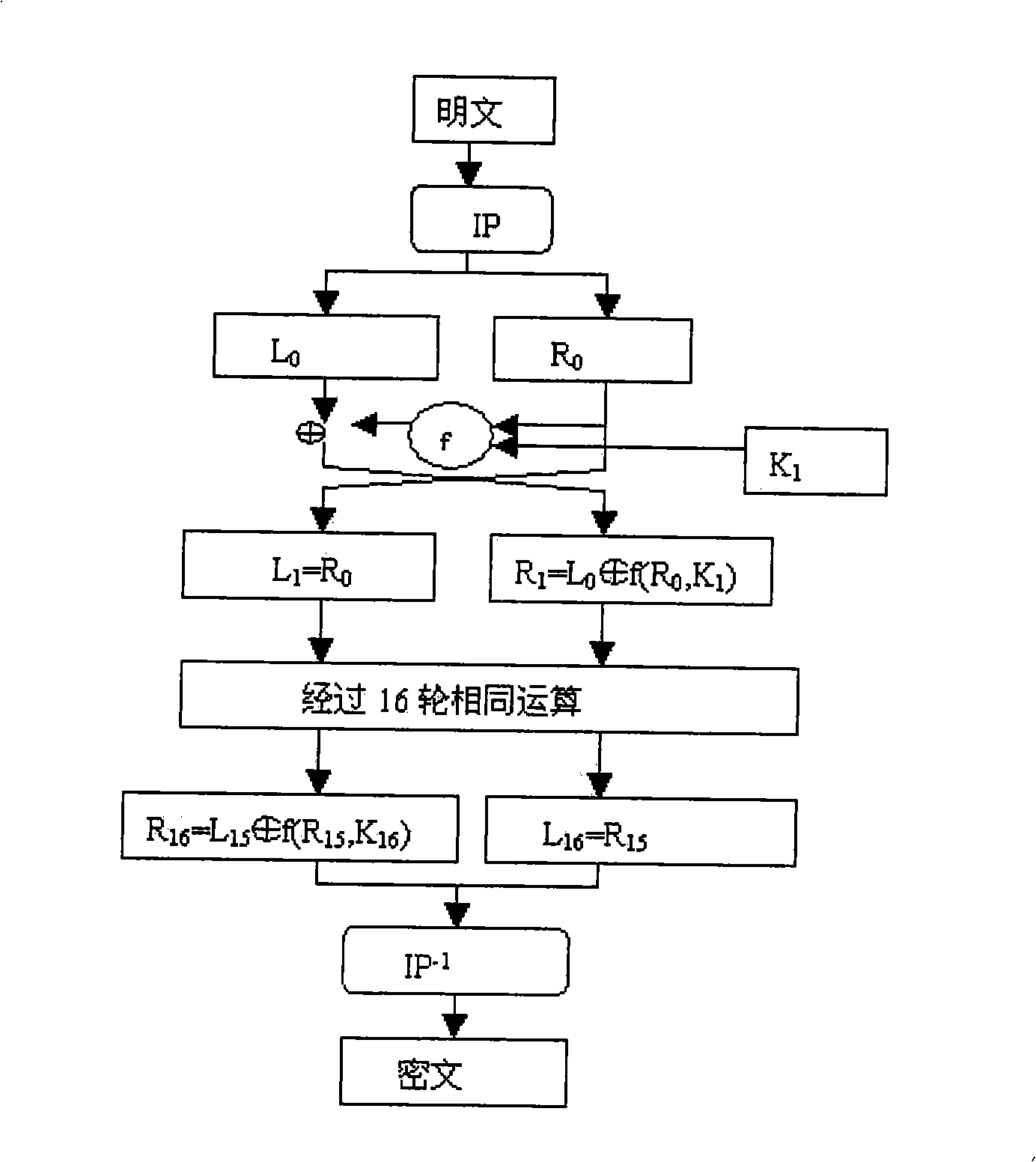
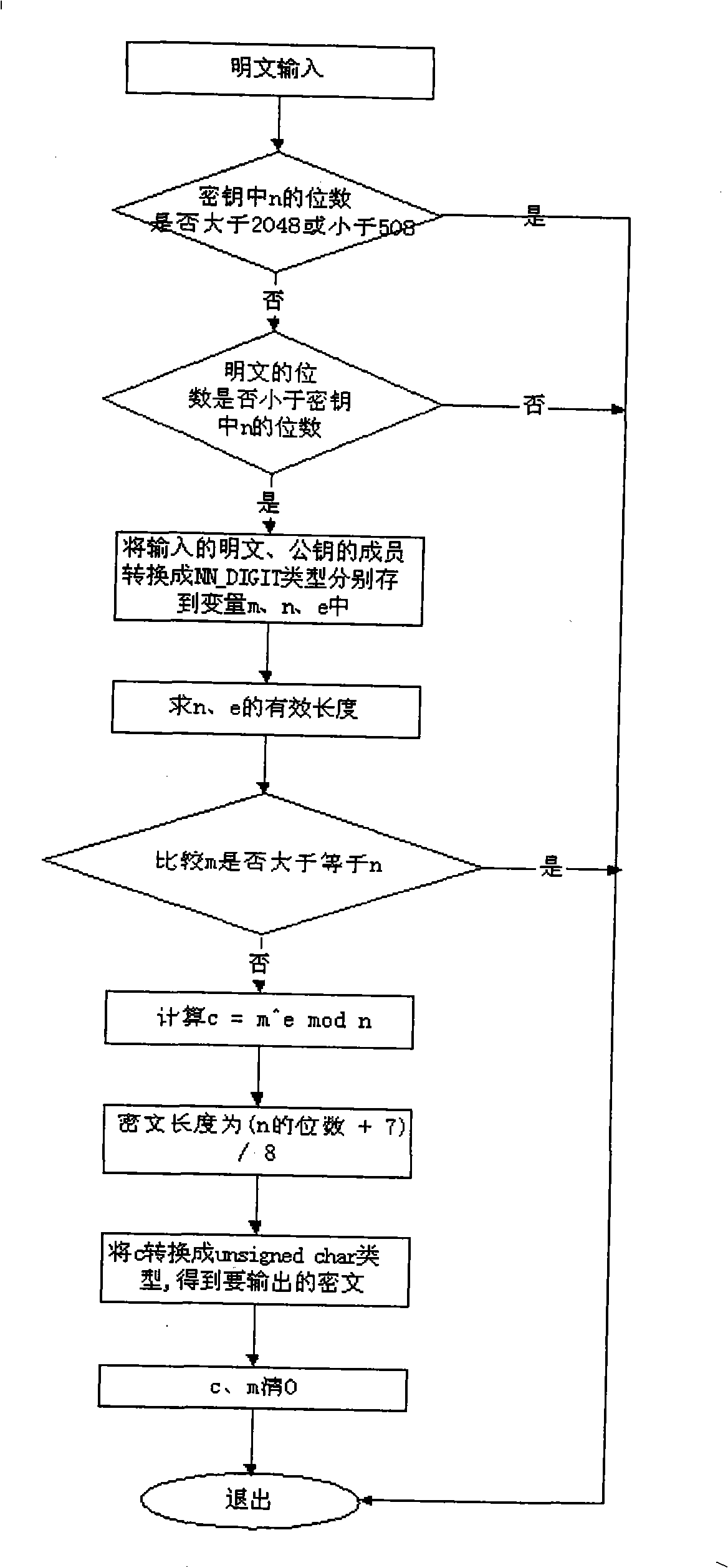
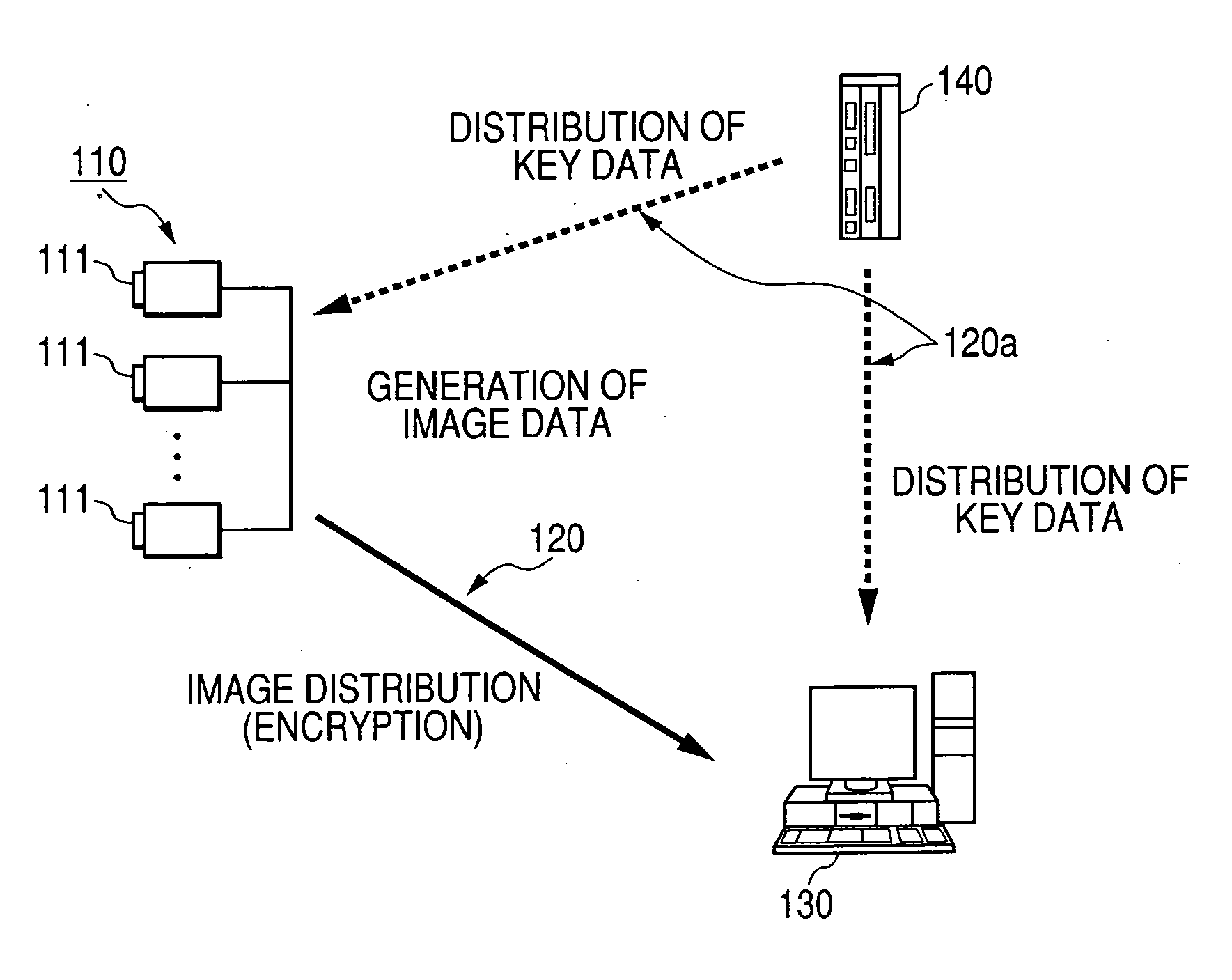
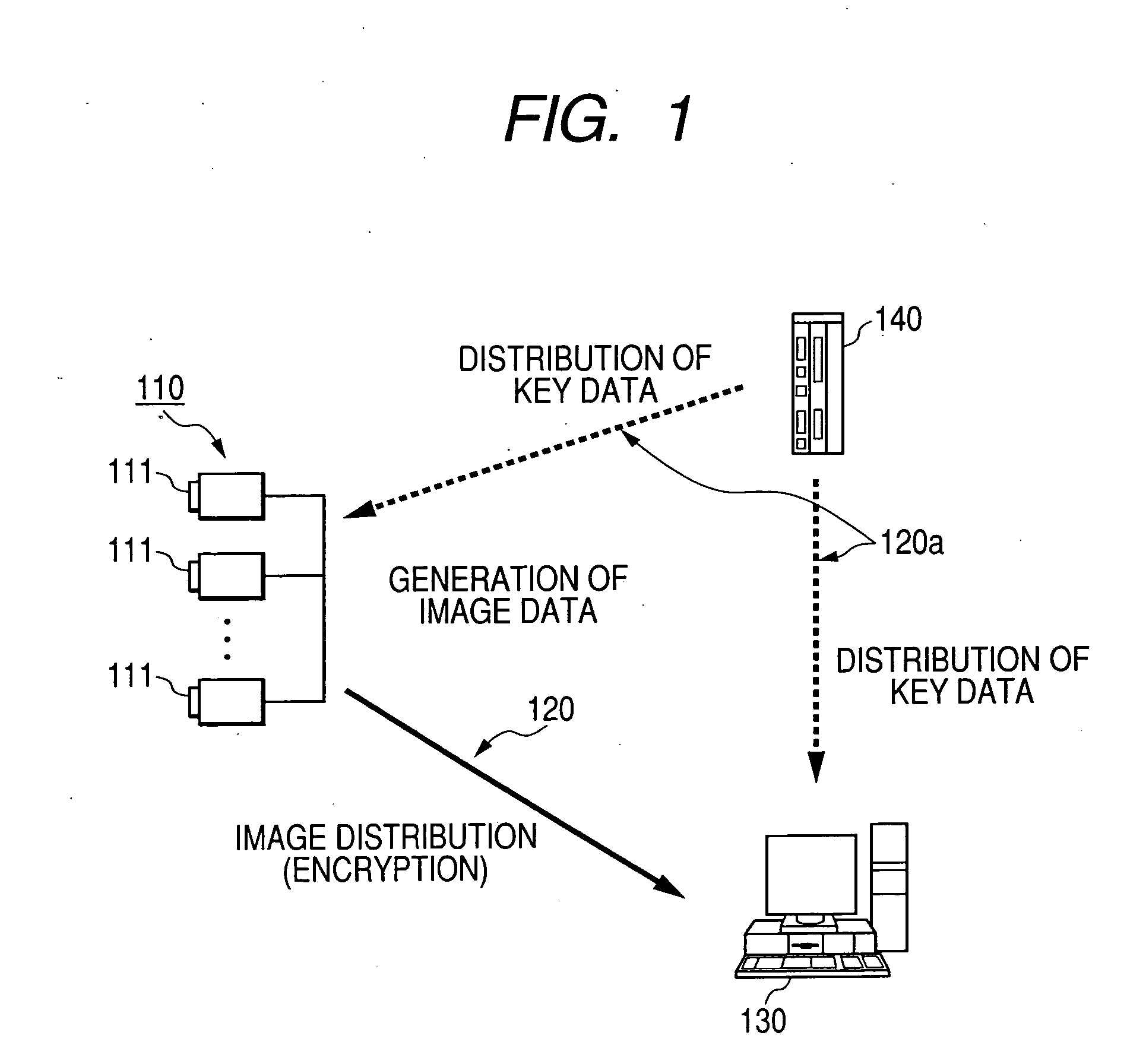
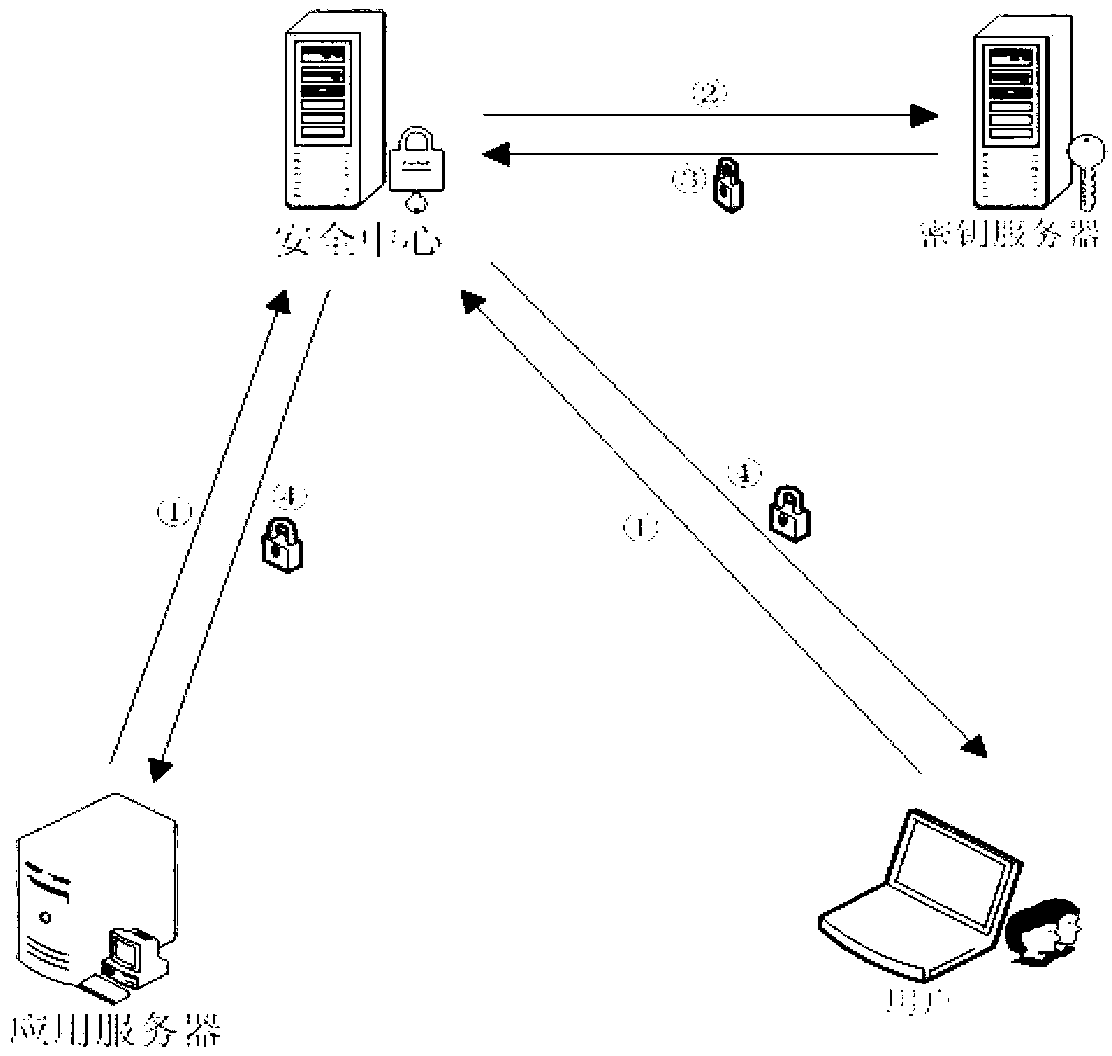
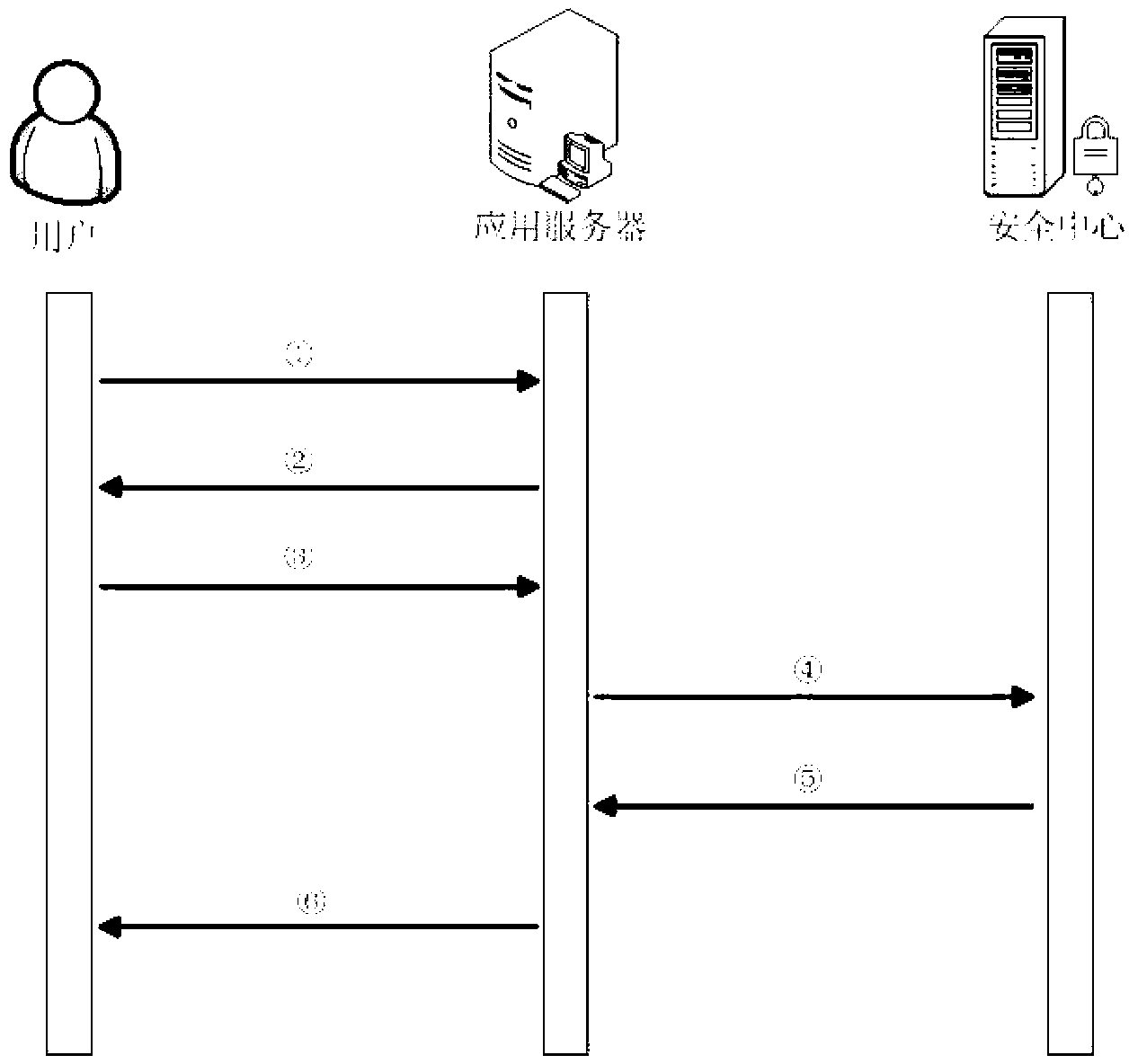
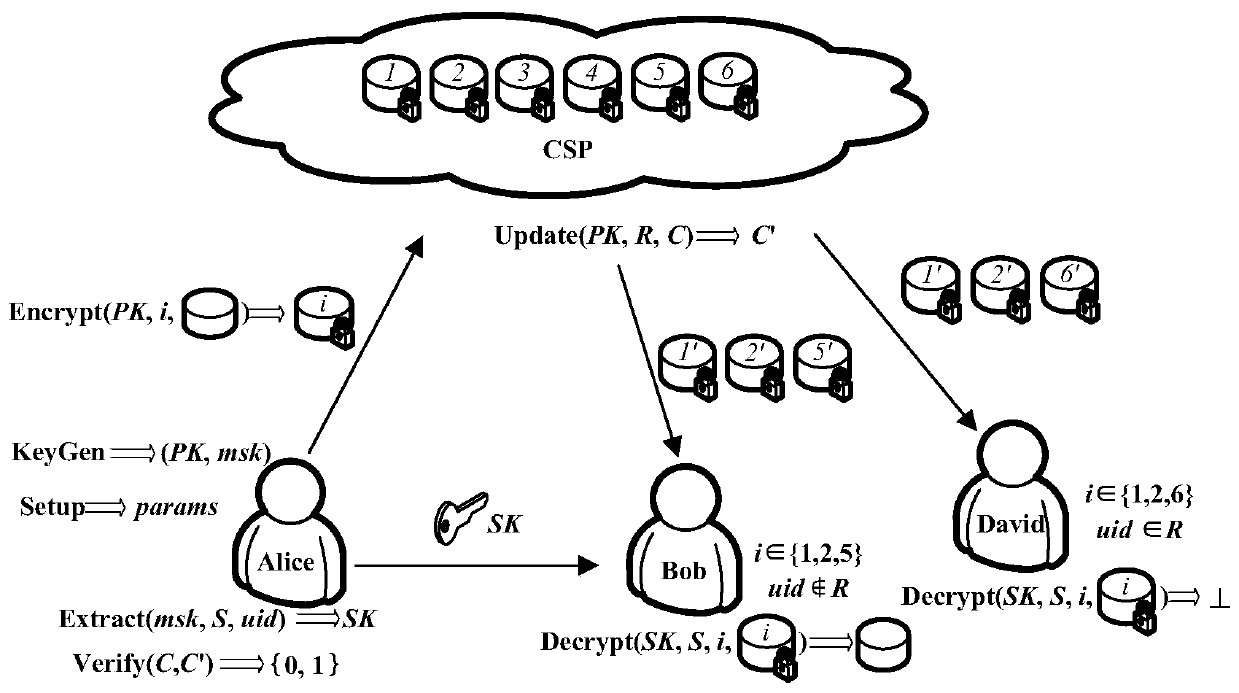
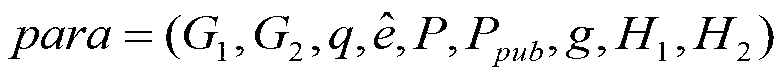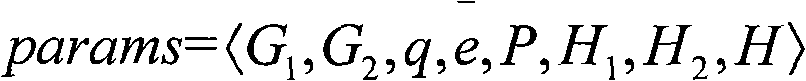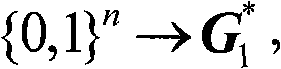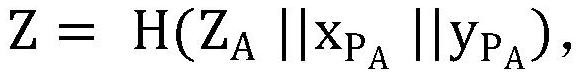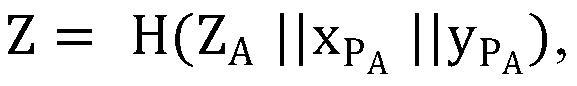Patents
Literature
36results about How to "Easy key management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
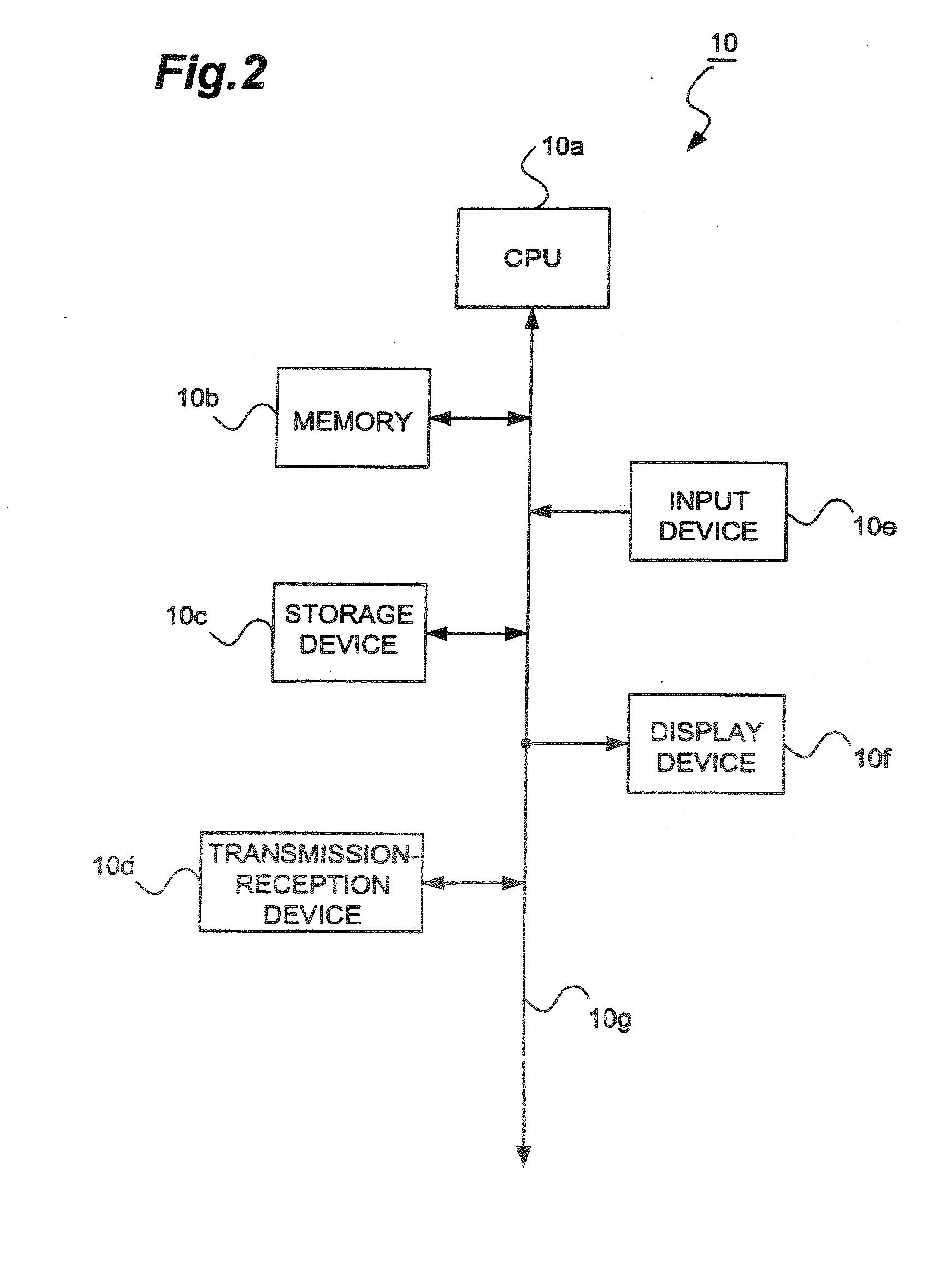
System for management of ubiquitously deployed intelligent locks
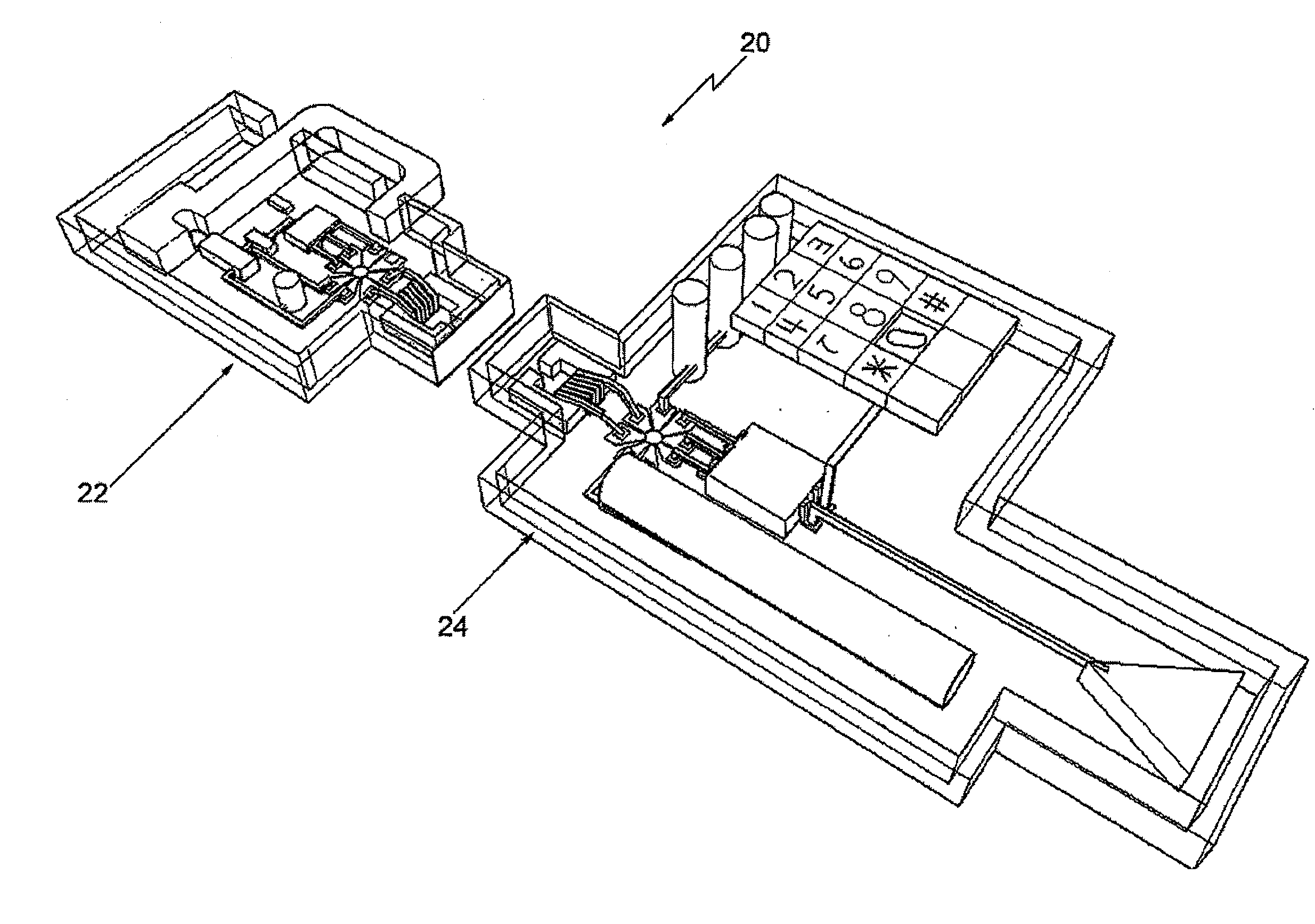
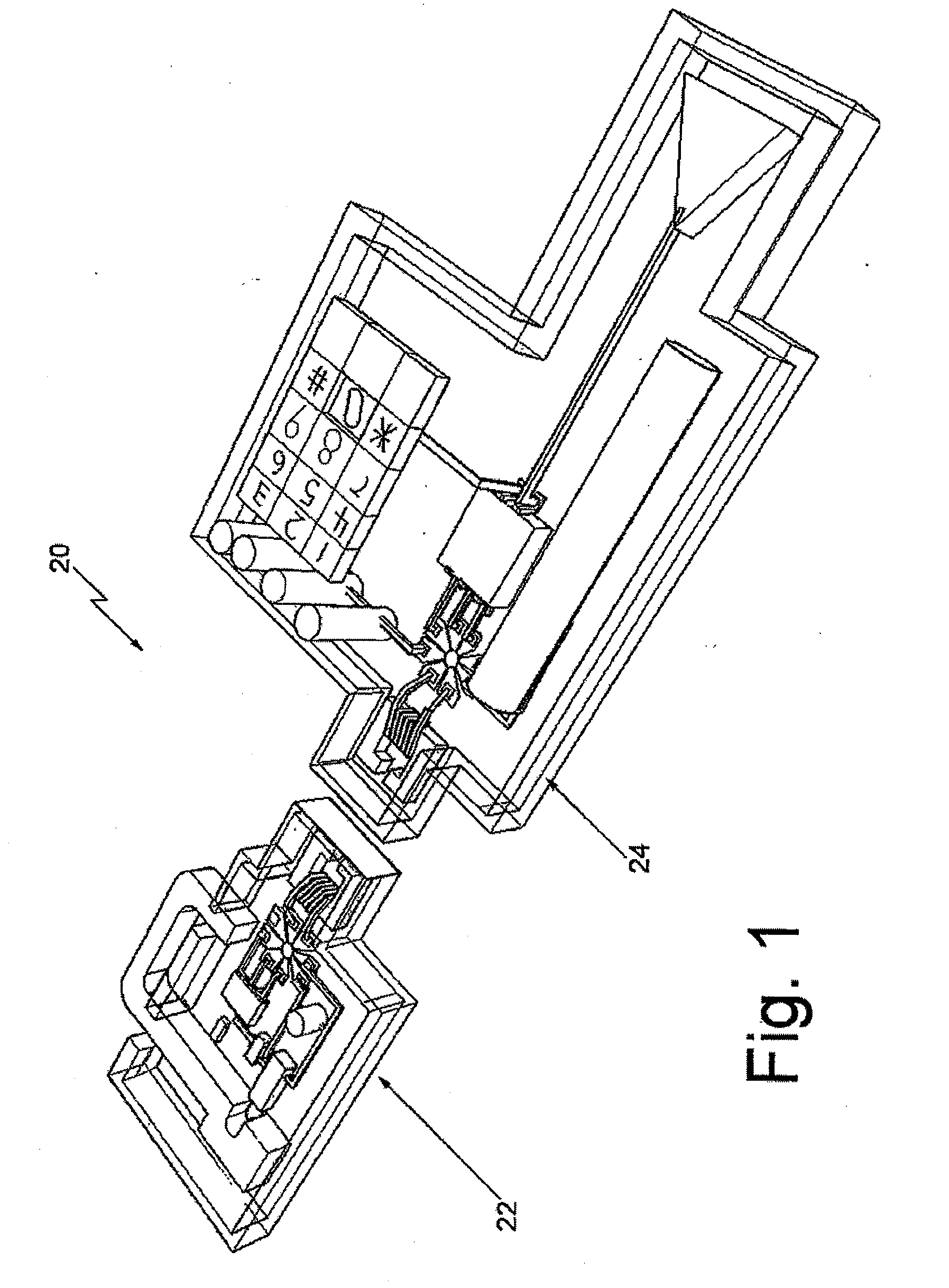
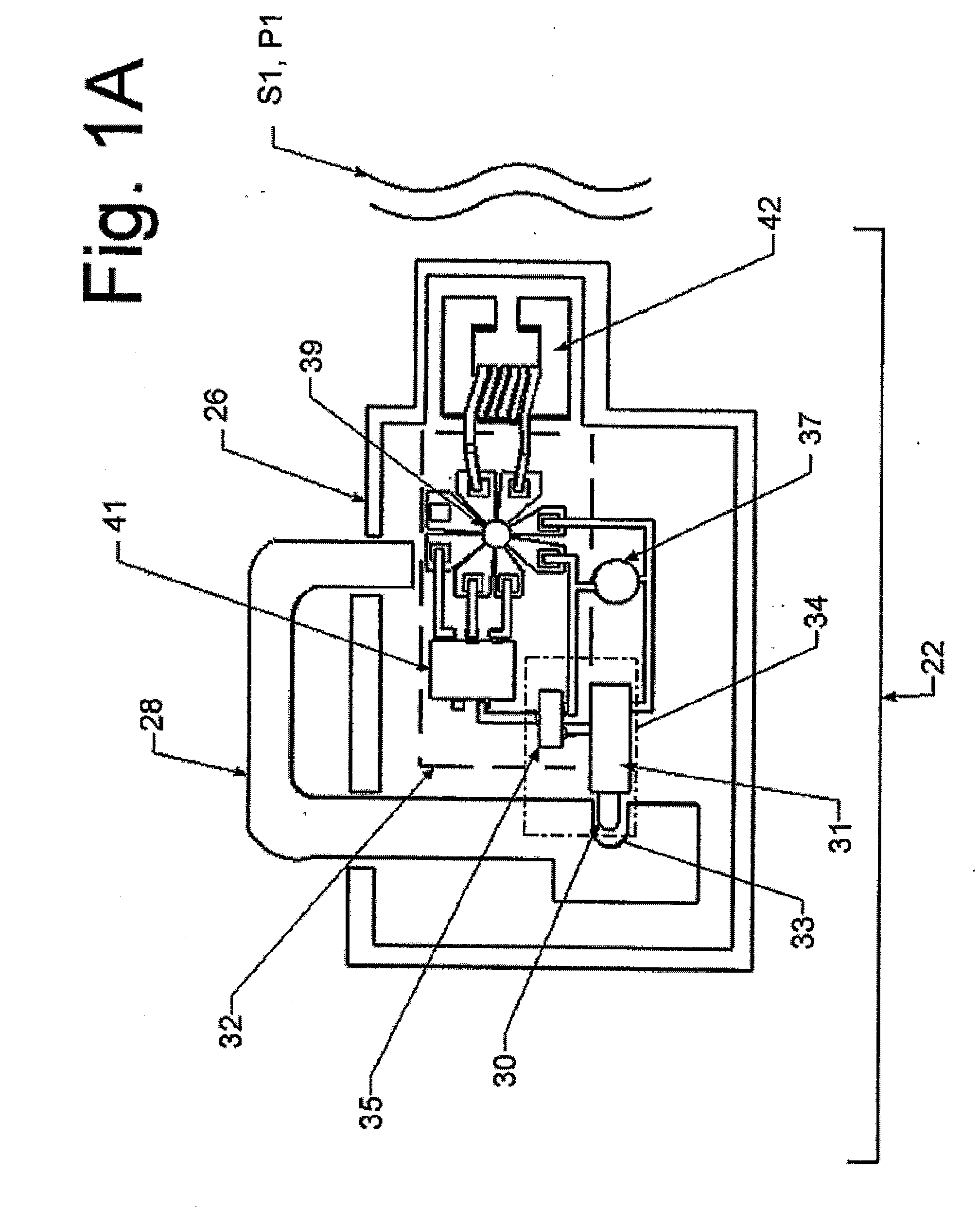
InactiveUS20070296545A1Easy key managementPromote exchangeElectric signal transmission systemsDigital data processing detailsEngineeringControl circuit
