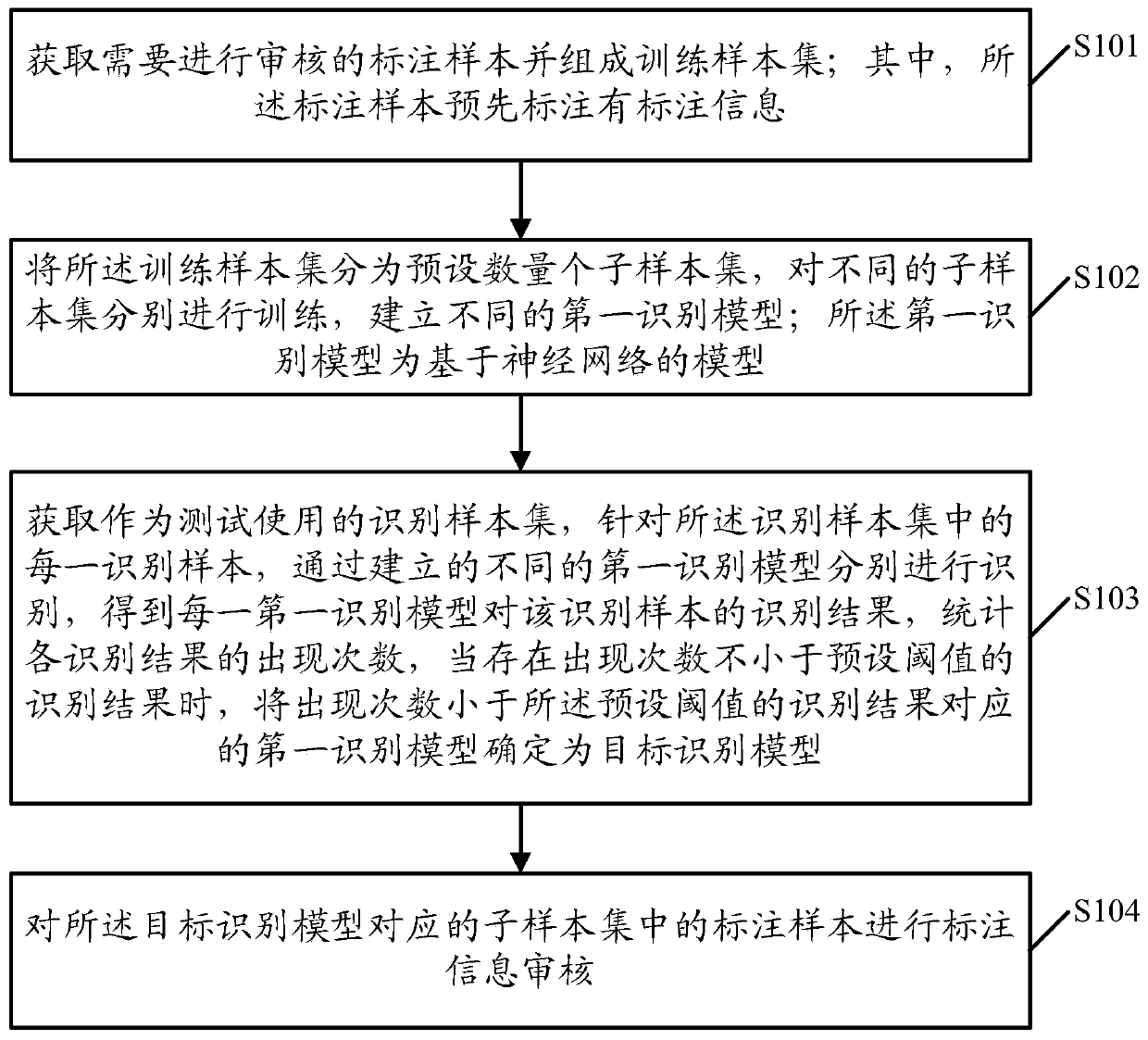
Sample labeling information auditing method and device
ActiveCN110222791AQuick reviewAvoid time costCharacter and pattern recognitionNeural architecturesPattern recognitionGoal recognition
The invention provides a sample labeling information auditing method and device. The method comprises the following steps: obtaining annotation samples needing to be audited and forming a training sample set; dividing the training sample set into a preset number of sub-sample sets, respectively training different sub-sample sets, and establishing different first recognition models; obtaining an identification sample set used for testing; carrying out identification on each identification sample in the identification sample set through the established different first identification models, andobtaining an identification result of each first identification model on the identification sample; counting the occurrence frequency of each identification result, and determining the first identification model corresponding to the identification result of which the occurrence frequency is smaller than a preset threshold as a target identification model when the identification result of which theoccurrence frequency is not smaller than the preset threshold exists; and carrying out labeling information audit on the labeled samples in the sub-sample set corresponding to the target identification model. By applying the scheme provided by the invention, the labeling result of the sample can be quickly audited.
Owner:HANGZHOU RUISHENG SOFTWARE CO LTD
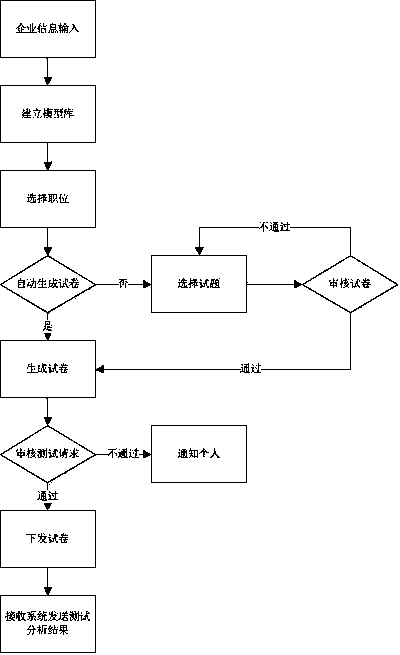
Competency model based talent assessment system and method
The invention discloses a competency model based talent assessment system and method. The system comprises an integrated management module, a data management module, a model base management module and an intelligent analysis module, wherein the integrated management module comprises a personal information management sub-module, an information inquiry sub-module and an information auditing sub-module; the data management module comprises a test question database, a test paper generation sub-module, a test paper management sub-module and an assessment data management sub-module; the model base management module comprises a model base and a model inquiry sub-module; the intelligent analysis module comprises an industry database, a parameter library, a competency model analysis and generation sub-module and a test result analysis sub-module. By the aid of the system, on one hand, enterprises are helped to build competency models in accordance therewith, talent assessment cost of the enterprises is reduced, and references are provided for talent engagement of the enterprises; on the other hand, individuals can make career development paths thereof clear so as to more effectively plan career development directions thereof.
Owner:ZHENJIANG RETECH INFORMATION TECH
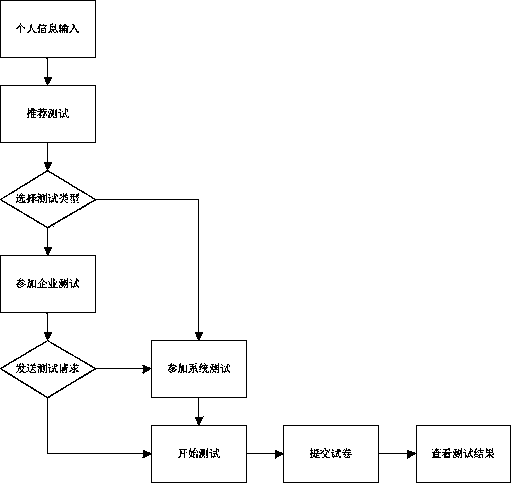
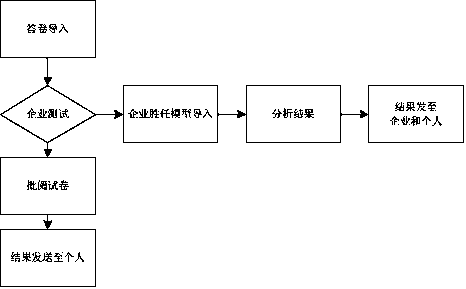
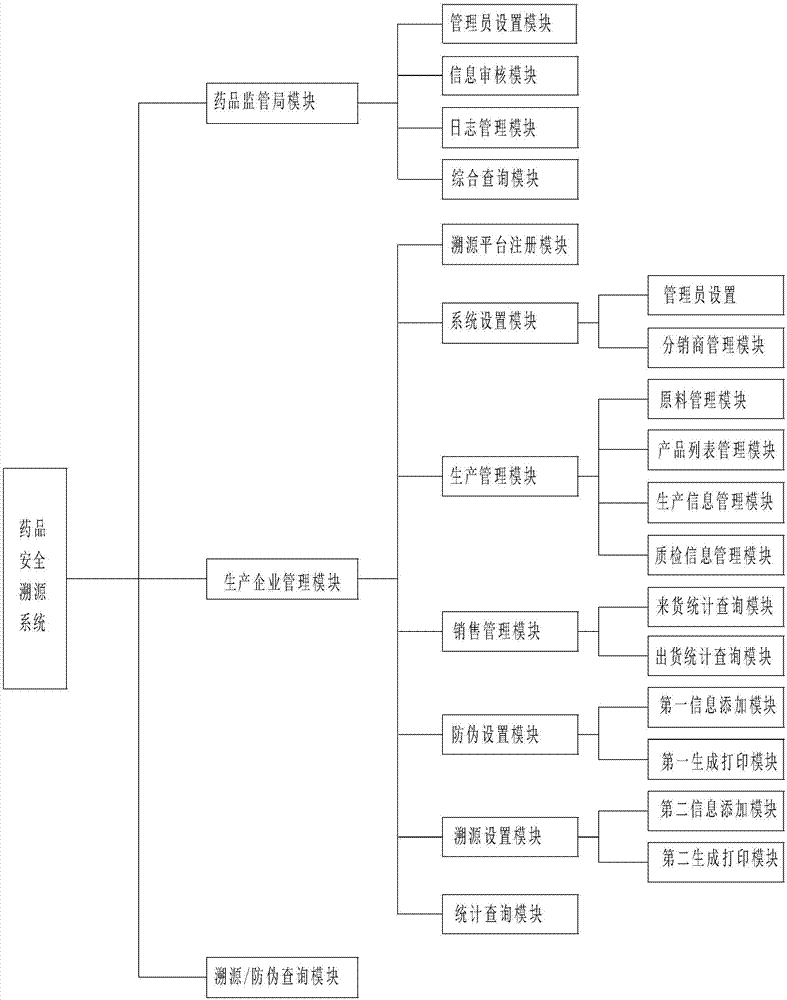
Medicine safety traceablility system and method
InactiveCN107358449ATrace back in timeRegulate the circulation marketCo-operative working arrangementsResourcesLog managementDrug product
The invention discloses a medicine safety traceablility system and method. The system comprises function modules as follows, a medicine supervision bureau module used for carrying out unified supervision personnel setting, information audit, log management and comprehensive query, a production enterprise management module used for realizing production management, sales management, anti-counterfeit setting, traceablility setting and statistics query functions, a traceablility / anti-counterfeit query module used for realizing code scanning to query the product traceablility information online and code scanning to display product anti-counterfeit codes and editing the information to input the anti-counterfeit codes to a communication traceablility platform to query product authenticity. The method is advantaged in that once medicines consumed by consumers have problems, the problems can be timely searched through the flow, medicine traceability can be timely carried out, and loss prevention of benefits of the consumers is guaranteed.
