Distributed cloud authentication system based on random instruction, apparatus and method thereof
A distributed, cloud authentication technology, applied in the transmission system, electrical components, etc., can solve the problems of slow authentication, long authentication time, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
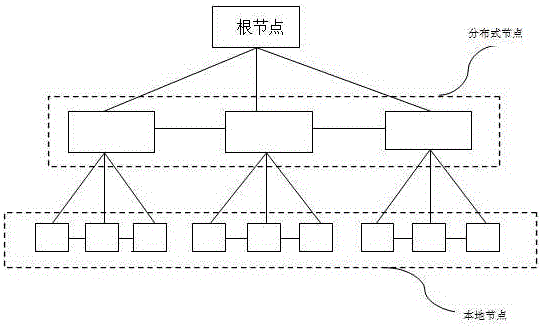
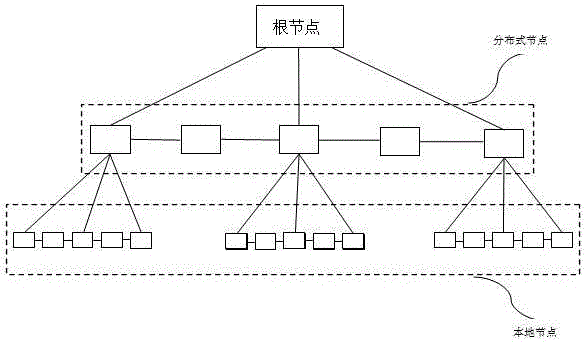
[0119] A distributed cloud authentication system based on random instructions, including: a terminal, a root node, a distributed node and a local node. It is characterized by:
[0120] The root node does not authenticate the authentication information sent by the terminal, but randomly instructs the distributed nodes to perform authentication and sends the authentication information to the distributed nodes.
[0121] The distributed nodes send the authentication result to the root node.
[0122] The root node judges the result sent by the distributed node according to a preset threshold, and sends the judgment result to the terminal.
[0123] Further, the root node judging the results sent by the distributed nodes according to the preset threshold includes: the root node makes a judgment according to the number of certified distributed nodes specified by the root node, for example, the certified distributed nodes If the number is greater than half of the number of distribute...
Embodiment 2
[0131] Such as figure 1 As shown, the number of distributed nodes is 3, and the number of distributed nodes randomly instructed by the root node is 3.
[0132] Further, the root node judging the results sent by the distributed nodes according to the preset threshold includes: the root node makes a judgment according to the number of passed distributed nodes specified by the root node, that is, 3, for example, the certified distributed node The number of nodes is greater than one-half of the specified number of distributed nodes 3 or 3 / 2, because the number of servers is an integer, which is an integer greater than one-half of the specified number of distributed nodes 3 or 3 / 2 2, that is, at this time, as long as the number of distributed nodes that pass the authentication is 2, it is determined that the authentication is passed, such as the number of distributed nodes that pass the authentication is less than one-half of the number of distributed nodes specified by it 3, that ...
Embodiment 3
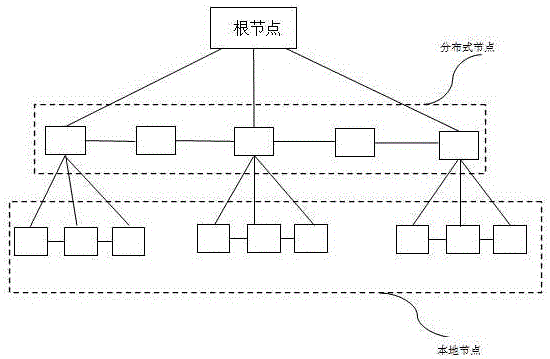
[0134] Such as figure 2 As shown, the number of distributed nodes is 5, and the number of distributed nodes randomly instructed by the root node is 3.
[0135] Further, the root node judging the results sent by the distributed nodes according to the preset threshold includes: the root node makes a judgment according to the number of passed distributed nodes specified by the root node, that is, 3, for example, the certified distributed node The number of nodes is greater than one-half of the specified number of distributed nodes 3 or 3 / 2, because the number of servers is an integer, which is an integer greater than one-half of the specified number of distributed nodes 3 or 3 / 2 2, that is, at this time, as long as the number of distributed nodes that pass the authentication is 2, it is determined that the authentication is passed, such as the number of distributed nodes that pass the authentication is less than one-half of the number of distributed nodes specified by it 3, that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com