User identification method based on multi-kernel learning fused with mouse and keyboard behavior characteristics
A multi-core learning and user identification technology, applied in the field of identity recognition, can solve problems such as the inability to achieve non-interference continuous authentication, differences in mouse and keyboard operation behaviors, and differences in recognition effects.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
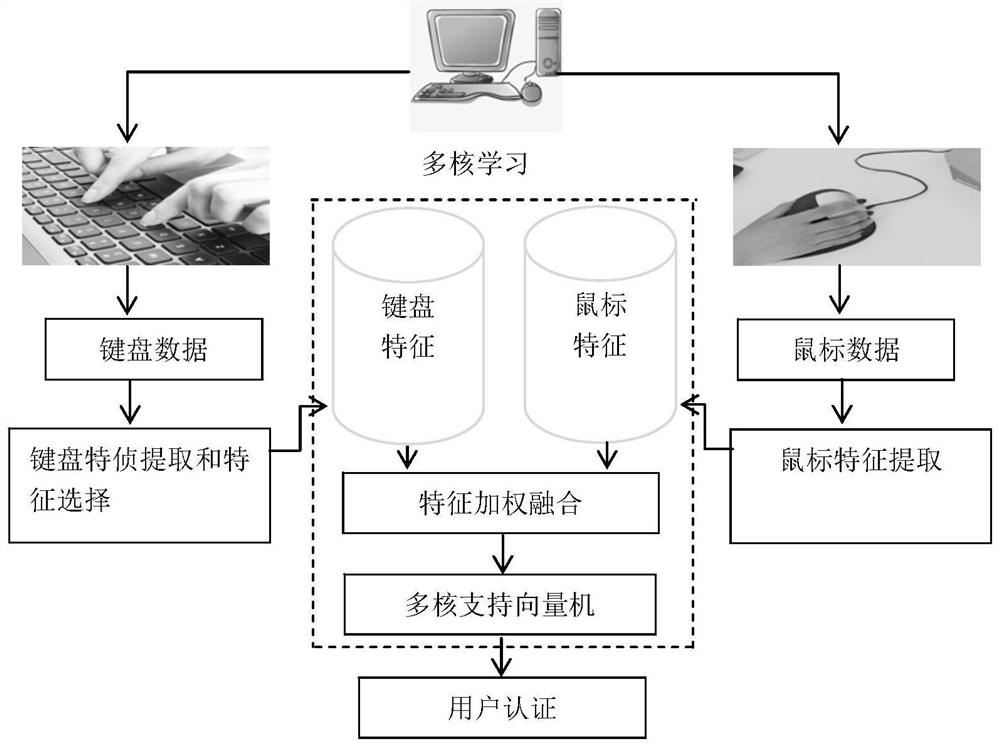
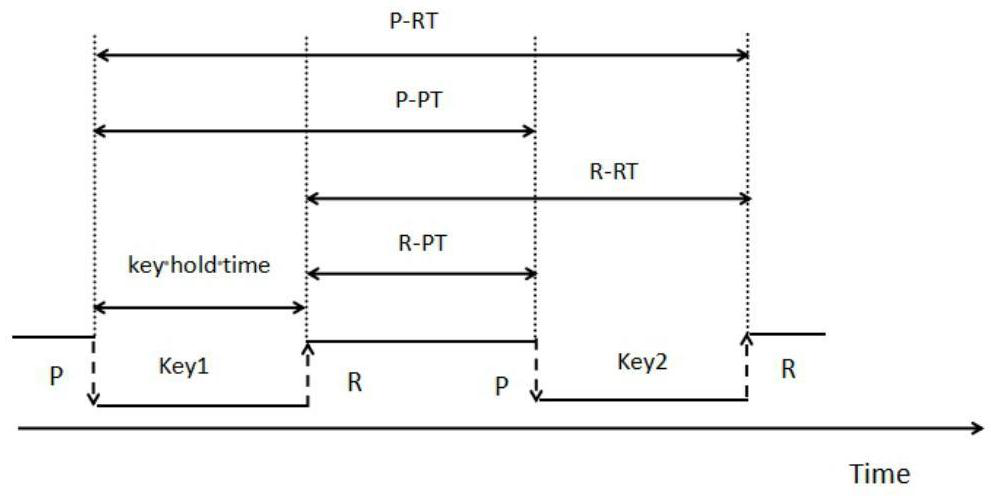
[0017] Such as figure 1 As shown, the present invention provides a user identification method based on multi-kernel learning (multiple kernel learning, MKL) fusion mouse and keyboard behavior characteristics, comprising: step 1, obtaining two types of human-computer interaction data of keyboard and mouse; Feature extraction with mouse features; step 3, feature mapping based on multi-core learning algorithm; step 4, use classifier modeling for user identification.
[0018] Step 1. Obtain human-computer interaction data of keyboard and mouse
[0019] In order to collect experimental data more realistically, 15 users were collected through the collection program in an uncontrolled environment. The data collection program uses HOOK technology, and the user can run the mouse and keyboard collection program in the background. There is no impact, and the user's operation is not subject to any restrictions. The collected data is the real data generated by the keyboard and mouse opera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com