File encryption and decryption system based on c/s architecture and speaker recognition technology
A technology for speaker recognition and file encryption, which is used in instruments, digital data authentication, computing, etc. to ensure security, improve robustness, and reduce load.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below with reference to the accompanying drawings.
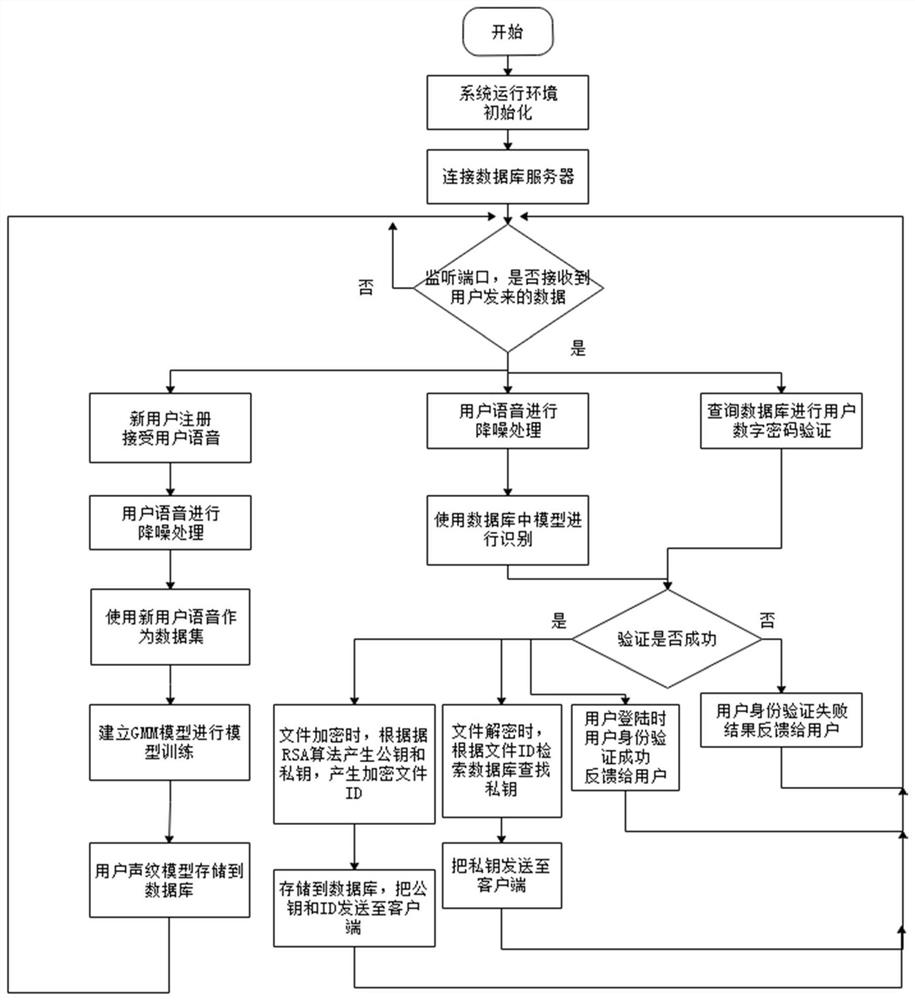
[0029] A file encryption decryption system based on C / S architecture and speaker recognition technology, mainly simplifies the operation of the client, and users only need to make the file to encrypt or decrypt the files to protect the user's personal file security and Personal privacy, which will be further described below with reference to the accompanying drawings and examples.
