Encryption/decryption method, encryption/decryption system, and encryption/decryption device for information transmission
A technology for information transmission, encryption and decryption, applied in transmission systems, electrical components, etc., can solve problems such as difficulty in ensuring user information security and self-theft, unfavorable storage and management of private information, limited usable range, etc., to increase password diversity and randomness, Easy encryption and decryption, easy to use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
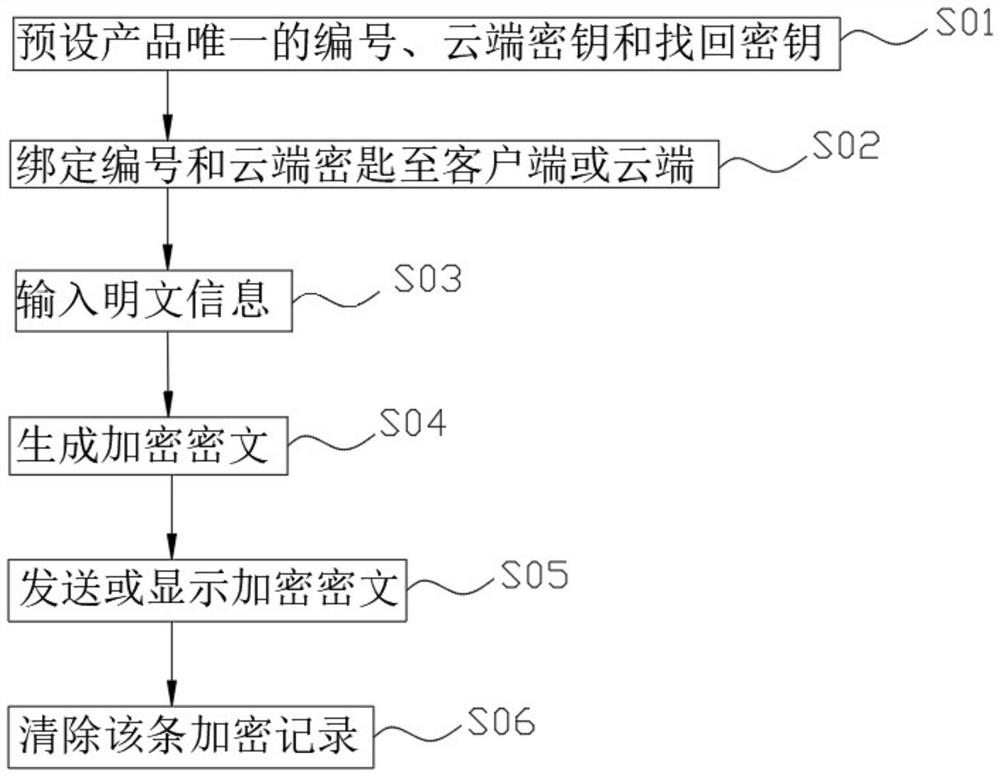
[0071] An encryption and decryption method for information transmission, including an encryption step, specifically: binding through a product number, inputting plaintext information for encryption, sending or displaying encrypted ciphertext through the product, and clearing encrypted records;
Embodiment 2
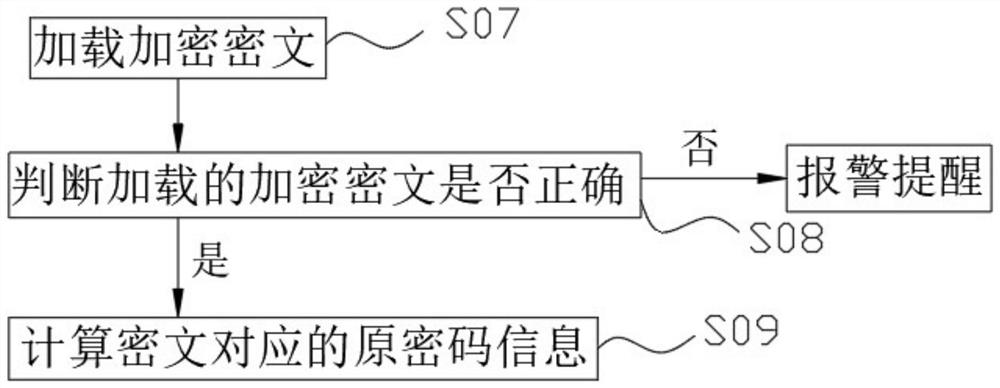
[0073] An encryption and decryption method for information transmission, the decryption step specifically includes: loading encrypted ciphertext, judging whether the encrypted ciphertext is correct, decrypting if correct, and alarming if wrong.
Embodiment 3
[0075] An encryption and decryption method for information transmission, comprising an encryption step and a decryption step, wherein:
[0076] Encryption steps: Bind by product number, enter plaintext information for encryption, send or display encrypted ciphertext through this product, and clear encrypted records;
[0077] Decryption step: load the encrypted ciphertext, and judge whether the encrypted ciphertext is correct, if it is correct, decrypt it, and if it is wrong, it will alarm and remind.
[0078] The purpose of the above three embodiments is to increase the security of account passwords and information storage by encrypting the original password twice, increase the diversity and randomness of account passwords, manage the stored information and encryption and decryption methods separately, and combine virtual and real information. , while decryption is convenient.
[0079] In above-mentioned embodiment 1 and embodiment 3, such as figure 1 As shown, the encryptio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com