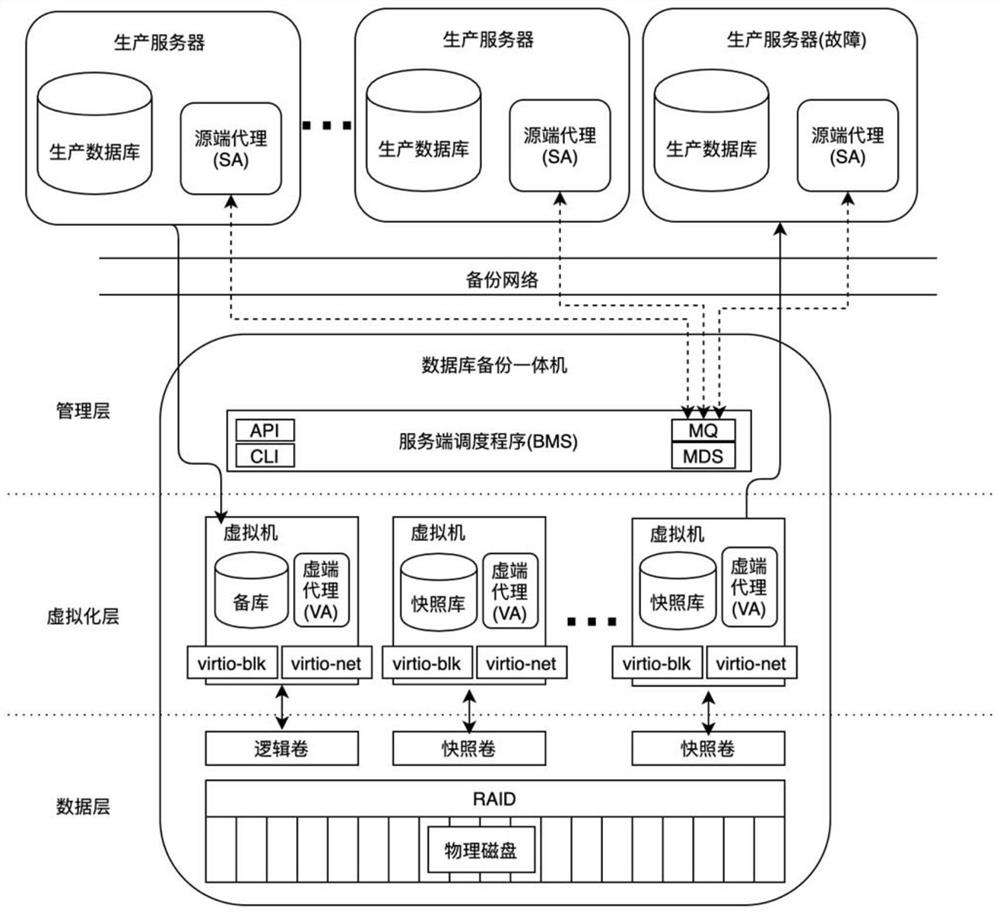
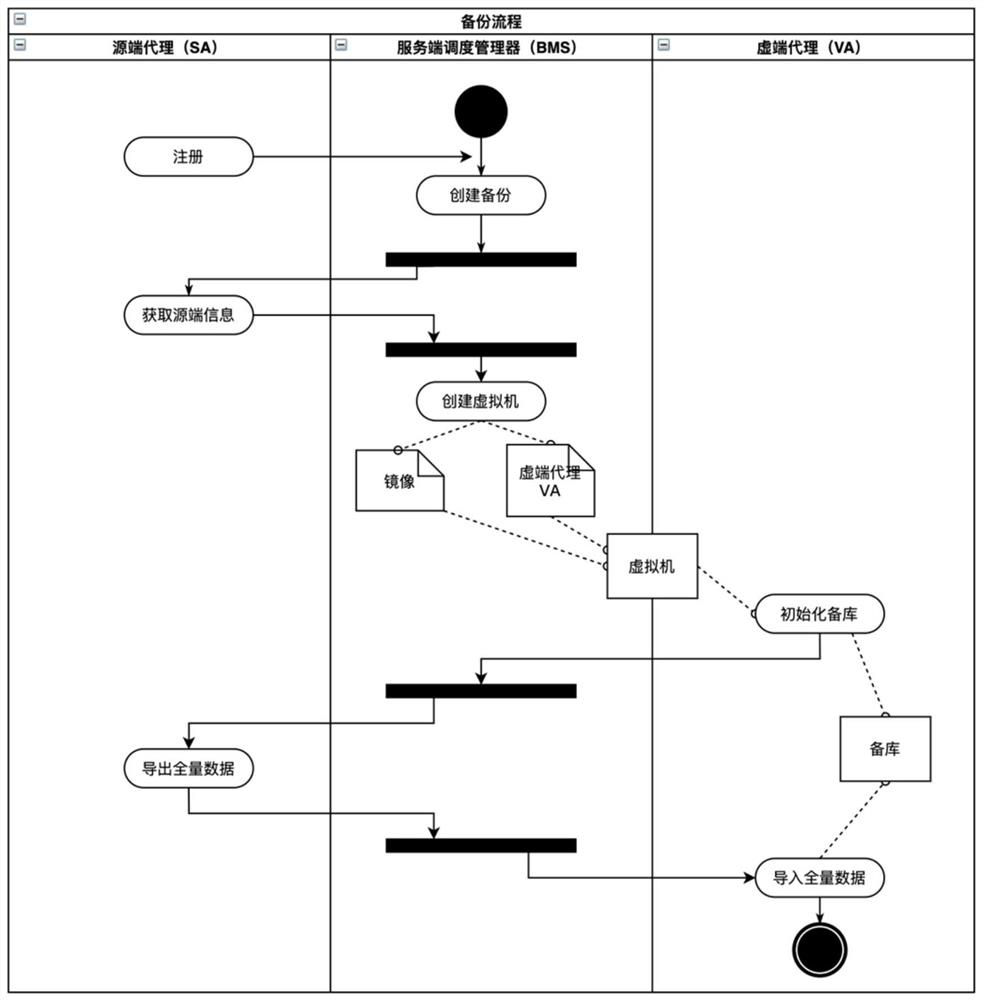
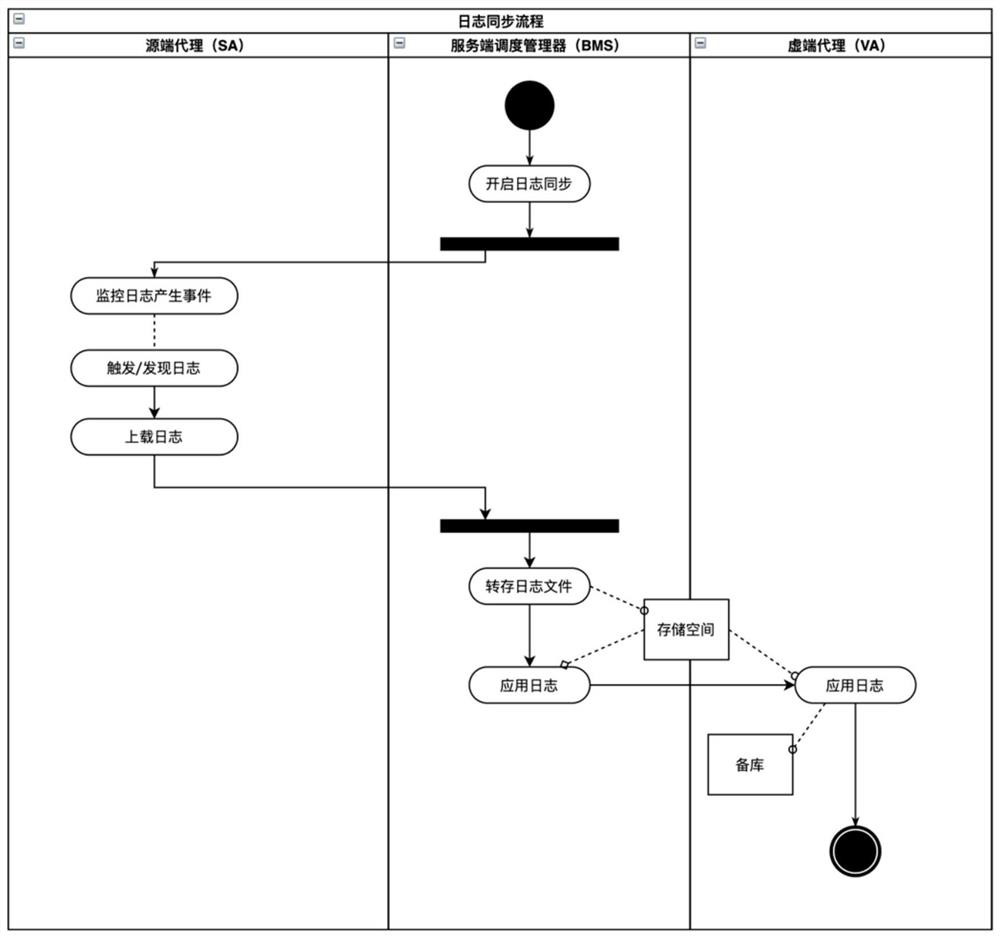
Patents
Literature
33results about How to "Achieve data recovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
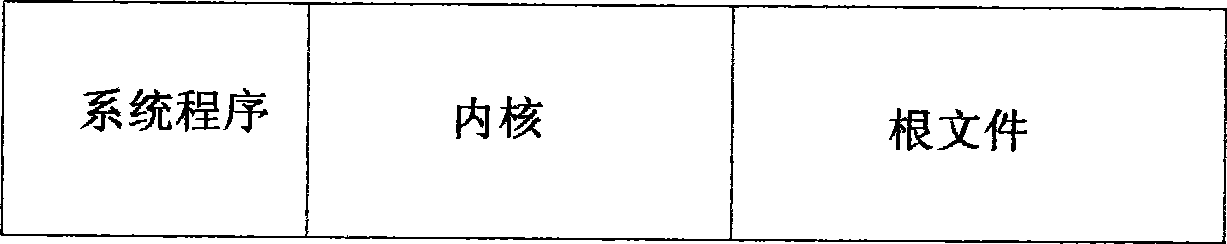
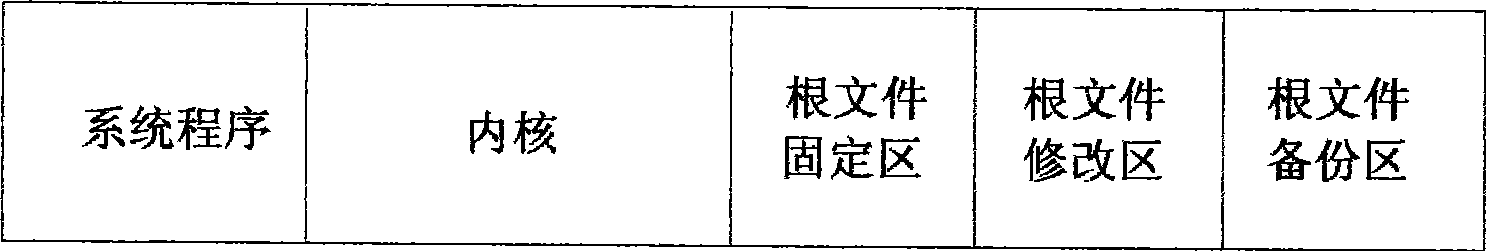
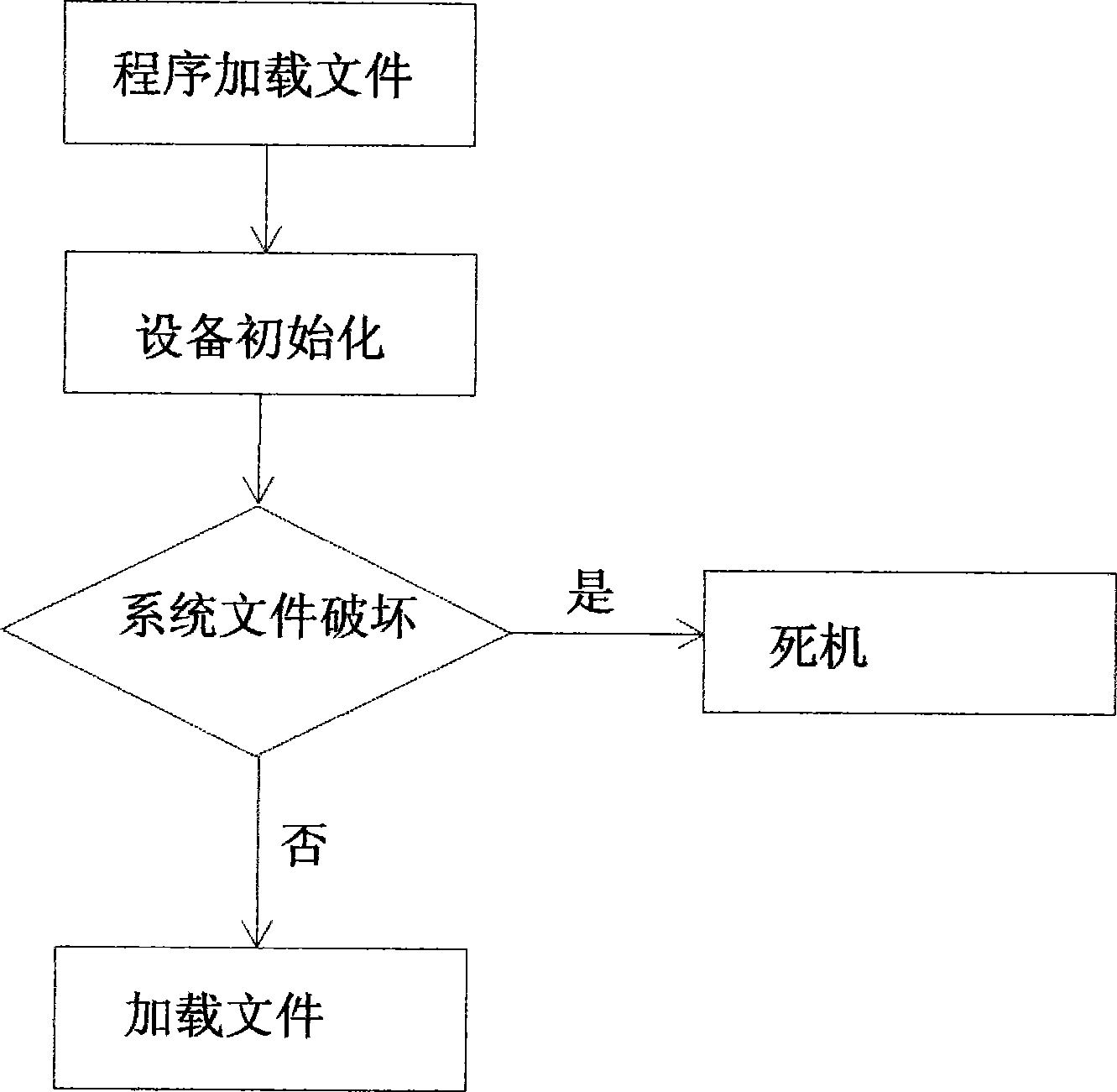
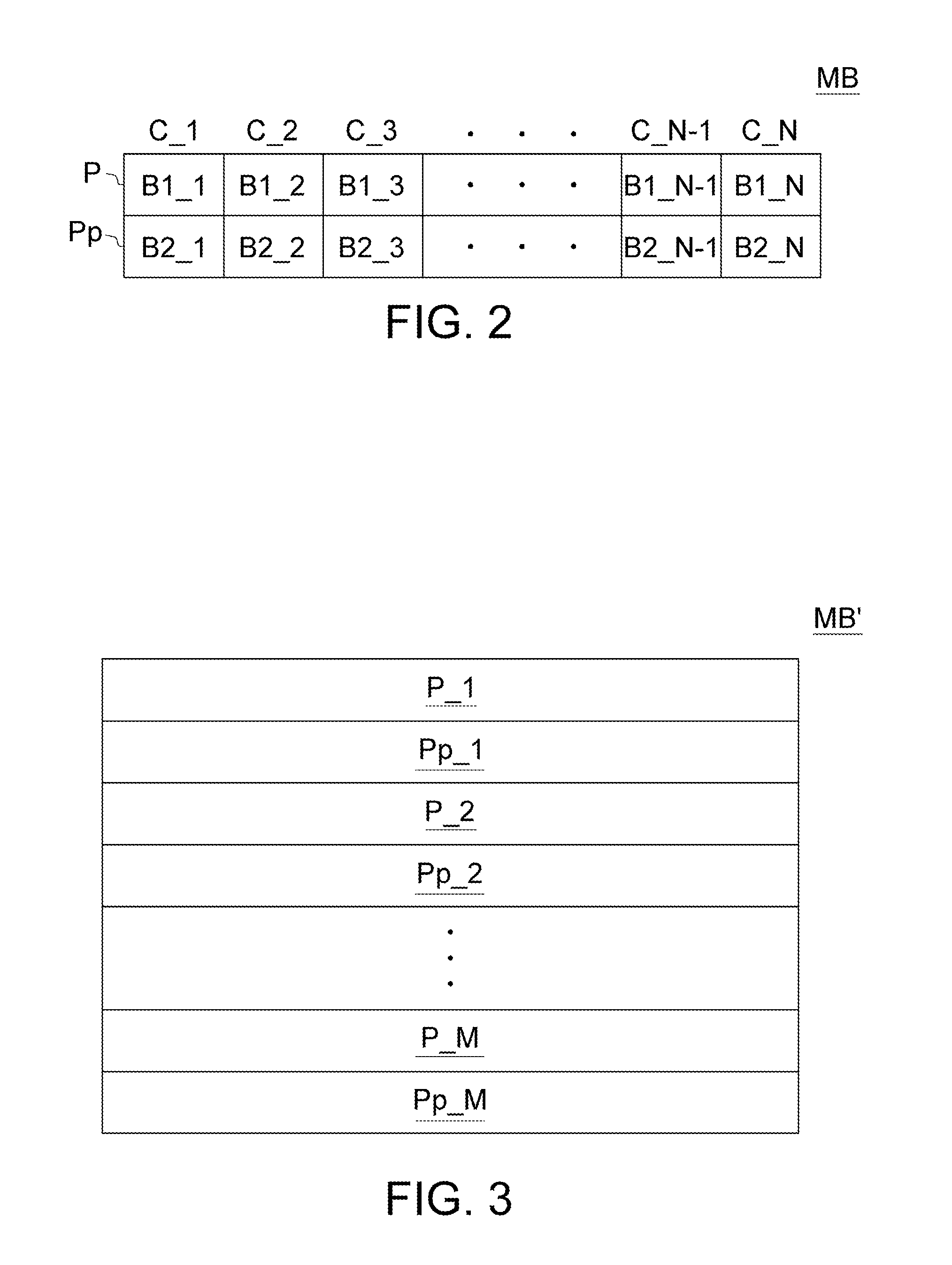
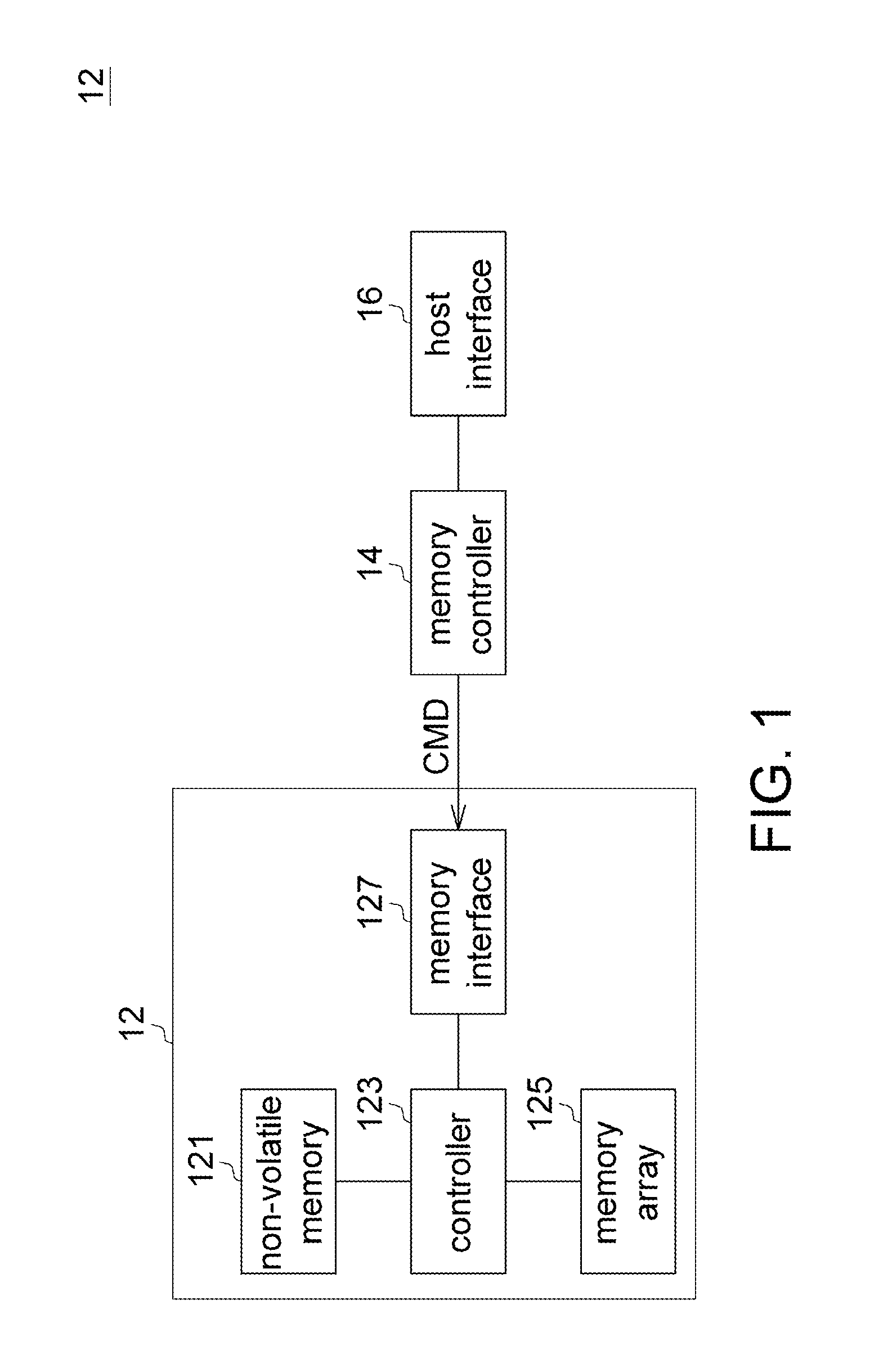
Method for recovering flash memory data at power-off of built-in Linux system
ActiveCN101477482AAvoid data lossSolve the shortcomings of low reading and writing efficiencySpecial data processing applicationsRedundant operation error correctionTemporary fileJFFS2
A method for recovering flash data in the event of power-off in an embedded Linux system solves the problem that sudden power-off at the time of read and write data flashing causes the defects of data loss or file system damage. The invention adopts the technical scheme as follows: defining and dividing a root file system in the flash memory into a fixation area, a modification area and a backup area; giving deferent loading manners to the subareas through a system file JFFS2; distributing configuration information in the root file system to the catalogues in the fixation area; and storing the temporary file produced during the system operation in the root file system in the memory. When data loss is caused by accidental power-off of the file system, the Linux system transfers the file system in spare subarea to carry out recovery of default setting and judges whether the current file system is damaged or not; whether to continuously conduct file loading to the file system is decided according to the detection to the system file with important parameters of system setting. The invention has the beneficial effects that the data recovery to the flash in the event of power-off is realized, and data loss in flashing process is avoided.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
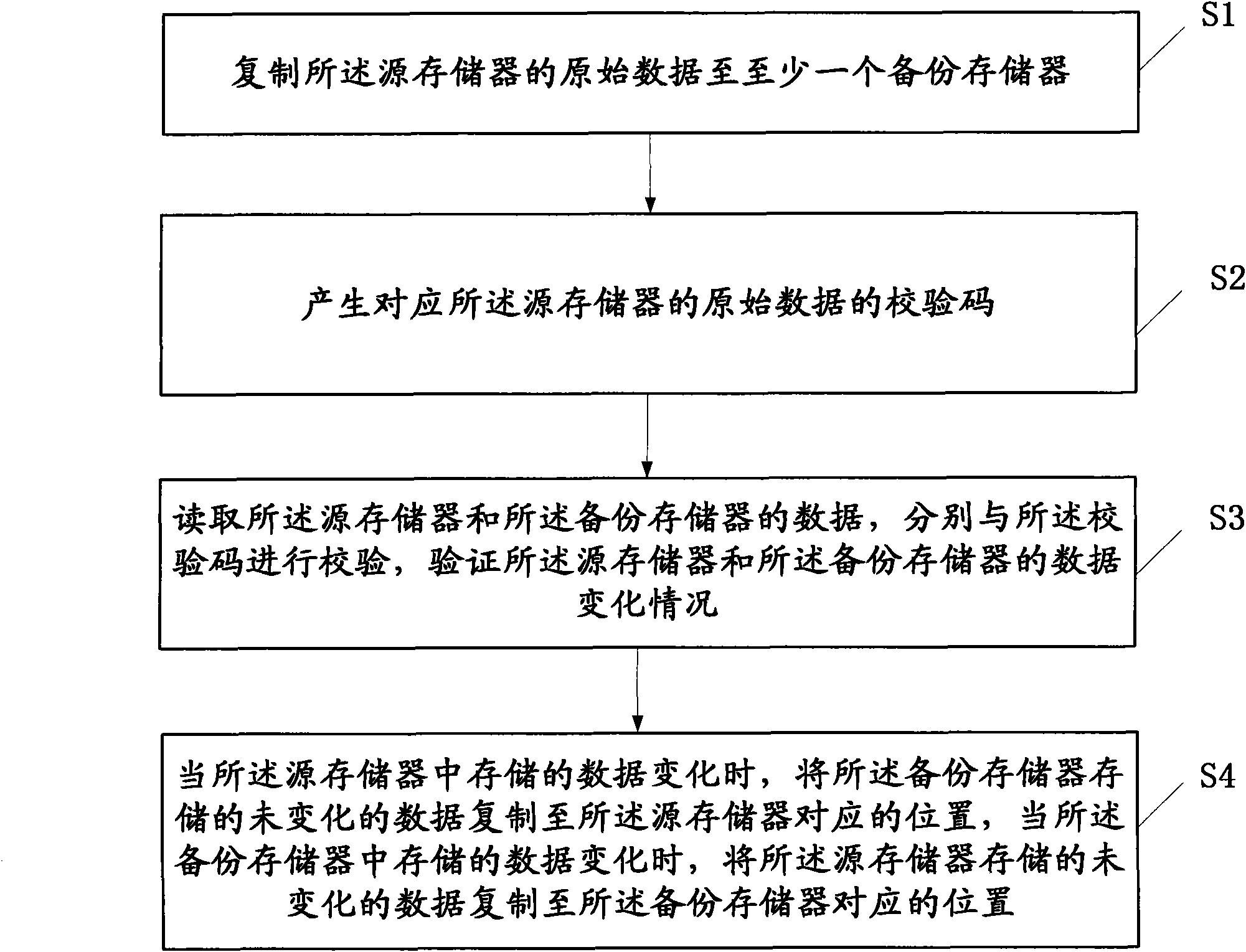
Method and device for maintaining data of drive circuit
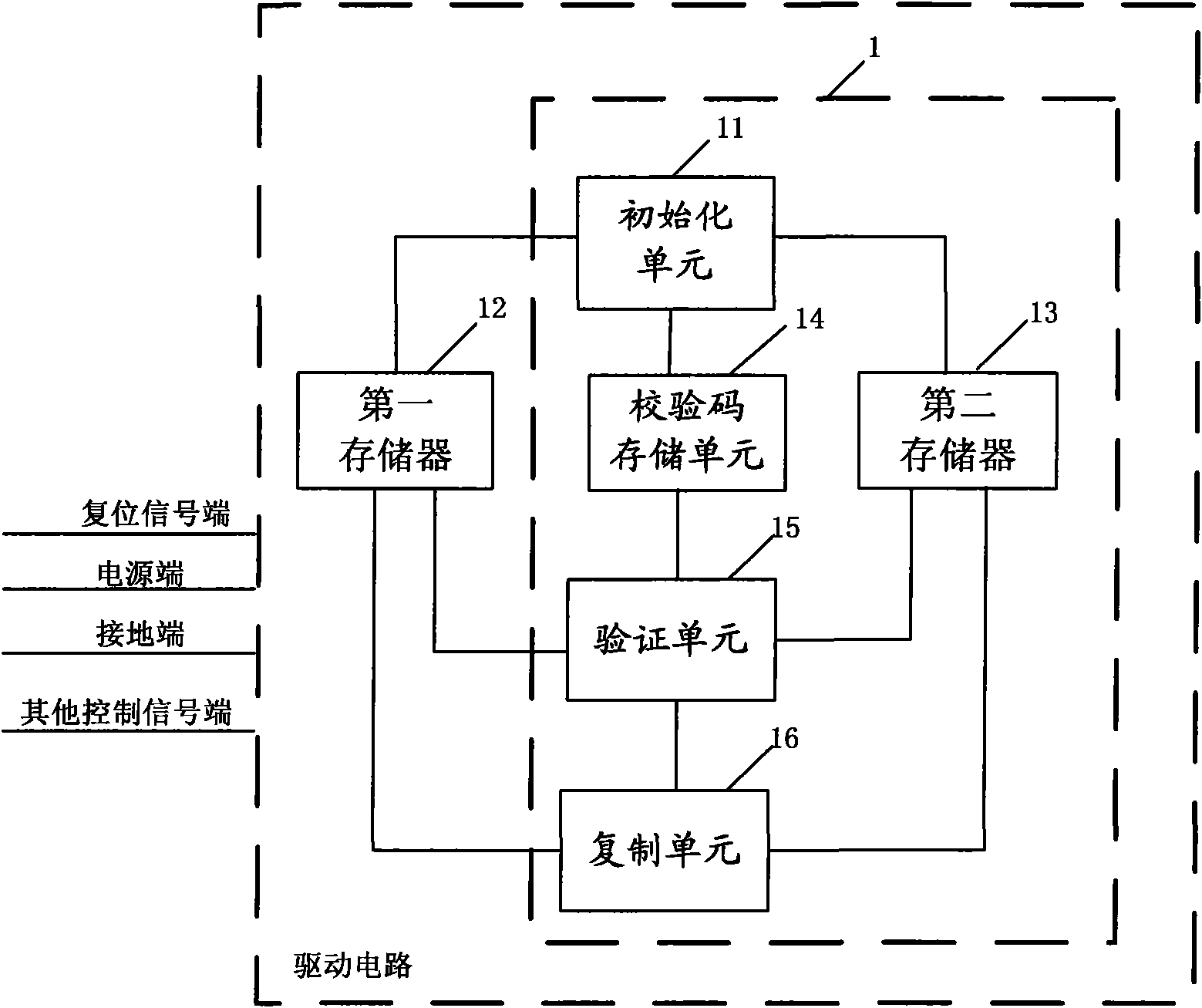
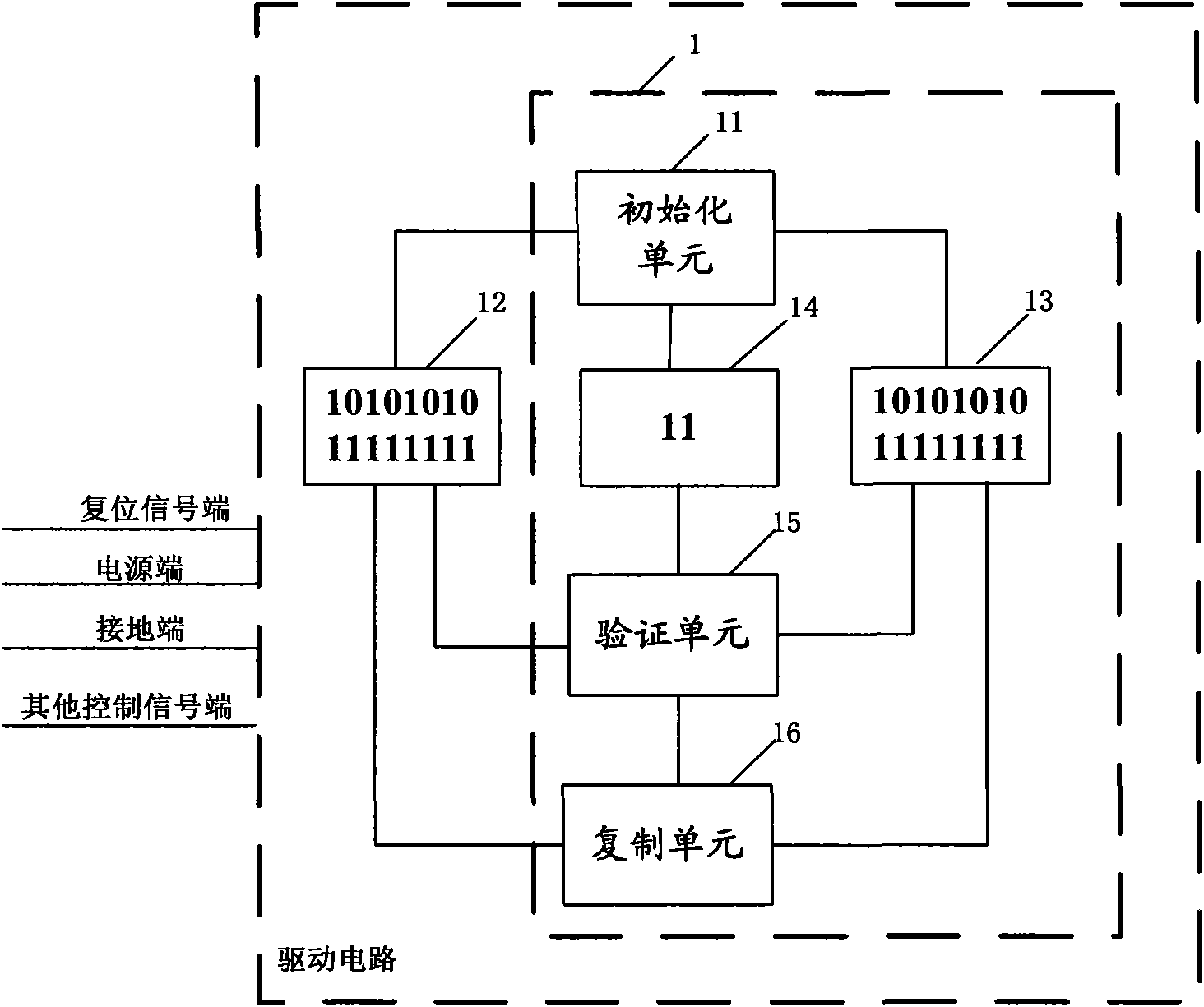
ActiveCN102103834AAchieve data recoverySimplify the verification processCathode-ray tube indicatorsElectrostatic dischargeOperating system