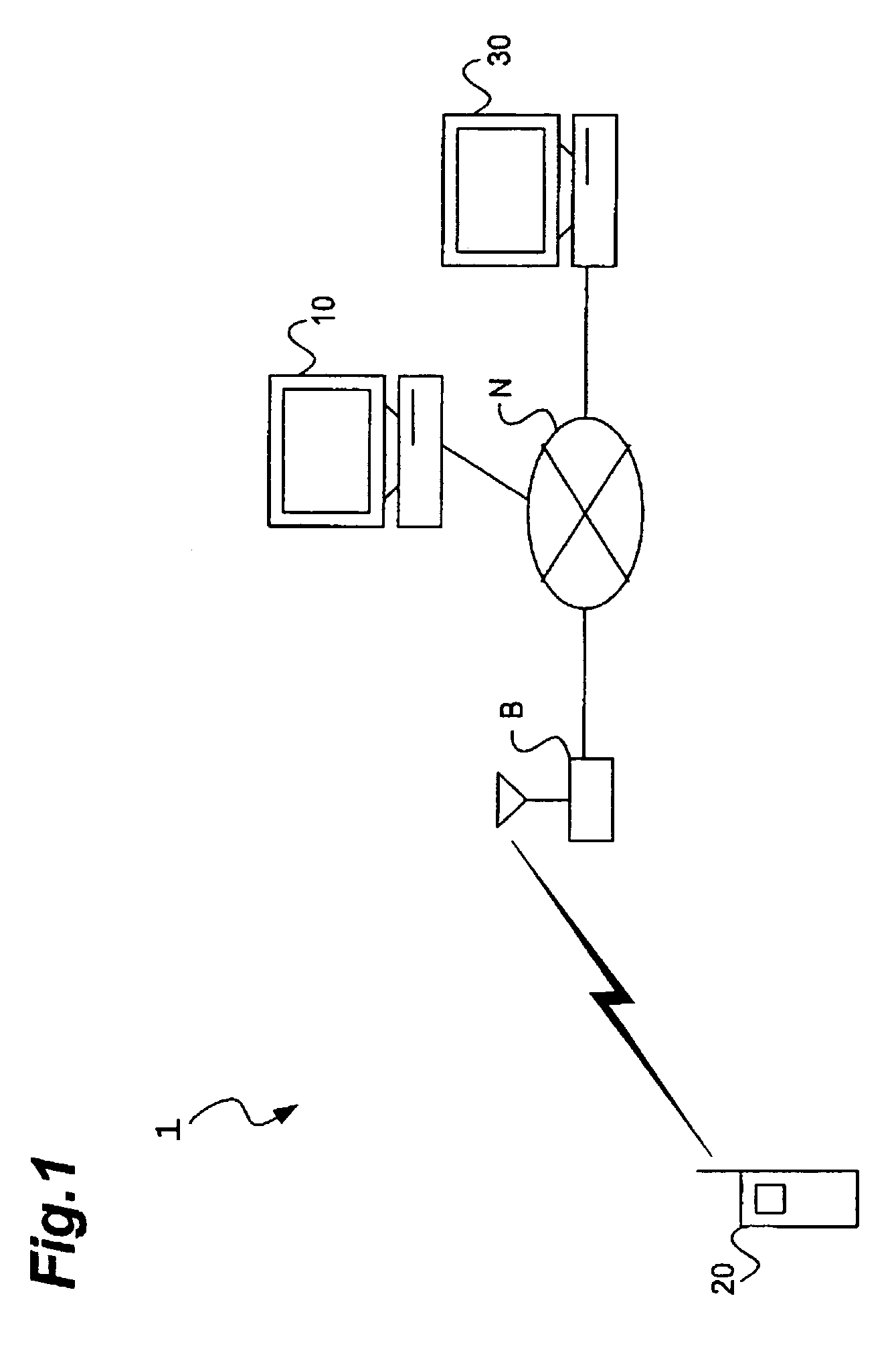
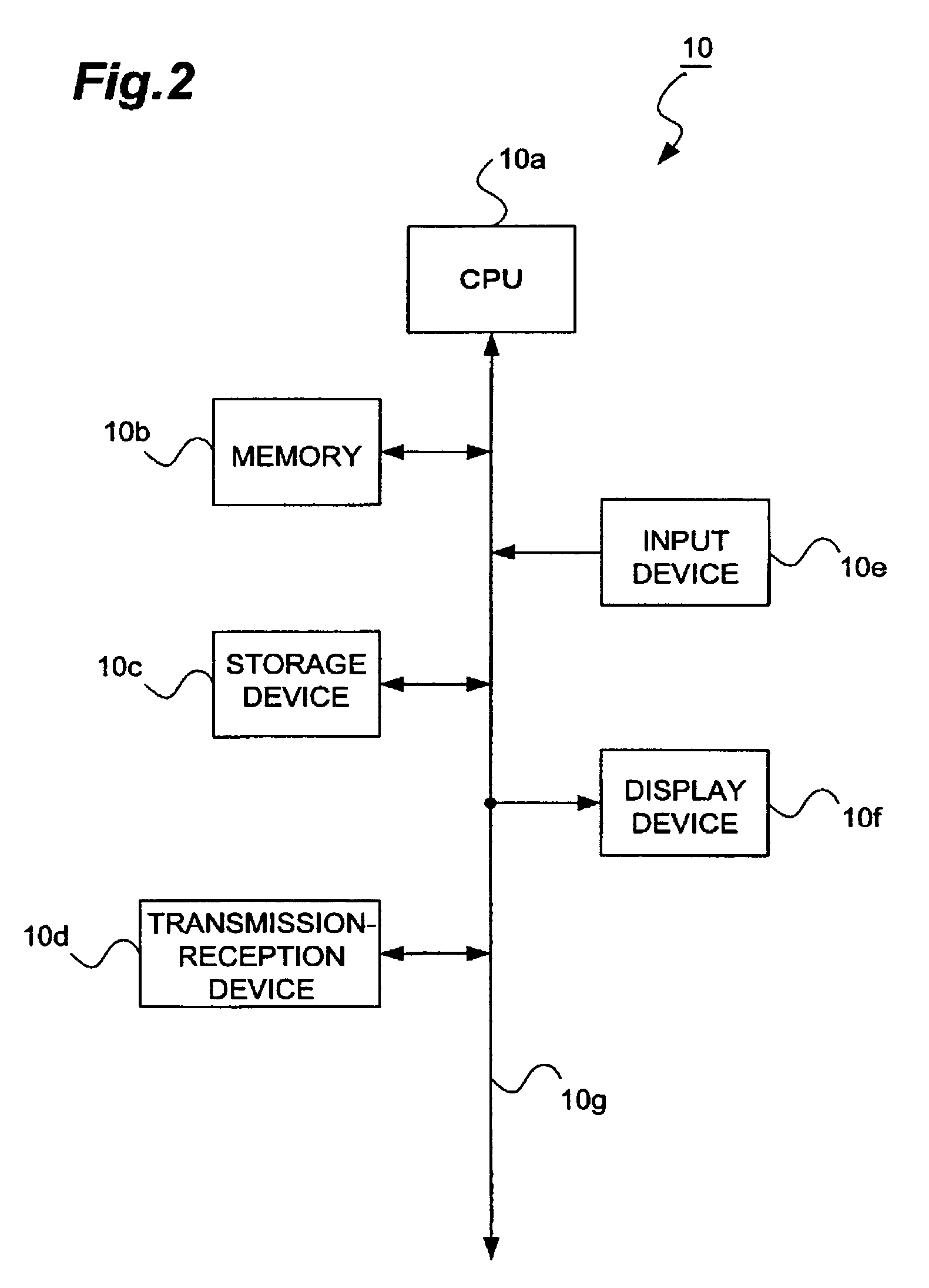
A lock system having a remote actuating key device, e.g., a portable member arranged to wirelessly transmit a wireless signal, and a passive lock device for receiving that signal. The lock device includes an actuatable trigger mechanism and a control circuit. The control circuit receives the wireless signal, which powers it. The control circuit also determines if the wireless signal is appropriate to unlock the lock, whereupon it produces a trigger signal. The trigger mechanism is responsive to the trigger signal to actuate and enable the lock device to be opened. The key device is also arranged to communicate via a wireless communications connection to a computer network. The communication with the computer network may carry commands and information. The key device may relay communications between the lock device and the computer network.
