User authentication device, user authentication method
A user authentication and user technology, applied in digital data authentication, computer security devices, image data processing, etc., can solve problems such as inability to deal with individual behavior patterns, and achieve the effects of shortening calculation time, efficient authentication, and high-speed verification processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0059] [Summary and Features of User Authentication Device in Embodiment 1]
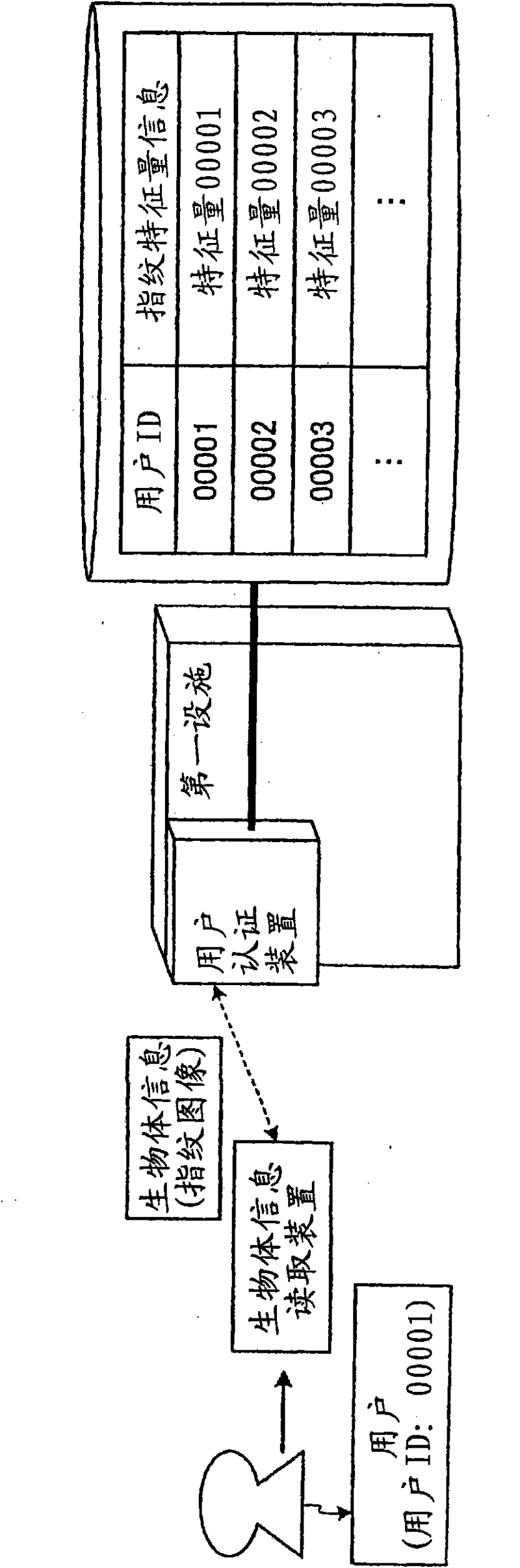
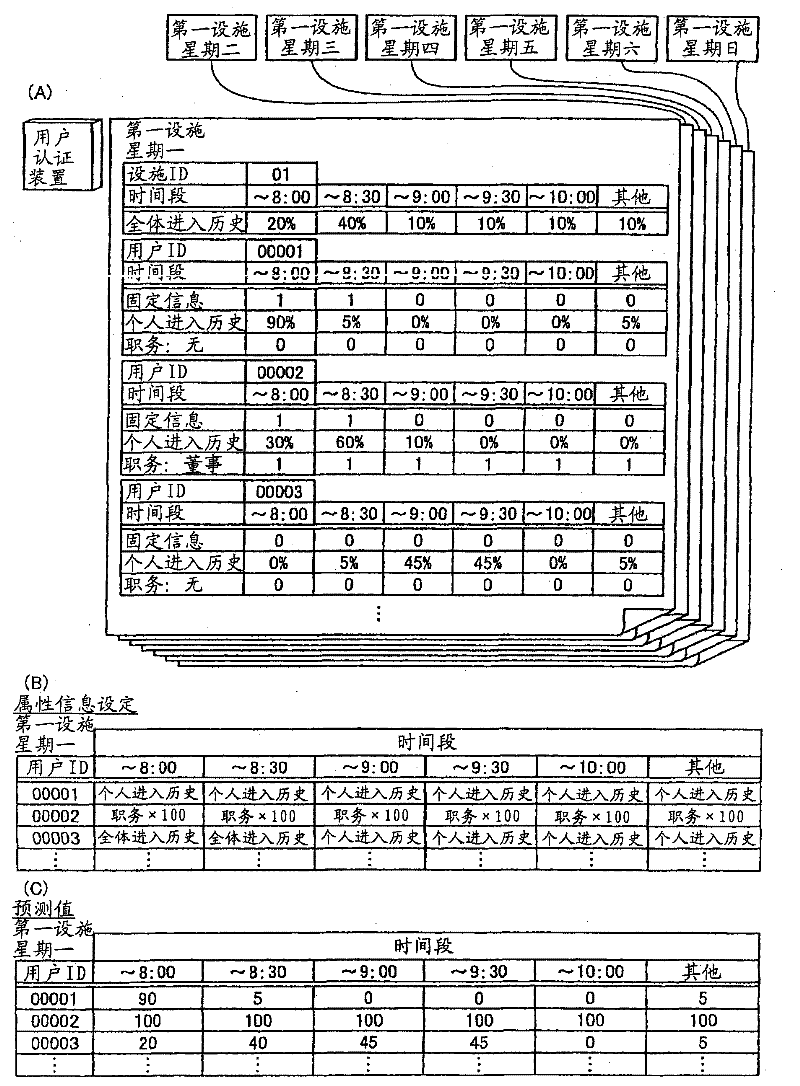
[0060] First, use Picture 1-1 , Figure 1-2 as well as Figure 1-3 , to specifically describe the main features of the user authentication device in Embodiment 1. Picture 1-1 , Figure 1-2 as well as Figure 1-3 It is a diagram for explaining the outline and features of the user authentication device in the first embodiment.
