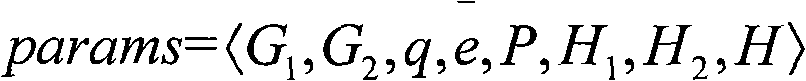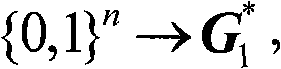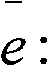Access authentication method, equipment and system of P2P (peer-to-peer) network
A technology of P2P network and network equipment, which is applied in the field of access authentication of P2P network, can solve the problems of complex key management work, heavy burden of certificate management work, complex access authentication method and mechanism, etc., and achieve simplified process and access authentication The effect of easy work and simple key management
Inactive Publication Date: 2010-08-25
HUAWEI TECH CO LTD
View PDF4 Cites 19 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
In the prior art, the access authentication method of the P2P network has a complex mechanism. With the increasing communication between interconnected devices, the burden of PKI certificate management is becoming heavier and the key management work is becoming more and more serious. complex
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment 1
Embodiment 2
Embodiment 3
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention discloses access authentication method, equipment and system of a P2P (peer-to-peer) network, belonging to the technical field of network communication. Network equipment in the P2P network is subjected to access authentication by adopting an identity-based public key IBC (Information Bearer Channel) mechanism. The method comprises the following steps of: receiving an access requesttransmitted by opposite terminal network equipment by home terminal network equipment; selecting a private key from the private keys of the home terminal network equipment as a conversation private key of the home terminal network equipment according to the private key level of the home terminal network equipment and the private key level of the opposite terminal network equipment; calculating a conversation main key of the home terminal network equipment according to the conversation private key of the home terminal network equipment, the identity information of the opposite terminal networkequipment corresponding to the conversation private key of the home terminal network equipment, a first negotiation parameter and a second random number determined by the home terminal network equipment; and returning an access response to the opposite terminal network equipment. By utilizing the IBC mechanism, distributed access authentication under the P2P network mode is solved, thus the IBC mechanism is particularly suitable for the P2P network.
Description
technical field The present invention relates to the field of communication technology, in particular to a P2P (Peer to Peer, peer-to-peer) network access authentication method, equipment and system. Background technique P2P network is a network that directly connects people and allows people to interact directly through the Internet. The P2P network gets rid of the traditional C (Client, client) / S (Server, server) mode of service, so that each user in the network can exchange data and make full use of the resources at the edge of the network. A typical P2P network is a wireless Mesh (mesh) network. The wireless Mesh network is composed of a group of MPs (Mesh Points, mesh network nodes) distributed in a mesh shape, and each MP is interconnected through a wireless relay link in a P2P manner. The multi-hop connection of the wireless Mesh network will become the development trend of the next-generation wireless communication network, which can provide users with truly ubiqui...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): H04W12/04H04W12/06H04L29/06H04L29/08H04W84/18
Inventor 江为强杨亚涛周元樊唱东辛阳李雪莲白媛谷勇浩
Owner HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com