Deployment method of IPSec-VPN in address discrete mapping network
An address and network technology, applied in the field of network applications, can solve the problems of identity spoofing, data encryption, data tampering, etc., and achieve the effect of improving network reliability, improving security level, and efficient encryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
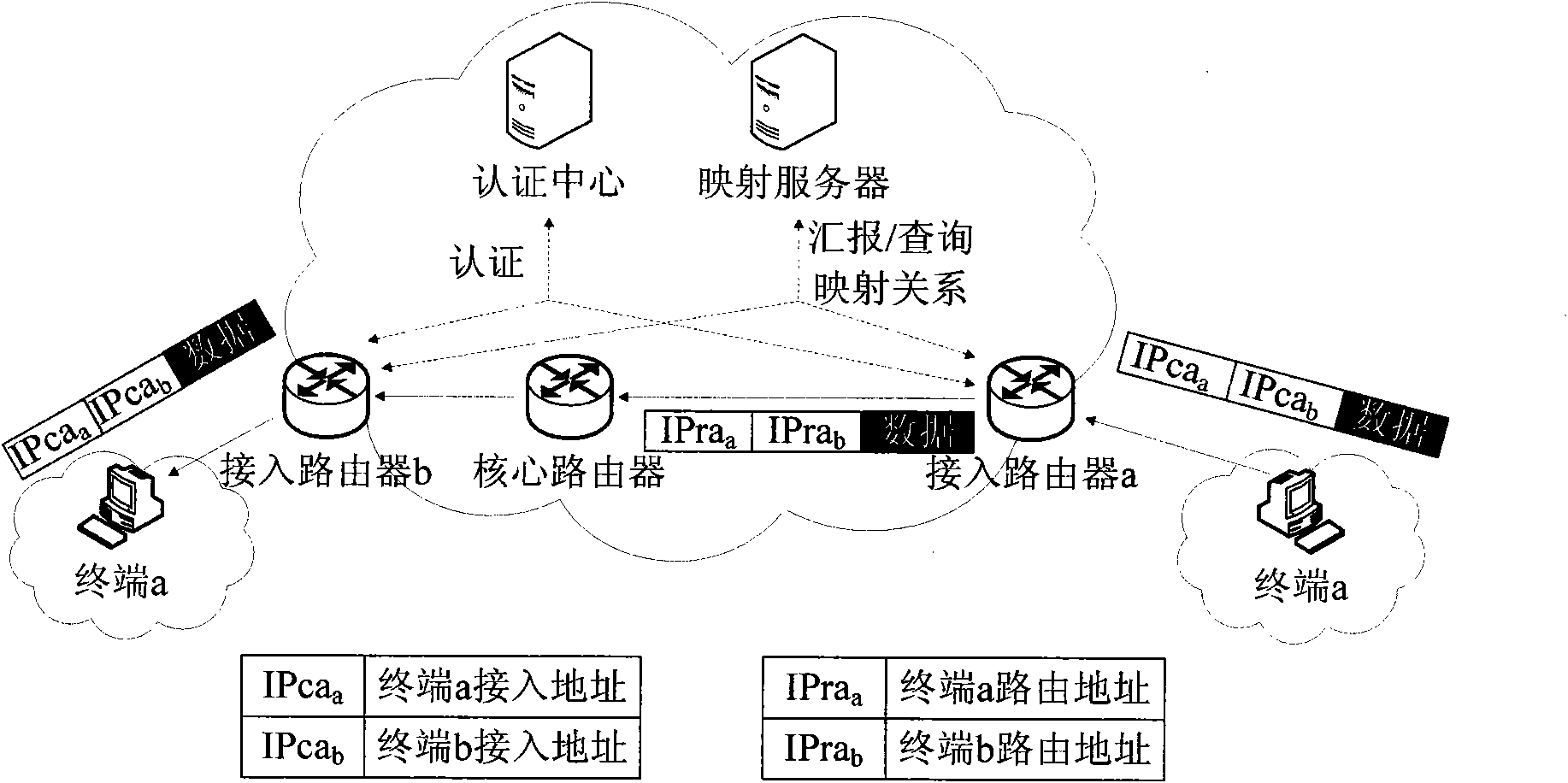
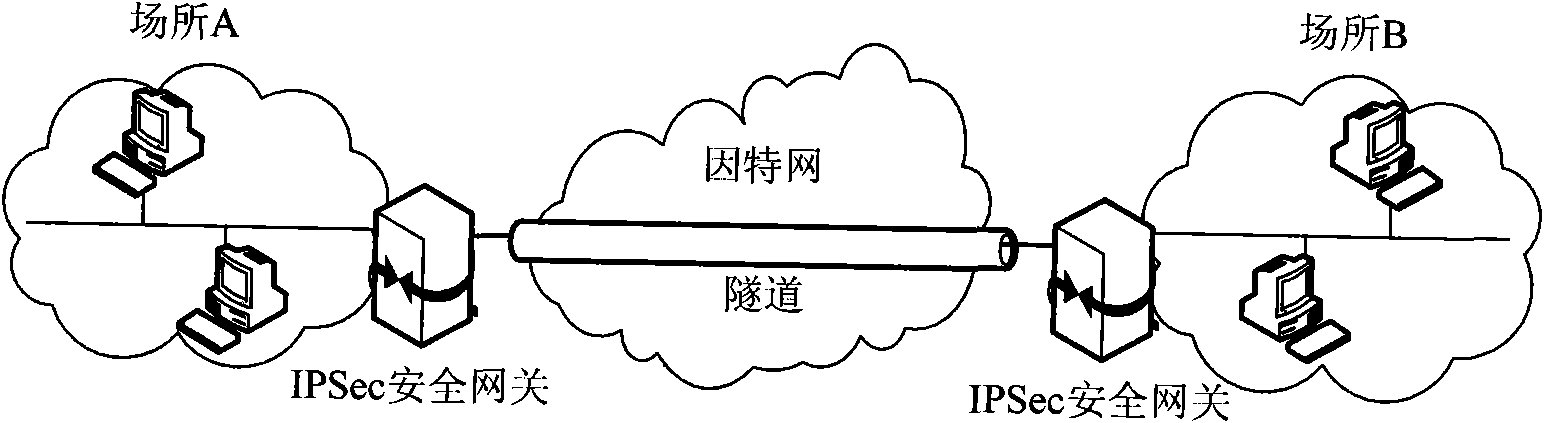
[0052] Example 1 as Figure 5 In the shown address separation mapping network IPSec-VPN deployment method, in this embodiment, an IPSec-VPN network passing through the core network is established between two access routers AR corresponding to two access networks that need to communicate with each other. VPN tunnels to protect communications between access networks.
[0053] Such as Figure 6 The shown communication flow chart of the IPSec-VPN deployment method in the address separation mapping network, the communication process includes the following three stages: .
[0054] Phase 1: Negotiation of security association phase, which completes the negotiation and establishment of security association SA between access routers, which is divided into two steps:
[0055] Step 1. The source-end access router a and the peer-end access router b use the access network end as the tunnel port, and use the access address pool of the access network as the object to be protected, negotiat...
