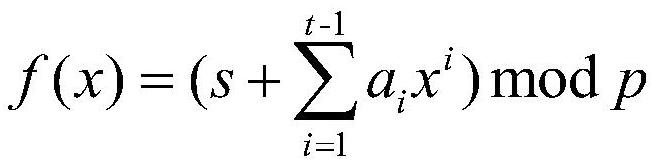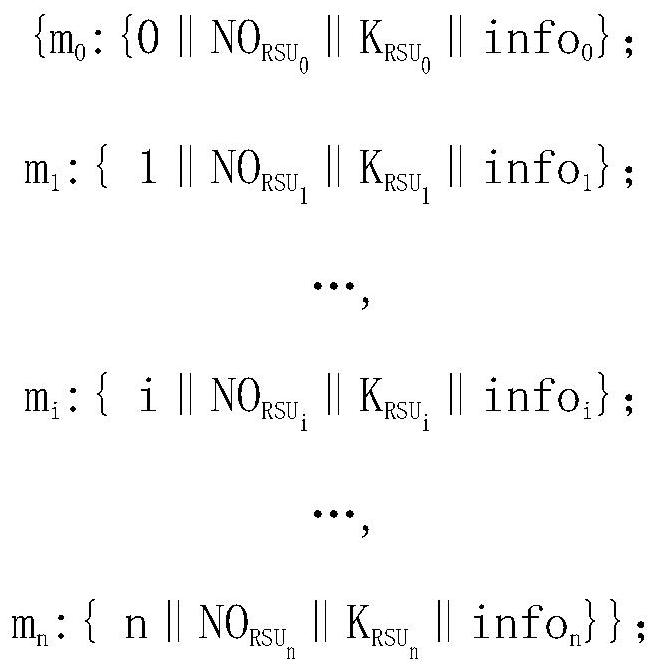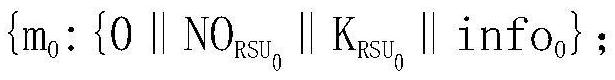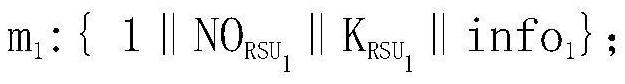Patents
Literature
49results about How to "Efficient authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
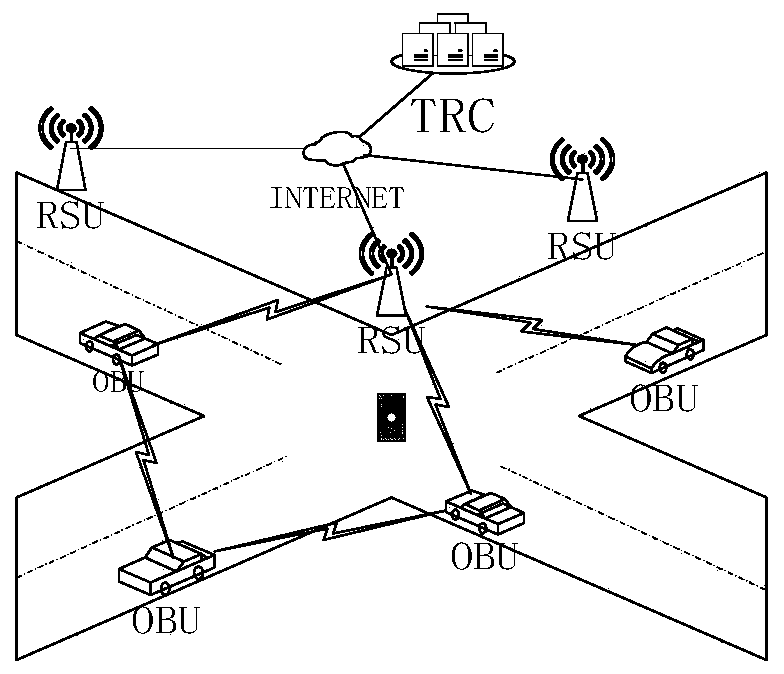
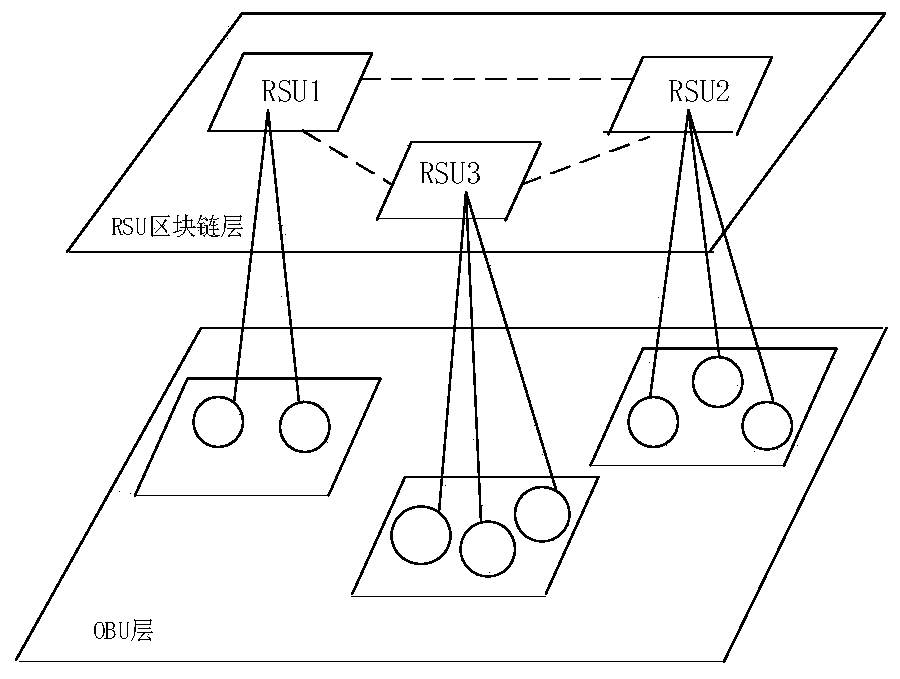
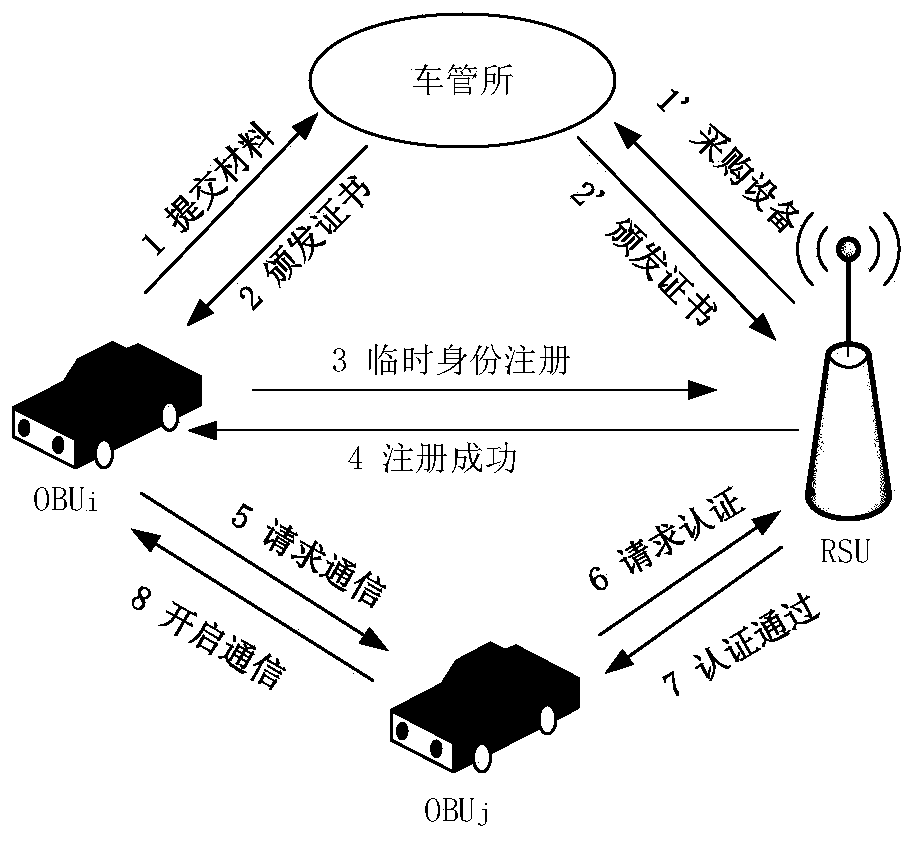
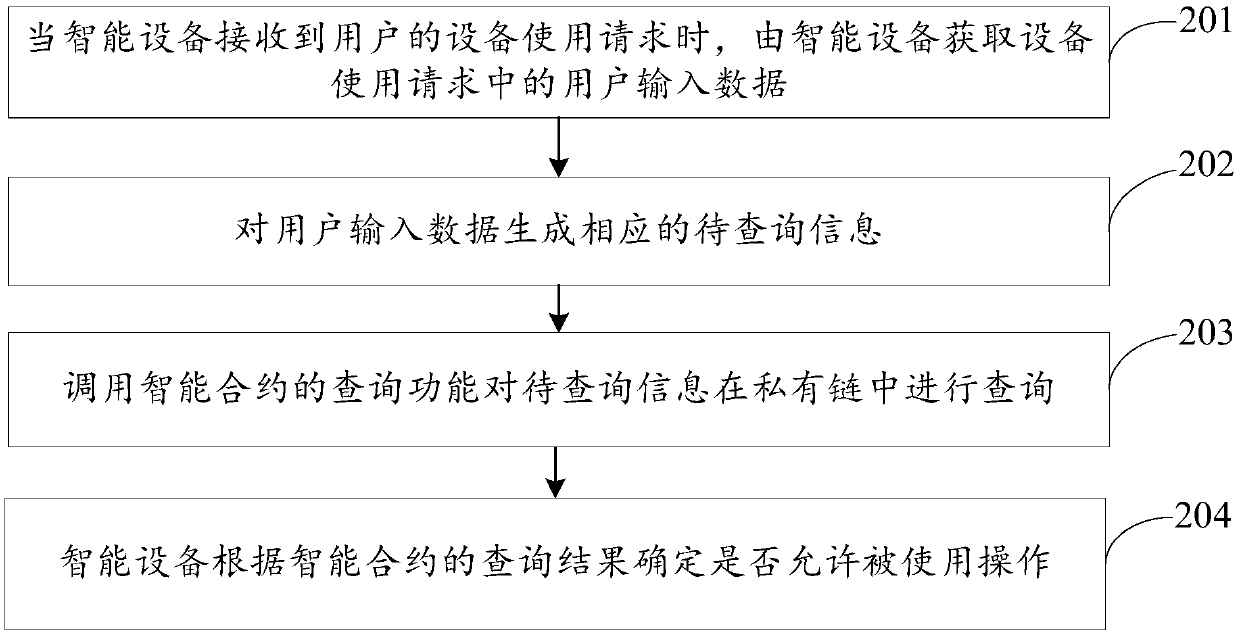
Efficient anonymous identity authentication method in Internet of Vehicles environment
ActiveCN111372248AImprove authentication efficiencyEnhanced anonymityPublic key for secure communicationParticular environment based servicesInternet privacyAttack
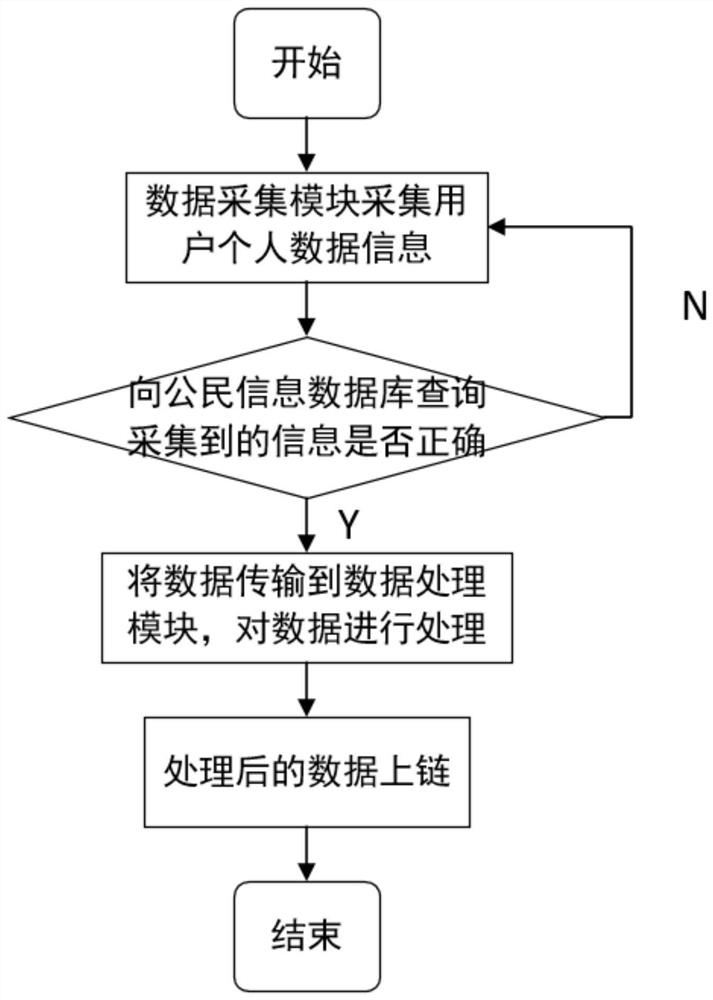
The invention provides an efficient anonymous identity authentication method in an Internet of Vehicles environment, and belongs to the technical field of Internet of Vehicles security. According to the technical scheme, the method comprises the following steps of vehicle offline registration, online registration and rapid identity authentication. The method has the beneficial effects that a temporary identity certificate Token mechanism is set, so that the authentication efficiency is improved while the vehicle anonymous two-way communication is realized; a block chain distributed account book mode is utilized, so that data traceability and tamper resistance are guaranteed, and the problems of relatively low identity authentication efficiency, easiness in attack and the like caused by traditional PKI authentication centralization of the Internet of Vehicles are solved; the combination of the blockchain PBFT consensus mechanism and the smart contract greatly reduces the authenticationtime delay of the traditional method.
Owner:NANTONG UNIVERSITY
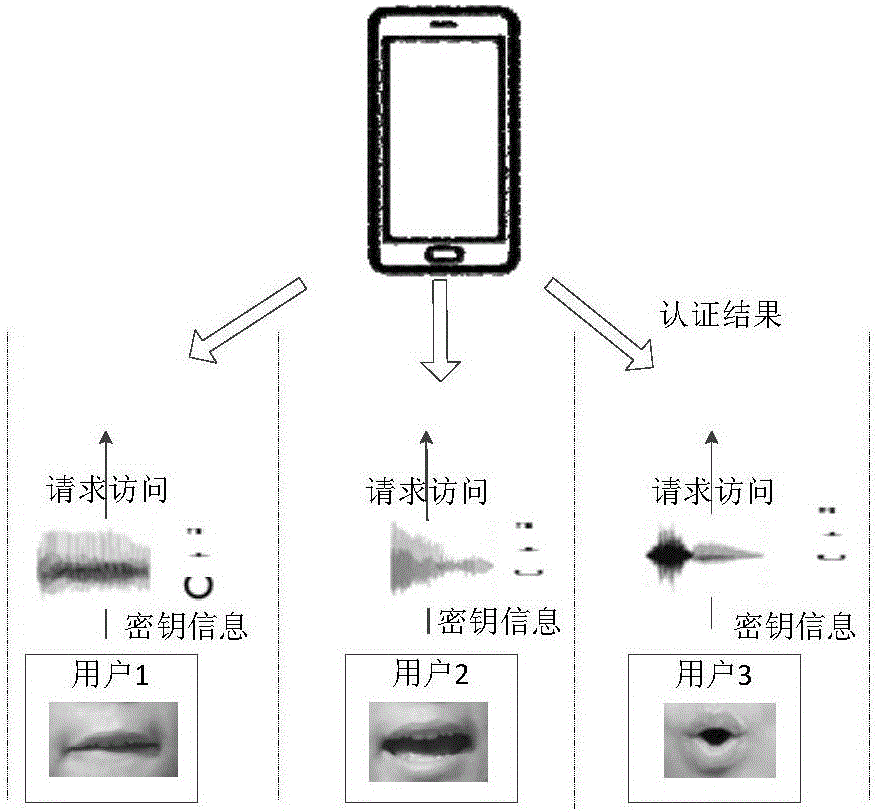
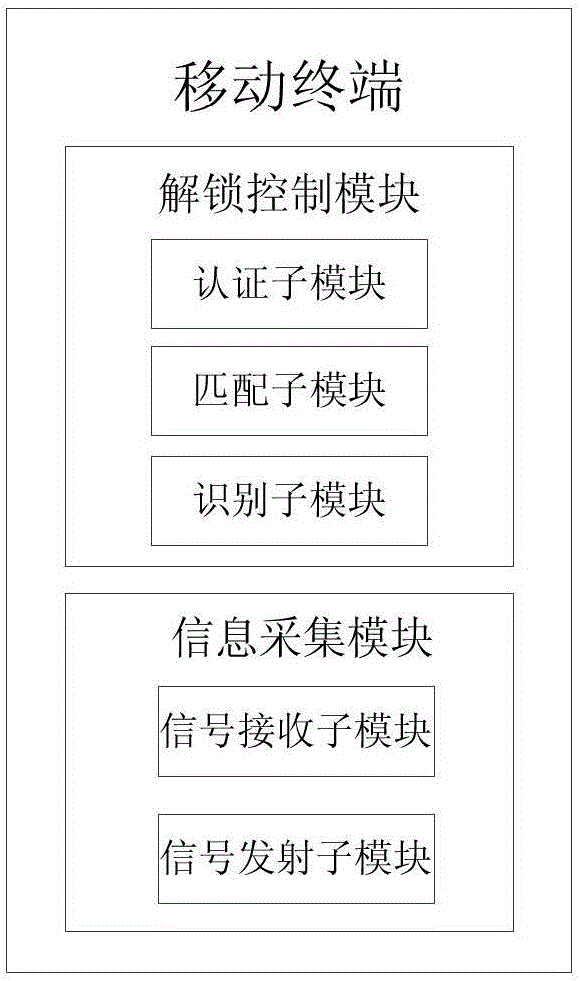
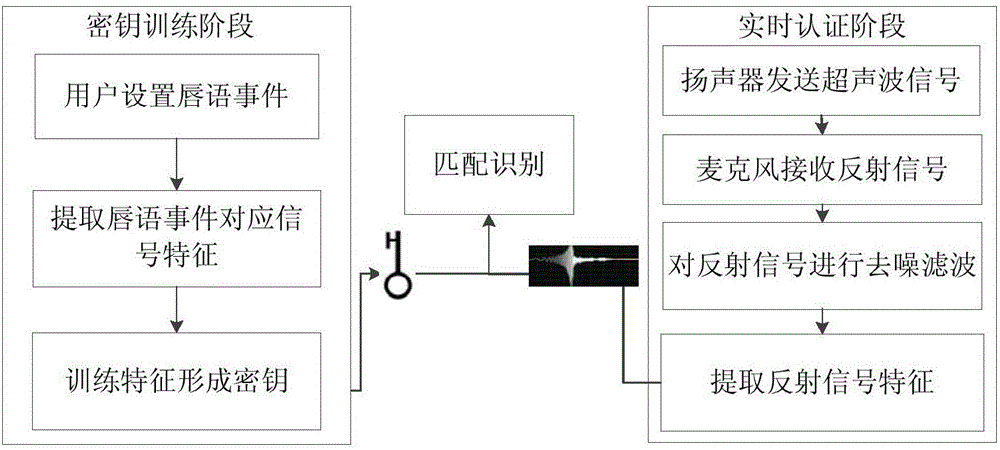
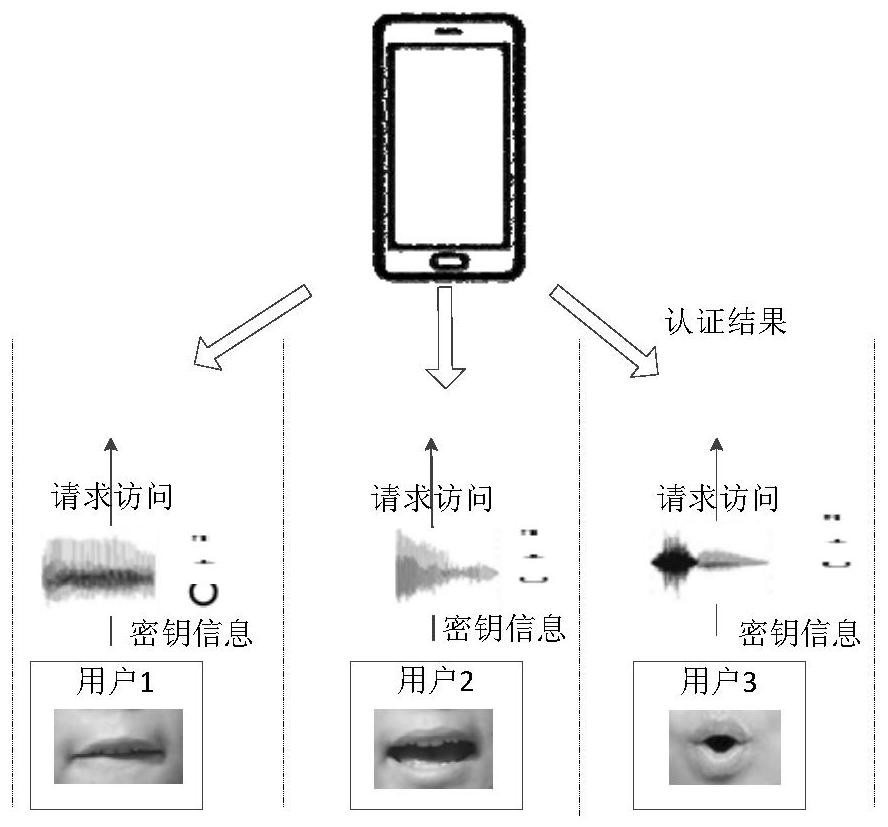
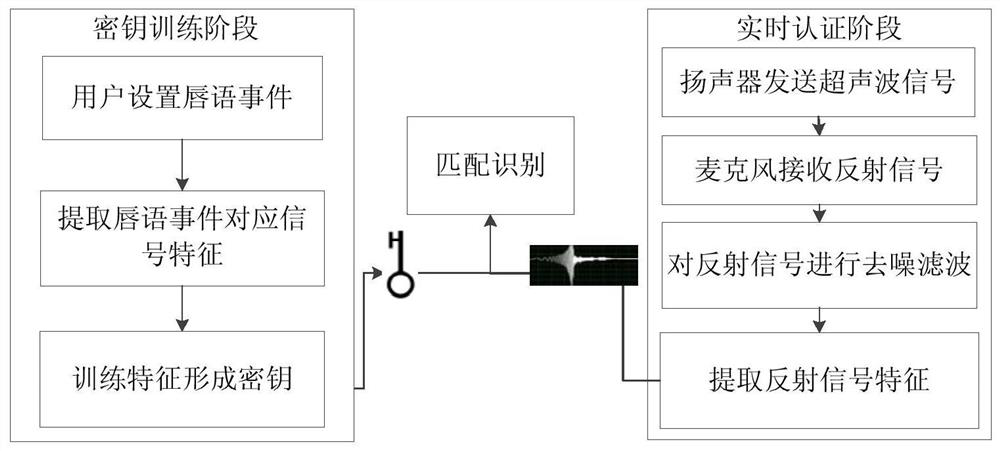
Identity authentication method based on ultrasonic lip-reading recognition
ActiveCN106778179AAvoid security breachesLower deployment costsDigital data authenticationFrequency spectrumFeature extraction
An identity authentication method based on ultrasonic lip-reading recognition comprises the steps of (1) transmitting, by a signal transmitting source, an ultrasonic signal, and receiving, by a signal receiving source, a reflected signal from the mouth; (2) extracting lip-reading characteristics from the reflected signal acquired which include spectral characteristics corresponding to a lip-reading event and dynamic lip outline characteristics of a user; (3) recognizing and authenticating the user according to the lip-reading characteristics extracted in step (2). The identity authentication method has the advantages that identity authentication characteristic parameters are acquired through ultrasonic sensing capacity without extra hardware customization, the deployment cost is low, and the applicable range of ultrasonic technology in mobile terminals is widened; the security vulnerabilities in the existing techniques such as facial recognition and fingerprint recognition are solved by taking advantage of differences between behavior habits of users expressing a same lip-reading event in conjunction with biological characteristics, and efficient identity authentication can be achieved.