Owner:安徽达仁信息科技有限公司
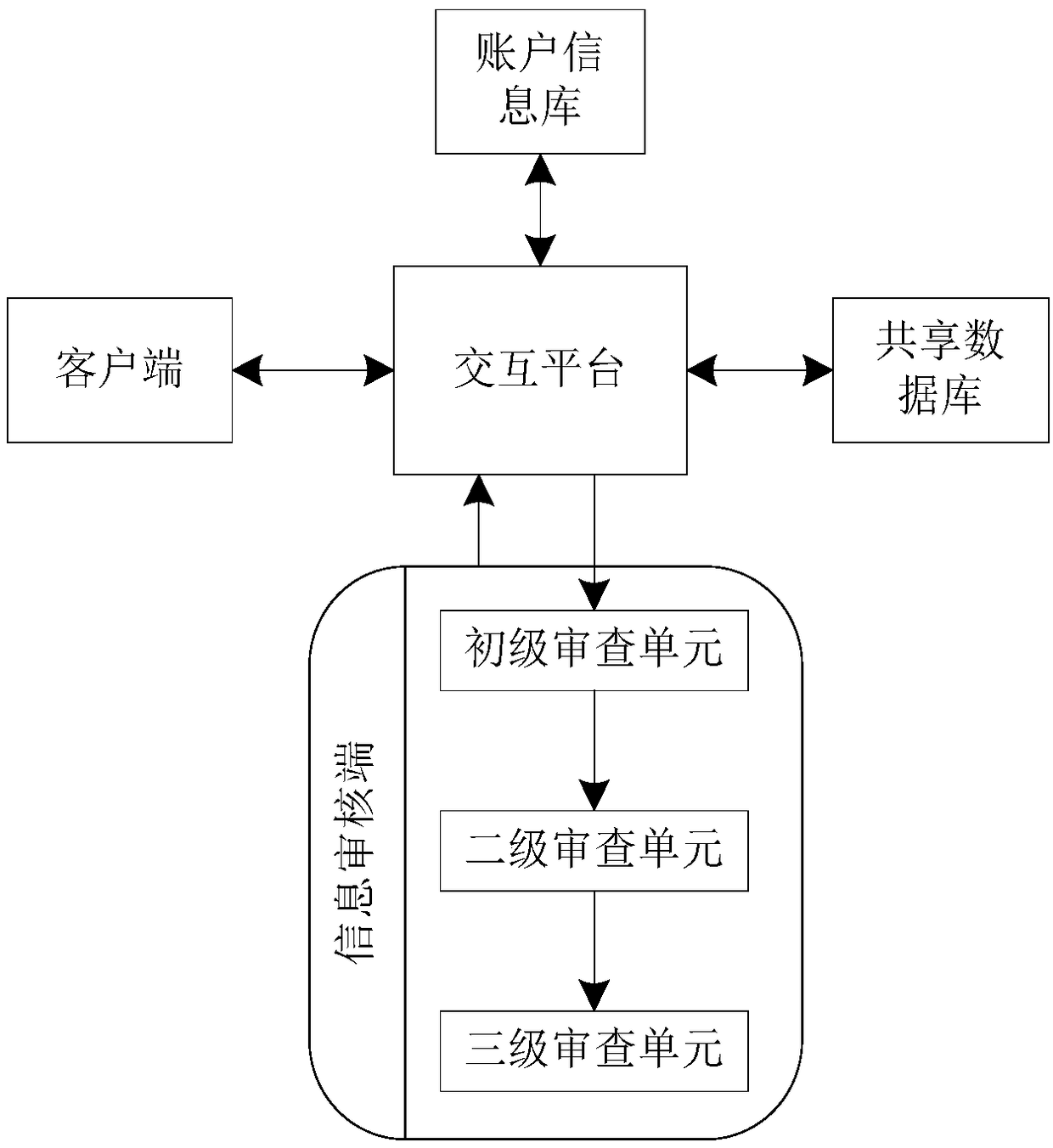
Shared knowledge platform system applied to medical information
InactiveCN109065180AImprove screening review qualityBuying/selling/leasing transactionsMedical referencesPaymentInformation repository
The invention discloses a shared knowledge platform system applied to the medical information. The system comprises a client, an interaction platform, a shared database, an information audit end and an account information database, wherein the client, the shared database, the information audit end and the account information database are in docking relation with the interaction platform, the client is provided with an information uploading interface and an information downloading interface, the information uploading interface includes a medical information uploading unit and an identity information uploading unit, the information downloading interface includes a downloading unit and a payment unit, the information audit end is provided with a primary audit unit, a secondary audit unit anda third-level audit unit, and the secondary audit unit and the third-level audit unit are correspondingly provided with multiple medical information examiner. During use, the screening audit quality of the shared medical information can be effectively improved, and individual extra earning accounts can be created for medical information uploading persons.
Owner:成都艾视美科技有限公司
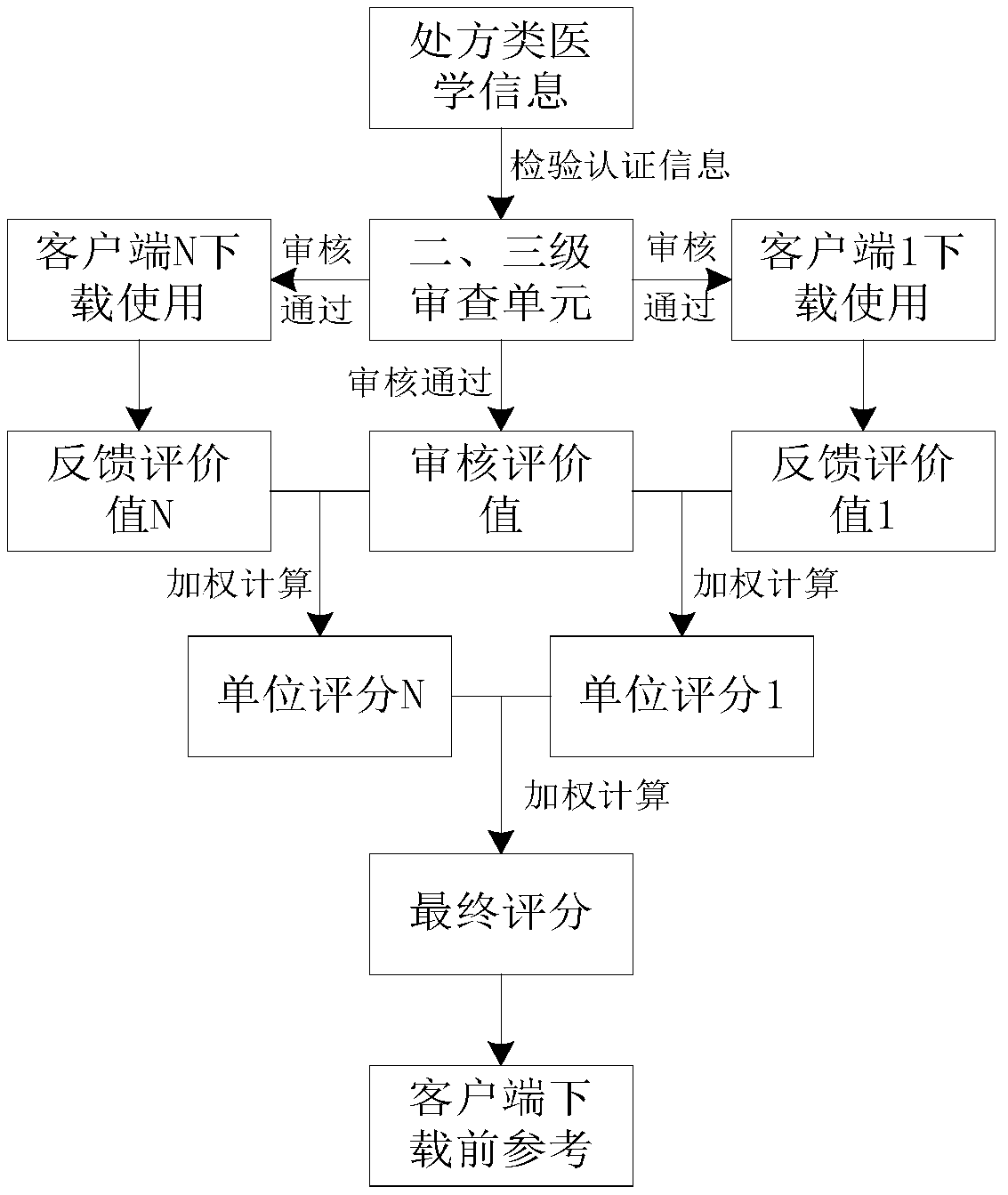
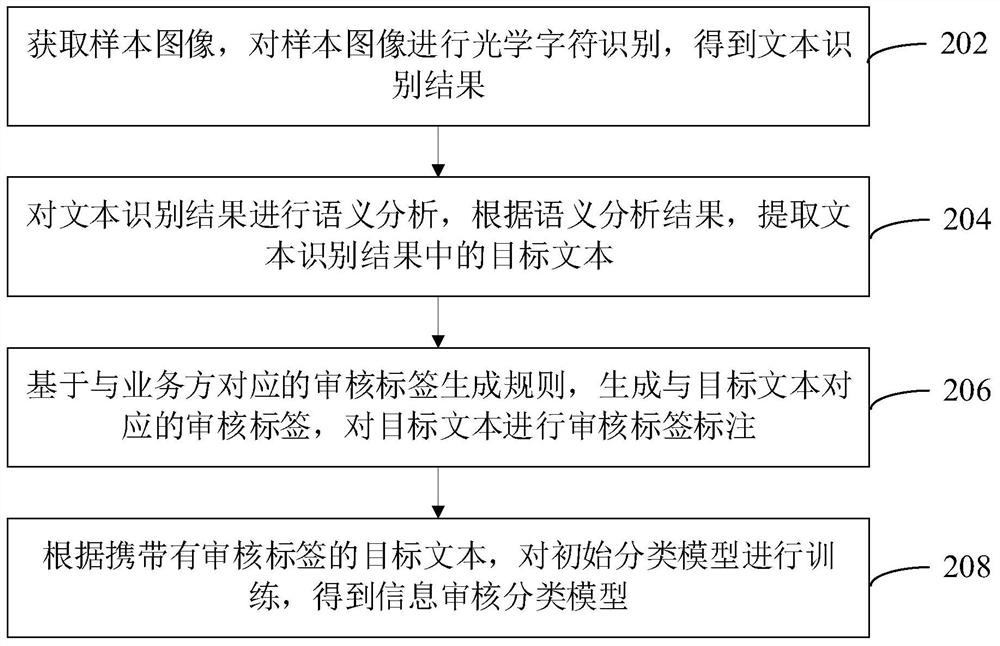
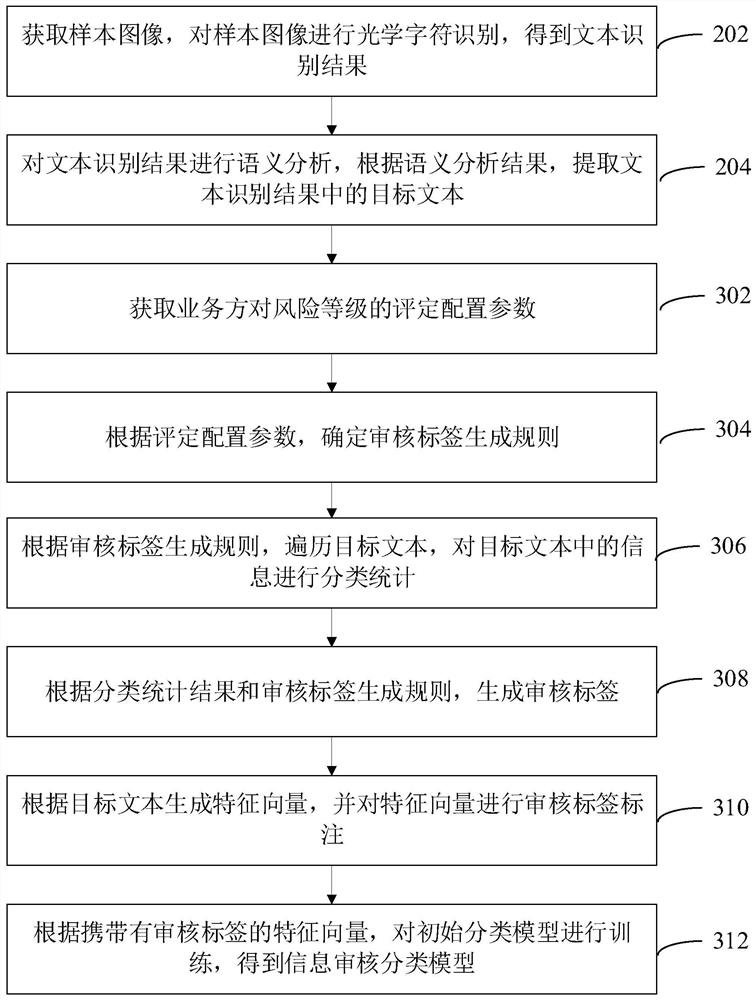
Construction method of information auditing classification model and information auditing method
PendingCN112613501AImprove training efficiencyRealize multiplexingFinanceSemantic analysisSample graphText recognition
The invention relates to the technical field of artificial intelligence, and provides a construction method and device of an information auditing classification model, computer equipment and a storage medium. The method comprises the steps of acquiring a sample image, performing optical character recognition on the sample image to obtain a text recognition result, performing semantic analysis, extracting a target text according to a semantic analysis result of the text recognition result, and generating an auditing label corresponding to the target text based on an auditing label generation rule corresponding to a business party to perform auditing label labeling, and performing model training according to the target text carrying the auditing label to obtain an information auditing classification model. Labeling processing is carried out without depending on manpower, the generation speed of samples is increased, audit labels suitable for model training of different business parties can be generated, reuse of sample images is achieved, and an information audit classification model is obtained through rapid training. In addition, the invention also relates to a blockchain technology, and the information auditing result of the user can be stored in the blockchain.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