Owner:CHECKPOINT SYST INC
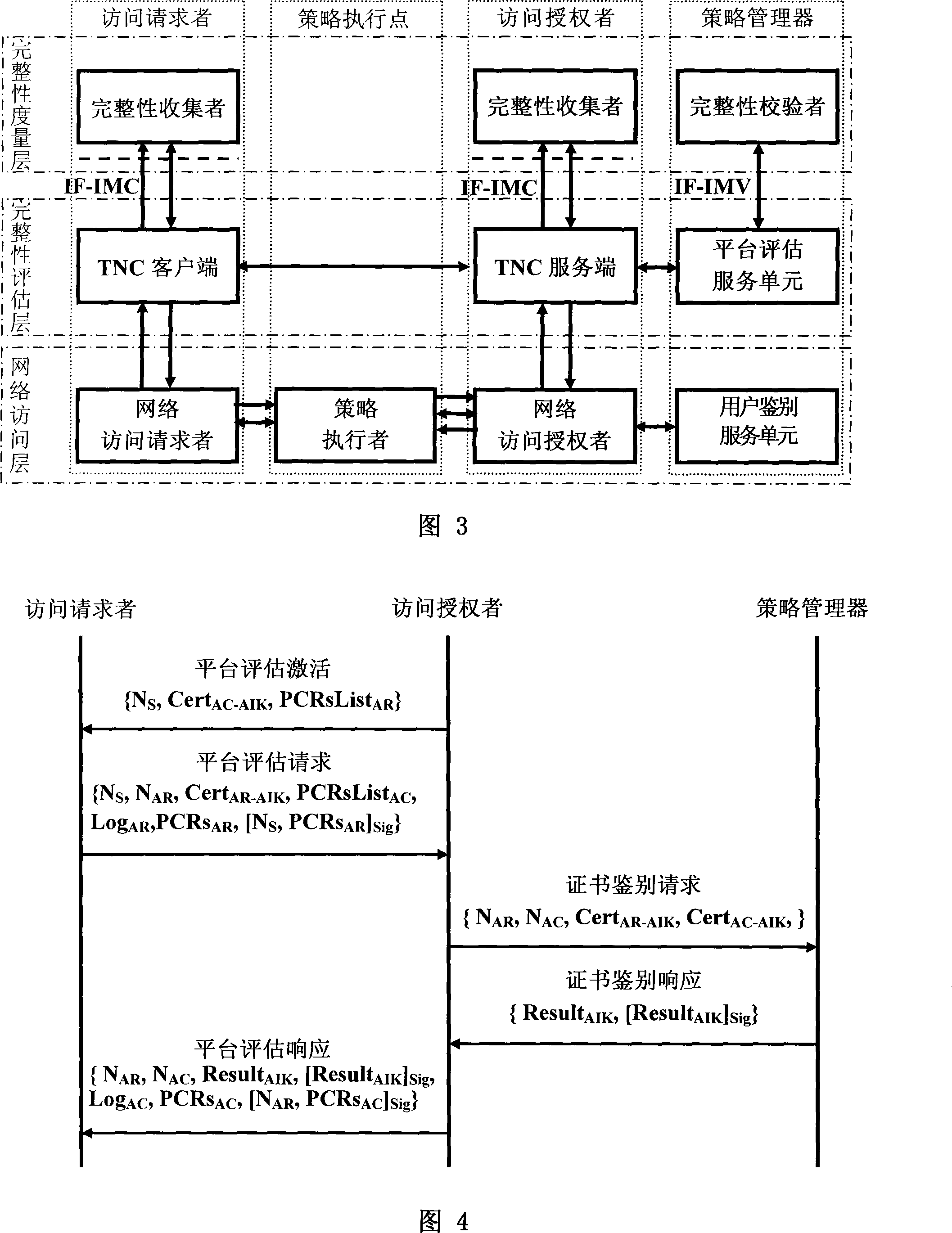
Reliable network access framework
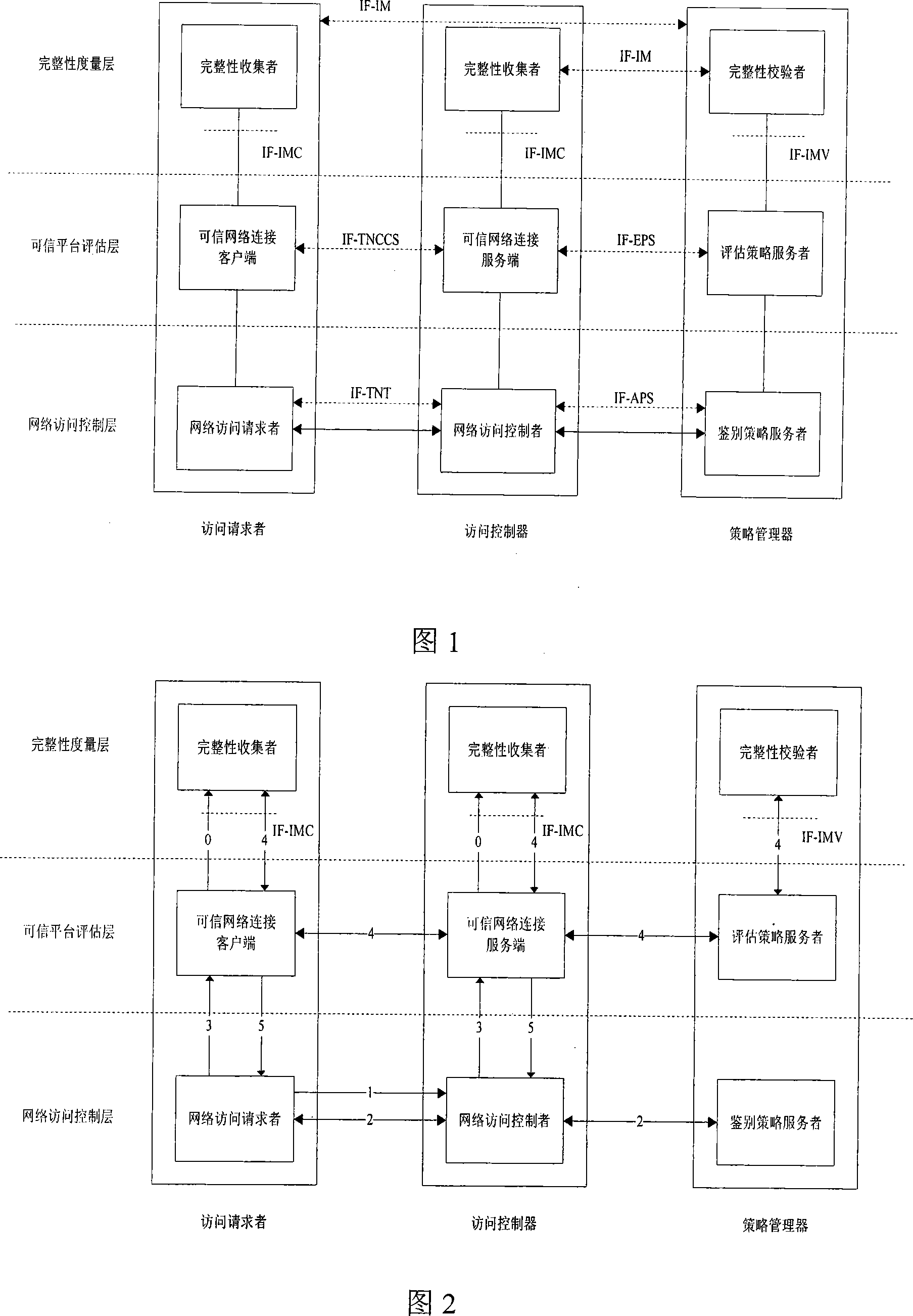
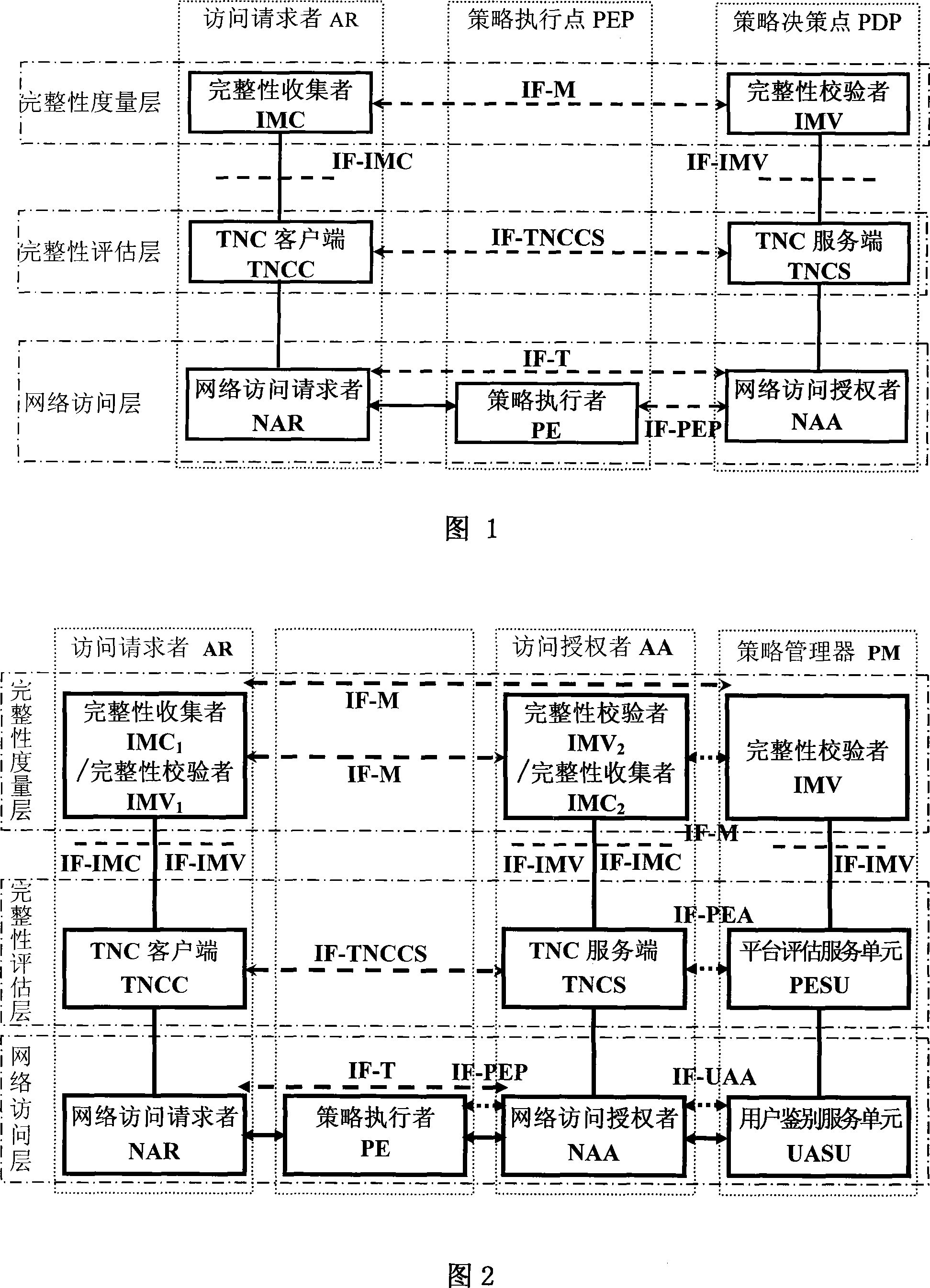
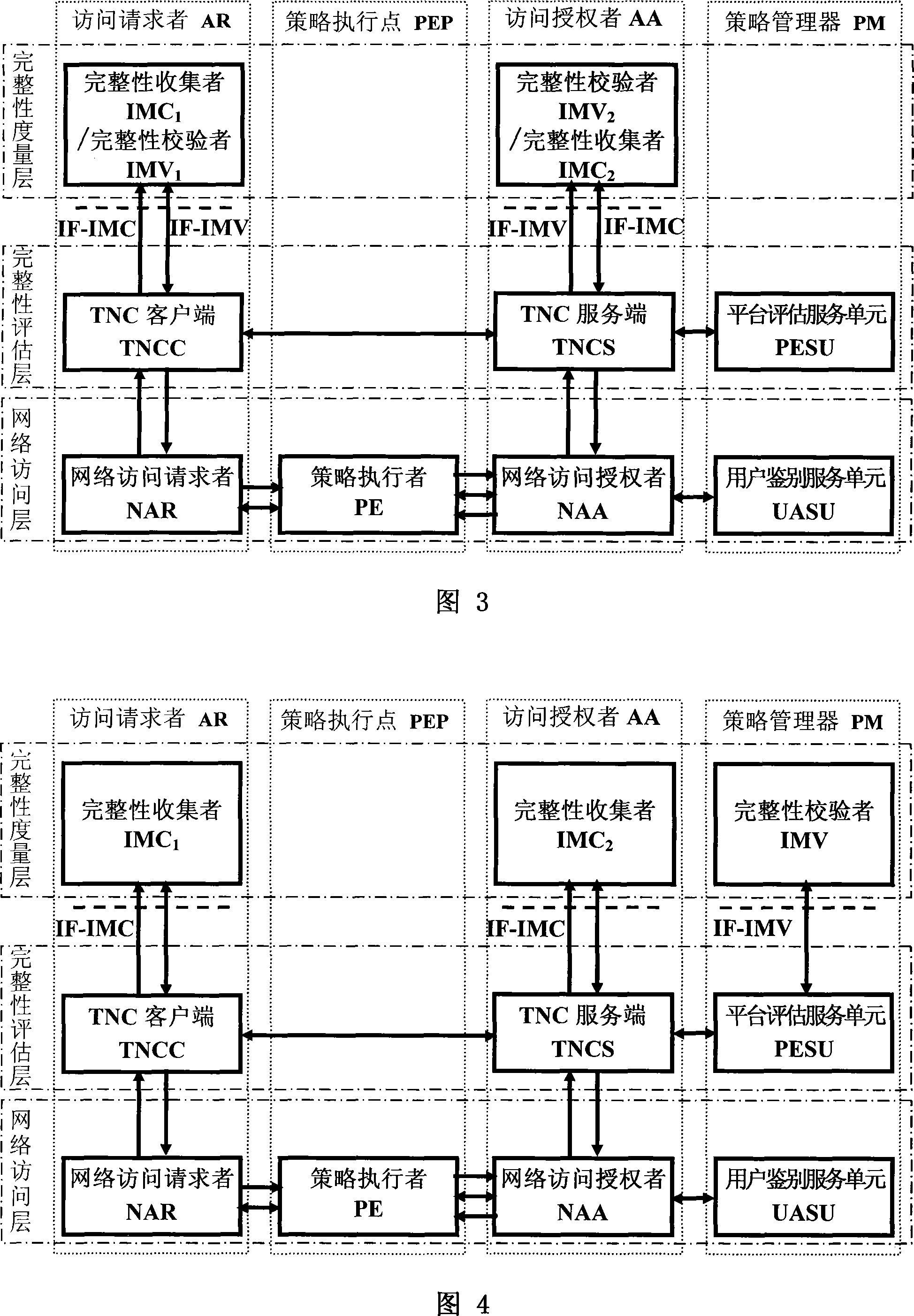
InactiveCN101136928AEasy to manage centrallyImprove distributionData switching by path configurationNetwork connectionsIntegrity assessmentExtensibility
Frame of the invention includes three entities: accessing requestor, accessing controller, and strategy manager. The strategy manager manages the accessing requestor and the accessing controller as well as implements bidirectional user ID authentication between them, and evaluates integrality of platform. Based on decision made from the strategy manager, the accessing requestor and the accessing controller control local ports. Before terminal is connected to network, trusty network connection architecture (TNCA) measures state of platform. Based on secure protocol of trusty third party, the invention implements the said authentication and evaluation of platform so as to guarantee security of TNCA. Introducing strategy manager simplifies key management of the architecture, raises extensibility of the architecture. Features are: higher security for evaluating integrality of platform, centralized verifying integrality, and higher universality.
