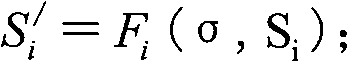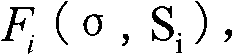Multicast data enciphered transmission method
A data encryption and data decryption technology, which is applied in the usage of multiple keys/algorithms, etc., can solve problems such as security risks, group key maintenance and complex management, and achieve security assurance, simple joining procedures, and simplified key management Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] Embodiment 1: Encrypted transmission applied to real-time data of stock trading
[0035] In stock trading, in order to ensure the security of data, the real-time data of stock trading must be encrypted by the stock trading center, and then transmitted to the stock trading points (a total of N) distributed all over the country through the network, and output after decryption at each trading point The real-time data in plain text is sent to each display terminal, that is, the real-time data is encrypted and transmitted through multicast. At present, this method of encrypted transmission adopts the group key method, that is, the stock exchange center distributes a group key to each trading point, and the sender and receiver of the data use this group key and a group key. A cryptographic algorithm performs encryption and decryption, and the group key is changed periodically. In this encrypted transmission, group members and any party who knows the group key can modify the ...
Embodiment 2
[0065] Embodiment 2: Applied to the real-time encrypted transmission of audio and video data of the multimedia conference system
[0066]Multimedia conferencing systems are most widely used in e-government affairs. In order to ensure that the content of the conference, that is, the audio and video data, is not known to unauthorized persons during the transmission process, the audio and video data transmitted in the conference is usually encrypted for transmission. Most of the methods used are group encryption. key network multicast method, that is, the conference center uses the group key agreed in advance, and adopts a block cipher algorithm such as 3DES or AES, etc., to encrypt the audio and video data of the conference content, and send them out through the network; each branch venue uses the same The group key is decrypted, and the corresponding audio and video plaintext information is displayed on the terminal. The potential safety hazards in this group key multicast mode...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com