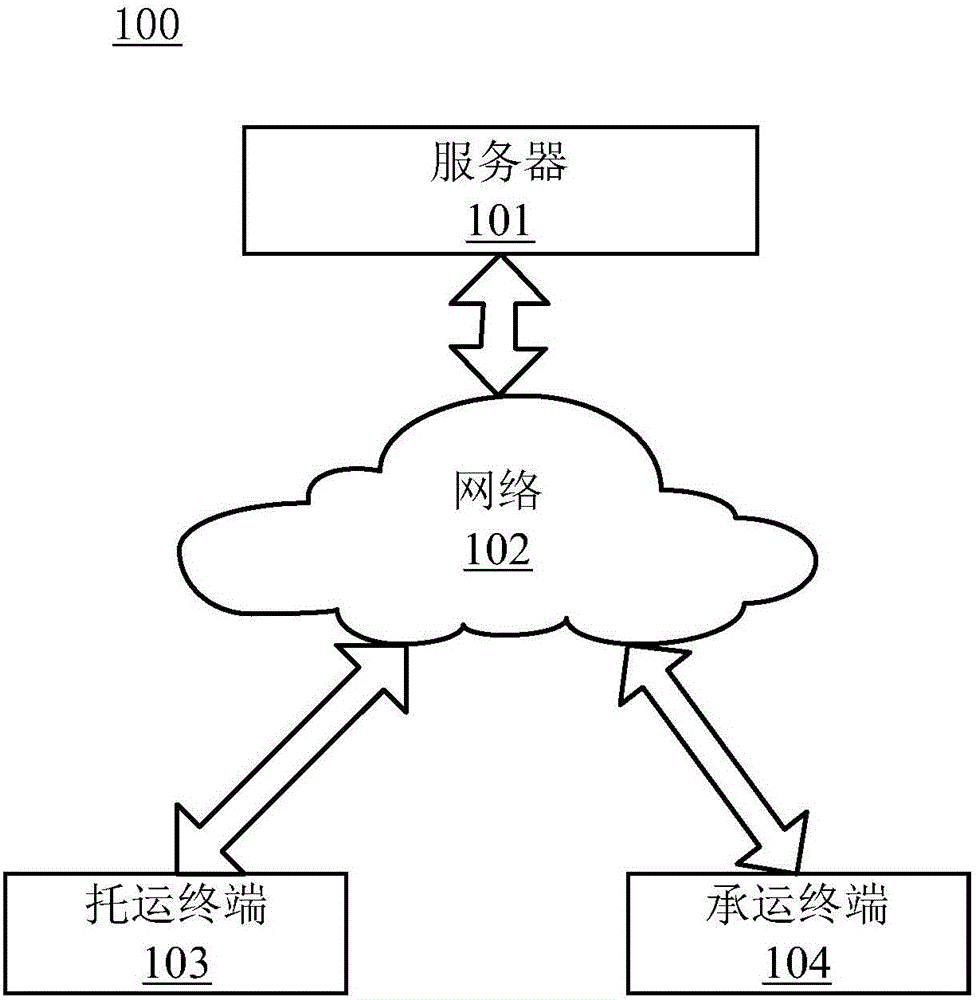
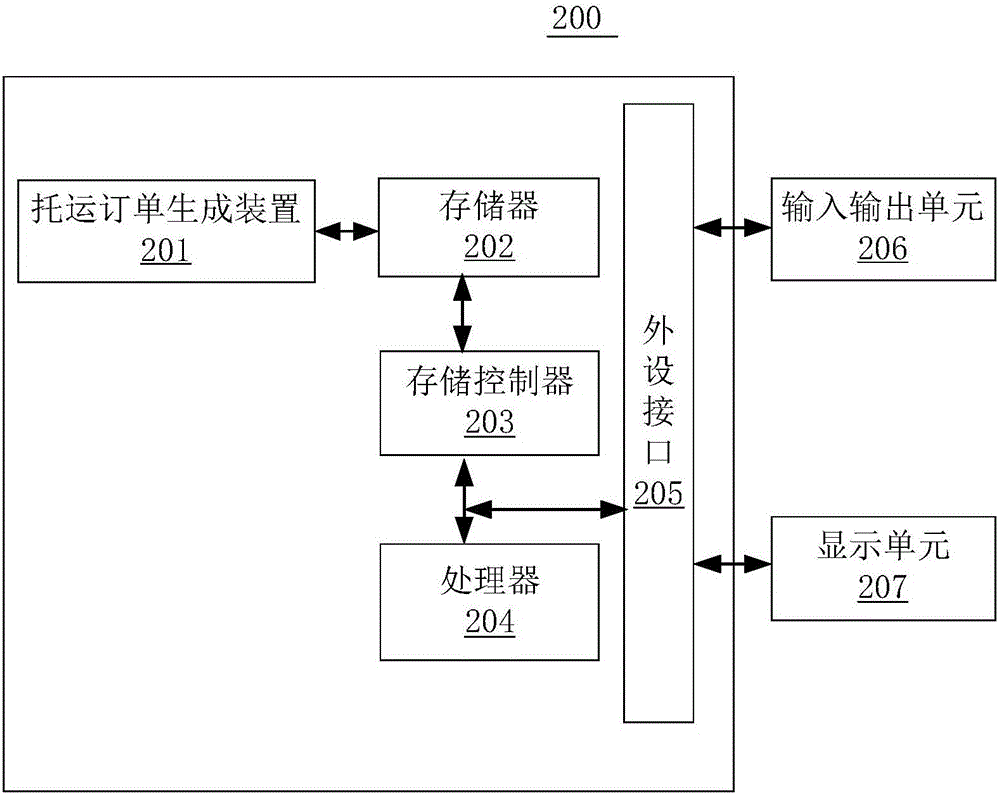
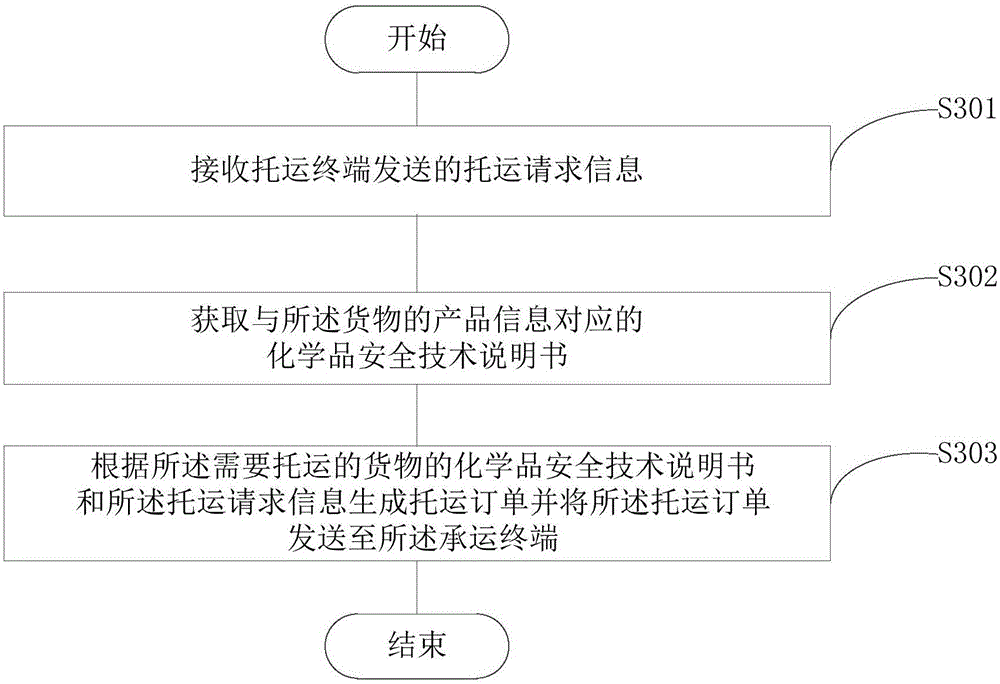
Consignment order generating method and device
The invention provides an order generating method and device. The technical problems that various aspects of dangerous goods transport are in separate operation management and are not in effective butt joint and data in a dangerous goods transport process cannot be timely uploaded, monitored and online queried in real time in market in the prior art are solved. The invention provides a transport management method, device and system. The system comprises a consignment terminal, a carrier terminal and the transport management device. The consignment terminal sends consignment request information to the transport management device. The transport management device matches consigned goods and a chemical safety technical specification, generates a consignment order according to the consignment request information and the corresponding chemical safety technical specification, and sends the consignment order to the carrier terminal. Through the system, the technical effects of goods consignment, information audit, goods consignment undertaking, corresponding information online interaction and query and the like are realized.
Owner:湖南润安危物联科技发展有限公司
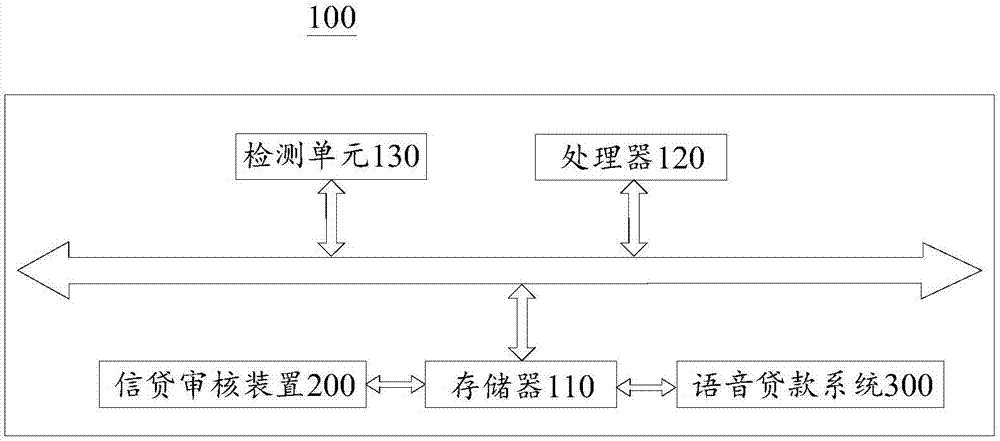
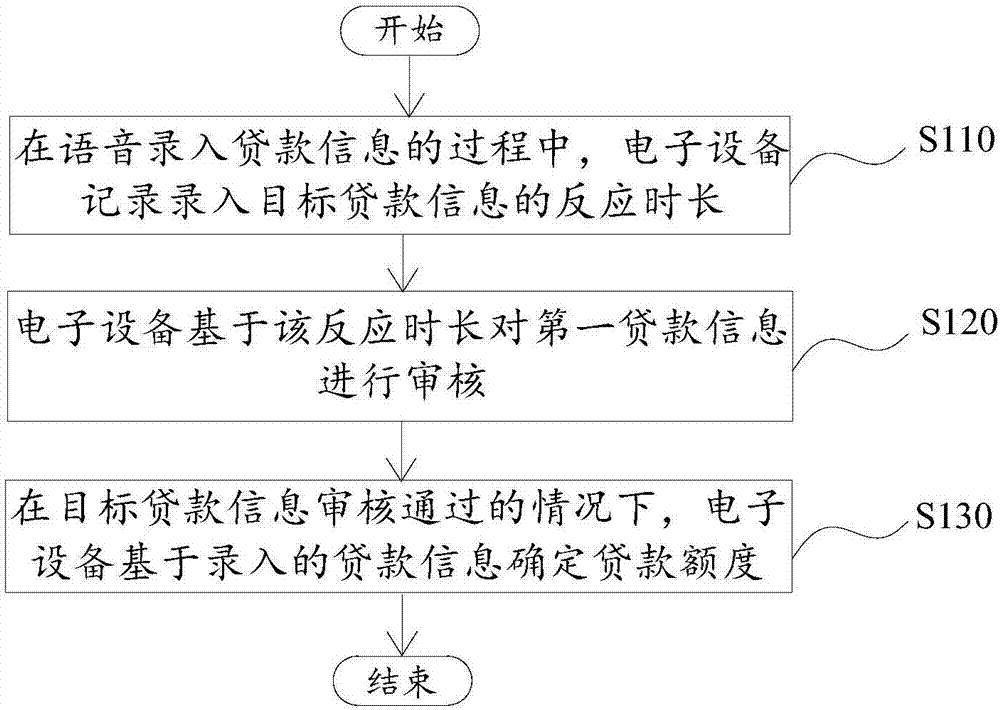
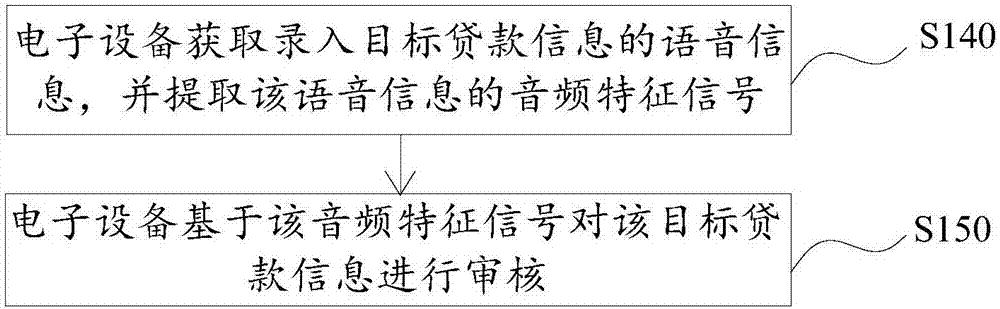
Information audit method and device
PendingCN107392757AImprove accuracyCorrect credit decisionFinanceSpeech recognitionComputer scienceSpeech sound
The present invention provides an information audit method and device. The method and device are applied to a voice loan system configured to record entering loan information through a voice mode. The method comprises: in the process of voice entering load information, recording reaction duration of recording target loan information, wherein the reaction duration is a time interval configured to perform prompt from the ending of voice broadcast of entering target loan information to starting of entering the target loan information; performing audit of the target loan information based on the reaction duration; and in the condition of passing of the target loan information audit, determining the loan limit based on the entered loan information. Therefore, the accuracy of the loan information audit can be improved, and the credit risk of a credit and loan platform. Besides, the loan information is audited through the reaction duration, and the information audit method and device are more accurate and rapid so as to greatly improve the audit efficiency compared to a traditional audit mode.