Embodiment 2
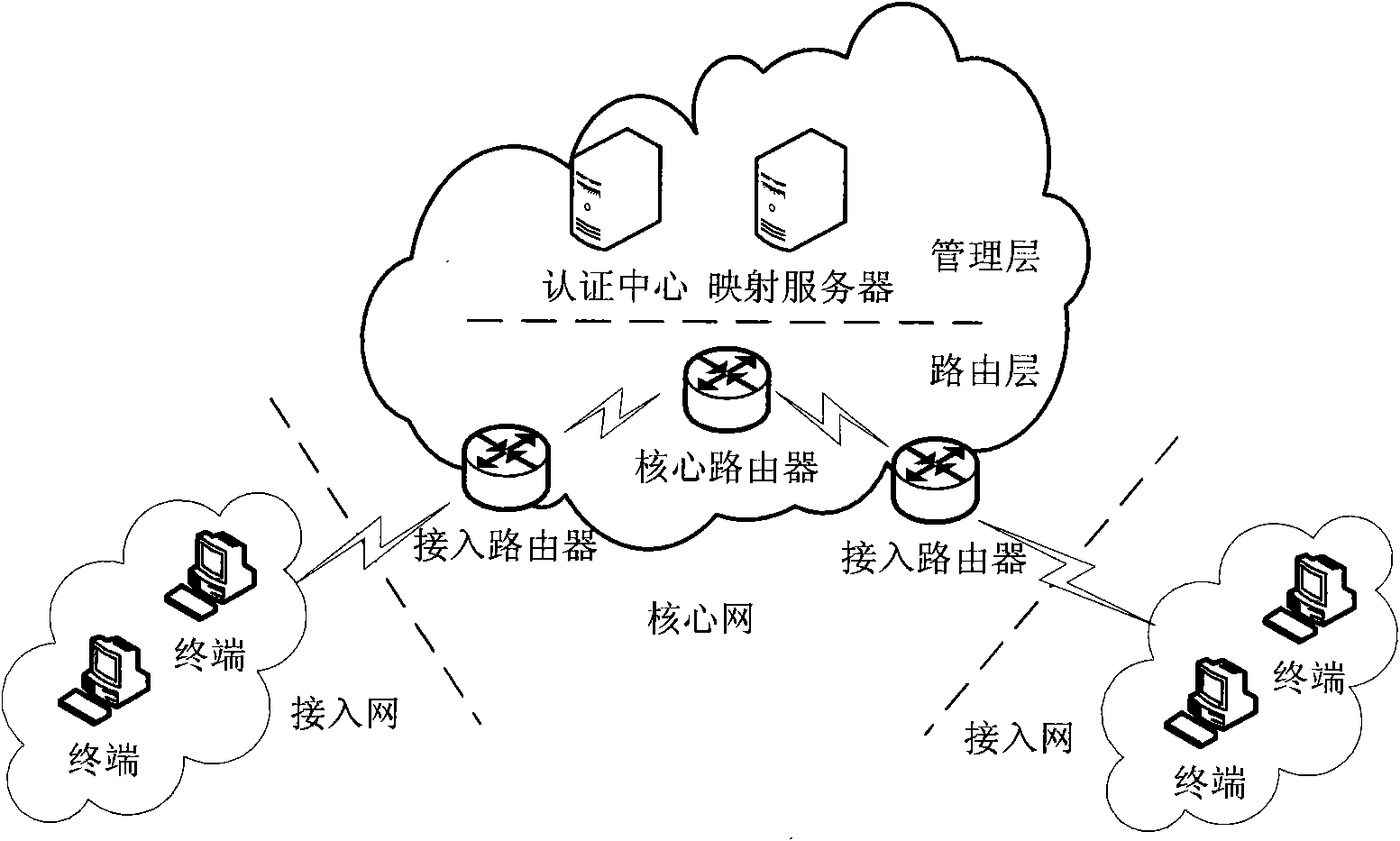
[0066] Example 2 as Figure 7 The implementation example of IPSec-VPN deployment in the address separation mapping network shown in the figure, the core network is composed of access router a, access router b, core router, authentication center and mapping server; terminal a and terminal b are used as access network users ; Establish an IPSec-VPN tunnel between access routers a and b.
[0067] In this specific implementation, the design of the access router is as follows Figure 8 As shown, the access router is composed of two parts, the user layer and the kernel layer. The user layer includes: user console module, IKE module, mapping table maintenance module and address pool module; the main body of the kernel layer is composed of three major modules: IPSec Kernel processing module, system kernel module and address separation mapping module.
[0068] The functions of each module in the user layer are as follows:
[0069] User console module: access to the router management...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com