Owner:BEIJING UNIV OF TECH
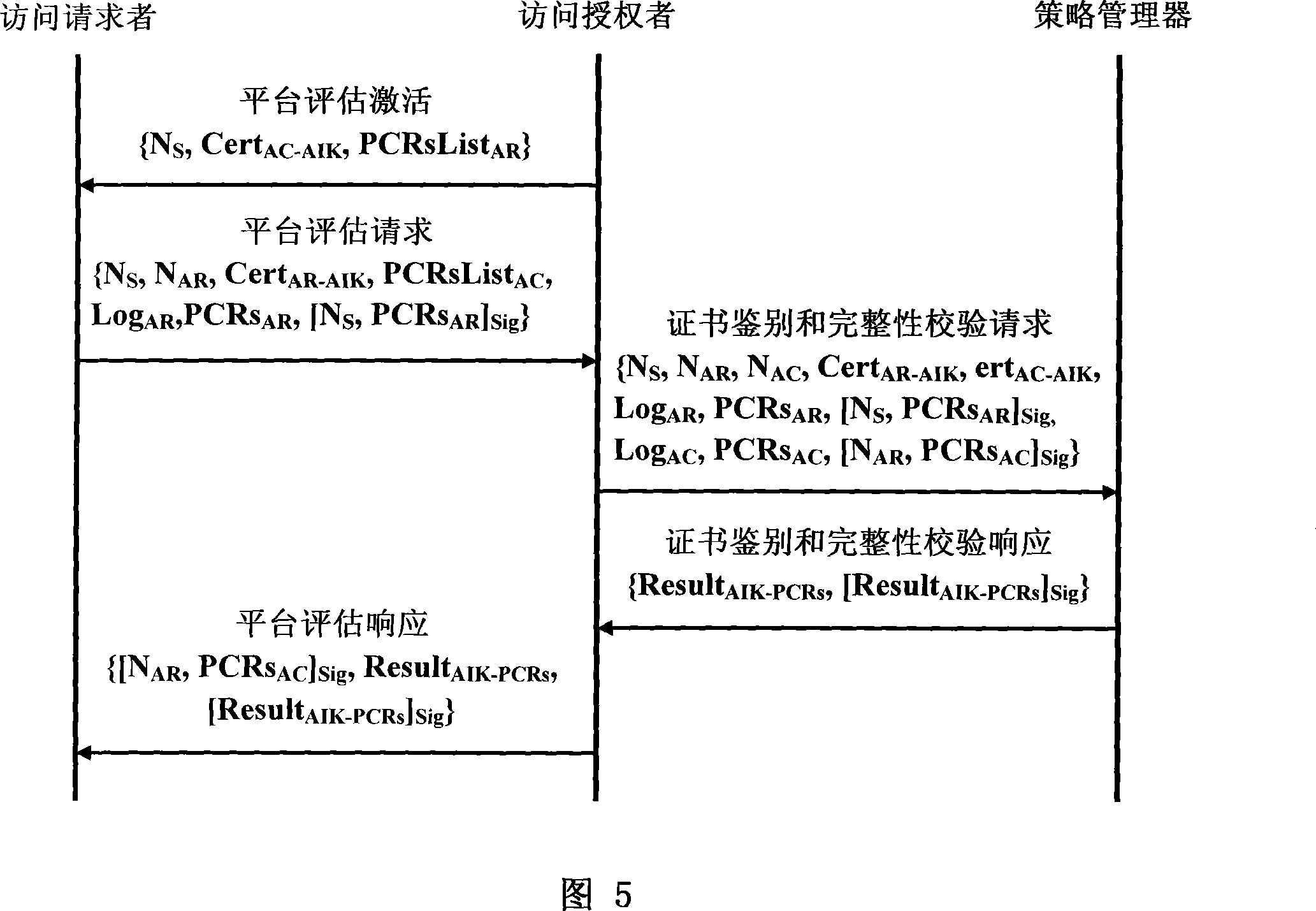
A trusted network connection method for enhancing security
ActiveCN101242267AImprove securityEasy to manageUser identity/authority verificationIntegrity assessmentNetwork connection
The invention provides a trusted network connection method for enhancing security, which pre-prepares a platform integrality information, prepares an integrality authentication request. A network access requester sends a access request to a network access controller, the network access controller starts a two-way authentication process of users, and user authentication service unit performs an equal authentication protocol. After the two-way user authentication is success, a TNC client-side and a TNC service side execute a platform integrality evaluate. The network access requester and network access authorizer achieve an inter access control between the access requester and a access authorizer based on a recommended control terminal respectively. The invention solves the technical problems in background technology that the security is low, the access requester may not validate validity of AIK certificate and the platform integrality evaluate is unequal. The invention simplifies the key management and integrality authentication mechanism, expands the range of applicability of trusted network connection.
Owner:CHINA IWNCOMM
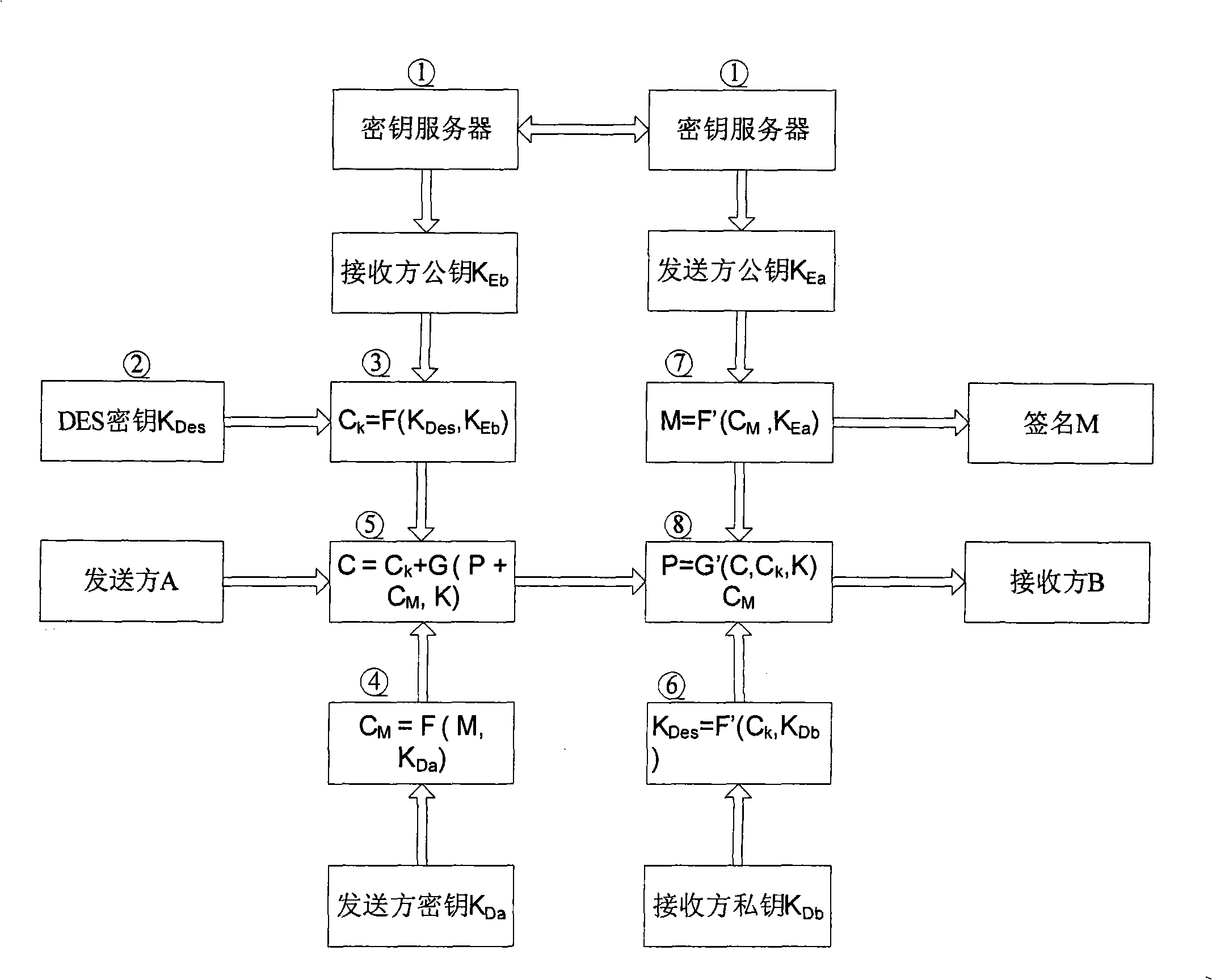
A mixed encryption method in session system
InactiveCN101262341AHigh speedEasy key managementPublic key for secure communicationUser identity/authority verificationComputer hardwareCommunications system
A mixed encryption scheme for a conference system is provided. The encrypting algorithm is that: before data communication, a message clear text is encrypted by using a DES method, and then the DES key is encrypted adopting an RSA method, so as to realize digital signature. By comprehensively using the existing encrypting algorithms DES and RSA, the strong points of which are utilized and the weak points are avoided. As the processing for main data adopts the DES encrypting algorithm, grouping processing for each datum can be completed in a very short time thanks to the fast speed of the DES encrypting algorithm; besides, the DES key encrypted by adopting the RSA algorithm can be publicized; therefore, the overall security system only requires few RSA decryption key. The mixed encryption scheme provided by the invention can not only give full play to the advantage of fast encrypting speed of the DES encrypting algorithm, but also give full play to the advantage of convenient management of the RSA algorithm; therefore, the mixed encryption scheme provided by the invention has the advantages of simple theory, fast speed and being easy to be realized; when being used in an instant communication system, the mixed encryption scheme can meet the requirement for real time and security of a conference system.
Owner:BEIHANG UNIV
Data encryption/decryption method and monitoring system
InactiveUS20060191009A1Improve securityEasy key managementKey distribution for secure communicationMemory loss protectionMonitoring systemContinuous data
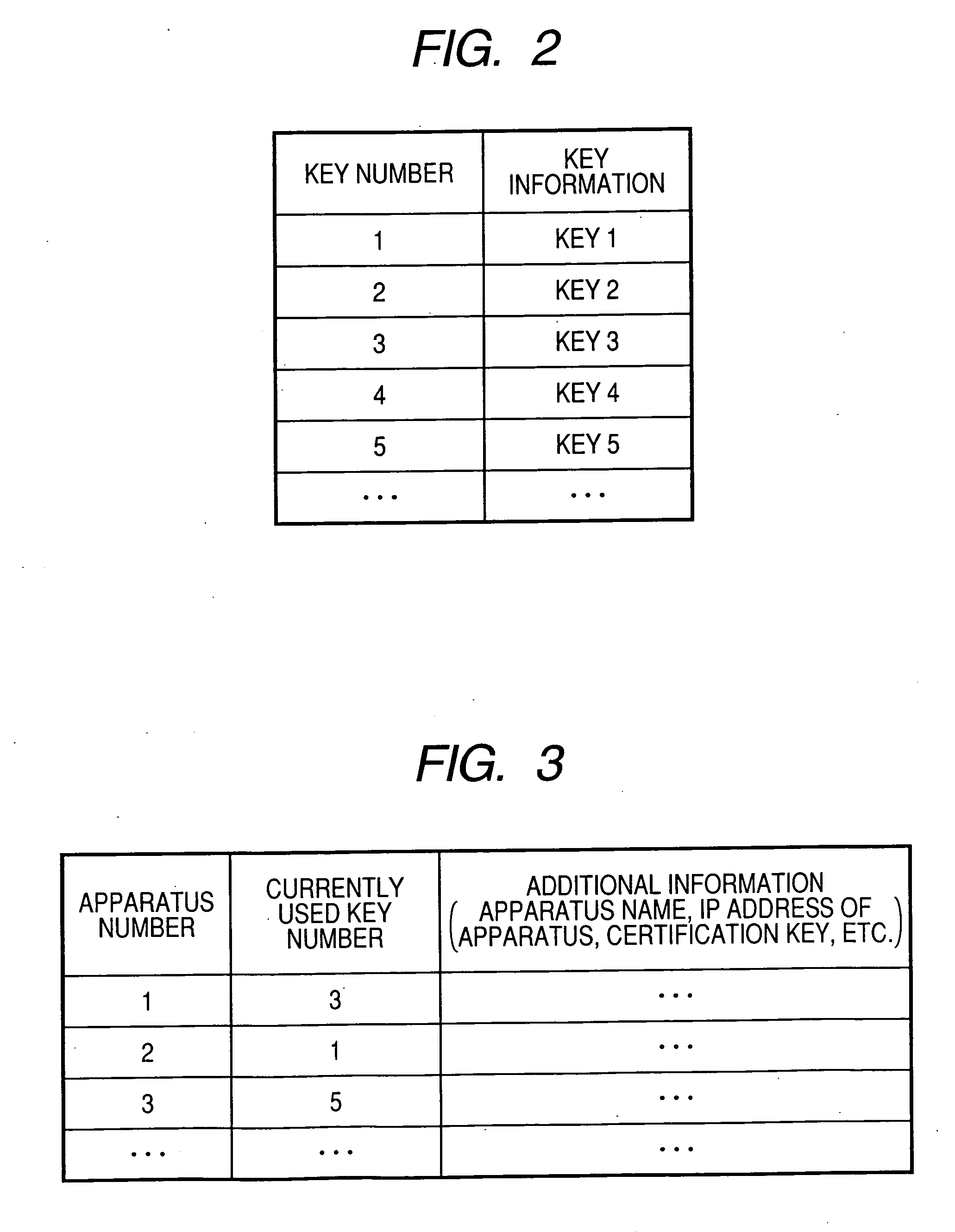
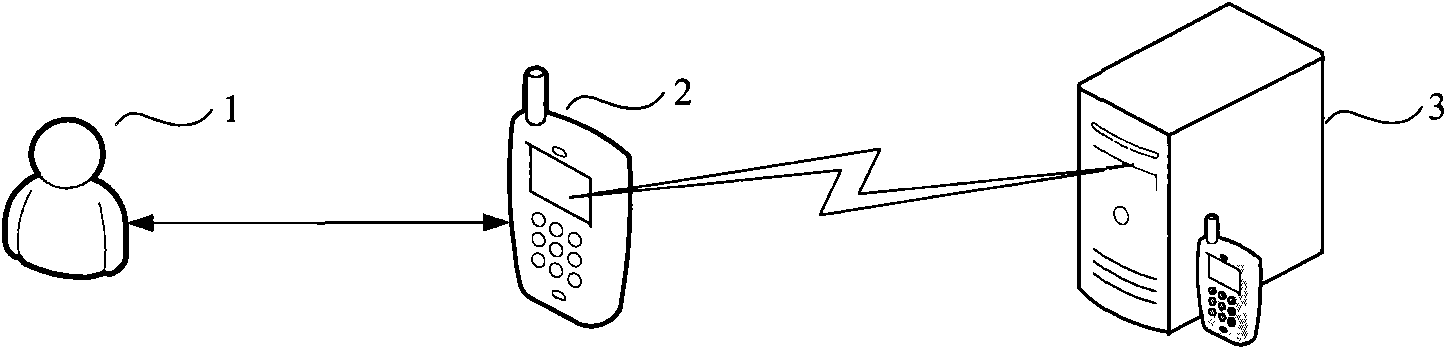
A monitoring system has a distribution apparatus which encrypts continuous data and distributes the encrypted continuous data via a network, a reproduction apparatus which decrypts the encrypted data distributed via the network to reproduce the continuous data, and a key management apparatus which has a key management database. The distribution apparatus obtains a key number correlated with the distribution apparatus and key information correlated with the key number from the key management apparatus, encrypts data with using the obtained key information, and distributes the encrypted data with the obtained key number. The reproduction apparatus transmits the key number appended to the encrypted data to the key management apparatus, obtains key information correlated with the transmitted key number, and decrypts the encrypted data with using the obtained key information.
Owner:YOKOGAWA ELECTRIC CORP
Mobile commerce identity authentication method
InactiveCN101969446AEliminate inconvenienceMeet the inconvenienceUser identity/authority verificationInternet Authentication ServiceThird party
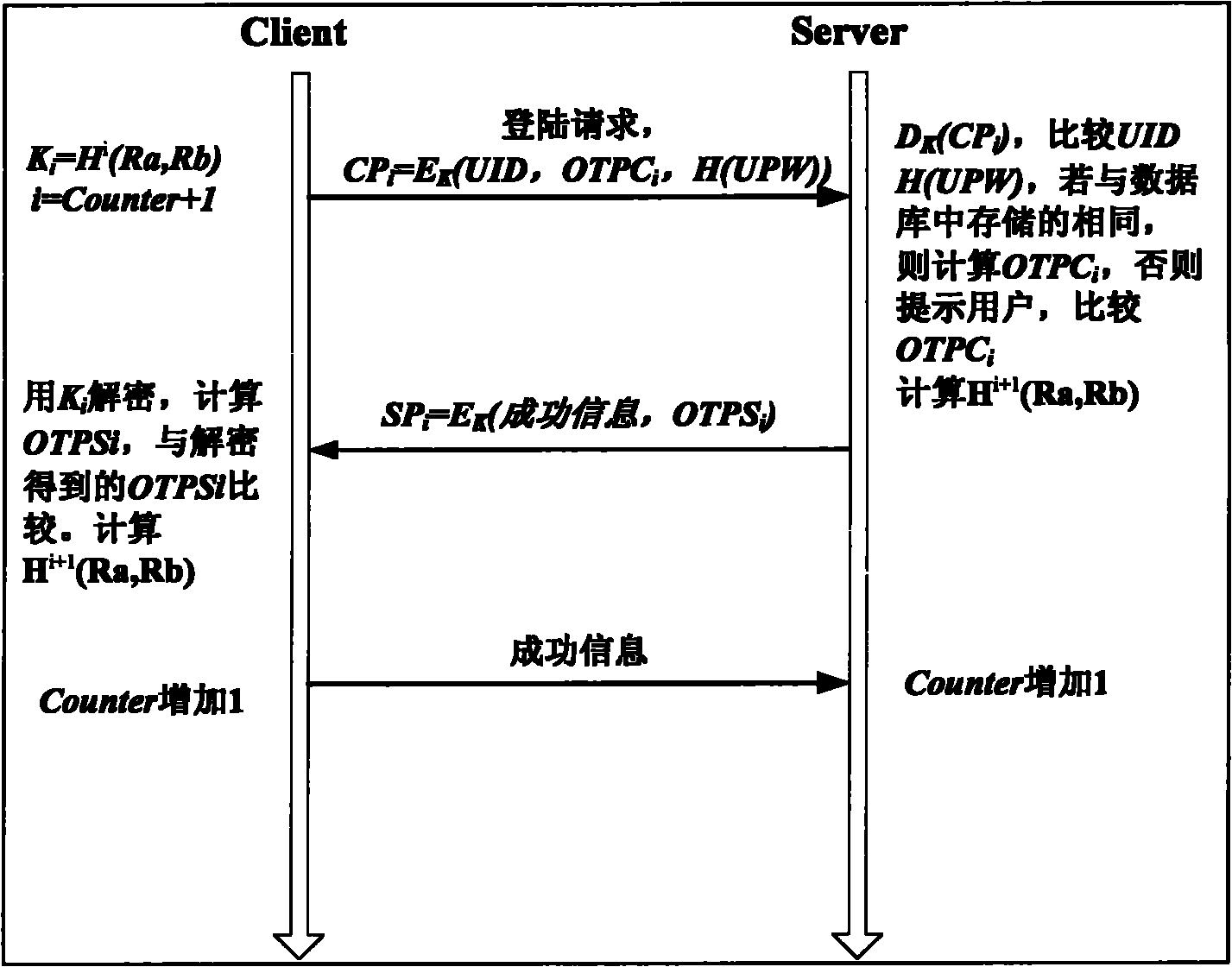
The invention provides a mobile commerce identity authentication method. In the method, key negotiation is realized by the most efficient elliptic curve-based public key cryptosystem in public key cryptosystems. An elliptic curve algorithm has the characteristics of low calculated amount and high safety, so the elliptic curve algorithm is used for generating a public key and a private key, and a public key cryptosystem without a third-party is realized and applied to the two-way authentication service of a client and a server.
Owner:BEIJING JIAOTONG UNIV
Identity-based key generation method and identity-based authentication method
InactiveCN103248488AGuaranteed privacyEnsure safetyUser identity/authority verificationPublic key certificateSecure authentication
The invention relates to an identity-based key generation method and an identity-based authentication method, and belongs to the technical field of communication and information security. According to the invention, based on the identity cryptographic technique, authentication and authorization to a subjective identity are realized; privacy and security of a legitimate user are ensured; the management of a key is simple; a systematical key management center is only responsible for establishing and distributing a private key for each user, and well manages a main key of a security center and a group of communal parameter files; an identity is used as a mark for realizing authentication; secure authentication can be realized only needing knowing identity marks of others, without needing exchange of public key certificates, validity verification and other related processes; and the whole process is simple and quick.