Owner:SIMPLECREDIT MICRO LENDING CO LTD
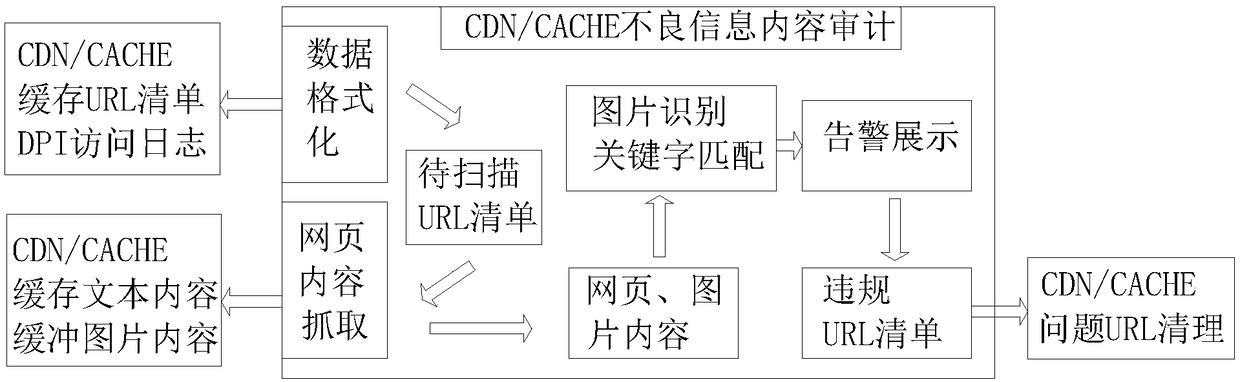
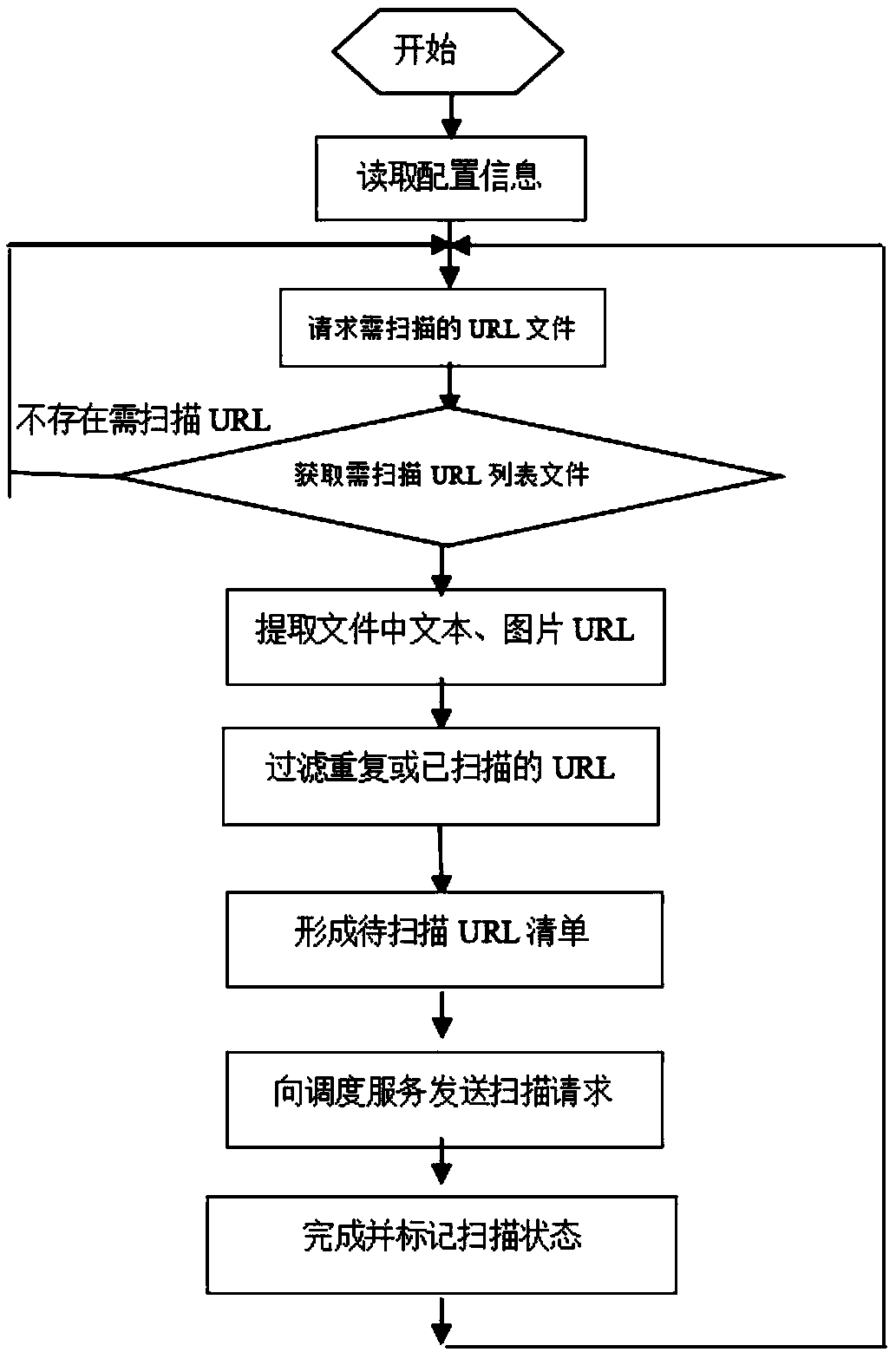
A method for auditing the content of bad information buffered by CDN and CACHE
InactiveCN109446461AEasy to readWebsite content managementWeb data queryingNetwork packetService coverage
The invention discloses a method for auditing the content of bad information buffered by CDN and CACHE. The method comprises the following steps of A acquiring a data packet through a data transmission interface; B carrying out the data format of a file analysis module; C using that file analysis module to generate URL to be scanned and transmit the URL to the web page content grabbing module; D using the data processing module to use the intelligent image recognition model to recognize the specific image of the picture, and complete the process of identifying and auditing the CDN / cache content. Compared with the prior art, the invention improves the service coverage range of the content audit, supports the bad information audit of the CDN / webcache service, and the crawler module can directly read the URL to be scanned through the file to carry out content crawling and obtain the web page content. By using the depth learning algorithm and simulating a human brain neural network, a model with high-level expressive force is constructed. Through the continuous training of big data and the frequent iteration, the precision can reach 99.5%.