Owner:NANJING UNIV
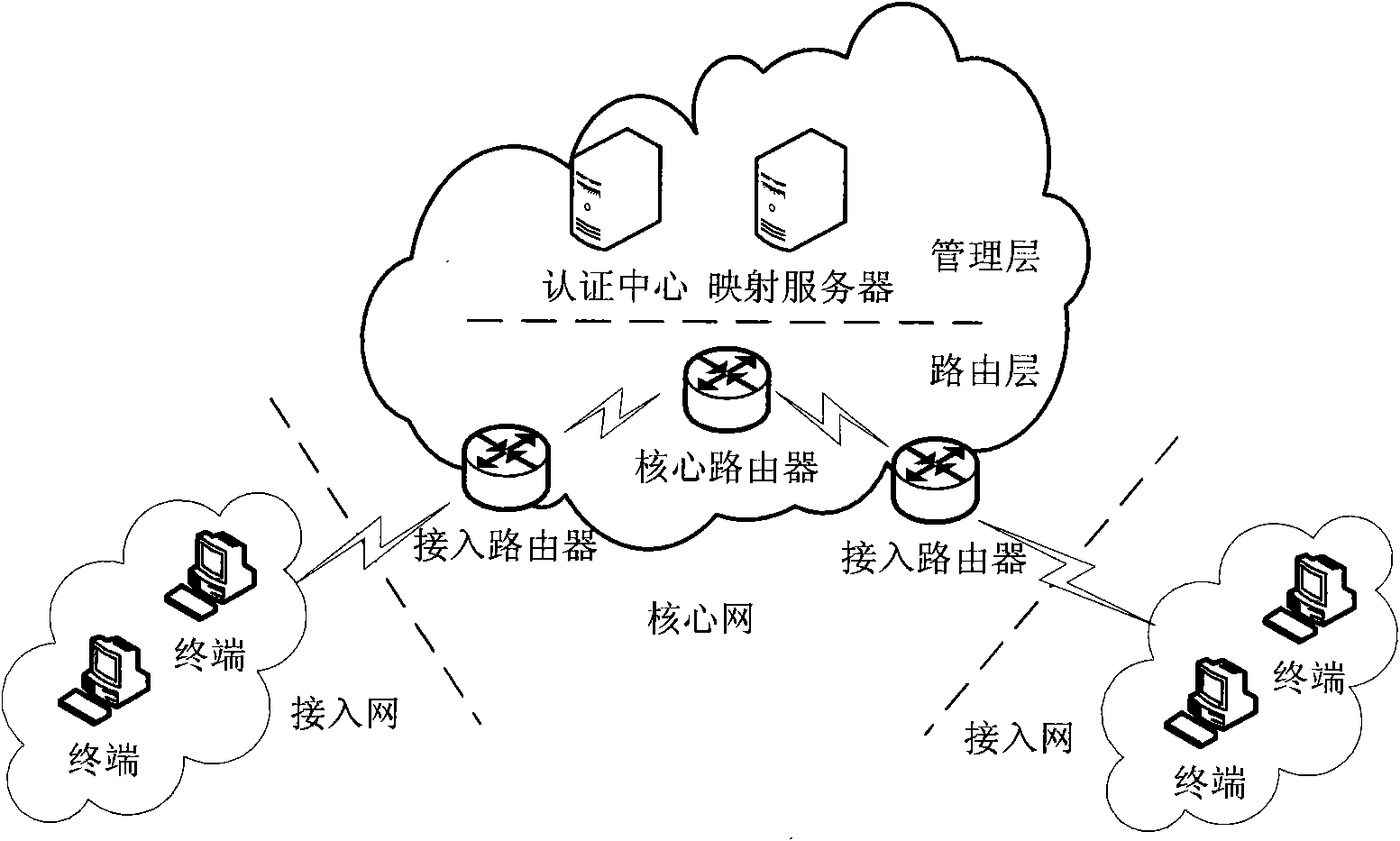
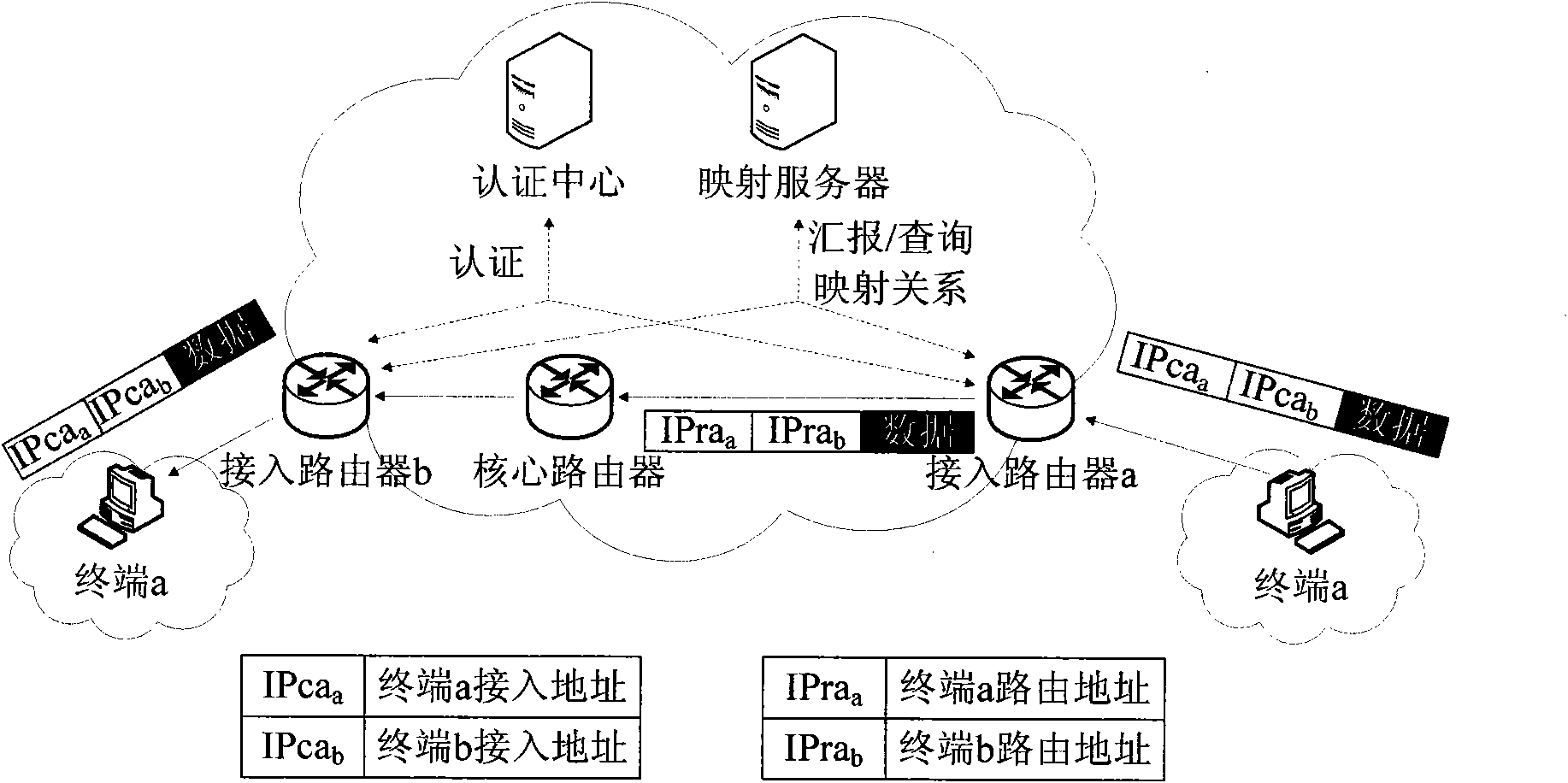
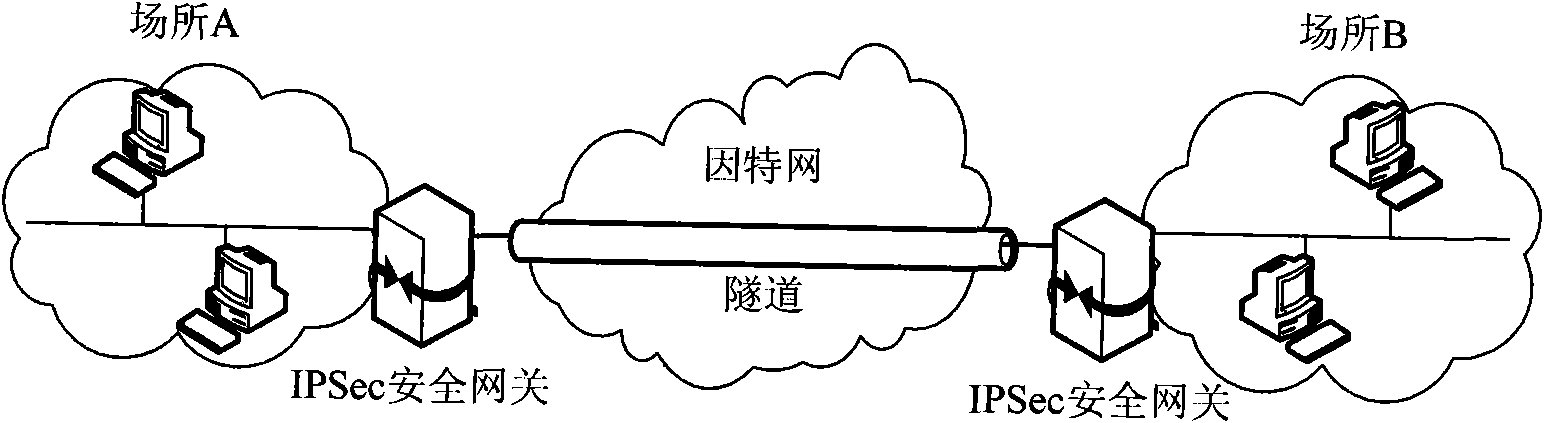
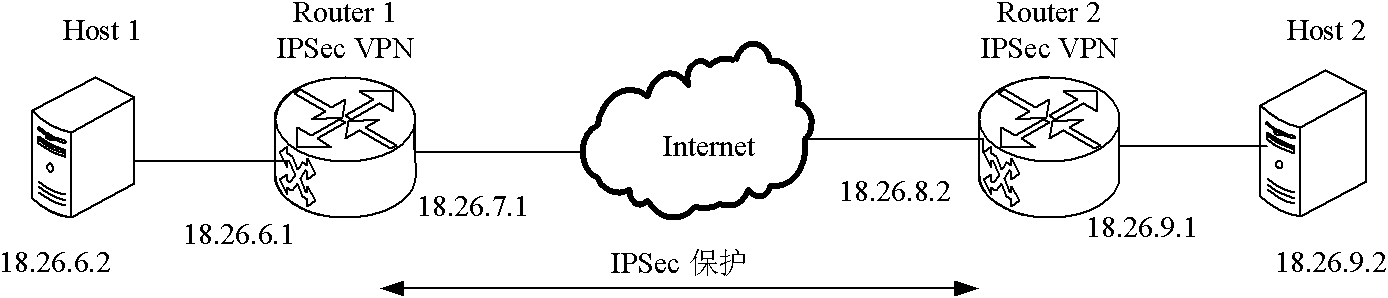
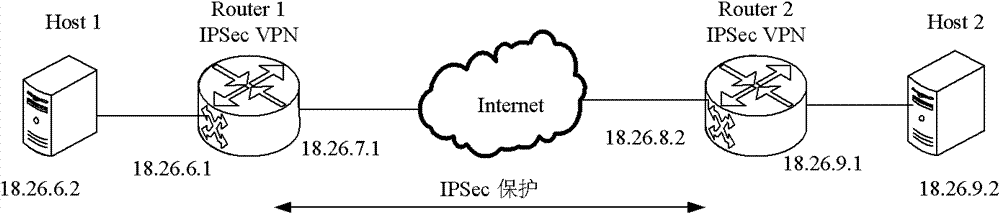
Deployment method of IPSec-VPN in address discrete mapping network
The invention relates to a deployment method of IPSec-VPN in an address discrete mapping network, belonging to the technical field of networks. The deployment method comprises a negotiation security alliance stage which is responsible for completing negotiation and establishment of a security alliance SA among access routers, an access authentication stage which is responsible for completing the authentication of the validity of a new access terminal and a communication stage referring to mutual communication of two access terminals after the previous two stages are completed. The method realizes the application of the IPSec in the address discrete map network by combining an IPSec-VPN technology, sufficiently utilizing the advantages of the address discrete mapping network and adopting the tunnel encapsulation idea, thereby providing the high-efficiency security insurance of encryption, authentication, replay attack resistance and the like for a core network, and improving the security level of the address discrete map network.
Owner:BEIJING JIAOTONG UNIV
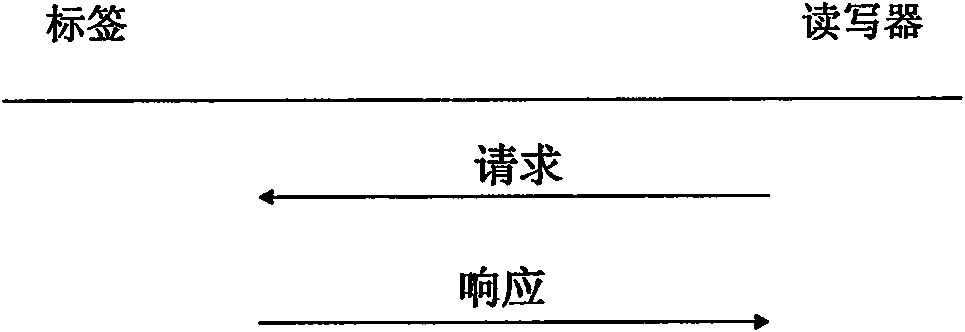
Radio frequency identification (RFID) privacy authenticating method
InactiveCN101645138AReduce storage and computing overheadStrong securityCo-operative working arrangementsRadio frequencyReader writer
The invention discloses a radio frequency identification (RFID) privacy authenticating method which comprises the following steps: system initialization: a reader-writer stores secret keys and indexesof all labels and a summary value of an index space; label recognition: the reader-writer transmits an authenticating request to the labels, the labels calculate and transmit authenticating information to the reader-writer, and reader-writer recognizes the labels after receiving the authenticating information; updating: after the labels are authenticated, the reader-writer updates the secret keysand the indexes of the labels and transmits updated information to the labels, and the labels update the stored secret keys and the indexes; and system maintenance: when the labels enter or depart from an RFID system, the reader-writer maintains the secret keys and the indexes of the labels. The invention can effectively resist various prior passive and active attacks; compared with an RFID authenticating method based on a balanced tree structure, the invention greatly reduces the storage and calculation cost at the label ends.
