A trusted network connection system for security enhancement
一种网络连接、安全性的技术,应用在可信网络连接系统领域,能够解决平台完整性评估不对、背景技术安全性低、无法验证AIK证书有效性等问题,达到简化密钥管理及完整性校验机制、提高安全性、简化密钥管理的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Since most of the existing networks are deployed using the TCG-TNC architecture, especially the wired network, the present invention is a trusted network connection architecture with enhanced security built on the TCG-TNC architecture.
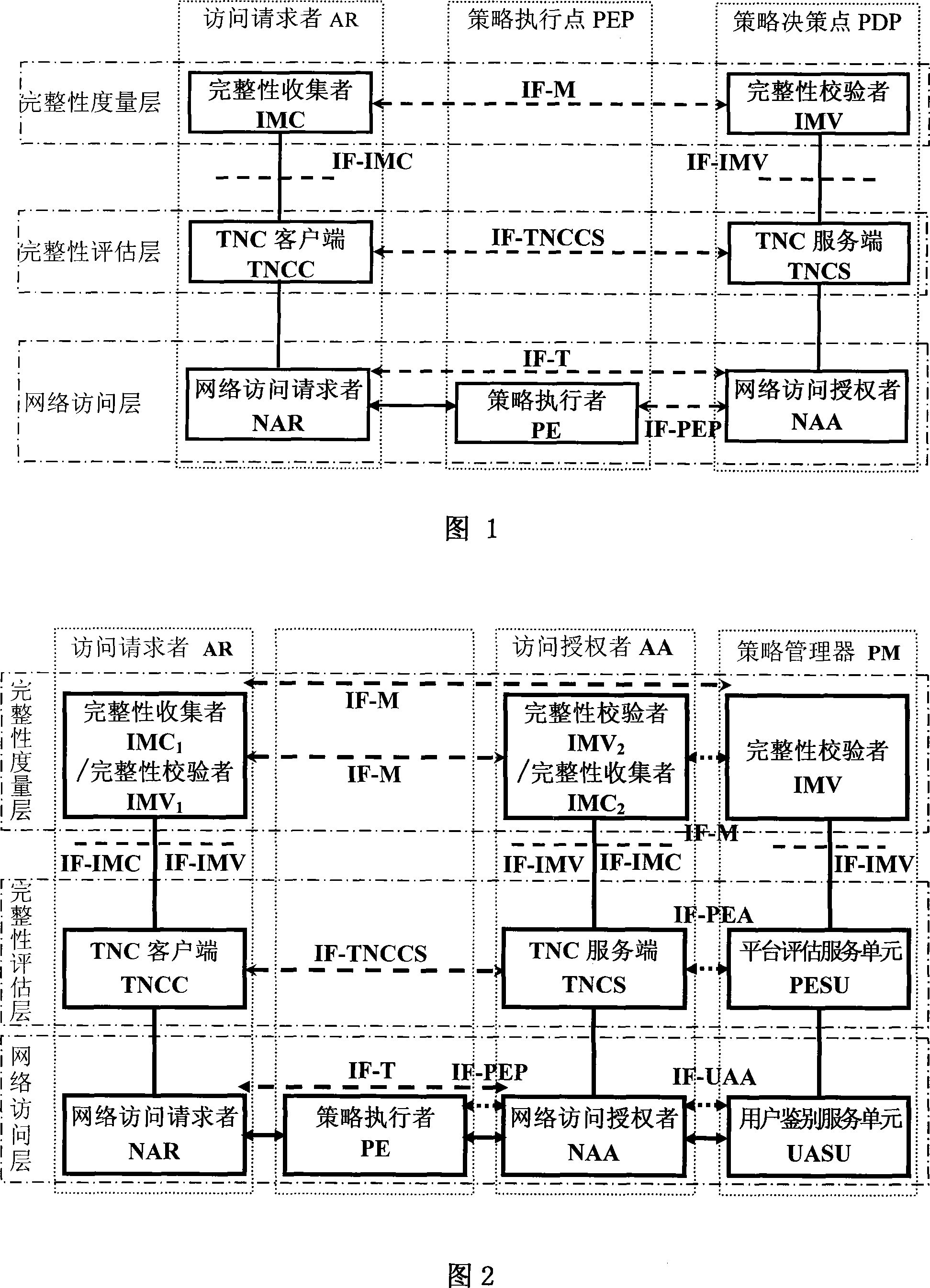
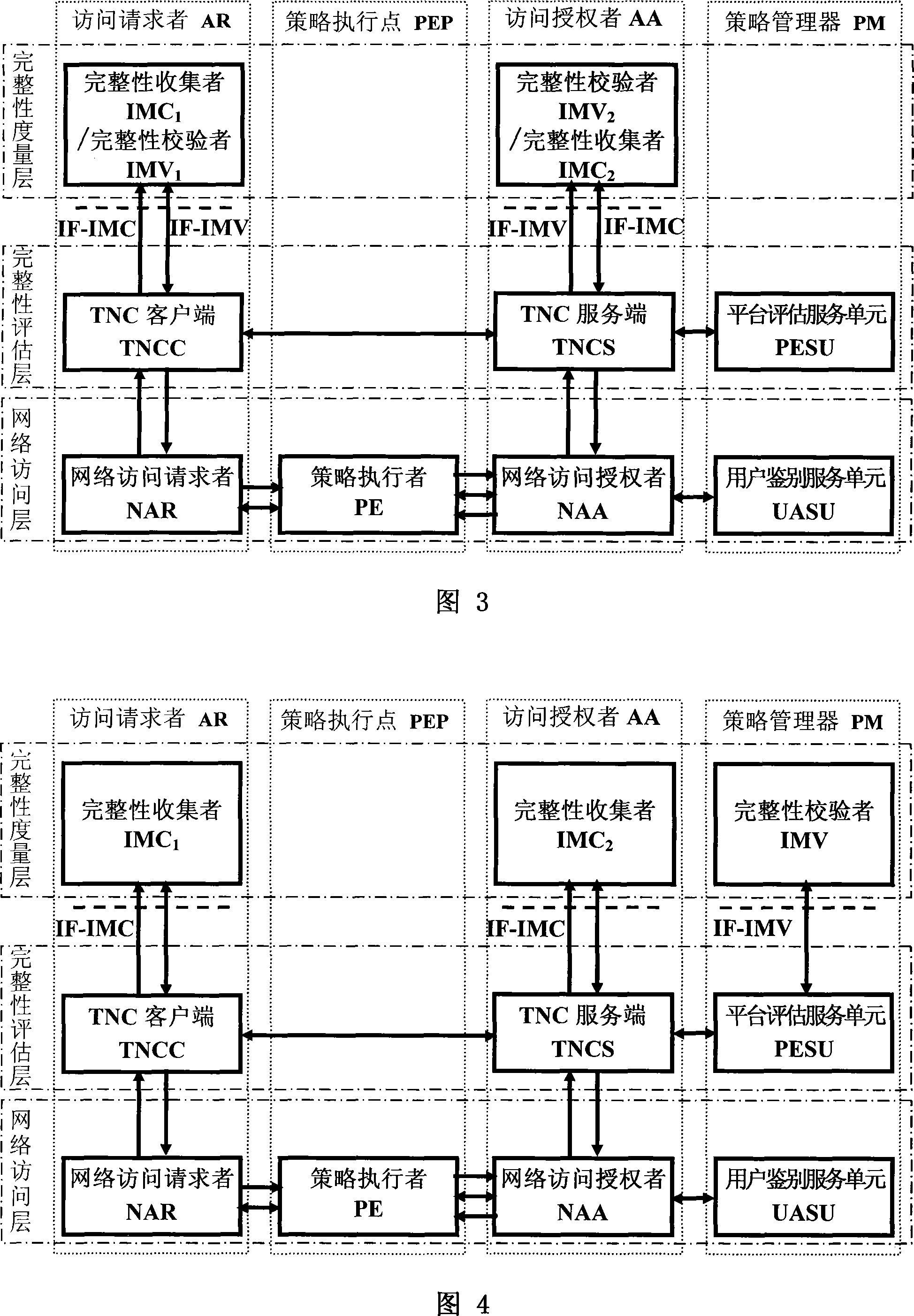
[0035] Referring to Fig. 2, the present invention is mainly composed of four logical entities: an access requester AR, a policy enforcement point PEP, an access authorizer AA and a policy manager PM, which can be distributed anywhere in the network. The access requester AR is also called requester, user station, etc., and the policy manager PM is also called authentication server, trusted server, background server, etc. The access requester AR and the policy enforcement point PEP are connected to the network through the authentication protocol, the policy enforcement point PEP and the access authorizer AA are connected through the network through the policy enforcement interface IF-PEP, and the access requester AR and the access authoriz...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com