Owner:CHENGDU SIWEI CENTURY TECH
Situation awareness method based on brain-like calculation
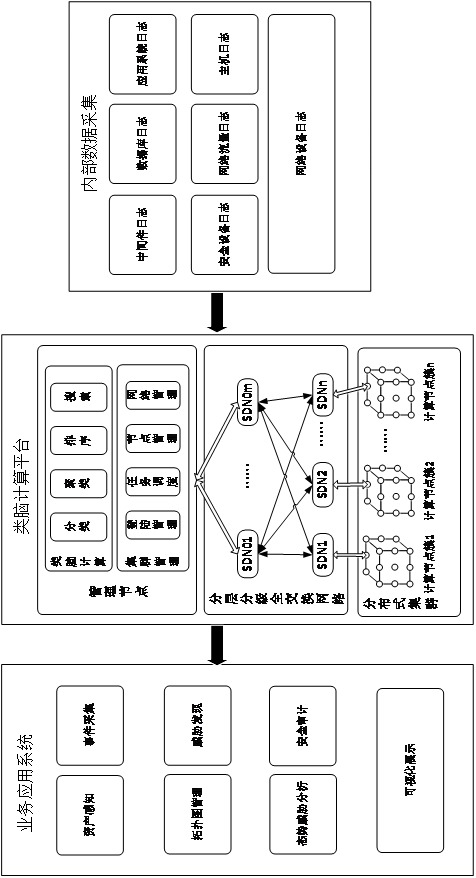
InactiveCN113242267ASecurity status visibleKnown security statusVisual data miningStructured data browsingEngineeringData mining
The invention discloses a situation awareness method based on brain-like calculation, and the method comprises the steps: obtaining state operation data, finding threats from the interior and exterior according to the state operation data, and carrying out the analysis and response of the threats; and determining mining abnormal intrusion information by analyzing the threats, auditing key data of a service system, and realizing corresponding functions by adopting a brain-like computing platform. According to the method, automatic learning, modeling and analysis are carried out from data to form a rule, and network situation assessment, network threat assessment and network situation prediction are carried out on the network space by using the rule, so that the security condition of the network space is visible, known, manageable, controllable, traceable and early-warning. A multi-level, multi-angle, multi-granularity, complete and detailed security situation awareness platform based on human, machine, object and other resource objects, a space-time range, an association relationship and other elements is constructed.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
Method and system for uniformly managing identity endorsement
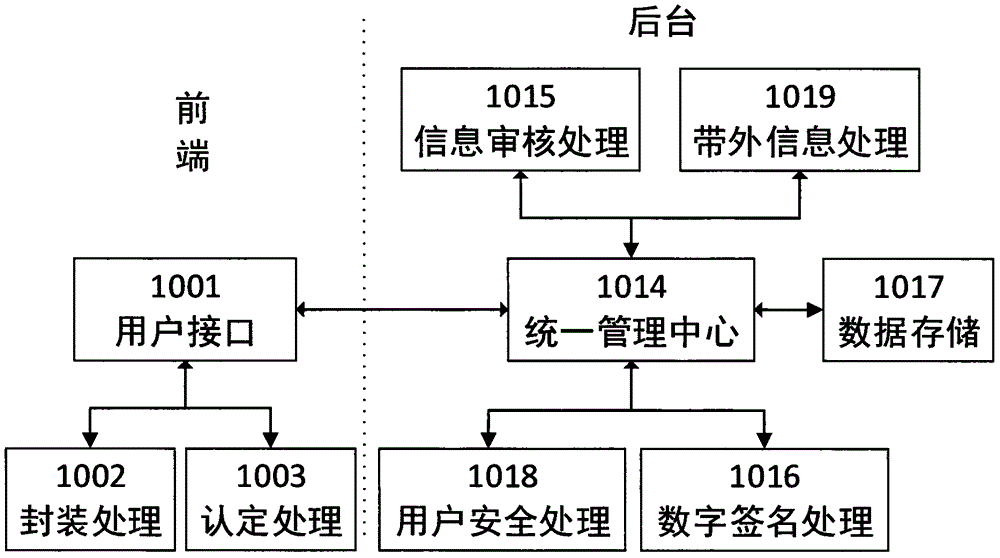
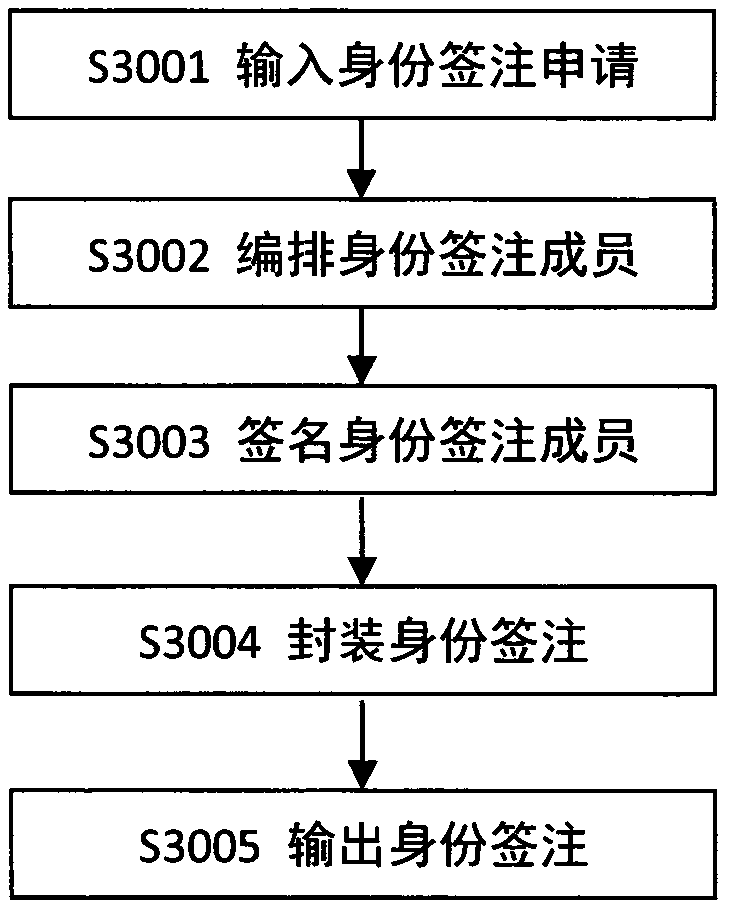
PendingCN106656511ASolve the real problemKey distribution for secure communicationUser identity/authority verificationInformation processingDigital signature
The invention discloses a method and system for uniformly managing identity endorsement. The method for managing the identity endorsement comprises the following steps: inputting an identity endorsement application, arranging identity endorsement members, signing the identity endorsement members by using asymmetric key algorithms and a unified private key, packaging the identity endorsement, and displaying, printing and recording the identity endorsement; the system for uniformly managing the identity endorsement comprises a front end application program and a background service program, the front end application program comprises a user interface unit, a package processing unit and a recognition processing unit, the background service program comprises a unified management center unit, an information audit processing unit, a digital signature processing unit, a data storage unit, and an out of band information processing unit. By adoption of the method and system disclosed by the invention, the problems of inconvenience, easy counterfeit and recognition difficulty and the like when people use certificates and cards in daily lives are solved, and the harms to the society caused by the counterfeit of the certificates and cards are avoided.
Owner:阳振庭
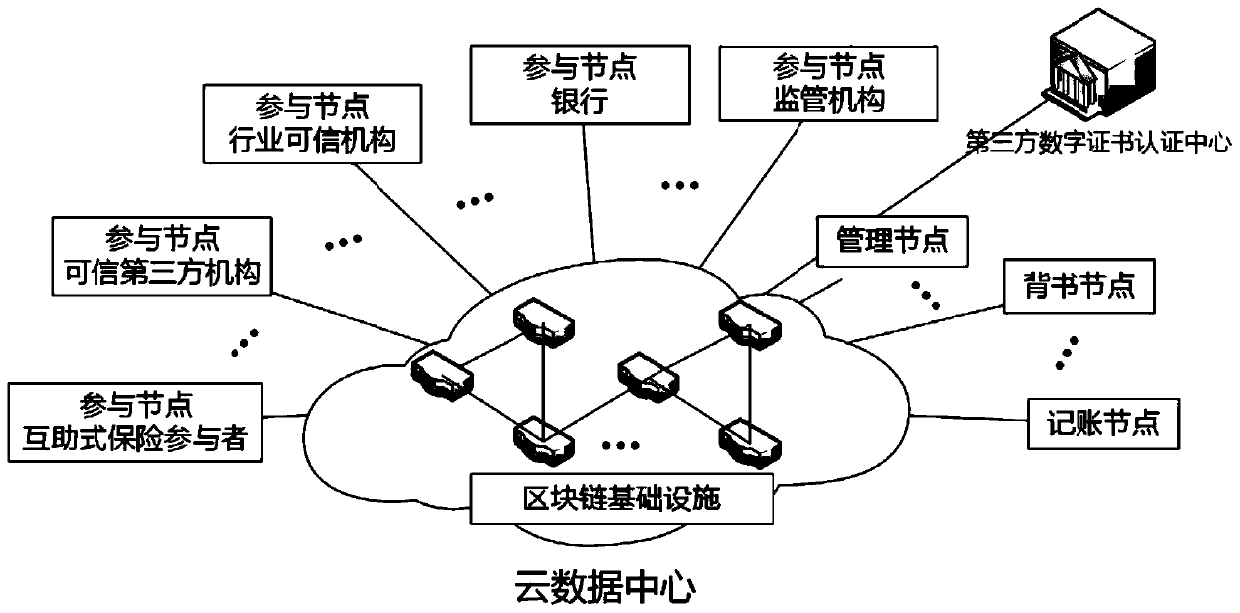
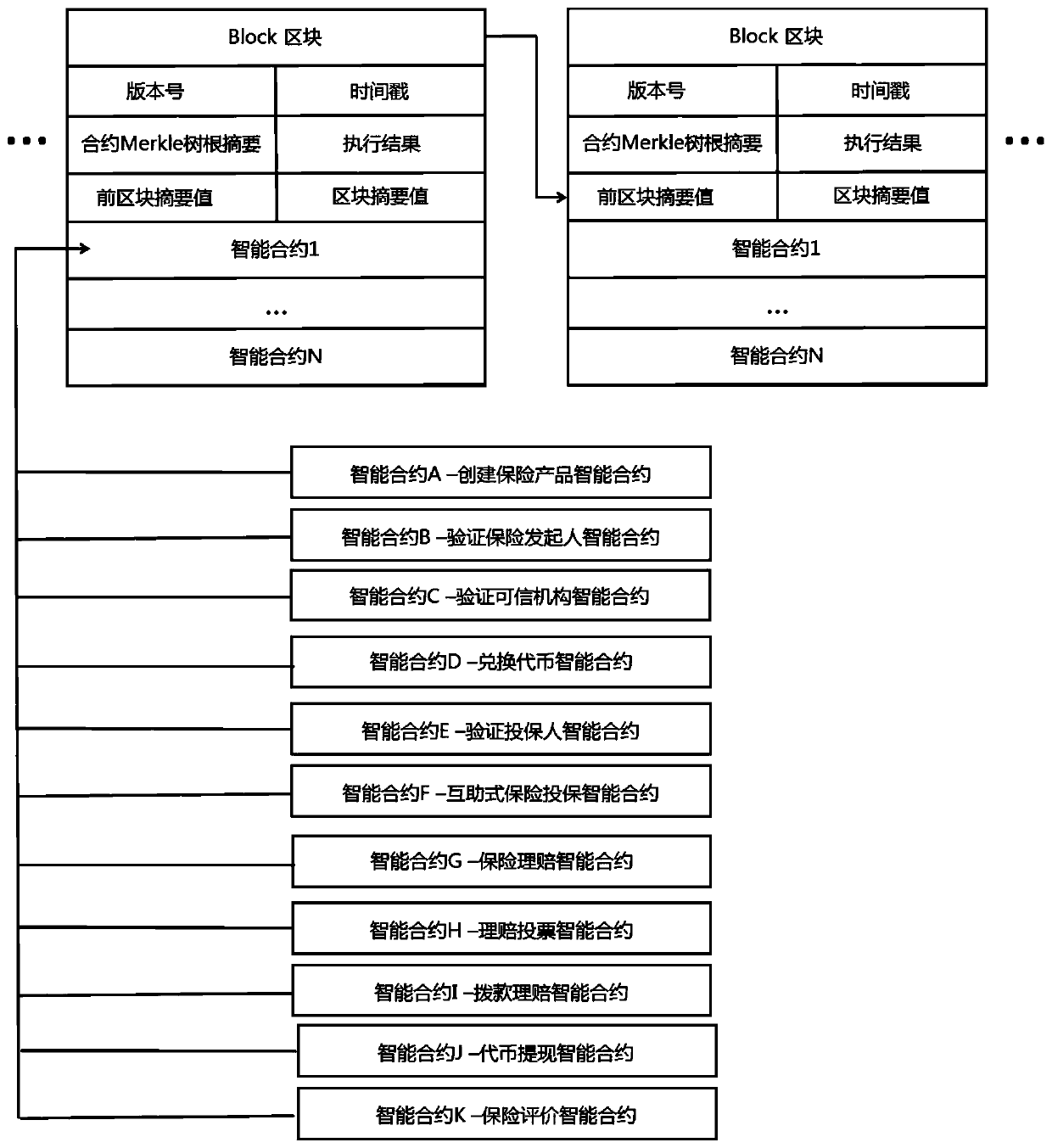
Mutual-help insurance method and device based on block chain, and medium
PendingCN111260485ARealize on-chainPrivacy protectionFinanceDigital data protectionThird partyInternet privacy
The invention discloses a mutual-help insurance method and device based on a block chain, and a medium. The method comprises the following steps: obtaining claim settlement application information sent by an insurance applicant terminal, and determining that the claim settlement application information conforms to insurance information according to an intelligent contract; sending the claim settlement application information to a third-party authentication institution for auditing, and determining to form a claim settlement case; obtaining anonymous claim settlement application information after anonymization processing of a third-party authentication institution, voting the anonymous claim settlement application information by each node on the mutual-aid insurance block chain