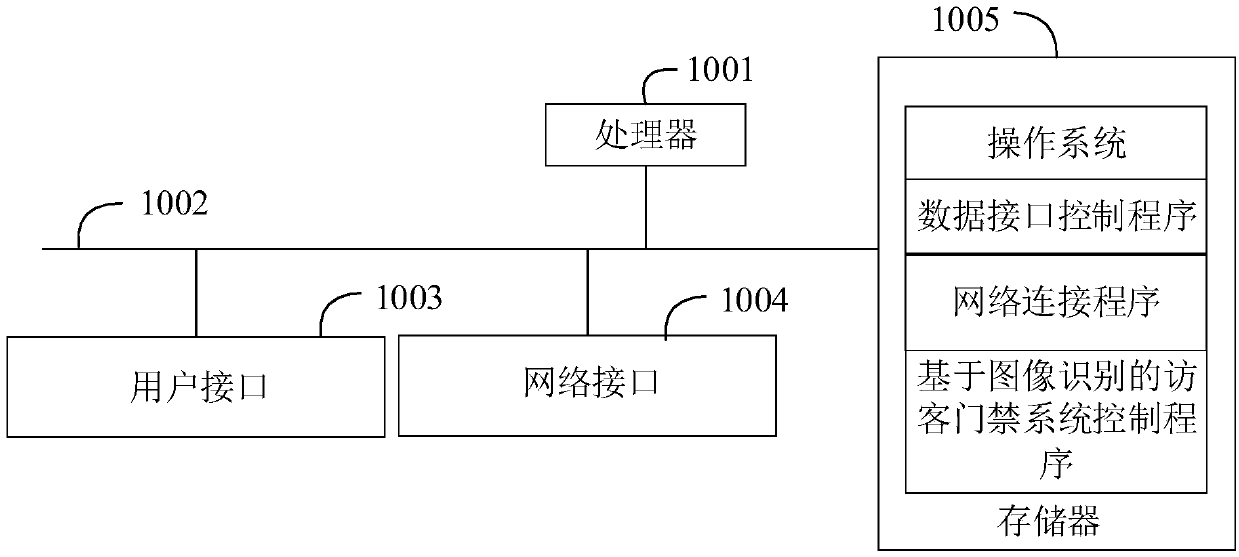
Method and device for controlling visitor access control system based on image recognition
A visitor access control and image recognition technology, which is applied in biometric recognition, character and pattern recognition, instruments, etc., can solve problems such as inconvenient, poor user experience, and low unlocking efficiency, so as to avoid cumbersome steps, improve user experience, The effect of improving certification and management efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
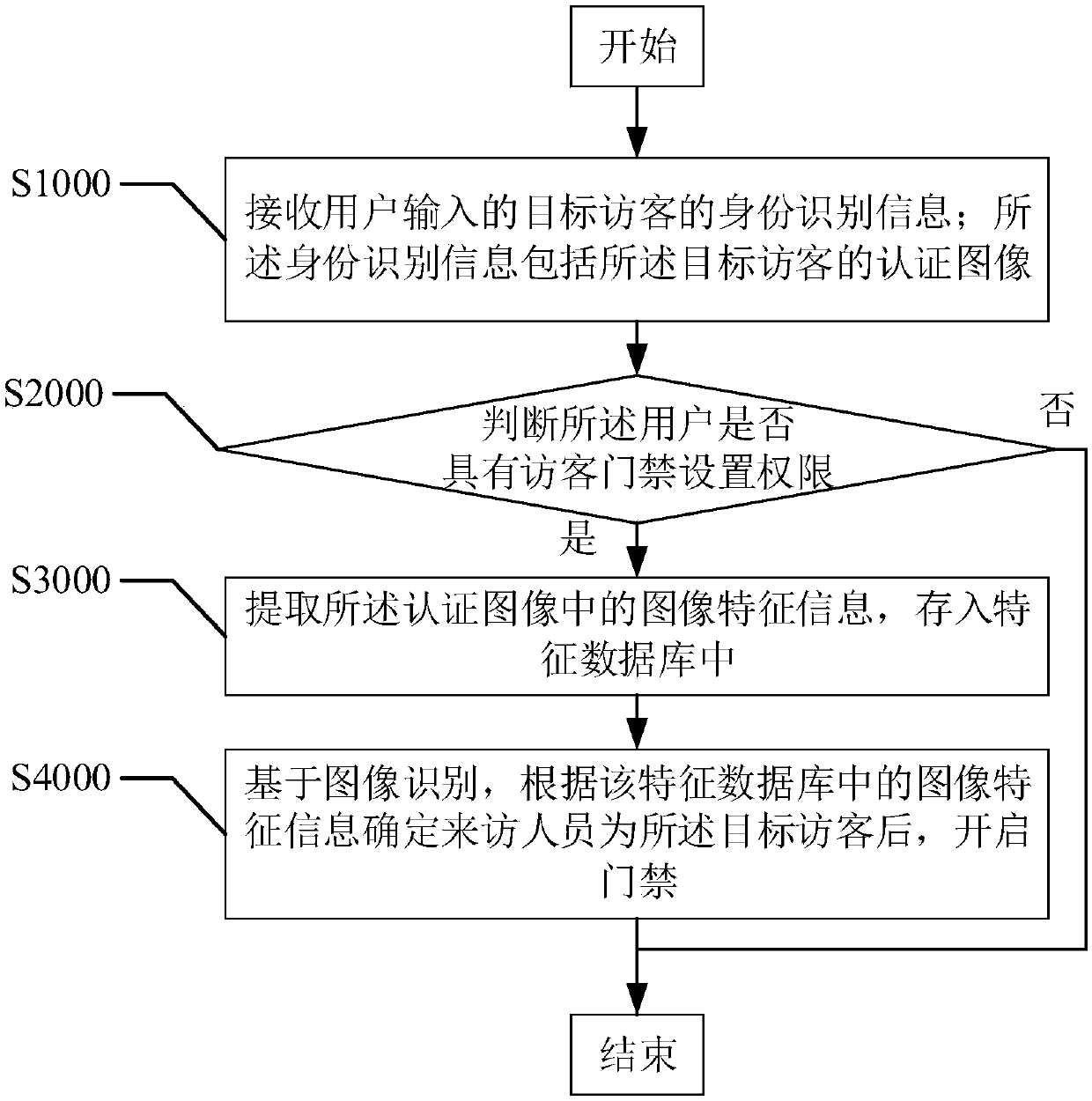
[0067] refer to figure 2 , the first embodiment of the present invention provides an image recognition-based visitor access control system control method, which is applied to a target area equipped with an image recognition-based visitor access control system, including:
[0068] Step S1000, receiving the identification information of the target visitor input by the user; the identification information includes the authentication image of the target visitor;
[0069] As mentioned above, the access control method provided in this embodiment can be applied to a target area equipped with an image recognition-based visitor access control system, wherein the target area is a safe area with access control, such as a community, property, unit, Warehouses, companies, etc. need access control areas. For example, in a community, when a target user known by the owner needs to enter the community, the owner can enter the relevant information of the target user to realize intelligent ide...
