Mobile commerce identity authentication method
A technology for identity authentication and business, which is applied in the field of mobile business information security, and can solve the problems that the computing load does not meet the computing power of the mobile terminal, the decimal attack of the password sequence method, and the OTP method does not support two-way authentication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
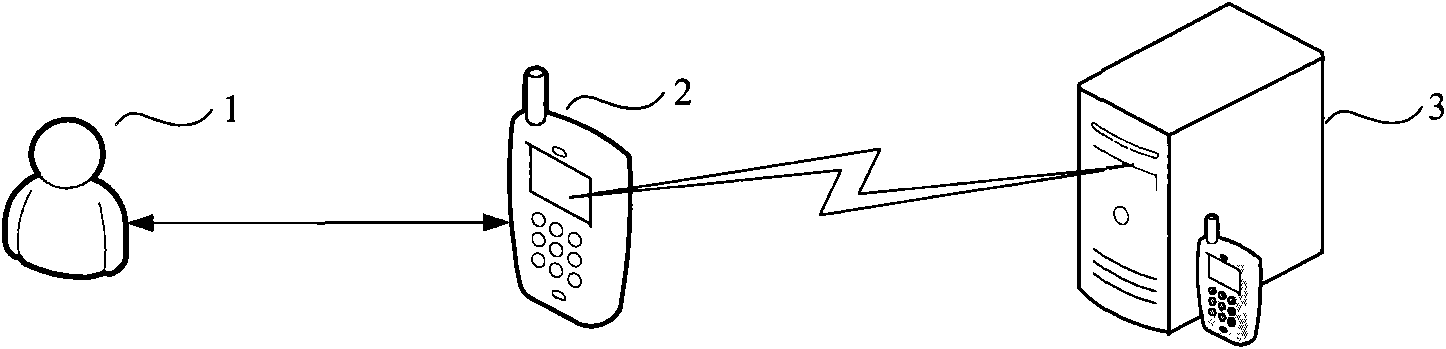
[0084] Authentication model schema such as figure 1 As shown, the model divides the authentication into two levels. The first level is the authentication of the identity of the user 1 by the mobile device 2, and the second level is the two-way identity authentication between the mobile device 2 and the authentication