according tothe intelligent contract, and determining to perform claim settlement; and sending the claim settlement application information to a supervision institution, determining a claim settlement amount bythe supervision institution according to the claim settlement fund balance checked by the intelligent contract and the claim settlement application information audited, and sending the corresponding compensation token to the account of the insurer side. An insurance participant, an identification institution and a supervision institution are combined, privacy of an insurance applicant is protectedthrough anonymization processing, and fair and transparent compensation is realized through a voting mechanism.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
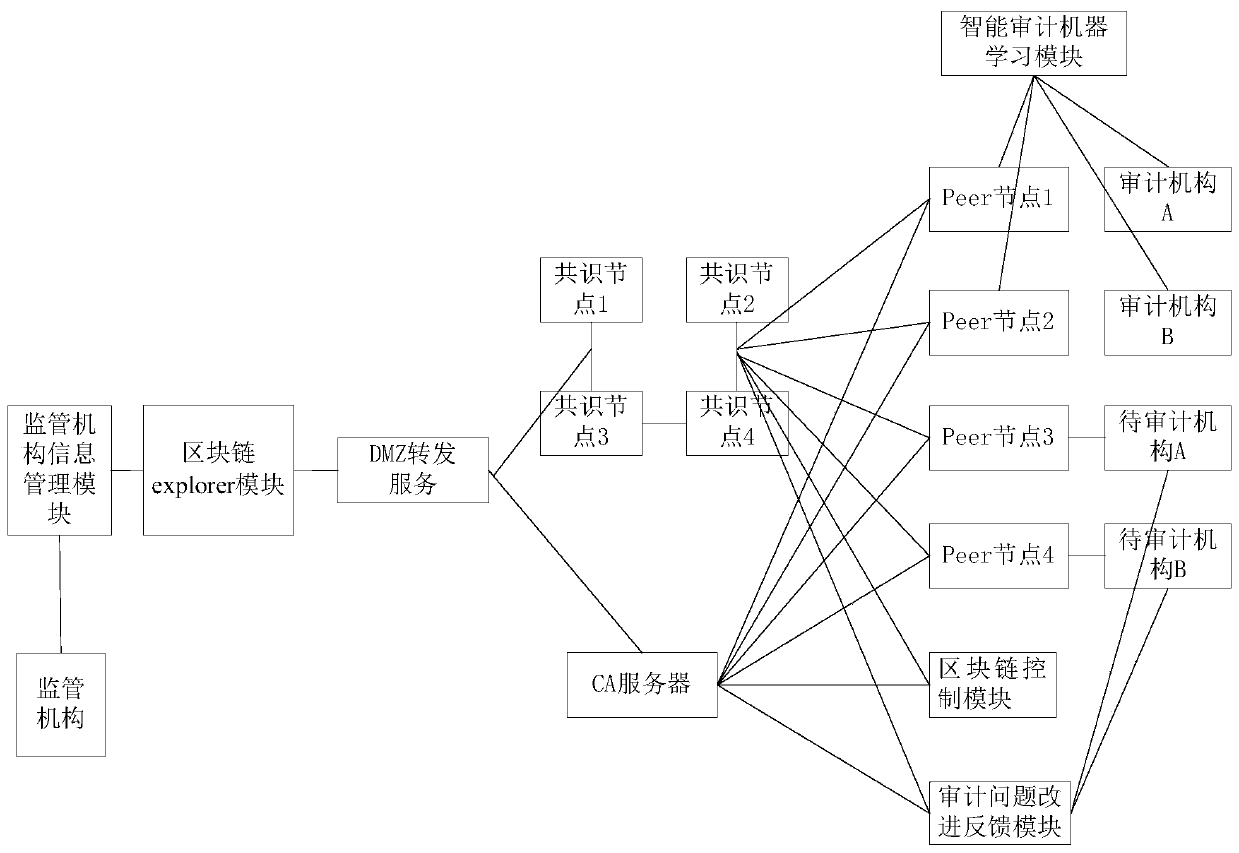
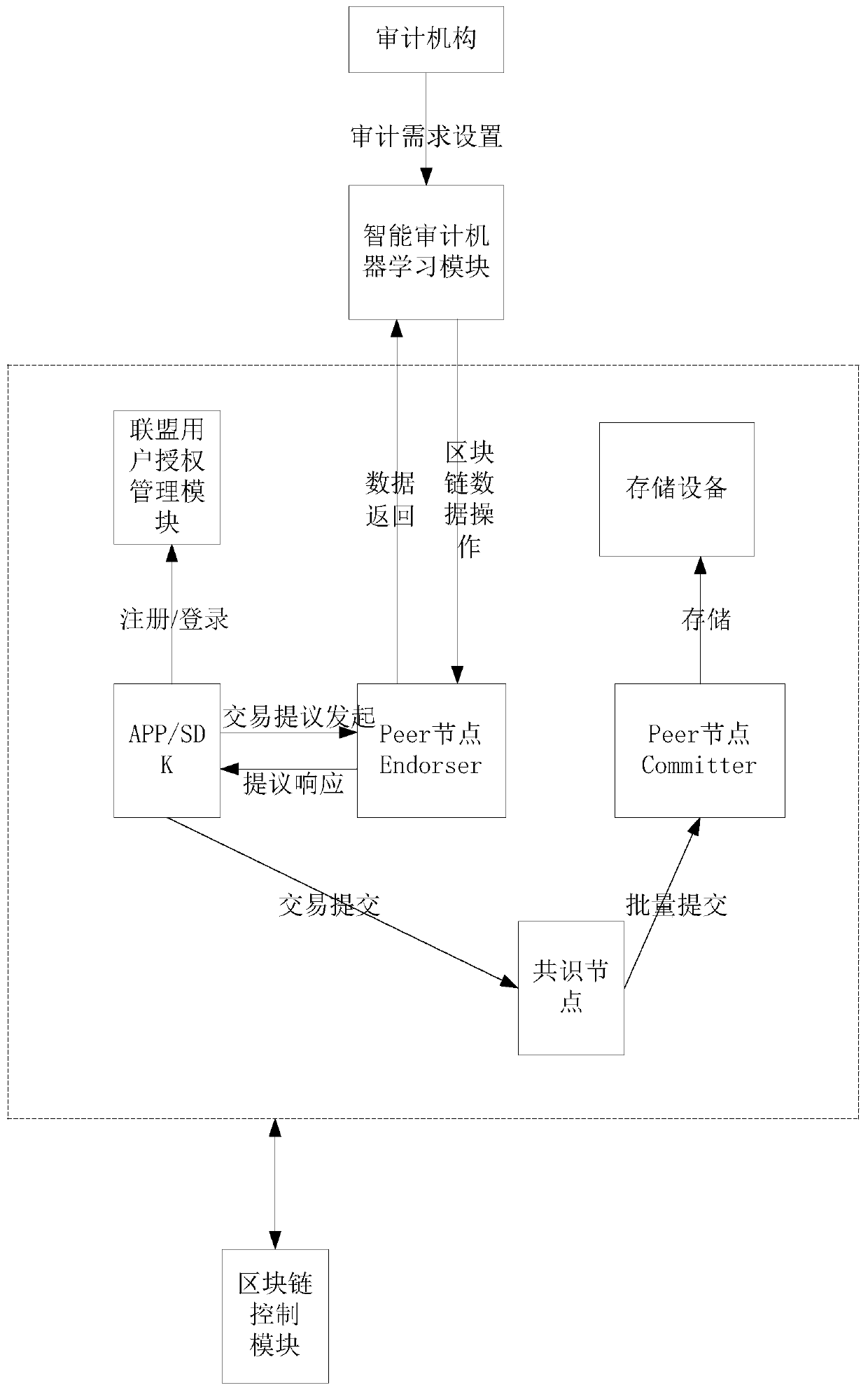
Intelligent auditing system, equipment and method based on block chain
PendingCN110990487AGuaranteed accuracyAdd feedback mechanismFinanceDatabase distribution/replicationAuthorizationAuthentication
The invention provides an intelligent auditing system and method based on a block chain, computer equipment and a computer readable storage medium, and relates to the technical field of data processing. The system comprises an alliance user authorization management module which is used for carrying out authority management on an accessed auditing mechanism and a to-be-audited mechanism, so that the auditing mechanism and the to-be-audited mechanism become nodes in a block chain after completing authentication and registration; the block chain service module is used for selecting a consensus mechanism and implementation logic of block operation; and the intelligent auditing machine learning module is used for receiving auditing demand information input by an auditing institution user and outputting an auditing scheme and implementation steps according to the auditing demand information. According to the system and the method, various audited information, audit report information and audit improvement information are uploaded, block construction packaging and related operations are carried out by various mechanisms and audit units, data sharing is realized on the basis of ensuring authenticity, an audit process is optimized, and the accuracy of an audit result is ensured.
Owner:BANK OF CHINA
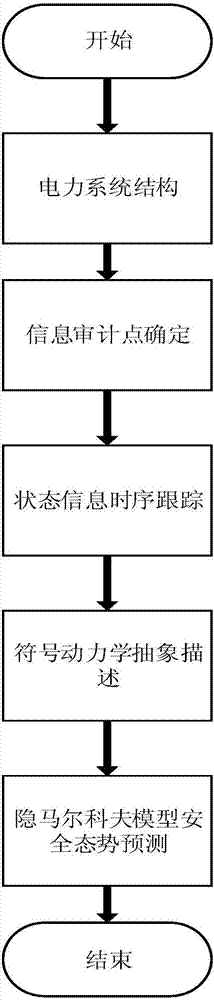
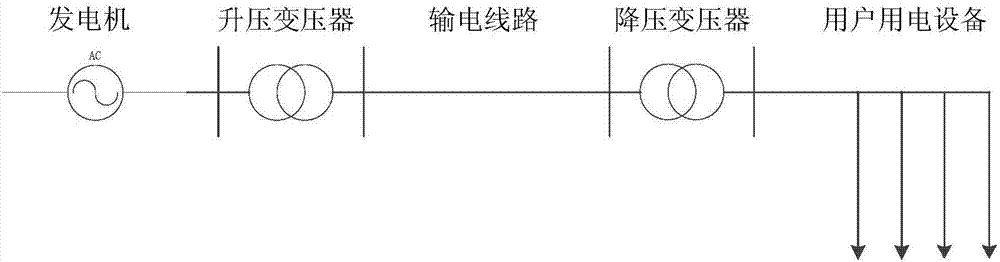
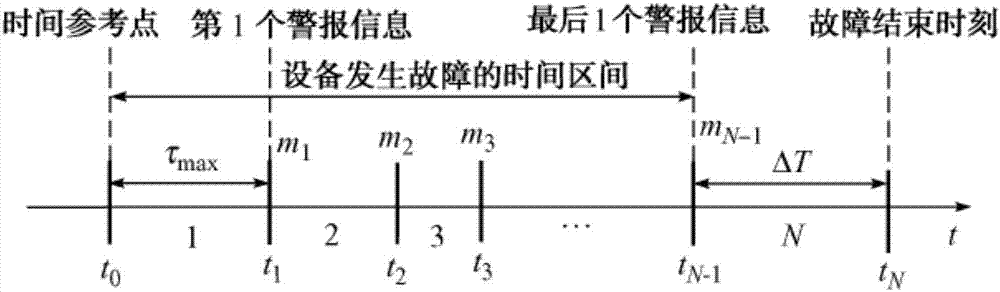
Spatio-temporal multidimensional safety assessment method for power equipment based on symbolic dynamics and Hidden Markov models
ActiveCN107292512AImprove performance of security assessmentsAccurately reflect the operating lawResourcesSystems intergating technologiesPredictive methodsElectric power system
The invention relates to a spatio-temporal multidimensional safety assessment method for power equipment based on symbolic dynamics and Hidden Markov models, and in particular to sub-link information auditing, time sequence tracking, risk assessment technology and a security situation prediction method based on symbolic dynamics and Hidden Markov models. The advantages of the present invention are as follows: 1. the structural division of a power system can optimize the collection of evaluation factor information; 2. The determining of the information audit points in various links and the improving of the audit information make the power equipment operation status information collection more accurate; 3. The time sequence tracking to the fault information of the audit points in various links considers the historical operation state of the power equipment, which makes the safety assessment more accurate; 4. the operation rules of power equipment can be accurately reflected; and 5. the use of hidden Markov models for the calculation of the prediction of the safety situation and, at the same time, the establishment of a suitable threshold to determine whether there is a safety risk of power equipment improve the accuracy of the assessment of the safety situation.
