Reliable network access framework
A network access and network connection technology, which is applied in the direction of network connection, data exchange network, data exchange through path configuration, etc., to achieve the effects of centralized management and distribution, high security, and centralized verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] information flow
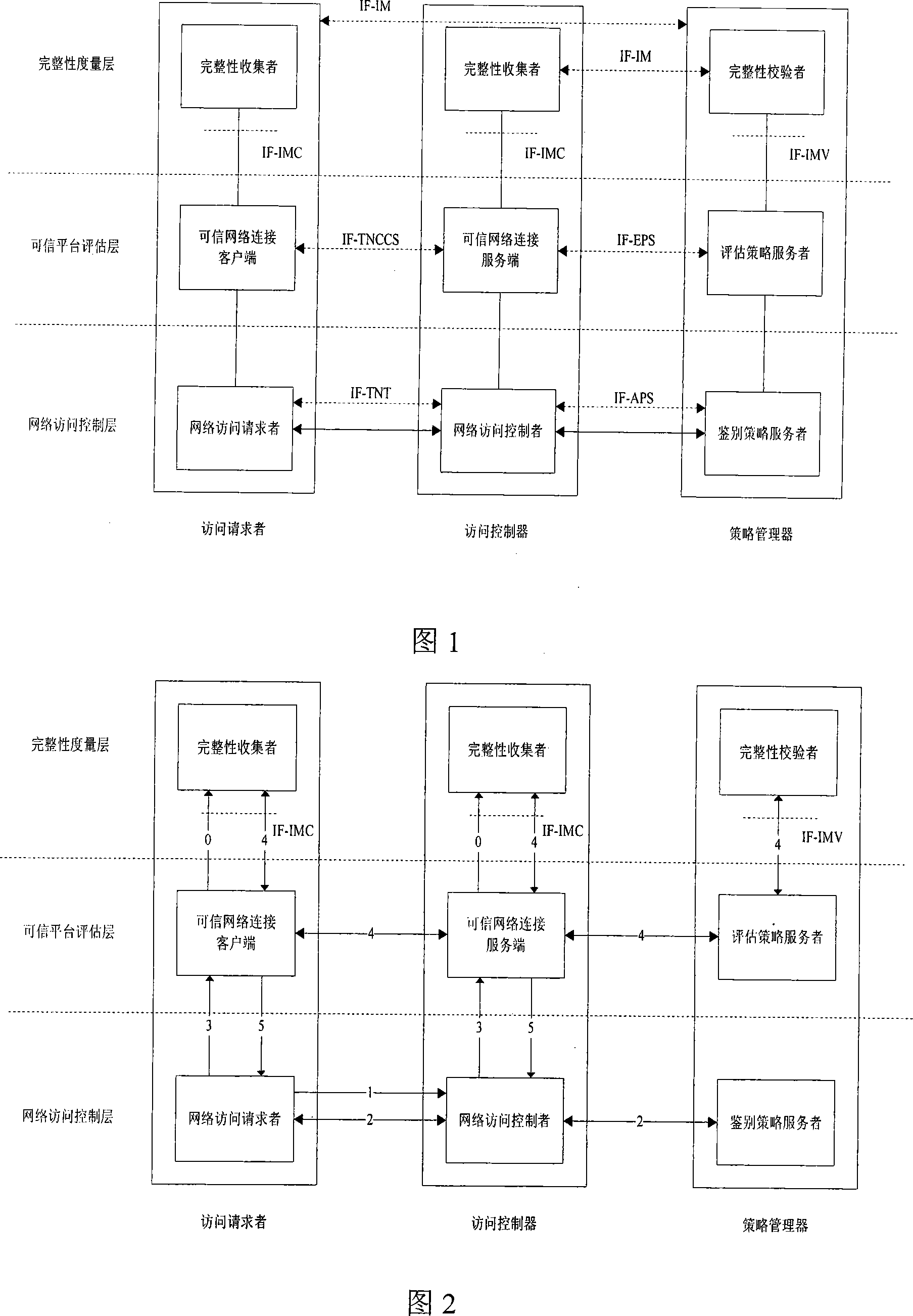
[0067] A complete information flow of the trusted network connection architecture is shown in Figure 2.
[0068] The information flow of the trusted network connection architecture is:
[0069] (1) The network access requester initiates an access request to the network access controller;
[0070] (2) After receiving the access request from the network access requester, the network access controller implements two-way user identity authentication between the access requester and the access controller with the network access requester and the authentication policy server. In the process of user identity authentication, the policy manager acts as a trusted third party, and a master key is negotiated between the access requester and the access controller. The access requester and the access controller use this master key to negotiate a session key between them. At the same time, the access requester and the access controller control the local port acco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com