Owner:XI AN JIAOTONG UNIV
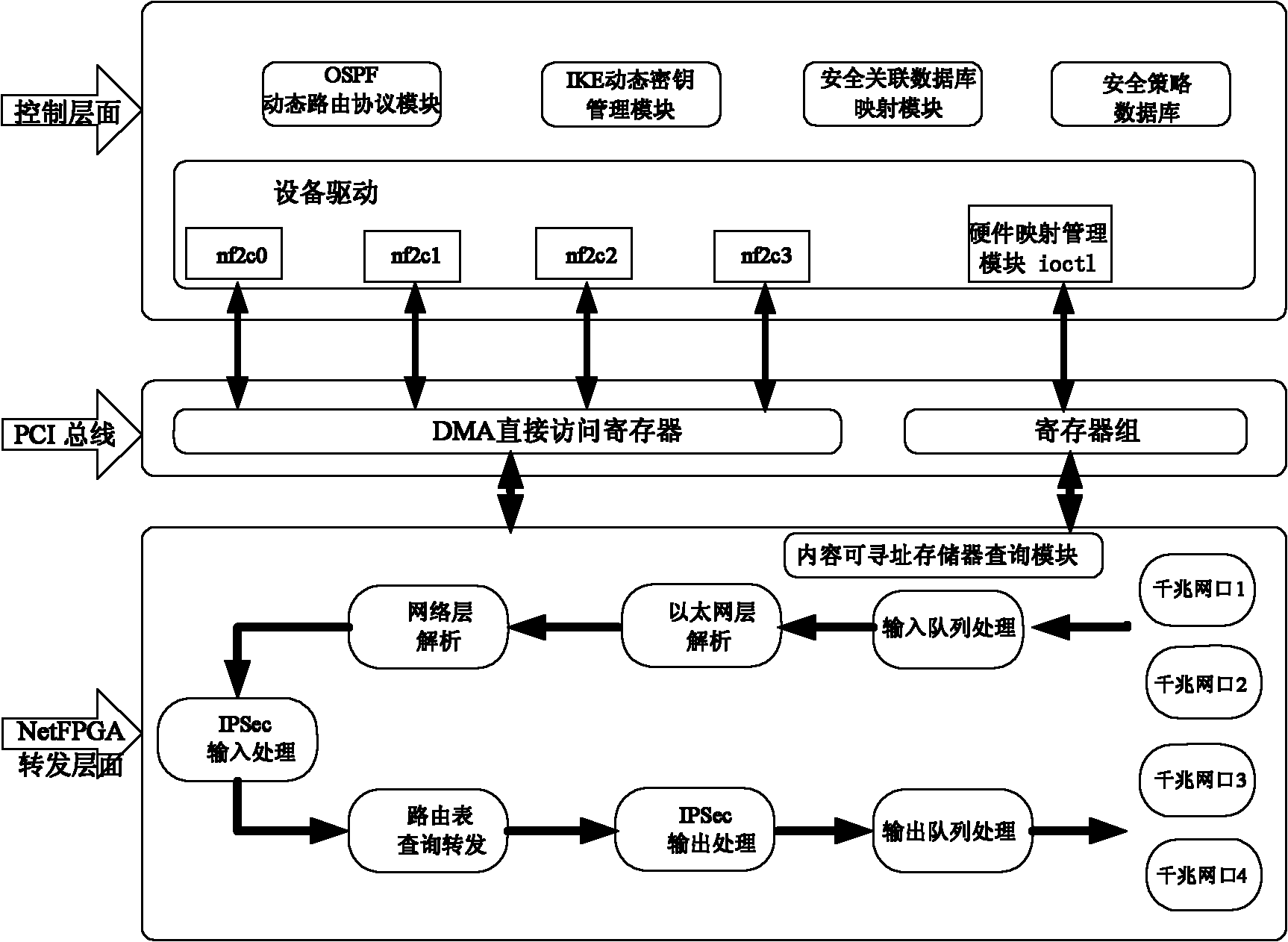
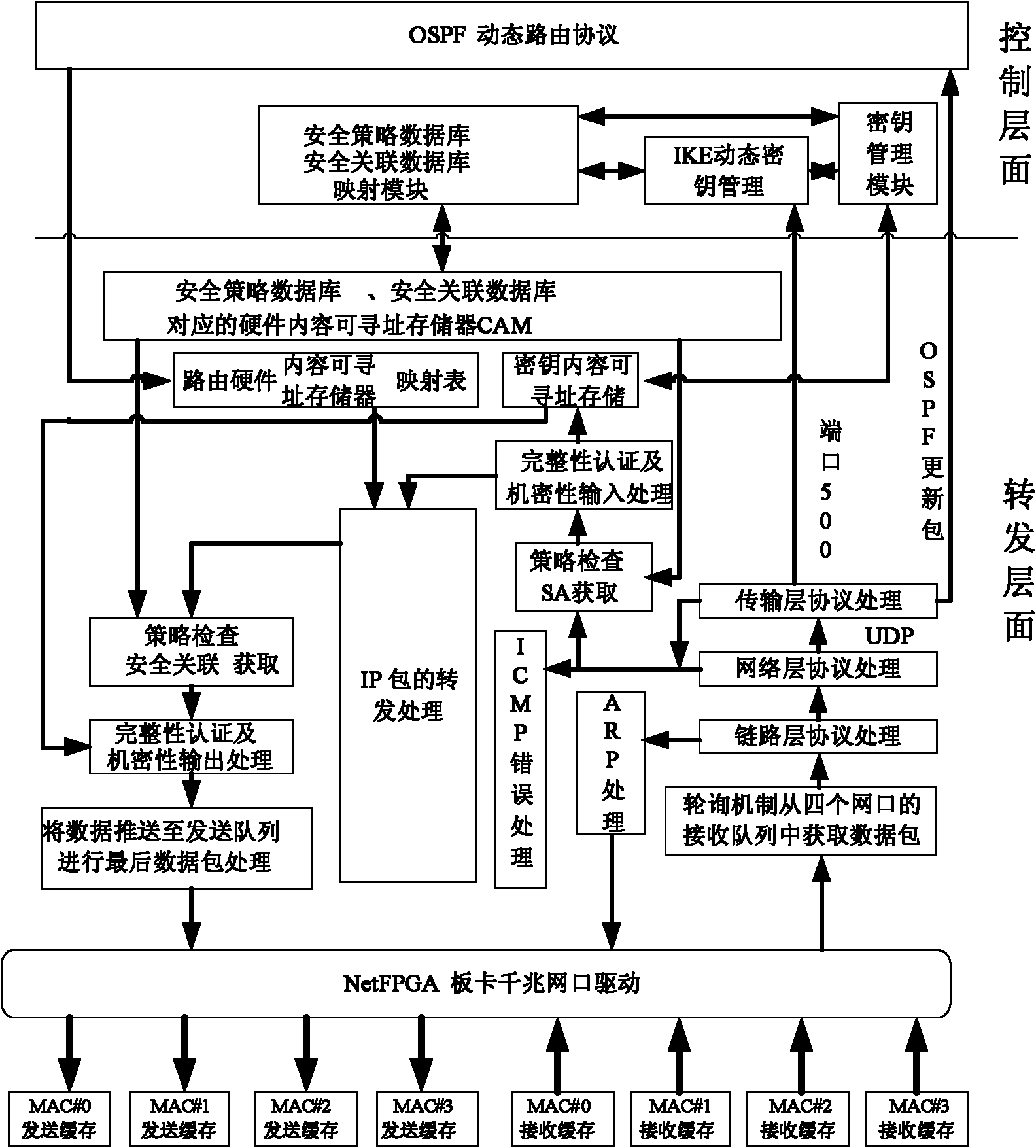
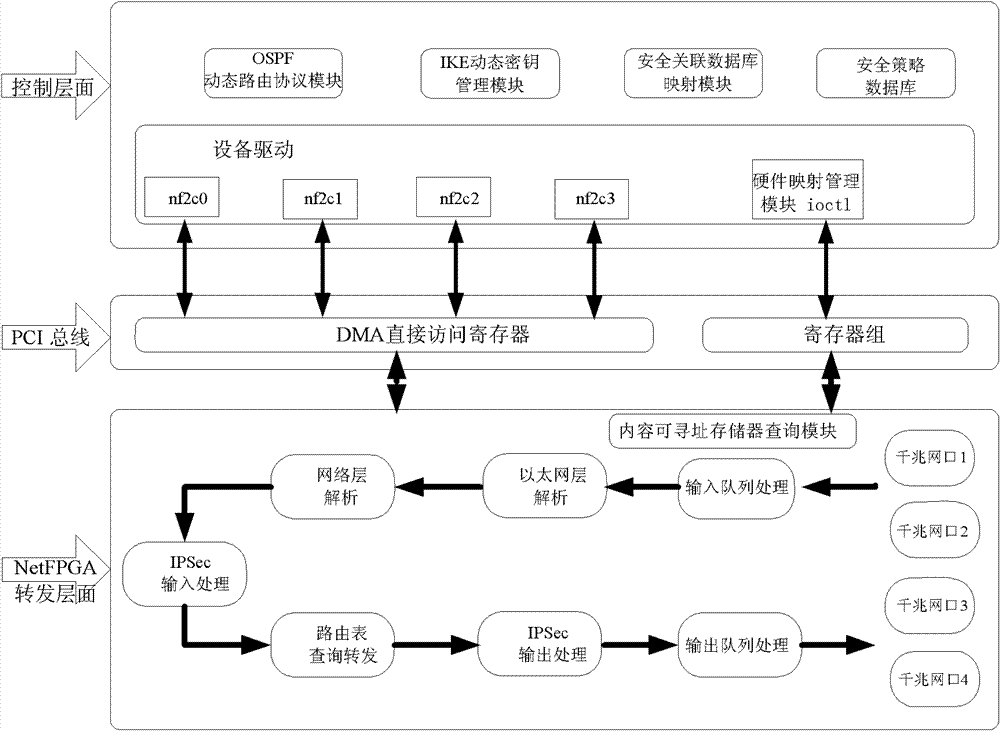
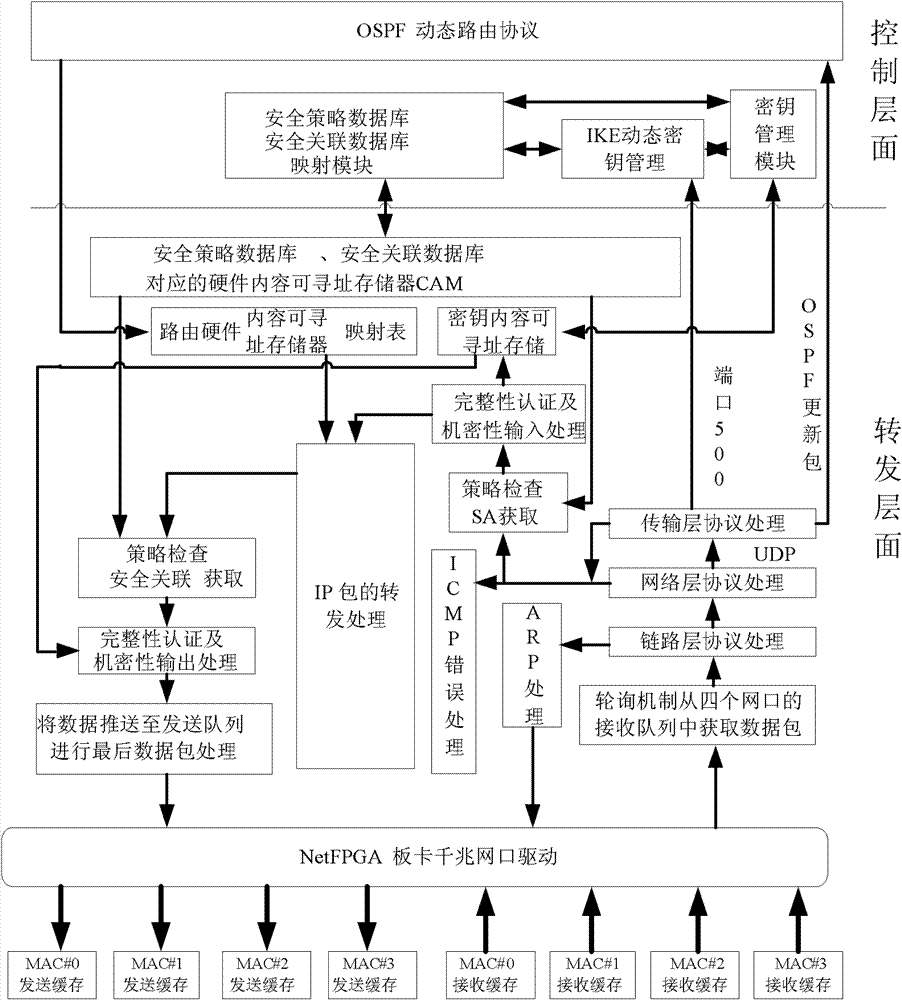
IPSecVPN (Internet Protocol Security Virtual Private Network) realizing system and method based on NetFPGA (Net Field Programmable Gate Array)
ActiveCN102065021AImprove processing speedRealize forwarding functionNetworks interconnectionData streamControl layer
The invention relates an IPSec VPN (Internet Protocol Security Virtual Private Network) realizing system and method based on a NetFPGA (Net Field Programmable Gate Array), wherein a control layer of a router is additively provided with an IKE (Internet Key Exchange) module, a security relation database mapping module and a security policy database, and a key management module is used for dynamically managing the key, the security relation and the security policy; and a forward layer is additionally provided with two independently designed IPSec input and output process modules in the originalNetFPGA standard router architecture by sufficiently utilizing the modularization reusable idea of a NetPGA development board. The scheme of the invention can realize the route forward function of the data flow in a hardware manner, and can also realize the great mass of calculation functions required by the IPSecVPN in a hardware manner, such as safe detaching / packing load and completeness authentication; in addition, the invention can effectively make a compromise on the data flow forward performance and the IPSec protocol processing performance.
Owner:北京地平线轨道技术有限公司
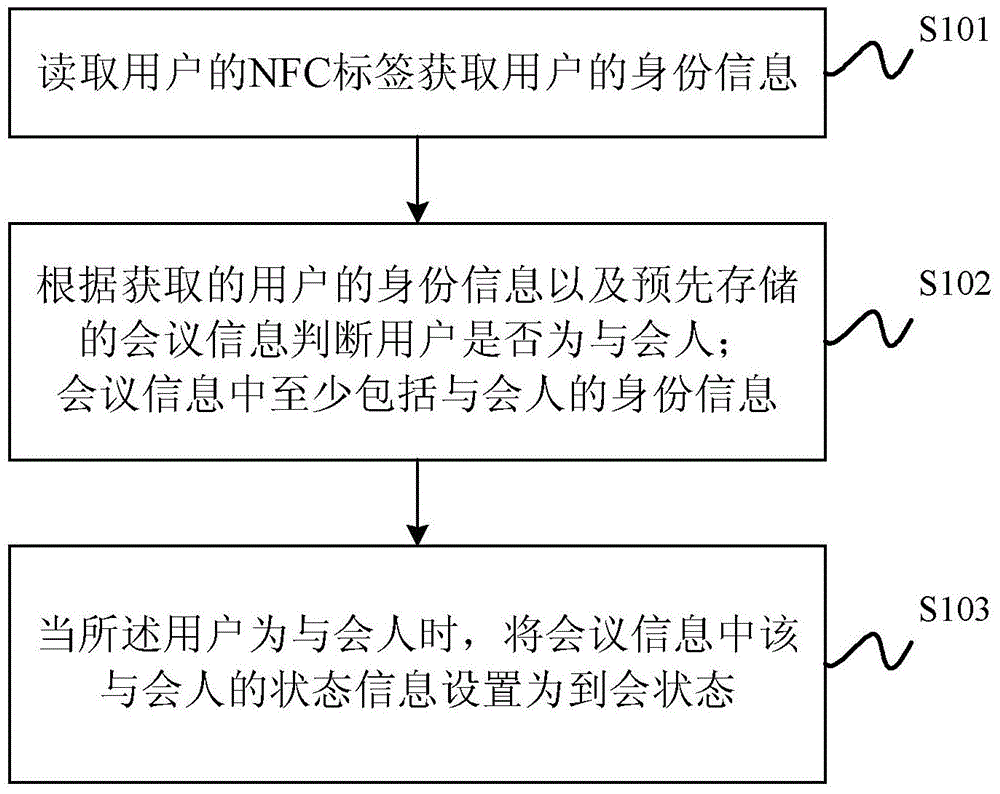
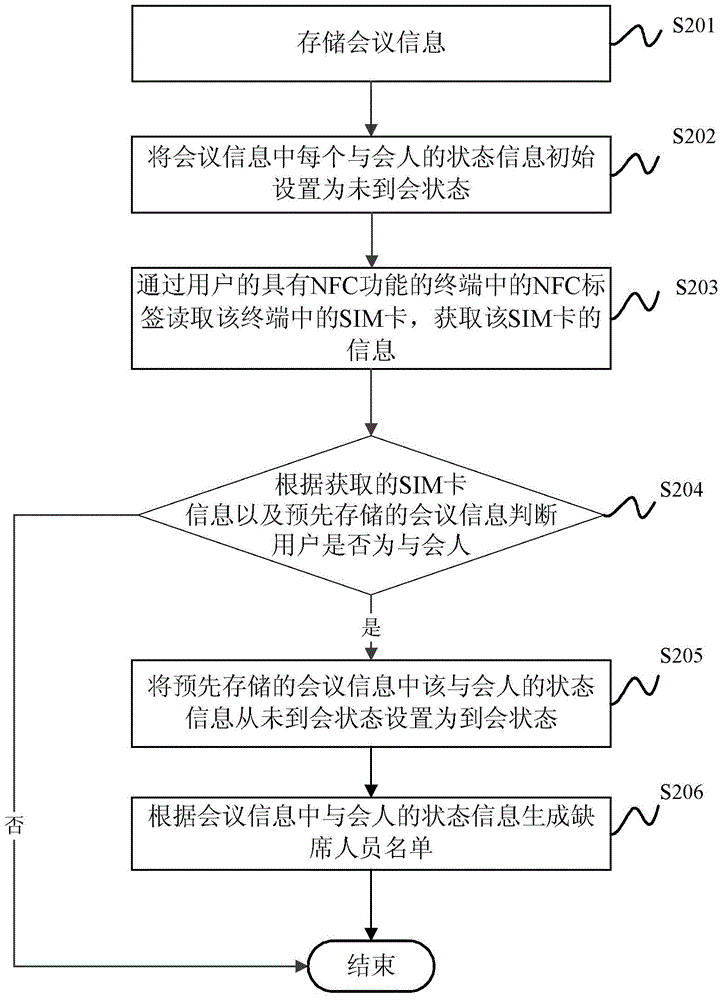
Identity authentication method, device and system and terminal equipment used for conference room
InactiveCN103607398AEfficient authenticationNear-field transmissionUser identity/authority verificationInternet privacyNear field communication
The invention provides an identity authentication method, device and system and terminal equipment used for a conference room. The method includes the steps that a near-field communication label of a user is read to acquire identity information of the user; whether the user is a participant or not is judged according to the acquired identity information of the user and conference information stored in advance, wherein the conference information at least includes identification information of participants; when it is judged that the user is a participant, the state information, in the conference information, of the user is set to be a participated state. Whether the user is a participant or not is judged through the user identity information acquired by reading the NFC label of the user, who participates in the conference or not can be known according to the state information, in the conference information, of the user, manpower or time for confirming whether the user is a participant or not and confirming who is absent is not needed any more, and identity authentication for the conference room is efficiently used.