[0061] In summary, the user authentication device in Embodiment 1 performs user authentication using biometric information.
[0062] That is, if Picture 1-1 As shown, for example, a user (user ID: 00001) who wishes to enter the "First Facility" which is one of a plurality of facilities installed on the company site makes the biometric information reading device read his own fingerprint, and when When the biometric information reading device sends the "fingerprint image" as the user's biometric information to the user authentication device, the user authentication device ...
Embodiment 2
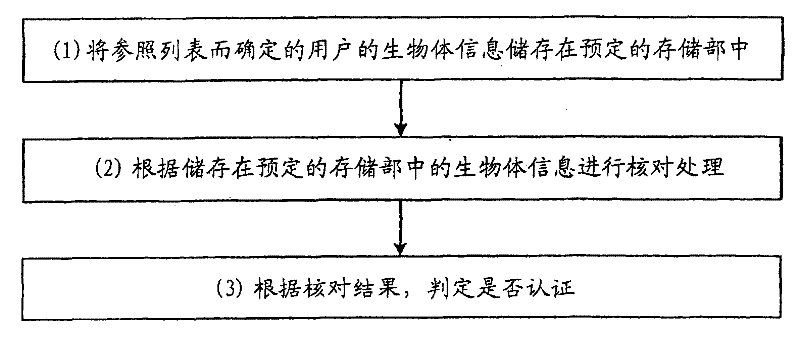
[0139] In the first embodiment described above, the case where the biometric information is stored in the predetermined storage unit in advance is described, and in the second embodiment, the case where the biometric information stored in the predetermined storage unit is cleared according to the situation is described.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com