Efficient anonymous identity authentication method in Internet of Vehicles environment
An identity authentication and car networking technology, applied in the field of efficient anonymous identity authentication in the car networking environment, can solve the problems of unmanned operation and management, the length of lattice signature needs to be optimized, and the lack of efficient and fast consensus mechanism, to achieve the protection of identity. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] In order to make the objectives, technical solutions and advantages of the present invention clearer, the following further describes the present invention in detail with reference to the accompanying drawings and embodiments. Of course, the specific embodiments described here are only used to explain the present invention, but not to limit the present invention.
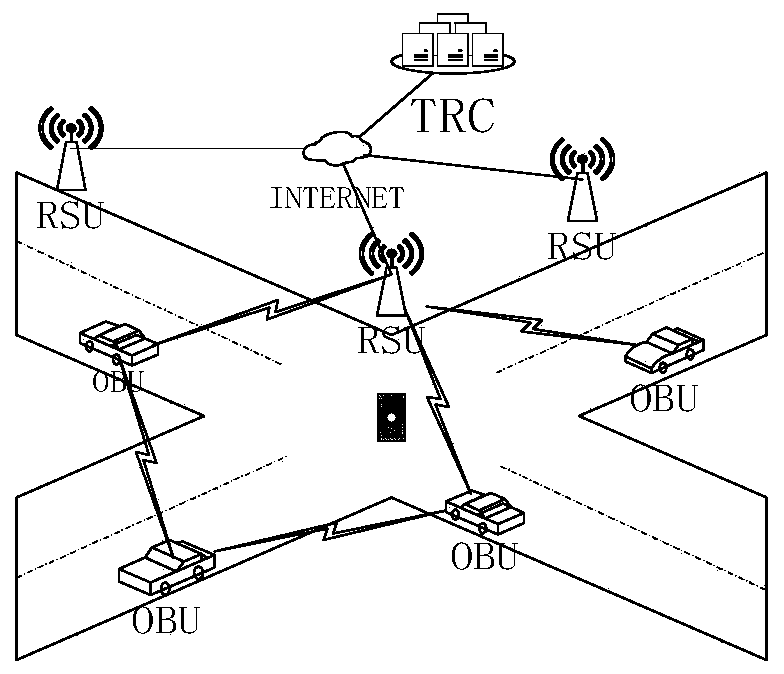
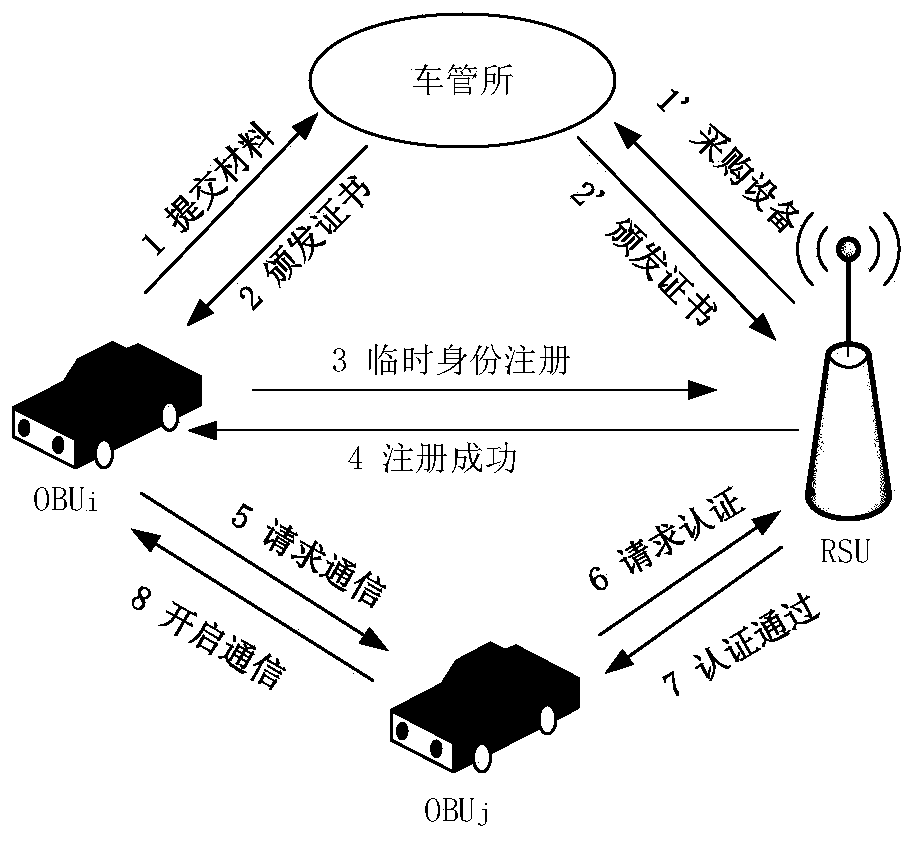
[0069] 1. In the present invention, the vehicle management office is an authoritative organization, and its public public key and issuing certificate are valid and reliable. The vehicle management office issues certificates for vehicles and RSUs offline to ensure that even if online data is leaked, the identity of the vehicle owner will not be private Cause a direct threat.
[0070] 2. The OBU device is embedded in the vehicle and protected by tamper-proof facilities. The OBU device generates a temporary identity to realize anonymous communication between vehicles.
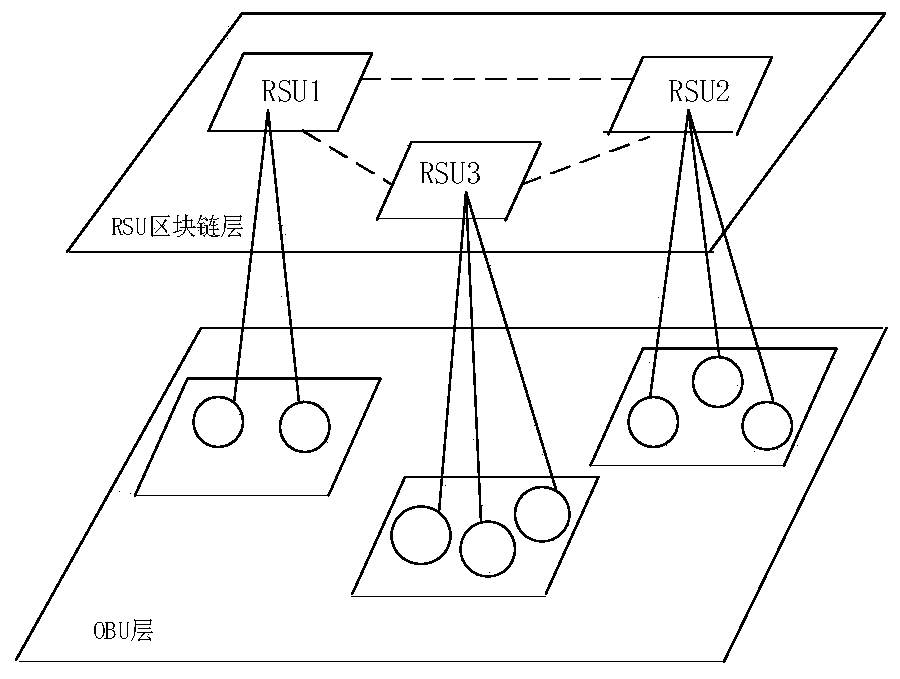
[0071] 3. RSU has strong computing power. All RS...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com