Network real-name system implementing method
An implementation method and technology of real-name system, applied in the field of information security, can solve the problems of high price, inability to achieve large-scale authentication, high establishment cost and maintenance cost, and achieve the effect of improving the efficiency of authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
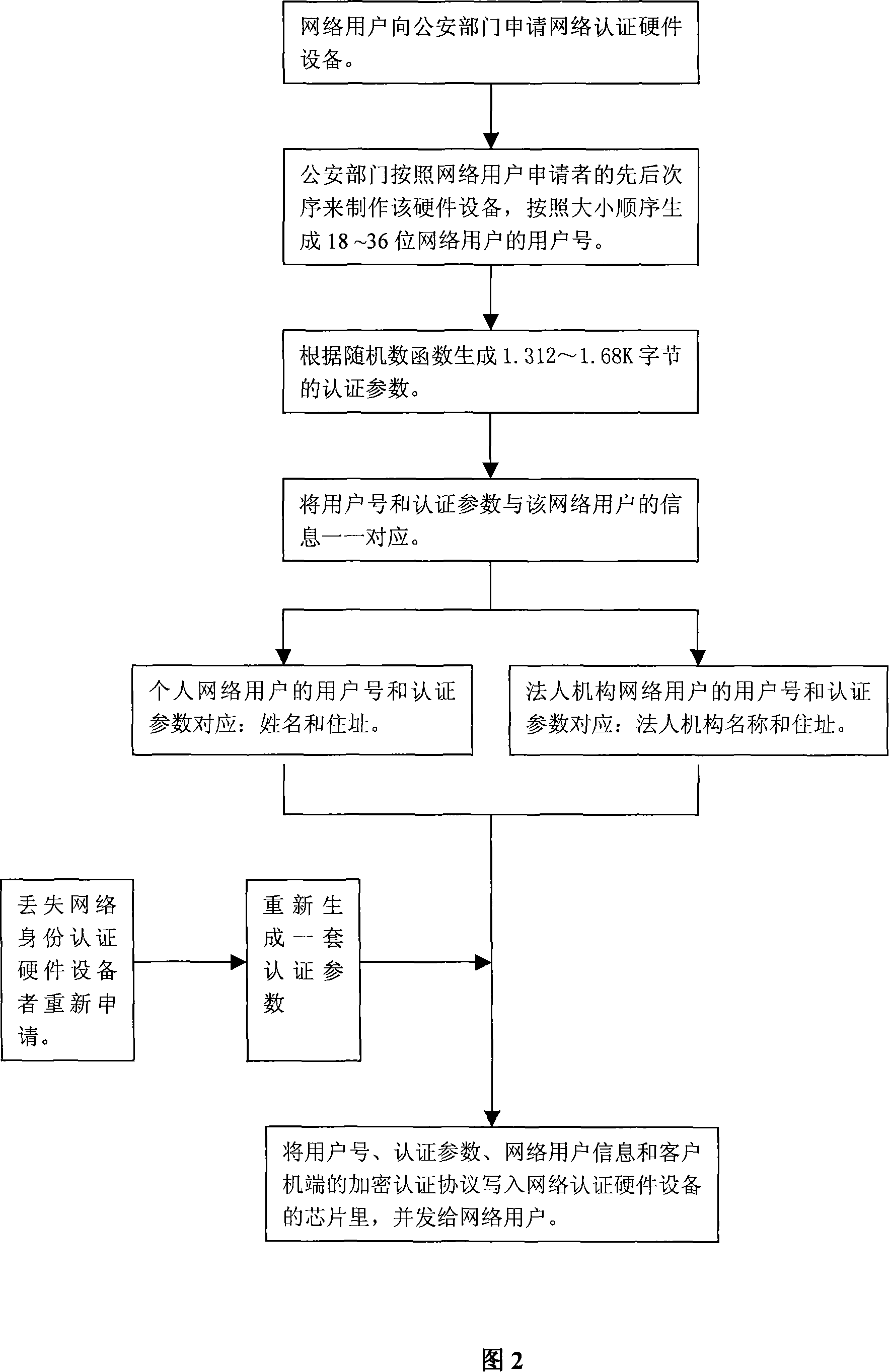
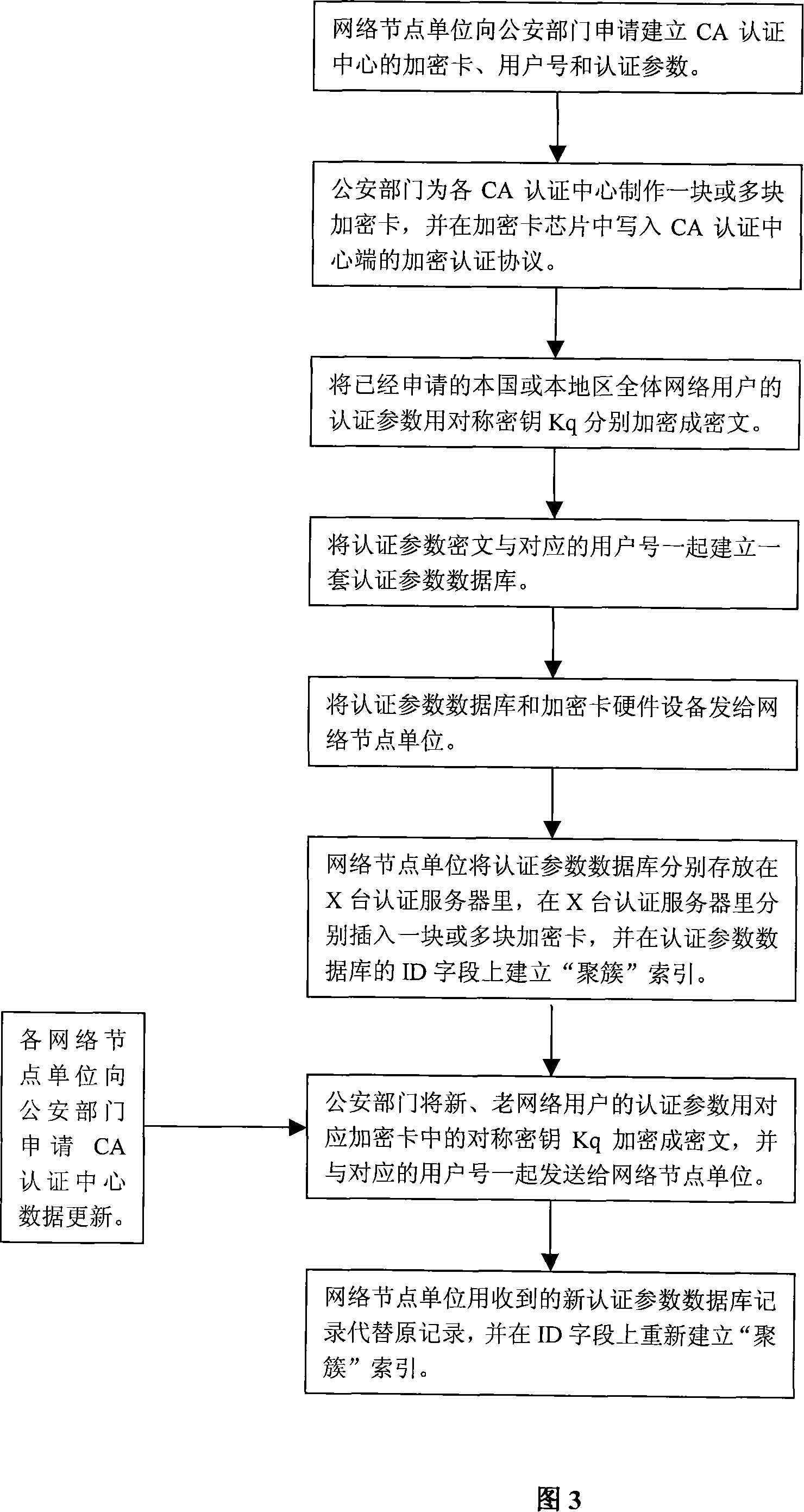
