A data access control method and system
A data access control and data technology, applied in the field of cloud computing, can solve problems such as high computing overhead, achieve the effects of improving efficiency, simplifying key management, and improving data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
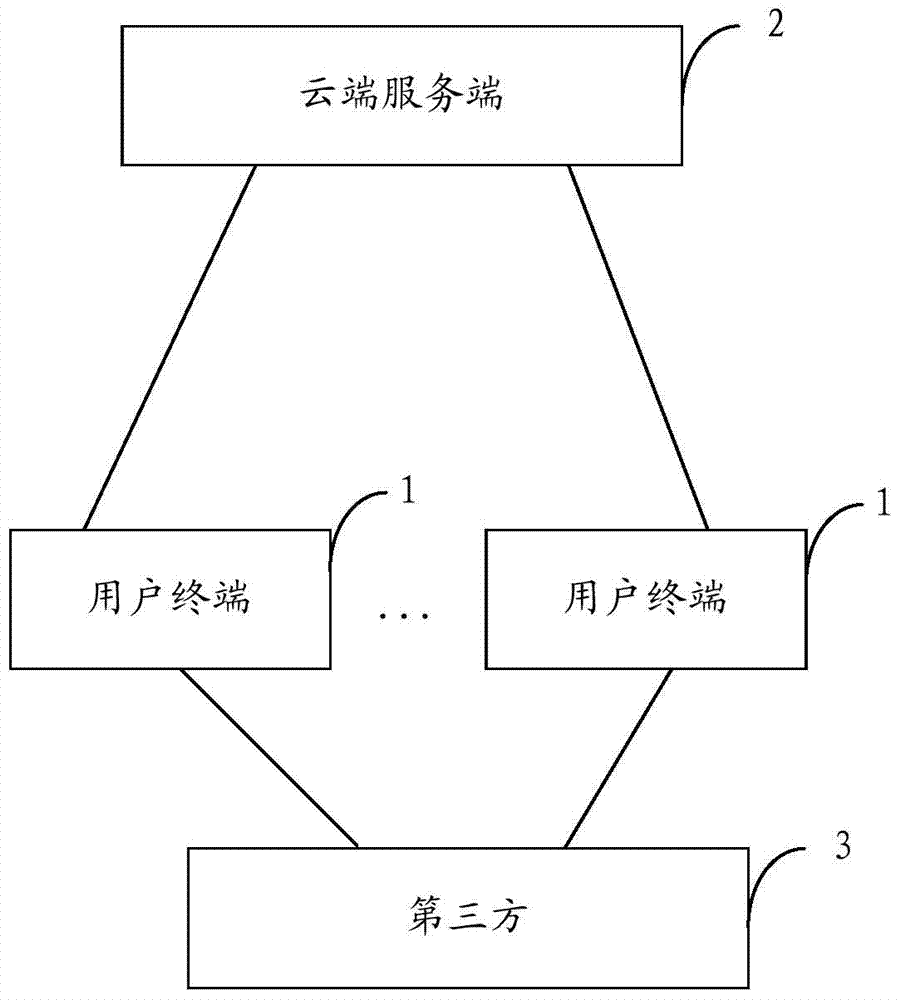
[0019] figure 1 It shows the applicable application scenarios of the data access control system provided by the first embodiment of the present invention, and for the convenience of description, only the part related to the embodiment of the present invention is shown.
[0020] like figure 1 As shown, the data access control system includes a plurality of user terminals 1 , a cloud server 2 and a third party 3 . The plurality of user terminals 1, cloud server 2 and third party 3 are connected and communicated in a wired or wireless manner.
[0021] Wherein, the user terminal 1 may be a mobile phone, a tablet computer, a computer, and the like.
[0022] The cloud server 2 and the third party 3 can be a single server, or a server composed of several functional servers.
[0023] In a multi-authority or multi-level organizational structure (such as in a hospital, including the dean, department director, chief doctor, attending doctor, etc.; in an enterprise, including general m...
Embodiment 2
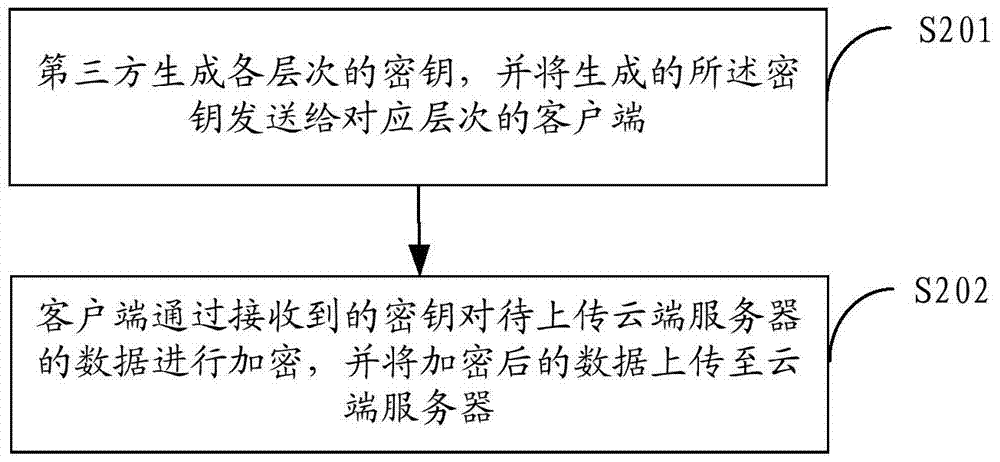
[0041] figure 2 The implementation flow of the data access control method provided by the second embodiment is shown, and the process of the method is described in detail as follows:
[0042] In step S201, the third party generates keys of each level, and sends the generated keys to clients of corresponding levels.
[0043] In this embodiment, the third party is a trusted (securely authenticated) third party. Specifically, the third party generates keys (including public keys and private keys) at each level based on the hierarchical access control model, and sends the generated keys to clients of corresponding levels.
[0044]Wherein, this embodiment includes at least a first level (level with higher authority) and a second level (level with lower authority), and user terminals at corresponding levels include user terminals at the first level and user terminals at the second level. The division of specific levels can be adjusted according to actual needs, which is not limit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com