Key aggregation encryption method capable of being revoked in cloud environment
An encryption method and cloud environment technology, applied in the field of key aggregation encryption, can solve the problems of not providing security certificates, expensive key update overhead, etc., achieve efficient user revocation efficiency, realize access control, and reduce the burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
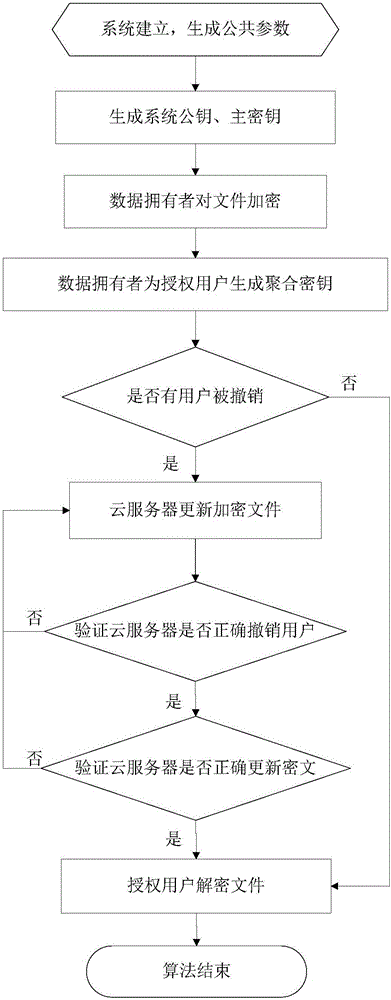
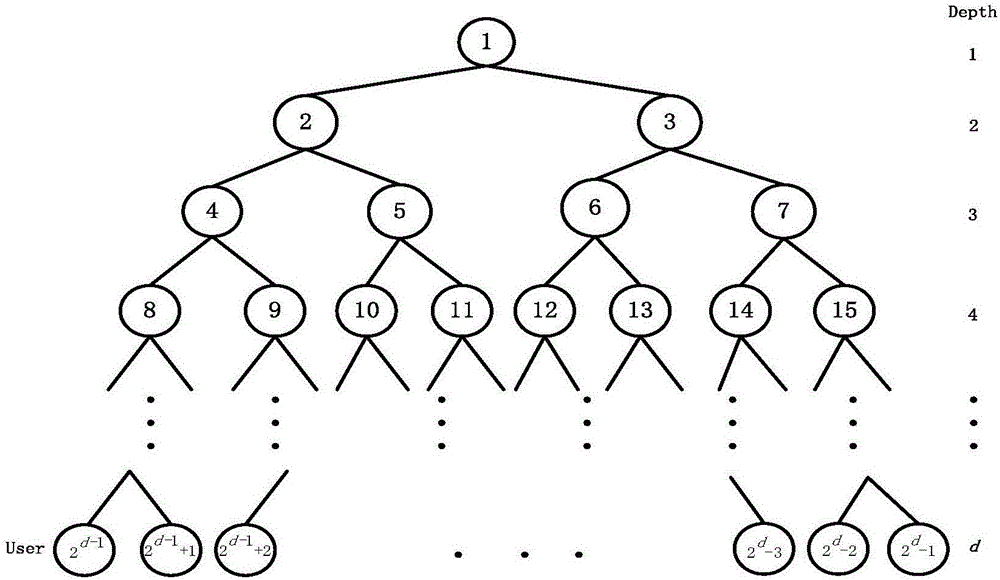
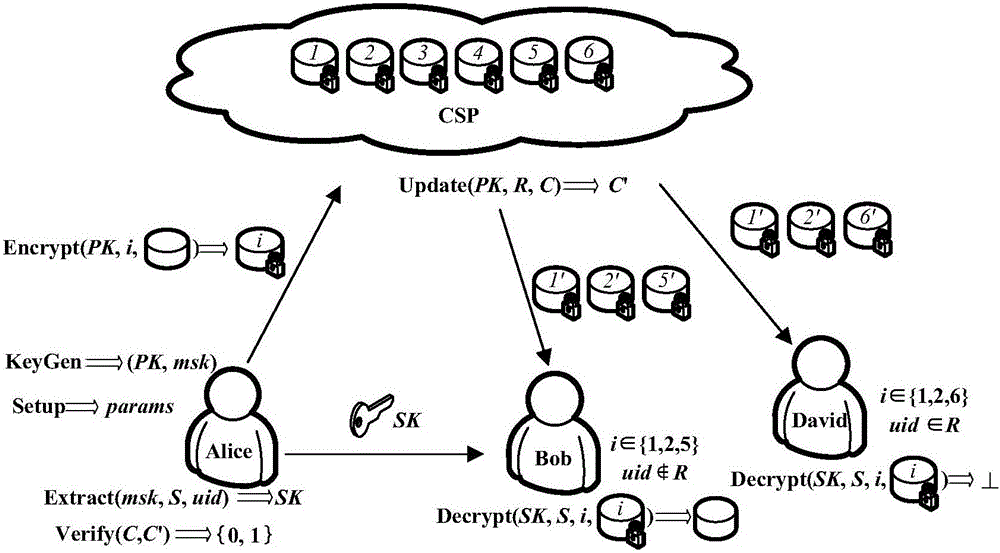
[0042] With the rapid development of network and storage technology, cloud storage has become a new service model, and data sharing is an important function of cloud storage. How to implement data sharing effectively, securely and flexibly; how to aggregate multiple decryption keys into a single key to minimize user key management costs and security risks; how to implement access control and revocation functions for users; If these problems are not solved, it is impossible to guarantee the security of cloud storage. Therefore, according to the characteristics of cloud storage, it is very necessary and urgent to study the corresponding security issues on this basis and establish an effective and secure key aggregation mechanism, which has important theoretical significance and application value.
[0043] In view of the above problems, this embodiment mainly studies the key aggregation mechanism in the cloud environment, and proposes a revocable key aggregation encryption method...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com