Owner:XIAOMI INC
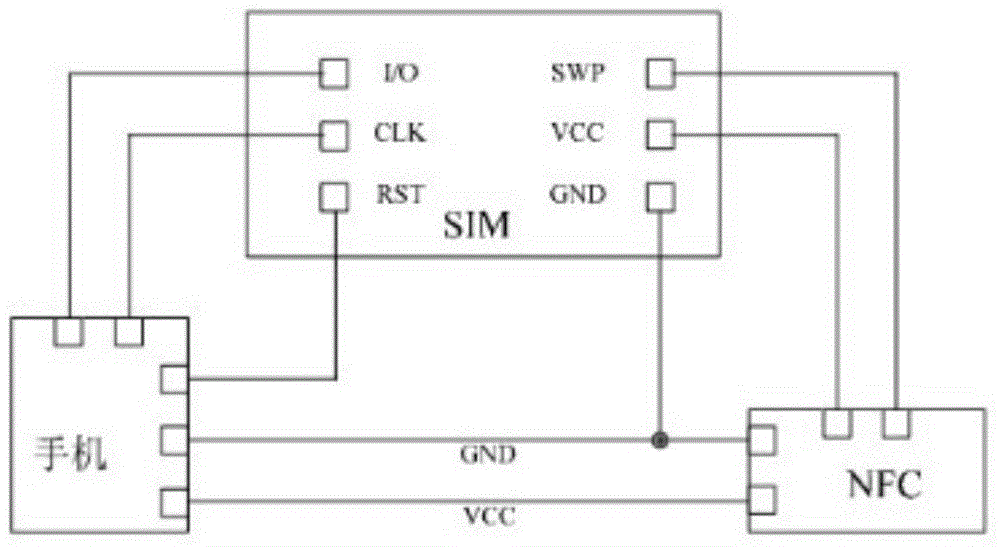
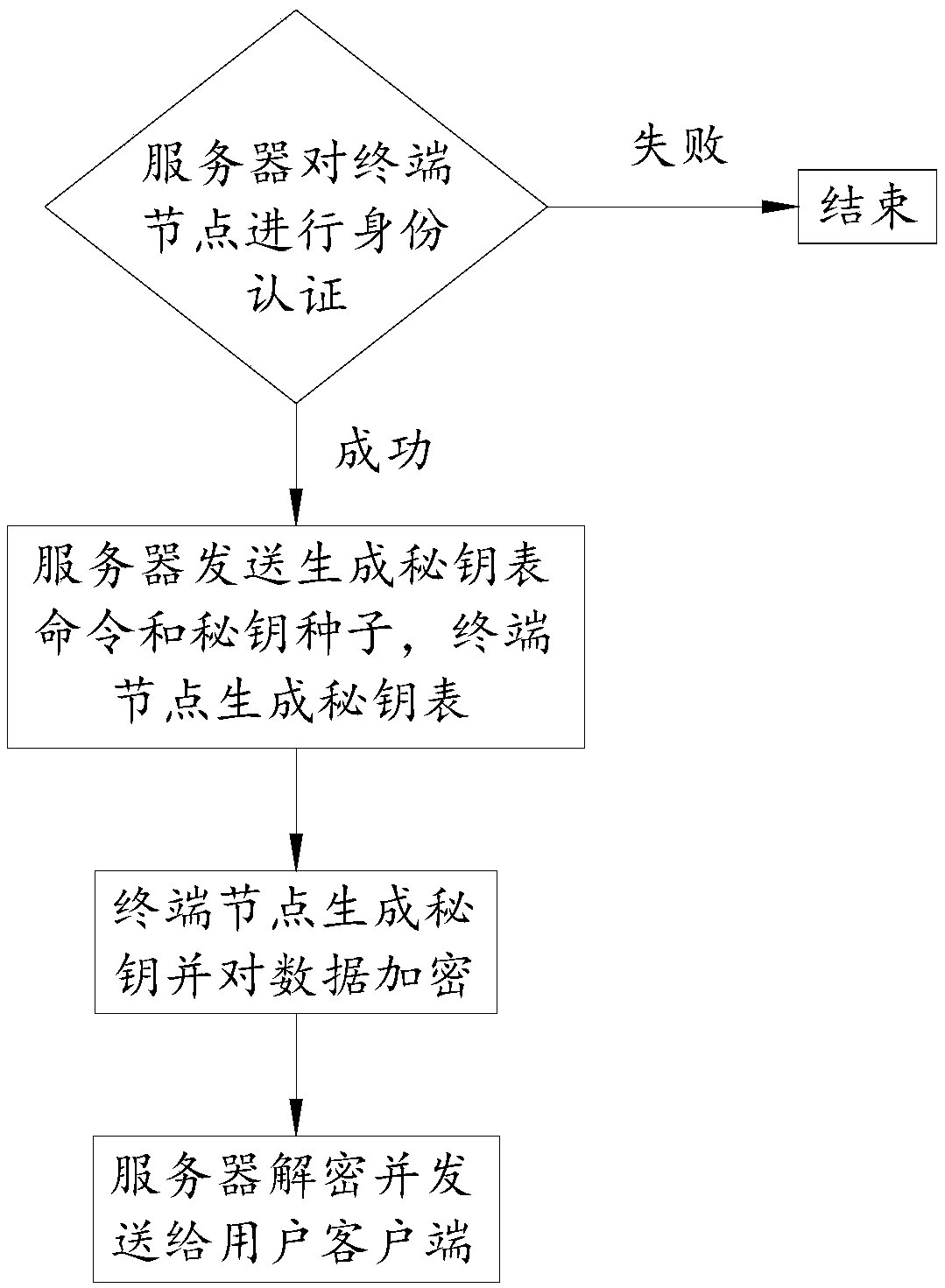
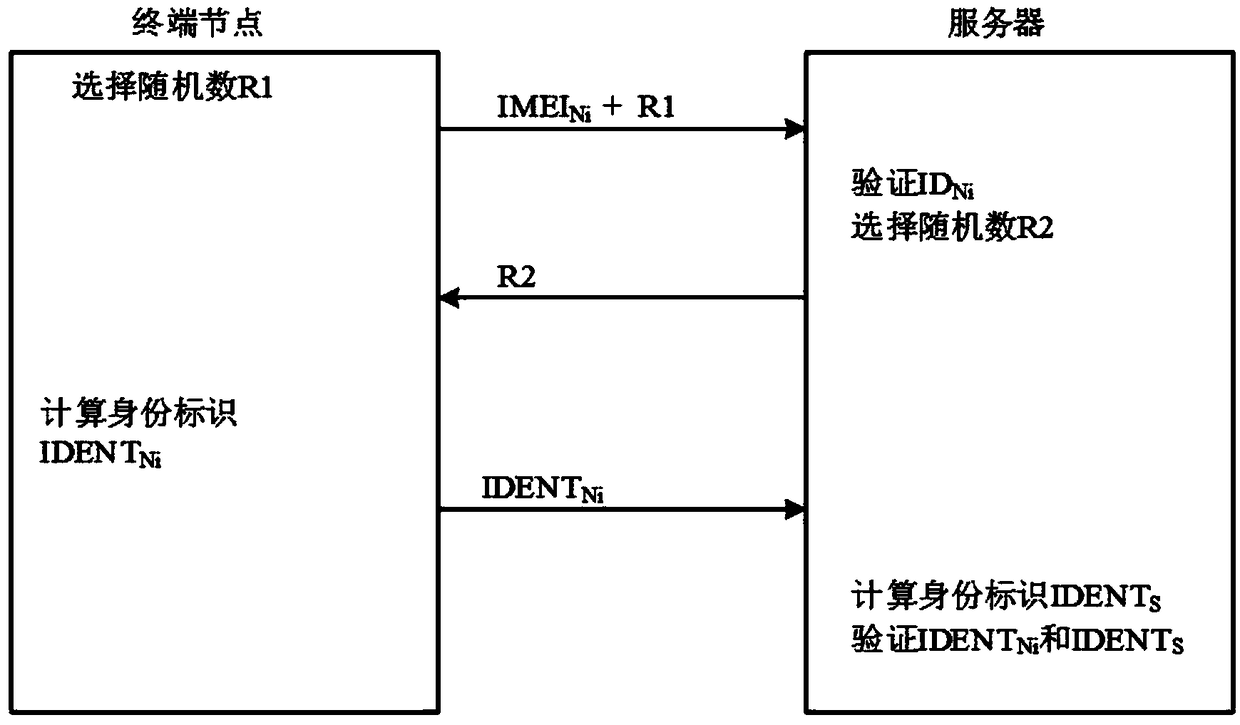
Encrypted communication method based on narrowband internet of things and encrypted communication device thereof
ActiveCN108989309AImprove securityEfficient authenticationTransmissionComputer terminalCommunication device
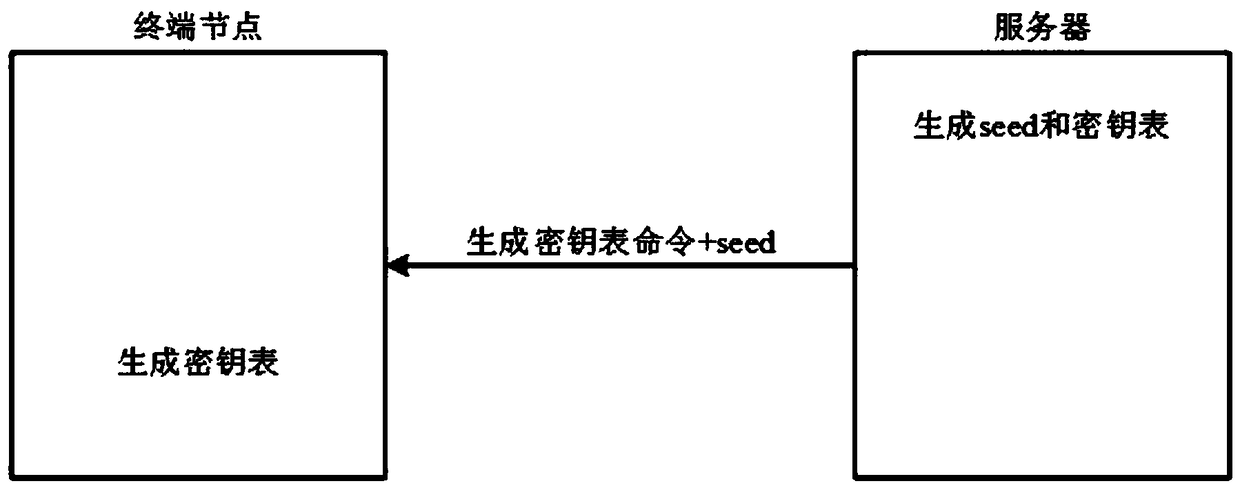
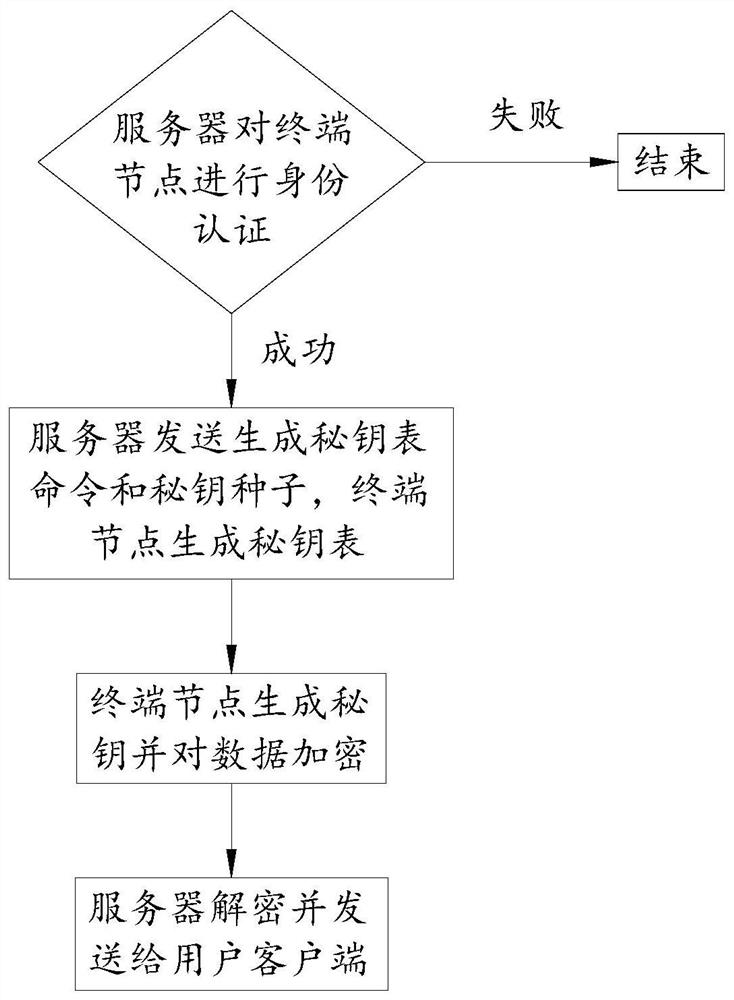
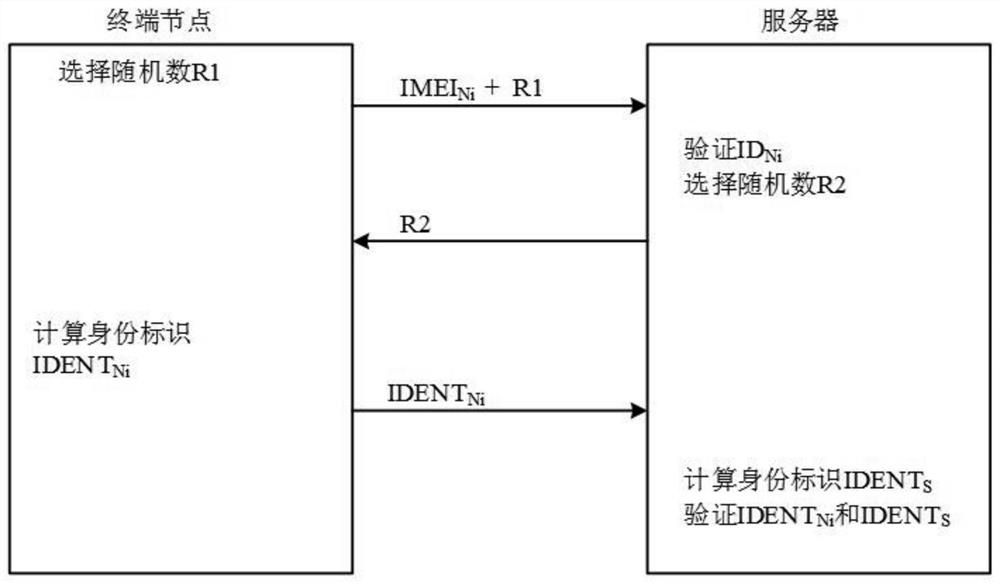
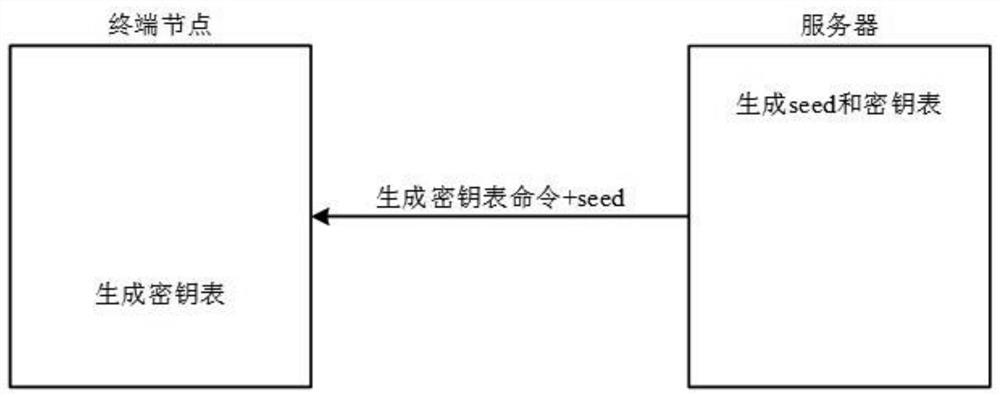
The invention discloses an encrypted communication method based on narrow-band internet of things and an encrypted communication device thereof. The communication method comprises the following steps:S1. A server authenticates a terminal node through a narrow-band internet of things communication module. If the authentication is successful, a communication connection is established, and if authentication fails, the process is ended; 2, the server sends a command for generating a secret key table and a secret key seed to the terminal node through a narrow band internet of things communicationmodule, and the terminal node generates the same secret key table as the server after receiving the secret key seed; 3, the terminal node generates a secret key and encrypts the data; and S4. the server decrypts the communication content and sends it to the user client. The invention utilizes the key seed to enable the terminal node and the server to have the same key table, and adopts the randomnumber coordinate method to share the key to improve the security of the key, so that the authentication between NB-IoT terminal and server is effectively carried out, thus improving the security of communication.
Owner:ZHANGJIAGANG INST OF IND TECH SOOCHOW UNIV +1
Software authentication method and system
InactiveCN102779247AEfficient authenticationImprove experienceComputer security arrangementsTime limitAuthentication
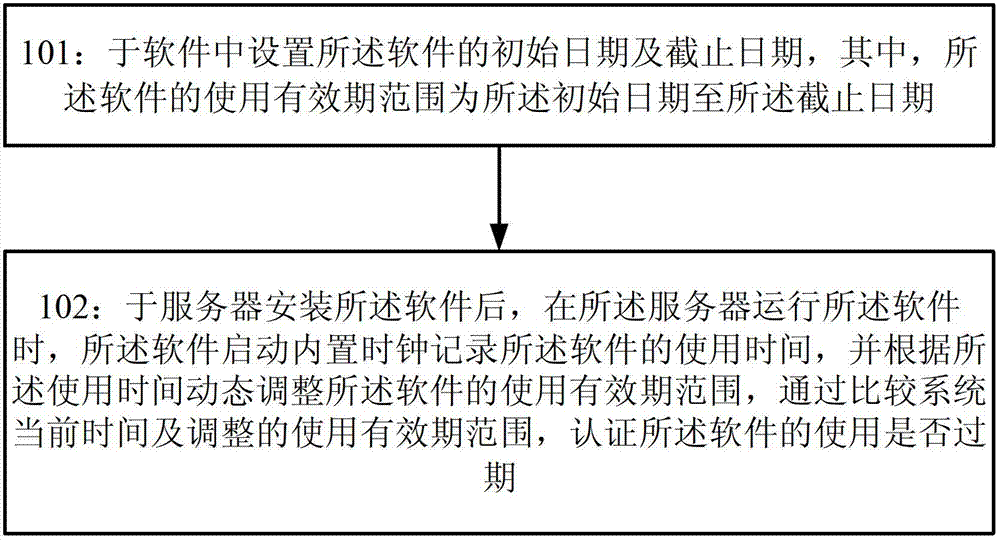
The invention provides a software authentication method and system. The method comprises the following steps of: setting an initial date and a deadline date of software in the software, wherein a utilization validity period range of the software ranges from the initial date to the deadline date; after the software is mounted on a server, recording utilization time of the software by starting an internally-arranged clock through the software when the software is operated by the server; dynamically adjusting the utilization validity period range of the software according to the utilization time; and comparing the current time of the system with the adjusted utilization validity period range to authenticate whether the utilization of the software exceeds the time limit or not.
Owner:SUZHOU CODYY NETWORK SCI & TECH
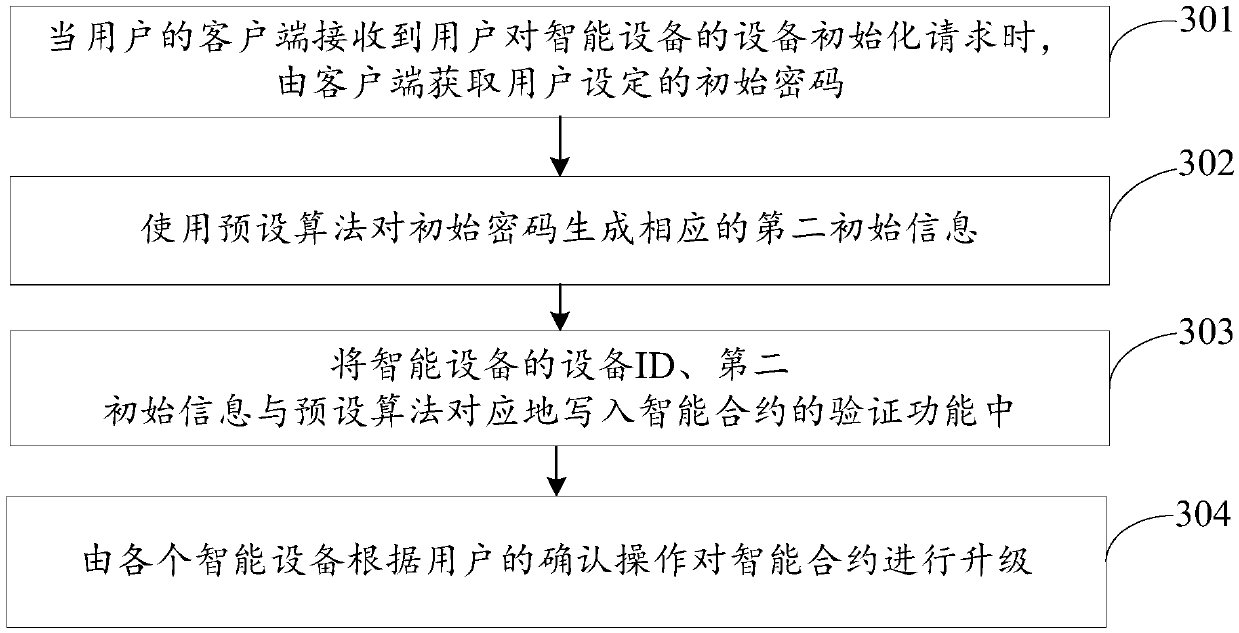
Realization method of intelligent equipment system, control methods and system of intelligent equipment
ActiveCN109660514APrevent leakageFix security issuesEncryption apparatus with shift registers/memoriesUser identity/authority verificationPrivate networkChain network
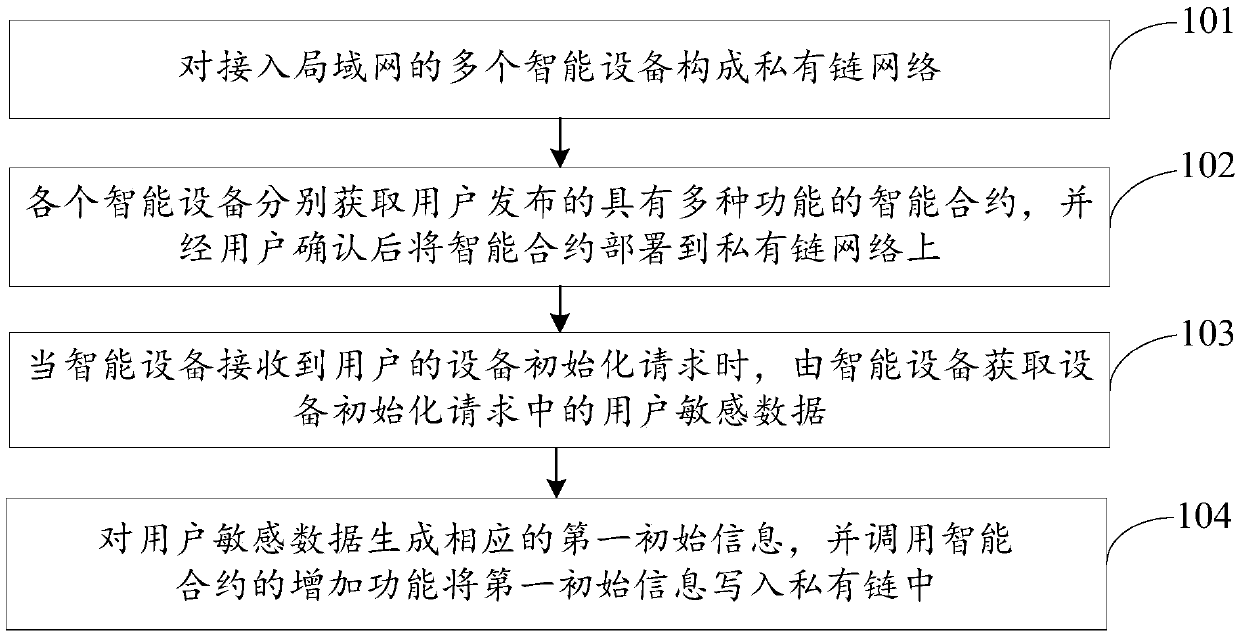
The invention discloses a realization method of an intelligent equipment system, control methods and system of intelligent equipment, and belongs to the technical field of the block chain. The methodcomprises the following steps: a private chain network is constructed for multiple intelligent equipment accessing to a local area network; each set of intelligent equipment acquires an intelligent contract published by a user and provided with multiple functions, and then deploys the intelligent contract on the private chain network after the user confirms; when the intelligent equipment receivesan equipment initialization request of the user, the intelligent equipment acquires user sensitive data in the equipment initialization request, and generates the corresponding first initial information for the user sensitive data; and an adding function of the intelligent contract is called to write the first initial information into the private chain. Through the embodiment of the invention, the user sensitive data acquired by the intelligent equipment is stored on the private chain through the intelligent contract, and the leakage of the user sensitive data can be avoided, thereby sufficiently guaranteeing the privacy and security of the user sensitive data.