Owner:CHINA ELECTRIC POWER RES INST +2
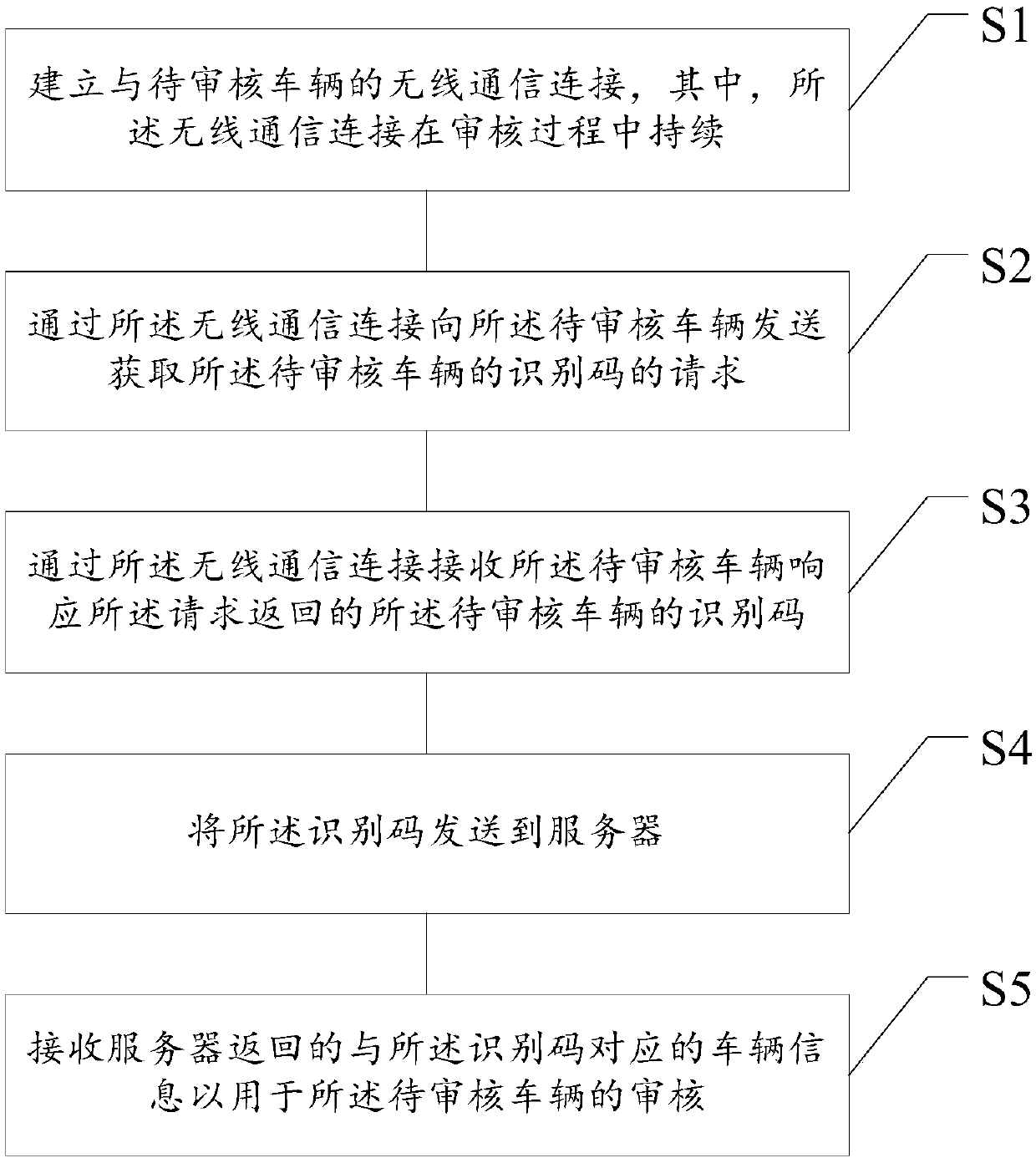
Vehicle information audit method and device, storage medium and electronic equipment
ActiveCN107909378AImprove experienceSimple review stepsFinanceCharacter and pattern recognitionInformation auditElectronic equipment
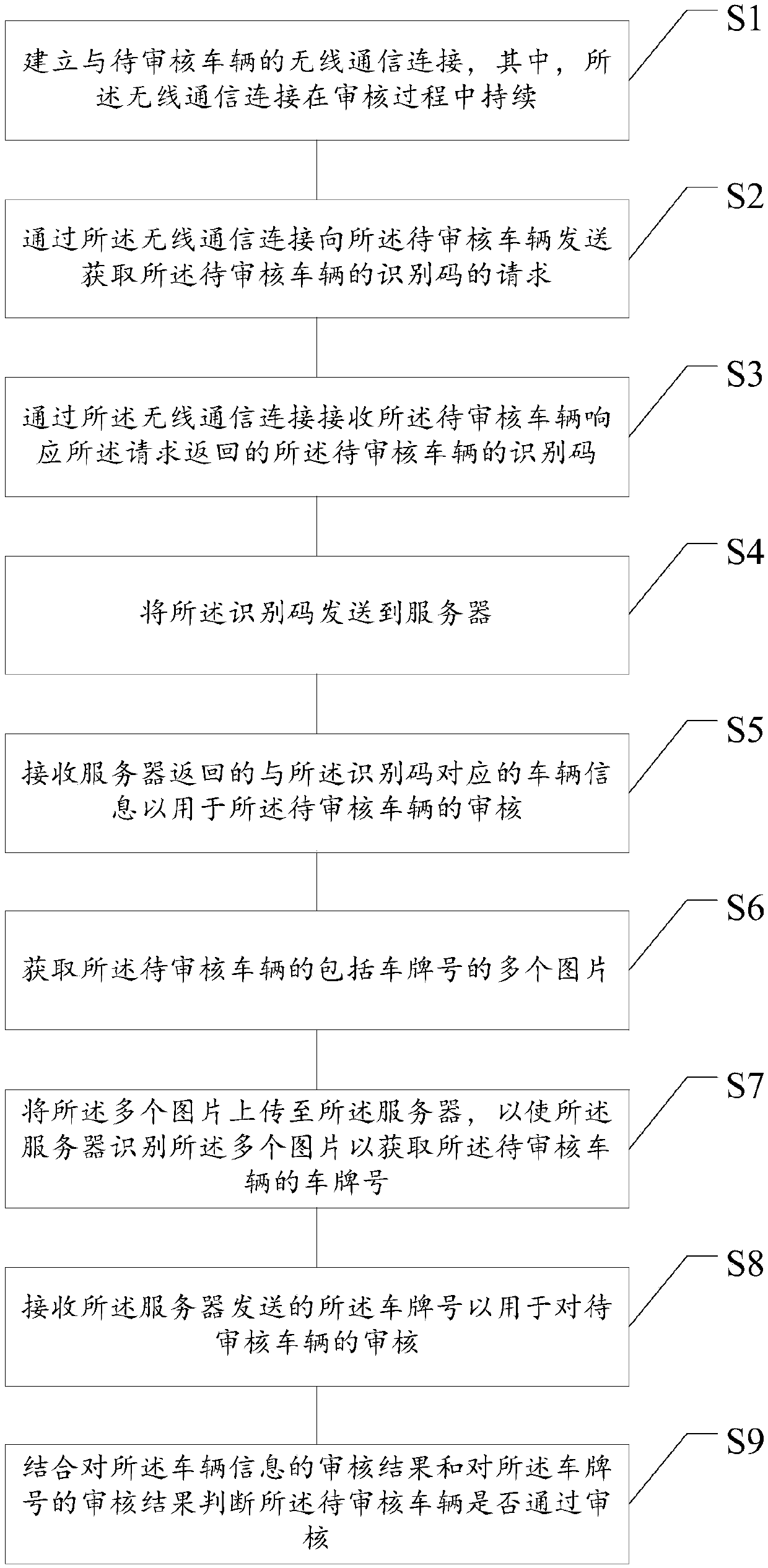
The invention relates to the data processing technology field and particularly relates to an insurance business vehicle information audit method and device, a storage medium and electronic equipment.The method comprises steps that wireless communication connection with a to-be-checked vehicle is established, and wireless communication connection is continued in the check process; a request for acquiring an identification code of the to-be-checked vehicle is sent to to the to-be-checked vehicle through wireless communication connection; an identification code of the to-be-checked vehicle returned for responding to the request is received through wireless communication connection; the identification code is sent to the server; the vehicle information which is returned by the server and corresponds to the identification code is received and is for check of the to-be-checked vehicle. The method is advantaged in that uniqueness and validity of the to-be-checked vehicle in the whole check process are guaranteed, the mode is simple and effective, the check step is simple, the method is not limited by location, light and environment factors, user experience is relatively good, moreover, compared with the prior art, check efficiency is higher, and check accuracy is higher.
Owner:TAIKANG LIFE INSURANCE CO LTD +1
Sharing hotel operation system based on cloud
InactiveCN108320240AQuality Asset ManagementHigh-quality operation serviceData processing applicationsTransmissionSystems managementPassword
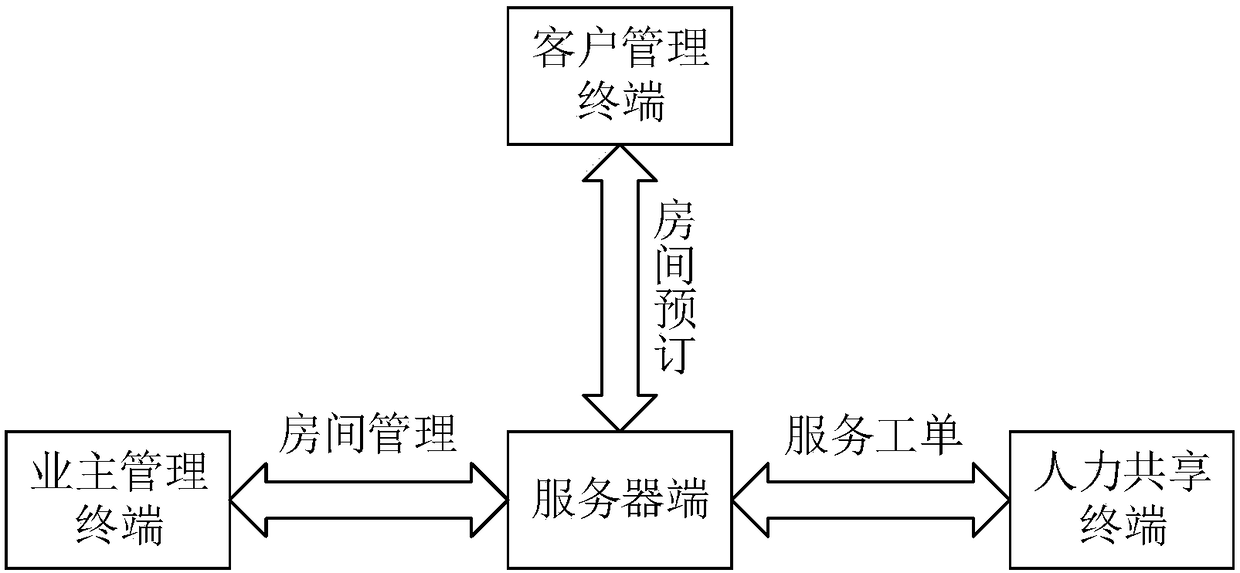
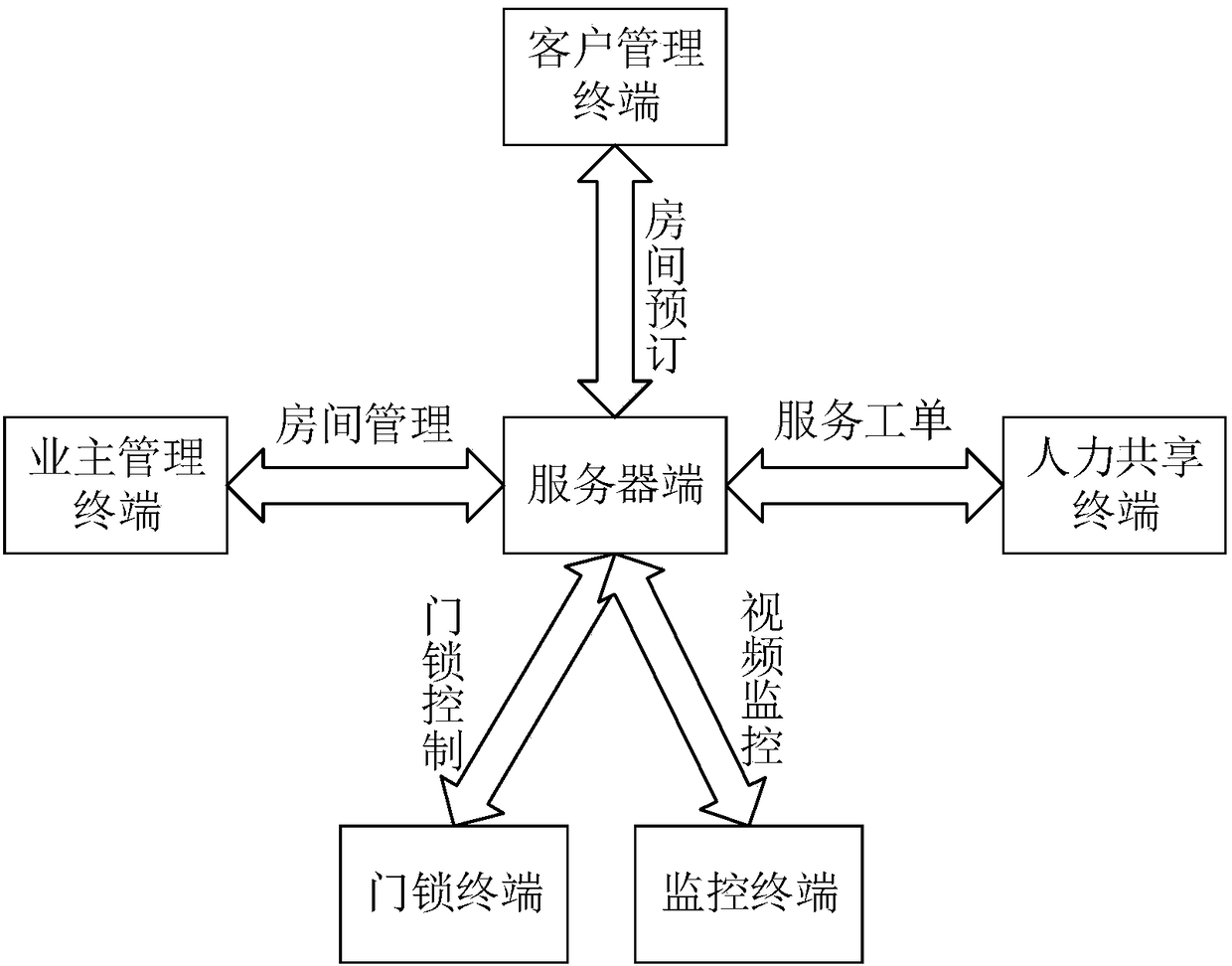
The present invention discloses a sharing hotel operation system based on cloud. The system comprises a server, an owner management terminal, a client management terminal and a human sharing terminal.The server is configured to perform business data interaction with the owner management terminal, the client management terminal or the human sharing terminal; the owner management terminal is configured to publish room information audited by the server; the client management terminal is configured to obtain door opening passwords according to the room information and perform feedback of the dooropening passwords to the client management server; and the human sharing terminal is configured to receive a service work order pushed by the server and reply an order receiving request or a work order completion request to allow the server to perform corresponding marking of the service work order. The sharing hotel operation system based on cloud can achieve unmanned system management from checking-in to checking-out of clients online and can integrate scattered labor resource offline to provide cleaning service so as to allow more hotel owners to share more high-quality asset management and operation service.