Owner:顾纯祥
Access authentication method, equipment and system of P2P (peer-to-peer) network
InactiveCN101815294ASimple access authentication workEasy encryption and decryptionNetwork topologiesTransmissionNetwork communicationPeer-to-peer
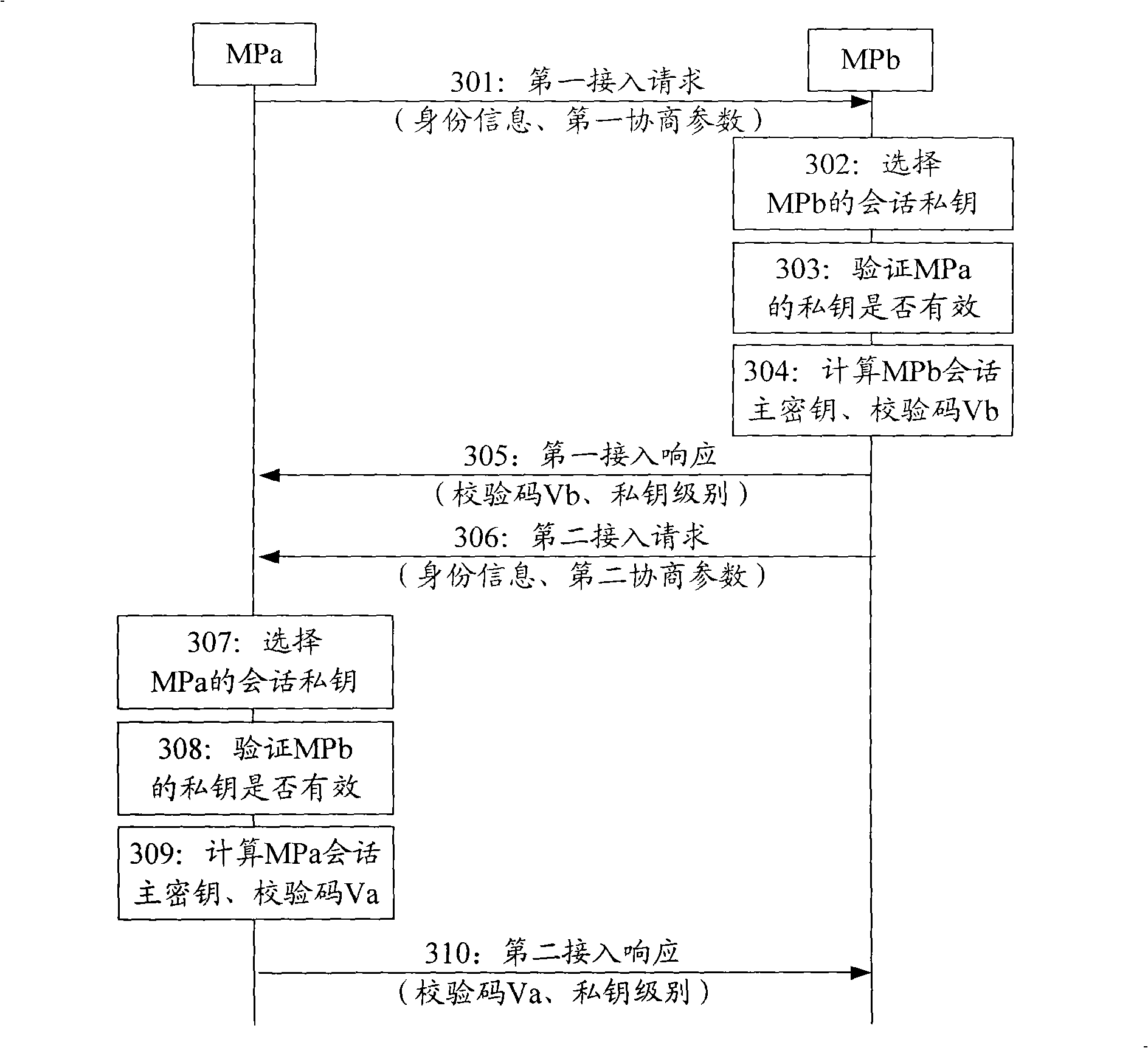
The invention discloses access authentication method, equipment and system of a P2P (peer-to-peer) network, belonging to the technical field of network communication. Network equipment in the P2P network is subjected to access authentication by adopting an identity-based public key IBC (Information Bearer Channel) mechanism. The method comprises the following steps of: receiving an access requesttransmitted by opposite terminal network equipment by home terminal network equipment; selecting a private key from the private keys of the home terminal network equipment as a conversation private key of the home terminal network equipment according to the private key level of the home terminal network equipment and the private key level of the opposite terminal network equipment; calculating a conversation main key of the home terminal network equipment according to the conversation private key of the home terminal network equipment, the identity information of the opposite terminal networkequipment corresponding to the conversation private key of the home terminal network equipment, a first negotiation parameter and a second random number determined by the home terminal network equipment; and returning an access response to the opposite terminal network equipment. By utilizing the IBC mechanism, distributed access authentication under the P2P network mode is solved, thus the IBC mechanism is particularly suitable for the P2P network.
Owner:HUAWEI TECH CO LTD
Key distribution method applicable to VOIP voice encryption
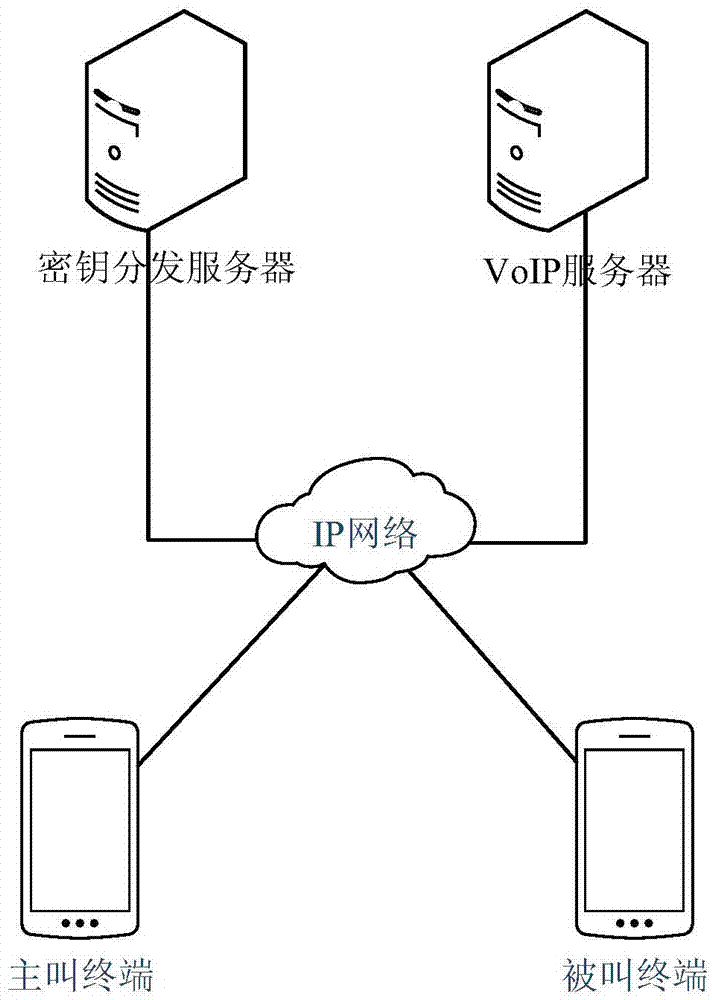
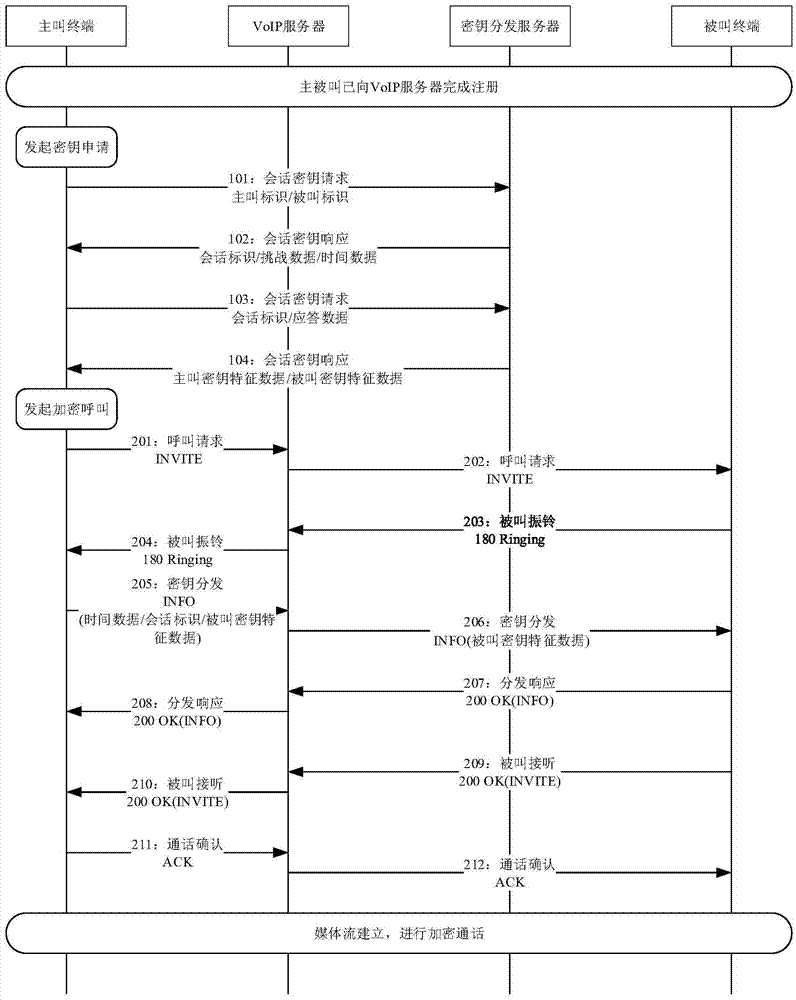
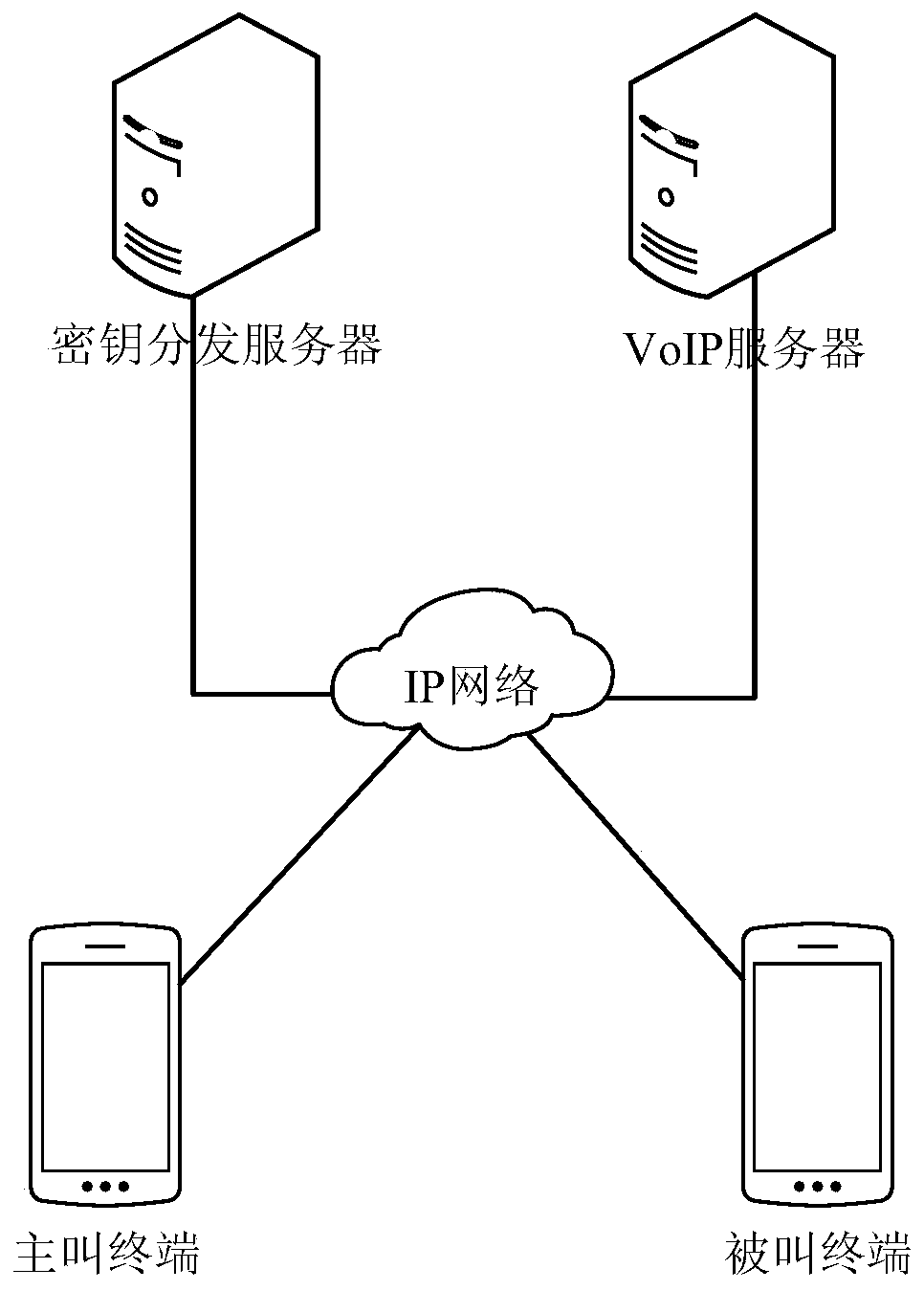
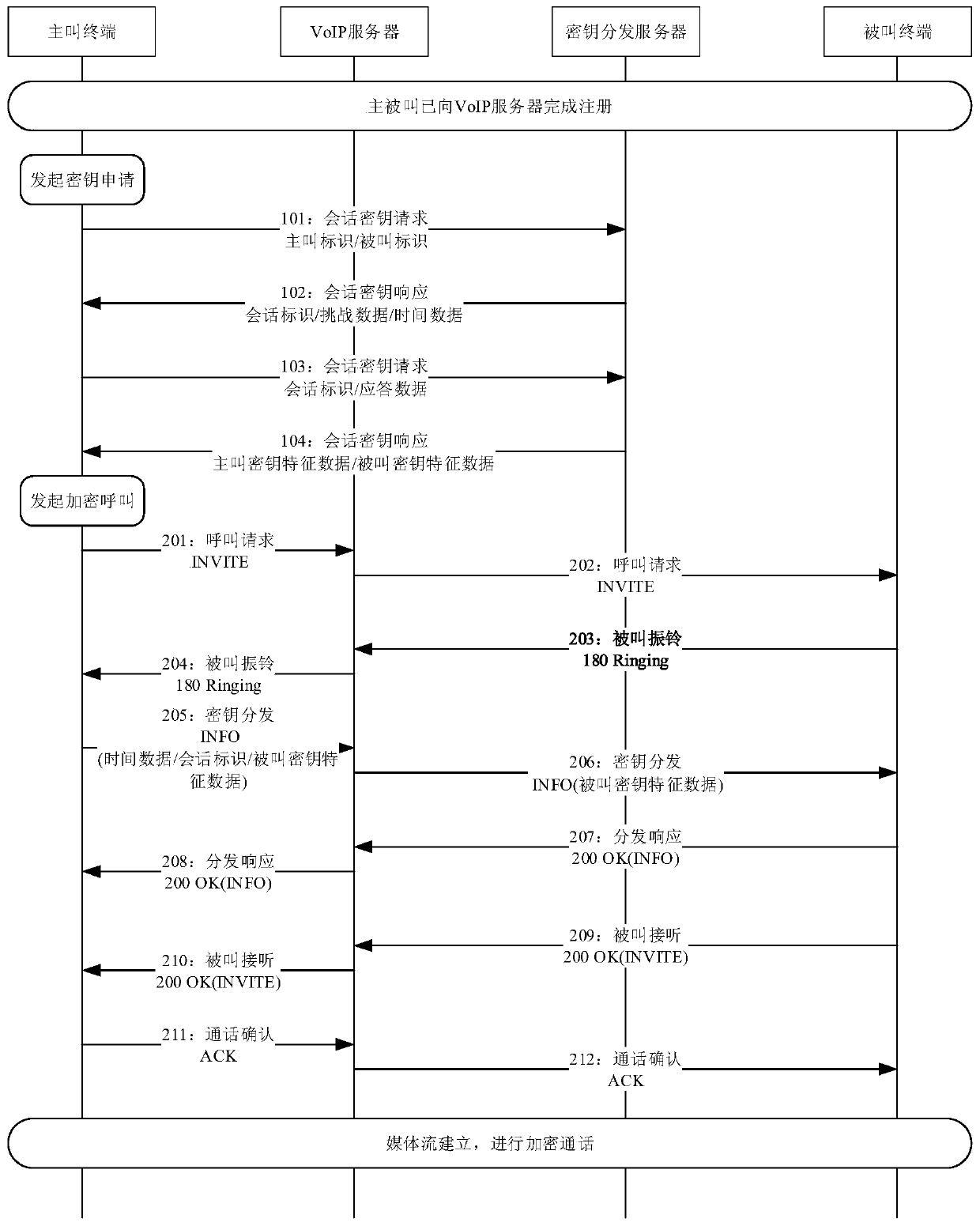
ActiveCN106936788AReduced Adjustment RetrofitEasy key managementKey distribution for secure communicationPlaintextSession Initiation Protocol
The invention discloses a key distribution method applicable to VOIP voice encryption, which is characterized in that a calling terminal initiates a session key application to a key distribution server (KDS) so as to trigger key distribution, the KDS generates a session key for a calling party and a called party and returns the session key to the calling terminal; the calling terminal initiates an encryption call to a called terminal through a VOIP server after acquiring the session key and sends key feature data generated by the KDS to the called terminal, and a media stream transmission channel is established between the calling party and the called party through the VOIP server; the calling party and the called party encrypt media streams by using the session key and send the encrypted media streams to each other, and the receiving parties decrypt the received data by using the session key so as to acquire the media streams. The key distribution method has the advantages that the key is directly generated by the KDS, thereby being easy to perform key management, and reducing adjustment and transformation for the VoIP server; the KDS performs identity verification on the calling party and the called party before the key is generated, thereby making up the vulnerability of identity authentication of an SIP (Session Initiation Protocol); one session is provided with one key, encryption is performed in the whole process, no plaintext appears in the transmission process, and the security is high.