Owner:SUNING COM CO LTD
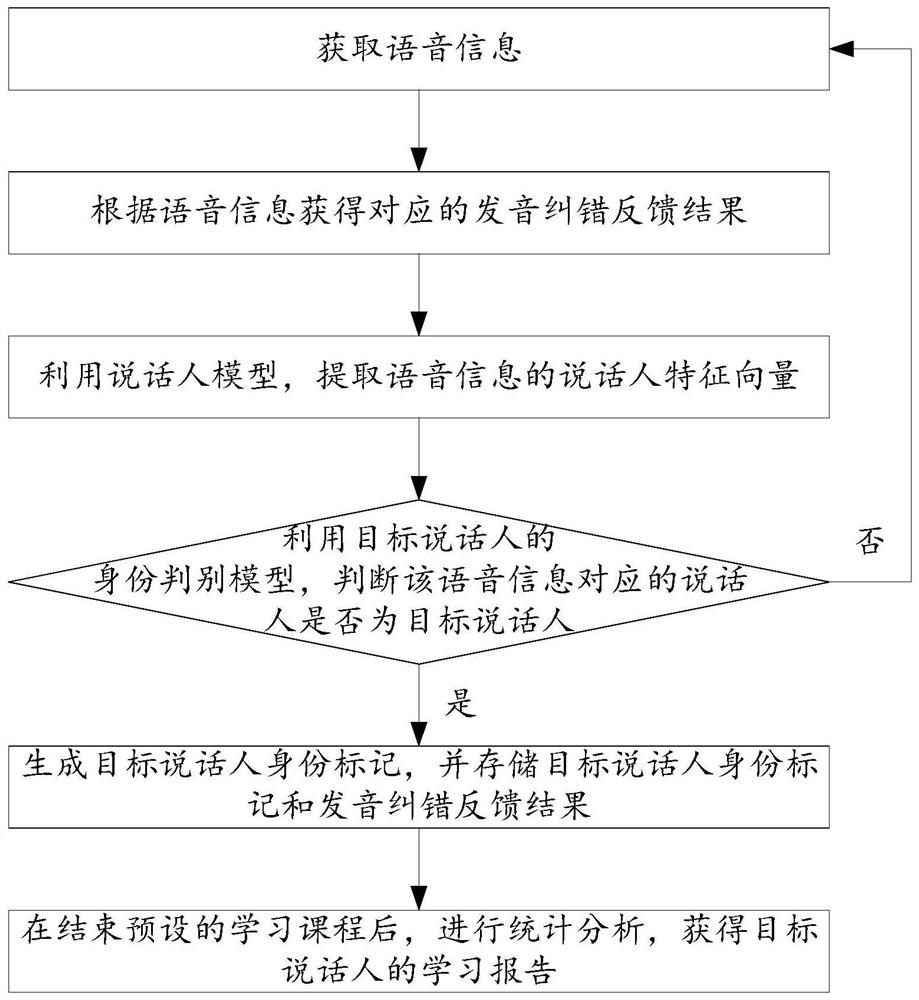
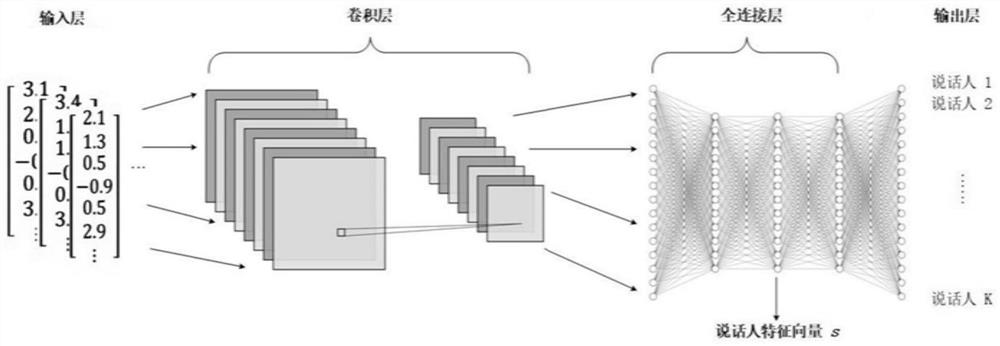
Pronunciation error correction learning method and device, storage medium and electronic equipment
PendingCN113053395AGuaranteed Learning ExperienceImplement identity authenticationSpeech analysisNeural architecturesModel extractionStatistical analysis
The invention discloses a pronunciation error correction learning method and device, a storage medium and electronic equipment, and relates to the technical field of online learning systems. The method comprises the steps of: acquiring voice information and a corresponding pronunciation error correction feedback result; extracting a speaker feature vector of the voice information by using a speaker model; according to the feature vector of the speaker and a stored feature vector of a target speaker, judging whether the speaker corresponding to the voice information is the target speaker or not by using an identity judgment model of the target speaker; and if yes, generating an identity mark of the target speaker, and storing the identity mark and the pronunciation error correction feedback result together, so as to perform statistical analysis after a preset learning course is ended, and obtain a learning report of the target speaker. According to the invention, the problem that the process of the identity authentication method in the existing online learning system is complex is solved, the identity authentication in the pronunciation error correction process is realized, and the situation that the identity authentication needs to be carried out independently before each pronunciation practice is avoided.
Owner:深圳市声希科技有限公司
Identity recognition method and device
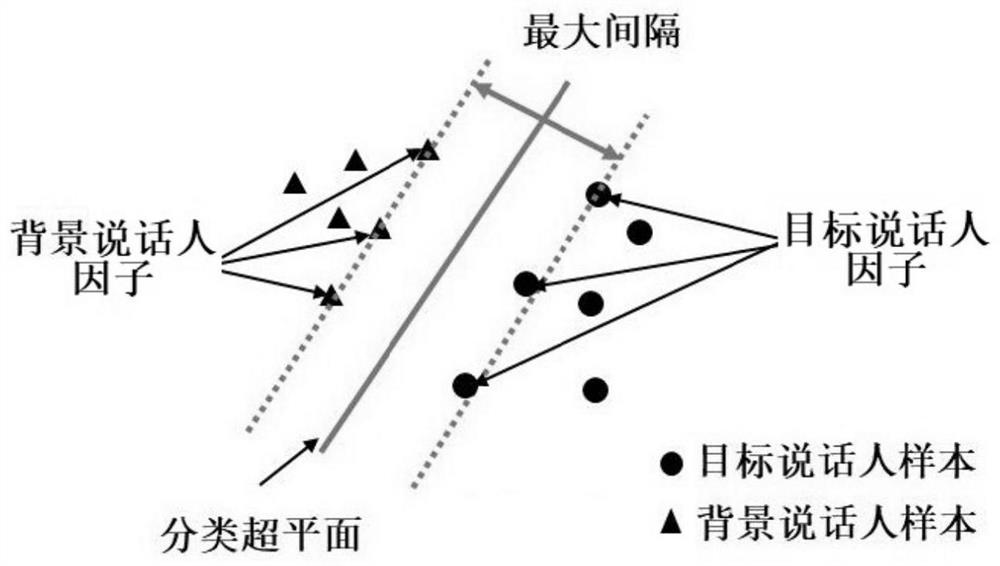
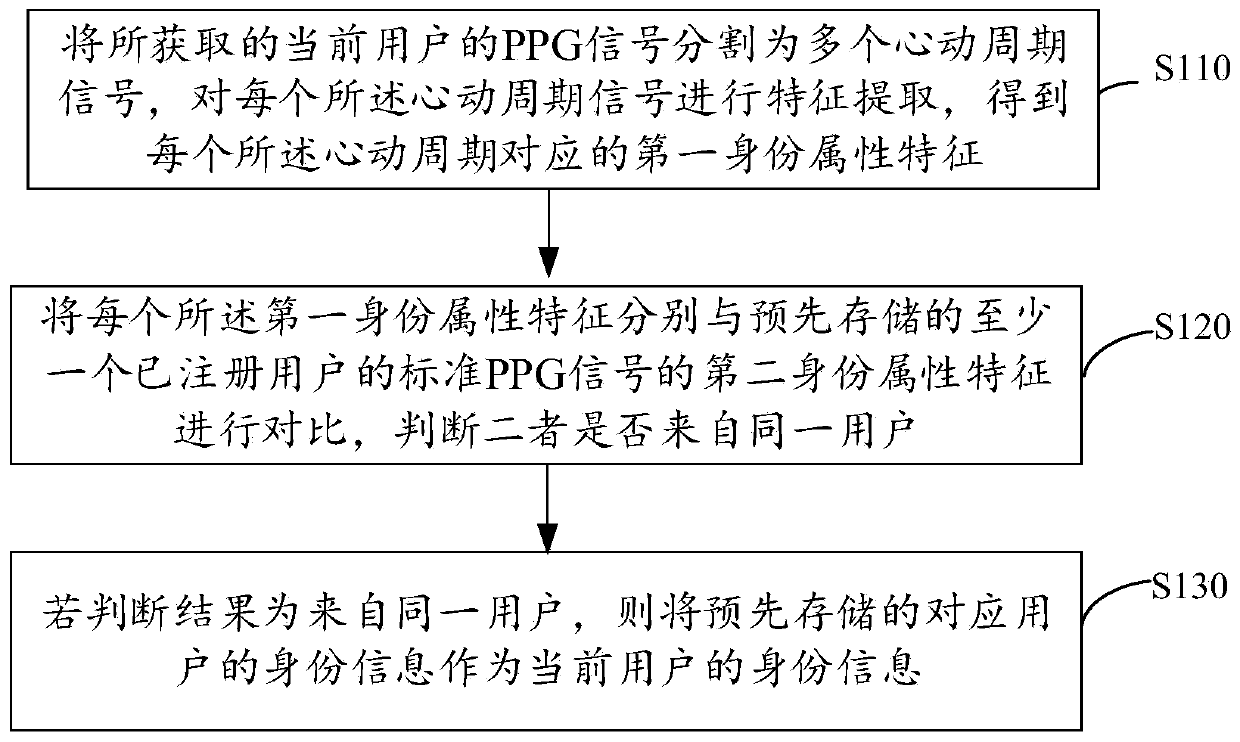
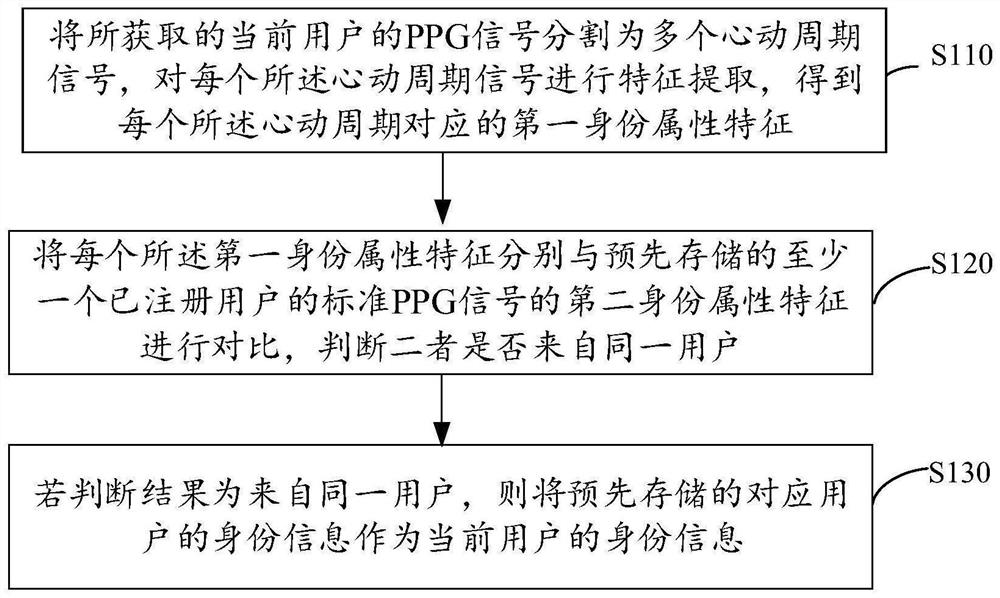
ActiveCN109919050AEfficient authenticationDistinctive featuresCharacter and pattern recognitionNeural architecturesFeature extractionIdentity recognition
The invention discloses an identity recognition method and device, and the method comprises the steps: dividing an obtained PPG signal of a current user into a plurality of cardiac cycle signals, carrying out the feature extraction of each cardiac cycle signal, and obtaining a first identity attribute feature corresponding to each cardiac cycle; Comparing each first identity attribute feature witha pre-stored second identity attribute feature of a standard PPG signal of at least one registered user, and judging whether the first identity attribute feature and the second identity attribute feature come from the same user or not; And if the judgment result is that the current user comes from the same user, taking pre-stored identity information corresponding to the user as the identity information of the current user.
Owner:天津惊帆科技有限公司
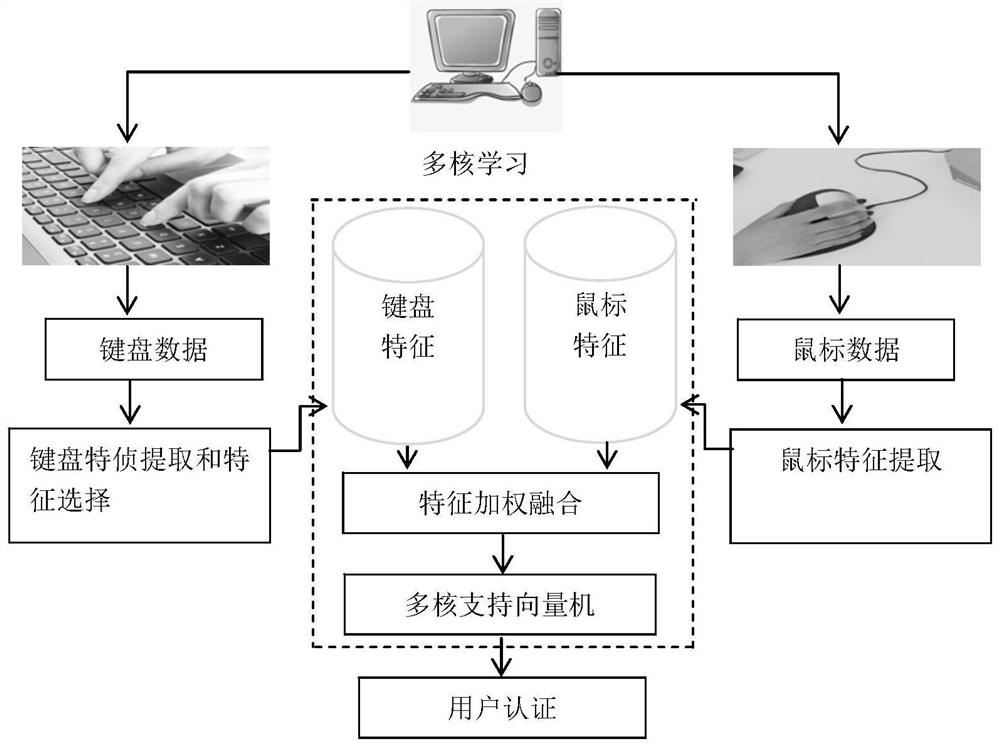
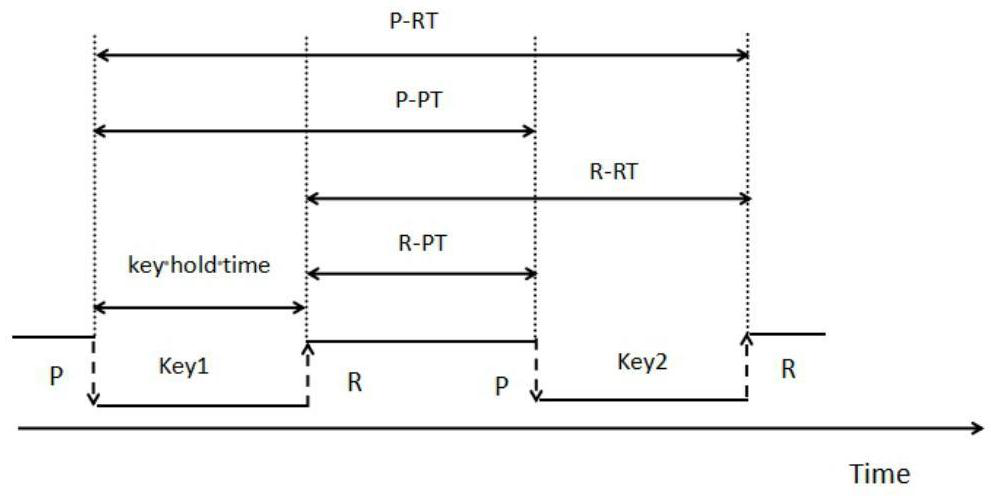
User identification method based on multi-kernel learning fused with mouse and keyboard behavior characteristics
ActiveCN111625789AEfficient authenticationImprove accuracyMathematical modelsKernel methodsSimulationProgram monitoring
The invention discloses a user identification method based on multi-kernel learning fused with mouse and keyboard behavior characteristics. In an uncontrolled environment, human-computer interaction behaviors of a user are monitored through a program to obtain real data generated by keyboard and mouse operations in daily work, two characteristics of a mouse and a keyboard are extracted, characteristic fusion and efficient classification are carried out through MKL, and finally efficient identity authentication of the user is achieved.
