Slave device authentication method and system for master device
An authentication method and master device technology, which is applied in user identity/authority verification and key distribution, can solve the problems that counterfeiters are difficult to imitate, only consider authentication, increase manufacturing costs, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
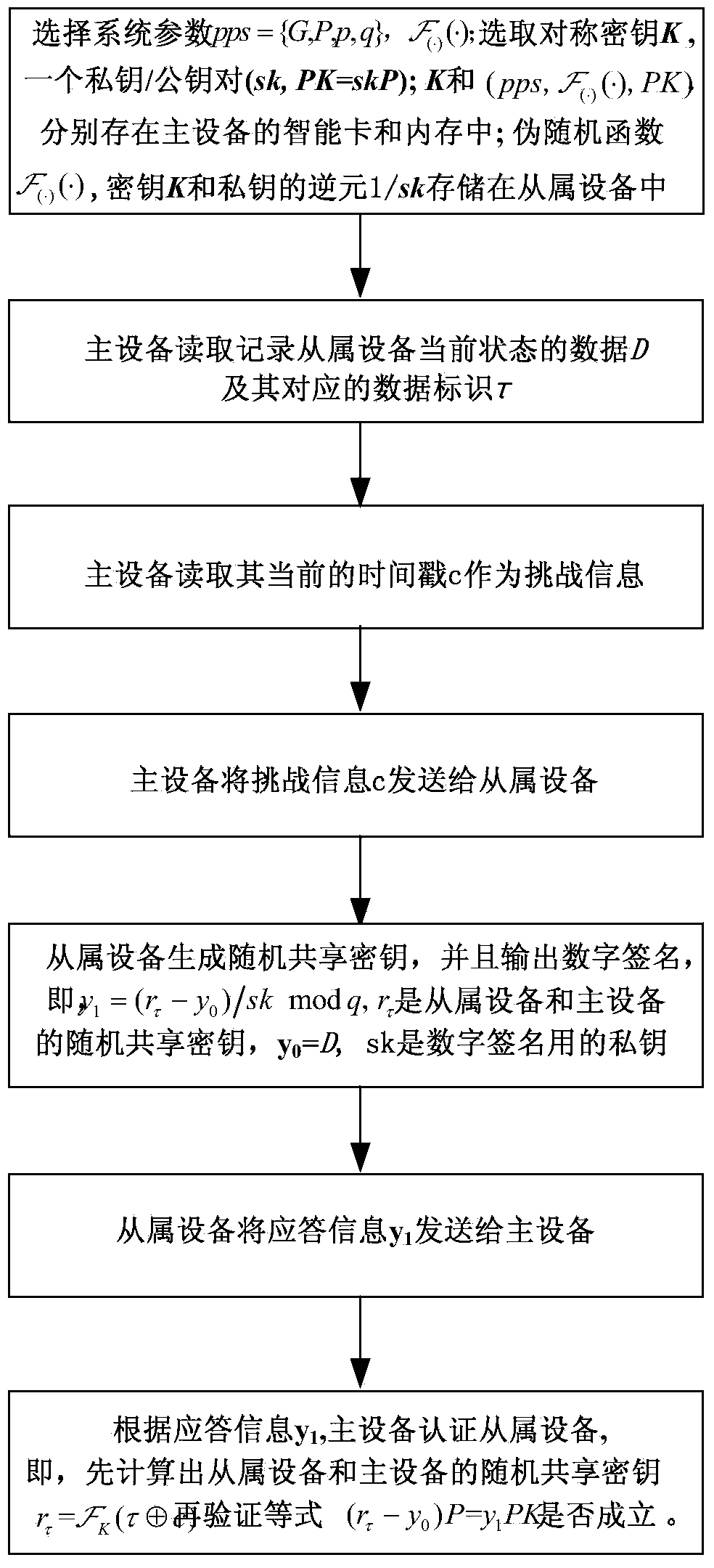
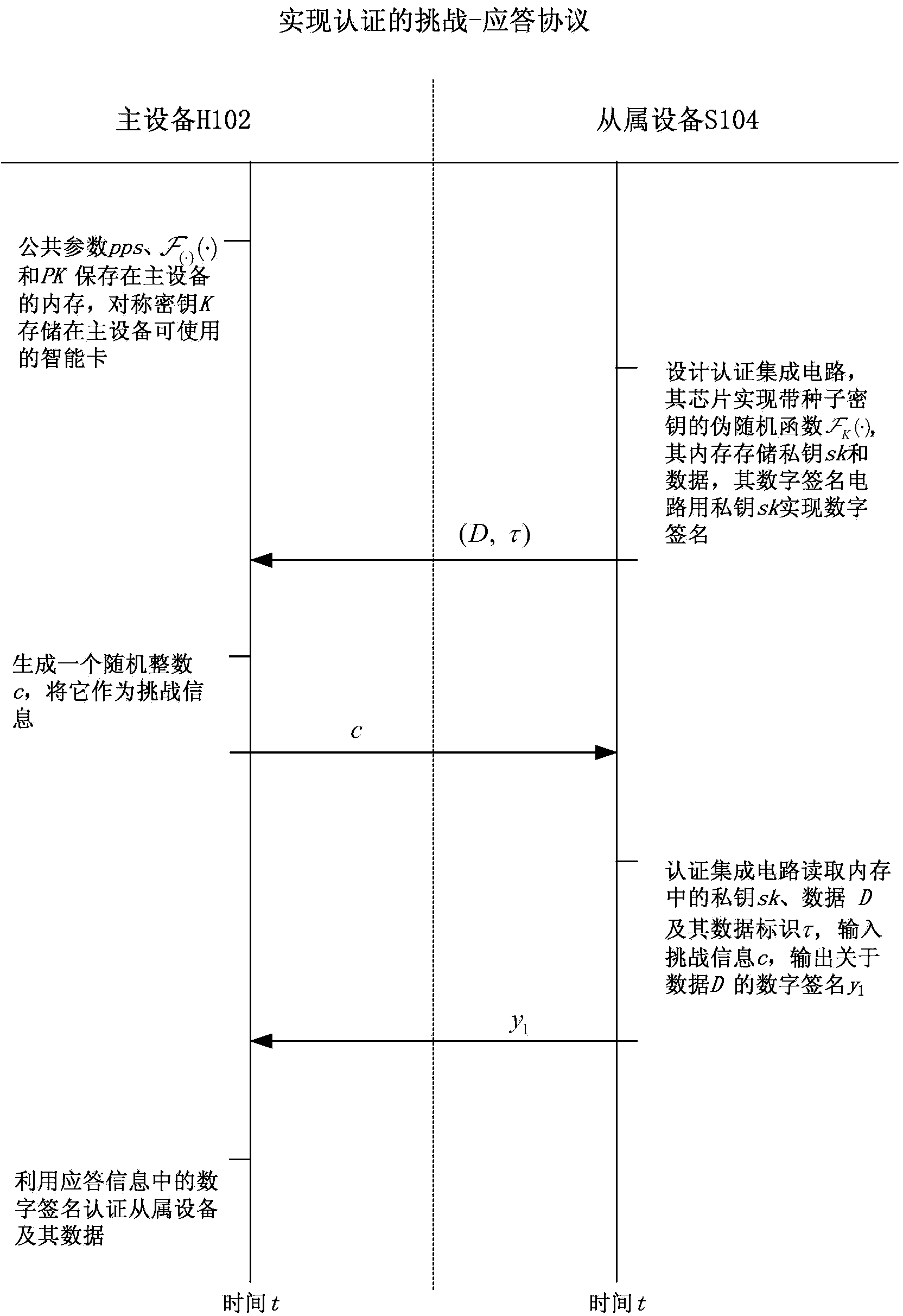
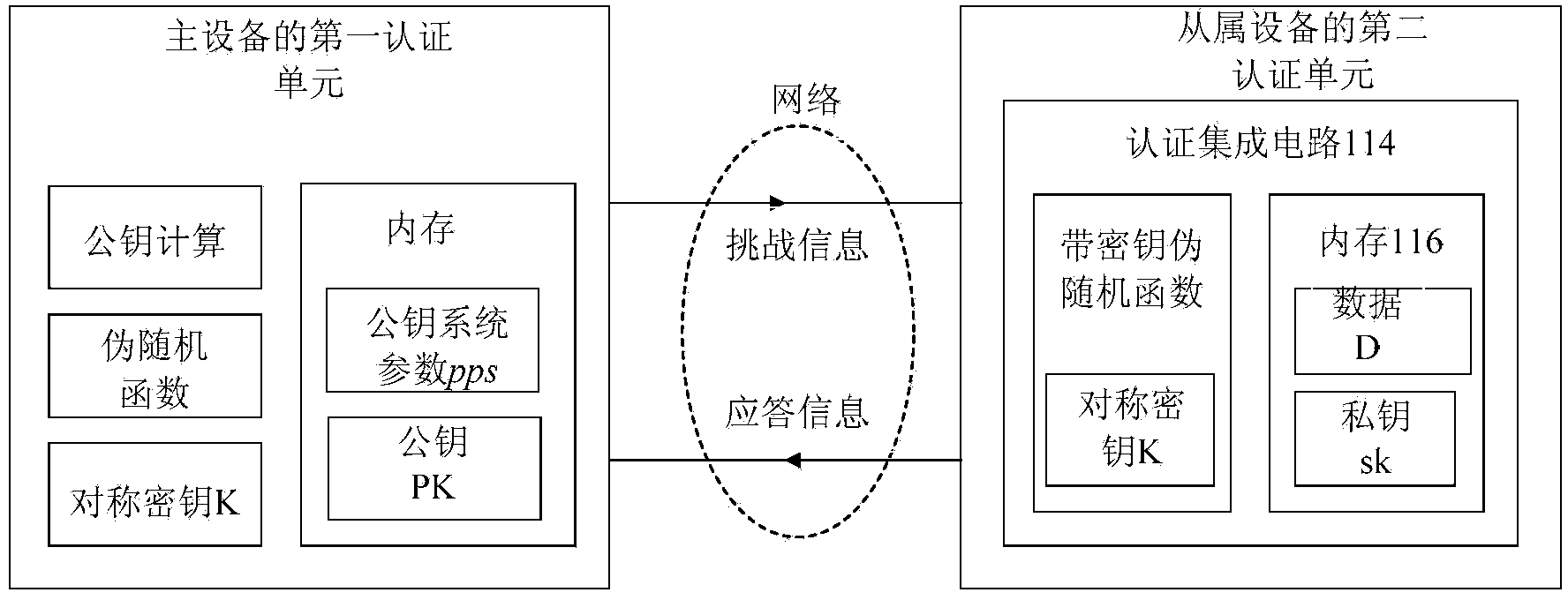
[0074] Such as figure 1 and 2 As shown, this embodiment discloses a method for authenticating a master device to its slave devices, wherein the steps for the master device to authenticate a slave device are as follows:
