A method and system for preventing ransomware attacks based on solid-state storage devices
A solid-state storage device and software technology, which is applied to the generation of response errors, error detection of redundant data in calculations, and instruments, etc. It can solve problems such as recovery, slow encryption speed, and large key management overhead to achieve reliability Data protection, impact reduction, and the effect of avoiding user misoperation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
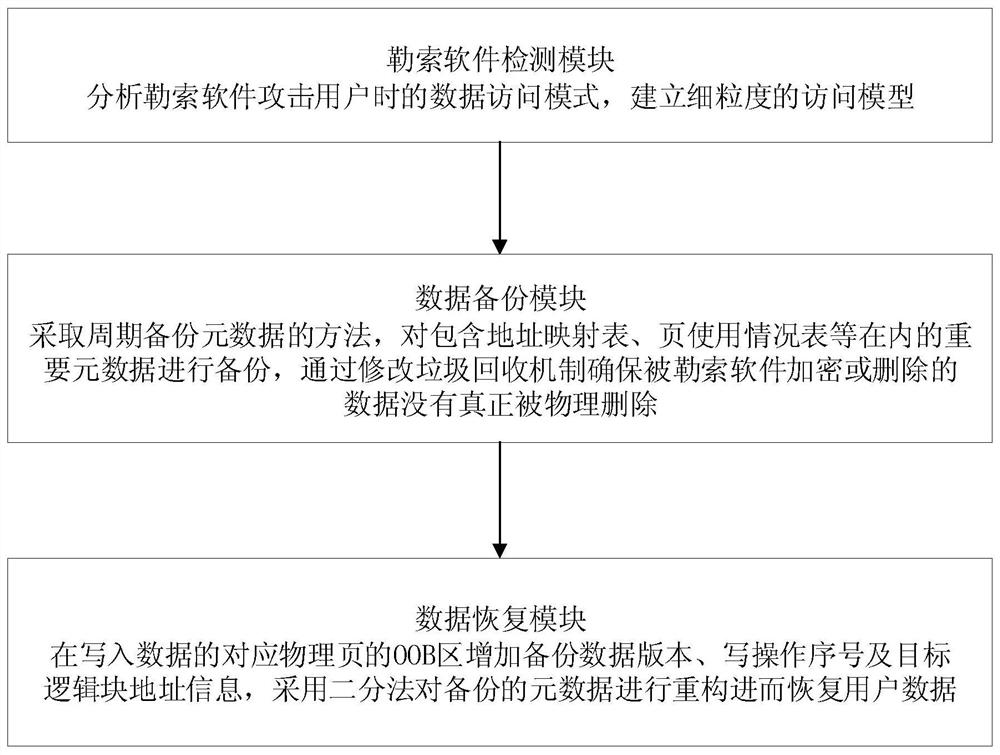
[0049] Such as figure 1 As shown, this embodiment provides a flowchart of a method for defending against ransomware attacks based on solid-state storage devices. Its steps mainly include:
[0050] 1) The ransomware detection module analyzes the data access mode when ransomware attacks users, and establishes a fine-grained access model;
[0051] 2) The data backup module adopts the method of periodically backing up metadata, backs up important metadata, and ensures that the data encrypted or deleted by the ransomware is not actually physically deleted by modifying the garbage collection mechanism;
[0052] 3) The data recovery module adds a data structure in the OOB (out-of-band) area of the corresponding physical page of the written data, including the backup data version, the write operation sequence number and the target logical block address, and uses the binary search method to search the backup metadata Refactor to restore user data.
[0053] High-level ransomware ca...
Embodiment 2
[0064] This embodiment implements a system prototype using OpenNFM. OpenNFM is an open source NAND flash memory controller framework, which is an architecture composed of three layers. The highest layer mainly deals with the mapping between the upper layer and the physical page address to the logical page address between the original flash memory, and the flash memory-based storage device can provide a unified block device interface of the file system. The middle layer is mainly responsible for usage equalization and bad block management. The lowest layer provides a primitive flash abstraction, shielding the special physical properties of NAND Flash. Port this system to lpc-h3131, a development board equipped with 180MHz ARM microcontroller, 512MB NAND flash memory and 32MB SDRAM. The block size of the flash memory is 128KB, and the page size is 2KB, so the entire NAND flash memory has 4,096 erase blocks, and each block consists of 64 pages. Each map entry can be represente...