The invention provides a method and device for maintaining data of a drive circuit. The drive circuit comprises a source memory for storing original data. The method comprises the following steps: duplicating the original data in the source memory to at least one backup memory; generating check codes corresponding to the original data in the source memory; periodically reading the data in the source memory and the data the backup memories and checking the data respectively with the check codes to verify whether the data in the source memory and the data in the backup memories change; and whenthe data stored in the source memory changes, duplicating the unchanged data stored in the backup memories to the corresponding positions of the source memory, and when the data stored in the backup memories change, duplicating the unchanged data stored in the source memory to the corresponding positions of the backup memories. According to the technical scheme adopted by the invention, the problem that destroying of the information in the memories caused by ESD (electrostatic discharge) leads to failure of the circuit to work normally can be effectively solved.
Owner:SHANGHAI TIANMA MICRO ELECTRONICS CO LTD
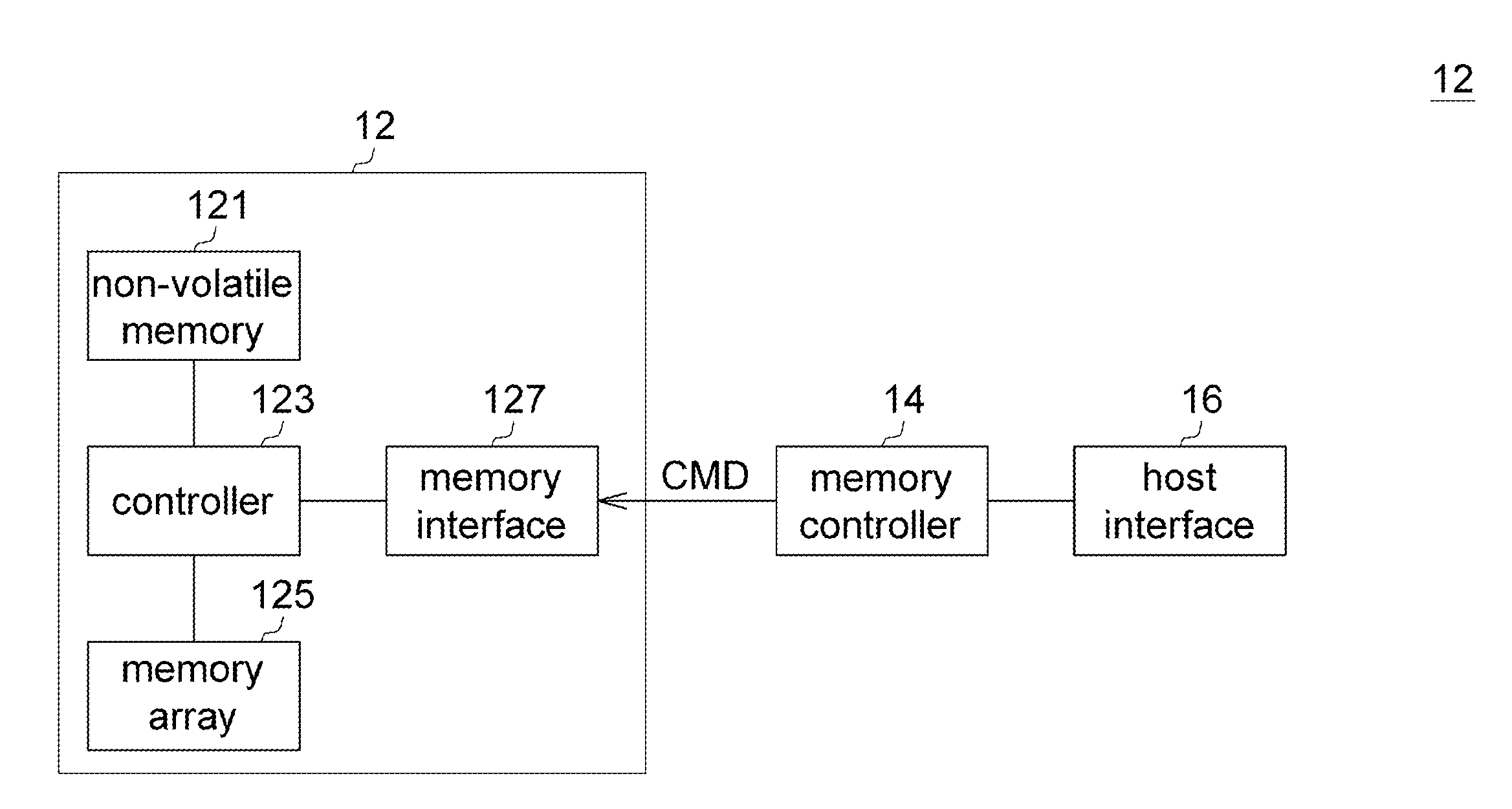
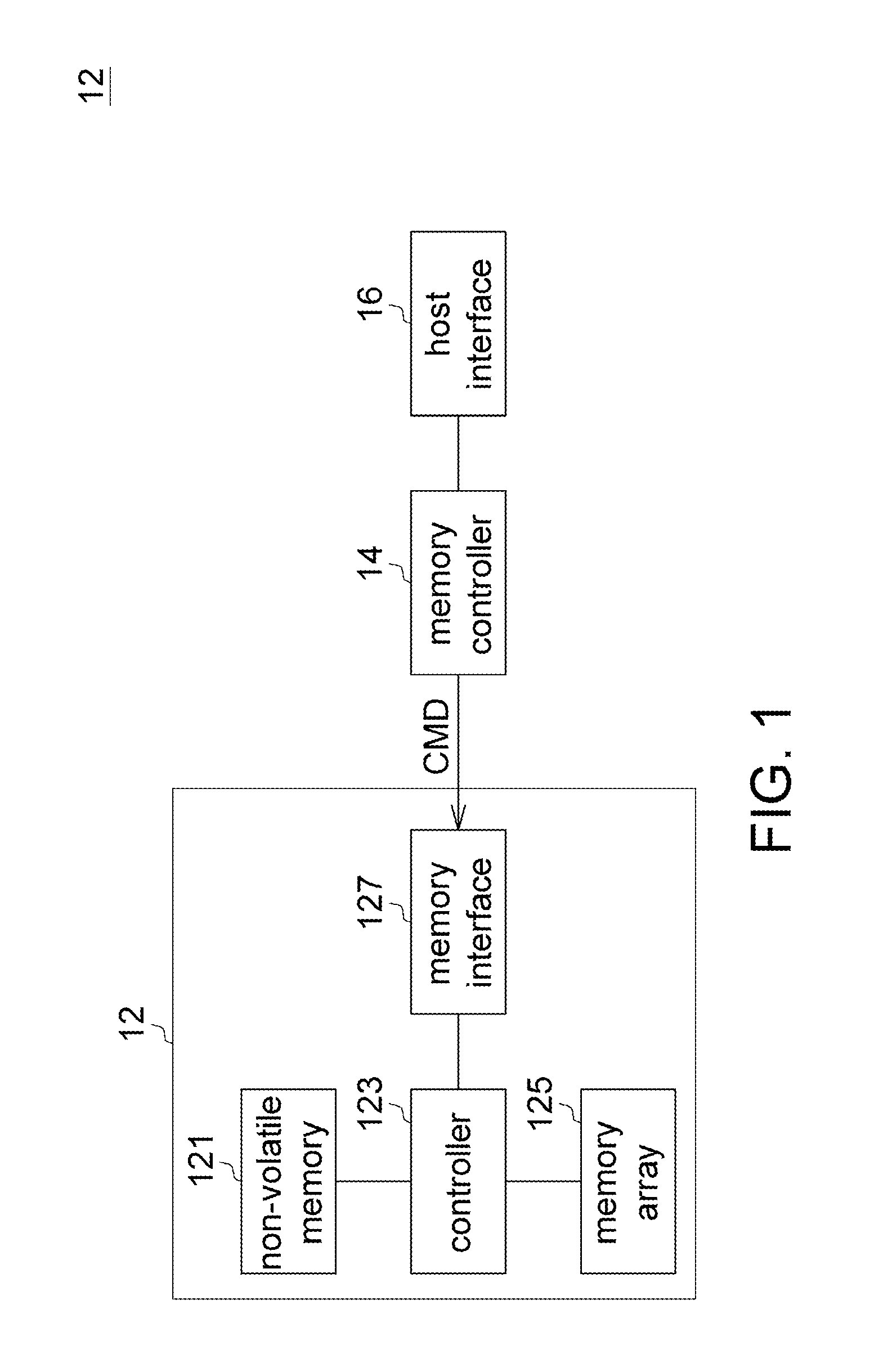
Program Method, Data Recovery Method, and Flash Memory Using the Same
ActiveUS20120265923A1Avoid data lossAchieve data recoveryMemory architecture accessing/allocationError detection/correctionData storingMulti-level cell
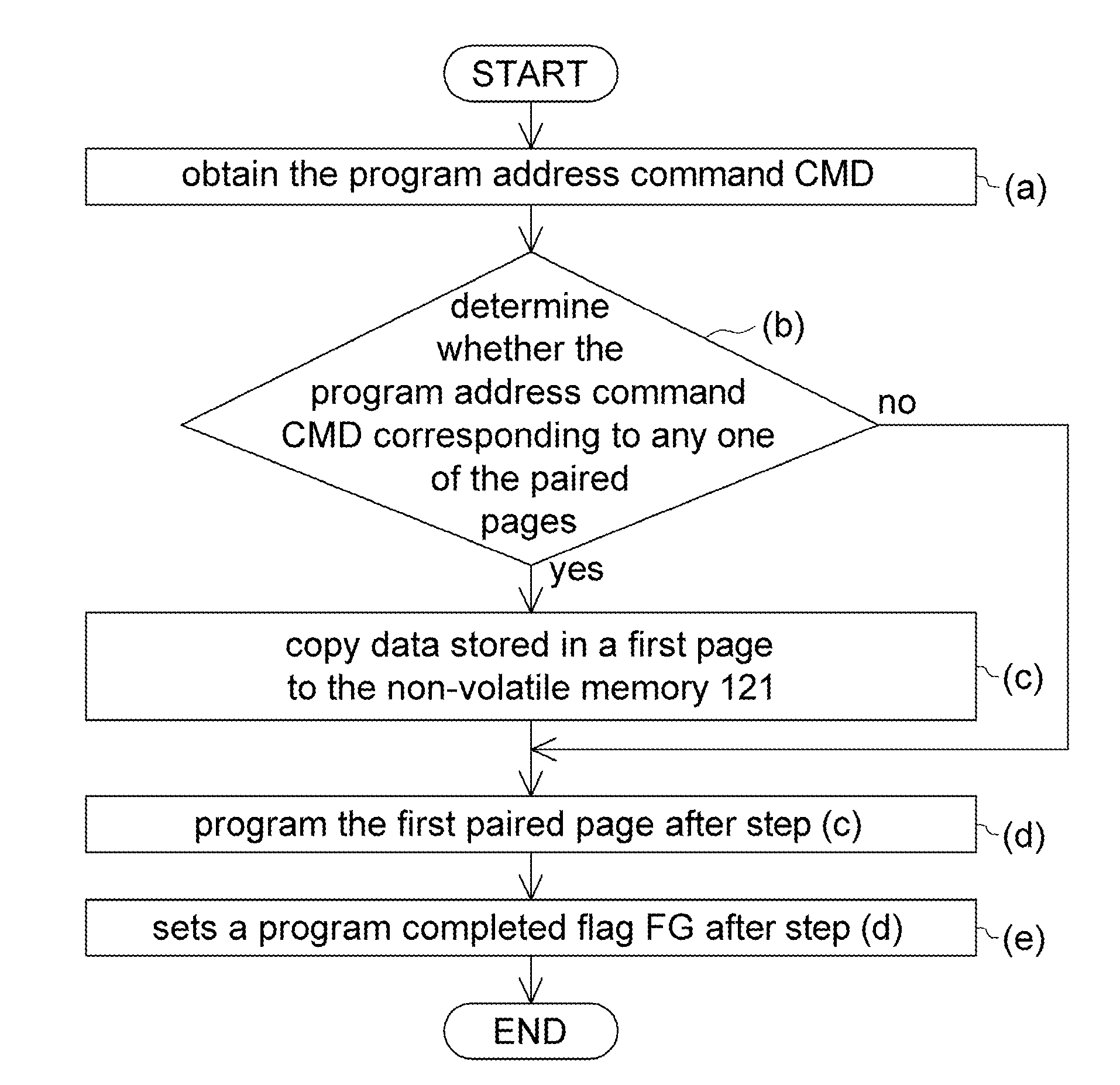
A program method for a multi-level cell (MLC) flash memory is provided. The memory array includes a plurality of pages and a plurality of paired pages, which correspond to the respective pages. The program method includes the following steps. Firstly, a program address command is obtained. Next, whether the program address command corresponding to any one of the paired pages is determined. When the program address command corresponds to a first paired page, which corresponds to a first page among the pages, among the paired pages, data stored in the first page to a non-volatile memory are copied. After that, the first paired page is programmed.