Owner:BEIJING DATANG GOHIGH SOFTWARE TECH
A secure communication method between mobile nodes in mobile self-organized network
InactiveCN1667999ABlocking insecurityAchieve securityKey distribution for secure communicationUser identity/authority verificationSecure communicationTelecommunications link
This invention disclose a secret communication method among mobile nexuses in a mobile self-organized network characterizing in applying Diffie-Hellman protocol and a public cryptographic key digital signature to realize double-way discrimination when setting up Ad Hoc mobile self-organized network link and deriving cryptographic key for the cipher of data link layer data frame and data completion, which realizes safety of segment by segment of the link, ensures that different links apply different working cryptographic keys in a mobile Ad Hoc network, solves the problem of counterfeit communication nexus and tap network and simplifies the management to said network link layer.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
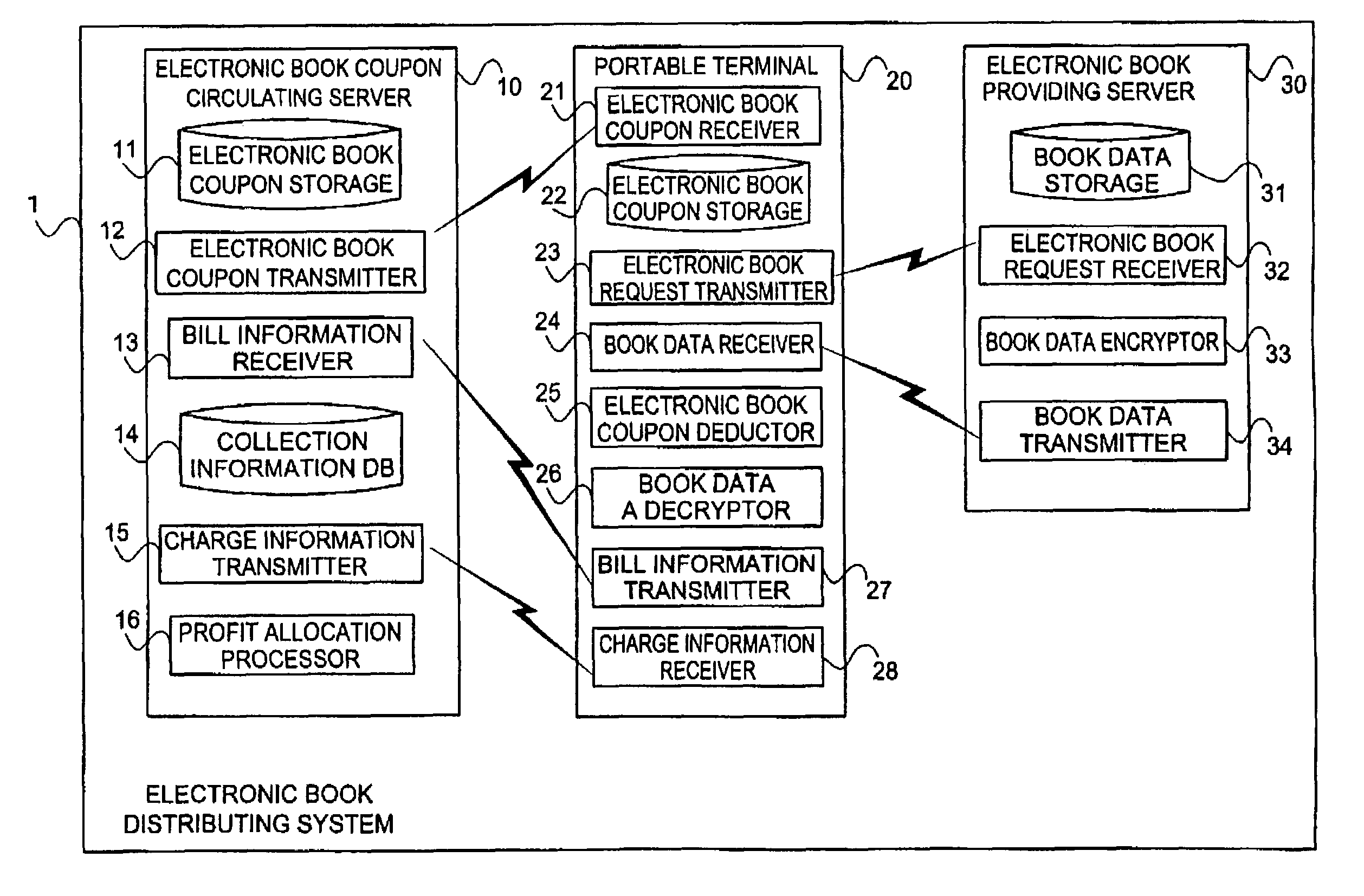
Communication terminal, portable terminal, circulating server, providing server, electronic book distributing method, and electronic book distributing program
InactiveUS7403924B2Improve convenienceReduce necessityDigital data processing detailsAnalogue secracy/subscription systemsElectronic bookComputer terminal
Owner:NTT DOCOMO INC +2
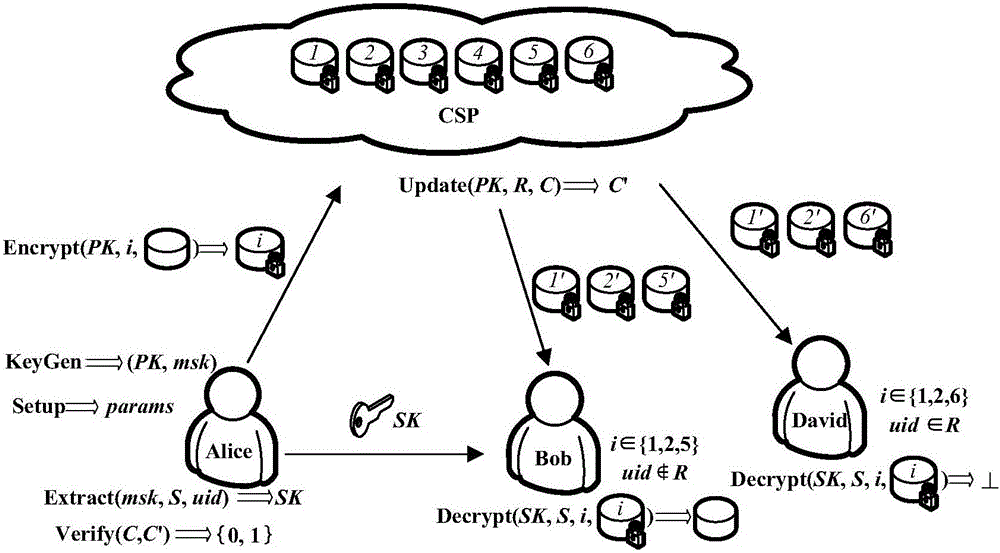
Key aggregation encryption method capable of being revoked in cloud environment
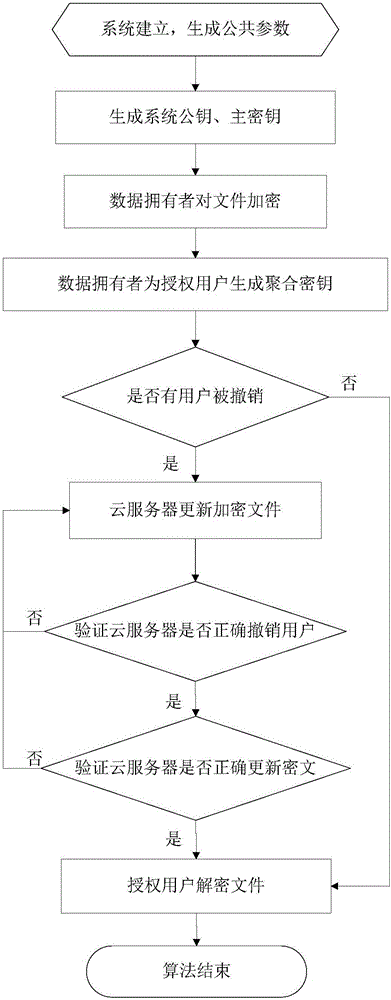
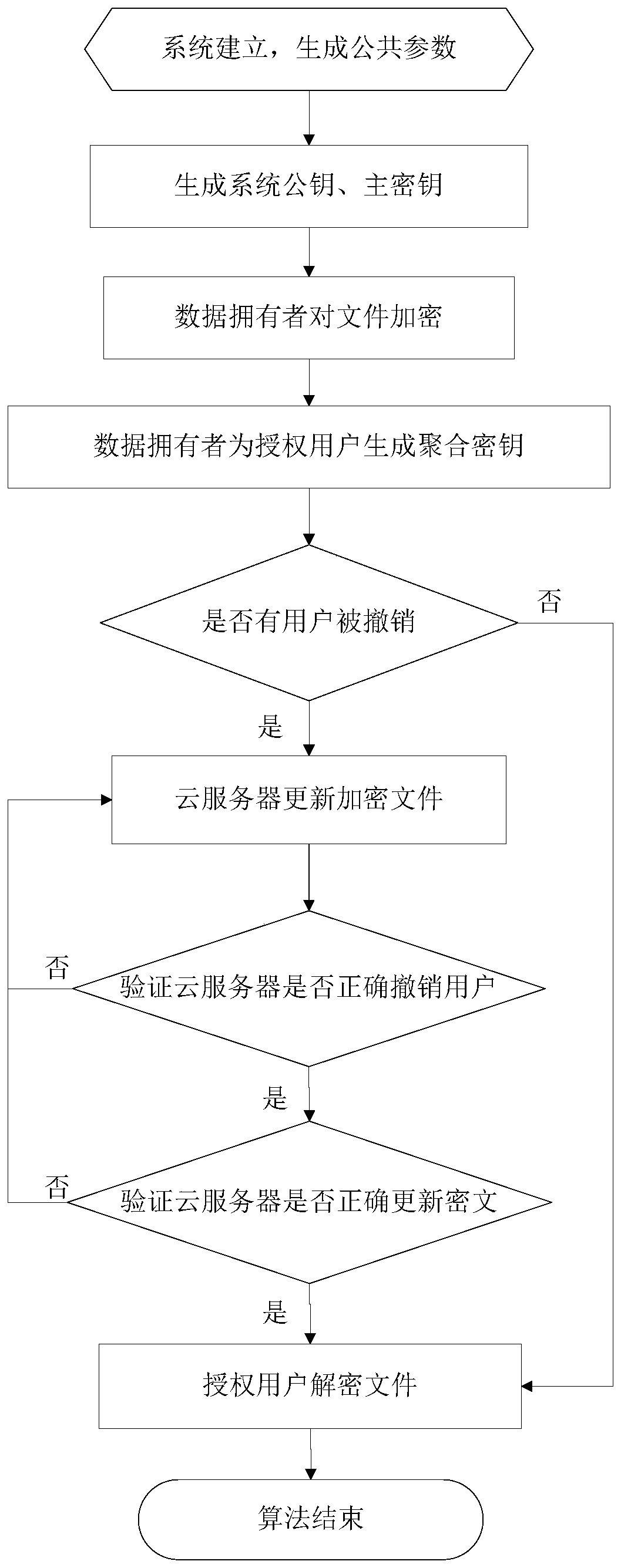
ActiveCN106788988APerfect dynamic management functionEasy key managementKey distribution for secure communicationPlaintextCiphertext
The invention discloses a key aggregation encryption method capable of being revoked in a cloud environment. A user revocation supporting function is added on the basis of a key aggregation mechanism, and a user dynamic management function on the key aggregation mechanism is improved. According to the method, not only is user key management simplified, but also different decryption permissions are granted to different users. Ciphertext is updated through a cloud storage server to achieve user permission revocation; when one user is revoked, the legal users do not need to update a key, and therefore the burden of an authority is reduced; and the ciphertext can be verified and updated, and it is guaranteed that user revocation is effectively executed. Security proof shows that on the basis of a Weak DHDHE assumption, it proves that the proposed method achieves non-adaptive selection plaintext security under a standard model. Performance analysis shows that by means of the method, the length of the user key and the ciphertext is kept to be O(1), the length of systematic public parameters is kept to be O(log N), more efficient user revocation efficiency is achieved, and control over access permissions of the users is effectively achieved.
Owner:广州广信网络科技有限公司 +1
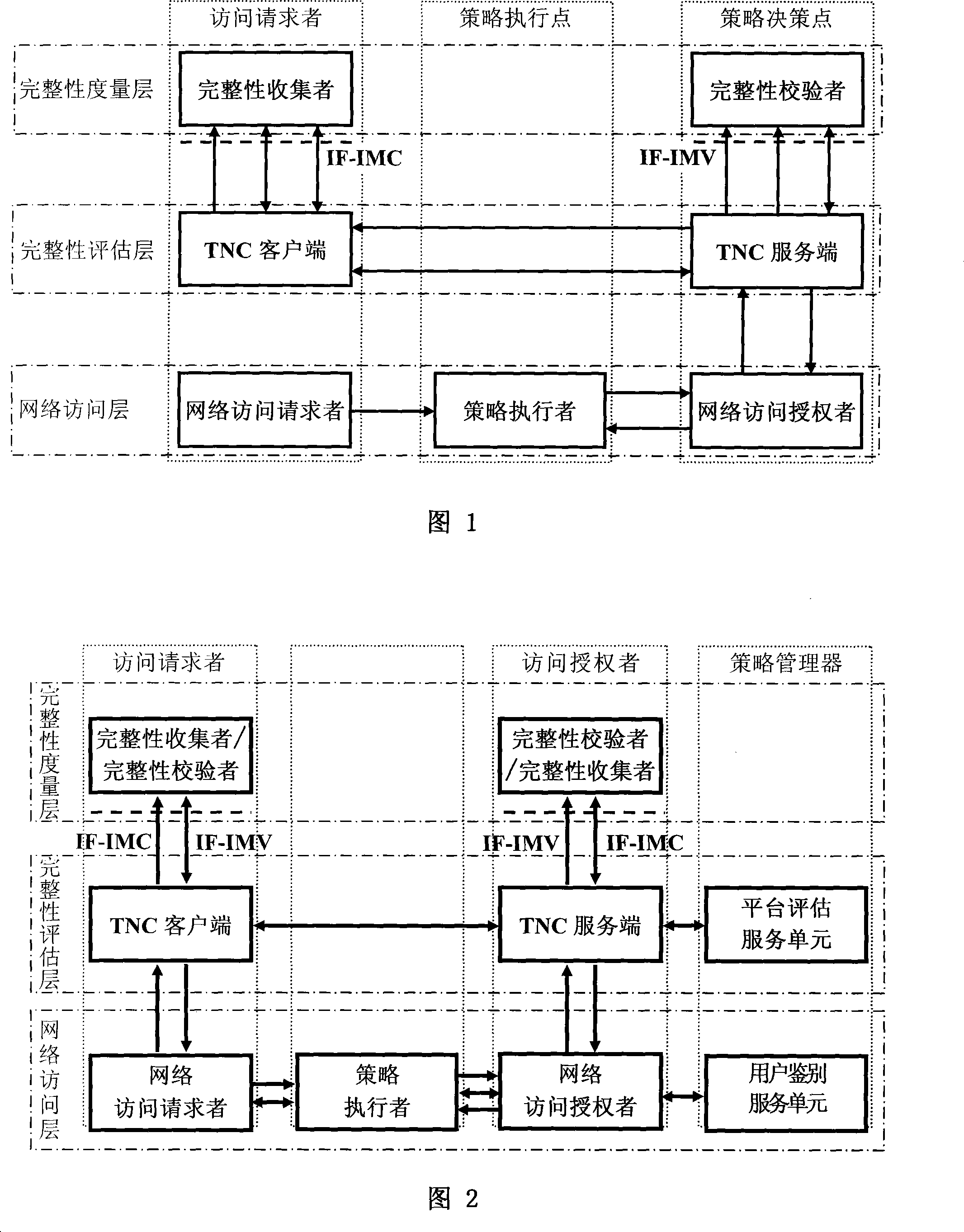
A trusted network connection system for security enhancement
ActiveCN101242401AImprove securityEasy to manageSecuring communicationIntegrity assessmentTransmission protocol
The invention relates to a safety-enhanced trusted network connecting system, the access requestor is network connected with a policy enforcement point in authentication protocol manner, the access requestor is network connected with an access authorizer by network authorizing transmission protocol interface, integrity evaluation interface and integrity measurement interface, the policy enforcement point is network connected with the access authorizer by policy implementation interface, the access authorizer is network connected with a policy manager by user identification authorization interface, platform evaluation authorization interface and integrity measurement interface, the access requestor is network connected with the policy manager by integrity measurement interface. The invention solves following technology problems: low security, inability of the access requestor to verify the validation of AIK certificate, and non-equivalence of platform integrity evaluation. The invention employs three-element equivalent identification protocol in network access layer and integrity evaluation layer, which improves the whole trusted network connection architecture and extends the application scope of trusted network connection.
Owner:CHINA IWNCOMM
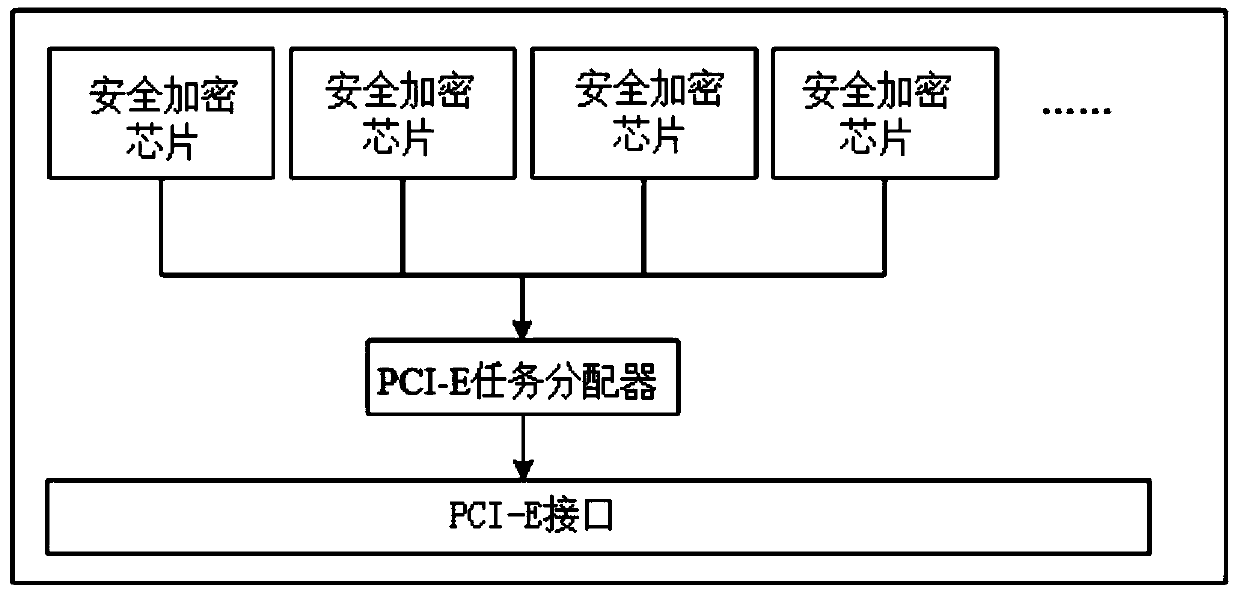
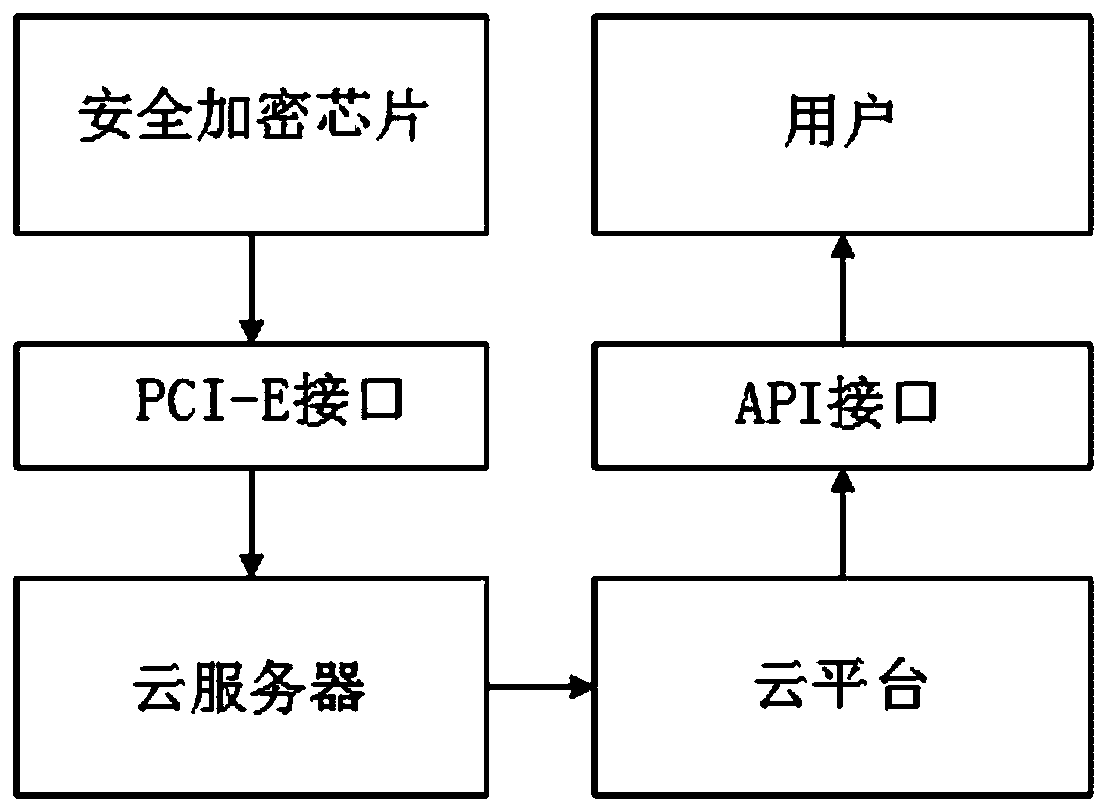
An embedded security encryption chip based on a cloud server
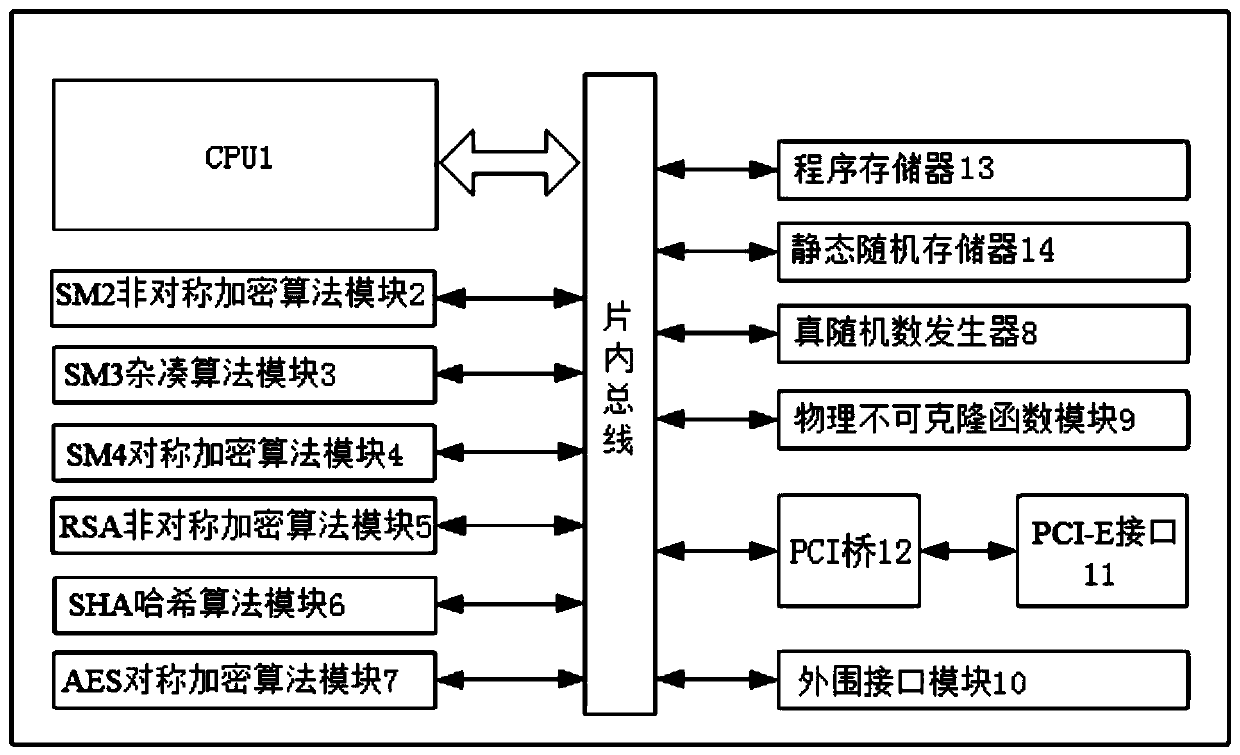
PendingCN109726598AEasy key managementSave resourcesInternal/peripheral component protectionResource consumptionPhysical unclonable function
The invention discloses an embedded security encryption chip based on a cloud server. The embedded security encryption chip comprises a CPU, an SM2 asymmetric encryption algorithm module, an SM3 hashalgorithm module, an SM4 symmetric encryption algorithm module, an RSA asymmetric encryption algorithm module, an SHA hash algorithm module, an AES symmetric encryption algorithm module, a true randomnumber generator, a physical unclonable function module and a peripheral interface module which are integrated in the system. the embedded security encryption chip is externally integrated with PCI-Einterface, PCI-E interface connects to on-chip bus through PCI bridge, and the security encryption chip is inserted into the cloud server through the PCI-E interface. The digital signature verification and encryption / decryption speed is high, the secret key cannot be cloned, the security is high, the complexity of secret key management can be greatly reduced, the system resource consumption is reduced, the power consumption is reduced, And the chip is inserted into the cloud server through the PCI-E without changing the hardware architecture of the server, and has a secure API, so that a usercan quickly and conveniently call.