Owner:BEIJING UNIV OF TECH +1
Banknote sorter with double-side image scanning function
InactiveCN102456247ASimple structureCompact structurePaper-money testing devicesCharacter and pattern recognitionContact image sensorContact type
The invention discloses a banknote sorter with a double-side image scanning function. The upper part of a contact-type image sensor is arranged on the upper module of the sorter. The lower part of the contact-type image sensor is arranged on the lower module of the sorter. The lower end surface of the upper part of the contact-type image sensor is smaller than the upper end surface of the lower part of the contact-type image sensor. Part of the upper end surface is overlapped with the lower end surface. A front side magnet, a side thick sliding wheel and a middle magnet are arranged on the upper module of the sorter. A banknote conveying wheel is arranged on the lower module of the sorter at a position corresponding to the front side magnet, a side thick shaft is arranged on the lower module of the sorter at a position corresponding to the side thick sliding wheel and a coder is arranged on the lower module of the sorter at a position corresponding to the middle magnet. A driving belt is additionally arranged at the front end of the upper module of the sorter. The internal structure of the banknote sorter with the double-side image scanning function is compact and the sorter is smart; and by adopting the image sensor, the sorter has the characteristic of high banknote authentication efficiency.
Owner:SHANGHAI GOOAO ELECTRONIC TECHNOLOGY CORP
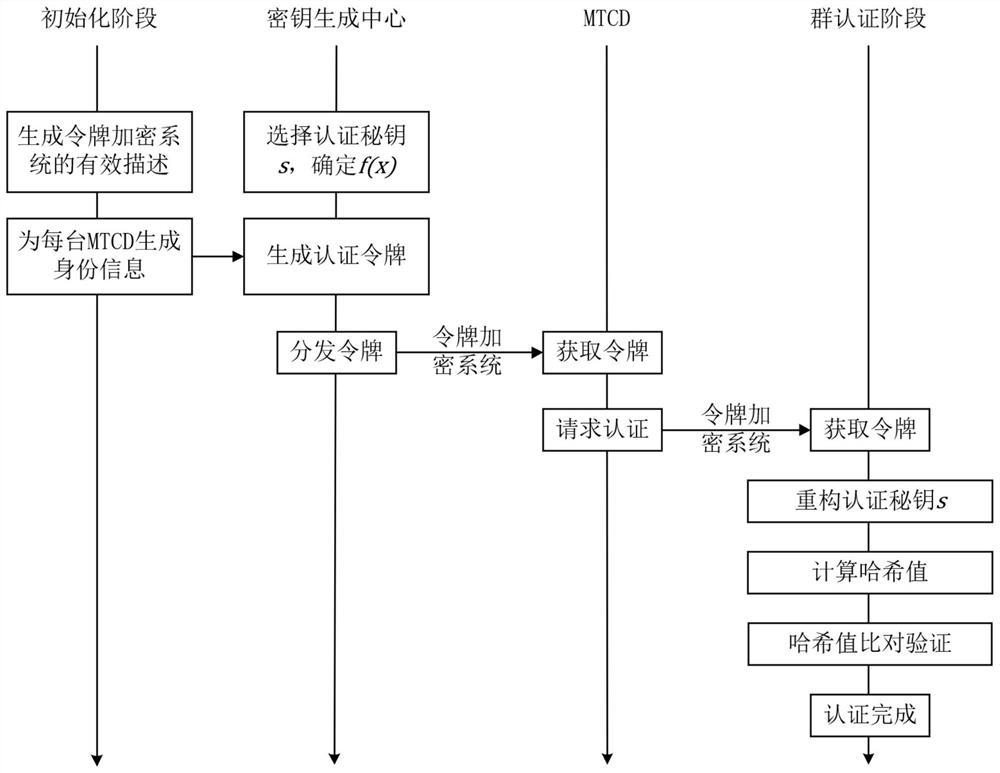
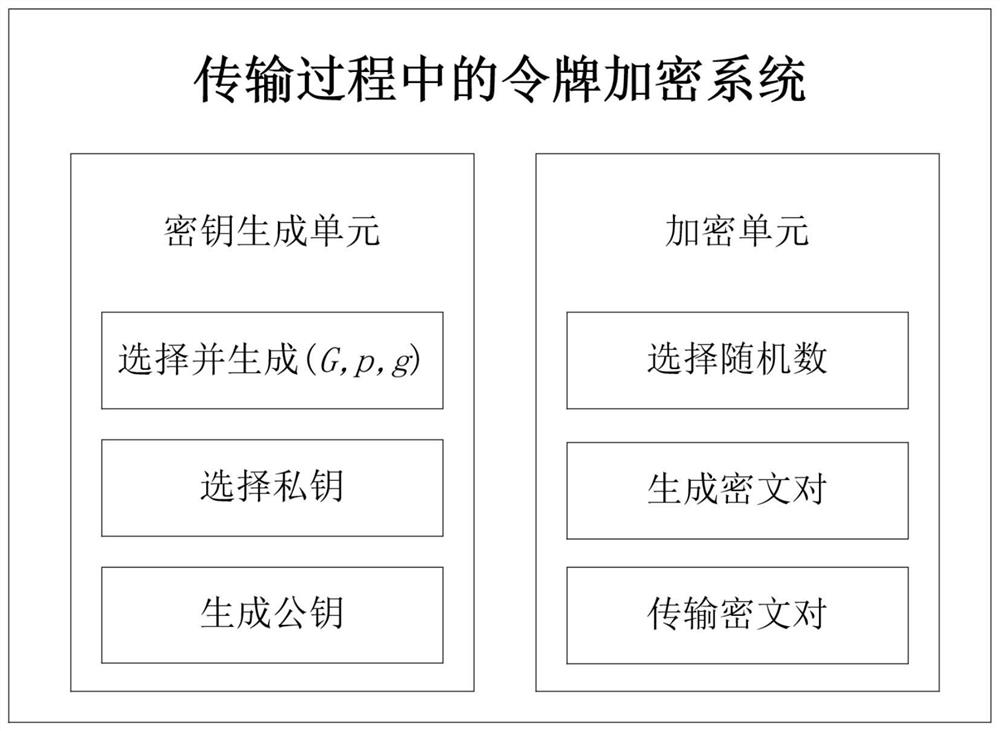
Group authentication method and system in asynchronous group communication of LTE network machine type communication equipment
ActiveCN112118569AComplete refactoringNo AccessUser identity/authority verificationSecurity arrangementAuthentication systemData messages
Related technologies of the Internet-of-things are developed rapidly and widely applied. Machine type communication (MTC) can complete data information exchange and sharing between equipment without active participation of a user, has the characteristics of low cost, low power consumption and capability of transmitting information on a large scale, and is one of the most important communication modes in the Internet-of-things. Therefore, the security of the MTC needs to be emphasized, and the data security of the user needs to be protected. The invention provides a group authentication methodand a group authentication system in asynchronous group communication of machine type communication equipment in an LTE network, which construct a group authentication scheme by utilizing a (t, n) secret sharing scheme of Shamir, authenticate m (m is greater than or equal to t) machine type communication equipment (MTCD) at one time, and ensure the legality of MTCD identity of an access network. Meanwhile, in the token transmission process, an ElGamal encryption algorithm is used to ensure the security of the authentication token in the transmission process. By utilizing the method and the system, the group authentication can be completed only by one-time calculation, the confidentiality can reach the calculation security, and each group member only needs to carry one authentication token.
Owner:LANZHOU UNIVERSITY
Method of automatically authenticating value-added-tax special invoices
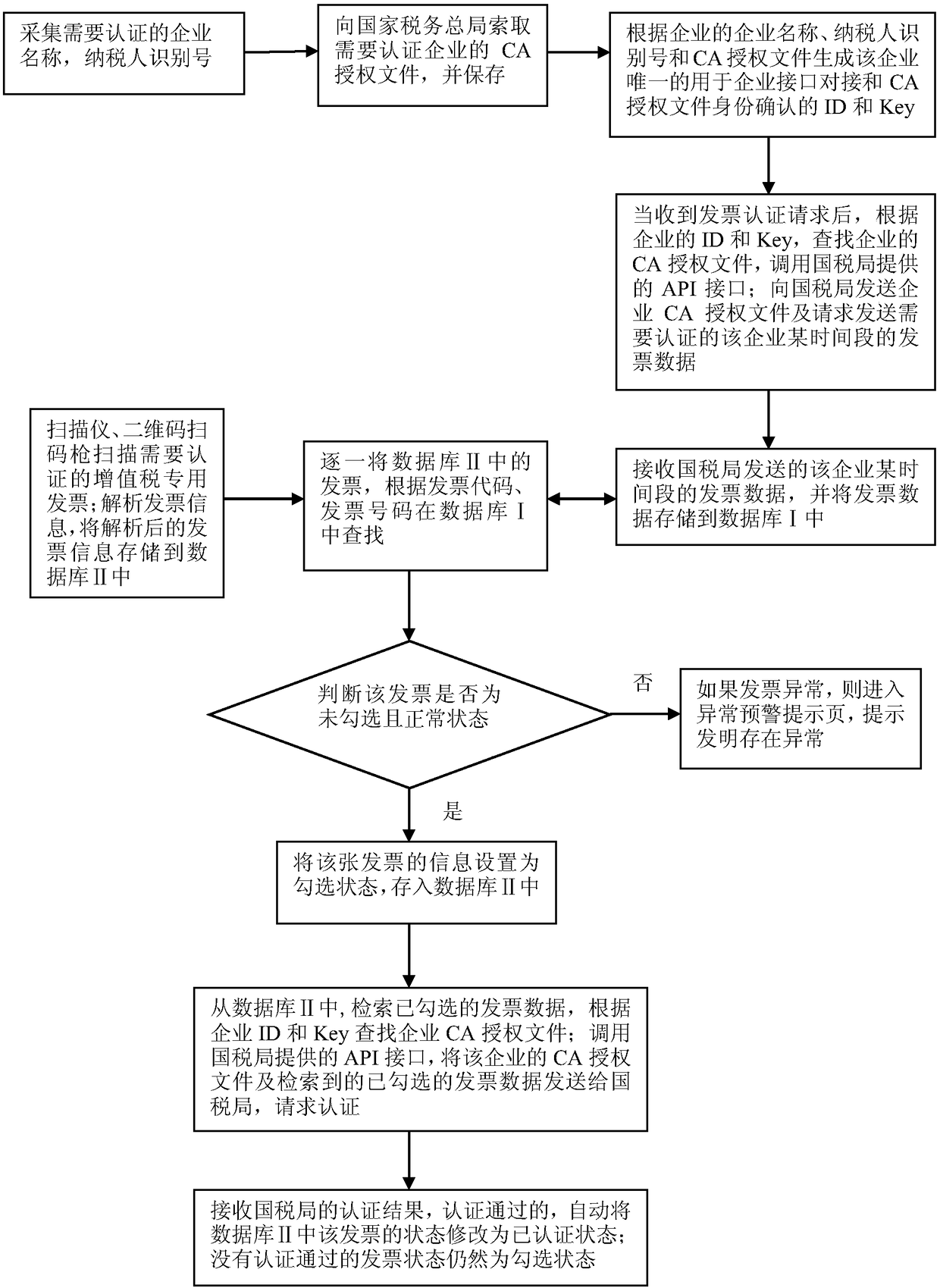
ActiveCN108710678AImplement automatic authenticationEfficient authenticationFinanceCo-operative working arrangementsButt jointInvoice
The invention provides a method of automatically authenticating value-added-tax special invoices. The method includes: collecting enterprise information needing to be authenticated; requesting a CA authorization file of an enterprise from the State Administration of Taxation, and saving the same; generating unique ID and Key, which are of the enterprise and are used for enterprise interface butt-joint-connection and CA authorization file identity confirmation, according to the enterprise information and the CA authorization file; calling an API interface, which is provided by the state tax bureau, when a request that the enterprise needs to authenticate the value-added-tax special invoices is received; sending the CA authorization file of the enterprise to the state tax bureau, requestingsending of invoice data which are of the enterprise and a certain time period and need to be authenticated, and saving the same to a database I; quickly and massively scanning the value-added-tax special invoices, which need to be authenticated, through scanners and two-dimensional-code scanning guns; parsing invoice information, and saving the same; retrieving the invoices, which need to be authenticated, one by one in the database I, and setting status thereof to ticked status after the same are found; sending the ticked invoices and the CA authorization file of the enterprise to the state tax bureau to request authentication, and keeping authentication results.
Owner:北京票通信息技术有限公司
Device access processing method, device access processing device and terminal
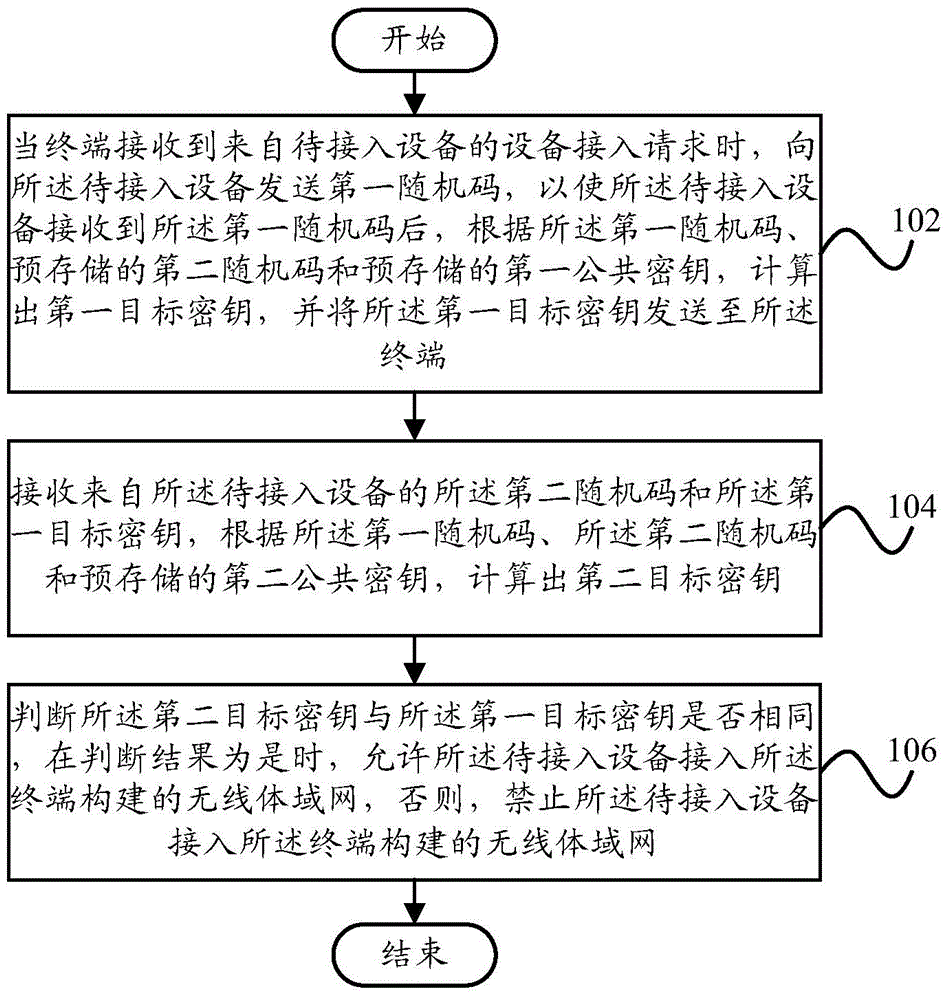
ActiveCN105636032AImprove versatilityEfficient authenticationUser identity/authority verificationSecurity arrangementComputer securitySecurity authentication