Owner:MACRONIX INT CO LTD
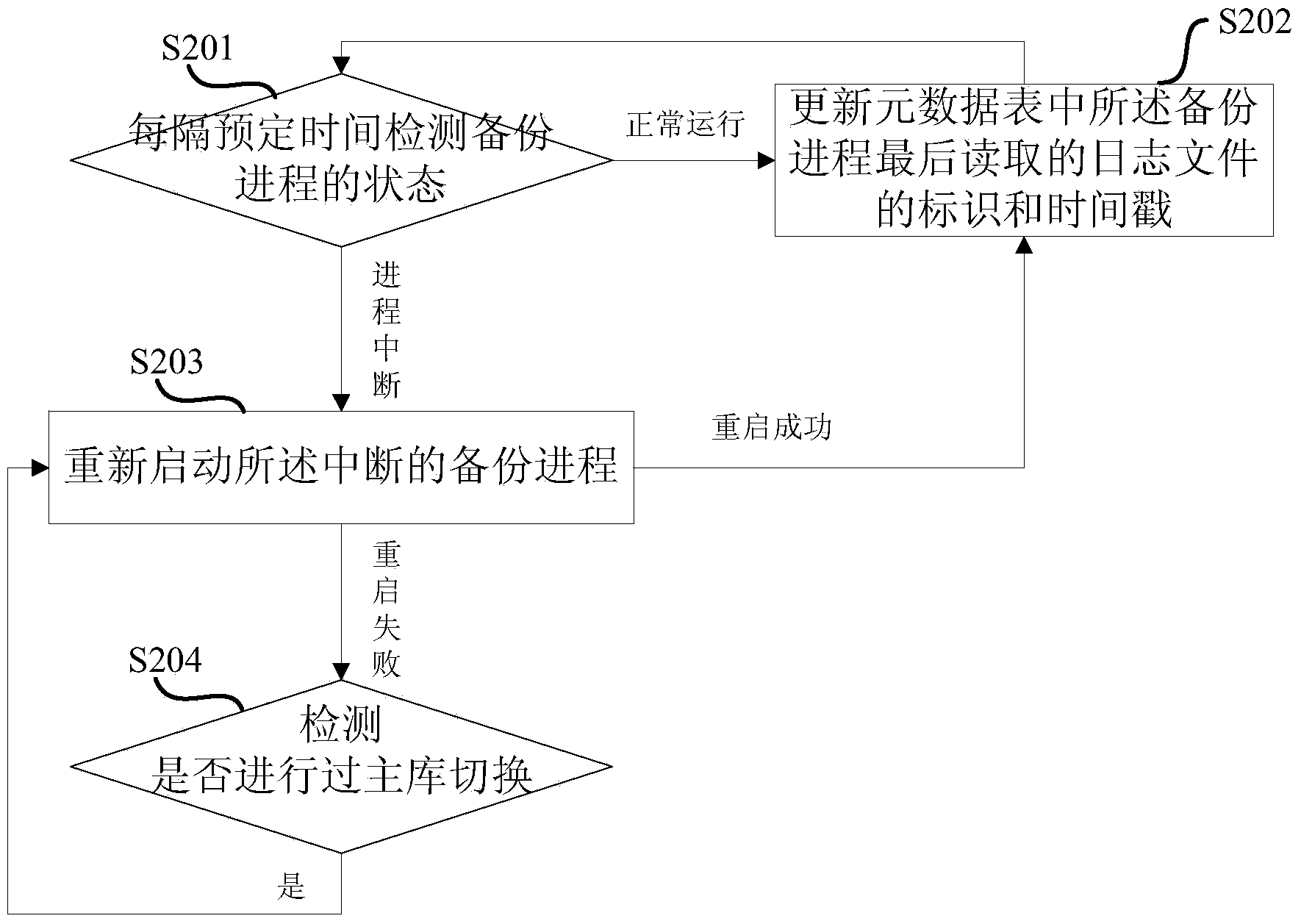
Log backup method and log backup device
ActiveCN103761165AImprove integrityAchieve data recoverySpecial data processing applicationsRedundant operation error correctionBackupLogfile
The invention discloses a log backup method and a log backup device. The log backup method includes starting one or a plurality of backup processes for performing backup on one or a plurality of log files corresponding to examples; scanning log files which are segmented by each backup process in each preset period and storing the log files segmented by each backup process. According to the technical scheme, the log backup method and the log backup device have the advantages that real-time backup can be performed on the log files, and the log files can be managed in a centralized manner.
Owner:BEIJING QIHOO TECH CO LTD
Method for realizing security electronic mail based on digital envelope
ActiveCN105323070AHigh speedImprove securityUser identity/authority verificationData switching networksConfidentialityCiphertext
The invention relates to the technical field of information security, and in particular relates to a method for realizing a security electronic mail based on a digital envelope. According to the invention, on the basis of the digital envelope technology based on PKI symmetric and asymmetric key algorithms, mail encryption and decryption information, user key information, data recovery information, mail ciphertext and other information are assembled into the digital envelope; and thus, encryption, decryption and data recovery of the electronic mail are realized. According to the invention, a session key is encrypted by obtaining all public key certificates of each receiver from a LDAP, such that interconnection and intercommunication of multiple certificates of one person are realized; when a mail blind copying function is started, mail information can be decrypted only by the private key of a blind copying user; therefore, the identity confidentiality of the blind copying user is ensured; in an emergency case that the private key of the user is lost or damaged, mail information can be decrypted without recovering the private key of the user through a KMC; and, by means of a high-grade security protection mechanism that the encrypted private key cannot be derived and a strict service approval signature mechanism, the security of recovered information is ensured from the perspectives of technologies and management.
Owner:BC P INC CHINA NAT PETROLEUM CORP +2
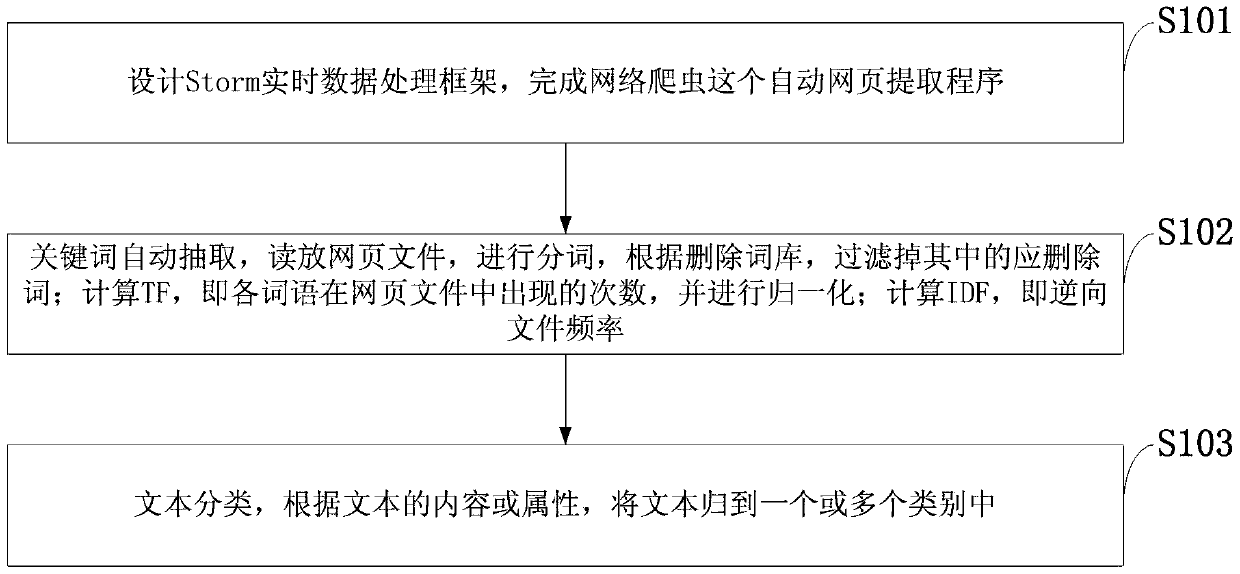
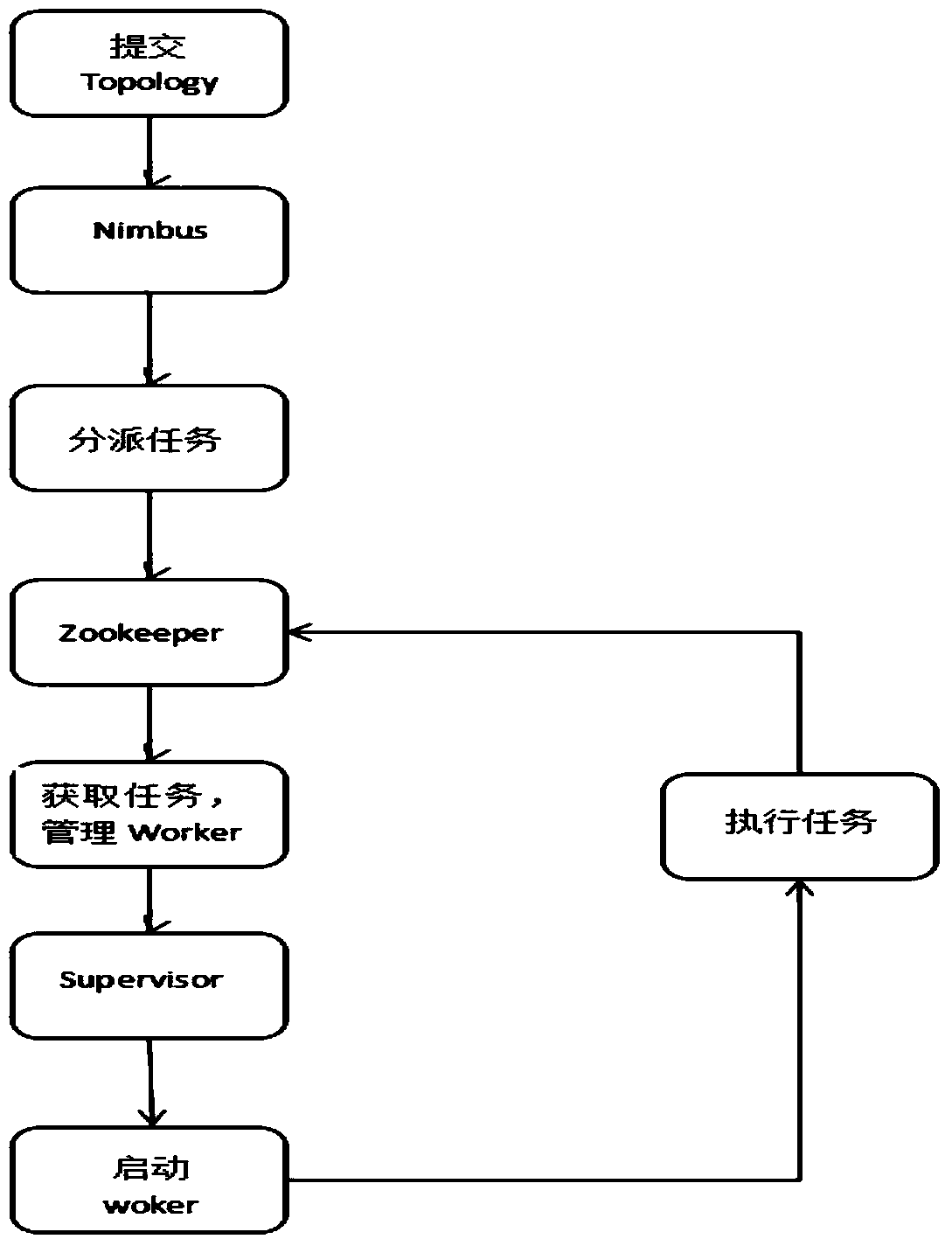
Storm based stream computing frame text index method and system
InactiveCN105930360AIncrease heightAchieve recoveryCharacter and pattern recognitionNatural language data processingFault toleranceData Corruption
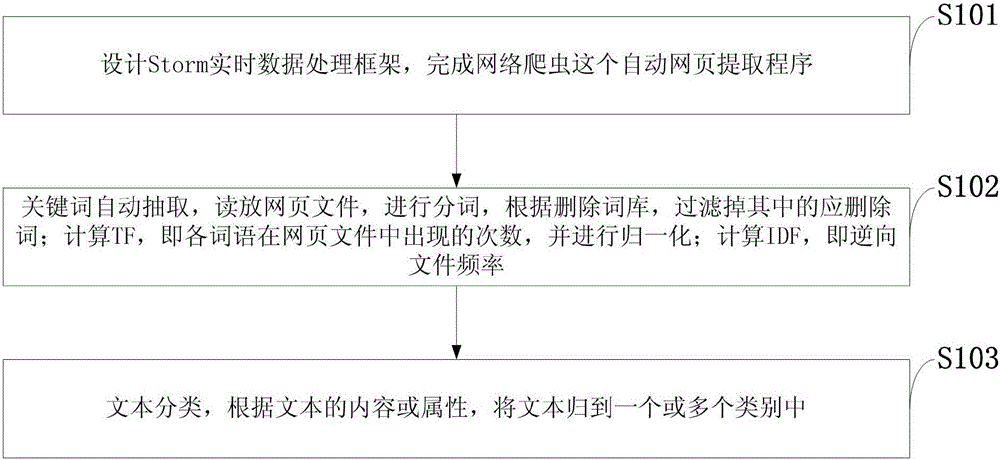
The invention discloses a Storm based stream computing frame text index method and system. The Storm based stream computing frame text index method includes: implementing topology of a storm, designing a Storm real-time data processing frame, and completing a webpage automatic extraction program of a web spider; automatically extracting key words; and classifying texts: classifying texts into one or more classifications according to content or attributes of the texts. The method and the system can allow backup data back in the conditions of data corruption or data loss, and recovers data; the function of centralized operation and maintenance of the system can be provided; an interface is beautiful and practical, and a convenient and visual graphical user management interface is achieved; function expansion can meet the demands of a user for later system expansion and use range expansion; and fault tolerance allows the system to have a certain fault tolerance mechanism when illegal data generates due to user input or wrong operations.
Owner:YUNNAN UNIV +2
Mobile terminal devices and method capable of recovering user's data automatically
InactiveCN1728855AAchieve data recoveryAvoid lostRadio/inductive link selection arrangementsNetwork data managementRecovery functionEncryption
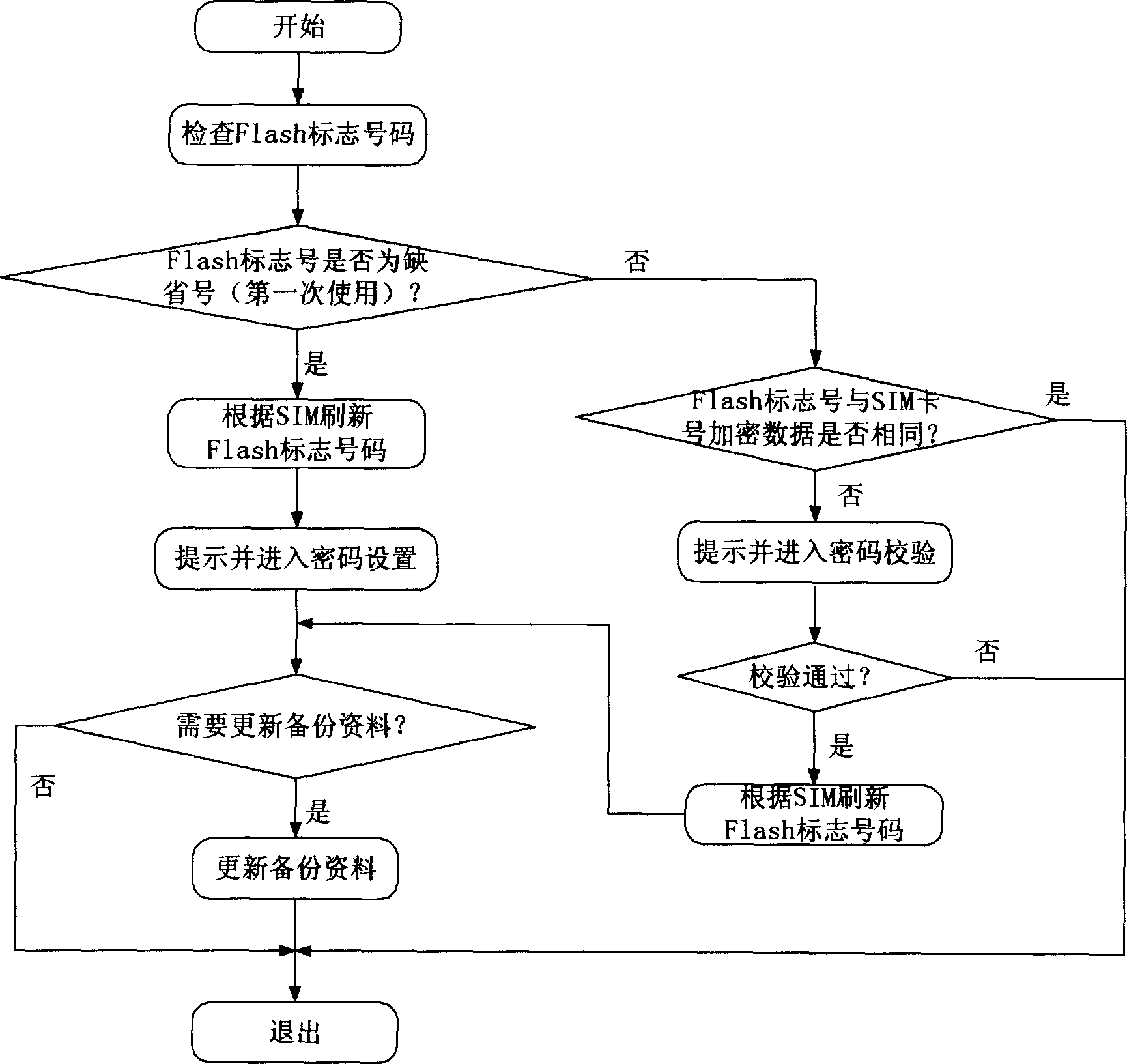
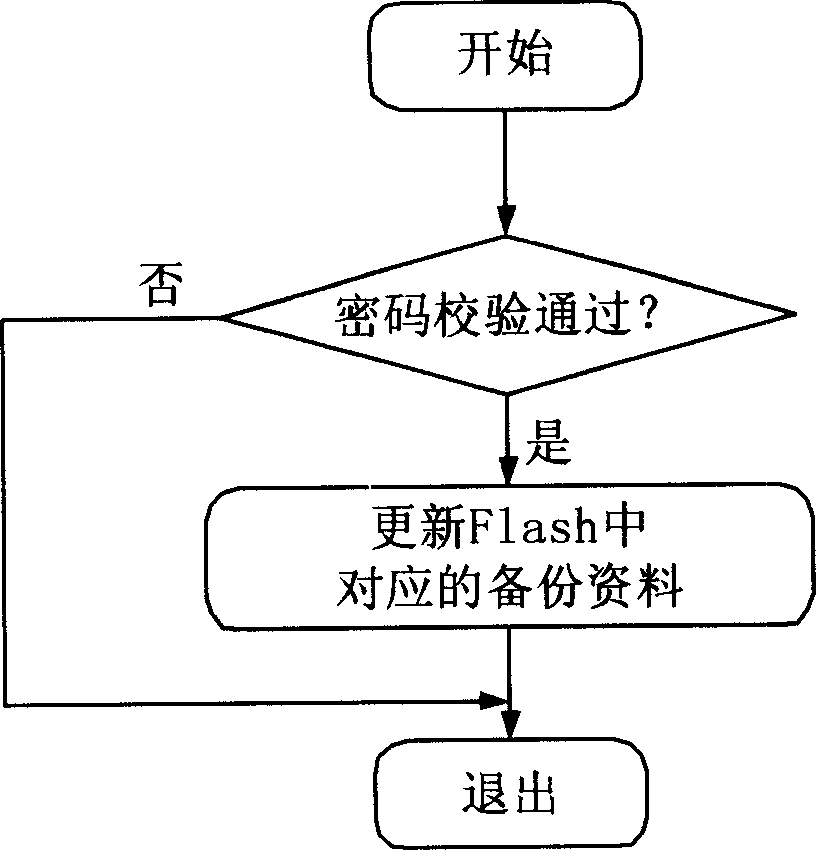
A piece of backup area divided from flash area of mobile terminal is in use for storing user data exclusively. The flash backup area is divided into three parts: number area, cipher area and data area. After a communication terminal device of using the said configuration is lost, owner informs operational manager to broadcast message through group transmission. Received the said message, all mobile terminals carry out encryption process for marked number in message, and compares it with flash mark number in this terminal. If the said numbers are identical, then backup data in flash is read out automatically. According to some format, operational manager forwards the backup data to the mobile terminal the user applies for. The invention realizes automatic recovery function of user data so as to prevent expanding loss further.
