Encoding Method of Chinese Character Cipher Based on Image Pixel Coordinates
A technology of image pixel coordinates and coding method, which is applied in the new Chinese character encryption algorithm and cipher coding field, can solve the problems of Chinese character message replacement encryption and security protection cipher coding method, etc., and achieves strong robustness and anti-cryptoanalysis ability. , the algorithm is simple, and the effect of ensuring confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] One, design idea of the present invention is as follows:
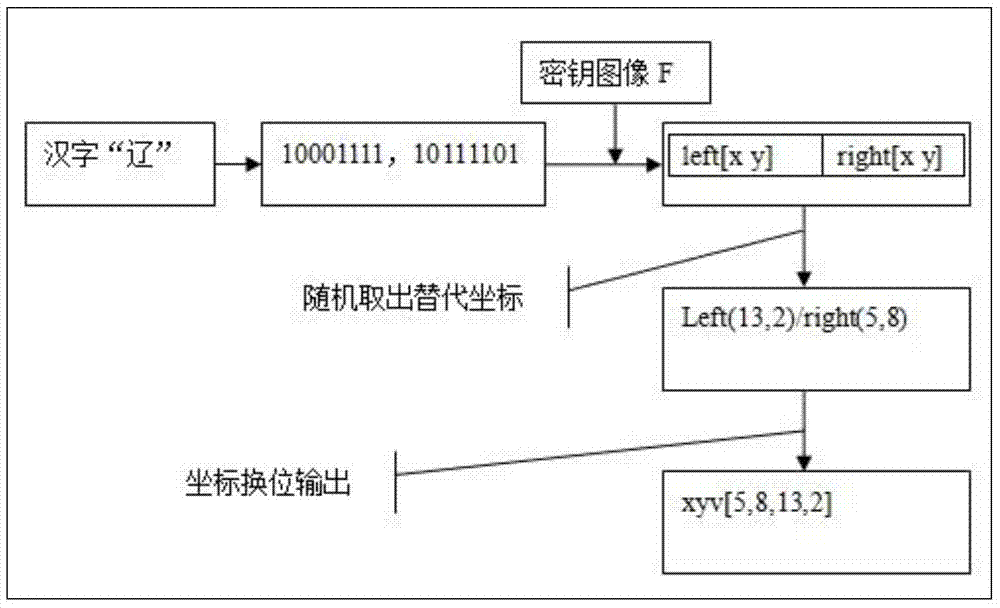
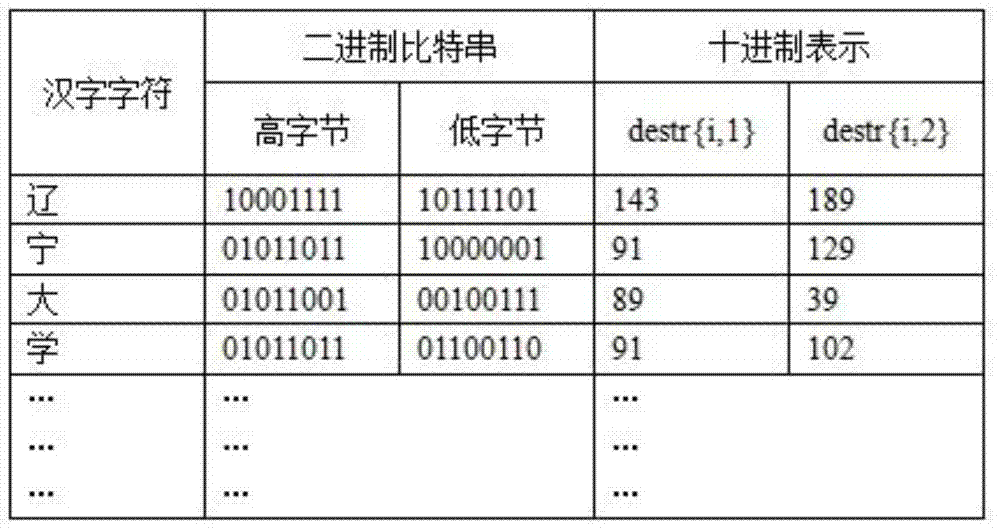
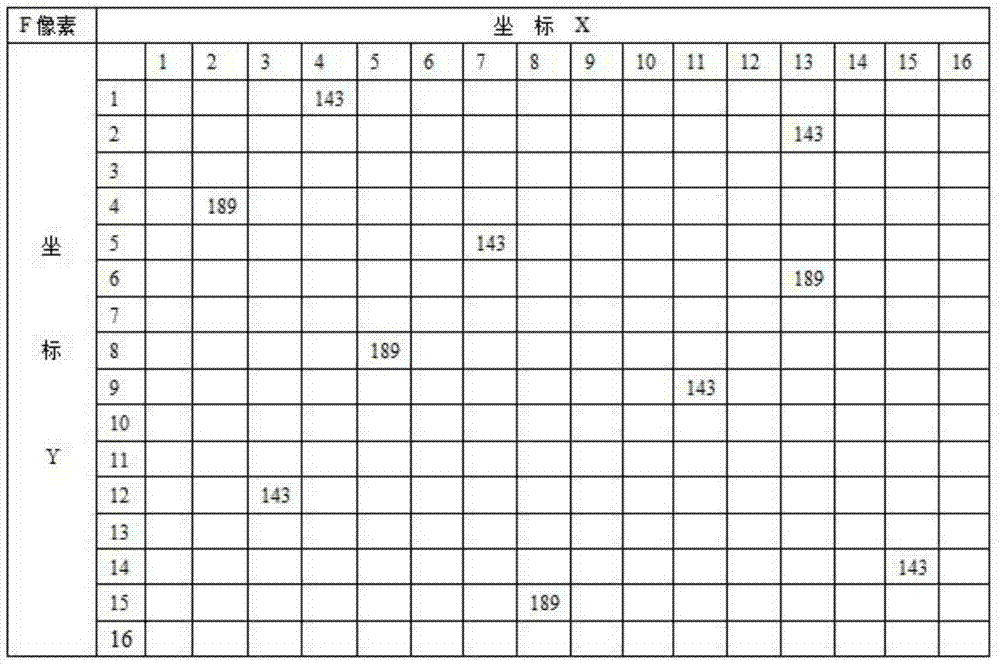
[0046] 1. Chinese characters exist in the form of binary numbers in computers and networks, and have the same digital characteristics as the pixel values of RGB digital images. Therefore, for each Chinese character, a completely matching binary can be found in the appropriate RGB image. Bit string, and take out the corresponding pixel coordinates to replace the Chinese characters for transmission and storage.
[0047] 2. Select the binary bit string matching the Chinese character in the RGB image by random number, and use the corresponding pixel coordinates to replace the Chinese character, so as to avoid the frequency characteristics of the replacement password and completely solve the attack problem of the frequency statistics analysis of the replacement password .
[0048]3, the Chinese characters are divided into two bytes or more sub-blocks, pixel matching is carried out for each sub-block and the coor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com