Owner:佛山芯珠微电子有限公司
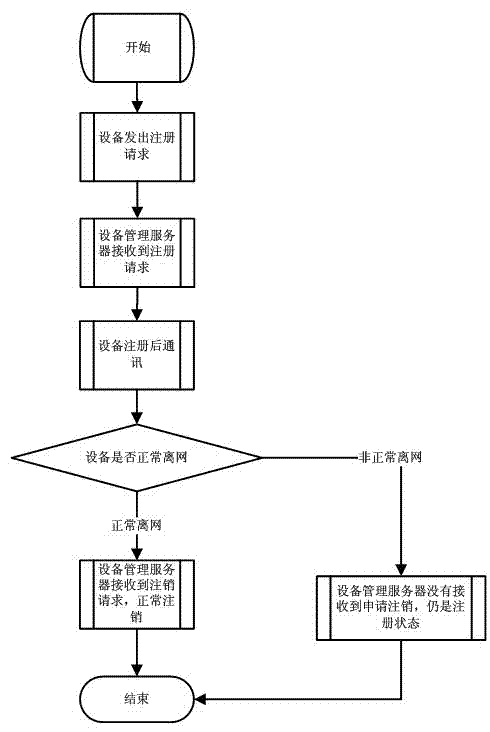
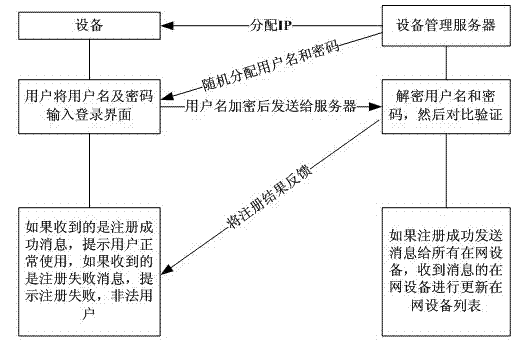
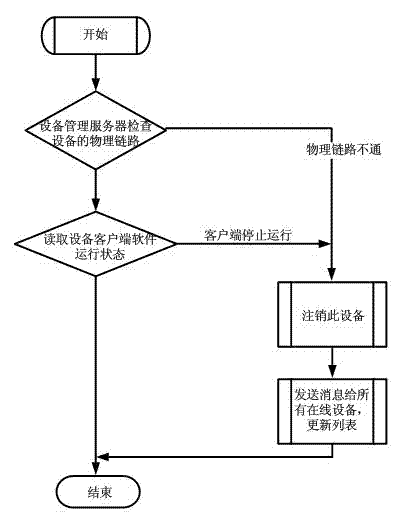
Method for registering and cancelling dynamic network organization devices
ActiveCN102932219AEasy key managementSave equipment resource and network resource overheadData switching by path configurationIp addressPassword
The invention relates to a method for registering and cancelling dynamic network organization devices. The method comprises the following steps: a device management server distributes an IP address, a user name and a password to each device in the network; an device user inputs the user names and passwords distributed by the device management server to the devices; the devices encrypt the user names and the passwords, and sends the encrypted user names and the passwords to the device management server; after receiving the encrypted user names and the passwords, the device management server performs decryption and comparison, and registration is realized after the comparison result is correct; the device management server checks on-network states of the registered devices; and the device management server automatically cancels out-of-network devices. According to the method, the device management server automatically checks the states of the on-network devices, so that the devices do not need to initiatively issue requests for registration and cancellation to the device management server, and the device management server can instantly acquire the on-network states of the devices and updates an on-network device list of each on-network device.
Owner:HISENSE BROADBAND MULTIMEDIA TECH
Authentication method based on smart card in multi-server environment
ActiveCN107248997AEasy key managementDoes not cause storage problemsKey distribution for secure communicationEncryption apparatus with shift registers/memoriesThird partySmart card
The invention discloses an authentication method based on a smart card in a multi-server environment. According to the authentication method, the participation of a third party in authentication is not needed, a user just needs to register for one time, the smart card only needs to store information of constants, the authentication and access among multiple servers can be realized, a server end also does not need to store any user information, and thus a problem that the information stored by the smart card is increased with the increase of registration servers when no third party participates authentication in the multi-server environment is solved. The security of an authentication model is proved through BAN logic analysis, at the same time performance analysis shows that the authentication scheme of the invention has a low storage cost requirement compared with an existing authentication scheme based on the smart card in the multi-server environment in the condition that computation cost and communication cost do not increase burden significantly.
Owner:广州梵星信息科技有限公司 +1
Binary channel multiple fingerprints optical encryption method
ActiveCN105809115AImprove securityEasy key managementBiometric pattern recognitionPrint image acquisitionInformation processingComputer hardware
The invention provides a binary channel multiple fingerprints optical encryption method comprising an encryption process and a deciphering process. A laser beam generator emits linearly polarized lights which are divided by a beam splitter into transmitting light and reflecting light. The transmitting light arrives to a left channel encryption key with fingerprint images and generates left channel modulated lasers. The reflecting light arrives to the right channel encryption key with fingerprint images and generates right channel modulated lasers. Recognizing the non-duplication characteristic of a biosignature, the invention integrates biological feature identification technologies with optical information processing technologies and provides such a binary channel multiple fingerprints optical encryption method, which is highly reliable and secure for encryption key management and is convenient for people to carry around. The method has a good application prospect in the information safety field.
Owner:SHANGHAI NORMAL UNIVERSITY
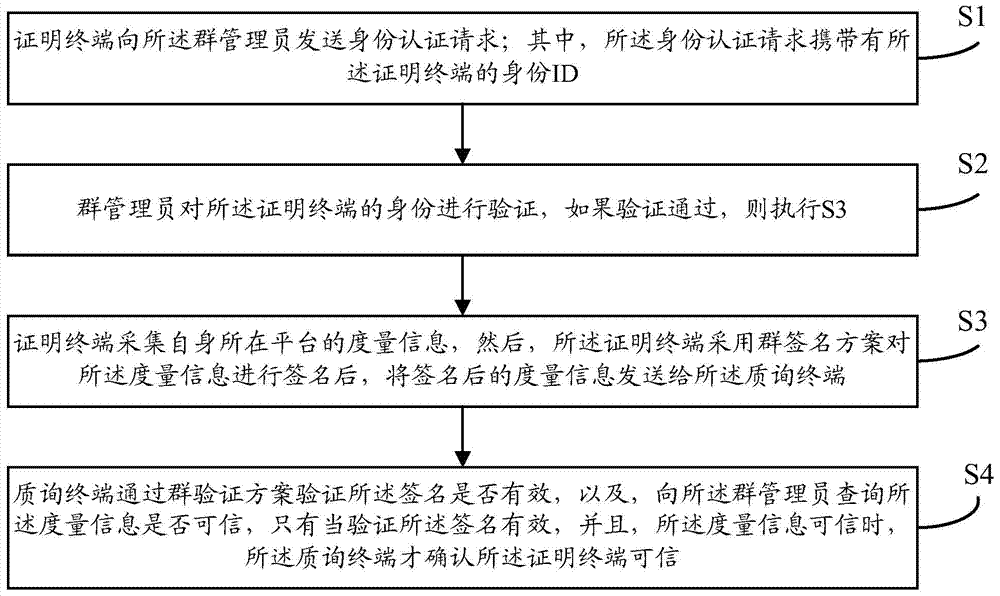
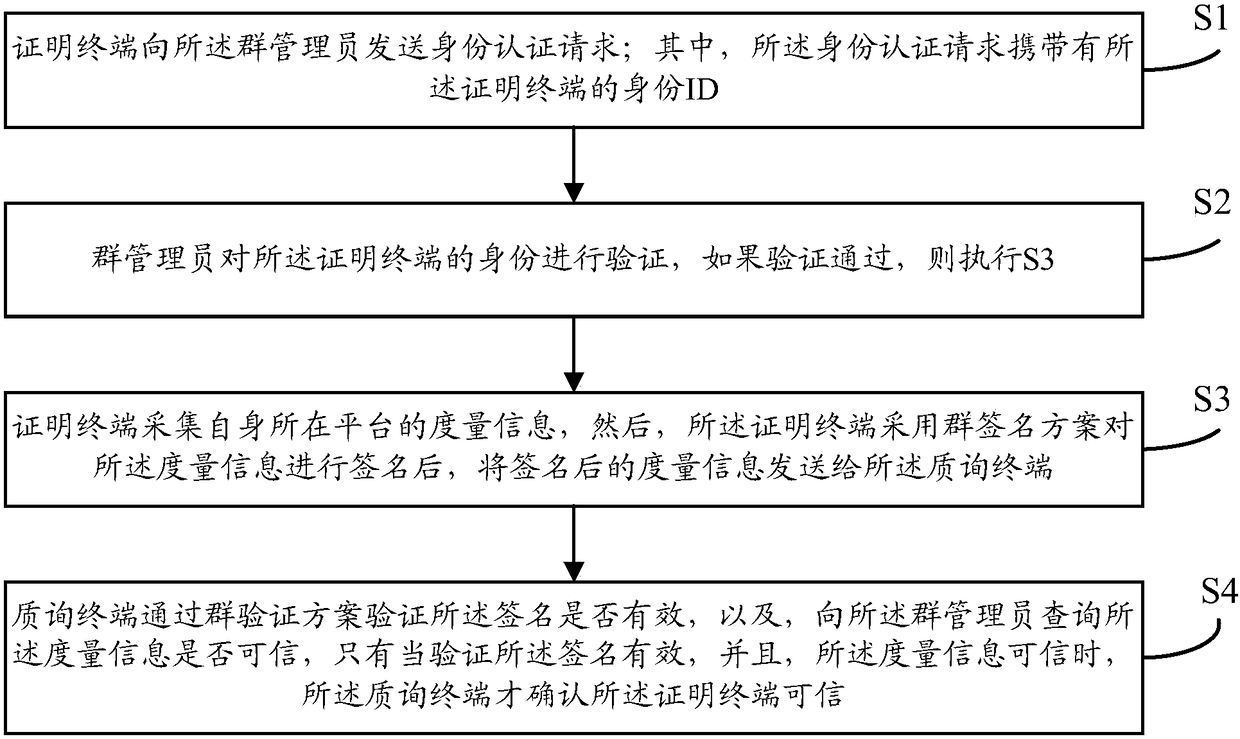
Remote proving method applicable to emergency rescue platform
InactiveCN104506532ASolve the credible proof problemGuarantee authenticitySecuring communicationSecure transmissionEmergency rescue
The invention provides a remote proving method applicable to emergency rescue platform. The remote providing method comprises the steps that a proving terminal sends an identity authentication request to a cluster administrator; the cluster administrator verifies the identity of the proving terminal; if passing the verification, the proving terminal acquires measurement information of a platform where the proving terminal is positioned, signs the measurement information by adopting a cluster signing scheme and sends the signed measurement information to an inquiry terminal; the inquiry terminal verifies whether the signature is effective according to a cluster verification scheme and inquires whether the measurement information is credible from the cluster administrator; only if the signature is effective and the measurement information is credible, the inquiry terminal confirms that the proving terminal is credible. The remote proving method has the advantages that the problem of credibility proving of a terminal can be effectively resolved, and the authenticity of data and secure transmission of the data are guaranteed; meanwhile, the remote proving method has the characteristic of proving traceability, and identity forgery attack and malicious fraud attack can be effectively resisted.
Owner:BEIJING BUSINESS INTELLIGENCE & COMM TECH +1
Mobile commerce identity authentication method
InactiveCN101969446BEliminate inconvenienceMeet the inconvenienceUser identity/authority verificationThird partyInternet Authentication Service
The invention provides a mobile commerce identity authentication method. In the method, key negotiation is realized by the most efficient elliptic curve-based public key cryptosystem in public key cryptosystems. An elliptic curve algorithm has the characteristics of low calculated amount and high safety, so the elliptic curve algorithm is used for generating a public key and a private key, and a public key cryptosystem without a third-party is realized and applied to the two-way authentication service of a client and a server.
Owner:BEIJING JIAOTONG UNIV
ID cryptography-based anti-quantum computing group communication method and system
ActiveCN111918285AImprove the safety of useEnsure safetyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer networkKey (cryptography)
The invention provides an ID cryptography-based anti-quantum computing group communication method and system, and the method comprises the steps: distributing respective identity IDs and private keysto group members through an ID cryptography mechanism, enabling the group members to calculate the public keys of opposite sides through the public IDs of the opposite sides during communication, andthen calculating symmetric keys according to the private keys of the group members and the public keys of the opposite sides; achieving one-to-one communication with the opposite side; when the secretkey is updated, enabling an administrator to encrypt the updating secret key by using the symmetric secret key of each group member and send the updating secret key, enabling each group member to calculate the symmetric secret key with the administrator to obtain the updating secret key, and updating the symmetric secret key pool of the administrator by using the updating secret key according toa preset updating method. According to the invention, the symmetric key pool and the ID cryptography are combined, and the use security of the symmetric key pool is further enhanced in the scene of group communication.
Owner:南京如般量子科技有限公司 +1
Key seed matrix and certificateless anti-collision key generation method based on matrix
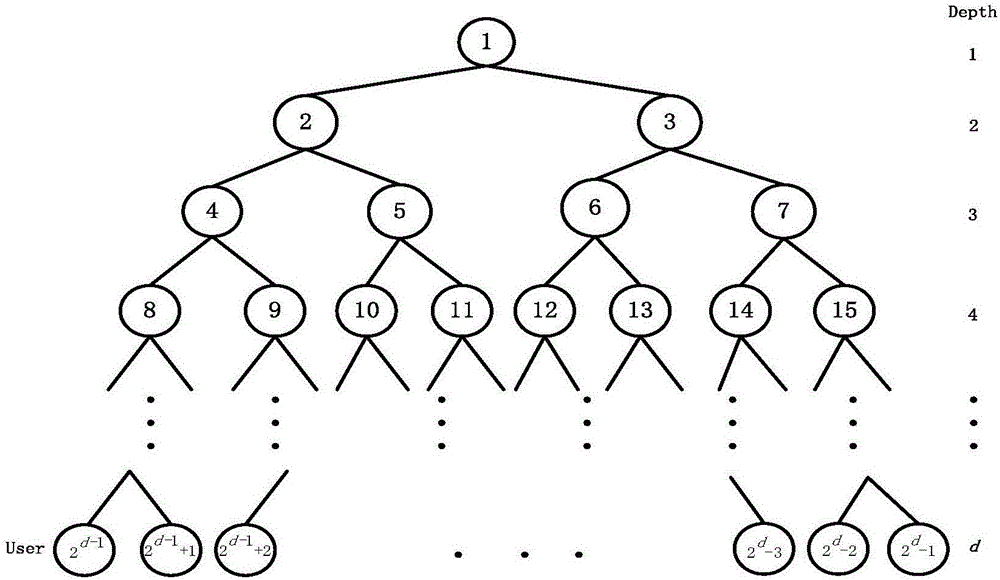
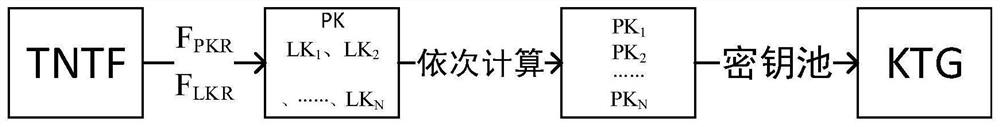
PendingCN114065188AEasy key managementImprove efficiencyRandom number generatorsDigital data authenticationCryptosystemKey generation
The invention discloses a key seed matrix and a certificateless anti-collision key generation method based on the key seed matrix. The key generation method comprises the following steps: a key generation center generating a 200-bit random number; calculating a public key of the equipment part according to the random number; the key generation center calculating a ZA value according to the equipment identifier and the public key seed matrix, and calculating a Z value according to the ZA value and the partial public key of the equipment; selecting and adding eight elements according to the coordinate of the Z value mapped to the private key seed matrix to obtain an equipment identification private key, and calculating an equipment identification public key according to the equipment identification private key; the key generation center calculating an equipment complete public key according to the equipment identification public key, and calculating an equipment complete private key according to the random number and the equipment identification private key; and after the complete equipment public key and the complete equipment private key are obtained, the key generation center issuing the key pair to the equipment end through the secure channel. According to the method, the advantages of a combined public key technology and a certificateless cryptosystem are combined, and the problems between the combined public key technology and the certificateless cryptosystem are solved.