Owner:上海贝豪通讯电子有限公司
Application method for accurately obtaining LLR information
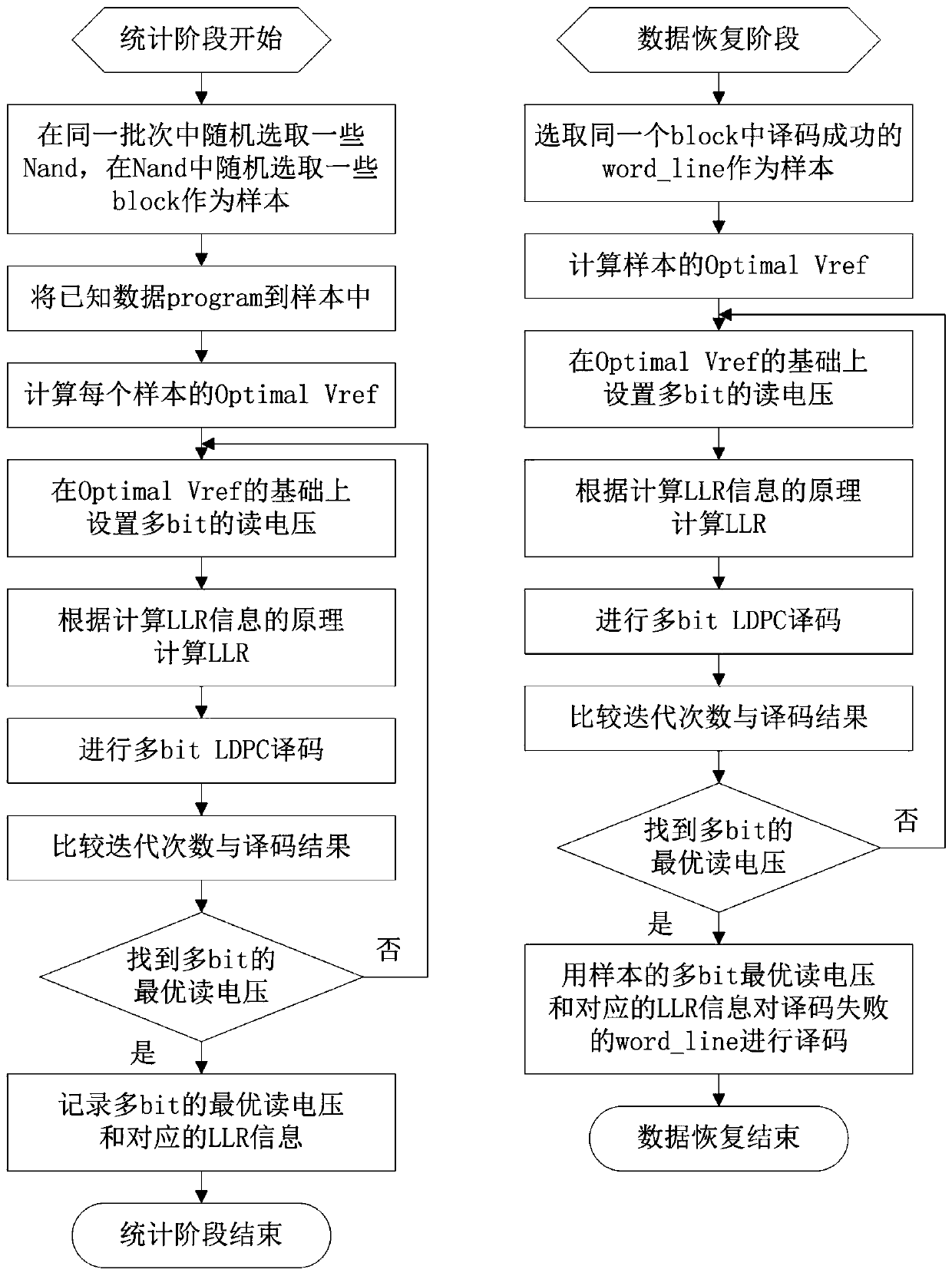
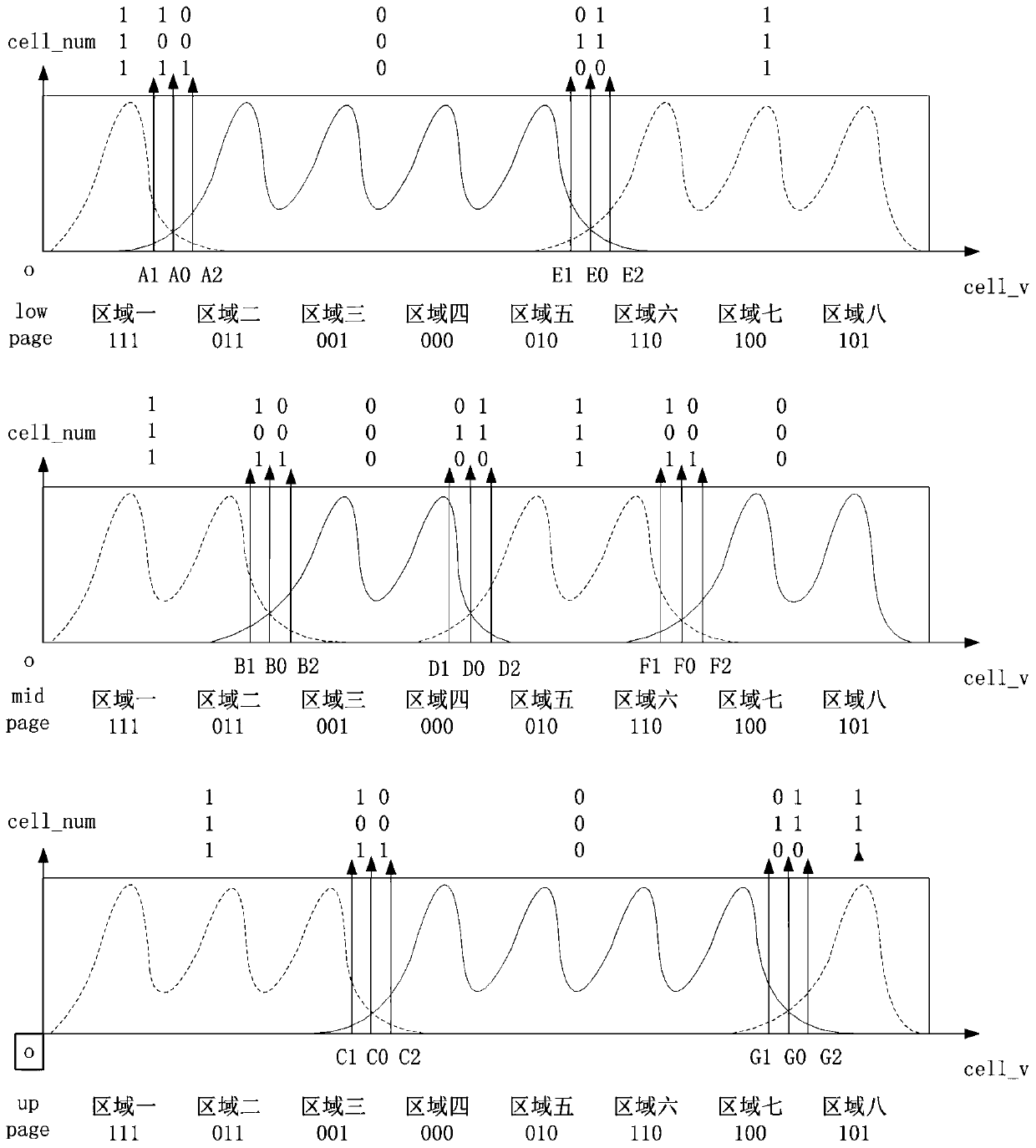
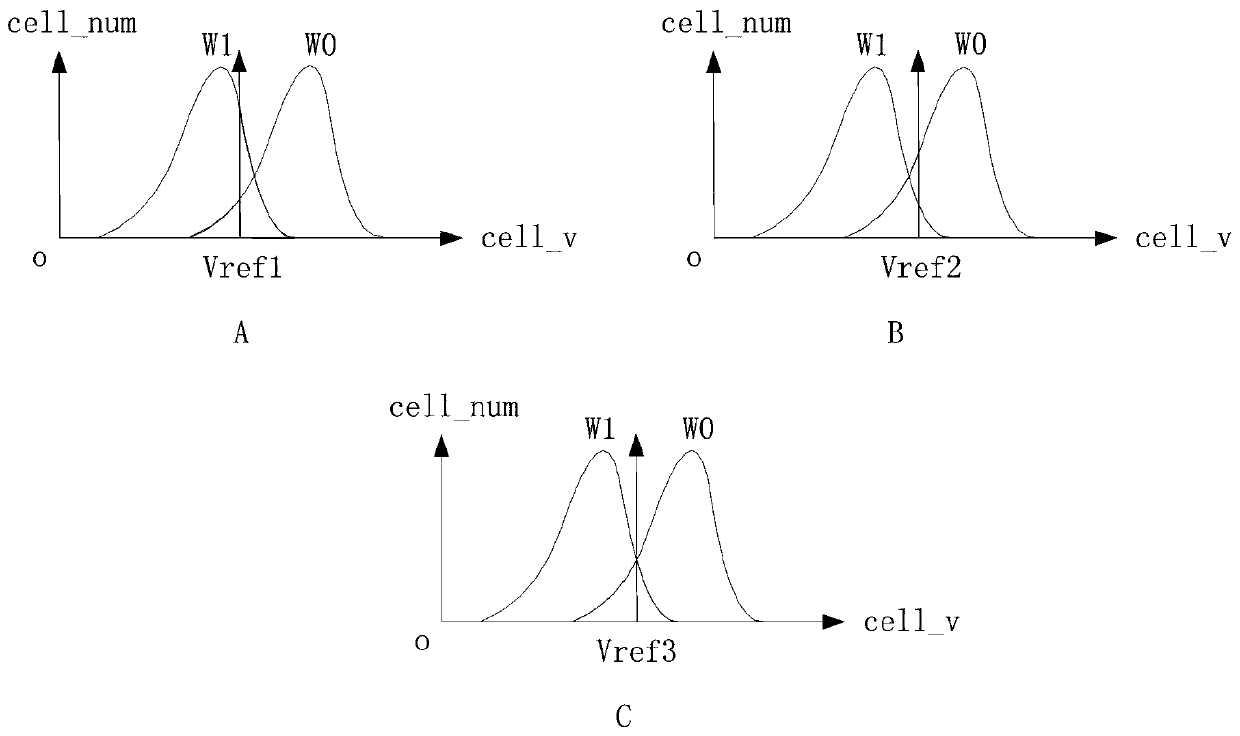
ActiveCN106981308AAccurate estimateEfficiency of normal read and write NANDError correction/detection using multiple parity bitsRead-only memoriesData recoveryLdpc decoding
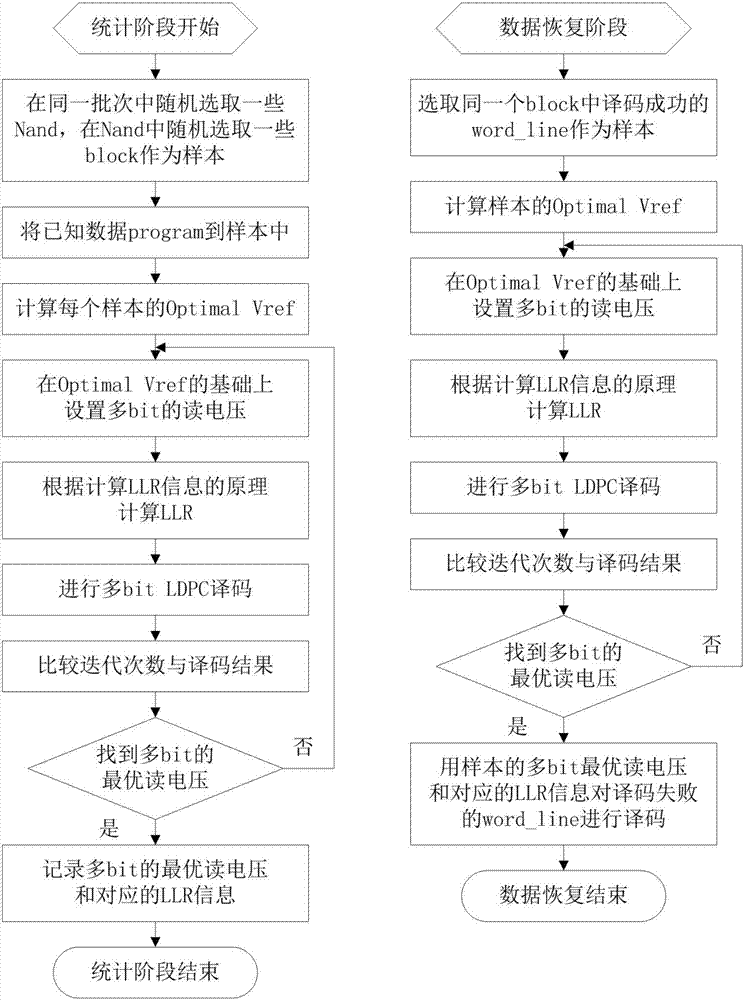
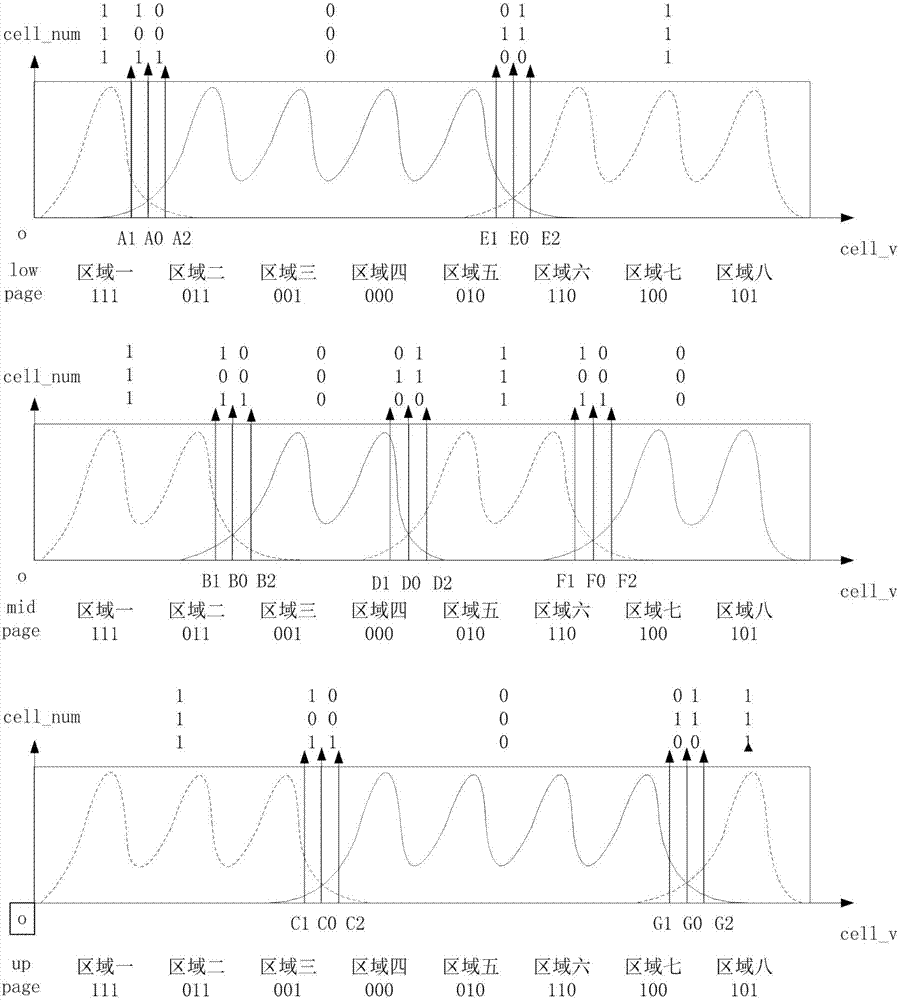
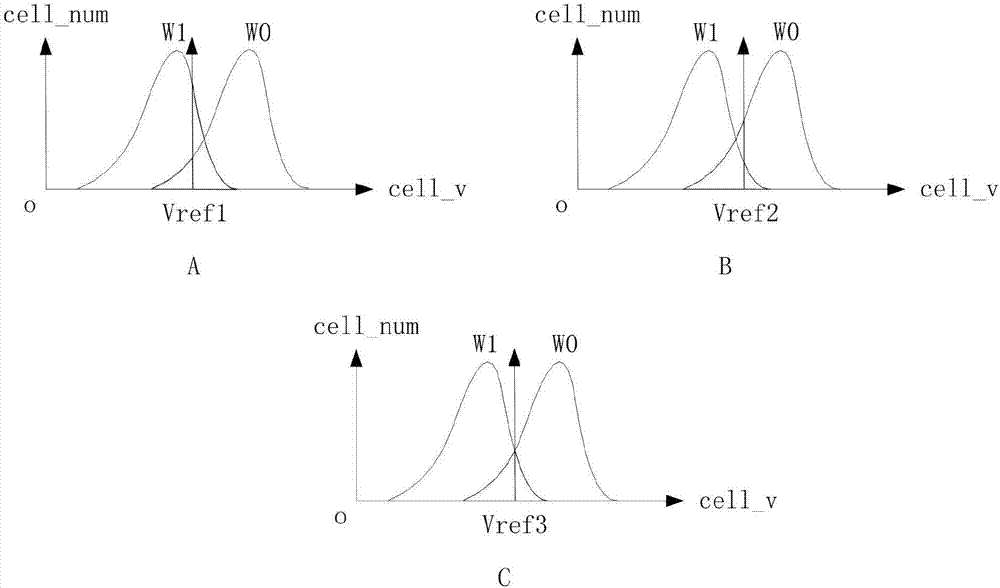
The invention discloses an application method for accurately obtaining LLR information. The method is characterized by comprising the steps of selecting statistics samples; calculating Optimal Vref of each sample; by setting multi-level multi-bit reading voltages, calculating the LLR information corresponding to the multi-level reading voltages, and performing multi-bit LDPC decoding; and by comparing iterative frequencies and decoding results of the multi-bit LDPC decoding corresponding to different reading voltages, recording the reading voltage with the lowest iterative frequency and the decoding correctness as a multi-bit optimal reading voltage, wherein the corresponding LLR information is initial LLR information of a batch of products, and the batch of the products finitely adopt the optimal reading voltage to read data by default and adopt the initial LLR information to decode the data. An empirical value is obtained by adding statistics and serves as a parameter during normal decoding to ensure normal NAND reading-writing efficiency; and when the normal decoding fails and data recovery needs to be carried out, the scheme can estimate more accurate multi-bit LLR information, thereby reducing the error code rate and realizing the data recovery.
Owner:RAMAXEL TECH SHENZHEN
Heterogeneous database unified disaster recovery backup method and device based on virtualization and snapshot
PendingCN114328009AGuaranteed reliabilityEnsure data securityDatabase distribution/replicationFile system administrationData synchronizationVirtualization
The invention relates to a heterogeneous database unified disaster recovery backup method and device based on virtualization and snapshot, and the method comprises the following steps: constructing a virtual machine matched with a source end hardware environment by using a virtualization technology, maintaining a standby database in the virtual machine, and keeping the standby database in data synchronization with a source database of a source end and in operation; carrying out primary full-amount backup; monitoring whether a source end generates a new log event or not in real time, and if yes, backing up the new log event and controlling the virtual machine to perform log synchronization at the same time; whether a snapshot instruction is generated or not is monitored in real time, and if yes, a data snapshot of a storage volume corresponding to a standby library in the virtual machine is obtained, and a virtual snapshot library is generated; and when recovery is executed, realizing data recovery based on the virtual snapshot library. Compared with the prior art, the method has the advantages that the reliability and the data security of a database system can be ensured, and meanwhile, physical resources are flexibly distributed and scheduled according to needs.
