Method for auditing SDN
A network and audit report technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as missed reports, lack of global vision, maliciousness, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
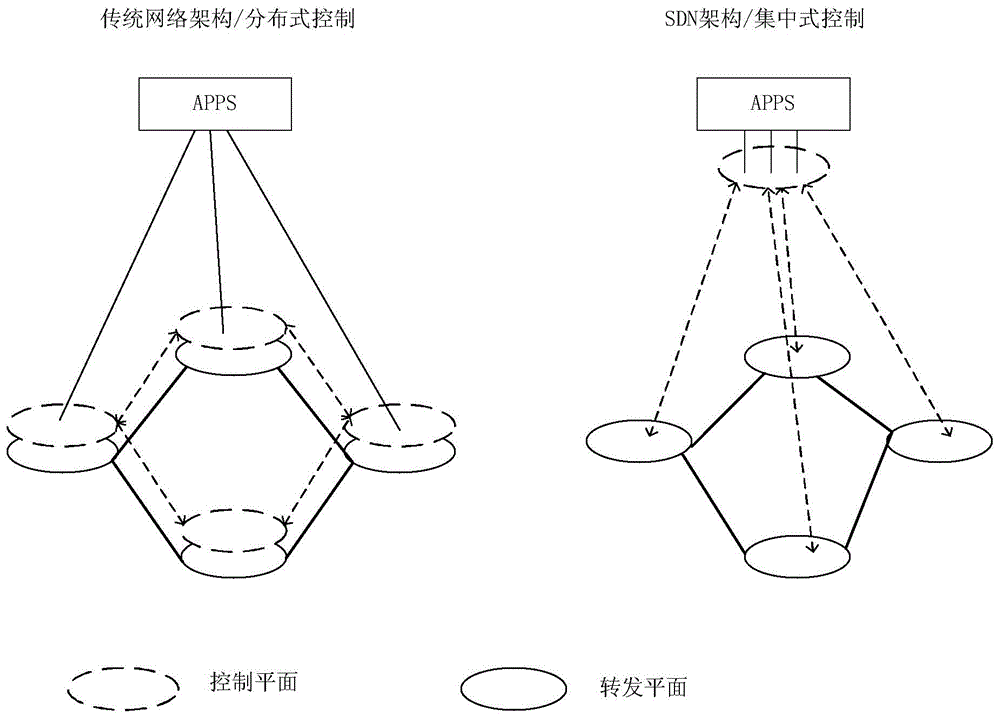
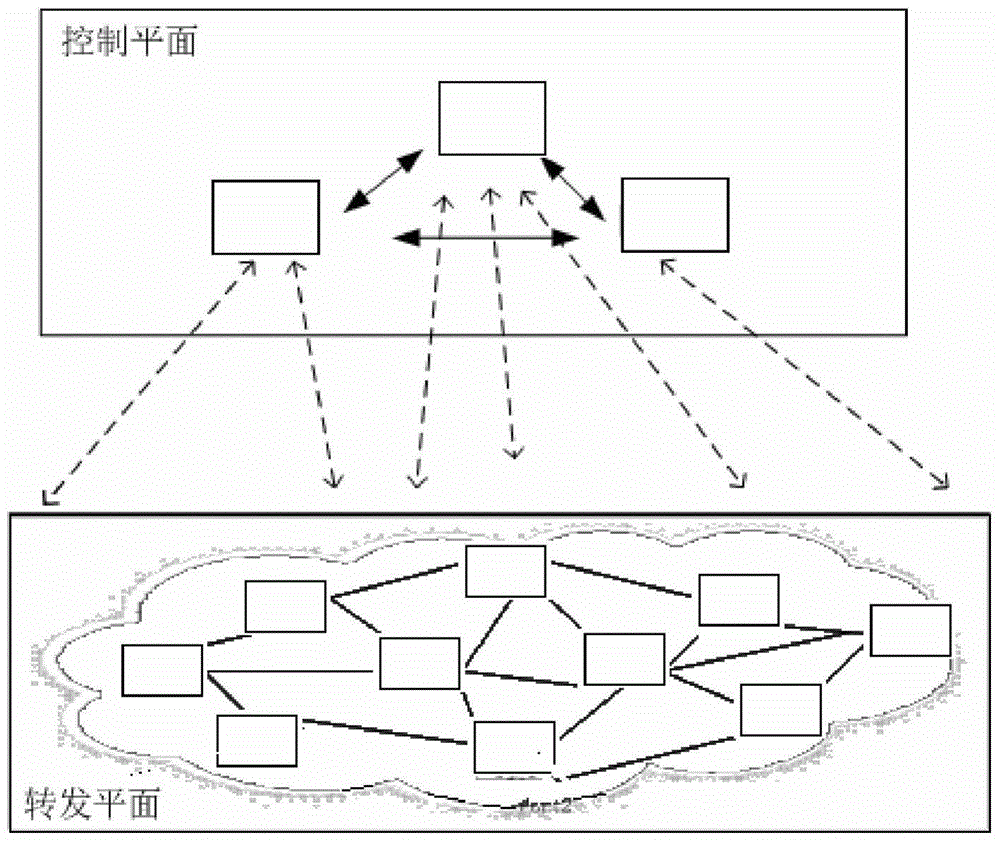
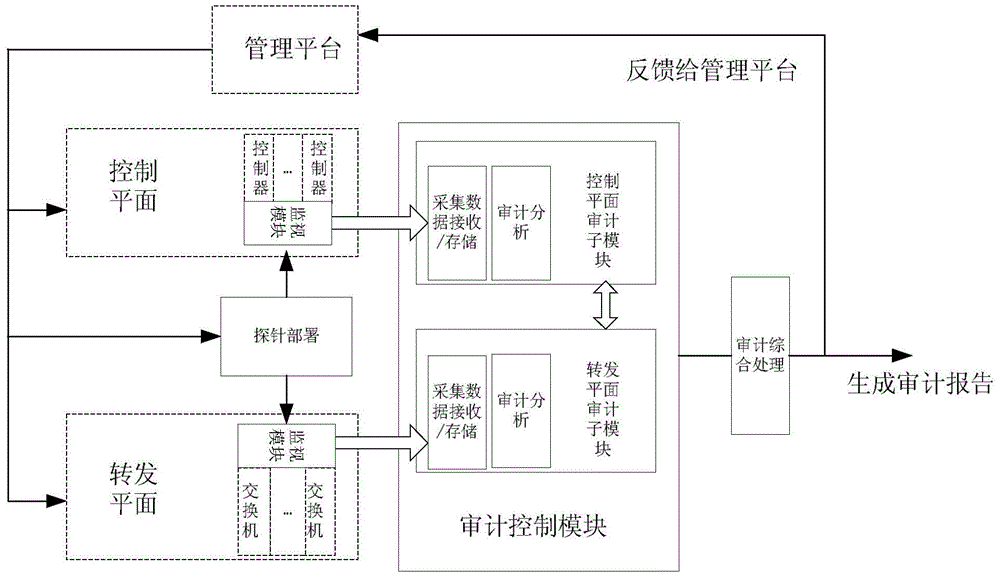
[0039] Example 1: figure 2It is the scheme of the present invention, based on the audit model of SDN network, wherein the dotted line box is the existing equipment, and the solid line box is the scheme device of the present invention, wherein:
[0040] The probe deployment step is to deploy probes on the SDN network control plane and forwarding plane according to the management decision, that is, the monitoring step; the management decision is based on the network’s own status, audit report recommendations or SLA (service level agreement) and other comprehensive formulations;
[0041] The monitoring step is used to monitor and collect statistics on SDN network traffic and events. Specifically, the audit content of the control plane includes but is not limited to application authentication, network element identity authentication, virus / attack detection and protection, security / control policy conflicts, configuration errors, etc. The collection / audit methods of the control pla...
Embodiment 2
[0055] Embodiment 2: as Figure 4 The control plane audit steps shown,
[0056] In this embodiment, the typical application authentication of the SDN control plane is taken as an example. The monitoring equipment of the control plane collects all data containing authentication information through the DPI deep message detection technology (the method of DPI collection may specifically be based on the DPI identification step Predetermined feature words are used to identify authentication-related information, and the DPI control step collects and sends the identified data), and sends it to the control plane audit control sub-step (audit control device 103 in the figure) for processing, wherein the collected data receiving / storage unit The received data is cached, and the audit analysis unit performs audit analysis on the data according to predetermined rules (such as based on authentication results / time / application type, etc.), and the analysis results are sent to the audit compr...
Embodiment 3
[0057] Embodiment 3: as Figure 5 The forwarding plane audit steps are shown.
[0058] In this embodiment, the flow of the forwarding plane flowing through the first port of the first device 101, the second port and the third port of the second device 102 is collected by means of bypass monitoring / statistics. First, the management platform is based on customer requirements or management It is required to deploy probes / monitors on the forwarding plane. This embodiment is mainly deployed on some ports of the first device 101 and the second device 102. The first port, the second port and the third port flow are collected, and the collected data is transmitted to the audit control step (audit control device 103 in the figure) through the interface of the monitor and the audit control step, wherein the collected data receiving / storage unit is to the received data Perform caching, the audit analysis unit performs audit analysis on the data according to predetermined rules (such as ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com