[0075] (1) Generate key: generate public parameter pps and pseudo-random function of the system The symmetric key K and the private key / public key pair (sk, PK) between the slave device and the master device that need to be authenticated; specifically:
[0076] In this step, public parameter pps={G, P, p, q}, symmetric key space are generated based on the public key cryptosystem on the elliptic curve and a pseudorandom function Among them, p and q are two large prime numbers in the public parameters, which are respectively 1024 bits and 160 bits in the present embodiment, satisfying p=αq+1, and α is a large prime number factor, and G is based on E(F on the elliptic curve p ) on an additive group, P is a generator of order q of G;
[0077] Pick the priv...
Embodiment 2
[0123] In this embodiment, a method for authenticating a master device to its slave devices is disclosed. The difference between this embodiment and Embodiment 1 is that in this embodiment, the master device simultaneously targets multiple slave devices C 1 ,...,C L for authentication, such as Figure 7 As shown, the specific steps are as follows:
[0124] S1. Generate a key: select the public parameter pps of the system and a pseudo-random function A symmetric key K and each slave device C to be authenticated i Private key / public key pair (sk i , PK i), where 1≤i≤L, L is the total number of slave devices that need to be authenticated at the same time, L>1; specifically:
[0125] In this step, public parameter pps={G, P, p, q}, symmetric key space are generated based on the public key cryptosystem on the elliptic curve pseudorandom function and each slave device S i public key PK i ; Among the public parameters, p and q are two large prime numbers, satisfying p=αq+...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com