Owner:SHANGHAI DRAGONNET TECH
Data processing system and data processing method
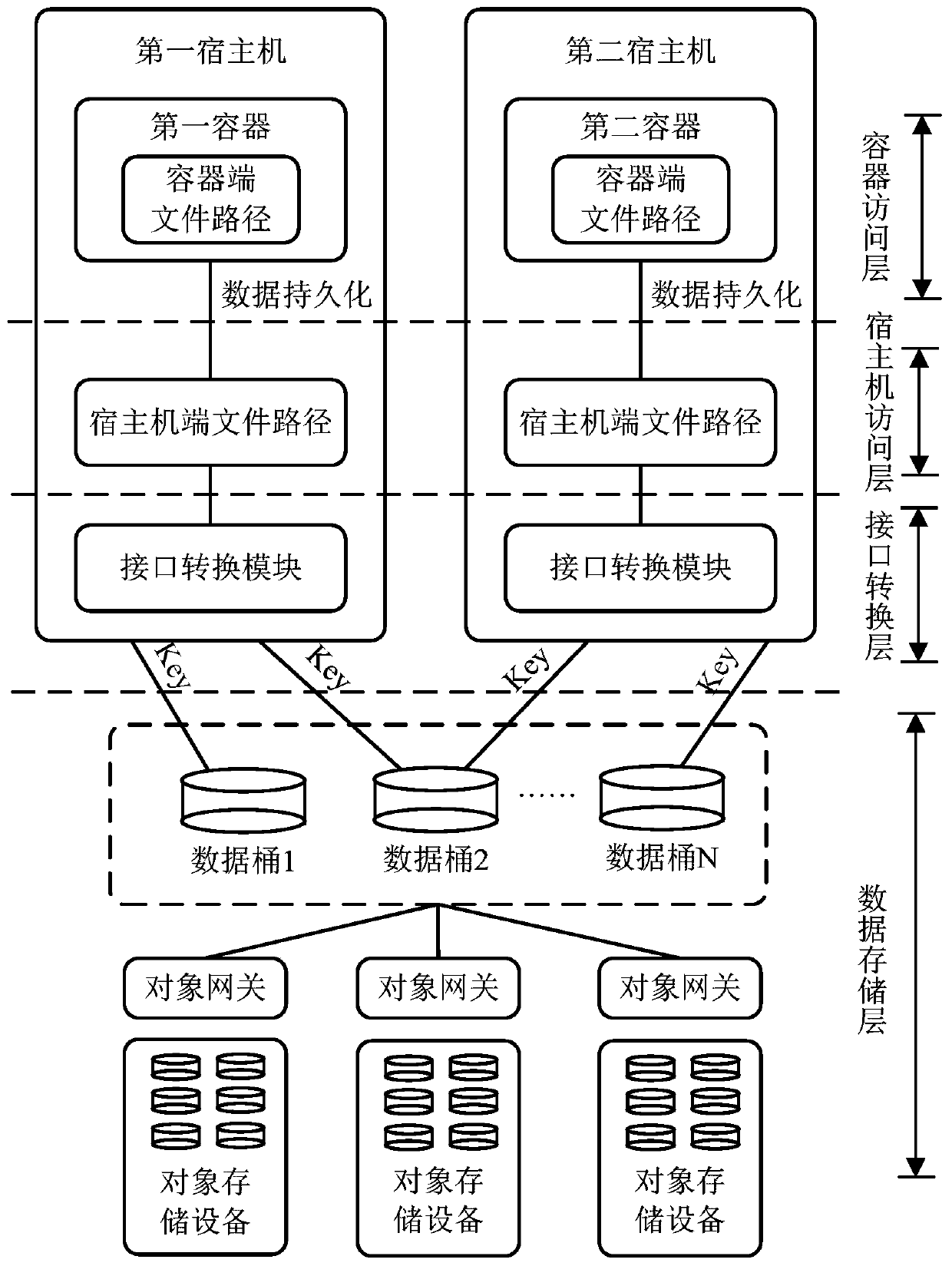
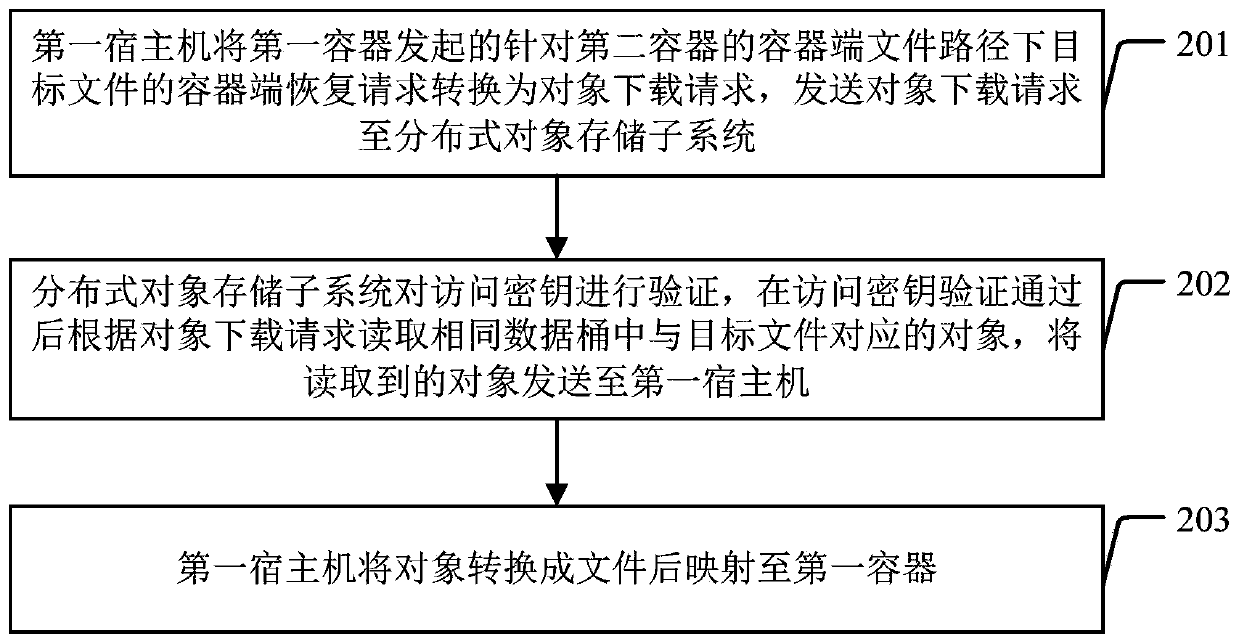
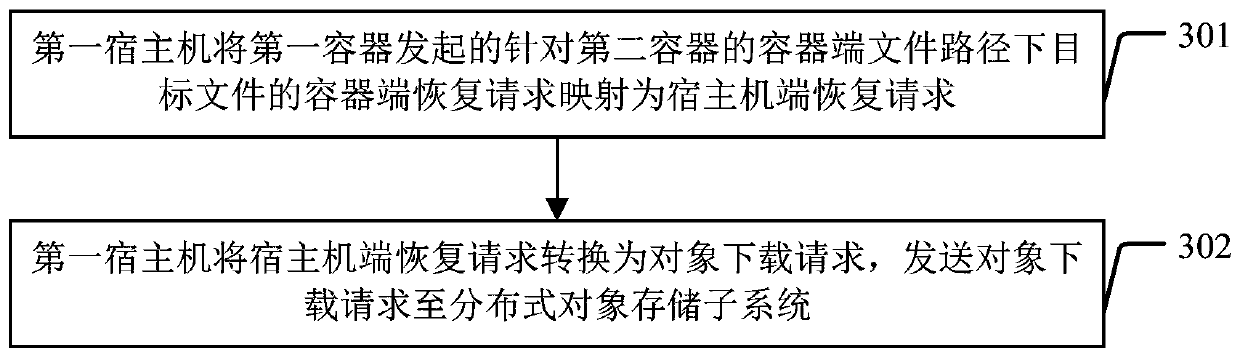
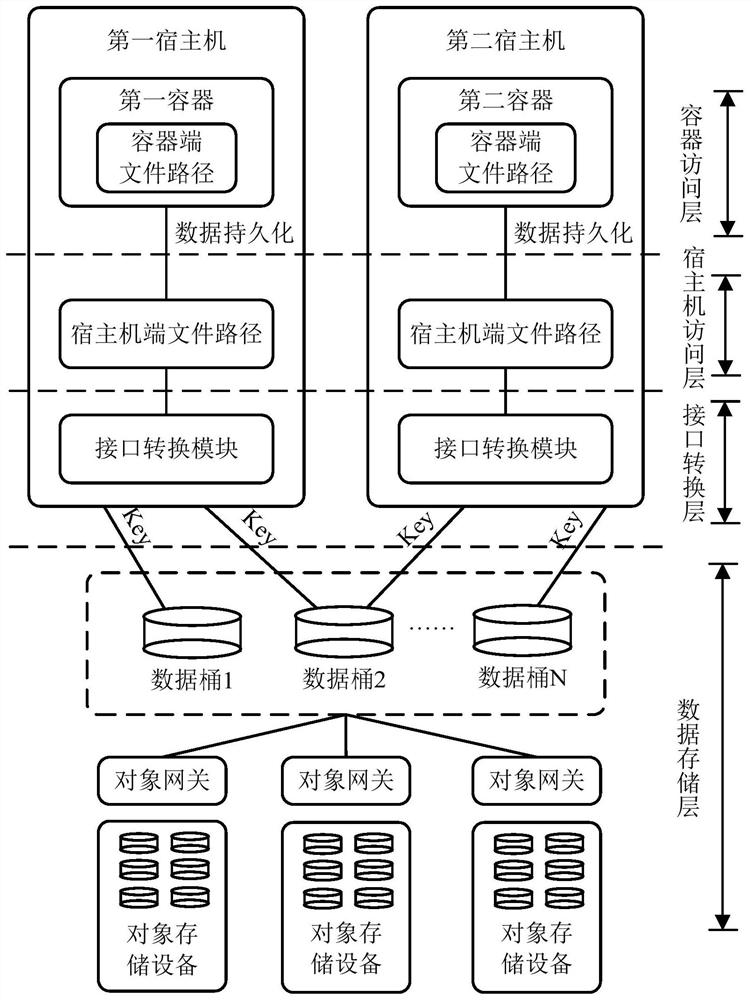
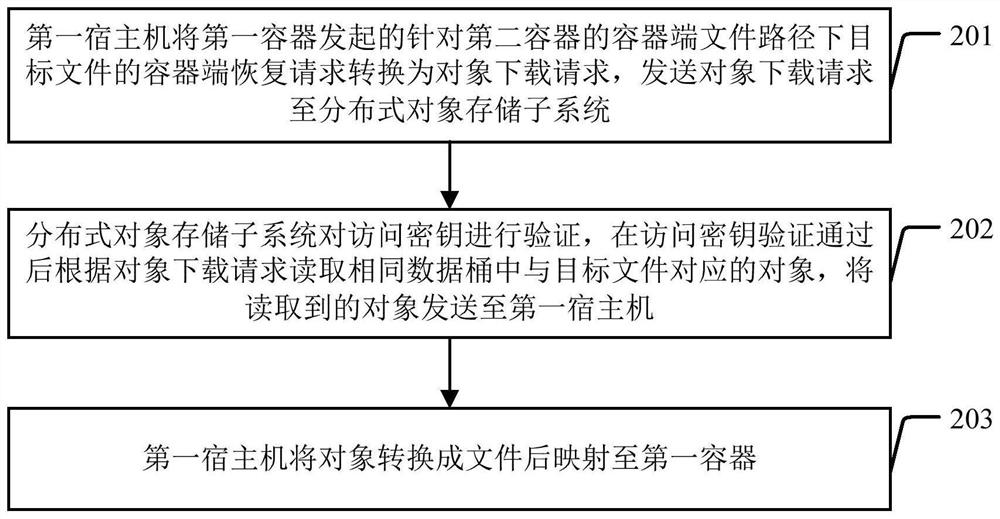
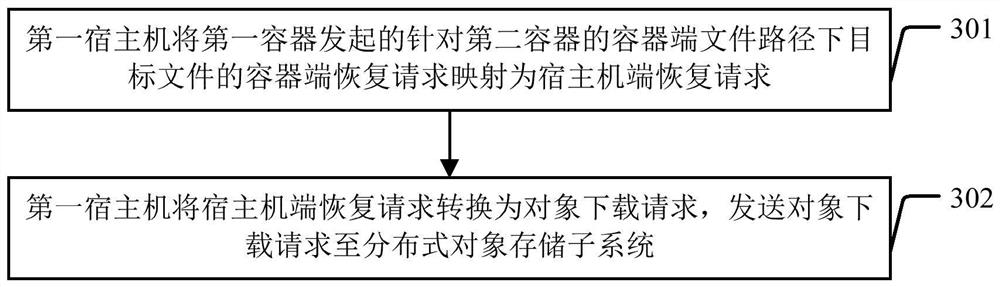
ActiveCN110012087AAchieve data recoveryTransmissionSoftware simulation/interpretation/emulationData processing systemDistributed object
The invention discloses a data processing system and a data processing method. The data processing system comprises a distributed object storage subsystem, a first host machine comprising a first container, and a second container. During cross-container data recovery, the first host machine converts a container end recovery request which is initiated by the first container and aims at a target file under a container end file path of the second container into an object downloading request comprising an access key of the same data barrel; and the distributed object storage subsystem reads an object corresponding to the target file in the same data bucket according to the object downloading request after the access key verification is passed, and sends the read object to the first host machine, and the first host machine then converts the object into a file and maps the file to the first container. According to the invention, the first container and the second container are different containers and are respectively loaded with container end file paths of the same data barrel, cross-container data recovery can be effectively realized.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
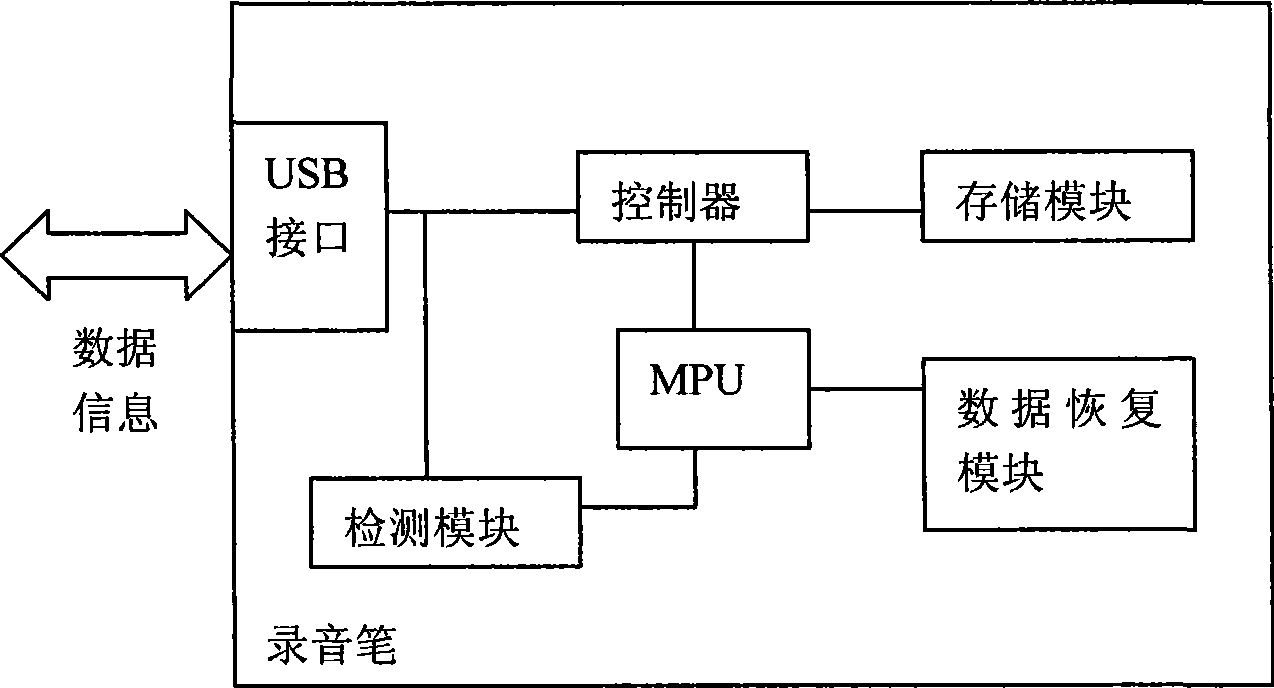
Electronic voice recording equipment with power-down data protection function
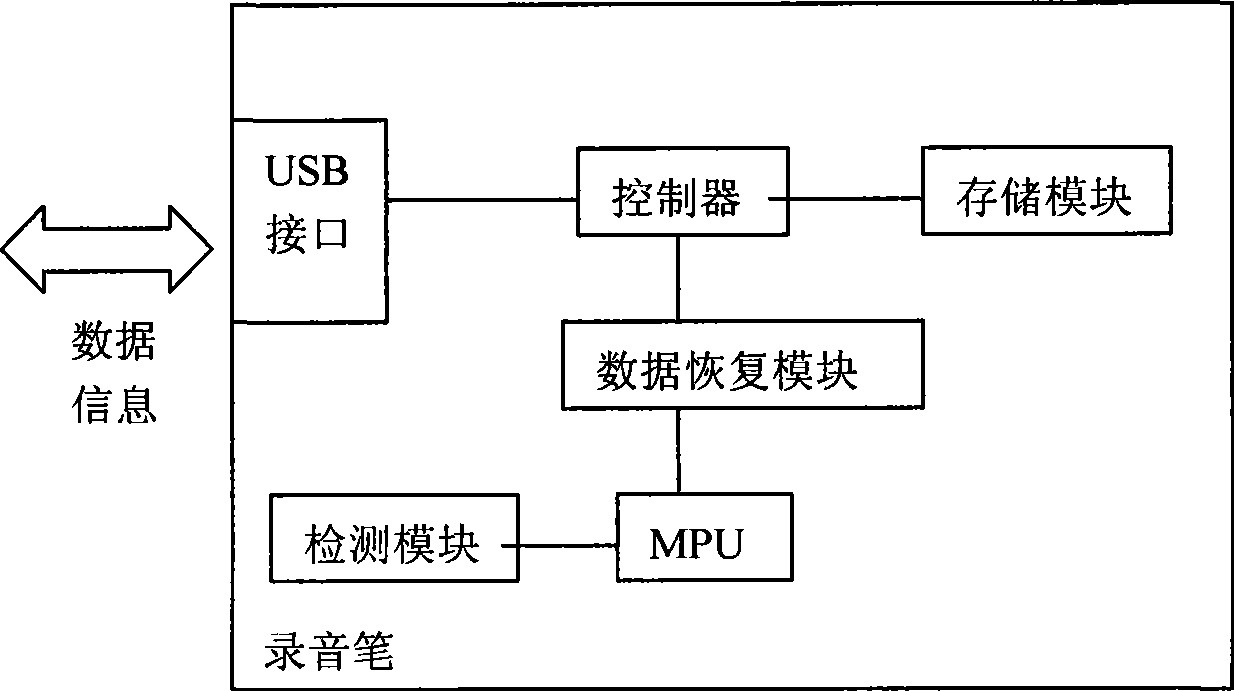
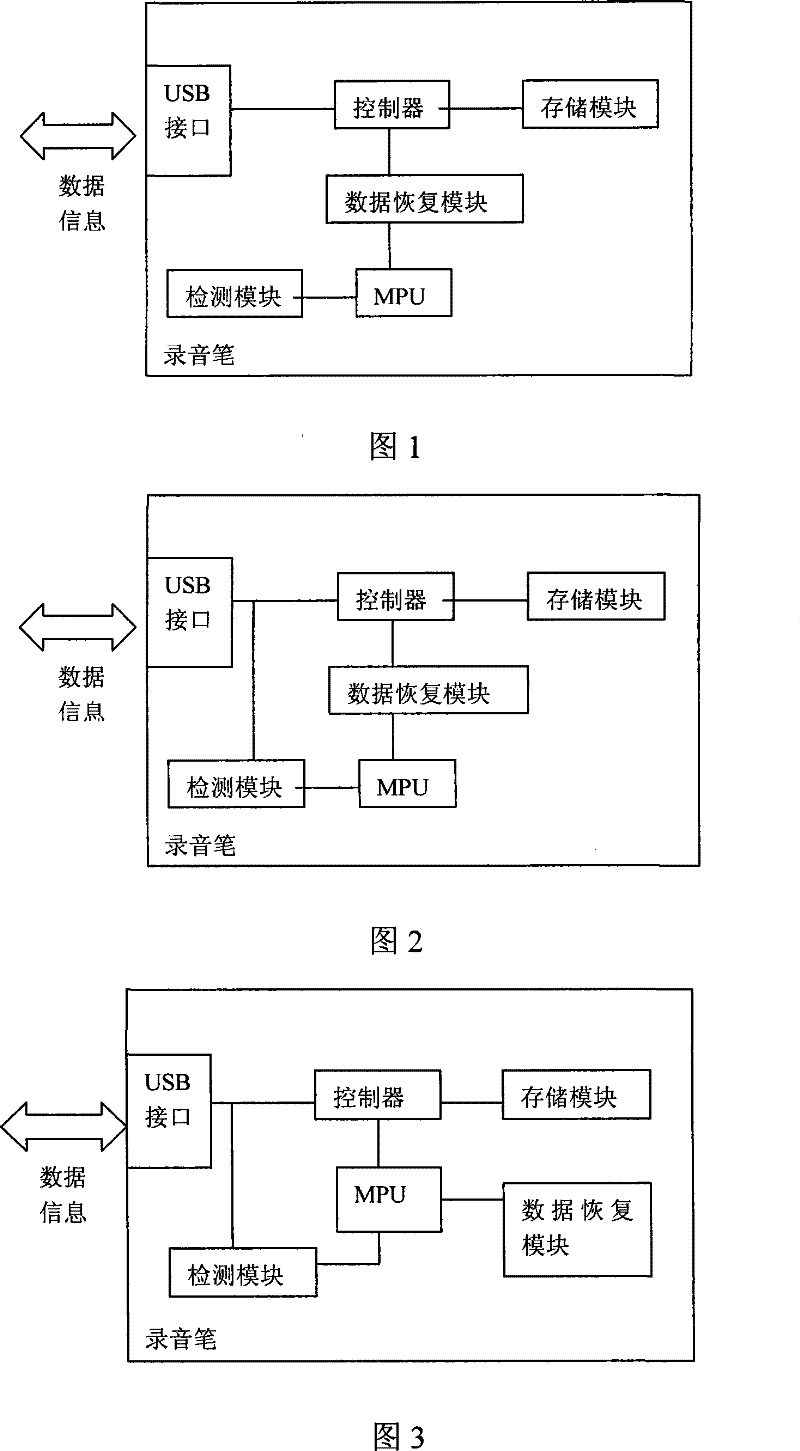
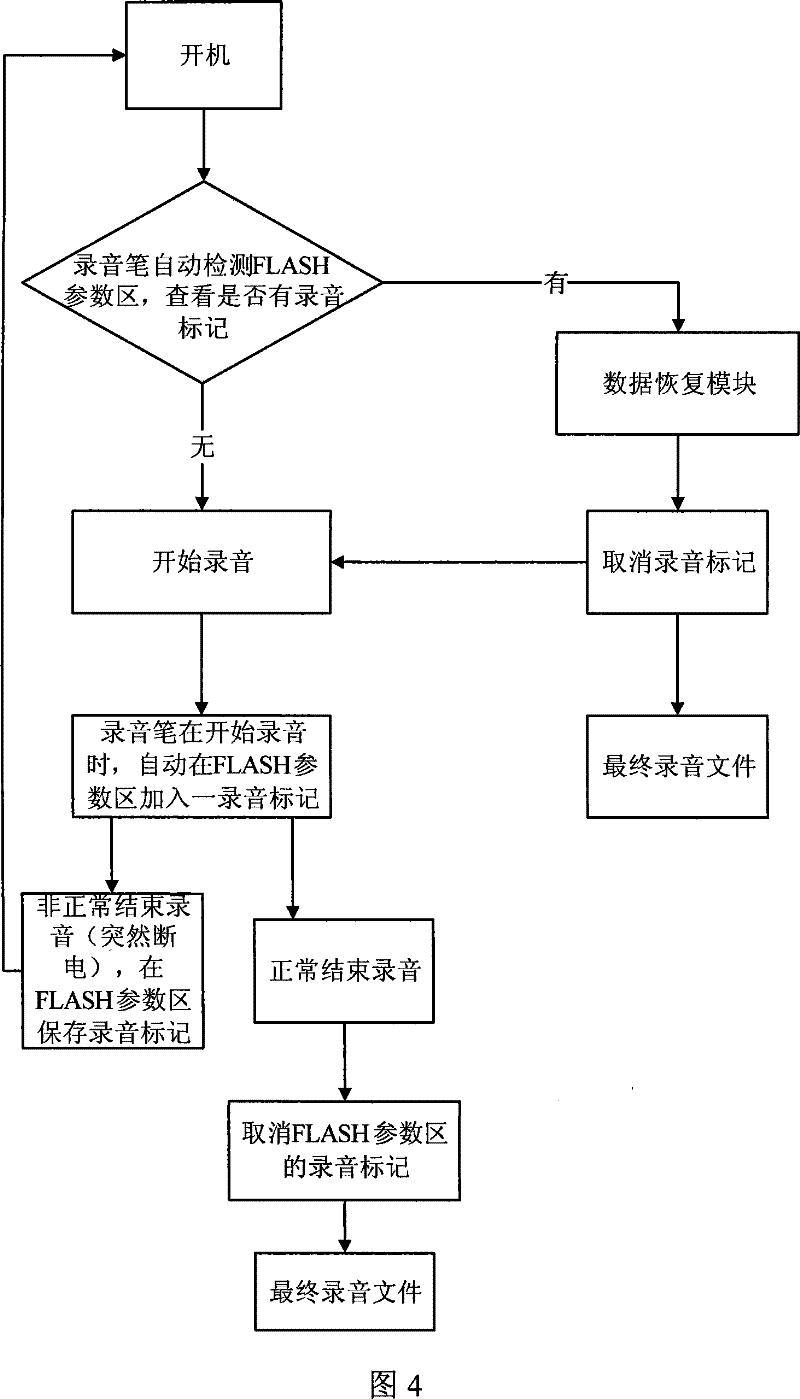
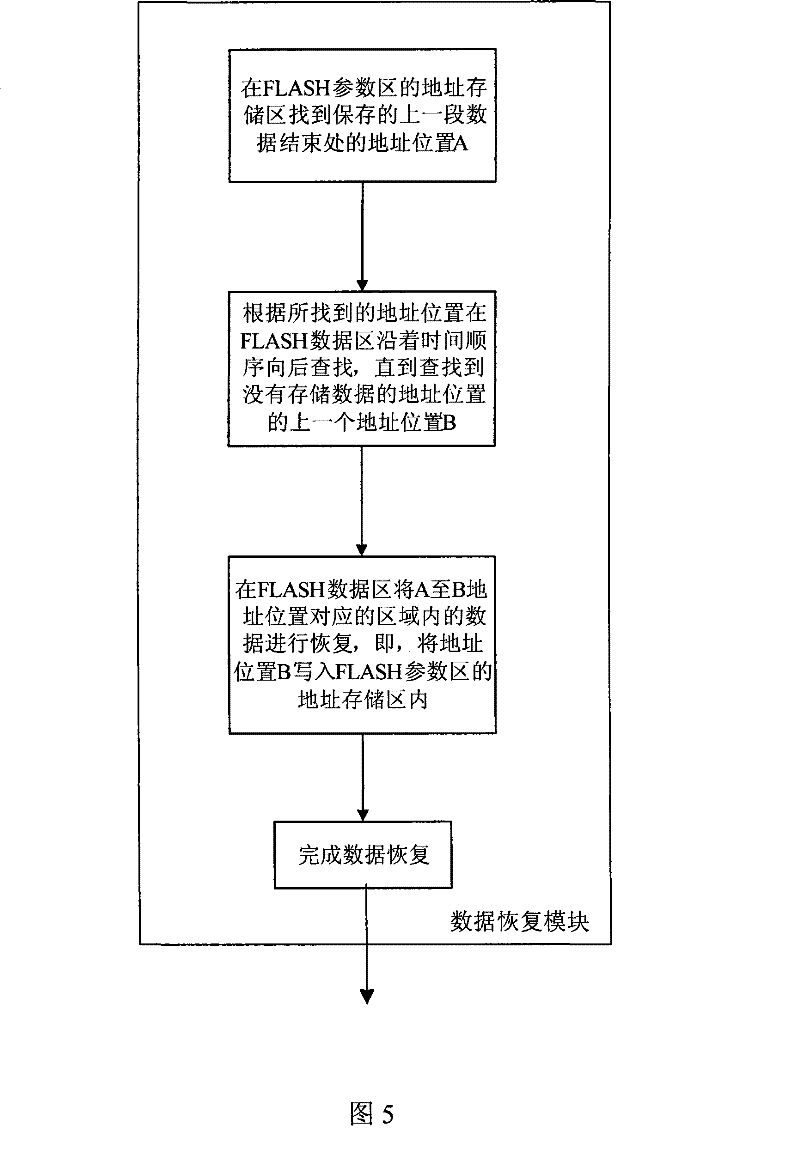
ActiveCN101471125AAchieve data recoveryAchieve preservationDigital storageElectricityComputer module
The invention relates to an electronic recording device providing the power-fail data protection, which comprises an interface which exchanges data with an external device, a controller connected with the interface, a storage module connected with the controller, and a microprocessor connected with the controller, and further comprises a data recovery module connected with the microprocessor, and a detecting module which is connected with the microprocessor and is used for detecting data conditions. Since using the technical proposal, the data before the power-fail can be recovered and stored under the condition that an electronic recording device is power-failed, which guarantees the safety of data and satisfies the requirements of optimum data storage under the condition of power-fail.