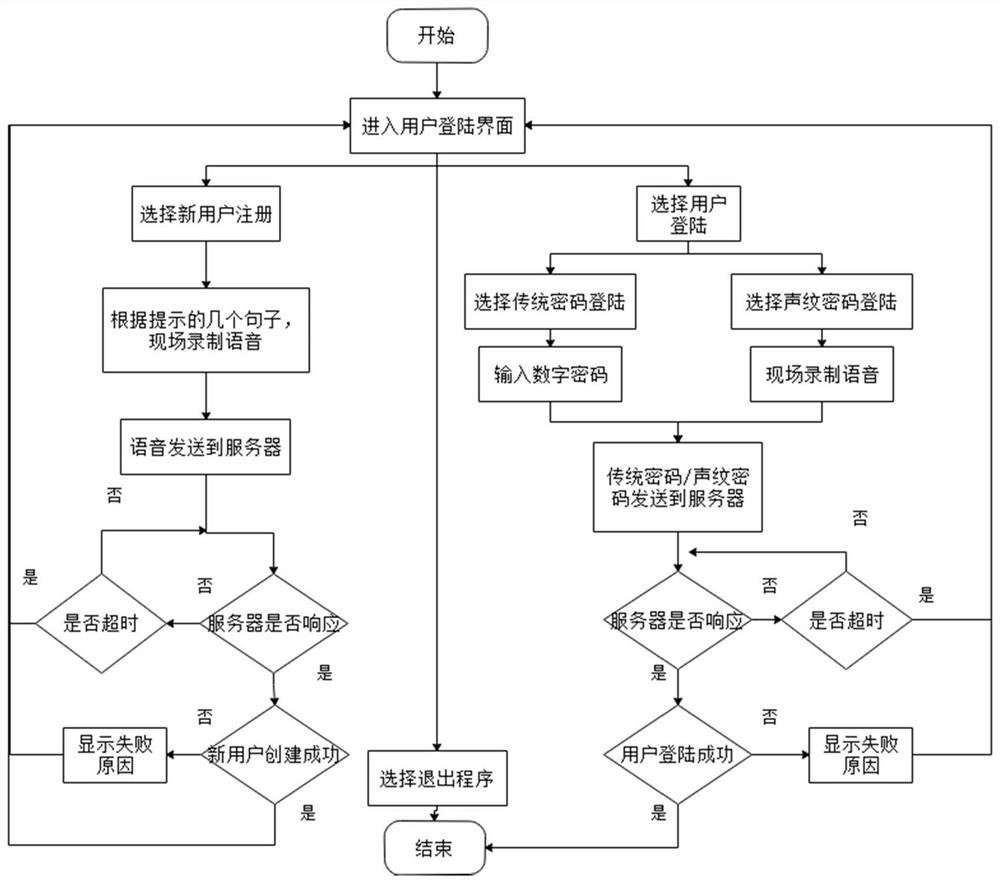
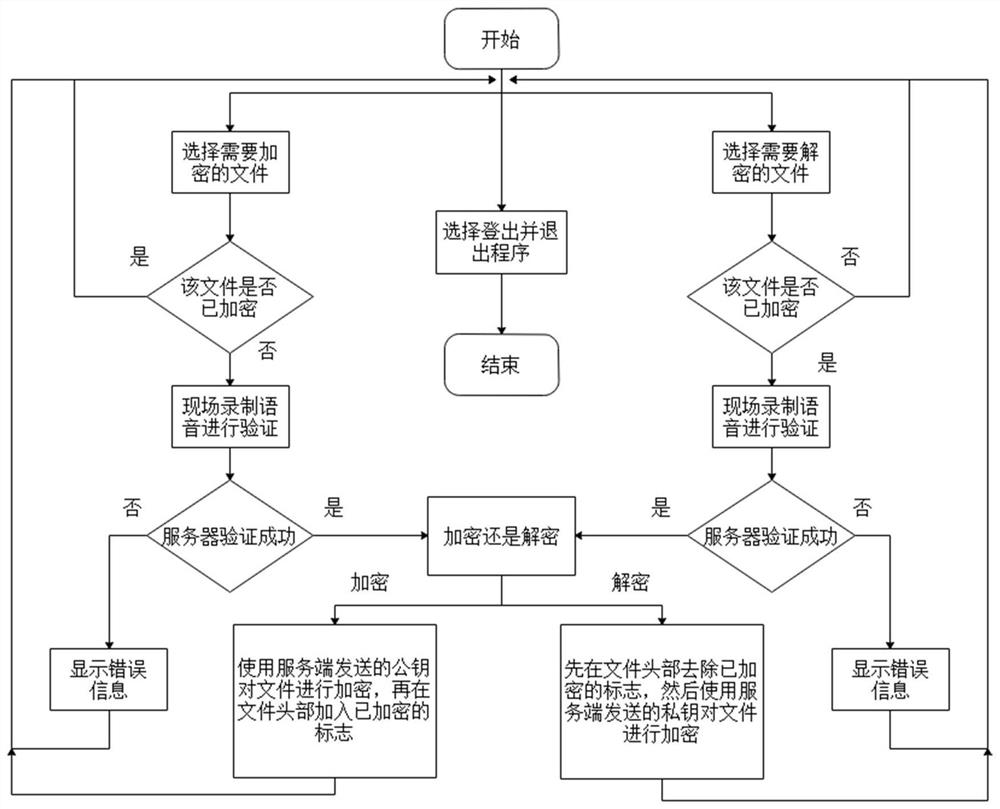
[0030] Client includes user login interface module, new user registration module, old user login module, file encryption, and decryption module, field voice acquisition module;
[0031] like figure 1 As shown, the user login interface module provides a channel for new user registration channels and old users log in;
[0032] The new user registration module has the following functions:
[0033] A. User Enter the username and password to register
[0034] Providing another user login method, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com