[0045] The implementation steps of the network real-name system are described below in conjunction with the accompanying drawings:
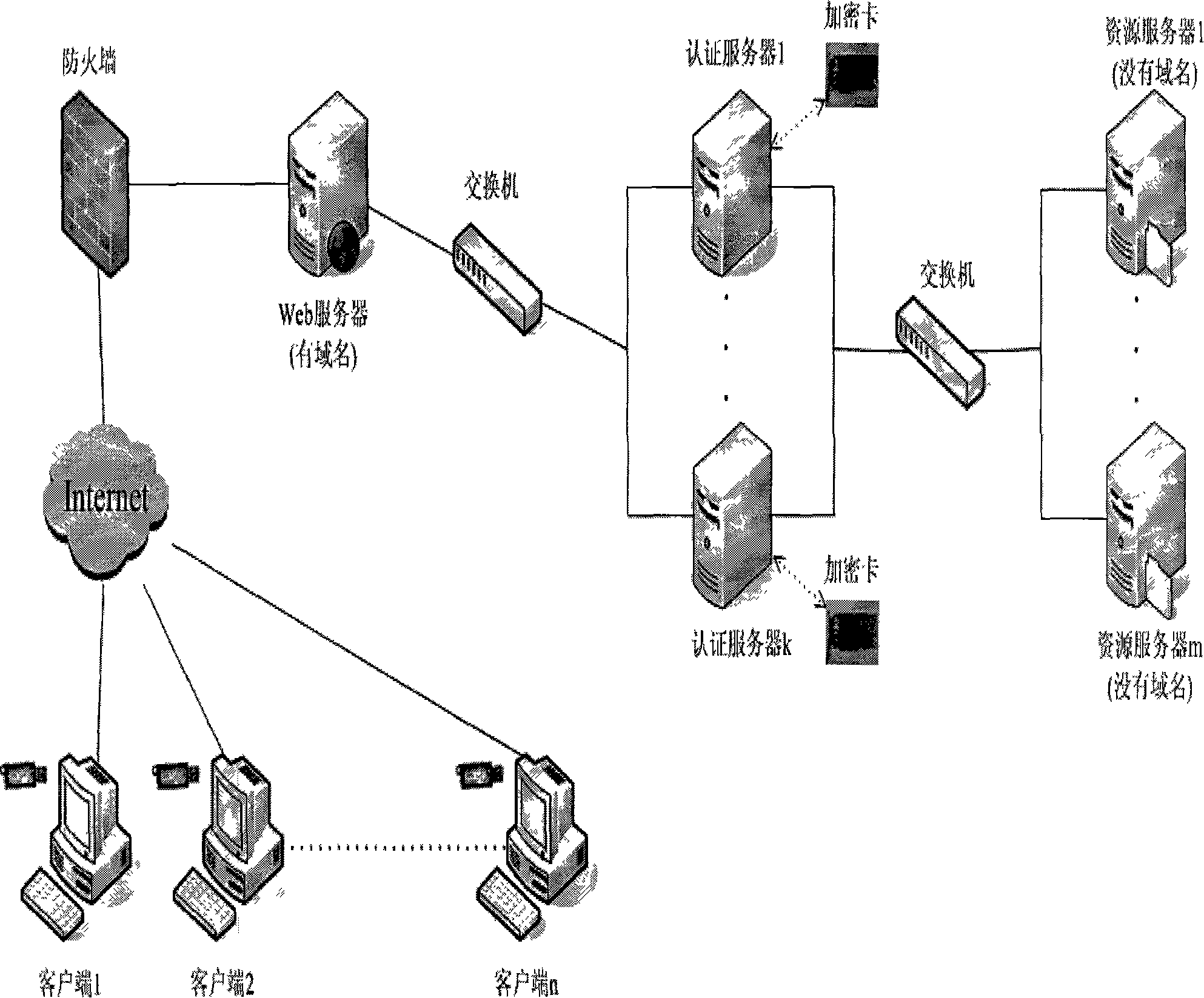
[0046] Figure 1: It illustrates the architecture of the network real-name system to establish a CA certification center on the network node. At the client side, each network user has a network authentication hardware device and plugs it into the client computer, and logs in to the WEB server of the network node through the Internet network. The WEB server connects the network The identity authentication task is handed over to the CA certification center. Only legitimate users who have passed the certification of the CA certification center can enter the resource or application server on the network node. The three parts of the WEB server, the CA certification center and the resource or application server are connected in series. , wherein: the CA certification center is composed of 1~K (K≤30) authentication servers, each authentication server is i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com