Owner:AIGO ELECTRONICS TECH
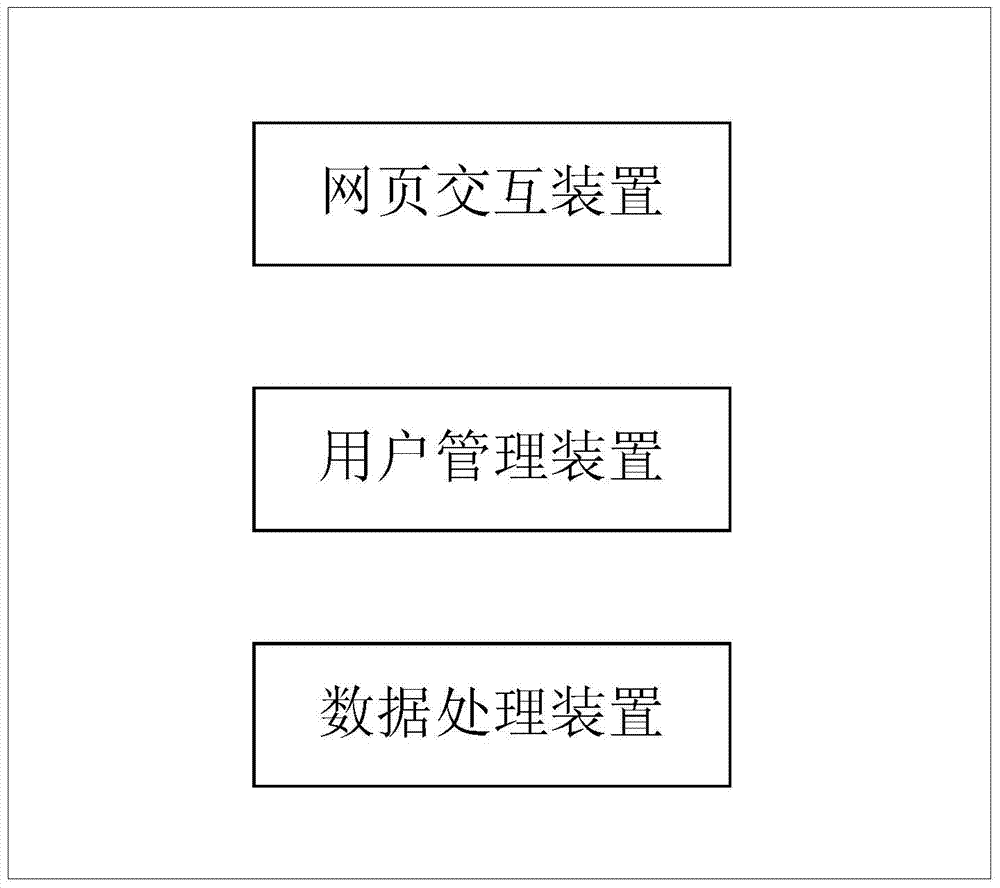
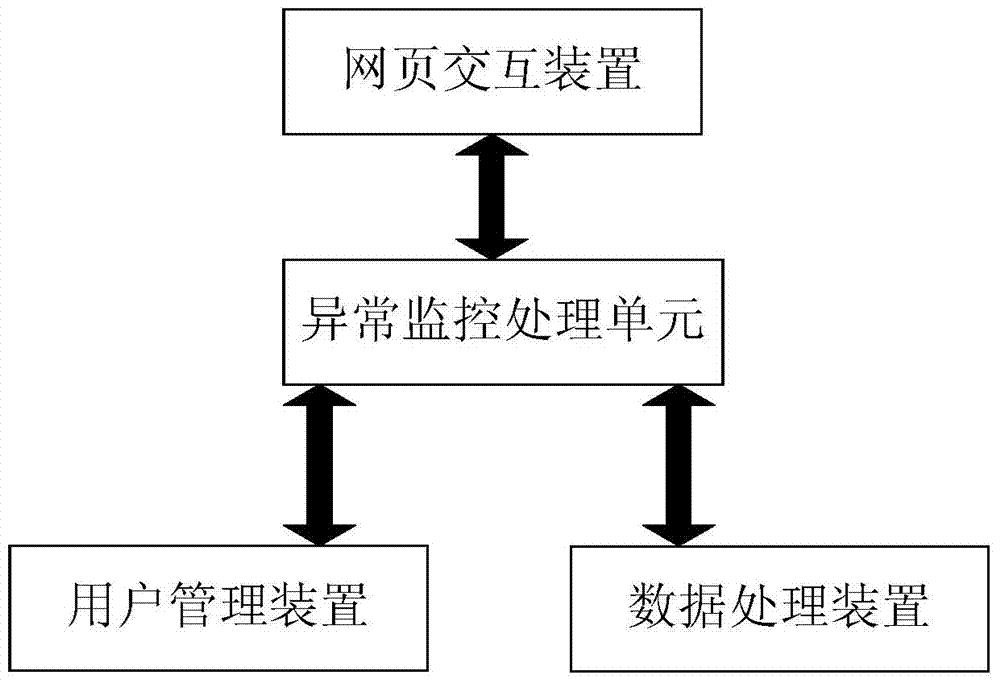
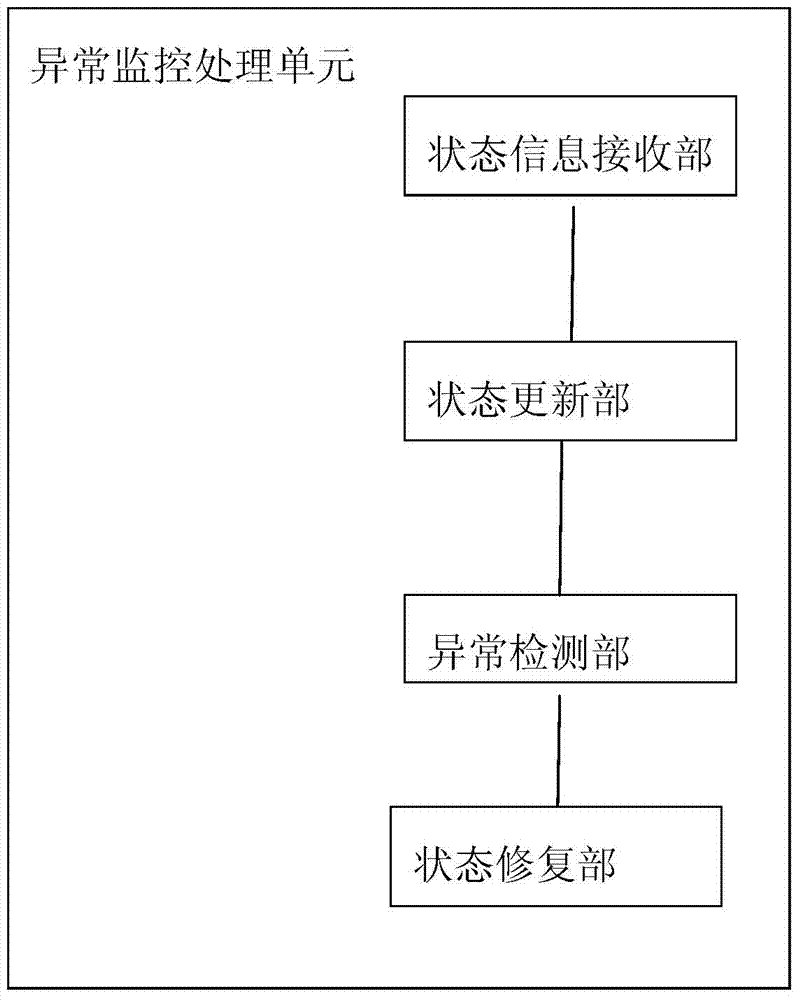
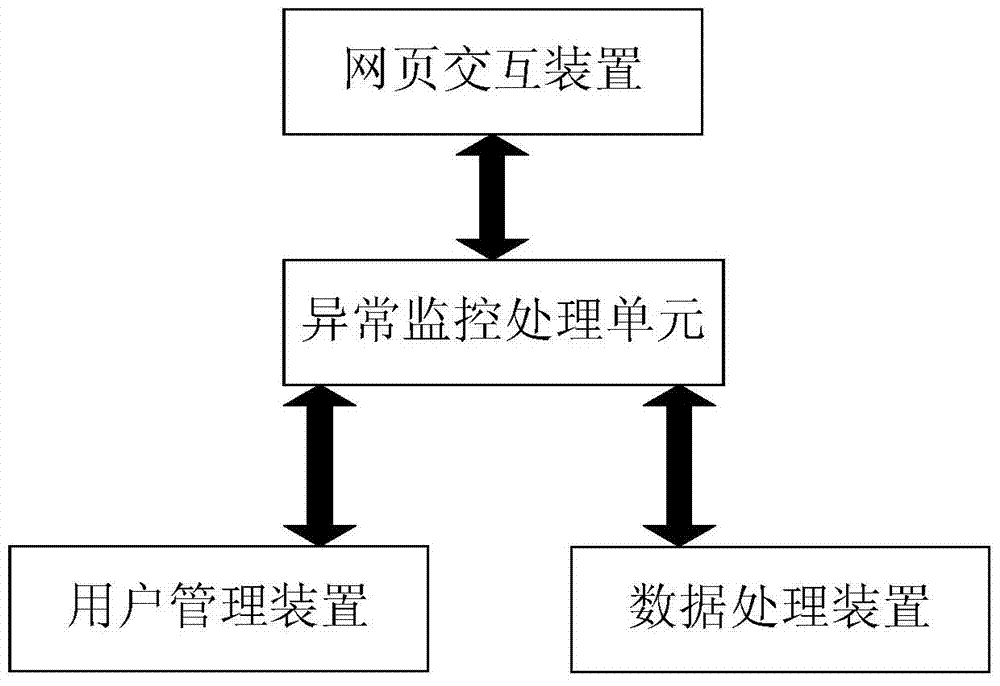
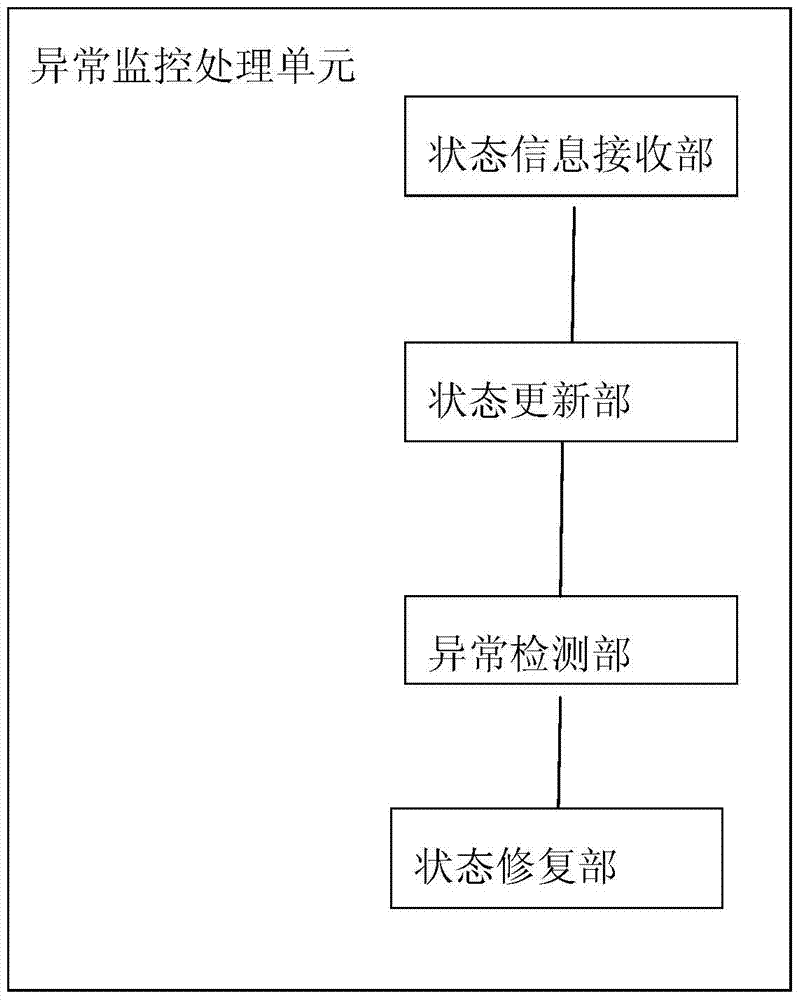
Server capable of achieving network abnormity repair and network abnormity repair method thereof
InactiveCN103490946AShorten recovery timeAvoid restartData switching networksInteraction deviceUser management
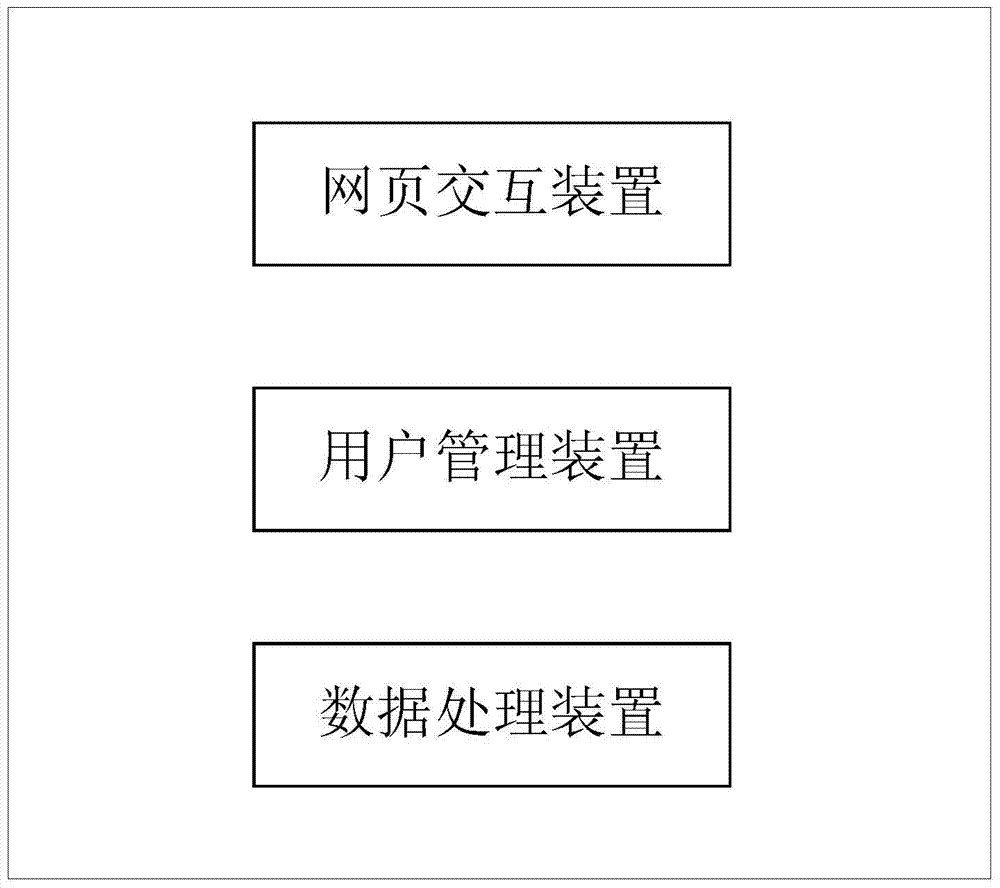
The invention provides a server capable of achieving network abnormity repair and a network abnormity repair method of the server. The server comprises a webpage interaction device, a user management device, a data processing device and an abnormity monitoring processing unit, wherein the webpage interaction device is used for processing operations between a user and a server system, the user management device is used for managing the login permission of the user, the data processing device is used for processing data accessed by the user, and the abnormity monitoring processing unit is used for monitoring the conditions of devices in the server in real time. According to the server and the network abnormity repair method of the server, concrete analysis can be carried out according to the specific conditions of an abnormity, a complete computer is prevented from being restarted, and the recovery time after the device abnormity is shortened.
Owner:OPZOON TECH
Data sending control method and device, terminal, base station and medium
ActiveCN112996052AAchieve data recoveryAchieve recoveryNetwork traffic/resource managementAdaptation strategy characterisationEngineeringReal-time computing
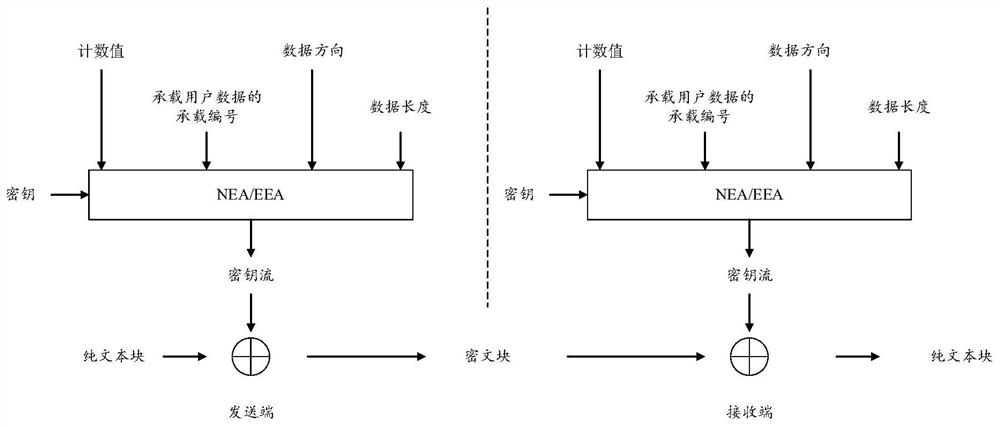
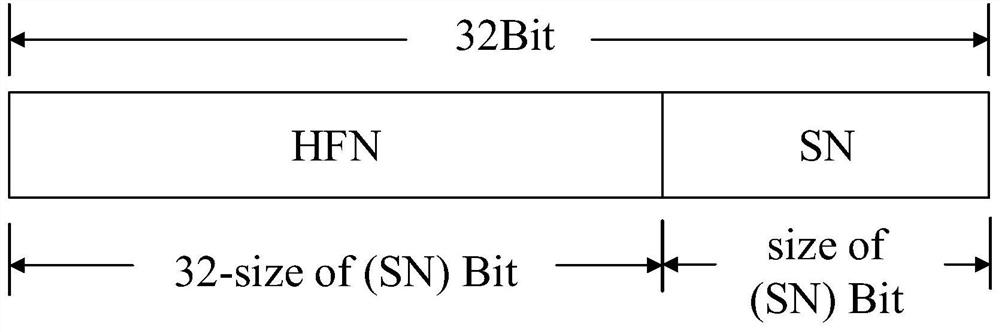
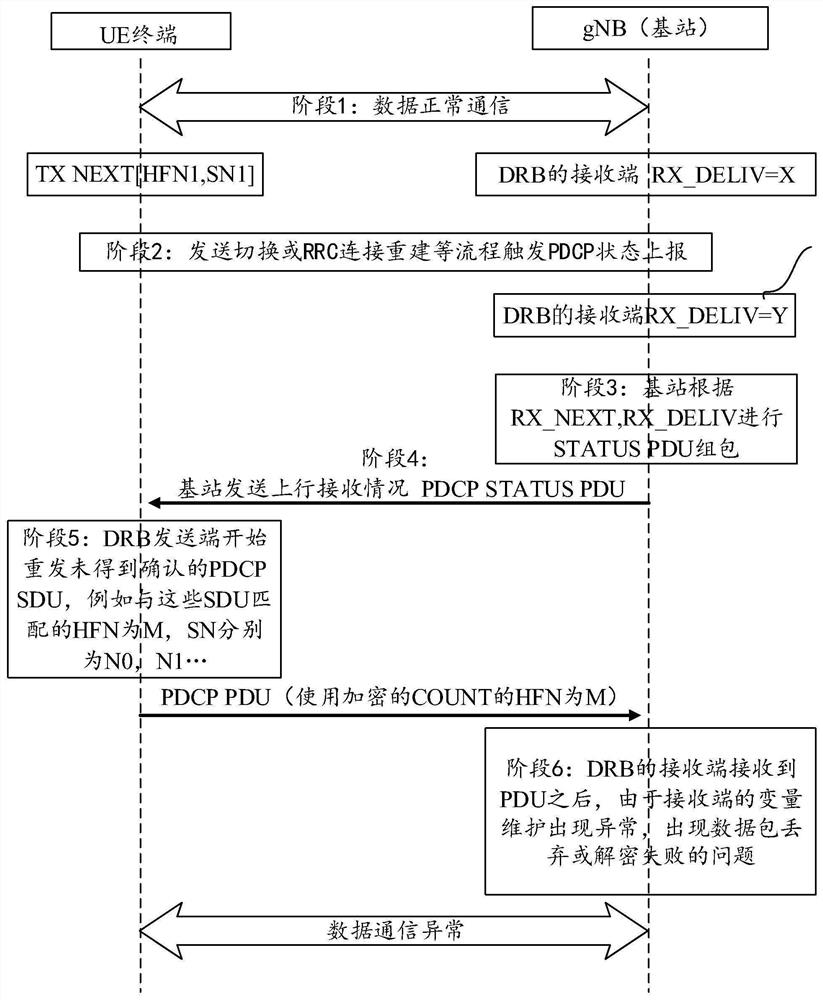
The embodiment of the invention provides a data sending control method and device, a terminal, a base station and a medium. The method comprises the steps of a PDCP sending end obtaining PDCP state report information sent by a PDCP receiving end; and if the parameter in the PDCP state report information fails to be matched with the current sending state of the PDCP sending end, correcting an encryption parameter of a subsequent PDCP PDU data packet to be sent or to be retransmitted by the sending end according to the parameter in the PDCP state report information so as to obtain the corrected encryption parameter. According to the scheme, the encryption parameter of the subsequent PDCP PDU data packet to be sent or to be resent at the sending end is corrected according to the parameter in the PDCP state report information, so that data recovery is realized.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
Server capable of realizing network anomaly repair and network anomaly repair method thereof
InactiveCN103490946BAchieve data recoveryShorten recovery timeData switching networksRecovery methodData access
The present invention provides a server capable of repairing network abnormalities and a method for repairing network abnormalities. The server includes: a web page interaction device for processing operations between users and the server system; a user management device for The login authority is managed; the data processing device is used for processing the data accessed by the user; and the abnormal monitoring processing unit is used for real-time monitoring of the status of each device in the server. According to the server and the method for repairing the abnormality of the network of the present invention, it can be analyzed in detail according to the specific situation of the abnormality, so as to avoid restarting of the whole machine and shorten the recovery time after the abnormality of the equipment.
Owner:OPZOON TECH
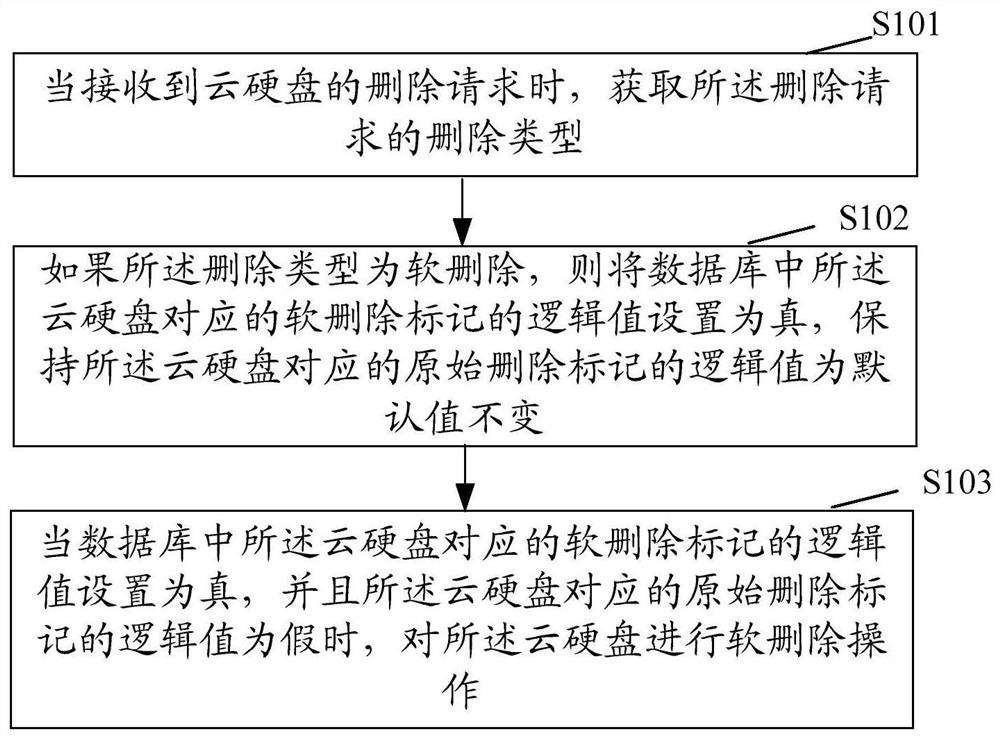
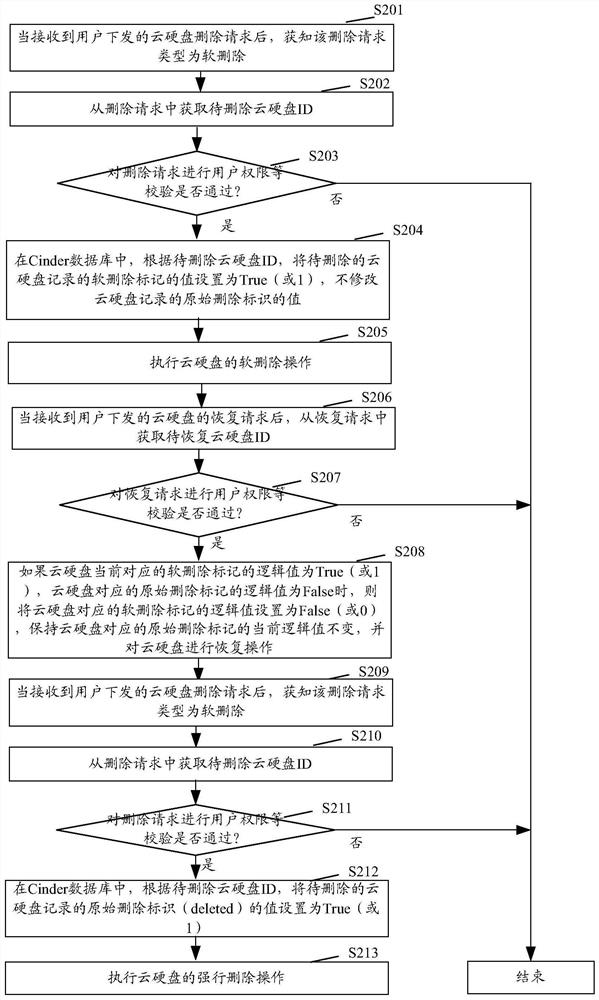
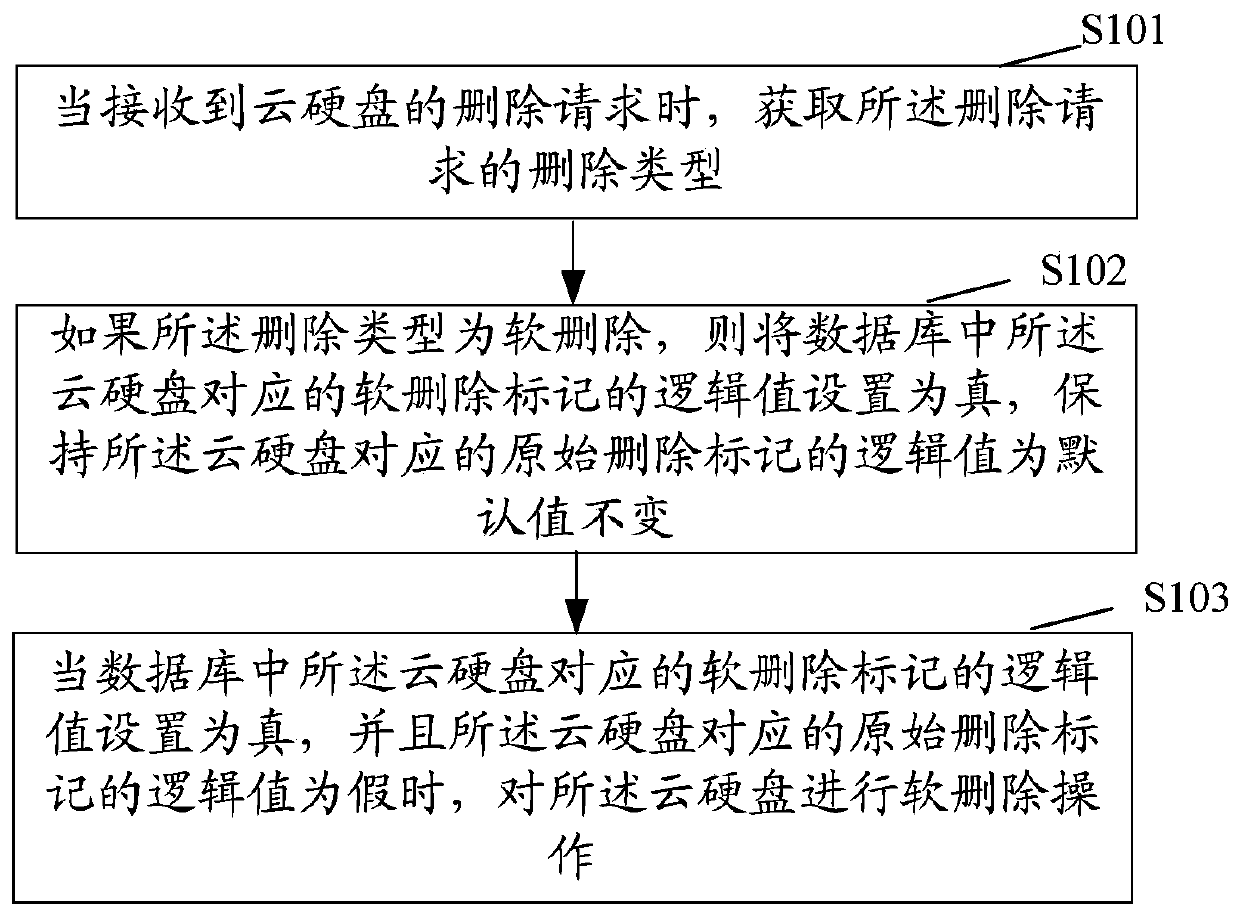
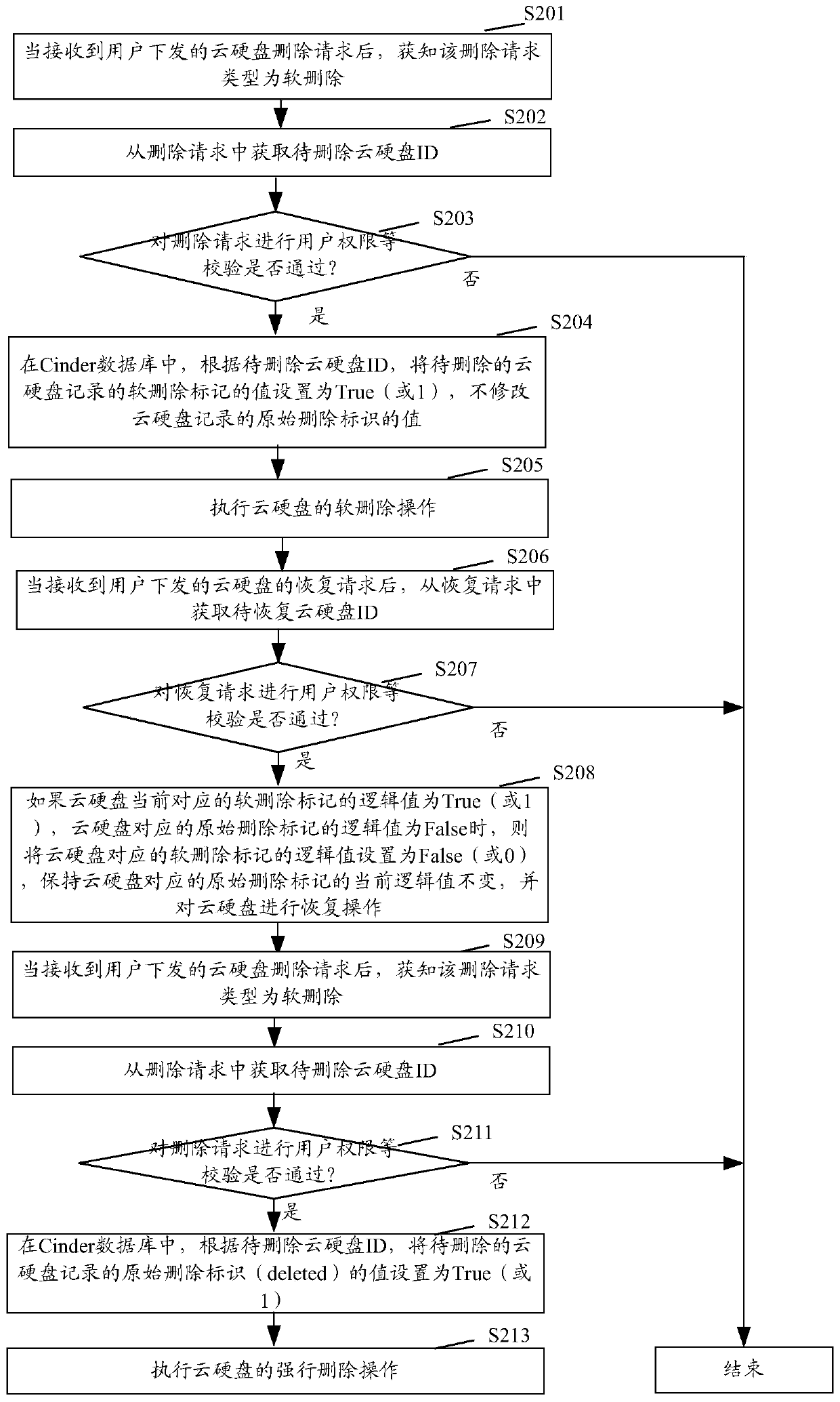
A data processing method and device
ActiveCN110381121BAchieve data recoveryResource allocationTransmissionTheoretical computer scienceData recovery
The present application provides a data processing method and device, and the method includes: when receiving a deletion request of a cloud hard disk, obtaining the deletion type of the deletion request; if the deletion type is soft deletion, the The logical value of the corresponding soft deletion flag of the cloud hard disk is set to true, and the logical value of the original deletion flag corresponding to the cloud hard disk is maintained as the default value; when the logical value of the soft deletion flag corresponding to the cloud hard disk in the database is set to is true, and the logical value of the original deletion flag corresponding to the cloud hard disk is false, perform a soft delete operation on the cloud hard disk; wherein, the default value of the logical value of the original deletion flag corresponding to the cloud hard disk is false. This application does not delete data violently, so that subsequent data recovery can be realized.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
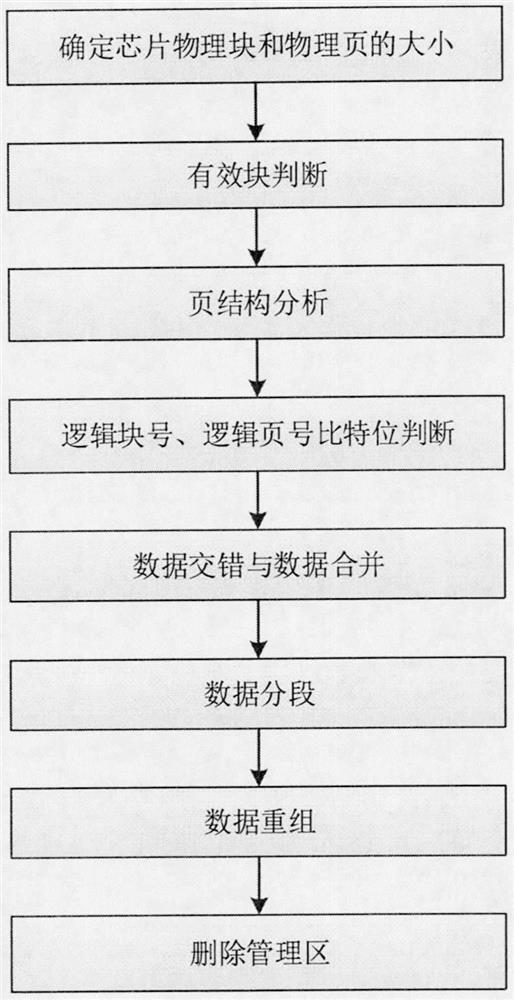
A method for analyzing data storage structure of nand FLASH memory chip
ActiveCN106201774BAchieve data recoveryImprove general performanceMemory adressing/allocation/relocationRedundant operation error correctionComputer architectureData segment
The invention discloses a data storage structure analyzing method of a NAND FLASH memory chip. The method comprises: determining the size of physical blocks and the size of physical pages of the chip, and opening a physical image as read-only; carrying out valid block judgement; analyzing the structure of the pages by utilizing the physical pages where continuous data exists; determining the positions of logical block numbers and the positions of logical page numbers according to the changes over bits of each physical page admin area; conducting data interleave analyzing and data merging according to the data continuity condition of a data volume which can reflect the continuity about data; judging whether or not to conduct data segmenting according to the duplication of the logical block numbers; conducting data reorganizing; and deleting the admin area data, and finally obtaining a logical image file. According to the data storage structure analyzing method of the NAND FLASH memory chip, the conversion from the physical image to the logical image of the storage chip is realized on the premise that an NAND FLASH control circuit is not used, thus the aim that conducting data recovering and obtaining evidence after this class of devices are damaged is achieved.