The invention discloses a device access processing method, a processing device and a terminal. The processing method comprises following steps: when the terminal receives a device access request from a to-be-accessed device, sending a first random code to the to-be-accessed device; after the to-be-accessed device receives the first random code, calculating a first target key according to the first random code, a pre-stored second random code and a pre-stored first public key; sending the first target key to the terminal; receiving a second random code and the first target key from the to-be-accessed device; calculating a second target key according to the first random code, the second random code and a pre-stored second public key; judging whether the second target key and the first target key are the same; if the judging result is yes, allowing the to-be-accessed device to access a wireless body area network, or forbidding the to-be-accessed device to access the wireless body area network. The technical solution of the invention is general, is low in calculation quantity and can carry out security authentication to the access device in the wireless body area network efficiently.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
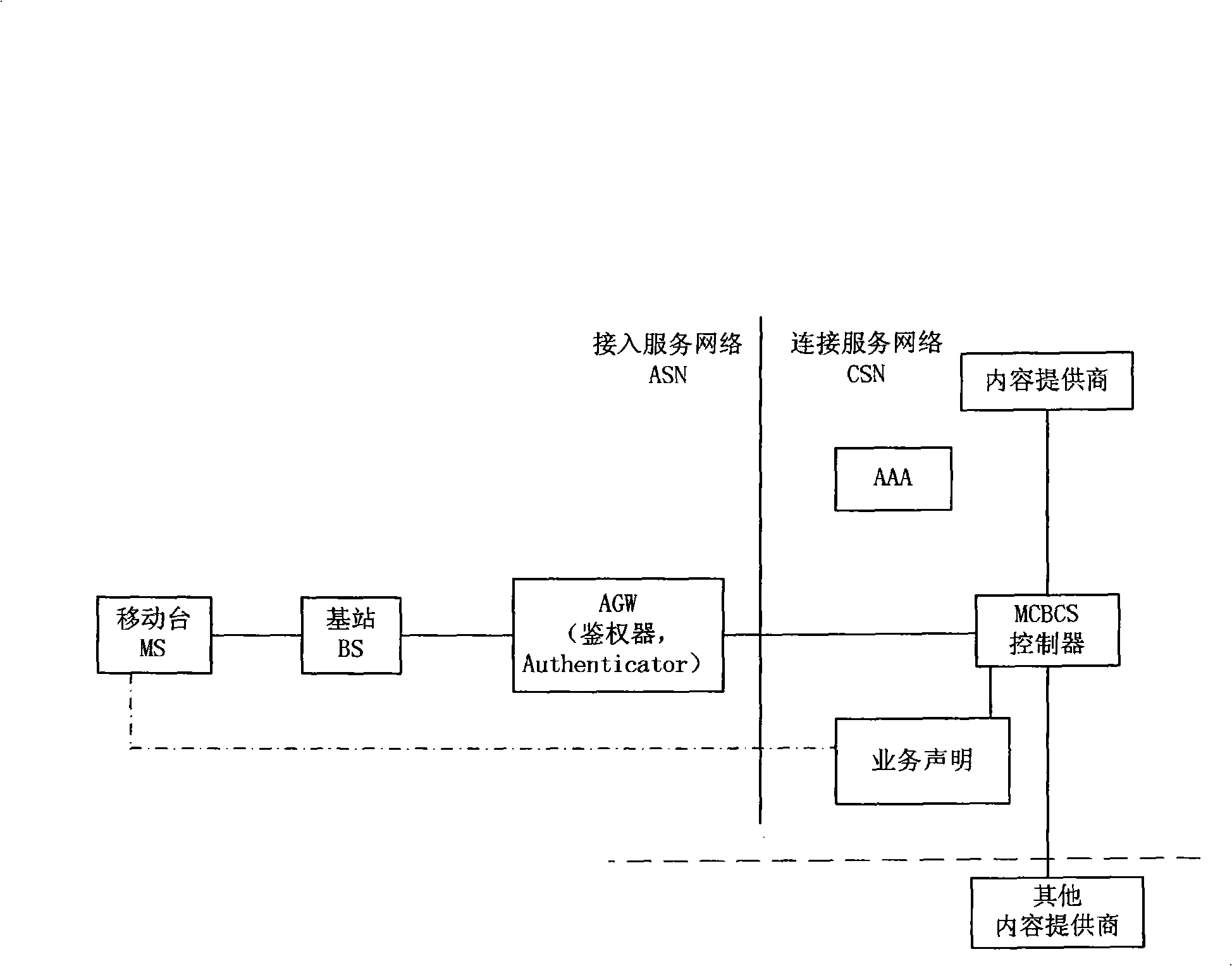
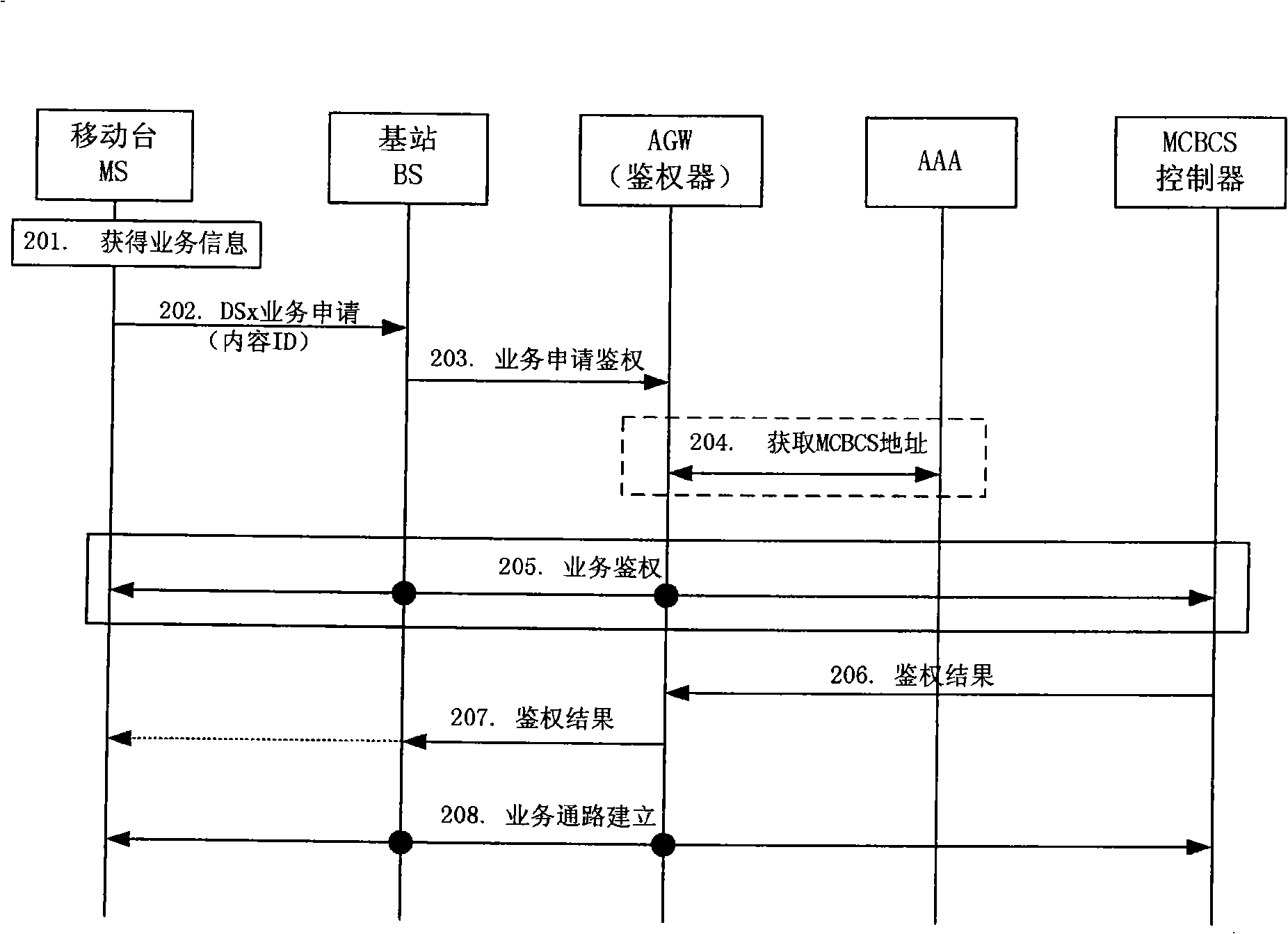
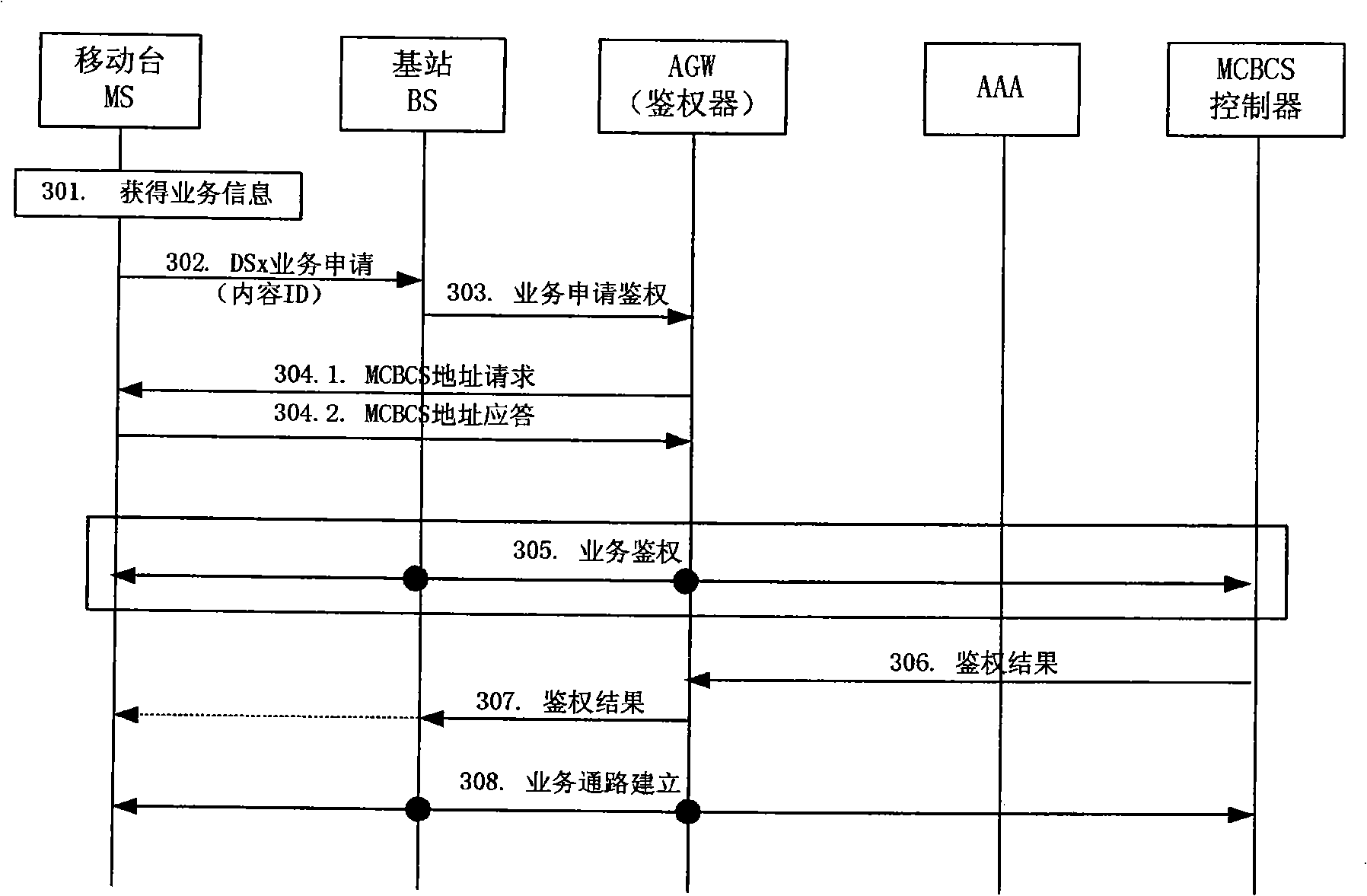
Method for multicast broadcasting service authentication
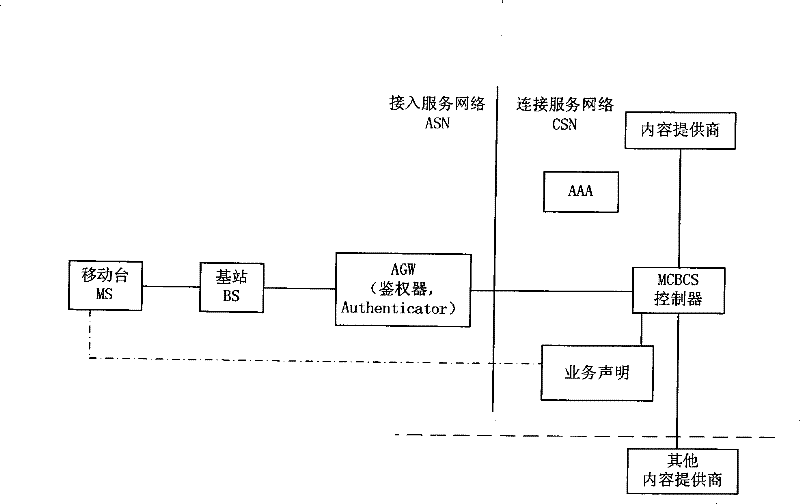
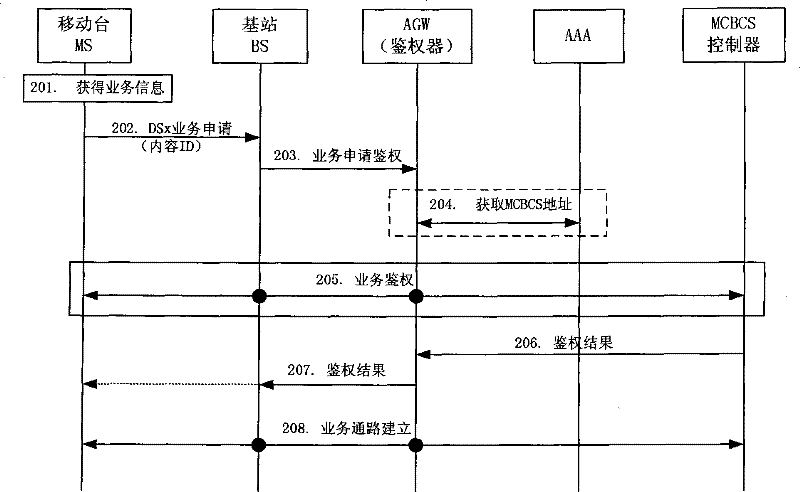
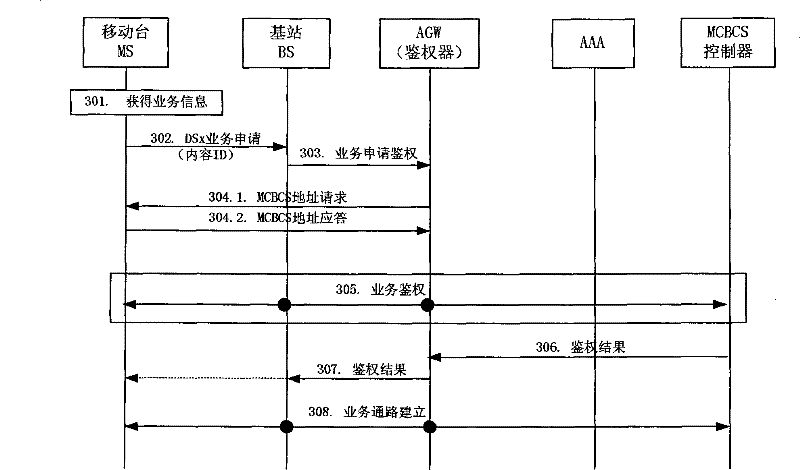
InactiveCN101296106AImprove business experienceEfficient authenticationSpecial service provision for substationData switching by path configurationService experienceComputer science
The invention discloses a method for authenticating multicast broadcast service which comprises the following steps: a mobile terminal initiates an application message for multicast broadcast service to a base station which transmits a request message for service authentication to a authenticator; the authenticator acquires a mark of a multicast broadcast service supplier or an address of a multicast broadcast service controller from the request message for the service authentication, or acquires the mark of the multicast broadcast service supplier or the address of the multicast broadcast service controller from the mobile terminal, and the authenticator acquires the address of the multicast broadcast service controller through the mark of the multicast broadcast service supplier; and the authenticator initiates an authentication request to the multicast broadcast service controller indicated by the address of the multicast broadcast service controller. By adopting the method of the invention, a highly efficient authentication of MCBCS registration process actively initiated by the user is realized and service experience of the user is improved.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
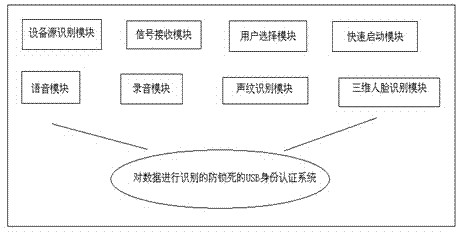
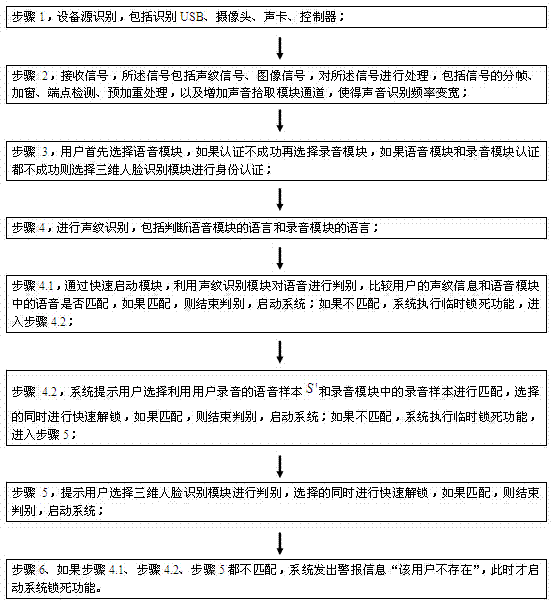
Anti-lock USB (universal serial bus) identity authentication system and anti-lock USB identity authentication method by means of recognizing data
InactiveCN104734858AEfficient authenticationAvoid deadlockUser identity/authority verificationUSBAuthentication system
The invention provides an anti-lock USB (universal serial bus) identity authentication system and an anti-lock USB identity authentication method by means of recognizing data. The anti-lock USB identity authentication system comprises an equipment source recognizing module, a signal receiving module, a user selection module, a speech module, a recording module, a voiceprint recognizing module, a three-dimensional face recognizing module and a quick starting module. The voiceprint recognizing module comprises a speech module judging module and a recording module judging module. The anti-lock USB identity authentication method includes steps of recognizing equipment sources; receiving signals; enabling users to select authentication modules; recognizing voiceprints; three-dimensionally recognizing faces of the users; matching results with one another. The anti-lock USB identity authentication system and the anti-lock USB identity authentication method have the advantages that a plurality of options for identity authentication can be provided for the users, so that identities of the users can be quickly and efficiently authenticated, system locking due to misoperation or accidents can be prevented, and problems of voiceprint matching failures due to poor personal health or unwell moods and incapability of using systems can be solved; the various authentication modules with authentication functions are built, and accordingly flexible, accurate and efficient identity authentication can be guaranteed.
Owner:HEILONGJIANG UNIV OF CHINESE MEDICINE
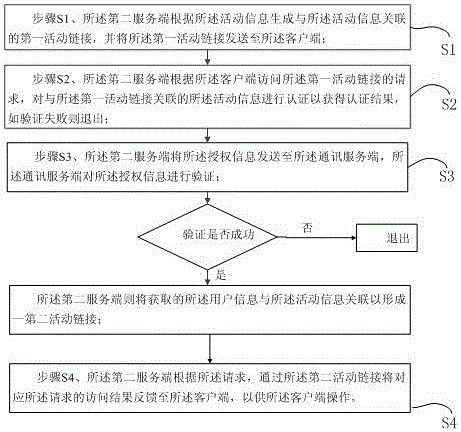
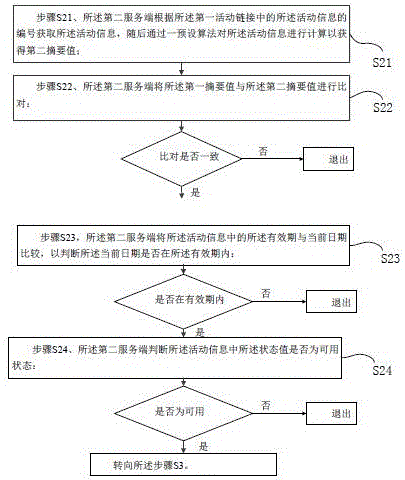
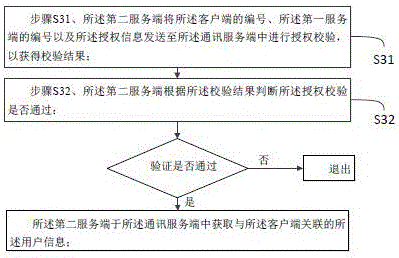
Activity management method and system based on instant messaging software
ActiveCN106161211AEasy to manageEasy accessData switching networksMarketingAuthorizationCommunications server
The invention provides an activity management method and system based on instant messaging software. A second server generates a first activity link associated with activity information according to the activity information and sends the first activity link to a client; the second server authenticates the activity information according to a request of the client for having access to the first activity link so as to judge whether the activity information is effective or not, and if not, exiting is conducted; a communication server receives authorization information sent by the second server and conducts verification; if the verification is passed, the second server associates acquired user information with the activity information to form a second activity link; if the verification fails, exiting is conducted; the second server feeds an access result corresponding to the request back to the client through the second activity link according to the request so that the client operation can be conducted. According to the technical scheme, the activity management method and system have the advantages that the activity information can be managed conveniently and authenticated efficiently in time, and a user of the client can have access to the activity information conveniently in time.