Embodiment 2
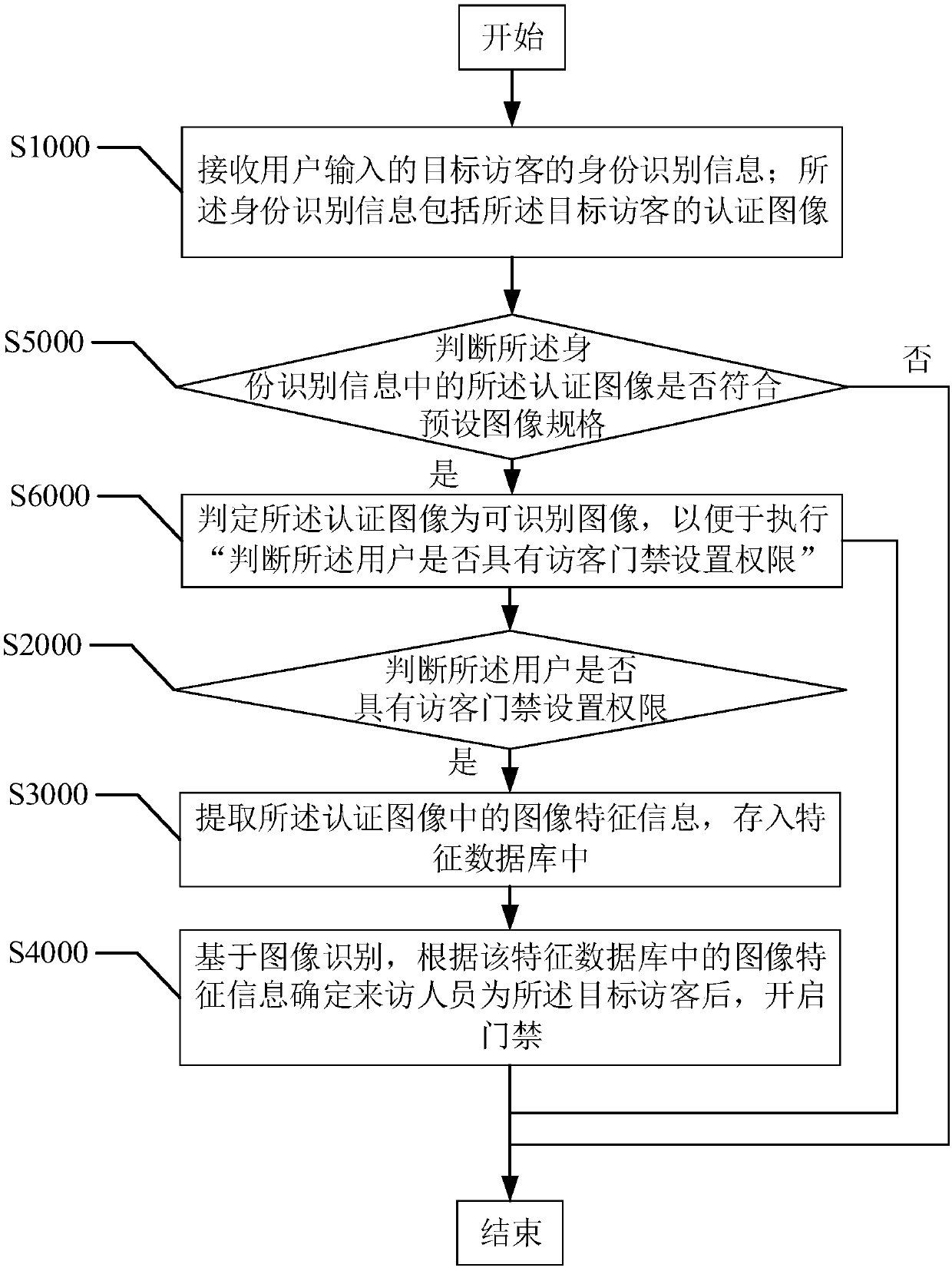
[0083] refer to image 3 , the second embodiment of the present invention provides an image recognition-based visitor access control system control method, based on the above figure 2 In the first embodiment shown, the step S2000, before "judging whether the user has the visitor access control setting authority", also includes:
[0084] Step S5000, judging whether the authentication image in the identification information conforms to a preset image specification;
[0085] Step S6000, if the authentication image conforms to the preset image specification, determine that the authentication image is an identifiable image, so as to perform "judging whether the user has the visitor access control setting authority".
[0086] As mentioned above, the authentication image of the target visitor provided by the user may have blurring, low resolution, ghosting, off-center image, and portraits of people in the overall image due to differences in image acquisition methods, channels, angl...
Embodiment 3
[0089] refer to Figure 4-6 , the third embodiment of the present invention provides an image recognition-based visitor access control system control method, based on the above figure 2 In the first embodiment shown, the step S4000, "based on image recognition, according to the image feature information in the feature database, after determining that the visitor is the target visitor, open the access control" includes:
[0090] Step S4100, after the visitor is detected to enter the image collection area, image collection is performed on the visitor to obtain an identity recognition image;
[0091] As mentioned above, the image collection of visitors can be collected through image collection equipment, such as high-definition cameras, cameras and other equipment.
[0092] Step S4200, perform image recognition on the identity recognition image, and if it is determined through image recognition that the visitor is the target visitor, unlock the access control.
[0093] As ment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com