Owner:中国人民解放军61660部队
A data recovery method of raid-5
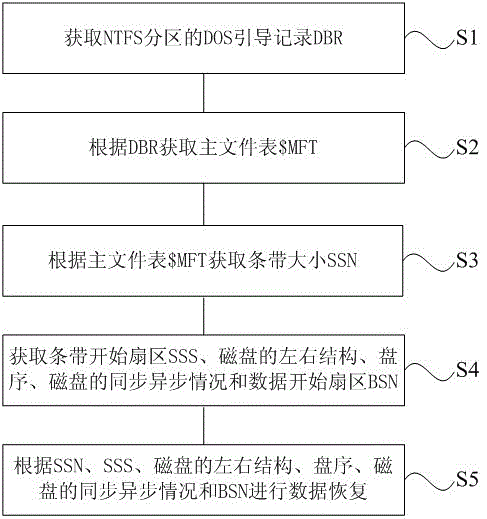
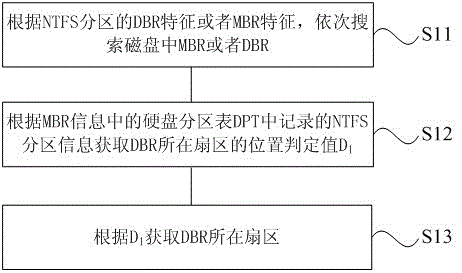
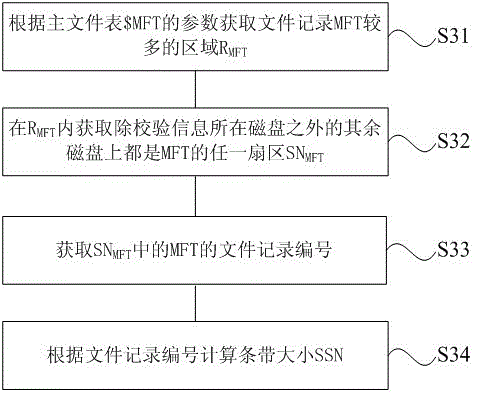
ActiveCN103150233BAchieve data recoveryAccurate analysisRedundant operation error correctionRAIDFile system
The invention provides a data recovery method of an RAID-5 (Redundant Array of Independent Disk 5), which comprises the steps that an DBR (Dos Boot Record) of an NTFS (New Technology File System) partition is acquired; a $ MFT (Master File Table) is acquired according to the DBR; a strip size SSN is acquired according to the $ MFT; an SSS (Strip Starting Sector) , left and right structures of a disk, a disk sequence, synchronous and asynchronous situations of the disk, and a data starting sector BSN are acquired; and data recovery is performed according to the SSN, the SSS, the left and right structures of the disk, the disk sequence, the synchronous and asynchronous situations of the disk, and the BSN. With the adoption of the method, RAID information of the RAID-5 can be analyzed accurately, and the data recovery is performed by using the RAID information. The method has better general applicability and higher recovery success rate.
Owner:厦门市美亚柏科信息安全研究所有限公司
An application method for accurately obtaining llr information
ActiveCN106981308BAccurate estimateEfficiency of normal read and write NANDRead-only memoriesError correction/detection using multiple parity bitsAlgorithmTheoretical computer science
The invention discloses an application method for accurately obtaining LLR information. The method is characterized by comprising the steps of selecting statistics samples; calculating Optimal Vref of each sample; by setting multi-level multi-bit reading voltages, calculating the LLR information corresponding to the multi-level reading voltages, and performing multi-bit LDPC decoding; and by comparing iterative frequencies and decoding results of the multi-bit LDPC decoding corresponding to different reading voltages, recording the reading voltage with the lowest iterative frequency and the decoding correctness as a multi-bit optimal reading voltage, wherein the corresponding LLR information is initial LLR information of a batch of products, and the batch of the products finitely adopt the optimal reading voltage to read data by default and adopt the initial LLR information to decode the data. An empirical value is obtained by adding statistics and serves as a parameter during normal decoding to ensure normal NAND reading-writing efficiency; and when the normal decoding fails and data recovery needs to be carried out, the scheme can estimate more accurate multi-bit LLR information, thereby reducing the error code rate and realizing the data recovery.
Owner:RAMAXEL TECH SHENZHEN
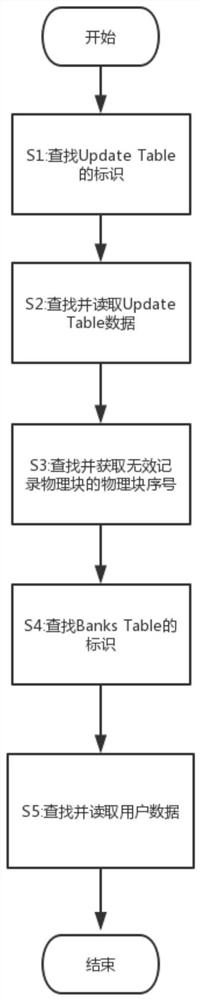
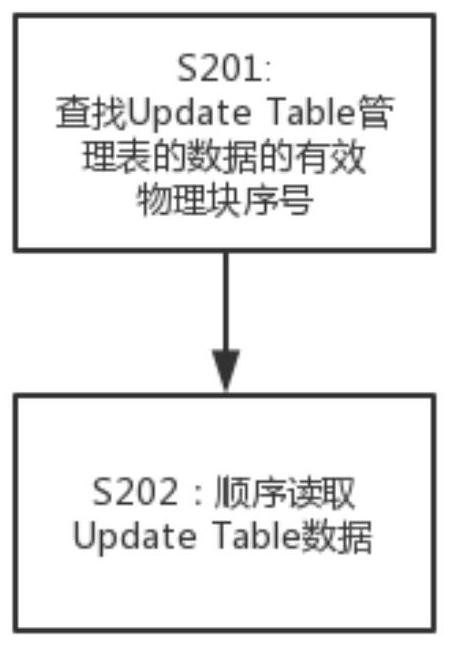
A method for reorganizing nand-flash chip data
ActiveCN107908572BSpeed up recoveryIncrease success rateMemory adressing/allocation/relocationByte addressingData reorganization
The invention discloses a method for reorganizing NAND-Flash chip data, which is characterized in that it includes the following steps, S1: within the byte length range of each physical block of the NAND-Flash chip, use the header of each physical block Byte address is initial address, searches for the mark of Update Table; S2: according to the mark of described Update Table, finds and reads Update Table data; S3: finds and obtains the physical of the invalid record physical block of described NAND-Flash chip Block sequence number, the invalid record physical block is a physical block that does not store data; S4: search for the logo of the Banks Table; S5: search and read user data according to the logo of the Banks Table; the present invention has simple and effective, data The beneficial effect of recovering and recombining high efficiency, and solving the problem that there is no data reorganizing technical solution for the chip whose main control chip model is SSS6677 in the prior art, realizes the data recovery of this type of NAND-Flash storage device and e-discovery.
Owner:SICHUAN QIAODUOTIANGONG PRECISION EQUIP CO LTD
Data processing system and data processing method
ActiveCN110012087BAchieve data recoveryTransmissionSoftware simulation/interpretation/emulationPathPingData processing system
The invention discloses a data processing system and a data processing method. The data processing system includes a distributed object storage subsystem, a first host machine including a first container, and a second container. When performing cross-container data recovery, the first host converts the container-side recovery request initiated by the first container for the target file under the container-side file path of the second container into an object download request including the access key of the same data bucket , the distributed object storage subsystem reads the object corresponding to the target file in the same data bucket according to the object download request after the access key verification is passed, and sends the read object to the first host, and the first host then sends the After the object is converted into a file, it is mapped to the first container. In view of the fact that the first container and the second container are different containers in the present invention, and the container-side file paths of the same data bucket are respectively mounted, data recovery across containers can be effectively realized.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
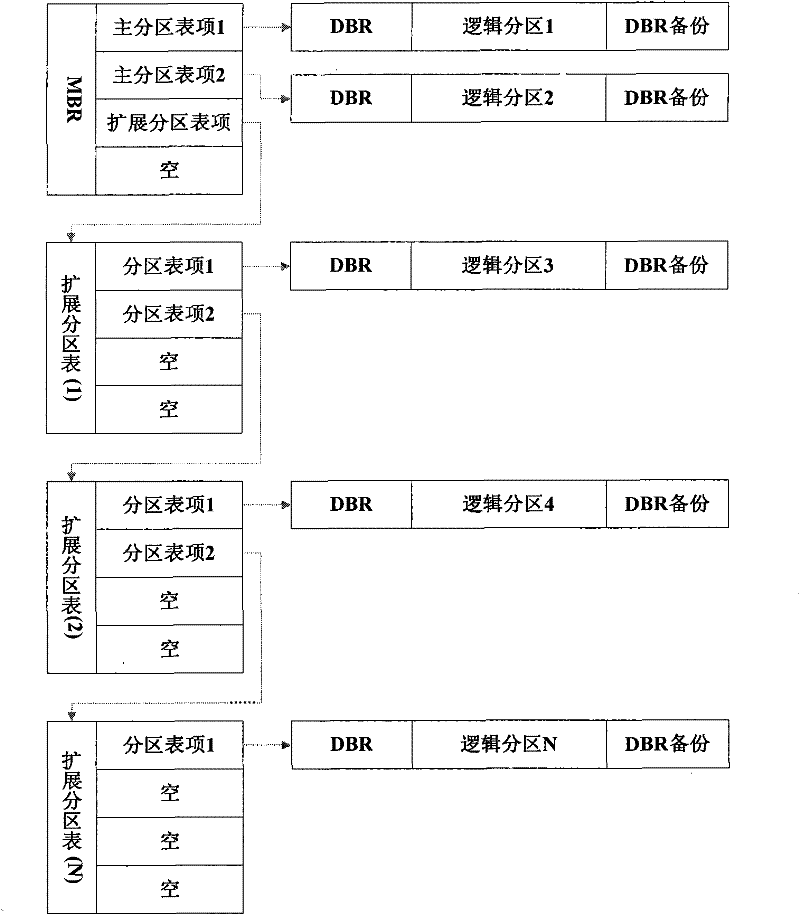
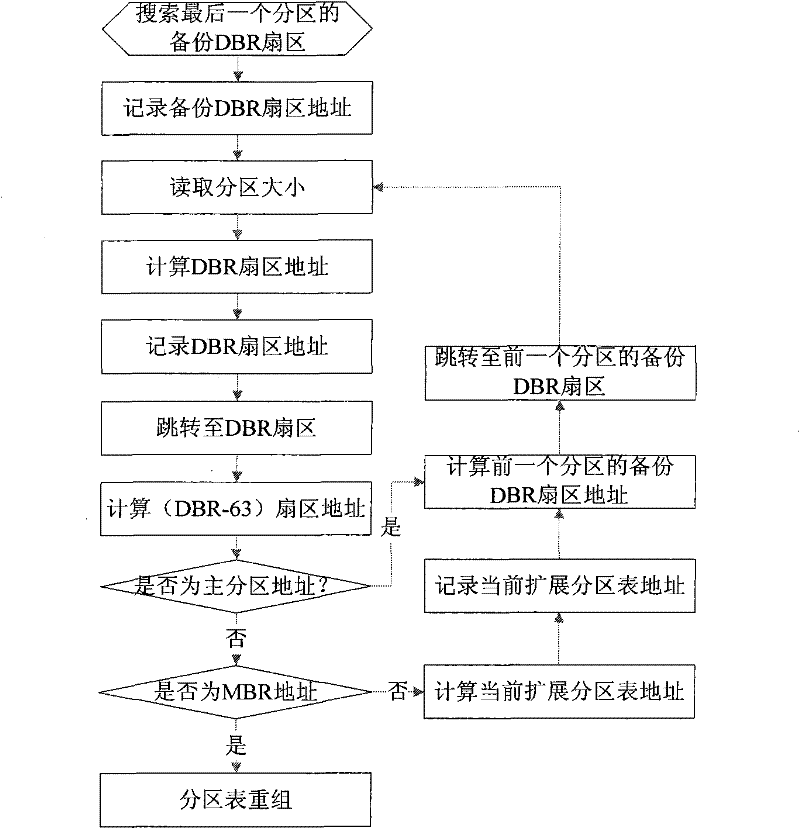
Fast reverse search restructuring and recovery method of hard disk partition table
ActiveCN101763296BAchieve data recoveryFast recoveryRedundant operation error correctionRecovery methodRestoration method
The invention discloses a fast reverse search restructuring and recovery method of a hard disk partition table. A destroyed main partition table is restored by adopting an NTFS partition table chain reverse search restructuring algorithm based on a back-up DBR, therefore, the data recovery of a hard disk is realized. The method comprises two processes of partitional and reverse scanning of an NTFS system and main partition table restructuring. The invention has fast recovery speed, simple operation and high recovery success ratio, and realizes the restructuring and the recovery of the whole main partition table.
Owner:江苏航天龙梦信息技术有限公司
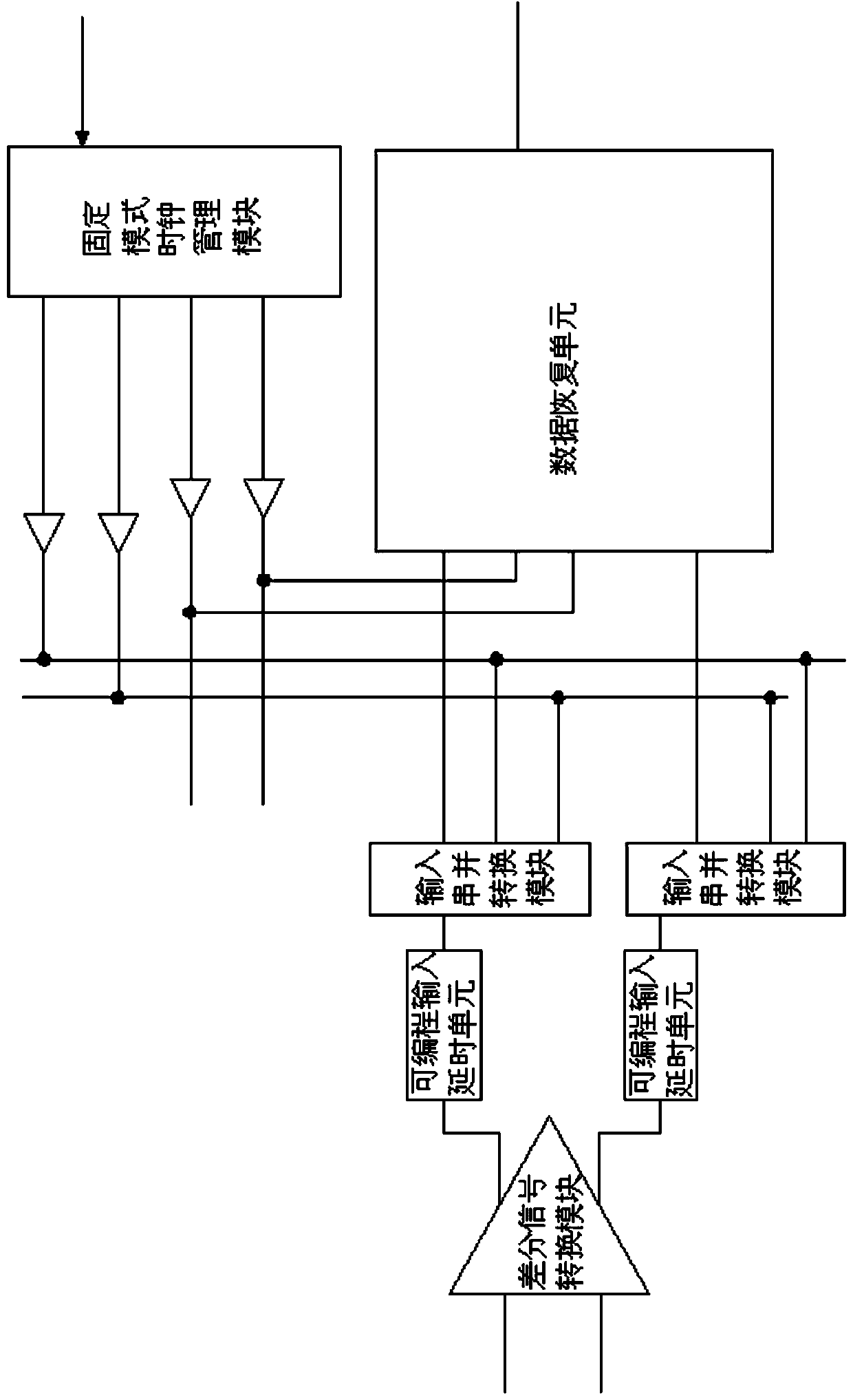
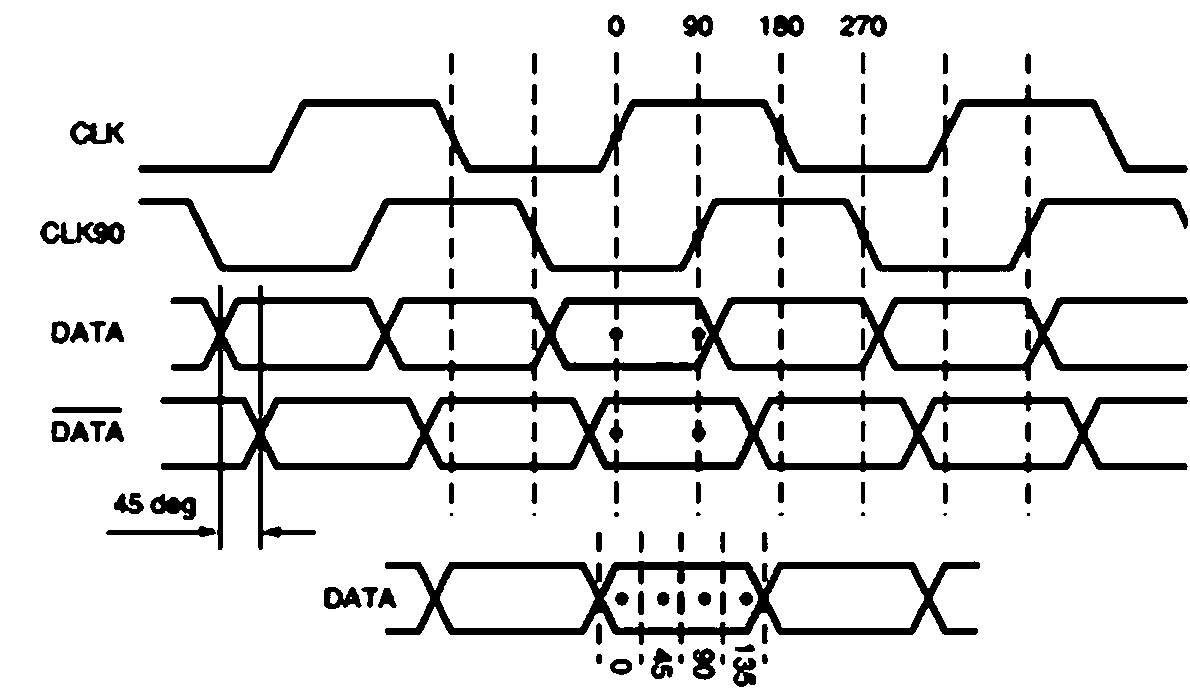
A FPGA implementation system and method for oversampling data clock recovery
ActiveCN106021025BFlexible to meet various needsAchieve data recoveryRedundant operation error correctionDifferential signalingFpga implementations
The invention discloses an oversampling data clock recovery FPGA realizing system and method; the system comprises a differential signal conversion module arranged in the FPGA, a programmable input delay unit, an input serial-parallel conversion module and a fixed mode clock management module; the differential signal conversion module is connected with the programmable input delay unit; the programmable input delay unit is connected with the input serial-parallel conversion module; the input serial-parallel conversion module is connected with the fixedly mode clock management module. The differential signal conversion module carries out caching treatment for an external input differential signal sent into the FPGA, thus forming two FPGA internal differential signals; aiming at the problems that the FPGA chip cannot provide sufficient GE port special pins, the novel method can use a normal IO to realize data clock recovery; the method uses normal IO to carry out data recovery, thus flexibly satisfying various demands, and the realizing number can no longer be limited by special pins carried by the FPGA chip.
