Warning function operating method for portable computer
A computer and portable technology, which is applied in computing, instruments, electrical digital data processing, etc., can solve the leakage of confidential information and achieve the effect of protecting confidential information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
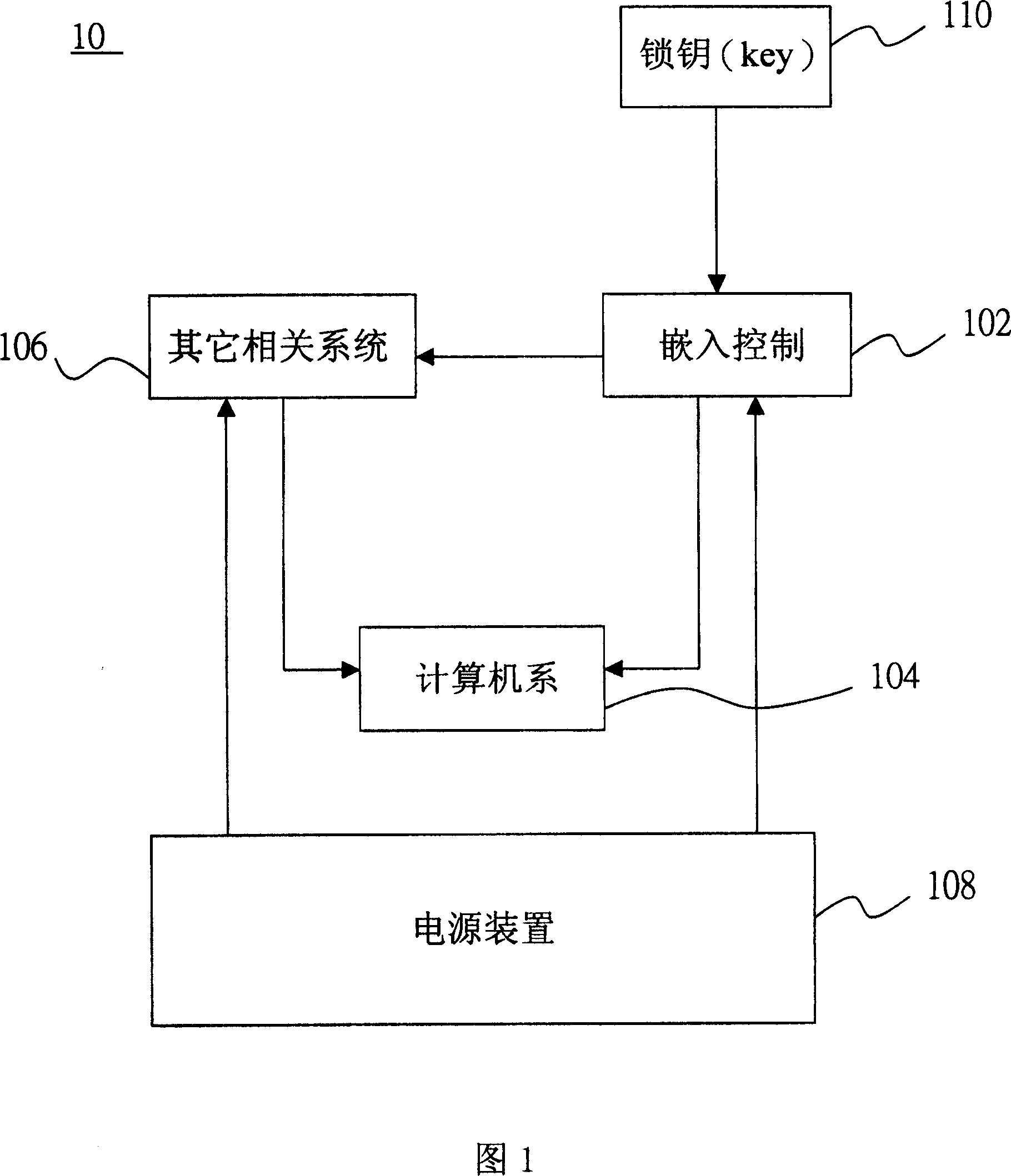
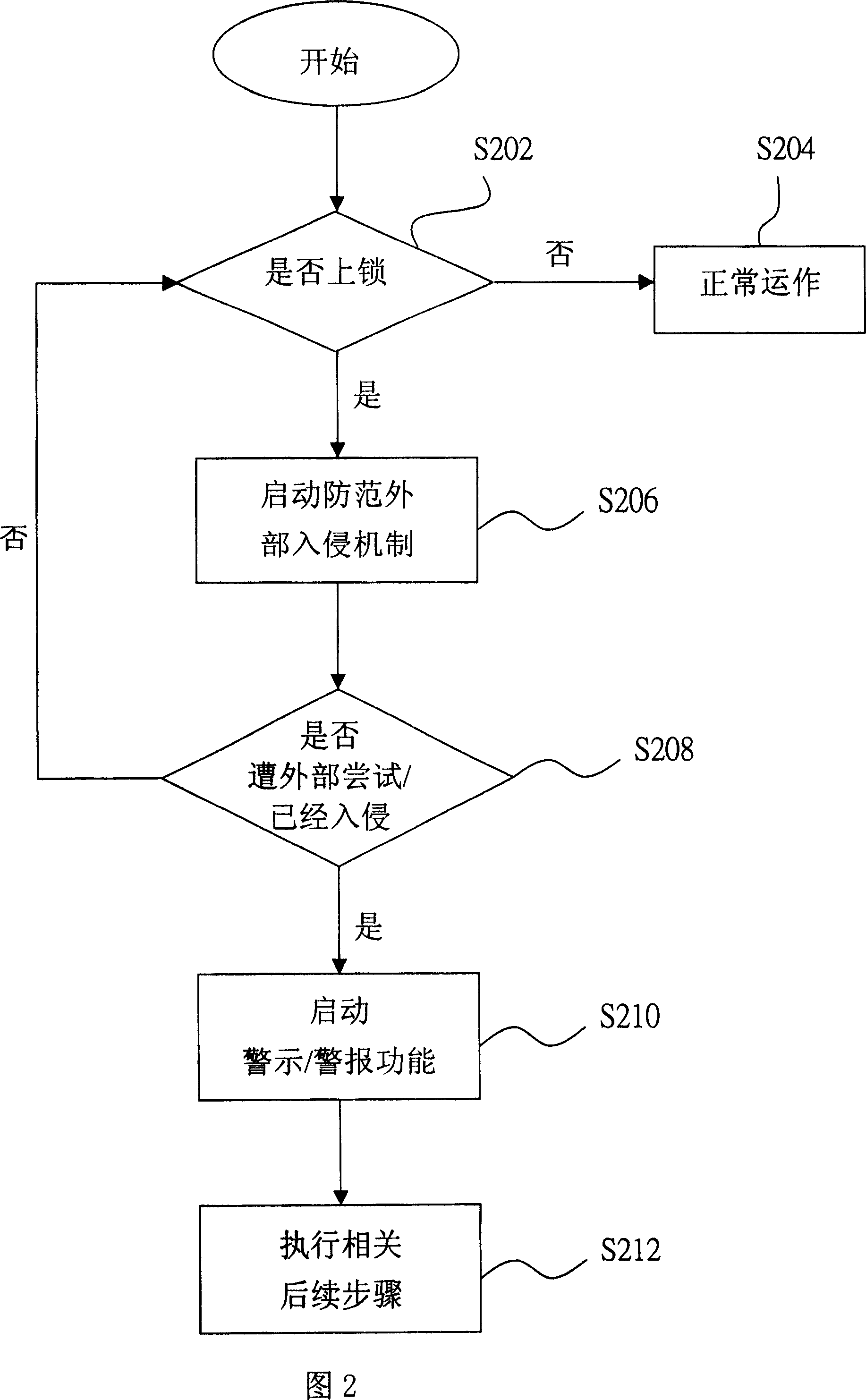
[0012] FIG. 1 is a schematic diagram of a portable computer 10 according to a preferred embodiment of the present invention. As can be seen from FIG. 1 , the portable computer 10 includes an embedded controller 102 , a computer system 104 , other related systems 106 , a power supply 108 , and a key 110 . Wherein, the embedded controller 102 is used to control the operation of the computer system 104 and other related systems 106, and it has a mechanism for preventing external intrusion. The lock key 110 is a signal generated by the relevant circuit of the lock key 110 in the portable computer 10 , so that the embedded controller 102 knows whether the portable computer 10 is locked or not. Wherein, the lock key 110 may be, for example, a component or function inside the portable computer 10 . For example, the lock key 110 may be a button in the portable computer 10, when the button is pressed, the embedded controller 102 will know that the portable computer 10 is locked. Alte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com