Owner:广州搜床网络科技有限公司
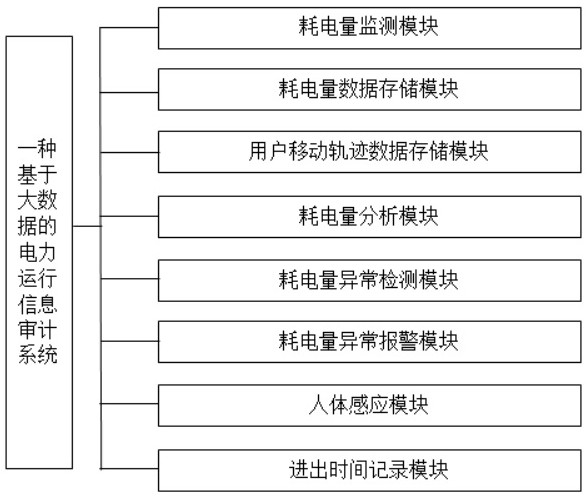
Electric power operation information auditing system based on big data
ActiveCN112600310AReduced chance of burnoutTimely replacementPower network operation systems integrationCircuit arrangementsElectric powerReliability engineering
The invention discloses a electric power operation information auditing system based on big data. The system comprises a power consumption monitoring module, a power consumption data storage module, auser movement track data storage module, a power consumption analysis module, a power consumption abnormality detection module, a power consumption abnormality alarm module, a human body induction module and an in-out time recording module. The system has the beneficial effects that: the method divides the indoor area of the home, determines the current area of the user and the residence time ofthe user in the area, acquires the power consumption data of each area in a certain time period through the power consumption monitoring, further classifies the household electric appliances of each area, acquires preset value of each area according to the area where the user is located and the household electrical appliance classification of each area, and accurately detects whether the power consumption of each area is abnormal or not by comparing the actual power consumption data of each area with the preset value, so that the possibility that the electrical appliance is burnt due to long-time work is reduced, and the potential safety hazard is reduced.
Owner:GUANGDONG UNIVERSITY OF BUSINESS STUDIES
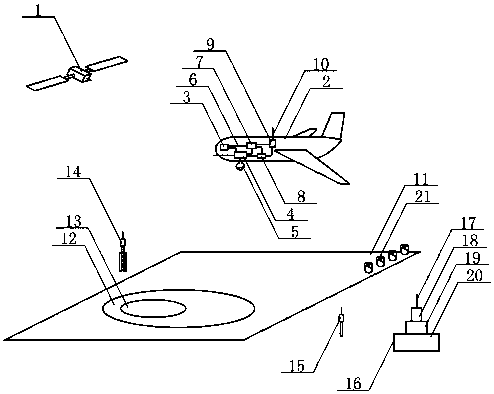
Insurance claim settlement system for determining freeze injuries of cabbage fields by use of drone based on Beidou navigation
InactiveCN107664487AEasy turnoverEasy to useFinanceSatellite radio beaconingEngineeringFreeze injury
The invention relates to an insurance claim settlement system for measuring freezing damage in cabbage fields by an unmanned aerial vehicle based on Beidou navigation, and belongs to the new technology field of insurance claim settlement. The Beidou satellite operating at high altitude communicates with the airborne mobile base station of the UAV cruising at low altitude above the cabbage field through radio waves, and the Beidou satellite communicates with the split mobile base station and the The integrated mobile base station set up on the right side of the cabbage field communicates information, adopts the enhanced technology combining the low-altitude base station and the ground base station, so that the user terminal of the insurance company can quickly and accurately measure the freezing damage area of the cabbage, and at the same time combines the photoelectricity of the drone The image information of the cabbage freezing damage recorded by the camera in the pod is used to review the degree of the cabbage freezing damage, and provide information on the area of the cabbage freezing damage and the degree of freezing damage to the insurance company. According to the contract and claim standard for farmers to insure the cabbage freezing damage agricultural insurance, use computer B to calculate the amount of cabbage freezing damage compensation. , and inform the insured farmers to receive the compensation in time.
Owner:WUXI TONGCHUN NEW ENERGY TECH
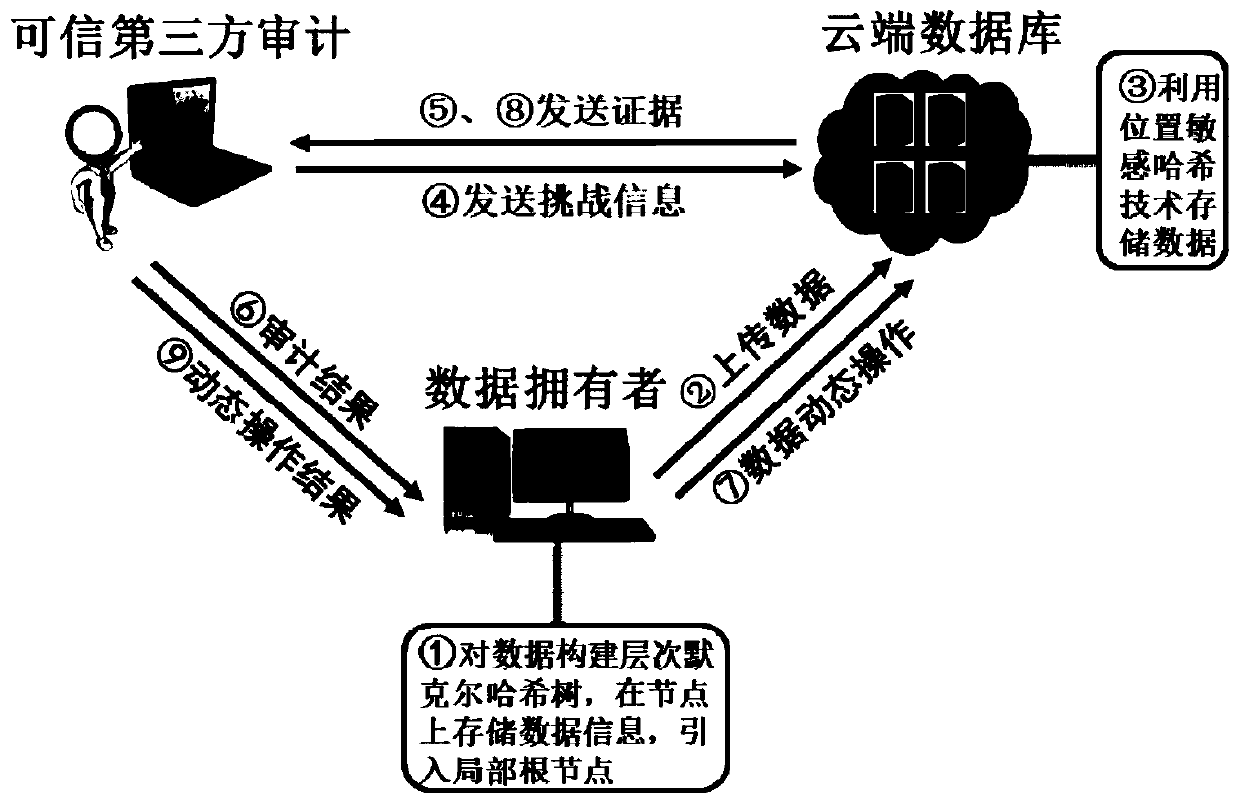
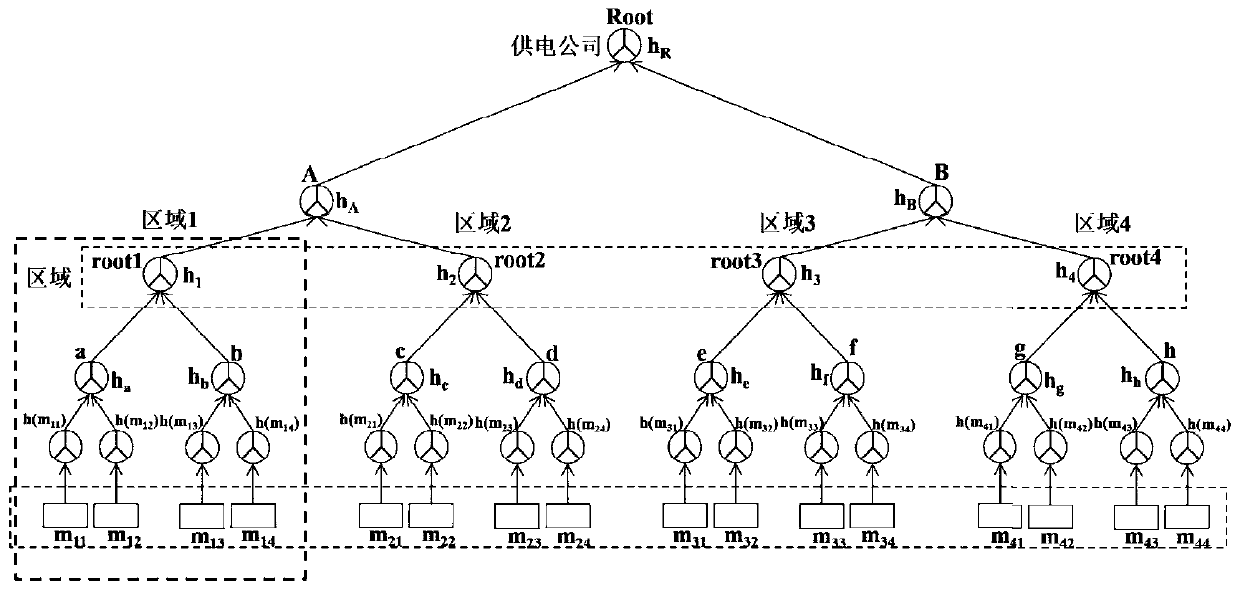
Light dynamic data integrity auditing method based on hierarchical Merkel hash tree
ActiveCN110958109AImprove update efficiencyIncrease profitEncryption apparatus with shift registers/memoriesDigital data protectionData integrityData information
The invention discloses a light dynamic data integrity auditing method based on a hierarchical Merkel hash tree, which comprises the following steps that: 1) a data owner constructs the hierarchical Merkel hash tree for data, stores data information on a node, and introduces a local root node; 2) a cloud database stores the data of the data owner by using a position sensitive hash technology; 3) the cloud database generates challenge evidence according to the challenge information audited by a trusted third party; 4) the trusted third-party audits the integrity of the evidence ; and 5) when dynamic operation is performed on the data, the cloud database generates evidence, and the trusted third-party performs integrity auditing on the dynamic data. Compared with the prior art, the method ishigh in the auditing efficiency, can be effectively reduce the communication and calculation expenditure, and supports efficient data updating.
Owner:SHANGHAI UNIVERSITY OF ELECTRIC POWER
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com