Owner:SHANGHAI HANDPAL INFORMATION TECH SERVICE
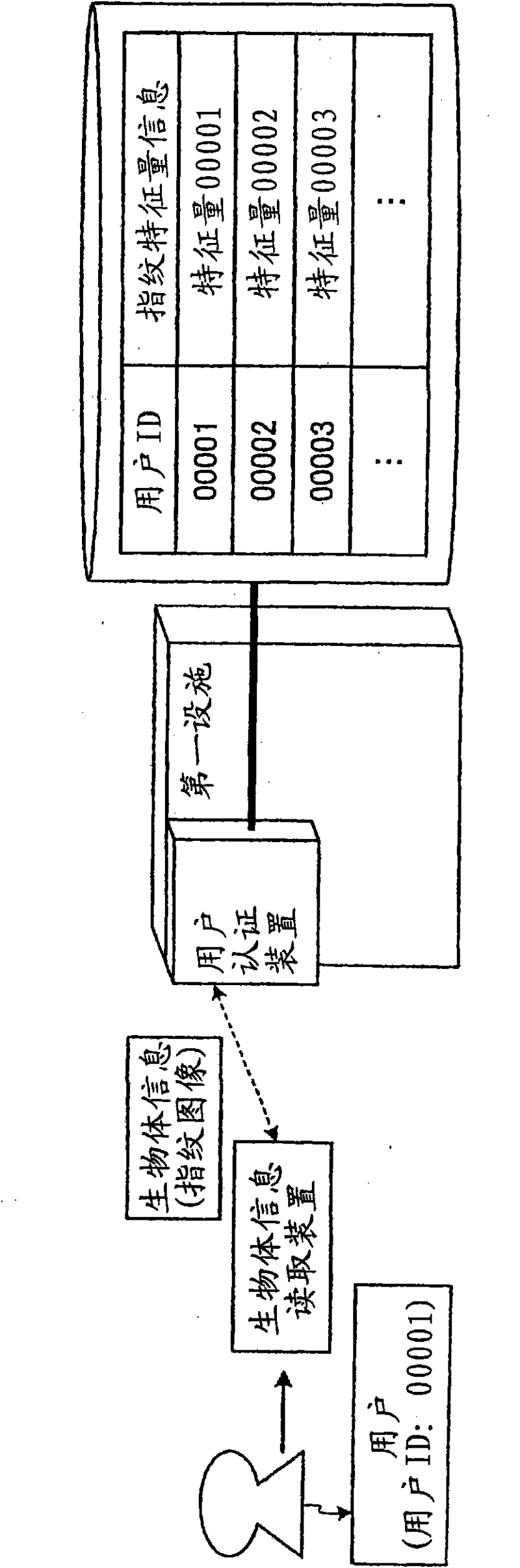
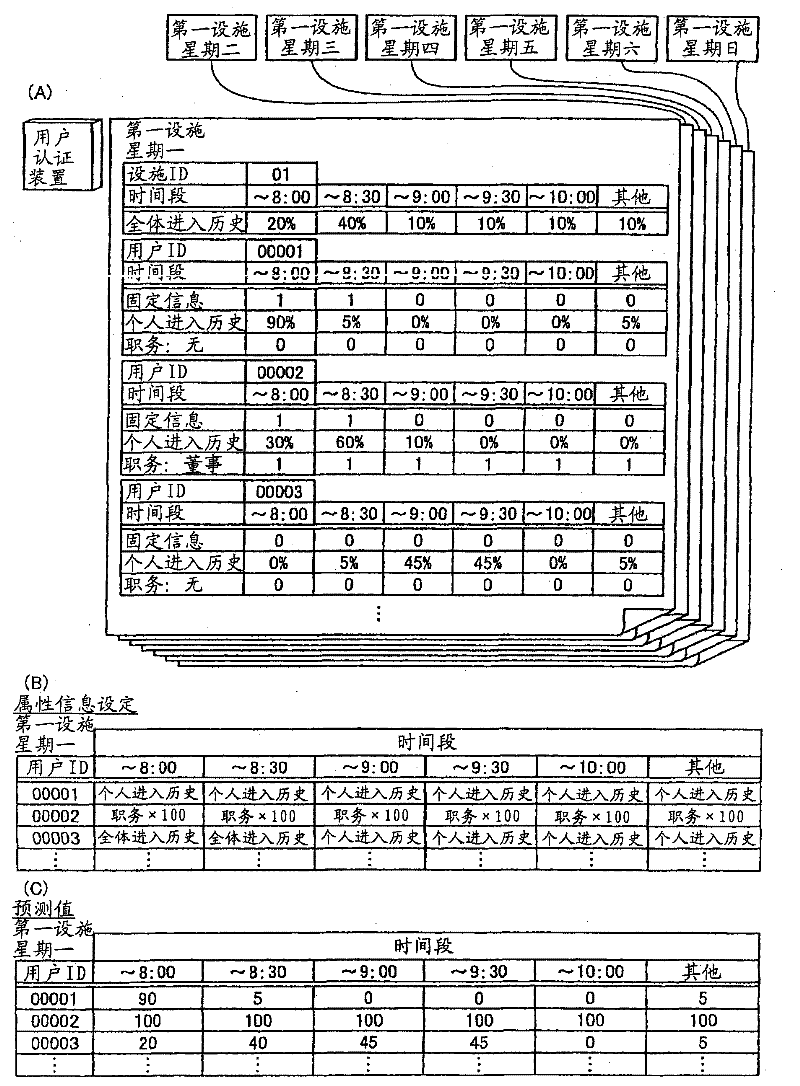
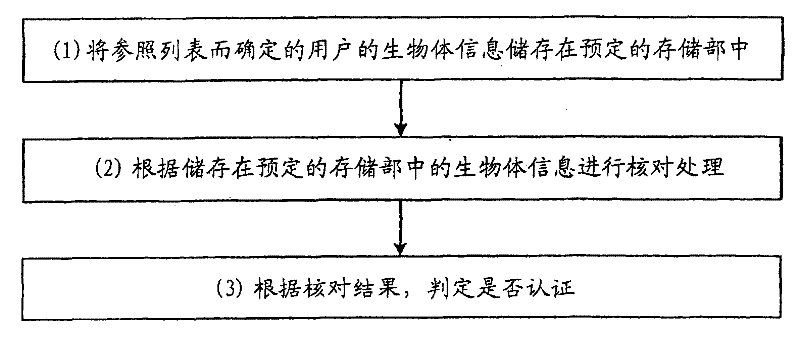
User authentication device, user authentication method
ActiveCN101689235BEfficient authenticationHigh precisionImage analysisCharacter and pattern recognitionInternet privacyUser authentication
Owner:FUJITSU LTD
Vehicle path planning method with privacy protection
InactiveCN113242222APrivacy protectionEfficient authenticationInstruments for road network navigationCommunication with homomorphic encryptionPrivacy protectionReal-time computing
The invention discloses a vehicle path planning method with privacy protection, and the method comprises the steps: an initialization stage: a certification authority constructs related information of a roadside unit, and generates and issues related safety parameters; a registration stage which is used for verifying the identity of the vehicle before entering the system; a query stage, in which path planning is carried out on the vehicle, and required roadside unit information is acquired from a certification authority. Path planning with privacy protection is realized by using BGN homomorphic encryption, so that the path information planned in advance is not leaked when the vehicle acquires the roadside unit information from the authentication authority, the privacy security of the vehicle is effectively protected, and the authentication efficiency of the vehicle and the roadside unit is greatly improved.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Anti-lock usb identity authentication system and method for identifying data
InactiveCN104734858BEfficient authenticationAvoid deadlockUser identity/authority verificationAuthentication systemUSB
The invention proposes an anti-locking USB identity authentication system and method for identifying data. The system includes: a device source identification module, a signal receiving module, a user selection module, a voice module, a recording module, a voiceprint recognition module, a three-dimensional face recognition module, and a quick start module, wherein the voiceprint recognition module includes a judgment module of the voice module and The judgment module of the recording module; the method includes: device source identification, signal reception, user selection authentication module, voiceprint recognition, three-dimensional face recognition, and matching result steps. Through the system and method, the user is provided with multiple choices for identity authentication, which can be quickly and efficiently authenticated, prevents the system from being locked due to improper operation or accident, and avoids the failure of voiceprint matching due to personal physical or emotional discomfort. Use the system and model the authentication function of each authentication module to ensure flexible, accurate and efficient identity authentication.
Owner:HEILONGJIANG UNIV OF CHINESE MEDICINE
Encrypted communication method and encrypted communication device based on narrowband internet of things
Owner:ZHANGJIAGANG INST OF IND TECH SOOCHOW UNIV +1
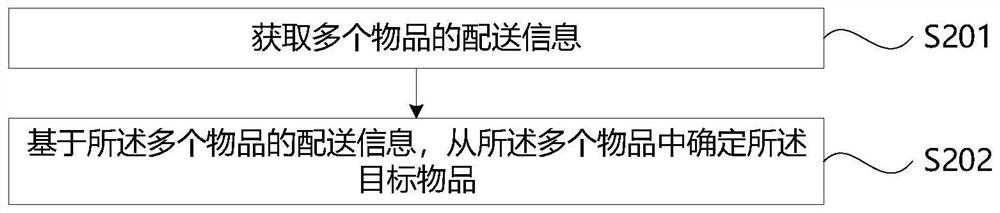
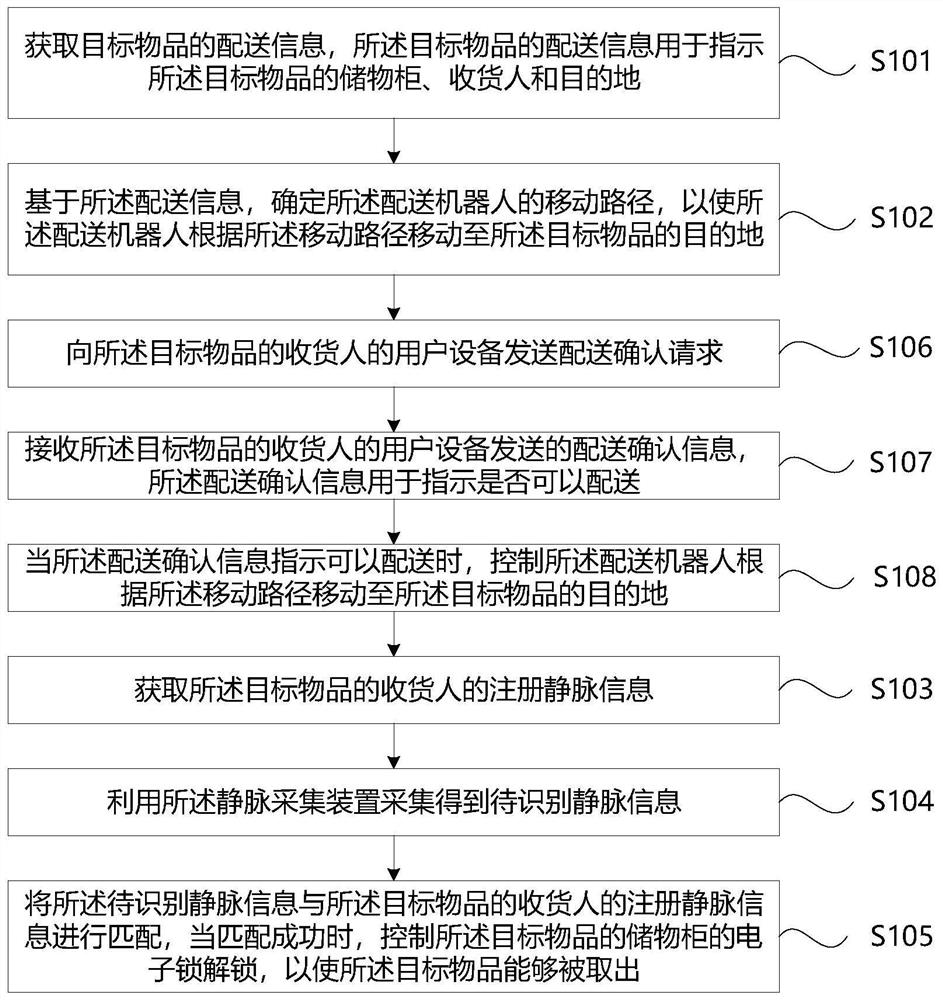
Control method of distribution robot and related device
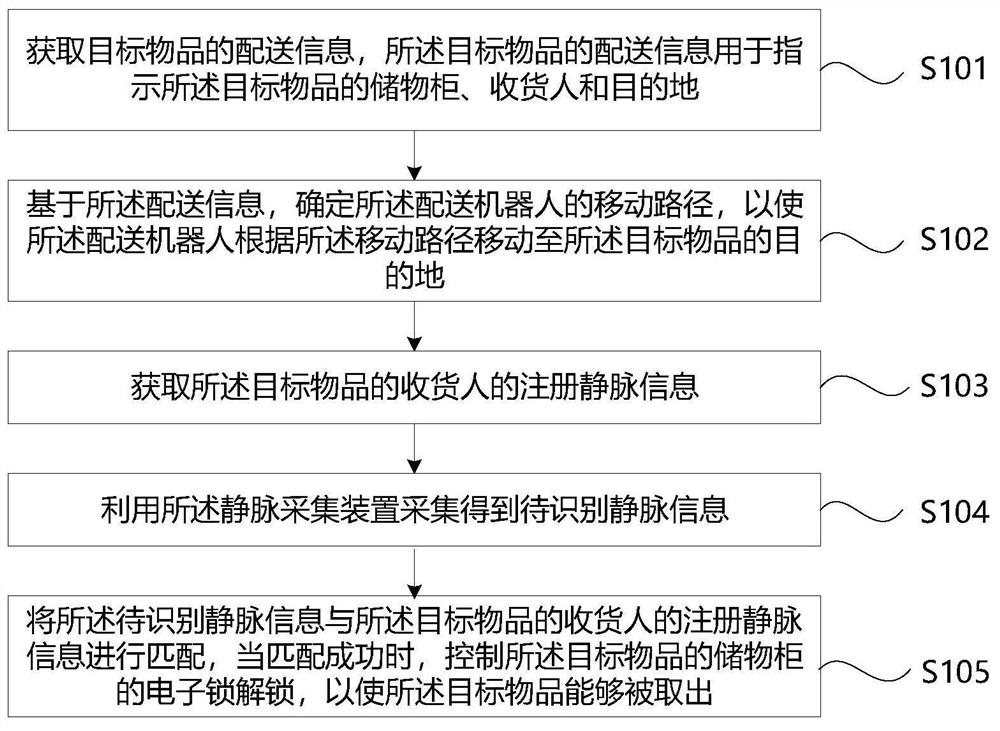
PendingCN113977597AEfficient accessEasy accessProgramme-controlled manipulatorTotal factory controlComputer visionControl objective
The invention provides a control method and device of a distribution robot, the distribution robot and a computer readable storage medium. The control method comprises the steps of acquiring distribution information of a target article, based on the distribution information, determining a moving path of the distribution robot, so that the distribution robot moves to a destination of the target article, acquiring registered vein information of a consignee of the target article, acquiring to-be-recognized vein information by using a vein acquisition device, and matching the to-be-recognized vein information with registered vein information of a consignee of the target article, and when matching succeeds, controlling an electronic lock of a storage cabinet of the target article to be unlocked, so that the target article can be taken out. According to the method and the device, the consignee of the target article can efficiently and conveniently perform identity verification and take the target article, so that the distribution efficiency is improved.
Owner:深兰机器人产业发展(河南)有限公司
Identification method and device
ActiveCN109919050BEfficient authenticationDistinctive featuresCharacter and pattern recognitionNeural architecturesFeature extractionMedicine
The invention discloses an identification method and device, wherein the identification method includes: dividing the obtained PPG signal of the current user into multiple cardiac cycle signals, performing feature extraction on each of the cardiac cycle signals, and obtaining each The first identity attribute characteristics corresponding to the cardiac cycle; each of the first identity attribute characteristics is compared with the second identity attribute characteristics of the standard PPG signal of at least one registered user in advance, and it is judged whether the two are from The same user; if the judgment result is from the same user, the pre-stored identity information of the corresponding user is used as the identity information of the current user.
Owner:天津惊帆科技有限公司
An identity authentication method based on ultrasonic lip recognition
ActiveCN106778179BAvoid security breachesLower deployment costsDigital data authenticationFeature extractionMedicine
An identity authentication method based on ultrasonic lip recognition, comprising the following steps: (1) a signal transmitting source sends an ultrasonic signal, and a signal receiving source receives a reflected signal from the mouth; (2) lip language feature extraction is performed on the collected reflected signal , the extracted lip features include a spectrum feature corresponding to a lip event and the user's dynamic lip contour features; (3) identifying and authenticating the user according to the lip features extracted in step (2). The beneficial effects of the present invention are: on the basis of no need for additional hardware customization, the characteristic parameters of identity authentication are obtained by using the ability of ultrasonic sensing, the deployment cost is low, and the application scene of ultrasonic technology in mobile terminals is expanded; the use of users to express the same lip language The difference in behavior habits at the time of the event, combined with biological characteristics, solves the security loopholes in existing technologies such as facial recognition and fingerprint recognition, and can achieve efficient identity authentication.
Owner:NANJING UNIV
Blockchain-based identity authentication system, authentication method, medium, and terminal
ActiveCN113221189BImplement lightweight authenticationLow costDatabase distribution/replicationDigital data protectionRelevant informationCiphertext
Owner:HUAZHONG UNIV OF SCI & TECH
A device and method for protecting secure socket layer session keys
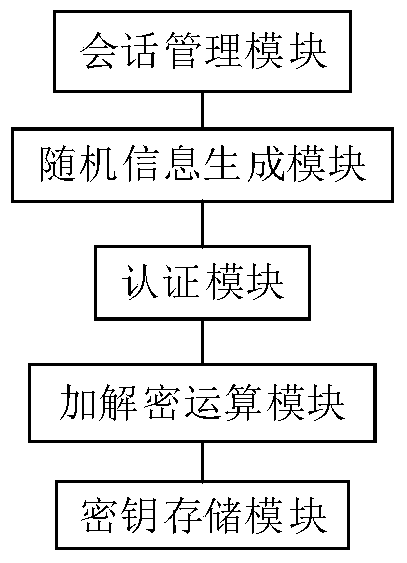
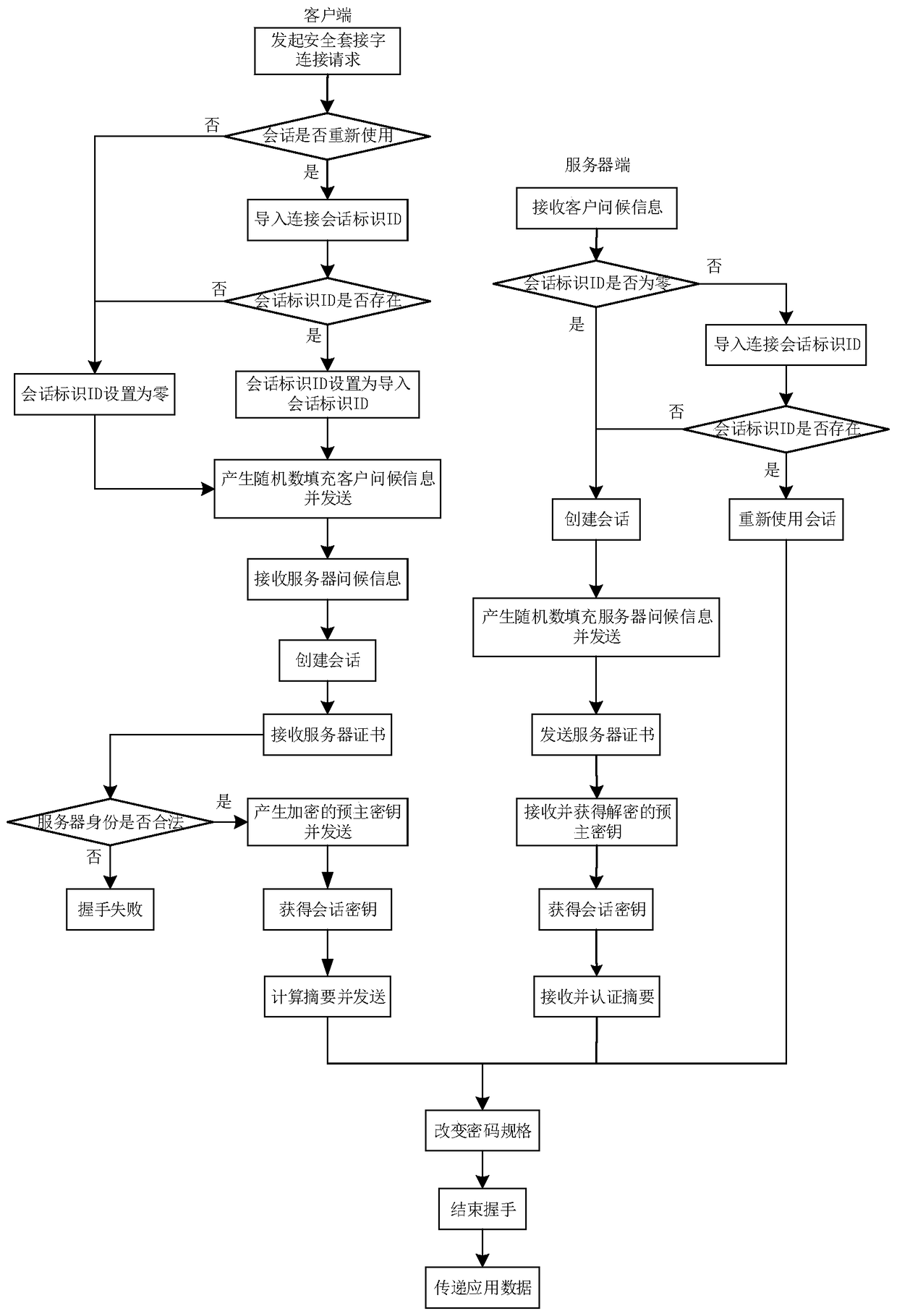
ActiveCN104702611BOvercome deficienciesSolve the lack of reliabilityTransmissionSession managementComputer module
The invention discloses equipment and a method for protecting a session key of a secure socket layer. By hardware equipment, key information of a protocol of the secure socket layer cannot be exposed in a software environment in a cleartext mode, and the safety of a key in communication of the protocol of the secure socket layer is improved. The equipment comprises a session management module, a random information generating module, a certification module, an encryption and decryption computing module and a key storage module. On the basis of secure socket layer protocol connection established by client sides and a server and session key facilities which are respectively arranged on the client sides and the server, the method comprises the following steps of management session implementing, random number generation, certification and generation and session key using and storing through the facilities by using the client sides and the server. The session key of the protocol of the secure socket layer is protected by the hardware equipment, the credibility of the session key is improved, and the protocol of the secure socket layer is safe and reliable.
Owner:XIDIAN UNIV
Method for multicast broadcasting service authentication
InactiveCN101296106BImprove business experienceEfficient authenticationSpecial service provision for substationData switching by path configurationService experienceBroadcast service
Owner:GLOBAL INNOVATION AGGREGATORS LLC
IPSecVPN (Internet Protocol Security Virtual Private Network) realizing system and method based on NetFPGA (Net Field Programmable Gate Array)
ActiveCN102065021BImprove processing speedRealize forwarding functionNetworks interconnectionData streamControl layer
The invention relates an IPSec VPN (Internet Protocol Security Virtual Private Network) realizing system and method based on a NetFPGA (Net Field Programmable Gate Array), wherein a control layer of a router is additively provided with an IKE (Internet Key Exchange) module, a security relation database mapping module and a security policy database, and a key management module is used for dynamically managing the key, the security relation and the security policy; and a forward layer is additionally provided with two independently designed IPSec input and output process modules in the original NetFPGA standard router architecture by sufficiently utilizing the modularization reusable idea of a NetPGA development board. The scheme of the invention can realize the route forward function of the data flow in a hardware manner, and can also realize the great mass of calculation functions required by the IPSecVPN in a hardware manner, such as safe detaching / packing load and completeness authentication; in addition, the invention can effectively make a compromise on the data flow forward performance and the IPSec protocol processing performance.
Owner:北京地平线轨道技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com