Owner:鄂尔多斯市迪曼森密码科技有限公司
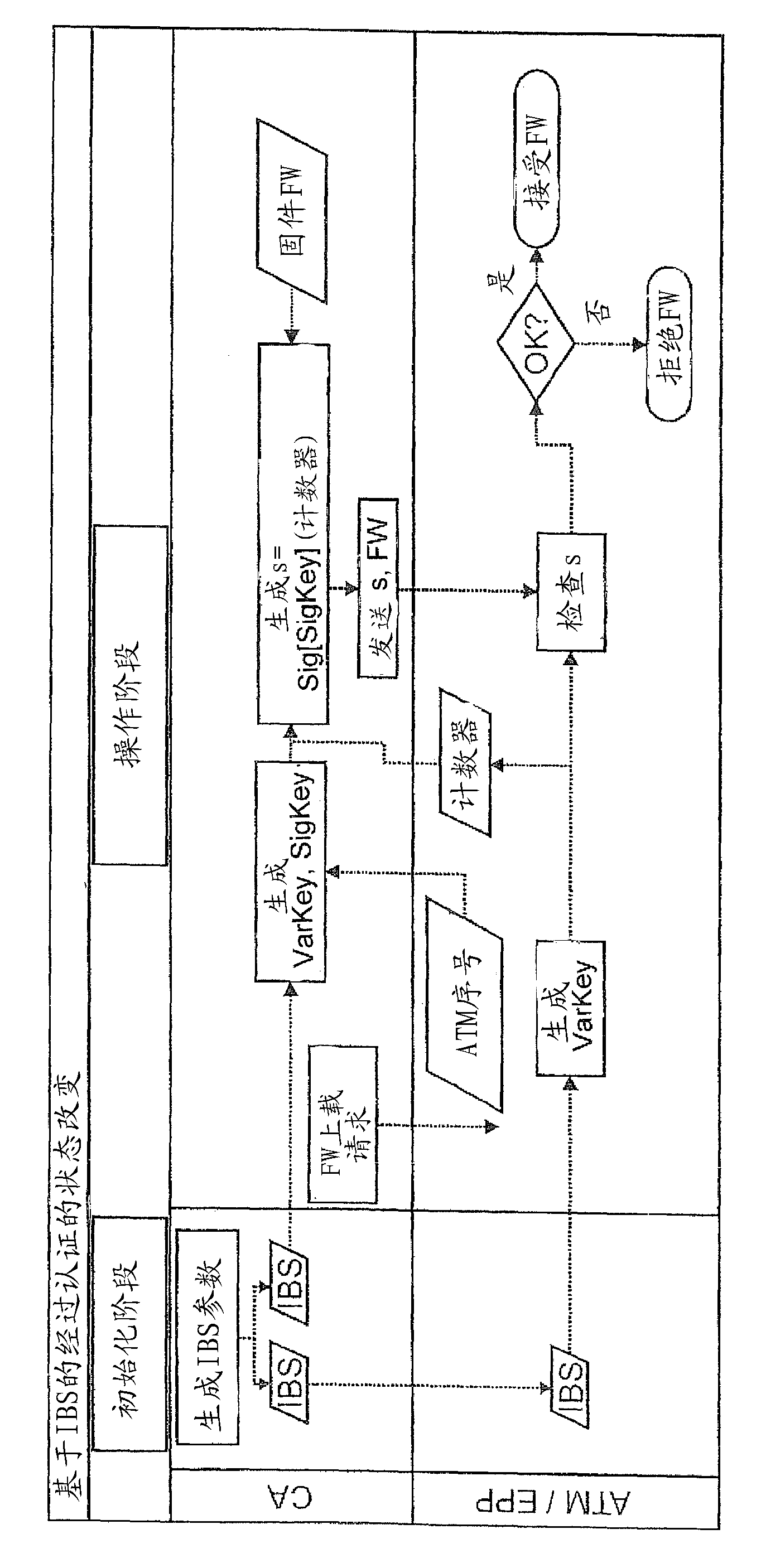
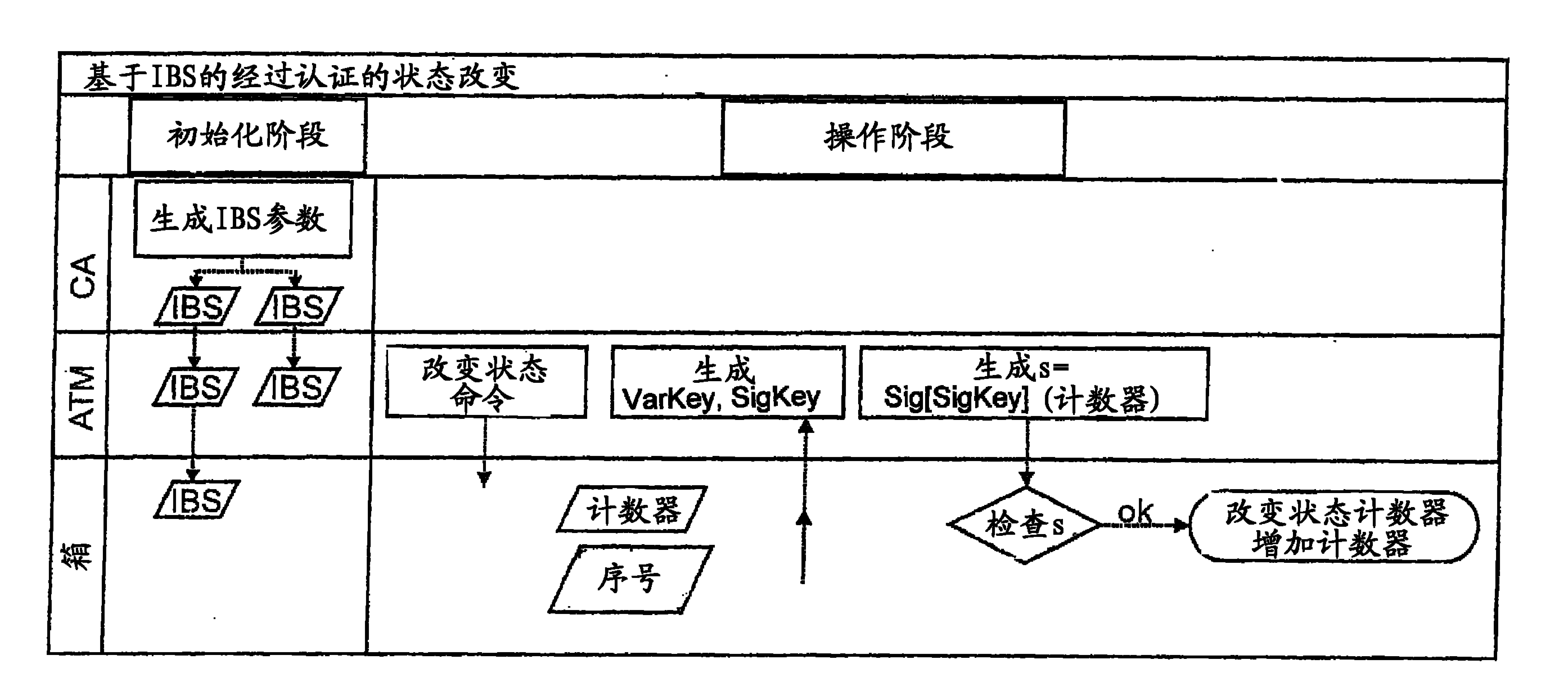
Method and device for authenticating components within an automatic teller machine
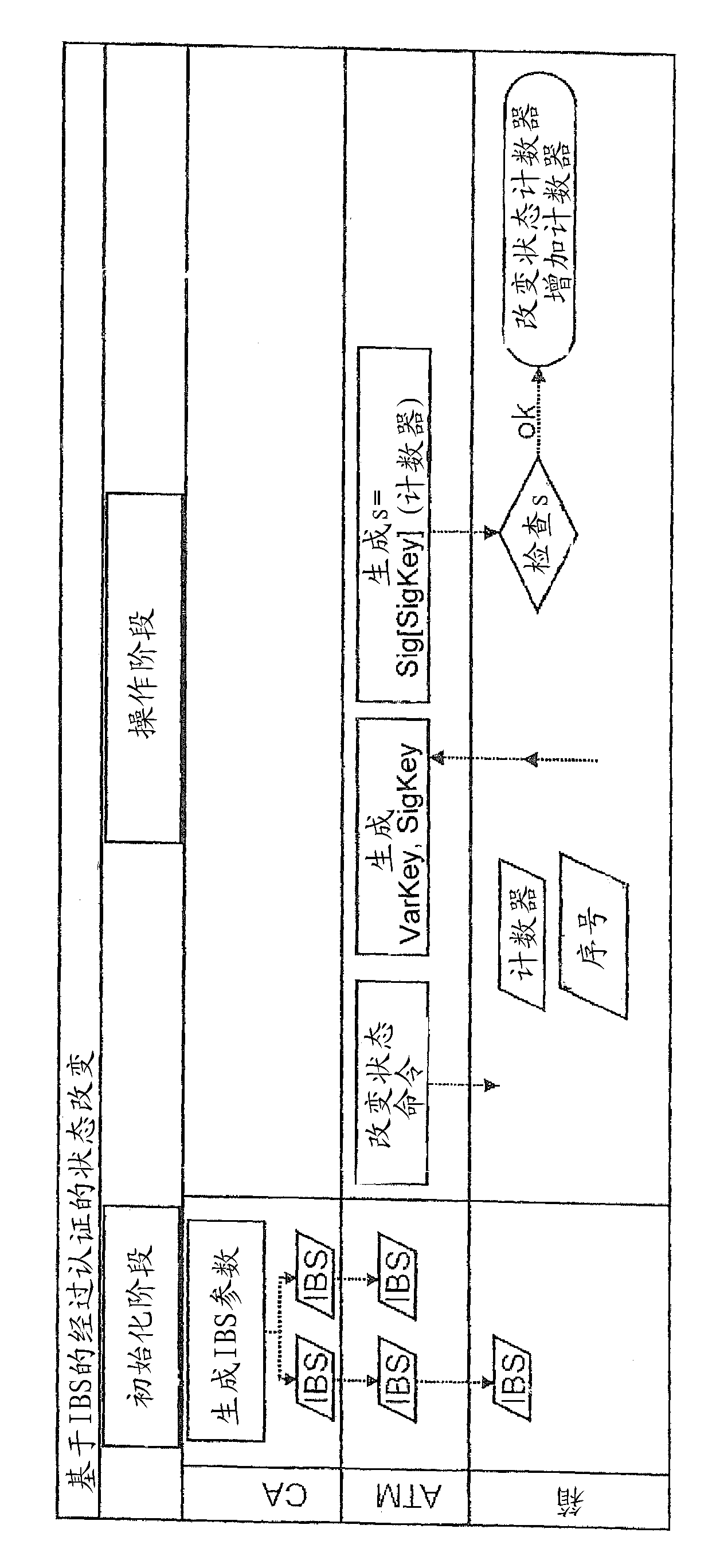
ActiveCN102511057AReduce usageEasy key managementComplete banking machinesPublic key for secure communicationComputer hardwareSelf-service
The invention relates to a device and a method for authenticating components of an self-service automatic teller machine, wherein the components comprise unambiguous identification information that can be exchanged among the components, wherein an authentication of the components and / or the information exchanged between the components is carried out by the encryption and / or signature of the information on basis of identity based encryption (IBE) that uses the identification information of the components.
Owner:WINCOR NIXDORF INT GMBH
Communication terminal, portable terminal, circulating server, providing server, electronic book distributing method, and eletronic book distributing program
InactiveUS20070250455A1Improve convenienceReduce necessityDigital data protectionApparatus for meter-controlled dispensingComputer terminalElectronic book
A portable terminal according to the present invention is provided with an electronic book coupon storage, a book data receiver, an electronic book coupon deductor, and a book data decryptor. The electronic book coupon storage stores an electronic book coupon used in acquisition of book data containing a plurality of page data units, along with a decryption key used in decryption of the plurality of page data units. The book data receiver receives the book data from an electronic book providing server. The electronic book coupon deductor deducts an electronic worth equivalent to a price according to page data requested to be read out, from the electronic book coupon. The book data decryptor decrypts the page data in steps of one page data unit by use of the decryption key in conjunction with the deduction of the electronic worth.
Owner:NTT DOCOMO INC +2
Multicast data enciphered transmission method
InactiveCN100588153CSolve unsafe problems such as easy leakageEnsure safetyMultiple keys/algorithms usageCryptographic nonceInformation security
This invention relates to a method for ciphered transmission of multicast data including a ciphering method to multicast data at the sending end of multicast source data and a deciphering method for deciphering multicast data at the receiving end, in which, when sending multicast data each time, the sender selects a cryptographic key randomly to cipher the information, yet the key is not told to the receiver, when deciphering, the receiver must utilizes its private key and the cryptographic key sent to the sender to get the key ciphering the multicast data then to decipher it to resume the data cleartext.
Owner:SOUTH CHINA UNIV OF TECH
A data access control method and system
ActiveCN103746798BImprove data securityEasy key managementKey distribution for secure communicationThird partyData access control
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
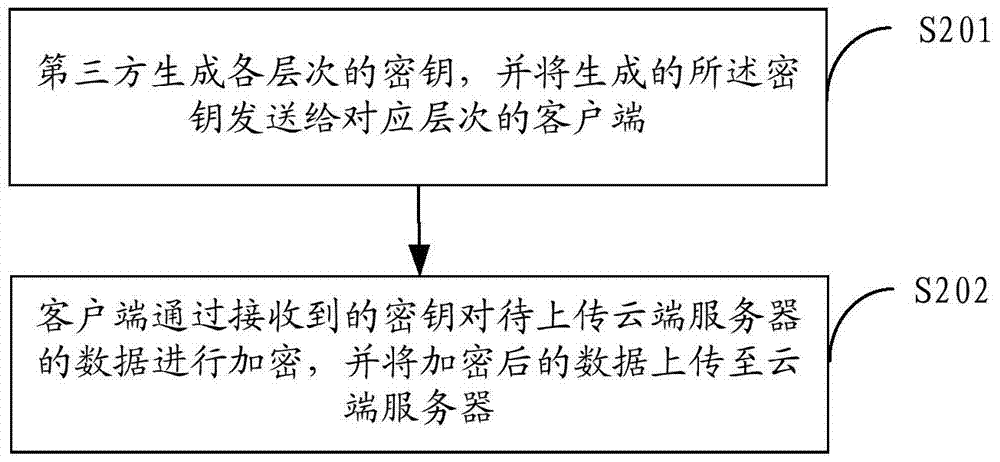
A Remote Attestation Method Applicable to Emergency Rescue Platform
InactiveCN104506532BSolve the credible proof problemGuarantee authenticitySecuring communicationEmergency rescueSecure transmission
The invention provides a remote proving method applicable to emergency rescue platform. The remote providing method comprises the steps that a proving terminal sends an identity authentication request to a cluster administrator; the cluster administrator verifies the identity of the proving terminal; if passing the verification, the proving terminal acquires measurement information of a platform where the proving terminal is positioned, signs the measurement information by adopting a cluster signing scheme and sends the signed measurement information to an inquiry terminal; the inquiry terminal verifies whether the signature is effective according to a cluster verification scheme and inquires whether the measurement information is credible from the cluster administrator; only if the signature is effective and the measurement information is credible, the inquiry terminal confirms that the proving terminal is credible. The remote proving method has the advantages that the problem of credibility proving of a terminal can be effectively resolved, and the authenticity of data and secure transmission of the data are guaranteed; meanwhile, the remote proving method has the characteristic of proving traceability, and identity forgery attack and malicious fraud attack can be effectively resisted.
Owner:BEIJING BUSINESS INTELLIGENCE & COMM TECH +1
A key distribution method suitable for VoIP voice encryption
ActiveCN106936788BReduced Adjustment RetrofitEasy key managementKey distribution for secure communicationPlaintextTransmission channel
The invention discloses a key distribution method suitable for VOIP voice encryption. The calling terminal initiates a session key application to a key distribution server (KDS for short), triggers key distribution, and the KDS generates a session between the main and called parties. The key is returned to the calling terminal; after the calling terminal obtains the session key, it initiates an encrypted call to the called terminal through the VOIP server, sends the key characteristic data generated by KDS to the called terminal, and the calling and called parties through the VOIP server Establish a media stream transmission channel; both parties use the session key to encrypt the media stream and transmit it to the other party, and the other party uses the session key to decrypt the received data to obtain the media stream. Advantages of the present invention: the key is directly generated by KDS, which is easy to manage the key and reduces the adjustment and transformation of the VoIP server; Encryption, full encryption, no plaintext in the transmission process, high security.
Owner:BEIJING DATANG GOHIGH SOFTWARE TECH
Revocable Key Aggregation Encryption Method in Cloud Environment
ActiveCN106788988BPerfect dynamic management functionEasy key managementKey distribution for secure communicationPlaintextCiphertext
The invention discloses a key aggregation encryption method capable of being revoked in a cloud environment. A user revocation supporting function is added on the basis of a key aggregation mechanism, and a user dynamic management function on the key aggregation mechanism is improved. According to the method, not only is user key management simplified, but also different decryption permissions are granted to different users. Ciphertext is updated through a cloud storage server to achieve user permission revocation; when one user is revoked, the legal users do not need to update a key, and therefore the burden of an authority is reduced; and the ciphertext can be verified and updated, and it is guaranteed that user revocation is effectively executed. Security proof shows that on the basis of a Weak DHDHE assumption, it proves that the proposed method achieves non-adaptive selection plaintext security under a standard model. Performance analysis shows that by means of the method, the length of the user key and the ciphertext is kept to be O(1), the length of systematic public parameters is kept to be O(log N), more efficient user revocation efficiency is achieved, and control over access permissions of the users is effectively achieved.
Owner:广州广信网络科技有限公司 +1
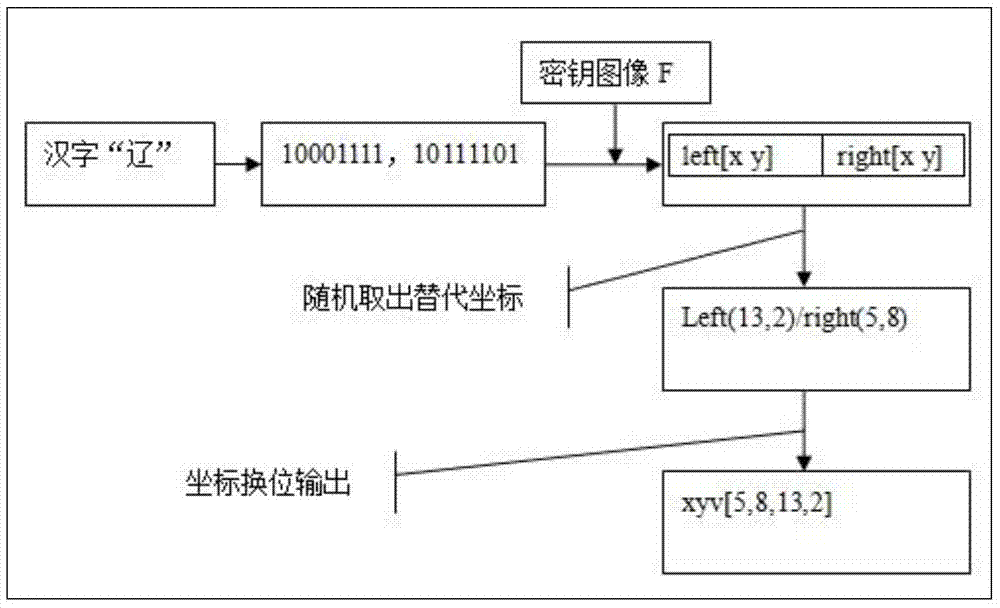
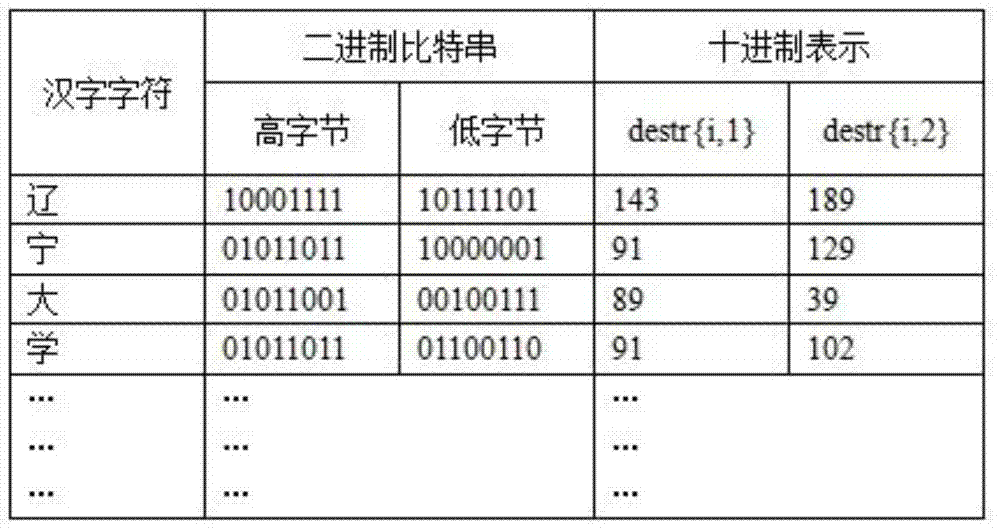
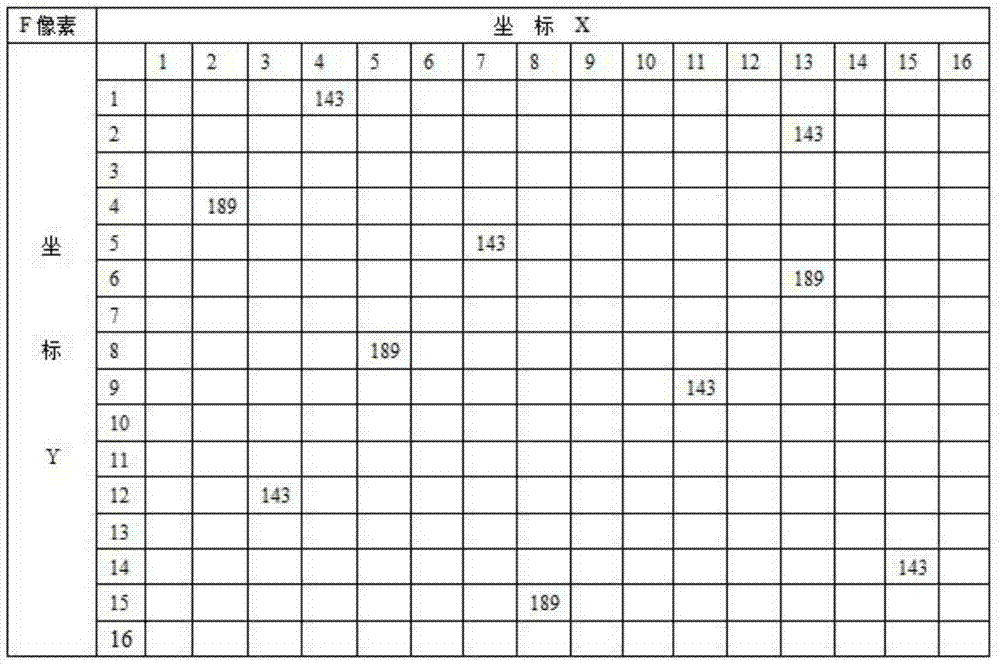
Encoding Method of Chinese Character Cipher Based on Image Pixel Coordinates
ActiveCN104468090BGuaranteed confidentialityIntegrity guaranteedEncryption apparatus with shift registers/memoriesPlaintextCiphertext
The invention discloses a Chinese character password encoding method based on image pixel coordinates. The encryption process: (1) input a Chinese character string in plain text, and take out the string length K; (2) read the public key image f1 and the private key image f2 respectively, Generate the key image F, and take out the image size M×N; (3) Convert each Chinese character into binary data and divide it into high and low byte blocks, and store them in the cell arrays destr{i,1} and destr{ i, 2}; (4) cyclically search for the pixel values matching the cell arrays destr{i,1} and destr{i,2} respectively in F, and read their pixel coordinates and store them in the two-dimensional matrix left[ x, y] and right[x, y]; (5) Randomly take out two coordinate values in left[x, y] and right[x, y] to replace the high byte and low byte blocks of the Chinese character ; (6) 4 values of these two coordinates are transposed by the agreed transposition order, and output in the four-dimensional matrix xyv[]; (7) when i=K, the encryption process ends, and the output K row four-dimensional matrix xyv[] ] is the ciphertext. The encryption method has the advantages of good confidentiality and flexible and convenient key management, and is a safe Chinese character password encoding method.
Owner:LIAONING UNIVERSITY
Access authentication method, equipment and system of P2P (peer-to-peer) network
InactiveCN101815294BSimple access authentication workEasy encryption and decryptionTransmissionNetwork communicationComputer science
The invention discloses access authentication method, equipment and system of a P2P (peer-to-peer) network, belonging to the technical field of network communication. Network equipment in the P2P network is subjected to access authentication by adopting an identity-based public key IBC (Information Bearer Channel) mechanism. The method comprises the following steps of: receiving an access requesttransmitted by opposite terminal network equipment by home terminal network equipment; selecting a private key from the private keys of the home terminal network equipment as a conversation private key of the home terminal network equipment according to the private key level of the home terminal network equipment and the private key level of the opposite terminal network equipment; calculating a conversation main key of the home terminal network equipment according to the conversation private key of the home terminal network equipment, the identity information of the opposite terminal networkequipment corresponding to the conversation private key of the home terminal network equipment, a first negotiation parameter and a second random number determined by the home terminal network equipment; and returning an access response to the opposite terminal network equipment. By utilizing the IBC mechanism, distributed access authentication under the P2P network mode is solved, thus the IBC mechanism is particularly suitable for the P2P network.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com