server 3. The first level verifies that the user 1 using the mobile device 2 is a legitimate user, and the second level verifies the legitimacy of the mobile device 2 and the authentication server 3, that is, it is not a counterfeit terminal. If the first-level verification fails, then the mobile device 2 and the authentication server 3 will not communicate. If the first-level verification is passed, the mobile device 2 automatically communicates with the authentication server 3, and the user 1 is invisible to the process and can only know whether the verification is passed.
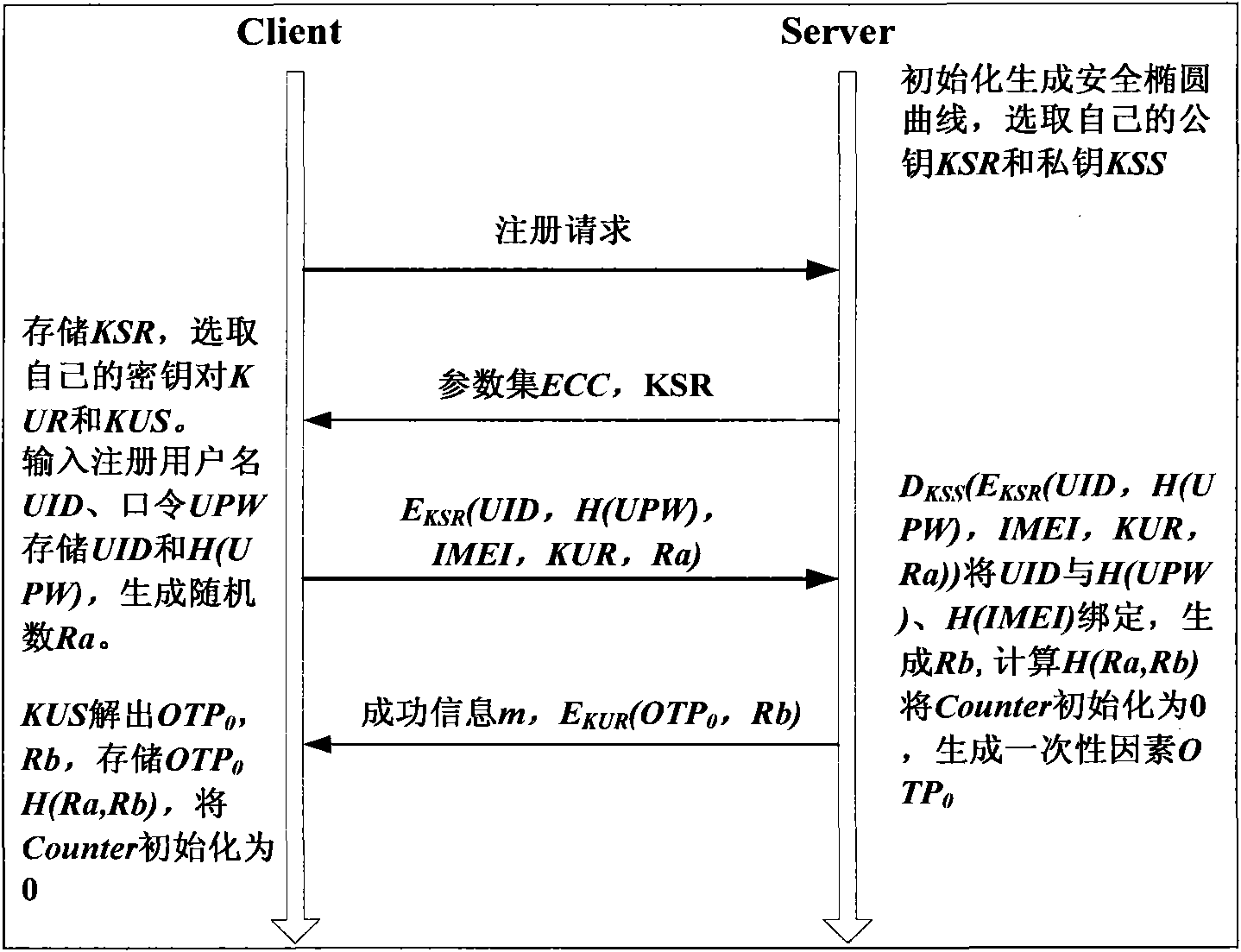
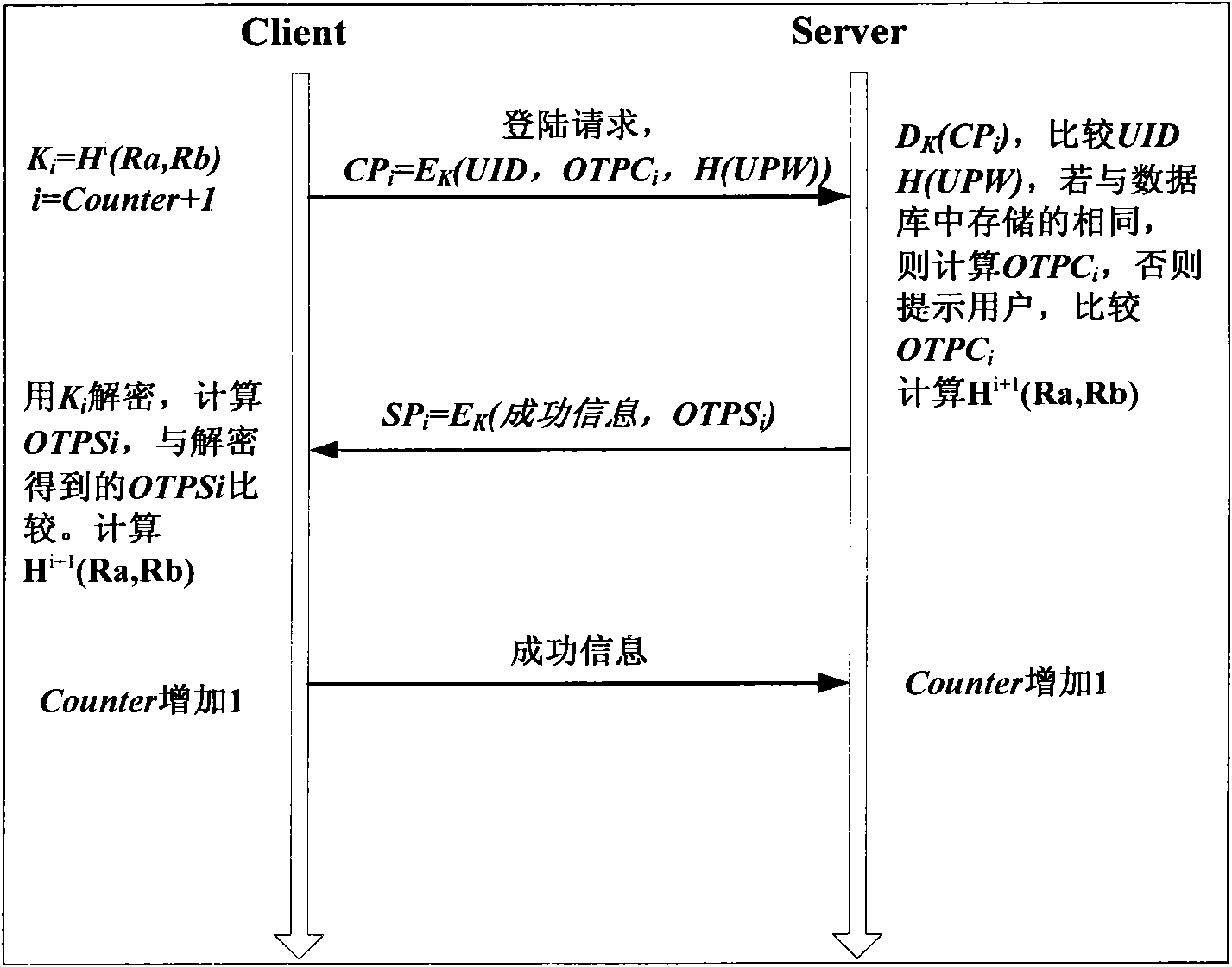
[0085] like Figures 2 to 4 They are the flow charts of the registration phase, login ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com