Embodiment 3
[0076] This embodiment is a method for detecting ransomware based on a solid-state storage device, comprising the following steps:
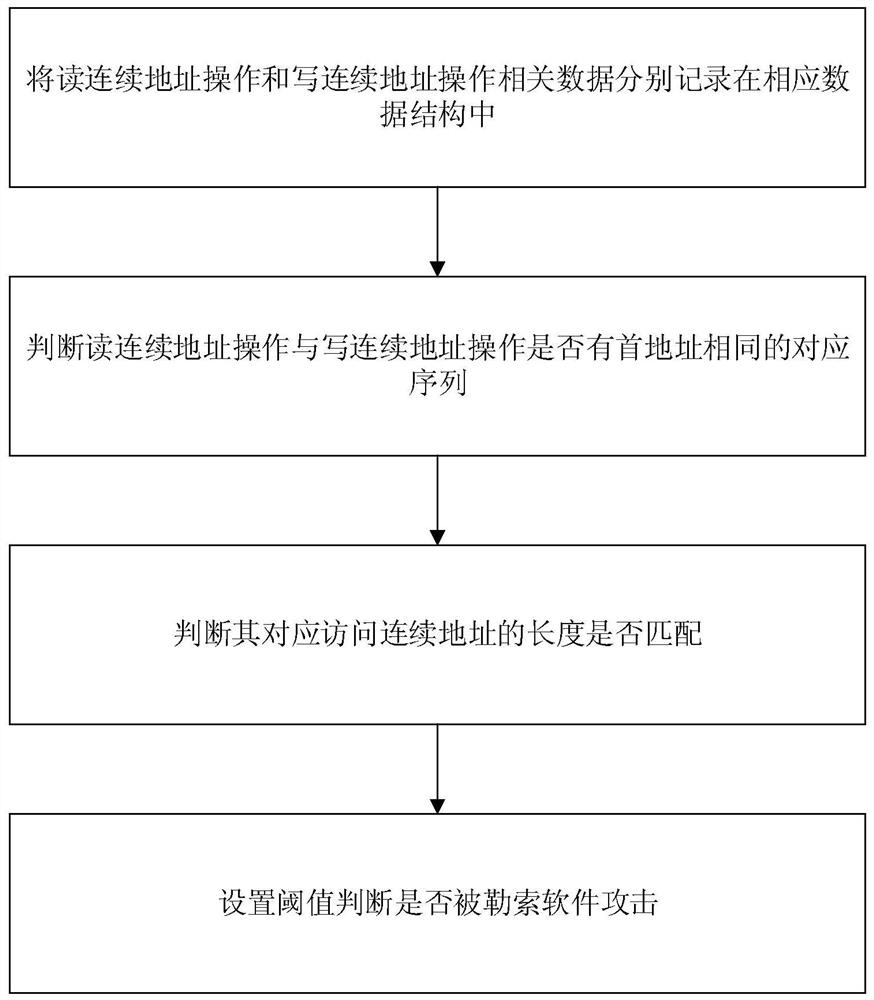
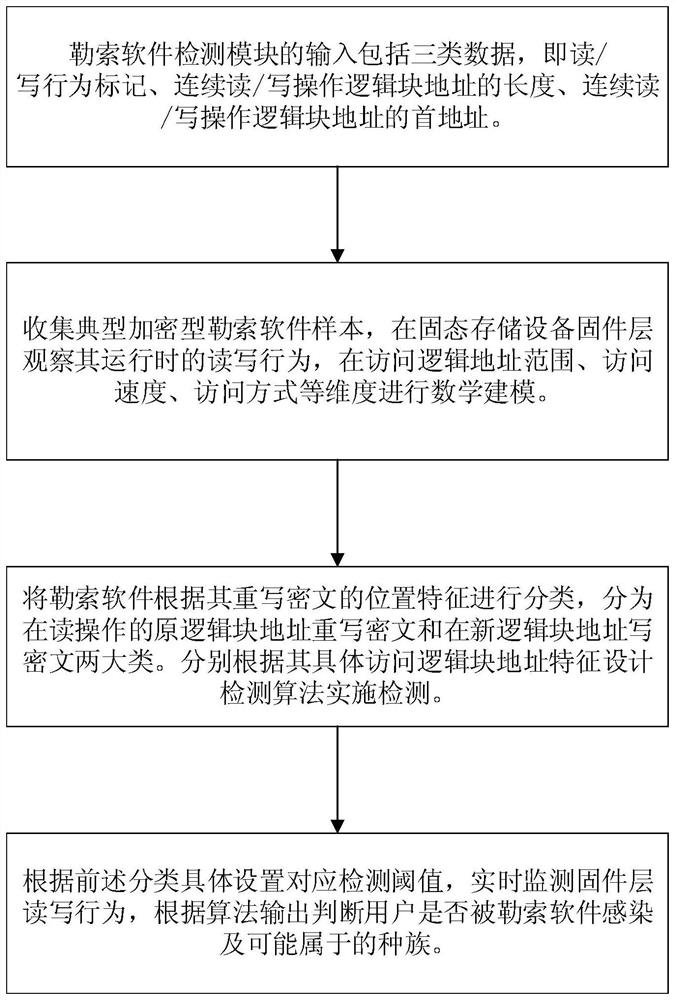
[0077] 1) Monitor the read and write behavior of ransomware in the flash conversion layer of the firmware of the solid-state storage device;
[0078] 2) According to the difference between the reading and writing behavior of ransomware and the data reading and writing behavior of normal user programs, a detection model based on the unique access mode of reading, writing and deleting data of ransomware is established;
[0079] 3) Use the established detection model to detect ransomware.
[0080] For the specific implementation process of the above steps, please refer to the content about ransomware detection in Embodiments 1 and 2.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com