Owner:OPHYLINK COMM TECH
Data recovery method, device and system based on distributed system
ActiveCN107451013BAchieve data recoveryRedundant operation error correctionData segmentData operations
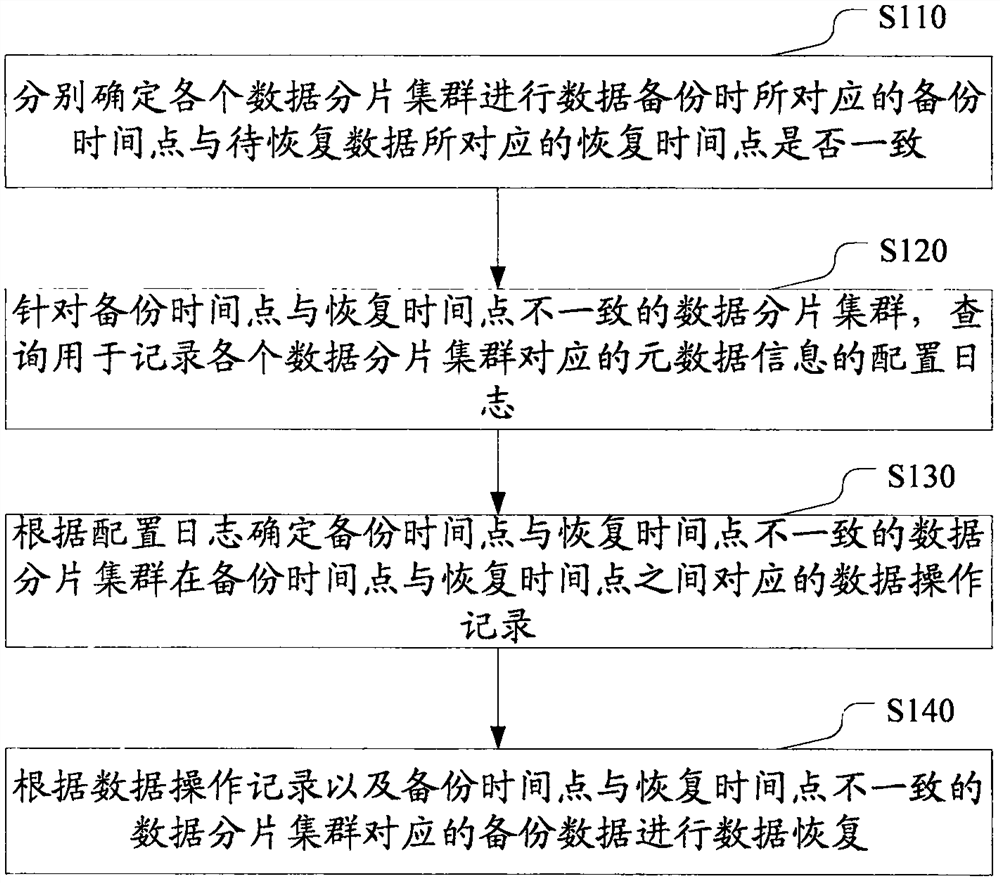
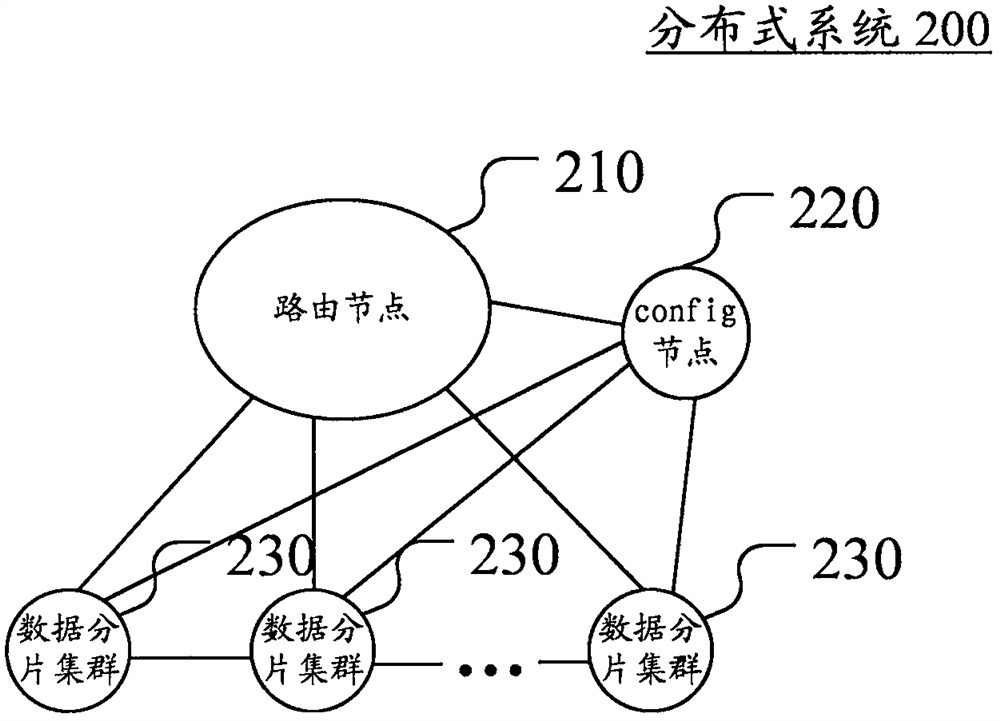
The present invention discloses a data recovery method, apparatus and system based on a distributed system. The method comprises: determining whether a backup time point corresponding to each data segment cluster during data backup is consistent with a recovery time point corresponding to to-be-recovered data; for the data segment cluster whose backup time point is inconsistent with a recovery time point, searching for a configuration log used for recording metadata information corresponding to each data segment cluster; according to the configuration log, determining a data operation record corresponding to the data segment cluster whose backup time point is inconsistent with the recovery time point between the backup time point and the recovery time point; and performing data recovery according to the data operation record and backup data corresponding to the data segment cluster whose backup time point is inconsistent with the recovery time point. According to the method provided by the present invention, data backup can be performed for each data segment cluster, so that data recovery of the distributed system is realized accurately and efficiently.
Owner:BEIJING QIHOO TECH CO LTD
A method and system for preventing ransomware attacks based on solid-state storage devices
ActiveCN109388945BAvoid misuseIncrease management costsPlatform integrity maintainanceRedundant operation error correctionSolid-state storageAttack
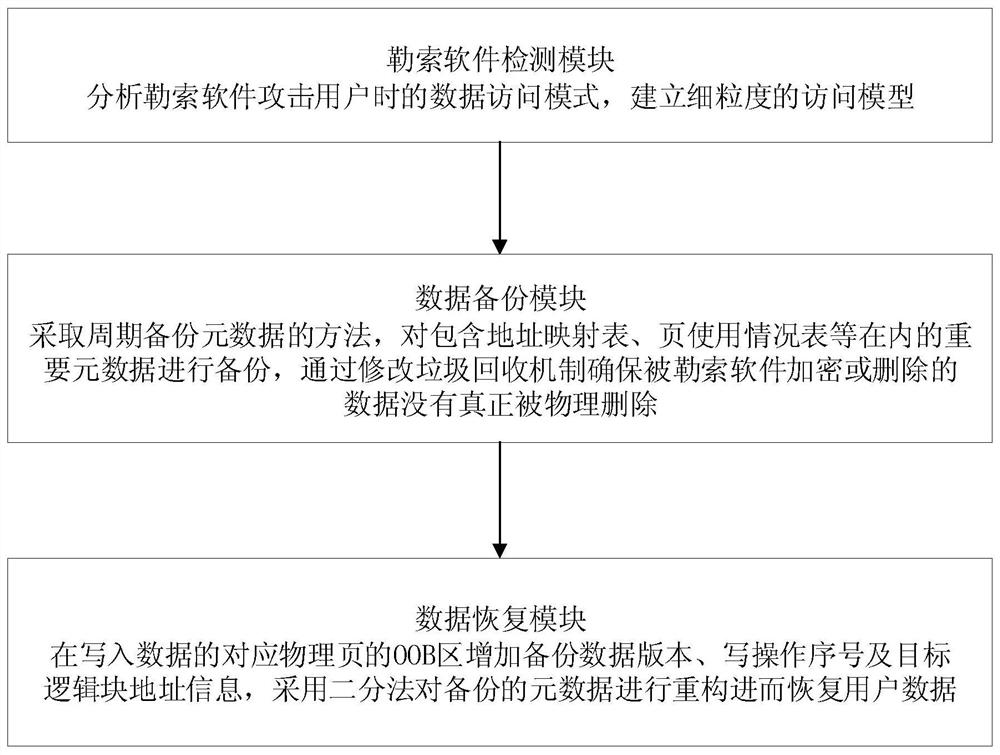
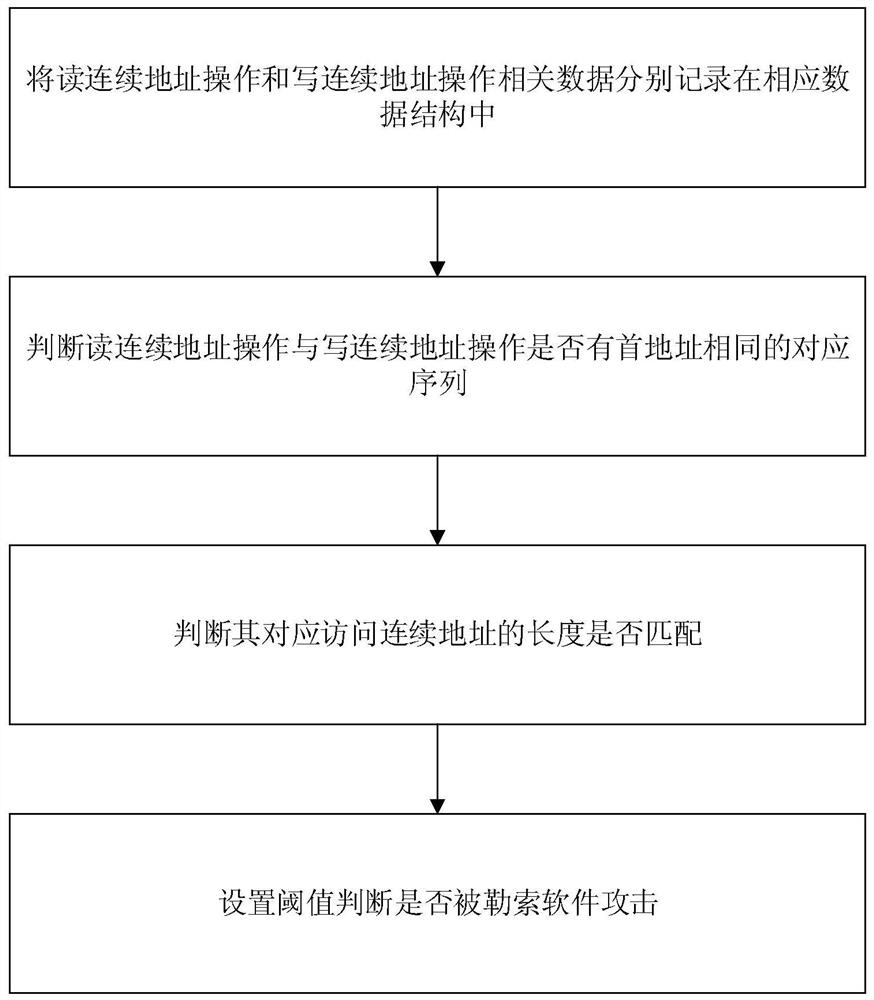
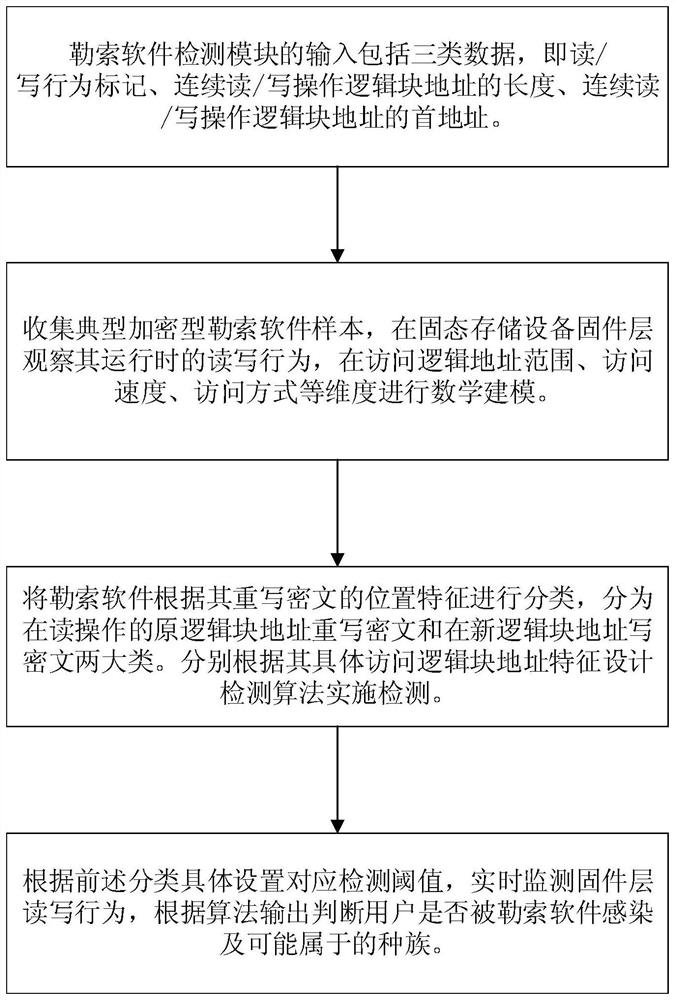
The invention discloses a method and system for preventing ransomware attacks based on solid-state storage devices, which realizes detection of ransomware in the firmware flash memory conversion layer of the solid-state storage devices, and utilizes the characteristics of non-in-situ update of solid-state storage devices to realize data lightweight backup and data backup. recover. The ransomware detection module establishes a fine-grained access model according to the special data access mode when the ransomware attacks the user; the data backup module adopts the method of periodic backup when the detection module does not detect the ransomware. The important metadata including the page usage table is backed up, and the garbage collection strategy is used to ensure that the data of the current backup version will not be physically deleted; the data recovery module adds the backup data version and the write operation by adding the backup data version in the OOB area of the corresponding physical page during the write operation. The serial number and target logical block address information are used to reconstruct the backup metadata by the dichotomy method, thereby realizing the rapid recovery of user data.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Program method, data recovery method, and flash memory using the same
ActiveUS8738844B2Avoid data lossAchieve data recoveryMemory architecture accessing/allocationError detection/correctionRecovery methodData storing
Owner:MACRONIX INT CO LTD
A Realization Method of Secure E-mail Based on Digital Envelope
ActiveCN105323070BRealize encryption and decryptionAchieve decryptionUser identity/authority verificationData switching networksCiphertextConfidentiality
The invention relates to the technical field of information security, and in particular relates to a method for realizing a security electronic mail based on a digital envelope. According to the invention, on the basis of the digital envelope technology based on PKI symmetric and asymmetric key algorithms, mail encryption and decryption information, user key information, data recovery information, mail ciphertext and other information are assembled into the digital envelope; and thus, encryption, decryption and data recovery of the electronic mail are realized. According to the invention, a session key is encrypted by obtaining all public key certificates of each receiver from a LDAP, such that interconnection and intercommunication of multiple certificates of one person are realized; when a mail blind copying function is started, mail information can be decrypted only by the private key of a blind copying user; therefore, the identity confidentiality of the blind copying user is ensured; in an emergency case that the private key of the user is lost or damaged, mail information can be decrypted without recovering the private key of the user through a KMC; and, by means of a high-grade security protection mechanism that the encrypted private key cannot be derived and a strict service approval signature mechanism, the security of recovered information is ensured from the perspectives of technologies and management.
Owner:BC P INC CHINA NAT PETROLEUM CORP +2
A text indexing method and system based on storm flow computing framework
InactiveCN105930360BIncrease heightAchieve recoveryCharacter and pattern recognitionNatural language data processingFault toleranceData Corruption
The invention discloses a text indexing method and system based on the Storm stream computing framework, comprising: the realization of the topology of Storm, the design of the Storm real-time data processing framework, and the completion of the automatic web page extraction program of the web crawler; automatic keyword extraction; text classification, according to the text The content or properties of , group the text into one or more categories. The invention enables itself to rewind the backup data in the case of data damage, loss, etc., to realize data recovery; provides the function of centralized operation and maintenance of the system itself; beautiful and practical interface, convenient and intuitive graphical user management interface; function expansion meets The user's requirements for system expansion and expansion of the scope of use in the future; fault tolerance: when illegal data is generated due to user input or misoperation, the system has a certain fault tolerance mechanism.
Owner:YUNNAN UNIV +2
Electronic voice recording equipment with power-down data protection function
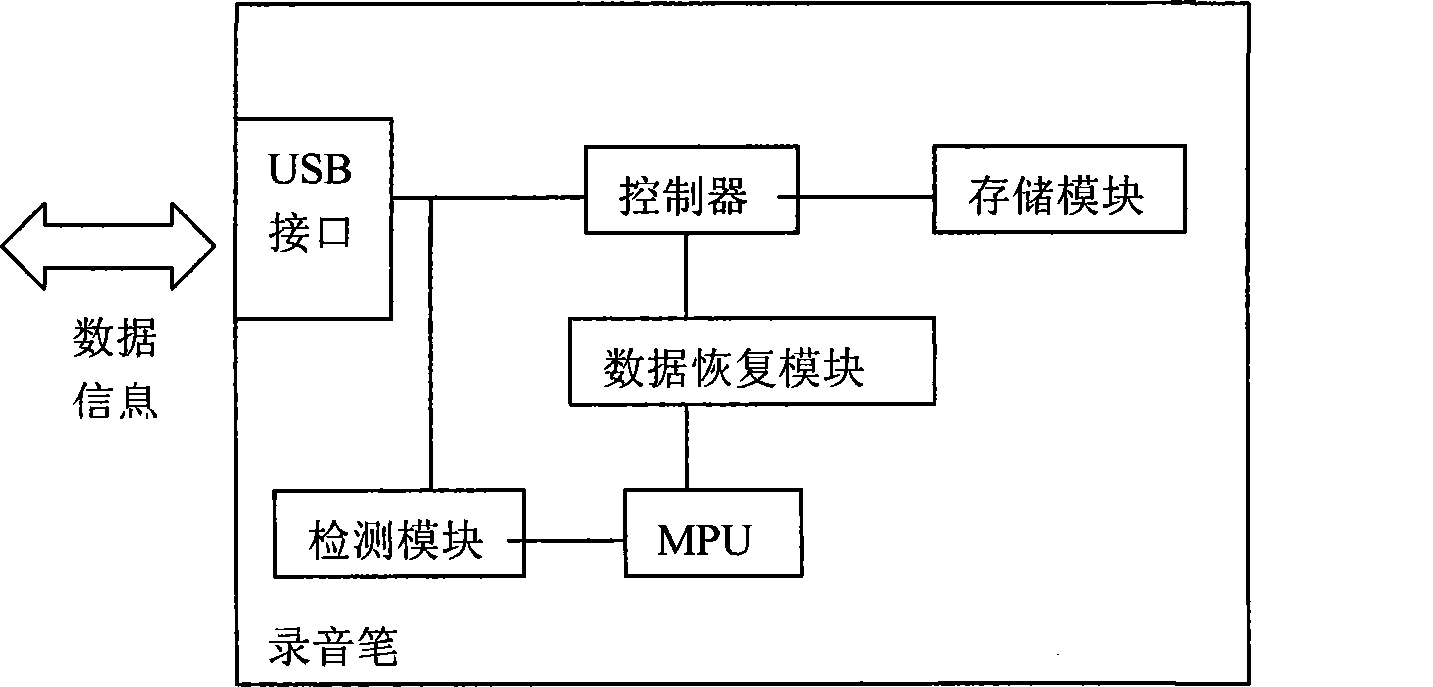
ActiveCN101471125BAchieve data recoveryAchieve preservationDigital storageElectricityComputer module
The invention relates to an electronic recording device providing the power-fail data protection, which comprises an interface which exchanges data with an external device, a controller connected with the interface, a storage module connected with the controller, and a microprocessor connected with the controller, and further comprises a data recovery module connected with the microprocessor, anda detecting module which is connected with the microprocessor and is used for detecting data conditions. Since using the technical proposal, the data before the power-fail can be recovered and storedunder the condition that an electronic recording device is power-failed, which guarantees the safety of data and satisfies the requirements of optimum data storage under the condition of power-fail.
Owner:AIGO ELECTRONICS TECH
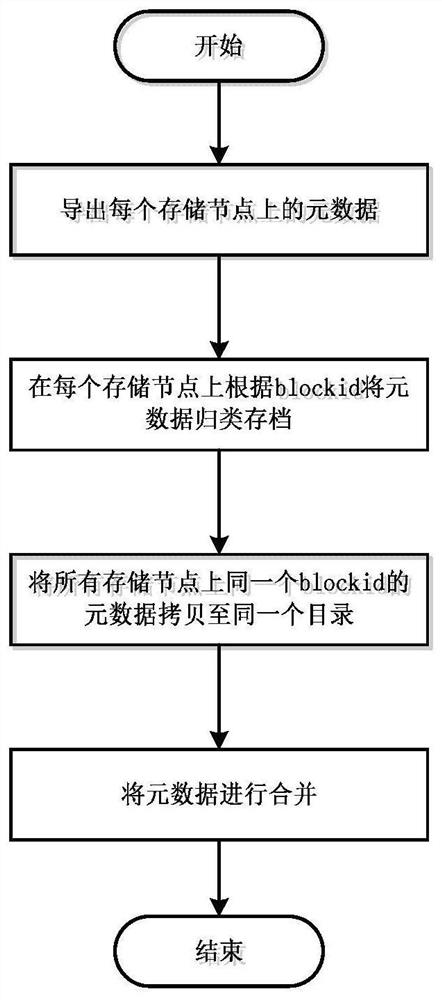
A Recovery Method for Distributed Storage Block Devices
ActiveCN109710180BAchieve data recoveryInput/output to record carriersDistributed data storeEngineering
The invention relates to the technical field of distributed data storage, in particular to a recovery method for distributed storage block devices. The method of the present invention includes the following steps: Step 1: export the metadata on each storage node; Step 2: classify and archive the metadata on each storage node according to the id of the block device; Step 3: export the metadata on all storage nodes Copy the metadata of the same id to the same directory; Step 4: Merge the metadata. The invention solves the problem of block device recovery when the distributed cluster fails.
Owner:G CLOUD TECH
Data processing method and device
The invention provides a data processing method and device, and the method comprises the steps: obtaining a deletion type of a deletion request when the deletion request of a cloud hard disk is received; if the deletion type is soft deletion, setting a logic value of a soft deletion mark corresponding to the cloud hard disk in a database to be true, and keeping the logic value of an original deletion mark corresponding to the cloud hard disk unchanged as a default value; and, when the logic value of the soft deletion mark corresponding to the cloud hard disk in the database is set to be true and the logic value of the original deletion mark corresponding to the cloud hard disk is false, performing soft deletion operation on the cloud hard disk, wherein the default value of the logic valueof the original deletion mark corresponding to the cloud hard disk is false. Violent deletion is not performed on the data, so that subsequent data recovery can be realized.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com